Network Video Recorders
Alibaba has unveiled Wan2.2-S2V (Speech-to-Video), its latest open-source model designed for digital human video creation. This innovative tool converts portrait photos into film-quality avatars capable of speaking, singing, and performing. Part of Alibaba’s Wan2.2 video generation series, the new model can generate high-quality animated videos from a single image and an audio clip. Visual representations Wan2.2-S2V offers versatile character animation abilities, enabling the desi...
Hikvision, a world-renowned manufacturer and supplier of security products and solutions that deliver the ideal combination of high performance and extreme value, announced the launch of HikCentral Lite (HCL) v1.1.1 with AcuSeek — a next-generation software platform that brings real-time AI video search and unified system management to facilities of any size. Now embedded in HCL, AcuSeek transforms how teams manage video surveillance, access, and alerts — delivering fast, natural-la...
Omnilert, a pioneer in AI-powered active shooter prevention technology, today announced a significant expansion of its Secure Schools Grant Program in response to overwhelming demand from schools and universities nationwide. Originally intended to support 20 schools, the program will now provide 50 schools across the United States with three years of free access to Omnilert's AI Gun Detection, the company's AI-driven firearm detection solution. This expansion is made possible in part through a...
Artificial Intelligence Technology Solutions, Inc, a global pioneer in AI-driven security and productivity solutions for enterprise clients, released insights from Steve Reinharz, CEO/CTO and founder of AITX and Robotic Assistance Devices, Inc. (RAD), highlighting his top five predictions for how artificial intelligence will reshape the security industry in 2026 and beyond. According to Reinharz, adoption of advanced AI security solutions is rapidly shifting from early adopters to mainstream ac...
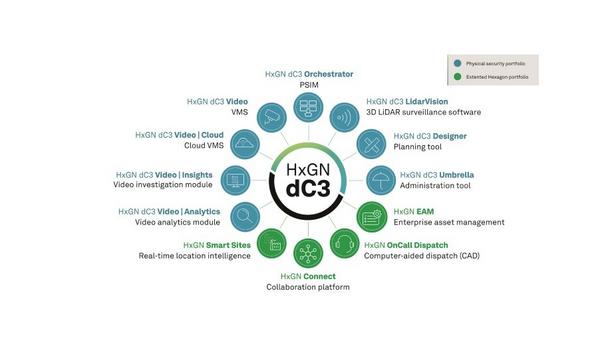
Hexagon’s Safety, Infrastructure & Geospatial division launches HxGN dC3 Video | Cloud, a new AI-enhanced, cloud-based video management system that enables more agile and resilient surveillance operations. With the increasing availability of reliable high-bandwidth connections, organizations are adopting a cloud-first strategy and turning to video surveillance as a service (VSaaS) for physical security, especially in distributed installations with many sites. The new cloud offering b...
Durite, a pioneer in vehicle safety, lighting, and auto electrical parts, will be showcasing its new AI Low Bridge Detection System at this year’s RTX show in Stoneleigh, on 24th-26th June. The Durite Low Bridge Detection System utilizes Smart AI-powered camera technology to detect and alert over-height vehicles to the presence of low bridges and also reads safety height signage. Durite’s range of vehicle safety The system is compatible with Durite’s range of vehicle safety...
