Retail surveillance
Wachter Inc., a pioneering technology solutions integrator and innovator, is pleased to provide the Loss Prevention Research Council (LPRC) with a state-of-the-art Proto LUMA hologram unit to enhance retail education and innovation efforts. This advanced technology will serve as an immersive platform to educate the retail community on loss prevention, history, and ongoing trends, while also offering dynamic marketing and engagement opportunities. Proto LUMA unit The Proto LUMA unit, a fully...
More than half (52%) of retail workers say they are likely to leave their current job in the next 12 months due to personal safety concerns, according to new research conducted by the Loss Prevention Research Council (LPRC) and in partnership with Verkada. The State of Retail Safety report reveals an alarming escalation in workplace violence from 2024, and offers critical insight into solutions that can protect retail workers, consumers and inventory without escalating tensions. Key findi...
The retail industry is perennially on the frontline of crime, particularly theft. From small high-street boutiques to sprawling department stores, retailers face the dual challenge of ensuring customer satisfaction while protecting their stock and assets. The safety of staff and shoppers is of paramount importance, but so too is the security of goods. This is where advancements in security solutions, tailored explicitly for retailers, are revolutionizing the industry. Scale of the issu...
Cozaint, a pioneer in innovative video surveillance solutions, announces the launch of ALICE1™, the first self-contained video surveillance recording and storage system that provides businesses with decades of secure, affordable video retention. By leveraging the proven reliability of Linear Tape Open (LTO) technology with a cloud-based search platform, ALICE1 makes it possible for organizations to store unlimited video footage at a fraction of the cost of traditional hard-drive solutions...
The latest generation of AI video solutions is significantly outperforming conventional security systems in retail applications, achieving faster return-on-investment and delivering notable new benefits, says IDIS in its latest market assessment. While conventional surveillance systems are focused largely on security and targeted at loss prevention, the latest AI-powered video solutions are proving to be as attractive to retail sales directors, marketing departments, and heads of finance, says...
3xLOGIC, the major provider of integrated and intelligent security solutions, has unveiled the InterACT Camera Series, a powerful new video surveillance solution. Combining high-definition imaging, edge-based deep learning analytics, and integrated deterrence features, InterACT proactively prevents crime before it takes place. Designed for businesses of all sizes in sectors such as retail, education, hospitality, and construction, InterACT cameras detect and respond to threats in real time,...
News
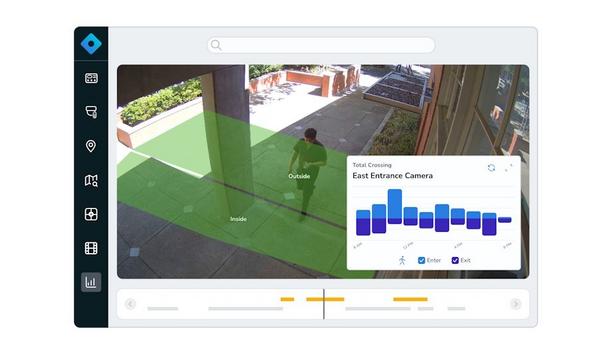
Rhombus, a pioneer in cloud-managed physical security solutions, announced the expansion of its AI-powered Operational Analytics capabilities with two powerful new features: Line Crossing and Occupancy Counting. These solutions give organizations real-time spatial intelligence tools to improve how they manage traffic flow, space utilization, and staffing. Both work with existing Rhombus camera infrastructure and can be centrally managed from the Rhombus console. Traditional surveillance by unlocking Rhombus persists to grow video intelligence beyond traditional surveillance by unlocking AI-fueled insights Rhombus continues to expand video intelligence beyond traditional surveillance by unlocking AI-fueled insights that help businesses solve everyday operational challenges. With these new features, security footage instantly becomes a live source of business intelligence to give teams a clear understanding of precisely how spaces are used and how to improve them. Right AI and powerful analytics "Video systems have long been siloed for security use only," said Brandon Salzberg, Chief Technology Officer at Rhombus, adding "But with the right AI and powerful analytics, those same systems can also power real-time operational intelligence that helps businesses grow." He continues, "Line Crossing and Occupancy Counting are great new examples of how we’re unlocking broader value from existing security camera infrastructure." Line crossing Line Crossing lets organizations define custom boundaries within camera views to monitor the directional traffic of how and when people or vehicles cross from one area to another. Line Crossing lets organizations define custom boundaries within camera views to monitor the traffic These insights are critical for identifying peak usage patterns and making layout or schedule changes that improve flow and efficiency. From retail store entrances to manufacturing loading docks, Line Crossing provides actionable data through clear, intuitive reporting. "We built Line Crossing to answer a simple question: how are people actually using your space?," said Rickey Cox, VP of Product at Rhombus, adding "We can surface directional insights that help organizations fine-tune everything from where to place employees to broader site design changes, without relying on guesswork." Occupancy counting Occupancy Counting provides ongoing estimates of how many people are in a given area by using AI models. The solution eliminates the need for manual headcounts or check-in systems, enabling teams to manage capacity and identify underused areas. These insights help organizations respond to fluctuations in foot traffic, optimize space layout, and better align staffing with actual demand. Solutions built for real-world use cases Both Line Crossing and Occupancy Counting are designed to support a wide range of operational needs across industries. For example: In retail environments, traffic flow data can inform smarter product placement and optimize underperforming departments. In manufacturing settings, tracking vendor deliveries can reduce congestion at loading docks. At fitness centers, occupancy visibility enables better fitness class and staff planning while minimizing safety hazards. Rhombus’ vision for smarter security, smarter operations The expansion of the Operational Analytics suite underscores Rhombus’ broader commitment to making its video intelligence solutions continually smarter, faster, and more adaptive. Rhombus’ broader commitment to making its video intelligence solutions continually smarter From real-time alerts to natural language video search, Rhombus uses AI to eliminate otherwise tedious manual efforts, accelerate investigations, and proactively detect threats. At the same time, the platform helps teams improve safety, increase efficiency, and make better decisions across their operations. By combining AI-enabled video analytics, audio detection, and IoT sensor data, Rhombus delivers a unified solution that adapts to each customer’s needs, supports evolving workflows, and helps organizations get more value from their existing security infrastructure. Seamless integration with the Rhombus platform Line Crossing and Occupancy Counting work with Rhombus’ dome, bullet, and multisensor camera series, and are available with no additional hardware or complex setup. Teams can access trends and reports through the same intuitive cloud-managed platform they already use, or pull data into their systems via Rhombus’ open APIs. Availability Line Crossing and Occupancy Counting are now available in limited release to customers with a Rhombus Enterprise license. Organizations interested in exploring the unique advantages of Rhombus’ Operational Analytics can book a demo.
Interface Systems, a pioneering managed service provider delivering business security, actionable insights, and purpose-built networks for multi-location businesses, released a compliance guide to help New York retailers meet the requirements of the state’s Retail Worker Safety Act and its chapter amendment, Senate Bill S740. The law’s 270-day grace period expired on June 4, 2025, and retailers that have not completed the mandated steps now face potential penalties and increased liability. Six-step plan for retailers Authored by Clay Campbell, Senior Vice President & General Counsel at Interface, the guide breaks down the law’s key mandates and outlines a clear, six-step plan retailers can begin implementing immediately: Publish a compliant workplace-violence policy in English and each employee’s primary language, including procedures for late shifts and cash handling, and a no-retaliation statement. Complete or update a location-specific risk assessment that scores each store on late hours, uncontrolled access, lone work, and past incidents. Then, rank sites and assign corrective action deadlines. Provide interactive training and communication at hire and at least annually (biennially for employers with fewer than 50 retail employees), and maintain signed training rosters aligned with payroll records. Deploy supporting technology by issuing and testing silent response buttons for chains with 500 or more employees statewide, pairing the devices with verified video, two-way audio, and live monitoring to reduce false alarms and speed response. Record and measure program data, storing the policy, assessments, training logs, alarm-test records, and police response times in a single repository while tracking incident rate, verified-alarm response time, training completion, and corrective-action completion. Stay inspection-ready by keeping all records current, accurate, and easily accessible. The New York Department of Labor may request documents after a complaint or major incident and can issue daily fines until violations are corrected. Silent-button requirement “Retailers that missed the deadline still have a path to compliance if they act quickly and follow a structured plan,” said Campbell. “This guide breaks the law down into six actionable steps that protect frontline employees and help businesses reduce their regulatory and legal risk.” The compliance guide also explains how Interface Systems’ Remote Video Monitoring and Virtual Security Guard services support the silent-button requirement and offer audit-ready evidence of incident handling.
