Semperis, a pioneer in identity-driven cyber resilience, announced the release of Lightning Identity Runtime Protection (IRP), a new identity threat detection and response (ITDR) offering that uses machine learning models developed by identity security experts to detect widespread and successful attack patterns such as password spray, credential stuffing, other brute force attacks, and risky anomalies.
The first offering in the Semperis Lightning™ platform, IRP brings critical identity context to attack pattern and anomaly detection, helping organizations spot and quickly respond to high-risk events.
Semperis' real-world experience
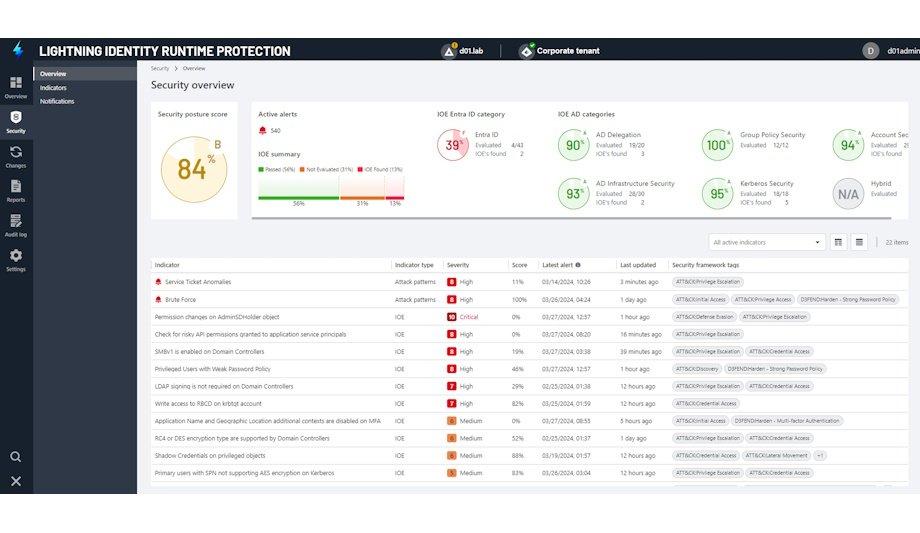
Lightning IRP addresses a persistent problem for cyber defenders: Known identity attack patterns like password spraying continue to be extremely successful because of the difficulty in detecting and responding to the sheer signal volume and noise.
Lightning IRP focuses defenders on the most critical identity attack alerts and reduces noise
Using trained algorithms based on Semperis' real-world experience responding to identity attacks in the wild and supporting the world's largest enterprises and government agencies, Lightning IRP detects sophisticated identity attacks that traditional ML solutions miss. Lightning IRP focuses defenders on the most critical identity attack alerts and reduces noise by layering in an identity-risk fabric that draws insights from multiple sources, including:
- Directory change tracking data across hybrid Active Directory and Entra ID environments.
- Hundreds of security indicators of exposure and compromise, regularly updated by Semperis' identity threat research team.
- Tier 0 attack path analysis to map out risky relationships to privileged groups with access to sensitive data.
Real-life identity system
“Detecting an anomaly is relatively easy,” said Semperis CEO Mickey Bresman. “Putting it into context is where the challenge is. We’ve combined deep machine learning expertise with our first-hand knowledge of how real-life identity system attacks work to provide meaningful context that helps organizations isolate and address high-risk threats.”
“IRP uses a growing threat library of exposures, compromises, and attack patterns in parallel with a continuous stream of identity security data to significantly accelerate an effective response to identity system threats,” said Semperis Chief Scientist Dr. Igor Baikalov, who before joining Semperis led the development of security intelligence and risk analytics solutions at Bank of America. “Identity Runtime Protection focuses on several use cases, including anomalous logons and service ticket anomalies, that have been problematic for years because they are hard to detect and respond to at scale,” said Dr. Baikalov.
Semperis’ identity threat intelligence
Lightning IRP captures, analyses, and correlates authentication activities with Semperis’ identity threat intelligence to detect known attack patterns or signal malicious behavior, including:
- Password spray attacks: Monitors logon attempts to detect patterns indicative of a password spray attack.
- Brute force attacks: Monitors repeated and rapid logon attempts against a single user to detect potential brute force attacks.
- Anomalous logons: Look for user logon anomalies that indicate an anomalous logon attack on AD.
- Anomalous resource access: Monitors a user’s activity and any interaction with services that indicate an attack on AD services.
- Service ticket anomalies: Look for suspicious service ticket requirements that indicate a Kerberoasting attack on AD.
Attack pattern detection capabilities
“Lightning IRP builds on our current offerings of pre-attack scanning for indicators of exposure and compromise and our ability to see changes happening across on-premises Active Directory and Entra ID,” said Semperis VP of Products Darren Mar-Elia.
“We’re extending our live attack pattern detection capabilities, changing the way the industry applies machine learning to detect cyberattacks.”
Learn why leading casinos are upgrading to smarter, faster, and more compliant systems