We've seen the rapid development and expansion of the cloud and Internet of Things (IoT) impact almost every aspect of the security industry; from surveillance technology to video management systems to data storage, the opportunities presented by increasing interconnectivity and communication between devices have revolutionised the way users handle security operations. And the access control market is no exception: according to research by Security Sales & Integration, 71 percent of companies were deploying a networked access control system in 2017.
The once-trusted, traditional mechanical lock-and-key access control systems may still function adequately in some instances, but these technologies can be less secure than newer door solutions. Complications can easily arise, such as in the case of a lost key or if access to a facility needs to be restricted. Security, building management and privacy concerns are likely to develop, as a company may not know who's entering and exiting the building at all times.
Remote And Instant Accessibility
Networked access control technology enables users to achieve two critically important components of a security system: remote and instant accessibility
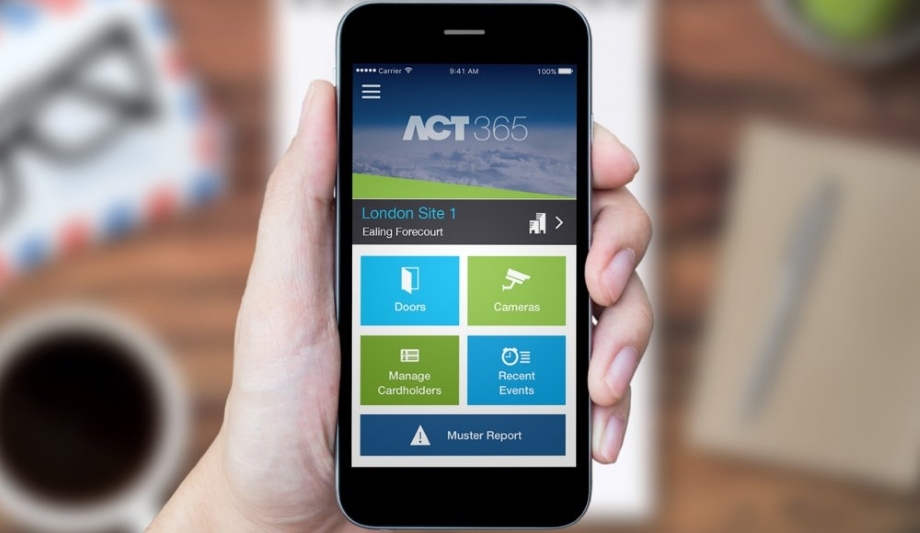
Today’s access control users expect more of an integrated system than a one-size-fits-all solution that is cumbersome to operate and expensive to scale. The shift to networked access control systems takes the hardwiring and complicated installations out of the equation, while also enhancing security and flexibility. A single interface that integrates multiple points of entry and can be accessed through a connected smart device anywhere at any time provides the ultimate simplicity and convenience.
Networked access control technology enables users to achieve two critically important components of a security system: remote and instant accessibility. Deciding whether access to a building should be granted or denied must be an immediate process, and this can quickly be accomplished through a central, networked hub rather than at the door. In the event of a security incident, real-time reporting capabilities facilitate streamlined response and all access can be restricted quickly.
Viewing Real-Time Muster Reports
Users can view real-time muster reports to aid in tracking all employees or students in the event of an emergency
Other useful functions of networked access control systems include the ability for technical queries to be diagnosed and resolved on the go, enabling site issues to be dealt with efficiently, thereby minimizing disruption. Users can also view real-time muster reports to aid in tracking all employees or students in the event of an emergency.
Networked access control solutions, such as ACT365, take advantage of the increasingly valuable cloud and IoT to supply end users with the freedom they desire through a secure, easy-to-use interface. Features such as remote monitoring, real-time muster reporting and central management contribute to the expanding growth of networked access control and allow users to save time and money while achieving peace of mind.
Discover how AI, biometrics, and analytics are transforming casino security