March Networks, a global pioneer in intelligent video surveillance and business intelligence, has announced the integration of its video management platform with IONODES PERCEPT Body Camera. Unveiled at NRF PROTECT 2025 in Texas, the integration brings expanded mobility and visibility to March Networks’ open-platform ecosystem. Commitment to innovation and open integration “Our integration with IONODES’ PERCEPT Body Camera reflects March Networks’ ongoing commitment to innovation and open integration,” said Todd Robinson, Product Manager at March Networks. “As video surveillance moves beyond fixed setups, this collaboration helps us deliver flexible, intelligent solutions for today’s fast-moving retail and financial services environments.” “We’re excited about this new integration with March Networks, which allows us to better serve the financial and retail sectors with advanced mobile and IoT video technologies,” said Philippe Beauchamps, Lead Product Manager at IONODES. “This certified, end-to-end integration ensures seamless compatibility and unlocks greater value for our shared customers.” Enhancing Safety and Visibility The IONODES PERCEPT Body Camera is a compact, high-performance wearable IoT solution that delivers secure wireless connectivity. It works seamlessly with the March Networks Command video management system to help ensure a consistent, high-quality user experience. Whether worn by staff or security personnel, the device adds flexible surveillance coverage for busy, high-value, or customer-sensitive areas. For Retail Environments Employee Safety & De-escalation: The visible, active camera presence helps deter verbal aggression and escalating behavior from customers once they realize they are being recorded. Loss Prevention: Enables proactive monitoring at POS, returns, and high-theft zones. Flexible Deployment: Easily worn by floor staff working at checkouts, on the floor, or in the warehouse to enhance inter-departmental operational oversight. Wide-Angle Coverage: 180° lens increases visibility in dynamic environments with busy zones and blind spots. Real-Time Response: Enables remote guidance and fast escalation during customer disputes. Retail-Ready Design: Rugged and reliable for all-day use indoors, outdoors, drive-thru and curbside. For Financial Services Environments Staff Protection in Open Branch Designs: As physical barriers disappear, wearable cameras provide security in close proximity interactions. Roving Surveillance: Enhances monitoring at teller lines and customer service zones. Incident Documentation: Pre- and post-event recordings preserve the complete context. Training and Compliance Support: Real-world footage helps onboard staff and reinforces security protocols. Open Platform Integration: Works seamlessly with the existing March Networks Video Management System (VMS) infrastructure. PERCEPT Body Camera This new integration reinforces March Networks’ commitment to delivering flexible, open-platform solutions that meet evolving customer needs. By integrating seamlessly with best-in-class wearable IoT technologies, such as the PERCEPT Body Camera from IONODES, March Networks empowers organizations with intelligent tools that enhance employee safety, streamline operations, and enable rapid response when it matters most.
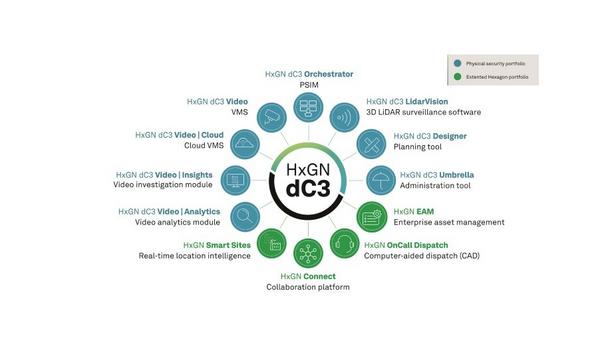
Hexagon’s Safety, Infrastructure & Geospatial division launches HxGN dC3 Video | Cloud, a new AI-enhanced, cloud-based video management system that enables more agile and resilient surveillance operations. With the increasing availability of reliable high-bandwidth connections, organizations are adopting a cloud-first strategy and turning to video surveillance as a service (VSaaS) for physical security, especially in distributed installations with many sites. The new cloud offering broadens the HxGN dC3 portfolio, Hexagon’s comprehensive ecosystem of physical security solutions, to provide organizations multiple deployment options and added benefits, such as increased scalability, real-time updates, and reduced operating costs. HxGN dC3 Video | Cloud HxGN dC3 Video | Cloud allows users to view, manage, and control video feeds from anywhere HxGN dC3 Video | Cloud allows users to view, manage, and control video feeds from anywhere. The platform also supports a broad spectrum of IP cameras from multiple vendors, avoiding dependence on any specific hardware. Video analytics leveraging generative AI significantly speeds up investigations by delivering insights through features like object tracking and behavior analysis. Generative AI also simplifies tasks such as monitoring, searching, and identifying actionable insights with seamless, natural-language interaction with the application. Robust security operations With end-to-end encryption, granular access controls, and compliance with global regulations, HxGN dC3 Video | Cloud supports robust security operations in health care, finance, retail, campus, public safety, and other enterprise organizations. “HxGN dC3 Video | Cloud represents a significant leap forward in video surveillance technology,” said Mladen Stojic, president of security for Hexagon’s Safety, Infrastructure & Geospatial division. “By combining the scalability and flexibility of the cloud with advanced AI-driven analytics, we’re empowering organizations to enhance their security operations with unprecedented efficiency, agility and insight.”
Elite Interactive Solutions, a remote video guarding innovator using patented intelligence and integration to achieve proven crime prevention, announces the third installment of its educational webinar series. Featuring some of the industry’s foremost subject matter experts and thought leaders, Elite Education Webinar sessions aim to inform security practitioners about the latest developments in security technologies and methodologies, crime and loss prevention, vertical market challenges, law enforcement, and more. New webinar The newest offering in the free series, “Driving Directions to Your Secure Auto Destination,” is set for Tuesday, July 15, at 11 a.m. Pacific Time / 2 p.m. Eastern Time. In addition to preventing automotive and property crime, the hour-long presentation will cover how the solution profoundly impacts losses, liability, and false alarms. substantial financial deficits More than a million vehicles were stolen in 2023, up more than 40% since 2019 More than a million vehicles were stolen in 2023, up more than 40% since 2019. Compounding those crimes are auto parts and accessories thefts, particularly of catalytic converters — a crime that can take as little as 30 seconds. A large percentage of the thefts take place at car dealerships, which suffer substantial financial deficits that also include staff time and insurance costs. The bottom line: traditional deterrents are not working, resulting in a loss of sales and revenue. Ineffective unmonitored surveillance cameras Over time, the effectiveness of unmonitored surveillance cameras has become marginalized. Criminals are no longer put off by cameras and realize video images are not investigated by law enforcement. Security guards are an immediate, onsite solution, but they are expensive and contracted only to observe and report. They do not physically engage intruders. The good news is there is one prominent security solutions provider that is drastically reducing losses for its customers. Elite Interactive Solutions’ remote guarding Elite’s command center agents directly prevented more than 16,000 crimes for automotive clients Whether it’s an auto dealership, parking facility, car rental lot or anywhere vehicles are kept — Elite Interactive Solutions’ remote guarding is the ultimate security and crime prevention answer. This solution prevents crime before it happens. During 2024, Elite’s command center agents directly prevented more than 16,000 crimes for automotive clients and assisted in nearly 500 arrests/detainments when it became necessary to engage law enforcement. The Elite difference is the unique integration of advanced AI-driven security technologies managed by highly trained remote security professionals and partnerships with law enforcement ensuring response. Session’s panel This session’s panel of leading crime prevention, auto dealer, technology, and community policing experts will help you evaluate how remote video guarding can help better protect your properties and vehicles — including augmenting or replacing security guards. Participating are Elite National Sales Director Jon Kromroy, former law enforcement executive Mitch Tavera, principal liaison for Elite’s Law Enforcement Advisory Board, and The Niello Company Director of Operations Matt Ryan. Discover the automotive storage solution to prevent: Vehicle & Parts Theft Vandalism of property Loitering & Trespassing Insurance Losses Legal Liabilities False Alarms
Dallmeier and Hexagon have agreed to form a technology partnership. Dallmeier electronic, a major manufacturer of video-based security solutions “Made in Germany”, and Hexagon, a global provider of digital reality solutions combining sensor, software, and autonomous technologies, are joining their expertise to work together and develop integrated security solutions for various application areas, particularly critical infrastructures. Panomera® technology integrated into Hexagon platform At the core of the partnership is the integration of Dallmeier Panomera® camera technology into Hexagon’s management solutions. Through this integration, video surveillance, video analytics and Physical Security Information Management (PSIM) can be combined to create seamless and holistic security solutions. Integration for greater security and efficiency for customers Customers would benefit from integrated and interoperable solutions that meet the highest security, efficiency and ease-of-use requirements. Whether at airports, railway operators, local authorities or financial institutions, users of the combination of Dallmeier video surveillance systems and Hexagon information and deployment management technology can detect security-related incidents quickly, assessing these incidents more accurately and respond effectively. Technology “Made in Europe” as a strategic advantage Both companies have decided to collaborate and work together on technology in order to offer high-quality security solutions In the context of geopolitical uncertainties and growing demands for data protection and sovereignty, European technologies are becoming increasingly important. Both companies have decided to collaborate and work together on technology in order to offer high-quality security solutions from Europe that are independent, trustworthy, reliable and sustainable. Comments on the partnership “We are very pleased to announce this partnership with Dallmeier. By combining our expertise, we can offer our customers even more innovative and comprehensive solutions,” explains Andreas Beerbaum, Vice President International Sales – Physical Security at Hexagon’s Safety, Infrastructure & Geospatial division. Thomas Dallmeier, Dallmeier’s CEO, adds: “Integrating our camera technology into VMS and PSIM systems from other manufacturers is a key milestone in Dallmeier’s strategy of offering a portfolio of open systems." "The integration of our Panomera® systems into the Hexagon platform enables end customers and system integrators using Hexagon to fulfill their requirements optimally.”


