Choosing the appropriate fingerprint technology for a given application is dependent on factors including the required level of security and matching accuracy, the desired capabilities and features, and the usability to achieve adoption and productivity goals.
A successful evaluation process will help ensure that this mature and proven user authentication method performs as expected.
Fingerprint biometric advantages
The speed, simplicity, accuracy, and cost-effectiveness of the fingerprint method have made it among the most widely used for biometric authentication across industry sectors ranging from banking and finance, retail, and healthcare, to government and law enforcement.
It performs biometric technology’s “something you are” function while offering unique characteristics that make it particularly valuable for many applications.
Unique identifier
The fingerprint biometric has the permanency of being reasonably stable and consistent over time
Among these characteristics is the pervasiveness and special nature of the fingerprint -- almost everyone has one, and each is a unique identifier.
The fingerprint biometric has the permanency of being reasonably stable and consistent over time. It is also easy to acquire, measure, and process.
High adoption rate
Another key attribute of a fingerprint biometric is its ability to be protected against threats ranging from abuse and misuse to theft, imitation, and substitution. When it is used with recognition techniques the resulting solution performs with a combination of accuracy, speed, scalability, and ease of use.
Fingerprint biometric solutions also have the highest adoption rate among biometric authentication solutions according to an industry report published by Payments Journal.
Three interrelated components
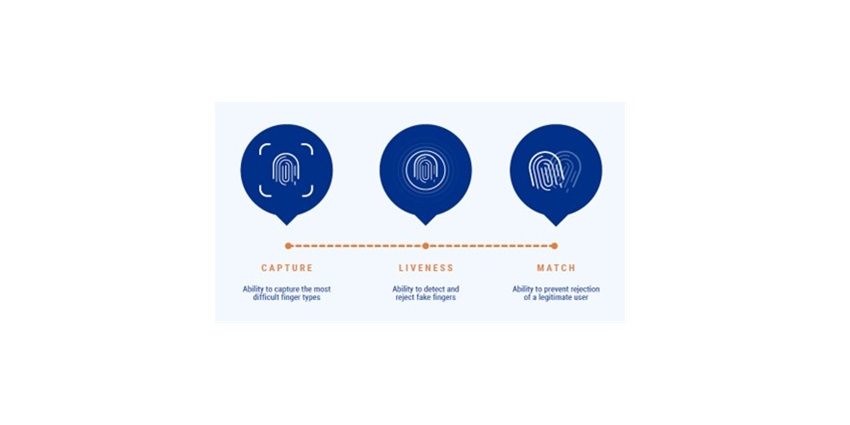
There are three basic components in any fingerprint biometric system as shown in Figure 1: capture (using a sensor that can capture even the most difficult finger types); liveness detection (using the Presentation Attack Detection – or PAD – technique); and matching (including preventing rejection of a legitimate user).
Biometric algorithm
The sensor captures and pre-processes the fingerprint data. It must be able to successfully capture fingerprint images for a range of skin types and print conditions under diverse temperatures, humidity, light, surface oil, dust, dirt, and other environmental conditions.
A biometric algorithm then extracts minutiae data about the fingerprint ridges (endings, bifurcations, islands, etc.) and their orientation and position.
PAD technique
Implementing a presentation attack detection (PAD) technique at this stage activates the fingerprint biometric system’s second key element: liveness detection. This verifies the fingerprint’s authenticity and that it belongs to a living person.
The system’s third element – matching – occurs after the PAD-verified fingerprint dataset has been securely stored as a record, known as a template, inside an enclave with cryptographic protection.
Check for liveness
The corresponding template of the legitimate user is then retrieved from secure storage
When the fingerprint is presented for matching, it is rechecked for liveness. The corresponding template of the legitimate user is then retrieved from secure storage and the process of matching the fingerprint with this template is executed.
This must be completed accurately and without rejecting a legitimate user.
Types of fingerprint sensing technologies
There are four prevailing categories of sensing technologies used with fingerprint readers: optical, capacitive, thin-film transistor (TFT), and multispectral imaging (MSI).
- Optical and capacitive method
Optical is the most mature sensor technology and offers the benefits of a compact size, good capture
Optical is the most mature sensor technology, and offers the benefits of a compact size, good capture and matching performance, a small enough size to fit in most desktop environments or shared workstations, and a high level of accuracy at a cost-effective price point across all use cases.
The capacitive method, on the other hand, is less prone to fake finger attempts while also offering a thin and compact size for space-limited applications, the power efficiency to support battery-operated devices, and the ability to handle both indoor and outdoor lighting conditions.