News
ONVIF®, the pioneering standardization initiative for IP-based physical security products, has announced that it has entered into a strategic collaboration with the Coalition for Content Provenance and Authenticity (C2PA) to preserve the integrity and authenticity of digital video in the evolving fight against content manipulation. The two groups will work together to raise awareness and promote the adoption of open standards that help verify the authenticity of video content across digital video platforms. ONVIF video authentication Content Credentials improve clarity and set end-to-end confidence in the realism of digital assets This initiative aligns the ONVIF video authentication specification with Content Credentials, the open standard published by the C2PA, which is comprised of Microsoft, Adobe, Google, Meta, BBC, and Truepic. Content Credentials enhances transparency and establishes end-to-end confidence in the authenticity of digital assets. This collaboration comes at a time when synthetic media, deepfakes, and AI-generated content are becoming increasingly indistinguishable from authentic footage. The tools that create this fake content pose a significant risk to public trust in video used for law enforcement, corporate security, and legal proceedings as well as in a wide range of digital media products. Content Credentials for video security “We are happy to welcome ONVIF as a liaison member to the C2PA,” said Andrew Jenks, Executive Chair of the C2PA. “As the global standard for provenance, Content Credentials plays a vital role in providing transparency in digital media." "The collaboration with ONVIF and the C2PA brings Content Credentials to video security – an environment where footage must reflect reality without alteration. We’re excited about our work together and the impact of our global, open standards.” Digital key specific to the surveillance camera The video authentication specification set by ONVIF, known as media signing, ensures that video footage The video authentication specification developed by ONVIF, known as media signing, ensures that video footage is cryptographically signed at the point of capture with a digital key specific to the individual surveillance camera. The signatures are embedded in the video, enabling an authentication tool to verify whether video frames – throughout the chain of custody – have been modified or manipulated since they left the camera. This is critical for video used in court proceedings, law enforcement investigations, and corporate security incidents, where any doubts about the validity of video evidence can undermine outcomes and erode institutional trust. C2PA’s core specification The C2PA’s core specification, Content Credentials, is a technical standard that allows publishers, creators, and consumers to trace the lifecycle of media, beginning from production (such as which camera captured an image, whether it was edited, and when) to consumption (displaying this information on the website or platform where the content appears). Content Credentials embed cryptographically signed, tamper-evident metadata directly into images, video, audio, and documents or stored in a manifest that travels with the content, making any alteration detectable. This metadata acts like a digital “nutrition label,” detailing the content’s origin, history, and any modifications made. Threats from generative AI ONVIF continues to work with its members to expand the number of IP interoperability solutions “Preserving the authenticity of video has never been more important as the threats from generative AI and other means of content manipulation continue to increase exponentially, regardless of industry and use case,” said Leo Levit, Chairman, Steering Committee, ONVIF. “The work of ONVIF to preserve video integrity and the recognition by the C2PA will help build user confidence that recorded video can be verified as genuine and untampered.” IP-based physical security products ONVIF is a pioneering and well-recognized industry forum driving interoperability for IP-based physical security products, with a global member base of established camera, video management system and access control companies and nearly 34,000 profile conformant products. ONVIF offers Profile S for streaming video; Profile G for video recording and storage; Profile C for physical access control; Profile A for broader access control configuration; Profile T for advanced video streaming; Profile M for metadata and events for analytics applications and Profile D for access control peripherals. ONVIF continues to work with its members to expand the number of IP interoperability solutions ONVIF conformant products can provide.
Battery Energy Storage Systems (BESS) are revolutionizing the way they power the world, acting as the source that keeps renewable energy flowing even when the sun isn’t shining or the wind isn’t blowing. As the backbone of modern energy infrastructure, BESS plays a crucial role in balancing supply and demand. However, with the increasing adoption of large-scale battery storage comes the responsibility for manufacturers, site managers, and regulators to manage its risks effectively. Thermal runaway in battery storage Much like an electrical surge that fries a circuit, thermal runaway rapidly escalates, putting lives Thermal runaway is the equivalent of a system overload. It’s a dangerous chain reaction in which an overheated battery cell loses its stability and begins to ignite its neighbors, setting off a firestorm that’s incredibly difficult to contain. It's of particular concern when dealing with lithium-ion batteries used in products such as electric vehicles, portable electronics, and grid-scale storage. Much like an electrical surge that fries a circuit, thermal runaway rapidly escalates, putting lives, infrastructure, and energy security at risk. Key factors cause a dangerous phenomenon Several factors can cause this dangerous phenomenon to ignite, including: Overcharging or overdischarging: Pushing a battery beyond its limits can cause excessive heat buildup, leading to system failure. Physical damage or manufacturing defects: Cracks, punctures, or design flaws can create weak links in the chain, making failures more likely. Environmental conditions: Exposure to high temperatures or external heat sources can turn a stable BESS