Expert commentary
A survey conducted by Blackhawk Network finds the average shopper plans to spend almost half of their holiday budget to buy gift cards this year versus only 39% in 2023. The global gift card market was valued at $1.3 billion USD in 2023, and it is projected to reach more than $5.2 billion USD by 2032. Fraud - a growing concern While gift cards continue to be top of mind for consumers for streamlined gifting, gift card fraud is a growing concern for consumers and businesses alike. According to the U.S. Department of Homeland Security’s Homeland Security Investigations (HSI) unit, gift card fraud, perpetrated by Chinese and other organized retail theft (ORT) rings, can be attributed to losses in the hundreds of millions of dollars globally, and is being used to fund other illicit crimes such as drug and human trafficking. The retailers implement procedures to mitigate attacks. Using data insights to detect emerging threats and identify hidden connections is among the ways retailers can protect the integrity of their gift card programs. How gift card fraud is manifested Typical physical gift card scheme involves purchasing items using stolen credit cards Gift card fraud occurs both at physical locations and online. A typical physical gift card scheme involves purchasing items using stolen credit cards and then returning the items for store credit or gift cards. While some stores have strict and well-enforced return policies to ensure that only customers entitled to refunds receive them, fraudsters employ fake tracking ID (FTID) tactics that focus on bypassing identification checks during returns, enabling them to return stolen merchandise or exploit refund policies. They use a combination of fake IDs and altered receipts or rely on lax return processes to achieve their goals. Once gift cards are obtained, criminals can sell them at a discount or use them for personal purchases, effectively converting stolen goods or false claims into untraceable funds. Tactics to convince consumers One tactic involves draining a gift card by obtaining the barcode, Card Verification Value (CVV) number, personal identification number (PIN), or activation code from beneath the slim cardboard packaging. Once they obtain the code(s) from physical cards, they reseal them, monitor online for consumers to buy and load the cards, then spend the balances before the consumers can. Some merchants have sought to combat this by keeping store-branded gift cards behind the checkout counter, handing them out after purchase. However, this approach can be costly and inconvenient for both retailers and customers, as it requires additional resources for in-store management and potentially slows the purchasing process. Other online tactics involve people who misrepresent themselves in a variety of phishing scams to convince consumers to purchase gift cards, then provide the card details to others who then drain the cards. Scammers tell the victim which gift card to buy (and where). They might say to put money on a card for an online store, a streaming service, or a specific retail store. These scammers often work as part of an organized crime network. Retailers leveraging open info, AI, to combat gift card fraud Retailers are empowered to improve the monitoring and analysis of gift card transaction patterns A growing number of retailers are leveraging publicly available (PAI) and hard-to-reach data and analytics to extract key insights that help fight various forms of gift card fraud and stay ahead of evolving fraud tactics. With such tools, retailers are empowered to improve the monitoring and analysis of gift card transaction patterns, identify anomalies, and implement proactive measures to prevent fraudulent activities before they can impact consumers and sales revenues. Retailers need this type of approach in their efforts to battle scammers, who continue to refine tactics for draining gift cards and committing other types of retail fraud. Beyond simply refining their techniques, fraudsters continue to advance their use of technology to commit their crimes. For example, cybercriminals also use bots to perform brute force attacks on gift card websites. They are increasingly using AI to perpetrate gift card fraud. Leveraging Latest AI And LLMs Retailers need to continually upgrade their fraud-fighting strategies and technologies as well. They can lean into PAI and analytics, in conjunction with existing security operations and investigations, to safeguard the integrity of their gift card programs and demonstrate their commitment to customers, reinforcing brand trust. In addition to leveraging the latest versions of AI and large language models (LLMs), retailers can take advantage of open-source intelligence (OSINT). By leveraging PAI and difficult-to-obtain data with analytics, brands are using OSINT to more quickly seize on evolving threat patterns to recognize current and shifting fraud schemes and stay ahead of evolving fraud tactics. In this way, the AI operates as a resource multiplier, compiling and processing data at faster-than-human speeds, while enabling the ability to extract actionable insights at scale. Users can make more accurate and timely decisions. Retailers need to upgrade their fraud-fighting strategies and technologies. Safeguarding gift cards, customer trust, and Brand integrity OSINT can inform retail security managers, loss prevention directors, fraud investigators, and others to help spot and deter gift card fraud. By using AI to detect patterns and anomalies, OSINT solutions can help fraud specialists spot patterns of suspicious activity that may indicate distinct instances of fraud. AI further helps fraud specialists identify members of ORT rings by uncovering hidden connections among seemingly unrelated individuals and transactions. The market for retail gift cards is large and continues to grow, and so too, is the gift card fraud threat. By adopting OSINT for fraud prevention, retailers can stay ahead of tech-savvy criminals, safeguarding gift card revenue streams as well as customer trust and brand integrity.
Choosing the appropriate fingerprint technology for a given application is dependent on factors including the required level of security and matching accuracy, the desired capabilities and features, and the usability to achieve adoption and productivity goals. A successful evaluation process will help ensure that this mature and proven user authentication method performs as expected. Fingerprint biometric advantages The speed, simplicity, accuracy, and cost-effectiveness of the fingerprint method have made it among the most widely used for biometric authentication across industry sectors ranging from banking and finance, retail, and healthcare, to government and law enforcement. It performs biometric technology’s “something you are” function while offering unique characteristics that make it particularly valuable for many applications. Unique identifier The fingerprint biometric has the permanency of being reasonably stable and consistent over time Among these characteristics is the pervasiveness and special nature of the fingerprint -- almost everyone has one, and each is a unique identifier. The fingerprint biometric has the permanency of being reasonably stable and consistent over time. It is also easy to acquire, measure, and process. High adoption rate Another key attribute of a fingerprint biometric is its ability to be protected against threats ranging from abuse and misuse to theft, imitation, and substitution. When it is used with recognition techniques the resulting solution performs with a combination of accuracy, speed, scalability, and ease of use. Fingerprint biometric solutions also have the highest adoption rate among biometric authentication solutions according to an industry report published by Payments Journal. Three interrelated components There are three basic components in any fingerprint biometric system as shown in Figure 1: capture (using a sensor that can capture even the most difficult finger types); liveness detection (using the Presentation Attack Detection – or PAD – technique); and matching (including preventing rejection of a legitimate user). Biometric algorithm The sensor captures and pre-processes the fingerprint data. It must be able to successfully capture fingerprint images for a range of skin types and print conditions under diverse temperatures, humidity, light, surface oil, dust, dirt, and other environmental conditions. A biometric algorithm then extracts minutiae data about the fingerprint ridges (endings, bifurcations, islands, etc.) and their orientation and position. PAD technique Implementing a presentation attack detection (PAD) technique at this stage activates the fingerprint biometric system’s second key element: liveness detection. This verifies the fingerprint’s authenticity and that it belongs to a living person. The system’s third element – matching – occurs after the PAD-verified fingerprint dataset has been securely stored as a record, known as a template, inside an enclave with cryptographic protection. Check for liveness The corresponding template of the legitimate user is then retrieved from secure storage When the fingerprint is presented for matching, it is rechecked for liveness. The corresponding template of the legitimate user is then retrieved from secure storage and the process of matching the fingerprint with this template is executed. This must be completed accurately and without rejecting a legitimate user. Types of fingerprint sensing technologies There are four prevailing categories of sensing technologies used with fingerprint readers: optical, capacitive, thin-film transistor (TFT), and multispectral imaging (MSI). Optical and capacitive method Optical is the most mature sensor technology and offers the benefits of a compact size, good capture Optical is the most mature sensor technology, and offers the benefits of a compact size, good capture and matching performance, a small enough size to fit in most desktop environments or shared workstations, and a high level of accuracy at a cost-effective price point across all use cases. The capacitive method, on the other hand, is less prone to fake finger attempts while also offering a thin and compact size for space-limited applications, the power efficiency to support battery-operated devices, and the ability to handle both indoor and outdoor lighting conditions. TFT technology The third technology goes a step further in capture accuracy. TFT technology can accurately recognize the smallest fingerprint features with ultra-high resolution and is used either as a larger-size matrix capacitive proximity detector (capacitive fingerprint sensor) or a larger-area matrix light detector (optical fingerprint sensor). It is ideal for in-the-field mobile identification applications that require a cost-effective, ultra-slim, and lightweight solution with low power consumption. MSI technology MSI technology differs from all three approaches, projecting multiple colors of light into the finger from different angles to collect both surface and subsurface biometrics data. It captures the most difficult fingerprints of diverse demographics, in a wide range of challenging environments. HID has used this patented technology in fingerprint readers that are compliant with ISO 30107-3 PAD Level 2 for advanced anti-spoofing against fraud. The technology also improves matching and offers sophisticated endpoint security that prohibits cyber criminals from gaining unauthorized access to networks by turning fingerprint readers into secure endpoints. Best practices for technology selection Much is expected of the current fingerprint solutions, including delivering a low total cost of ownership Much is expected of the current fingerprint solutions, including delivering a low total cost of ownership. There are three top considerations: security, suitability, and usability. Each is important and the best approach is to strike a balance between all three. Following are the questions to ask during the selection process: Security: What is the regulatory environment? Financial and government services, healthcare, and law enforcement are some examples of highly regulated sectors with elevated security compliance requirements. Are there mandates in place for advanced capturing and biometric authentication specifications? How important is it to ensure anti-spoofing through liveness detection? Will endpoint security be required so that, if the fingerprint device is hacked, no network, system, or data behind the firewall will be impacted? Suitability: Where will the biometric technology be implemented? There will be additional considerations if it is to be embedded in portable, battery-operated devices that require low power consumption. Where will the technology be used? Will it need to fit into small spaces or be used in challenging indoor or outdoor conditions and environments? Will durability be important? Some deployments will face unpredictable weather and difficult lighting conditions for image capture. Will the technology be used for mission-critical border control or a more common – and less demanding -- commercial use? Usability Is it critical that the technology easily and consistently perform capture and matching? Will there be high volumes of fingerprint captures and matches? Is “friction frustration” a concern? If so, the solution must perform matching quickly and accurately to sustain high levels of user productivity. Will the fingerprint device be used by one person exclusively, or multiple people in a shared workstation setting? How diverse is the user population? Some readers are designed to handle all types of fingerprints and diversified demographics. Different applications Fingerprint biometrics is a proven solution to address real-world challenges, each with its requirements The answers to these questions will help determine the best choice of fingerprint technology. Different applications apply fingerprint biometrics to very different use cases but in all cases. It is a proven solution to address real-world challenges, each with its requirements. For instance, in a healthcare clinician’s terminal area or a similar shared environment with limited space, a durable, low-profile capacitive sensor may be the right answer. For an organization in a highly regulated, mission-critical environment like a bank or border control agency, advanced technologies such as MSI readers may be needed to avoid the serious repercussions of a spoofed identity or the rejection of a legitimate one. Requirements for a biometric solution These are just a few of the requirements to consider when choosing a fingerprint solution. In banking and finance, alone, fingerprint biometrics is used for applications ranging from transacting at the ATM to customer onboarding (eKYC), compliance (AML/KYC), and fraud prevention. The retail sector adds even more, including age verification, loss prevention, point of sale (POS) security, self-service checkout, and secure time and attendance. Law enforcement organizations have their unique requirements, using fingerprint biometrics for background checks, criminal booking, crime investigation, inmate management, mobile identification, and more. For government agencies, typical applications include benefits distribution, border security, citizen ID, employ authentication (SSO/MFA), and voter registration. Each application requires a thorough assessment of the best fingerprint technology for the job. The right touch The right solution will deliver the optimal balance of security, suitability, and usability Fingerprint biometric solutions empower a wide range of use cases with the simple touch of a finger. The right solution will deliver the optimal balance of security, suitability, and usability based on an analysis of criteria including specific application requirements, the characteristics and size of the user population, and challenges posed by environmental conditions. Accuracy, efficiency, and security The world faces increasingly dangerous fraud, account takeover, and impersonation threats. As industries and enterprises work to improve and evolve their identity and access strategies to combat these threats, fingerprint biometrics continue to prove their value through solutions that meet the key selection criteria while delivering the highest levels of accuracy, efficiency, and security.
