The introduction of the GDPR has deeply affected businesses using video surveillance. Striking a balance between the safety and security needs and safeguarding third-party privacy when processing personal data can be a challenge. But with planning, the right documentation, the right tools, and the right partner, it can be done.
The European Union General Data Protection Regulation, GDPR, was introduced in May last year to protect the privacy of individual citizens; how personal data is collected, processed, and shared. As the regulation isn’t just about written details, like names and addresses; it also applies to any information that can identify someone, which therefore includes video surveillance data such as pictures and videos.
Guidelines that help compliancy
As a business owner, there are some things that one needs to get straight when handling personal data. Trying to bring some clarity and helping companies do the right thing, the European Data Protection Board (EDPB) has published useful guidelines. These cover all GDPR compliance aspects, from planning and installing to running the video surveillance. For example, it includes what one may record, how long one can save it, and how and when one can export it.
A professional supplier should also be able to help, both with the information that one needs as well as the right hardware and software to protect third-party privacy.
Starting on the right foot
Let’s say that, as a store owner, one is in the process of installing video surveillance. It might be to protect the premises against vandalism or to keep track of what happens in the store to reduce thefts, or to improve staff and customer security. Generally, this will make one the data controller. Documentation and processes are critical to comply with GDPR
Documentation and processes are critical to comply with GDPR. The first step is to explain why one needs to install cameras that could potentially infringe on third-party individuals. This balance of interest is vital in the regulation, the legitimate interests versus those individuals whose personal data is being collected, held, or processed, also known as the data subjects.
Video surveillance – areas to consider
Once established the legitimate need to install video surveillance, it’s time to design the system. From an overall system perspective, there are a few areas that one needs to consider.
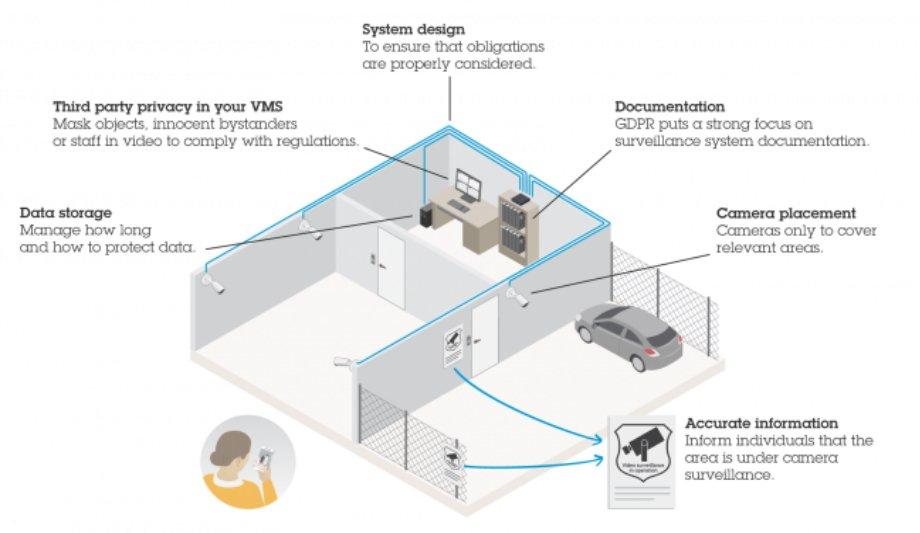
System design
When designing the video surveillance system, AXIS Site Designer helps to ensure that GDPR obligations are properly considered. Here one can define the retention time, define the camera's field of view and resolution to ensure the right images are captured.
AXIS Site Designer provides installation notes which can be used to inform the installer of GDPR considerations such as the need for privacy masks and specific installation requirements.
Data storage
Data storage covers two areas: how long one should store the data and how to protect it. In general, one is not allowed to store data for “longer than is necessary for the purposes for which the data are processed,” what the GDPR calls “storage limitation”. Depending on the purpose, three or four days is usually enough. The longer one wants to store the data, the greater legitimate interests must be.
To protect the data, one should secure physical access to the location where the video management system and data is stored. The video management system itself must be secured against unauthorized access to the stored recordings containing personal data.
Using AXIS Camera Station, one can easily set safe passwords, both for the VMS and the camera and they can even be randomized. User permissions can also be applied to limit functionality appropriate for the operator. Any leaks of personal data or security breaches must be reported to the relevant supervisory authority promptly.
Third-party privacy in VMS
Tools for the protection of privacy should be core functions of video management software. Sometimes one may need to mask objects and innocent bystanders or staff in a video to comply with regulations.
Using the inbuilt video redaction in AXIS Camera Station one can easily pixelate parts of the video before exporting. Any individuals’ requests to access any personal data can be met quickly and efficiently due to the simple export of masked video.
Documentation
The GDPR puts a strong focus on surveillance system documentation, during the planning as well as the operation. One should be able to provide information about how data is processed and who will have access to the collected data, and must keep a written record of the operation. AXIS Site Designer and the installation verifier and logs in AXIS Camera Station provide useful information to document the installation.
Camera placement
Axis PTZ cameras support for 3D masking allow masking to be maintained when the camera’s field of view changes It’s crucial that the cameras only cover relevant areas, what the GDPR calls “data minimization”. It states that personal data must be “adequate, relevant, and limited to what is necessary for the purposes for which they are processed”. For example, if one wants to protect the shopfront, the cameras shouldn't include irrelevant parts of the street.
Static privacy masks should be utilized to prevent viewing of public areas such as windows. Axis offers privacy masking in most cameras. It enables selected areas of a scene to be blocked or masked from viewing and recording. Axis PTZ cameras with support for 3D masking allow masking to be maintained even as the camera’s field of view changes through panning, tilting, and zooming as the masking moves with the camera’s coordinate system.
AXIS Live Privacy Shield offers dynamic privacy masking. It’s a camera analytic, which one can use to monitor live indoor activities without collecting any sensitive personal data. It safeguards privacy by anonymizing people in a video but allows monitoring of activities or movements.
Accurate information
One must put up clear signs to inform third-party individuals that the area is under camera surveillance. They have the right to know the details of why they are being recorded and how the data will be used.
Individuals also have the right to access any personal data that one has collected, both an overview and the actual data.
Additional considerations
In addition to the areas already covered, general IT system security should be considered as this could lead to a data breach:
- Make sure that the system is secure by implementing strong passwords and policies for all devices and software
- Choose equipment from companies that apply cybersecurity best practices
- Consider and if possible, restrict internet exposure
- Ensure that all devices are running with the latest firmware since the newest version could close vulnerabilities
- AXIS Camera Station, will prompt the user for firmware updates and simplify the management of the video surveillance devices
- Ensure that the system supports encrypted data communication between devices in the system, such as HTTPS
- AXIS Camera Station supports HTTPS between the server-client and the cameras so that the system handles data safely
Get the right partner
Offering the required third-party privacy protection and complying with the GDPR may seem overwhelming. And while an individual, as the data controller, is generally responsible for GDPR compliance, installers, distributors, and manufacturers are there to help and support.
With the right surveillance supplier or partner, users will get equipment that safeguards personal data, but also support and services that will take the weight off the shoulders. They can help get the best of both worlds – GDPR compliance as well as the safety and security that one needs.
Discover how AI, biometrics, and analytics are transforming casino security