into a ticking time bomb. Adoption of BESS units The fallout from a BESS fire can be severe, resulting in massive financial losses, grid instability The fallout from a BESS fire can be severe, resulting in massive financial losses, grid instability, and environmental harm. And when they consider that these storage units are often installed near other high-energy infrastructure, the potential for disaster multiplies. With the adoption of BESS units ramping up across the globe, soaring by more than 50% in 2024 alone, the potential risks must be managed in a way that safeguards workers, critical assets, communities, and the environment. Stop the Spark Before it Starts: The power of thermal monitoring The best way to prevent thermal runaway is to detect heat anomalies before they escalate. But without the right monitoring tools in place, operators are left in the dark, often unaware of hidden dangers until it’s too late. The best way to prevent thermal runaway is to detect heat anomalies before they escalate That’s where thermal imaging technology plays a pivotal role. By offering continuous, real-time temperature surveillance, advanced thermal imaging can alert personnel to dangerous situations as they being to develop, so that no hot spot beyond specifications goes unnoticed. Like a circuit breaker that prevents an electrical overload, thermal monitoring acts as a failsafe, allowing site managers to catch and address overheating batteries before they ignite. Energizing safety: What makes a thermal monitoring system? To truly keep BESS operations running smoothly without the risk of meltdown, thermal monitoring systems must offer: High-resolution imaging: The ability to detect even the slightest temperature variations across battery stacks, ensuring no heat anomaly slips through the cracks Wide field of view: Comprehensive coverage that leaves no blind spots, just as a well-designed electrical grid leaves no home without power Advanced analytics: Smart detection technology that filters out false alarms caused by reflections, weather, or routine human activity 24/7 real-time monitoring: A non-stop watchdog that never sleeps, ensuring site managers stay wired into potential risks at all hours. With 640 × 480 thermal resolution, FSX® (Flexible Scene Enhancement) technology, on-the-edge analytics, and offered fields of view up to 80°, FLIR’s industry-pioneering A500f/A700f Advanced Smart Sensor camera is key to ensuring site owners' valuable peace of mind. Powering a safer future BESS technology is charging ahead, and with it, the responsibility to keep energy storage systems safe and stable. If left unmonitored, thermal runaway could pull the plug on renewable energy progress, jeopardizing the benefits of grid resilience, sustainability, and energy security. By integrating cutting-edge thermal imaging into BESS infrastructure, operators can stay ahead of the curve, preventing small temperature fluctuations from sparking massive disasters. Because in the high-stakes world of energy storage, early detection isn’t just a bright idea it’s the only way to keep the power on.
The Z-Wave Alliance, the standards development organization dedicated to advancing the smart home and Z-Wave® technology, announces that pioneering silicon providers Silicon Labs and Trident IoT have both achieved the Alliance’s newly established Z-Wave Protocol Certification. As the silicon solutions providers currently supporting the Z-Wave ecosystem, this certification ensures that all products developed on their platforms maintain the required levels of interoperability, heightened security, and continued innovation across a global Z-Wave marketplace. Z-Wave Protocol Certification The new Z-Wave Protocol Certification contributes to and further validates the rigorous standards The new Z-Wave Protocol Certification contributes to and further validates the rigorous standards set by the Z-Wave Alliance, ensuring that core tenets of Z-Wave technology, such as interoperability, backwards compatibility, enhanced security, and robust developer resources, remain across all Z-Wave-enabled products. Trident IoT brings a focused, developer-first approach to Z-Wave innovation. Founded by long-time pioneers within the IoT space, the company was established to meet growing demand for streamlined silicon, certification, and design support tailored to the Z-Wave ecosystem. Innovative Z-Wave products “Achieving Z-Wave Alliance certification for our semiconductor solutions and SDK is a testament to our dedication to quality, interoperability, and developer empowerment,” said Mariusz Malkowski, CTO at Trident IoT. “This milestone enables our partners to confidently accelerate their time-to-market with fully certifiable and innovative Z-Wave products.” Latest Z-Wave software release Z-Wave Protocol Certification enables Silicon Labs customers to develop and certify Z-Wave products Silicon Labs, a pioneering innovator in low-power wireless solutions, builds upon its extended pedigree of Z-Wave innovation through this certification achievement. The Z-Wave Protocol Certification enables Silicon Labs customers to develop and certify Z-Wave products using its EFR32ZG23, EFR32ZG28, and ZGM230S hardware platforms along with their latest Z-Wave software release (v7.23.1). Open Z-Wave technology “When Silicon Labs made the strategic decision to open Z-Wave technology up to the community in the name of open-source advancement, the goal was always to drive member contribution, broader adoption, and strengthen the ecosystem,” said Abitzen Xavier, Staff Product Manager for Proprietary & Z-Wave at Silicon Labs. “Z-Wave continues to be a pioneering platform in the smart home and beyond. Silicon Labs is pleased to provide this new certification and its accompanying enhancements to help our customers continue to build secure, reliable, and interoperable Z-Wave devices.” Smart home and IoT innovation Avi Rosenthal, Chairman of the Board for the Z-Wave Alliance, praised the contributions of both companies, stating, “The achievements by Trident IoT and Silicon Labs mark significant milestones, reinforcing the strength and versatility of the Z-Wave ecosystem." "By taking the necessary steps to certify their solutions, these companies now provide manufacturers and developers with essential tools for accelerating smart home and IoT innovation.”