With the rise of organized retail crime (ORC) making headlines, retailers are grappling with the dual challenge of safeguarding both their staff and store assets, while addressing the economic pressures that impact profitability and consumer demand. RFID technology The key lies in identifying effective solutions to counter the current surge in ORC, enabling retailers to secure their vulnerable staff and protect inventory for paying customers. Technology plays a crucial role in supporting brands on this mission, with RFID technology continuing to be a valuable solution. It aids retailers in gaining better control over retail crime, leveraging inventory data. The ongoing surge in retail crime Inflation has elevated the challenges around affording items, prompting criminals to target the retail sector Seen as a global issue, the British Retail Consortium recently reported that incidents of theft have increased by 27% across 10 of the largest cities in the UK, with some cities reporting up to a 68% increase. In the US, retailer Target reported an inventory loss of $500 million for 2023, amounting to a 100-basis point hit to gross margins in 2023. The current surge in theft is not attributed to a singular cause. Inflation has elevated the challenges around affording items, prompting criminals to target the retail sector. Lack of preventive measures A significant contributing factor is the lack of sufficient preventive measures by law enforcement, which in some cases has led to a rise in more severe incidents. However, the implementation of technologies like RFID allows retailers to efficiently build cases against criminals, putting them in a stronger position when it comes to reporting thefts. Not all retail crimes are orchestrated by large entities or executed through sophisticated methods. Some stores have seen a reduction in staff numbers and, as a result, there are fewer people on the shop floor, making it easier for shoplifters to carry out their activities unnoticed. The true impact of retail crime Over 70% of retailers believed the threat of ORC had increased over the past five years, according to a recent survey The impact of retail crime on businesses extends beyond financial and economic consequences; it has also led to a surge in violence against retail staff, an ongoing trend elevated by the pandemic. Over 70% of retailers believed the threat of ORC had increased over the past five years, according to a recent survey conducted by the National Retail Federation. This escalation in violence not only results in immediate repercussions but also contributes to long-term mental health issues for staff, fostering an atmosphere of insecurity that has compelled some retailers to close their physical stores. Policy implementation Given the challenge of staff retention across various businesses, addressing retail crime becomes an even more urgent matter. Additionally, retailers are wary of their employees facing potential danger and the prospect of legal action. Consequently, many have implemented policies prohibiting employees from actively intervening when confronted with shoplifters. Privacy concerns with facial recognition Retail crime also affects customers, as businesses seek to offset losses by raising prices Retail crime also affects customers, as businesses seek to offset losses by raising prices, further burdening financially strained consumers. The presence of visible security systems not only makes stores more hostile but also diminishes the overall customer experience. While facial recognition technology is considered a potential solution, privacy concerns have emerged in its various applications. Today’s problems, yesterday’s solutions Retailers are resorting to historic measures such as steel cables, physical monitoring, or plastic screens to resolve customer issues. However, the reality is that these solutions are unfit for solving the problem, causing friction for both customers and staff. Digital solutions The newer approach involves equipping retail staff with body cams and providing new training The newer approach involves equipping retail staff with body cams and providing new training to deter shoplifters. Some stores are even offering the police discounted food and beverages to encourage their presence. The responsibility lies with management teams to seek effective solutions. In an era dominated by data and technology, retailers must shift their focus from traditional security methods to digital solutions that align with the challenges of today’s society and modern retail environments. Shrinkage When discussing theft or organized retail crime, retailers commonly use the term "shrinkage," referring to not only theft but the broader issue of lost inventory. Additional drivers of shrinkage include damage, fraud, and internal theft. A significant problem arises as losses are often based on guesswork and estimates rather than concrete numbers. Retailers may lack a comprehensive understanding of their inventories, further increasing the issue of shrinkage. Combating shrinkage Utilizing RFID technology notably helps in boosting inventory accuracy Some retailers still struggle with limited knowledge of the whereabouts of items, a challenge heightened by the issue of shrinkage. Utilizing RFID technology notably helps in boosting inventory accuracy. This enhancement enables retailers to obtain a clearer understanding of their inventory and the precise locations of items. Comprehensive strategy Changes in the in-store experience have highlighted the relevance of RFID, especially as self-service checkouts encounter double the shrinkage levels compared to traditional checkout stores. To combat retail theft effectively, a comprehensive strategy should involve the integration of labels, deactivation, electronic article surveillance, and data analytics. This combination works synergistically to reduce shrinkage and enhance product availability. Retail data analytics platforms RFID data can swiftly alert nearby stores, providing an opportunity for staff to monitor shop floors Linking hardware to an underlying data analytics platform empowers retailers to make more informed decisions. Retail data analytics platforms delve into alarms, deactivations, and visitor metrics, providing a deeper understanding of theft patterns. RFID technology drives efficiency by pinpointing frequently stolen items, allowing for the identification of theft patterns. In instances of flash mobs in major metropolitan areas, RFID data can swiftly alert nearby stores, providing an opportunity for staff to monitor shop floors and incoming customers. Real-time optimization The crucial question remains whether both shoppers and retailers are prepared to shoulder the responsibility for these additional precautions. Nevertheless, these changes leverage data more effectively, optimizing loss prevention strategies almost in real-time rather than relying on biannual inventory counts, therefore transitioning from static to dynamic loss prevention. Holistic approach Striking a balance between security measures and providing a seamless shopping experience is key In a retail environment, not all items require protection, and prioritizing the safeguarding of the most frequently stolen and valuable items can significantly impact shrinkage. A holistic approach to retail theft is imperative, considering the entire journey of an item through the retail environment. Striking a balance between security measures and providing a seamless shopping experience is key. Protection without hindrance As stores move towards being checkout-free, retail criminals (or ORC gangs) will be presented with lucrative opportunities to steal, so retailers need to be one step ahead by introducing unobtrusive and effective technology solutions. For example, case building can be improved with item-level data. RFID data offers a more precise means of assessing the value of stolen items compared to relying solely on CCTV. It provides detailed insights into the specific items removed from the store and the timing of these incidents. This proves beneficial in tracking repeat offenders. Increased visibility with a proactive approach The modern retail environment continues to evolve and criminals are never far behind. RFID technology plays a crucial role in minimizing shrinkage by enhancing inventory visibility. Moreover, it leverages the power of data to stay ahead, enabling better predictions of retail crime and the formulation of prevention strategies. This proactive approach allows for the implementation of more tailored solutions to alter outcomes positively.