- TFT technology
The third technology goes a step further in capture accuracy. TFT technology can accurately recognize the smallest fingerprint features with ultra-high resolution and is used either as a larger-size matrix capacitive proximity detector (capacitive fingerprint sensor) or a larger-area matrix light detector (optical fingerprint sensor).
It is ideal for in-the-field mobile identification applications that require a cost-effective, ultra-slim, and lightweight solution with low power consumption.
- MSI technology
MSI technology differs from all three approaches, projecting multiple colors of light into the finger from different angles to collect both surface and subsurface biometrics data. It captures the most difficult fingerprints of diverse demographics, in a wide range of challenging environments.
HID has used this patented technology in fingerprint readers that are compliant with ISO 30107-3 PAD Level 2 for advanced anti-spoofing against fraud. The technology also improves matching and offers sophisticated endpoint security that prohibits cyber criminals from gaining unauthorized access to networks by turning fingerprint readers into secure endpoints.
Best practices for technology selection
Much is expected of the current fingerprint solutions, including delivering a low total cost of ownership
Much is expected of the current fingerprint solutions, including delivering a low total cost of ownership. There are three top considerations: security, suitability, and usability.
Each is important and the best approach is to strike a balance between all three. Following are the questions to ask during the selection process:
Security:
- What is the regulatory environment? Financial and government services, healthcare, and law enforcement are some examples of highly regulated sectors with elevated security compliance requirements.
- Are there mandates in place for advanced capturing and biometric authentication specifications?
- How important is it to ensure anti-spoofing through liveness detection?
- Will endpoint security be required so that, if the fingerprint device is hacked, no network, system, or data behind the firewall will be impacted?
Suitability:
- Where will the biometric technology be implemented? There will be additional considerations if it is to be embedded in portable, battery-operated devices that require low power consumption.
- Where will the technology be used? Will it need to fit into small spaces or be used in challenging indoor or outdoor conditions and environments?
- Will durability be important? Some deployments will face unpredictable weather and difficult lighting conditions for image capture.
- Will the technology be used for mission-critical border control or a more common – and less demanding -- commercial use?
Usability
- Is it critical that the technology easily and consistently perform capture and matching?
- Will there be high volumes of fingerprint captures and matches?
- Is “friction frustration” a concern? If so, the solution must perform matching quickly and accurately to sustain high levels of user productivity.
- Will the fingerprint device be used by one person exclusively, or multiple people in a shared workstation setting?
- How diverse is the user population? Some readers are designed to handle all types of fingerprints and diversified demographics.
Different applications
Fingerprint biometrics is a proven solution to address real-world challenges, each with its requirements
The answers to these questions will help determine the best choice of fingerprint technology. Different applications apply fingerprint biometrics to very different use cases but in all cases. It is a proven solution to address real-world challenges, each with its requirements.
For instance, in a healthcare clinician’s terminal area or a similar shared environment with limited space, a durable, low-profile capacitive sensor may be the right answer. For an organization in a highly regulated, mission-critical environment like a bank or border control agency, advanced technologies such as MSI readers may be needed to avoid the serious repercussions of a spoofed identity or the rejection of a legitimate one.
Requirements for a biometric solution
These are just a few of the requirements to consider when choosing a fingerprint solution.
- In banking and finance, alone, fingerprint biometrics is used for applications ranging from transacting at the ATM to customer onboarding (eKYC), compliance (AML/KYC), and fraud prevention.
- The retail sector adds even more, including age verification, loss prevention, point of sale (POS) security, self-service checkout, and secure time and attendance.
- Law enforcement organizations have their unique requirements, using fingerprint biometrics for background checks, criminal booking, crime investigation, inmate management, mobile identification, and more.
- For government agencies, typical applications include benefits distribution, border security, citizen ID, employ authentication (SSO/MFA), and voter registration.
Each application requires a thorough assessment of the best fingerprint technology for the job.
The right touch
The right solution will deliver the optimal balance of security, suitability, and usability
Fingerprint biometric solutions empower a wide range of use cases with the simple touch of a finger.
The right solution will deliver the optimal balance of security, suitability, and usability based on an analysis of criteria including specific application requirements, the characteristics and size of the user population, and challenges posed by environmental conditions.
Accuracy, efficiency, and security
The world faces increasingly dangerous fraud, account takeover, and impersonation threats.
As industries and enterprises work to improve and evolve their identity and access strategies to combat these threats, fingerprint biometrics continue to prove their value through solutions that meet the key selection criteria while delivering the highest levels of accuracy, efficiency, and security.
Learn why leading casinos are upgrading to smarter, faster, and more compliant systems




