Security beat
Companies at GSX 2023 emphasized new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the security market. Today, more than half of the company’s lineup supports AI at the edge so the customer has a wide choice of form factors when seeking to leverage the feature set. AI processing relay, extended warranty i-PRO is increasing their warranty period from 5 to 7 years, which could be a lifetime warranty in some cases I-PRO also has an “AI processing relay” device that accepts non-AI video streams and applies edge analytics. AI has progressed from a high-end technology to a feature available in a variety of cameras at different price points. i-PRO is also increasing its warranty period from 5 to 7 years, which could be a lifetime warranty in some cases depending on a customer’s refresh schedule and lifecycle management. Active Guard, MonitorCast The company’s video management system (Video Insight) is continuing to build new features including “Active Guard,” an integrated metadata sorter. Their access control platform, MonitorCast, is a Mercury-based solution that is tightly integrated with Video Insight. Their embedded recorders now have PoE built in. “We can move at a faster pace to fill out our product line since leaving Panasonic,” says Adam Lowenstein, Director of Product Management. “We can focus our business on adapting to the market.” Emphasis on retail and other verticals Shoplifting is a timely issue, and retail is a vertical market that got a lot of attention at GSX 2023. “We see a lot of retailers who are primarily interested in protecting employee safety, but also assets,” says Brandon Davito, Verkada’s SVP of Product and Operations. “Shrinkage is a CEO-level priority.” “Retailers are getting more engaged with security posture, instead of letting perpetrators walk,” Davito adds. Intrusion detection Verkada has an intrusion product that will notify a central station if there is an alarm On the alarm side, Verkada has an intrusion product that will notify a central station if there is an alarm, and operators can review videos to confirm the alarm. Other capabilities seeking to discourage trespassers include sirens, strobes, and “talkdown” capabilities. International expansion Verkada continues to expand internationally with 16 offices in all, including Sydney, Tokyo, and London. The core value proposition is to enable customers to manage their onsite infrastructure more simply, including new elements such as PTZ cameras, intercoms, and visitor management. Verkada emphasizes ease of use, including a mobile application to allow access to be managed across the user base. Forging partnerships “We are committed to the channel and industry, and we continue to build relationships and expand our reach,” says Davito. Among the industry relationships is a new partnership with Convergint, which was hinted at during the show and announced later the same day. They are also expanding their partnerships with Schlage, Allegion, and ASSA ABLOY. Working with other verticals They offer new features for K -12 schools, and a new alarm platform is easier to deploy and manage Verkada has also found success across multiple other verticals, notably healthcare, where they integrate with an electronic medical records system. They offer new features for K-12 schools, and a new alarm platform is easier to deploy and manage. They are integrating wireless locks to secure interior doors in schools, looking to secure the perimeter, and installing guest management systems. Transitioning the Mid-Market to the Cloud Salient is squarely focused on the “mid-market,” a large swath of systems somewhere between small businesses and enterprise-level systems. Pure cloud systems are not as attractive to this market, which has a built-out infrastructure of on-premise systems. Adding a camera to an existing system is easier and less expensive than tying it to the cloud. Benefits of cloud It’s a market that may not be ready for pure cloud, but there are benefits to be realized from adding a cloud element to existing systems. “We are continuing to augment our premise-based solutions with added cloud capabilities and flexibility,” says Sanjay Challa, Salient’s Chief Product Officer. The feedback Salient hears from their customers is “I want to own my data.” The hybrid cloud approach offers the right mix of control, flexibility, and unit economics. Cloud add-on capabilities We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive" Cloud add-on capabilities include bringing more intelligence about system operation to the user via the cloud. Over time, Salient expects to sell more cloud-centric offerings based on feedback from integrators and customers. “We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive over time,” says Challa. Vaidio AI technology Salient seeks to be a transition pioneer to help customers realize the path to the cloud. Their approach is “crawl, walk, run,” and helping customers make the transition at each stage. Salient has added AI to its product offering, incorporating Vaidio AI technology from IronYun into a powerful suite and broad array of on-premise analytics, which are gaining traction. The seamless approach makes it easy for customers to embrace AI analytics, although Salient remains broadly committed to open systems. Addressing ‘Soft’ Features for Integrators AMAG is in the process of enhancing its product line with the next generation of access control panels. However, “product” is just part of the new developments at AMAG. In addition to “hard” features (such as products), the company is looking to improve its “soft” features, too; that is, how they work with the integrator channel. Integrator channel Rebuilding a process to make your organization more efficient, is relatively easy; it just takes a lot of persistence" “We have the depth of our legacy customer base we can learn from, we just need to close the feedback loop quicker,” says Kyle Gordon, AMAG’s Executive Vice President of Global Sales, Marketing, and commercial Excellence, who acknowledges the value of reinstating face-to-face meetings after COVID. “We are laser-focused on nurturing our integrator channel,” he says. “Developing new features takes time, but rebuilding a process to make your organization more efficient, that’s relatively easy; it just takes a lot of persistence,” says Gordon. More cohesive internal communication is another useful tool, he says. Disrupting the cloud based on price Wasabi is working to make cloud applications less expensive by offering a “disruptive” price on cloud storage, $6.99 per terabyte per month (80% less than hyperscalers). Contending “hyperscalers” like AWS are charging too much for cloud storage, Wasabi is using its own intellectual property and server equipment co-located in data centers around the world. Wasabi sells “hot cloud storage,” which refers to the fact that they only have one tier of storage and data is always accessible. In contrast, a company such as AWS might charge an “egress fee” for access to data stored in a “colder” tier. Cloud storage “We saw that several video surveillance companies had not yet adopted cloud storage, and we saw an opportunity to make it easy to use,” said Drew Schlussel, Wasabi’s Senior Director of Product Marketing. “We just install a little bit of software that allows them to store data in the cloud and bring it back from the cloud.” Performance, protection (cybersecurity), and price Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies such as Genetec and Milestone. Emphasizing performance, protection (cybersecurity), and price, their data centers are certified to SOC 2 and ISO 27001 standards. Faster throughput for weapons detection Xtract One is a young company focusing on weapons detection in a time of accelerated concern about gun issues post-COVID. Founded in Canada and based on technology developed at McMaster University, Xtract One has found a niche in providing weapons detection at stadiums and arenas. These customers already have budgets, and it is easy to shift the money to a newer, faster technology. Madison Square Garden in New York City is among its customers. Cost savings solution Xtract One can increase throughput to 30 to 50 people per entrance per minute (compared to 5 to 6 people per minute when using metal detectors). The solution doesn’t require anyone to empty their pockets and the system alarms on items beyond guns and knives. Using Xtract One allows customers to reduce the number of screening lanes and security staff, providing additional cost savings, all while getting fans through the screening process in half the time. Purpose-built sensors The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties In addition to stadiums and arenas, Xtract One, formerly Patriot One, is also getting “inbound” interest from schools, hospitals, manufacturers, and other verticals that makeup 50% of their business. “We’re on a rocket ride, mainly because the weapons issues are not going away,” says Peter Evans, CEO and Director at Xtract One. The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties, all correlated by an AI engine. Providing early warning of violence ZeroEyes is another company focused on weapons detection. Their AI gun detection system works with video images to identify if someone is “brandishing” (carrying) a weapon. In other words, the system does not detect concealed weapons. Identifying someone carrying a weapon provides early warning of a possible violent act. Increased response with AI-enables images Images are identified by AI and sent to a monitoring center where a human confirms the image before contacting first responders. Knowing the location of a shooter enables staff to lock entry points, move people to safety, and direct first responders. The company was founded to leverage existing camera views to stop mass shootings and gun violence by reducing response times.
New buzzwords were abundant in the articles that generated the most clicks on our website in 2022. From the metaverse to the Internet of Things, from frictionless access control to artificial intelligence (AI), the topics most popular among our site’s visitors were at the cutting edge of change and innovation in the physical security marketplace. Here is a review of the Top 10 Articles of 2022, based on reader clicks, including links to the original content: Metaverse will promote collaboration and enable more efficiencies for security Metaverse is a familiar buzzword currently, but few people grasp what it means. In the simplest terms, the metaverse is an online “place” where physical, virtual, and augmented realities are shared. The term, Metaverse, suggests a more immersive online environment that combines elements of augmented reality (AR) and virtual reality (VR). For the physical security industry, the looming creation of a complex online environment offers possibilities and challenges. Establishing identity will be a central principle of the metaverse, and various biometrics are at the core of ensuring the identity of someone interacting in the virtual world. Cybersecurity elements are also key. On the benefits side, the security market is already taking advantage of technologies related to the eventual evolution of the metaverse. For example, the industry has deployed AR to provide information about a door lock’s status on a screen, headset, or smart glasses as a patrolling guard walks by. What are the security challenges of the transportation industry? Because transit agencies rely on several IoT devices, they get exposed to higher cybersecurity risks Rapid technological advancement, increasing urbanization, and the growing expectations of commuters and governments are pressuring transit industry players to modernize. Commuters, urban planners, first responders, and other stakeholders want to use transit data to support their decision-making. Transit agencies’ security and operations teams need closer collaboration to stay ahead. However, for many years, most transit agencies have relied on siloed, proprietary systems. Because transit agencies rely on an ever-growing number of Internet of Things (IoT) devices, they also get exposed to higher cybersecurity risks as there are more network access points to manage. The future is here: ADT’s innovation lab evaluating robots and indoor drones New robots and indoor drones for security applications are on the horizon, based on the work of ADT Commercials’ Innovation Lab, which is evaluating the latest technologies’ value to customers and some typical use cases. The ideal use of humanoid robots is to perform jobs that are considered repetitive, dirty, dangerous, and/or mundane. In security, that describes most security guard positions. As the name implies, autonomous indoor drones are focused on flying indoors versus the outdoor environment, which is heavily regulated by the U.S. Federal Aviation Administration (FAA). Flying autonomously indoors not only eliminates FAA oversight but also will enable ADT Commercial to offer another choice to customers to further reduce their dependencies on and costs of human guards. Innovative security: the key to business efficiency, cost savings, and more Organizations have shifted business focus countless times since the onset of the pandemic. While many leaders have been primarily concerned with the immediate health and safety of their customers and employees, 2022 has given rise to a new trend. More than ever, business leaders are seeking security solutions that increase operational efficiency and cost savings as well as improve logistics and business insight. As working environments become more complex, organizations looking to drive higher productivity and profitability margins should consider security upgrades that prioritize integrated analytics and automation. Shoplifting today is more sophisticated, and so are the tools to fight it One tool to fight shoplifting is analytics, which can be used to determine where shrink is occurring Shoplifting is often viewed as petty theft by individuals, but that is not always the case. Overall, shoplifting is becoming more sophisticated and coordinated. Traditional “shoplifting” has two major differences when compared to organized retail crime (ORC). The differences are numbers and motivation. ORC consists of groups working together to monetize theft, very different than an individual taking an item they need. One tool to fight to shoplift is analytics, which can be used to determine where shrink is occurring. Understanding where crimes take place helps retailers make strategic decisions about where to place their loss prevention efforts. Oosto offers 10 reasons to switch to frictionless access control in commercial buildings Access control for buildings is nothing new. It’s only in recent years that the urgency to implement smarter, more efficient, and more convenient forms of access control has increased, in the context of public and private sector digital transformation. Upheavals from the COVID-19 pandemic have forced organizations to re-think, pivot, and invest in new technology solutions that will incorporate Artificial Intelligence (AI) and Machine Learning, to gain speed in their operations, glean actionable insights from their video analytics, and enhance productivity with their teams. Which security trend is here to stay? Technologies and trends in the security marketplace come and go with some regularity. But how can you tell which trends are gaining traction and which amount to “the flavor of the month.” For example, while many physical security departments were hesitant to consider cloud-connected solutions in the past, they now better understand the benefits these solutions bring and how they can help them utilize their resources to achieve business goals while minimizing overall operational complexity. Other technologies mentioned in the article include mobile credentials, AI-based analytics, video management systems, cybersecurity, and a new emphasis on data. What do these technology trends have in common? They are opening new possibilities for greater system efficiency and functionality. In short, they are playing a role in transforming our industry. GSX 2022 reflects changing technologies and evolving role of security The role of the security director increasingly will encompass facets of cybersecurity and physical security GSX 2022 in Atlanta highlighted the changing role of security in the enterprise. The role of the security director increasingly will encompass facets of cybersecurity as well as physical security. Transitioning to an operation that incorporates both disciplines requires a workforce that embraces education and building new skills. Education and the opportunity to build new skills are evident everywhere at GSX, including in the hundreds of education sessions and also in the knowledge shared on the show floor in the exhibit hall. Consolidation changing the face of the security market Consolidation is a dominant trend in the security marketplace. Large companies typically swallow up smaller companies as a means of expanding both their technology portfolios and their geographic reach. Sometimes a big fish is swallowed up by an even bigger fish. Despite the pandemic and resulting economic challenges, the security market has continued to be a desirable environment for both big players and startups, which then provide abundant acquisition targets for larger companies. This article highlighted recent mergers and acquisition news. Six trends at the intersection of video and AI Video has evolved beyond the capabilities of advanced imaging and performance to include another level: Artificial Intelligence. Video imaging technology combines with AI, delivers a wealth of new data, not just for traditional physical security applications, but for a much deeper analysis of past, present, and even future events across the enterprise. This is more than a big development for the physical security industry; it is a monumental paradigm shift that is changing how security system models are envisioned, designed, and deployed. Much of the heightened demand for advanced video analytics is being driven by six prevalent industry trends.
Shoplifting is often viewed as petty theft by individuals, but that is not always the case. Overall, shoplifting is becoming more sophisticated and coordinated. Sometimes, retail crimes are strategic and expertly choreographed. Every step is carefully thought out — from the brand to the location to the items that are taken. Shoplifting, a major safety concern Also, the violence that accompanies these events is rising. Shoppers are rightly concerned about their safety while shopping, and the brand reputations of retailers are under threat. Traditional ‘shoplifting’ has two major differences, when compared to organized retail crime (ORC). The differences are numbers and motivation. ORC consists of groups working together to monetize theft, very different than an individual taking an item they need. Rise in organized retail crimes (ORC) ORC groups take in-demand items that they can resell for a profit, either online or at a physical location ORC groups take in-demand items that they can resell for a profit, either online or at a physical location. Also, ORC attacks are not random - they come with a high level of strategic thinking. “Armed with the right tools, retailers can identify ORC patterns that allow them to potentially anticipate and take steps to mitigate future events,” said Craig Szklany, the Vice President and Product General Manager - Loss Prevention & Liability at Sensormatic Solutions. Although ORC was rising before 2020, the COVID-19 pandemic and its impact on people’s lives and livelihoods accelerated the trend. Economy impacts shoplifting The economy also impacts shoplifting. “When consumers have less money to spend, they are more likely to steal necessities,” said Craig Szklany, adding “Keeping food on the table or finding an alternate source of income to pay the mortgage can be powerful motivators, and some individuals turn to retail crime to keep up.” One tool to fight shoplifting is analytics, which can be used to determine where shrink is occurring. Craig Szklany continues, “Understanding where crimes take place helps retailers make strategic decisions about where to place their loss prevention efforts.” Loss prevention systems with artificial intelligence (AI) Some of these systems are equipped with artificial intelligence (AI) that can identify ‘red’ and ‘green’ shoppers (thieves versus well-intentioned customers), as they move throughout the store, so retailers can respond proactively to potential threats. With enough data on these patterns, systems can alert retailers of at-risk locations" “Widespread use of these technologies can also help track ORC groups, as they move around regions or countries,” said Craig Szklany, adding “With enough data on these patterns, systems can alert retailers of at-risk locations.” He continues, “The increased use of scan-and-go and other forms of self-service checkout has made it easier for consumers to steal. Implementation of these systems has been one of the biggest factors in increased shrink for retailers.” Store visibility technology “The purpose of scan-and-go is to provide a seamless shopping experience for consumers, with smoother checkout and to help retailers reduce the need for employees,” stated Craig Szklany, adding “However, with increased theft, retailers need some form of monitoring at these sections.” He continues, “With store visibility technology and AI, retailers can both monitor self-checkout for theft, while also gathering insights that enable them to better identify and predict theft at these checkouts.” Intelligence-led loss prevention technology Craig Szklany adds, “Intelligence-led loss prevention technology provides a huge return on investment (ROI). Traditionally, items that left the store were as good as gone. With RFID and smart-exit technology, that is no longer the case.” These systems allow retailers to quantify theft events and include data on what was stolen and how much it cost. With that information, retailers can take a proactive approach to theft prevention, by providing enhanced evidence packages to law enforcement, which increases the chances of the items being returned to stores. Challenge of shift to the Internet of Things (IoT) The biggest change in retail technology in the last five years is the shift to the Internet of Things (IoT) The biggest change in retail technology in the last five years is the shift to the Internet of Things (IoT) and Store Visibility technology. Stores outfitted with integrated tags, pedestals, and AI-enabled video cameras can be connected holistically, so that retailers have a clearer insight into the thieves’ journeys in real-time. That data helps prevent future theft. These technologies provide a more accurate look into what exactly went missing, when, and where, which allows retailers to respond to shoplifting, in a way that they had not been possible in the past. Modern loss prevention technologies offer flexibility “The great thing about modern loss prevention technologies is that they’re flexible,” stated Craig Szklany, adding “The same system that tracks ORC events can provide insight into energy use, floor optimization, customer experience, and more.” RFID tags allow retailers to track inventory at the item level, so they are better prepared to make decisions about stocking and promotions. Computer-vision-based AI (artificial intelligence) that identifies ‘red’ and ‘green’ shoppers can also track customer sentiments and demographics, to enable retailers to offer special discounts and enhanced customer service, in order to improve customer experiences and establish loyalty. Benefits of video loss prevention technologies Ahead of busy shopping seasons, many retailers hire extra employees to serve as physical deterrents against theft, but labor shortages may take this practice out of reach this year. Video loss prevention technologies can reinforce retailers’ workforce, allowing them to be proactive against theft without drawing associates from their main goal: helping customers.
Case studies
DFNBG Gastro GmbH & Co. KG, operator of 48 Dunkin' branches and other catering establishments in Germany, has migrated to the MOBOTIX CLOUD for the central management of its video surveillance. DFNBG partnered with MOBOTIX Diamond Partner VALEO IT Neteye GmbH for more than ten years, who have implemented and continuously optimized secure and efficient MOBOTIX video solutions in the 48 Dunkin' branches. Data protection regulations The operation of local storage systems was proving particularly difficult in shopping centers Due to the strong growth of DFNBG, the demands on the existing video management system increased. The local storage of video data became increasingly complex - both in terms of data protection regulations and the management of access rights. The operation of local storage systems was proving particularly difficult in shopping centers. The solution: a gradual migration from local NAS storage to the data protection-compliant MOBOTIX CLOUD. Access management and GDPR: the MOBOTIX CLOUD as a solution The MOBOTIX CLOUD video surveillance-as-a-service (VSaaS) offering allows users to conveniently control their cameras via a free app. The recorded videos are stored in highly available and cyber-secure data centers located close to the user. This ensures data protection-compliant storage in accordance with the GDPR. Intelligent camera technology A key advantage of the MOBOTIX CLOUD is the combination of intelligent camera technology A key advantage of the MOBOTIX CLOUD is the combination of intelligent camera technology and a powerful cloud platform. The cameras analyze events on site and only transfer relevant data to the cloud. This minimizes bandwidth requirements while maintaining the highest security standards. MOBOTIX Bridge Communication between the cameras and the cloud takes place via the MOBOTIX Bridge, a highly secure connection unit that ensures protected data transmission. The cloud solution also eliminates the need to operate separate server rooms with high security standards on site - a clear advantage for branches in shopping centers or high-traffic locations. DFNBG can control access rights Around half of the Dunkin' branches have already been converted to the MOBOTIX CLOUD Cloud data is managed directly by the users themselves. This means that companies such as DFNBG can control their access rights centrally without having to create individual solutions for each branch. “It was clear to us that the system is secure - including cyber-secure - and exceeds our requirements. But the central management of all access rights really saves us time and money,” says Harry Taubert, Construction & Development Manager at DFNBG. Around half of the Dunkin' branches have already been converted to the MOBOTIX CLOUD, and the remaining locations will follow successively. VALEO IT Neteye: MOBOTIX Partner for innovative video solutions As a long-standing MOBOTIX Diamond Partner and one of the largest integrators of MOBOTIX systems in Germany, VALEO IT Neteye has been instrumental in delivering customized, future-ready surveillance solutions to DFNBG. VALEO IT Neteye also offers full-service training to DFNBG to ensure everyone stays up to date with industry changes. “We only offer our customers MOBOTIX solutions because we are absolutely convinced of the quality and durability of the products manufactured in Germany,” explains Norbert von Breidbach-Bürresheim, Managing Director of VALEO IT Neteye.
Founded in Taiwan, 85°C Bakery Cafe has rapidly expanded into an internationally recognized brand, known for its diverse baked goods and beverages. With over 80 locations across the United States, the company faced the complex challenge of managing security and operations at scale—especially with a lean IT team of just seven people. To keep operations running smoothly, they partnered with VIVOTEK, a global pioneer in security solutions, to deploy the AI-powered VORTEX Cloud Surveillance Platform, which enhances visibility, reliability, and operational efficiency across their retail operations. “Retail is not just about selling things. It’s about building trust and creating relationships.” — Ariel, IT Director, 85°C Bakery Cafe Challenge Legacy Surveillance Systems Can’t Keep Up with Expansion Growth Outpaces Surveillance: As 85°C expanded rapidly across the U.S., their existing surveillance systems struggled to keep pace, resulting in operational challenges. In retail, fast incident resolution is crucial to customer satisfaction. At 85°C Bakery Cafe, their legacy surveillance system became a bottleneck, leading to increased costs, time delays, and operational risks. Unstable Legacy Systems: NVR failures occurred monthly, taking upward of 25 days to repair, with a cost impact of around $2,000 annually for replacements. Fragmented Management: Lack of centralized access made it difficult to monitor, retrieve, or share video footage. Limited Support: With only a seven-member IT team, managing all systems across multiple stores and scaling was challenging. Solution Built for Retail Efficiency: Faster Setup & Deployment and Centralized Cloud Control To overcome these challenges, 85°C Bakery Cafe implemented VORTEX by VIVOTEK, an AI-powered cloud surveillance solution designed for retail efficiency. For a small IT team managing dozens of busy stores, simplifying setup, streamlining operations, and supporting growth without overhauling infrastructure were critical. Hybrid Compatibility: VORTEX unifies over 200 legacy cameras and 150 cloud cameras onto one platform without extra replacement costs. Centralized management: It enables remote access control, receives instant alerts, searches the video footage in seconds with AI technology, and simplifies incident handling. Rapid Deployment: Plug-and-play setup cuts deployment time by 50%, keeping store launches efficient and streamlined. “Setting up in each location used to take us two to three days… With VORTEX plug-and-play, we’re done in just one day.” — Jason Chow, Tech Support Manager, 85°C Bakery Cafe. Results Smoother Operations and Better Customer Experience For 85°C Bakery Cafe, VORTEX made physical security operations more proactive by improving response times, reducing disruptions, and giving staff the tools to stay focused on customers, not equipment. The plug-and-play setup cut installation time by up to 50%, while cloud-based management reduced site visits and operational costs. These improvements not only lightened the technical workload and streamlined daily operations but also strengthened customer trust with faster service and reliable incident resolution. "With Deep Search, we can find people or items in seconds. If a customer loses something, we trace it and recover it quickly."— Nolan Carter, Facilities Manager, 85°C Bakery Cafe. "VORTEX helps us prevent disputes and track items that go missing. It keeps the entire store running smoothly. When stores run better, customers stay longer and they come back more often."— Ariel, IT Director, 85°C Bakery Cafe.
Established in 1997, Dubai-based BMA International operates fashion retail in the Middle East and Asia across the Kingdom of Saudi Arabia (KSA), United Arab Emirates (UAE), Bahrain, Oman, Kuwait and Qatar with more than 250 stores offering two major brands — Redtag and twenty4. BMA’s steady growth is a testament to its focus on building trust with its shoppers, employees, suppliers and stakeholders to create a company that is people-centric, ambitious and results-oriented. Challenge Fraud is a common problem in the retail sector, particularly within large chains with hundreds of locations and tens of thousands of employees. BMA’s retail stores were no exception. Following an internal audit, security of point-of-sale (POS) terminals in retail outlets were identified as a serious concern, particularly the misuse of floor supervisors’ credentials to access terminals and modify or cancel transactions. The problem persisted even after BMA switched from passwords to a smart card-based authentication system The problem persisted even after BMA switched from passwords to a smart card-based authentication system. The most common issues involved supervisors leaving smart cards with cashiers to use in their absence and failing to return the cards when separation from an employer occurs — a frequent occurrence as many of BMA’s retail employees are expatriates who often return to their home countries. Fraudulent use of the smart card was also a common problem. Once a sale was completed and the customer had left the store with their purchased items, the smart card could be used to improperly access the system so the cashier could void the transaction and pocket the “refund,” resulting in both monetary and inventory losses. Biometric-based system “BMA’s internal auditors were concerned with the lack of control over the cards and the potential for fraudulent transactions due to their mishandling. They observed clear gaps in security and authentication practices that led directly to fraud and revenue leakage, resulting in the Internal Audit Committee recommending to the BMA Board of Directors that action be taken to plug the security holes by tightening the authentication process,” said Nainan M. Kurian, CEO of Technowave International LLC. The decision was made to transition authentication to a biometric-based system that would provide the required security at a competitive price that aligned with the esthetics of the retail stores. The system also needed to be compatible with the Oracle Retail Xstore Office Cloud Service, which BMA International was adopting across its brands. Solution A fingerprint reader from HID is ideal for use by multiple people in a shared environment BMA International and its technology partner, Technowave International LLC, determined that the HID DigitalPersona® 4500 Fingerprint Reader met all their requirements — a decision supported by recommendations from other retailers that had deployed the product, and by the fact that competitive solutions were incompatible with Oracle Retail Xstore, a crucial requirement. A USB peripheral with a compact design to conserve space, this fingerprint reader from HID is ideal for use by multiple people in a shared environment. Its professional, modern design looks elegant in retail settings while offering superior authentication control via biometric functionality that uses optical scanning technology to achieve excellent image quality and reliability. HID DigitalPersona 4500 Fingerprint Reader With this easy-to-use technology, floor supervisors simply place their finger on the reader window, which rapidly captures and encrypts the fingerprint image, and then provides a red flash as a visual cue indicating that it was properly captured. That image is sent to the DigitalPersona FingerJetTM biometric engine for verification, and once the user has been authenticated, access to the POS terminal is granted. “Deploying the HID DigitalPersona 4500 Fingerprint Reader was simple and caused no disruption to retail operations. It paved the way for significant reduction in the malpractice that had been occurring with the smart card system,” said Kurian. Result Since deploying more than 1,100 HID fingerprint readers in retail outlets across KSA, UAE, Oman, Bahrain, Kuwait and Qatar, BMA has eliminated nearly all POS fraud and abuse. The system has also driven tangible improvements in the attendance and punctuality of floor supervisors, who must now be physically present in the store for authentication to take place. The HID authentication system is also capable of multiple types of authentications — providing flexibility that is appreciated by users who work at multiple locations. “Because the HID DigitalPersona 4500 Fingerprint Reader requires proof of presence for authentication, there is greater accountability among supervisors which resulted in immediate cessation of POS fraud and stopped both revenue and inventory leakage. The exceptional support provided by HID Global has also allowed BMA to take full advantage of the system’s functionality and flexibility,” said Kurian.
Take a walk to the local high street. Compared to a few years ago, they may notice many more “To Let” signs in empty shop windows. It comes as no surprise given the number of shocks to the economic system over the last five years, ranging from COVID-19 to international conflicts, all of which have led to various consequences, such as energy price hikes, interest rate increases, and a general shift in many people's work patterns and consumer behavior. Vacant retail space The total number of void private sector commercial properties stands at approximately 165,000 According to Savills Research, the overall footfall of vacant retail space in the UK is around 14.5%, while the total number of void private sector commercial properties stands at approximately 165,000. Additionally, an estimate of 7,000 commercial and business properties owned by Local Governments in Great Britain have been unoccupied for over 12 months. Net Zero ambitions Furthermore, a recent BBC article points out that business tenants are more inclined to search for smaller, newer and more energy-efficient office spaces to rent, are willing to downsize owing to hybrid working, and seek buildings that complement their Net Zero ambitions. This might be interpreted as an indication that a number of long-standing commercial premises would become vacant in the near future, forcing owners to update and repurpose empty spaces to meet the demands of a changing market. A costly asset that requires extra protection Insurance companies charge higher premiums for void property and require regular security While the property market and customer demands are shifting, some truths remain unchanged: commercial property should generate money, not drain it. However, void sites imply outgoing costs and no profit, so it only makes sense that any vacant space should be flipped as soon as possible. Unoccupied premises can become an alluring target for squatters, vandals, thieves, and trespassers, which is one of the main reasons why insurance companies charge higher premiums for void property and require regular security and fire safety checks too. Enhanced security measures Such properties must be protected by enhanced security measures. This often involves the installation of steel doors and screens, perimeter protection, vigilant surveillance, and prompt alarm response. After all, any break-in can cause far greater financial damage than the costs of protection; and the owner is legally liable for any injuries sustained by trespassers. Meanwhile, legit access is very much required by contractors to upgrade and renovate the site in preparation for the next business occupier. Any delays or missed visits result in further charges on an asset that is essentially nothing but another bill while vacant. Access issues: Fetch the keys For every contractor visit, property check or viewing, a key must be obtained offsite and then returned A minor but, consequently, very important issue might arise when accessing a site that is unmanned 24/7. For every contractor visit, property inspection or viewing, a key must be obtained offsite and then returned. This takes time, implies unnecessary travel and, potentially, may result in additional missed visit fees and rebooking arrangements in instances when a contractor is unable to gain entry. As a result, it may slow down the void property turnaround time. Keyholding arrangements Furthermore, complex keyholding arrangements can also slow down the security alarm response time. More and more security companies are moving away from the traditional keyholding model, in which keys are stored at the central location or in heavy key lockers in vans during patrols. While reaction time is critical, time is frequently wasted collecting keys or waiting for a keyholding patrol (rather than the nearest one) to arrive on site. Lock up and leave the keys. Securely. Keyholding solution must be more robust than doors or other means of entry to stop opportunistic intruders What about storing keys at the point of entry? This may be controversial, but it is a solution that has gained popularity in void property management with the implementation of secure range key safes and lock boxes. The primary concern in such an approach is security. Even though the property is void, the keyholding solution must be more robust than doors or other means of entry to prevent opportunistic intruders from taking advantage of the new keyholding arrangement. Smart key management solutions Stuart Wheeler, Managing Director of Keynetics, a company that offers smart key management solutions with security-certified key safes, comments, “Over the years, we have developed strong relationships with the top void property management companies in the UK and Europe. These clients require a keyholding solution that enables efficient FM service provision for vacant properties while also providing a high level of security.” “Storing keys at the point of need enables quicker alarm response times and allows approved contractors to enter the premises without any delays, but security must not be compromised; in that respect, our SentriGuard key safes are suitable for commercial properties and certified to LPS 1175 (Loss Prevention Standard) C1 and C3 security ratings, which is unrivaled by any other supplier.” SentriGuard key management system Stuart confirmed that in addition to security, the SentriGuard key management system is highly praised for its innovative technology. First, it incorporates a bespoke cloud-based platform that allows customers to manage access to multiple properties remotely and generate various audit reports that can also serve as proof of service delivery. Second, assigned individuals may gain access to premises either using the mobile app or a time-restricted code. He added, “The ability for clients to access real-time data of site visits with a solution that does not break the bank and is secure has been the key to the success here in the U.K. and now across mainland Europe.”
Amthal has worked with Hertfordshire Garden Centre to install additional IP CCTV across its retail site and upgrade existing systems, including its intruder alarm solution, for the safety and security of staff and visitors. Based in Redbourn on the outskirts of St Albans, Hertfordshire Garden Centre is a small, independent retail premises, serving as a cherished hub for home and gardening enthusiasts. IP CCTV, intruder alarm system Amthal has worked closely with the team to ensure a secure operation, most recently adding IP CCTV and an updated intruder alarm system. Enabling staff to work in a safe environment and visitors to explore, learn, and purchase with complete peace of mind. Graham Armstrong, Owner of Hertfordshire Garden Centre, said “Faced with the cost of living crisis and a corresponding surge in shoplifting, security of our site is a top priority. But it’s not solely the Police’s job to look after us, we have to take proactive responsibility for our staff and our visitors, without compromising our friendly and welcoming environment." Real-time management and security Amthal has recently added over 20 IP cameras and upgraded the existing visual verification systems Graham Armstrong adds, “We have worked in partnership with Amthal, a local company that fully understands the brief. The team has consistently delivered great service and has shown to be knowledgeable and helpful at all times. Installations and upgrade work programs have occurred with minimal disruption to the daily operations of our retail site. It all comes together for our staff and visitors to know they are in a secure garden center world.” Amthal has recently added over 20 IP cameras and upgraded the existing visual verification systems, allowing management and security to review activity throughout the premises in real time and empowering personnel to respond promptly to any potential incidents. A monitored intruder alarm solution The addition of a new monitored intruder alarm solution is geared to quickly detect any breach and provide advanced security against unauthorized access attempts. Jacki Adams, Installation Supervisor at Amthal Fire & Security, said “In the current climate, retail crime has hit record levels, increasing by more than a third over the past year alone. What Hertfordshire Garden Centre demonstrates is by taking a proactive approach to enhancing the security infrastructure on-site, they are doing all they can to protect teams and visitors." Comprehensive surveillance and monitoring Jacki Adams adds, “What it also shows is the importance of reviewing security regularly with the help of a trusted partner such as Amthal. We can identify the opportunities for extended CCTV coverage and upgrade systems in place to ensure comprehensive surveillance and monitoring capability. Here, the move reflects a commitment to creating a safe and secure haven for all home and gardening enthusiasts.”
The Body Shop has installed bespoke Traka RFID locker solutions at its main distribution center to ensure intelligent management and accountability of assets, enhance security, and streamline operations. As a global pioneer in ethical and sustainable beauty products, The Body Shop recognizes the importance of responsible resource management, business practices, and asset security. Traka intelligent locker systems At its main distribution center in Littlehampton, three large-scale Traka intelligent locker systems have been installed to manage different devices. The first uses Traka’s multi-bay cradle locker solution to manage 30 VoCollect voice-picking devices and Bluetooth headsets, all charged and ready to operate. Three large-scale Traka intelligent locker systems have been installed to manage different devices The second houses 40 Falcon handheld scanners, managed by Traka’s specialist Asset Master Locker range with charging and battery points located. The final system presents secure storage for a kit of equipment, specifically designed for the forklift truck drivers, with each locker compartment containing a Falcon scanner, Radio and Printer. Each intelligent locker solution is offered with RFID asset detection and specialist TrakaWEB software, to provide managers with instant audit control capability to establish exact times when physical devices are removed and returned to lockers. New standards in design Says The Shift Manager, responsible for the project: “To keep up with high demands, our distribution center operates 24/7. It is constantly evolving, driving new standards in design and use of technology to ensure our products reach our stores to meet our loyal customer demands." “To operate at maximum capacity, we need to make it as simple and as quick as possible for authorized colleagues to not only gain access to the devices they need but also ensure they are operational and in good working order. With the introduction of Traka, we have eliminated manual control, plus we have a complete audit on all devices that we can access from anywhere. We have already noted increased accountability, traceability and fault logging, all coming together to reduce lost time and enhance operational efficiency.” Net 2 access control cards Access to other assets and tools can only be granted to authorized personnel for their job specification The three locker solutions have been installed in two separate locations around the distribution center, to ensure staff can easily access equipment in their work area. Eliminating the need to travel to a central location and queue to access or organize equipment has led to improved productivity at the start and end of shift periods. Traka has also ensured all systems operate using existing Paxton Net 2 access control cards to minimize facility disruption during or after installation. Access to different assets and equipment can only be granted to authorized personnel for their identified job specification, with staff only able to take one device or kit at a time. Author's quote Lee Payne, Traka Business Development Manager added: “The introduction of Traka systems to a global distribution center such as The Body Shop demonstrates how simple process enhancements can make a significant difference. From the initial brief through to implementation, we worked closely with the team to identify the exact requirements for each site and the accessibility needs for staff." “We understood the need for curfew notifications, fault logging and careful authorized access control. We planned with the team to separate out the systems into specific work areas and use the Traka orange to help the locker systems stand out, all to ensure vital time could be saved for staff and management. The result is a smoother, more efficient operation throughout the supply chain, helping The Body Shop continue its mission of delivering its best-loved ethical beauty products."


Round table discussion
As physical security technologies become more complex, it is incumbent on the dealer/integrator to have the skills and expertise needed to ensure that a system operates smoothly. The value of integrators increasingly rests on the skill sets they bring to bear when installing a system. If the skills are missing, there is a problem. We asked this week’s Expert Panel Roundtable: What missing skills among security integrators can cause problems for customers?
The role of the integrator/installer in the physical security marketplace is shifting as technologies evolve and applications expand. Integrators are being faced with a need to augment their expertise both in a wider range of systems and deeper into the specifics of each increasingly complex technology. At the end of the day, it falls to the integrator/installer to ensure a system performs as promised, however much a consultant or even a manufacturer might be involved in the process. We asked this week’s Expert Panel Roundtable: How is the role of the security installer/integrator changing?
The holiday season is marked by festive spirit and family celebrations, but it is also the busiest time of year for retailers. Busy shoppers willing to spend money are an upside to the holiday shopping season, and many businesses depend on the holiday rush as a critical element to having a successful year. A downside of a busy holiday season is an increase in retail security threats including shoplifting. We asked this week’s Expert Panel Roundtable: How can technology address loss prevention challenges during the holiday shopping season?
Products


White papers

Total Cost of Ownership for Video Surveillance
Download
Understanding All-In-One Solutions
Download
How Video Technology Is Transforming Loss Prevention, Operations, And Customer Experience In The Retail Sector
Download
How Intelligent Video Is Transforming Banking And Financial Institutions
Download
Why SAAS Security Platform Is More Popular In American SMEs
Download
A Guide To Moving Physical Security Into The Cloud
Download
Intelligent Video Security Solutions
Download
Security Investments Retailers Should Consider For Their 2021 Budget
Download
How End-to-End Video Security Solutions Can Help Your Organization With Social Distancing
Download
Smart Security Cameras: Excellence in Retail
Download
Nine Ways To Make Your Retail Security System Work Harder
Download
How To Catch Shoplifters With Thermal Imaging
Download
Loss Prevention and Beyond: How Video Innovation Enriches Retailers
Download