Pioneering fire and life safety solutions manufacturer, Advanced, has won an award at the 2025 Fire & Security Matters (FSM) Awards, recognizing its achievements in fire safety, customer service, innovation, and sustainability. At the ceremony, held at Coventry’s CBS Arena on 5th June, Advanced won the award for Fire Safety Project of the Year, and was also commended in the Fire Safety Manufacturer of the Year category. Modernize fire safety Advanced’s double win at last year’s FSM Awards and mark a significant milestone in its ongoing mission These accolades follow Advanced’s double win at last year’s FSM Awards and mark a significant milestone in its ongoing mission to create a safer, more sustainable future. Advanced’s installation of its AdvancedLive system at Blists Hill Victorian Town earned the company Fire Safety Project of the Year. Delivered in partnership with Chubb Fire & Security, the project showcased how cutting-edge technology can be tailored to meet the challenges of a historically sensitive, multi-structure site. Wireless connectivity, intuitive controls, and a bespoke visual interface helped modernize fire safety across the landmark site without compromising its heritage. Fire system management Meanwhile, the judging panel commended the strength and innovation behind Advanced’s next-generation MxPro 5 fire panel, which played a key role in earning recognition in the Fire Safety Manufacturer of the Year category. Featuring a faster processor, improved configuration speeds, and seamless integration with AdvancedLive, the panel highlights the company’s commitment to smarter, more connected fire system management. Combined with continued investment in product development and responsiveness to market needs, these advancements helped distinguish Advanced in a highly competitive category. R&D and customer support Combined with continued investment in product growth and responsiveness to market needs Commenting on the awards, Advanced Managing Director Antonio Telesca said: "To be recognized at this year’s FSM Awards is an incredible achievement and a reflection of the hard work, talent, and passion of our entire team." "These awards celebrate every department across the business, from R&D and customer support to sustainability and project delivery, and I’d like to thank our customers and partners for their continued trust and support.” Innovation and achievement The 2025 FSM Awards brought together over 400 fire and security professionals to celebrate innovation and achievement across the sector. Representing Advanced at the event were Salvy Vittozzi, Phil Calvey, Paul Duffy, Rachael Houghton, Mark Ramshaw, Paul Taylor, Conor MacLeod, and Sarah Yule.
Regula, a developer of forensic devices and identity verification solutions, introduces the first-ever device designed for fast and trustworthy detection of morphed facial images in identity documents. The new morphing detector Regula 4166 is a compact, pen-sized tool that effectively addresses the growing challenge of face morphing, a technique where two facial images are blended to create a single photo resembling several individuals. Advanced forensic equipment Face morphing is very difficult to identify, even with advanced forensic equipment Face morphing poses significant security risks at border controls and other identity verification points. The dangers of this threat are not limited to illegal border crossings; it also facilitates other types of crimes such as labor crime, modern-day slavery, organized crime, and terrorism. Though not new and less sophisticated than other identity fraud techniques, face morphing is very difficult to identify, even with advanced forensic equipment. To do it “the traditional way,” a document examiner has to conduct multiple checks, scrutinizing a facial image under various lights and angles of observation. In this case, success largely depends on the specialist's competency. Regula 4166: game changer The new Regula 4166 is a game changer. Designed specifically to highlight overprinting traces (typical of morphing), like paint droplets, it provides the necessary visualization of the photo surface and structure. It is achieved thanks to a special lighting mode and a specific camera angle that enables three-dimensional visualization. As a result, face morphing is identified with visual certainty. Key features of the morphing detector Regula 4166 3D surface visualization: The device provides a three-dimensional view of the examined photo surface thanks to the tilted positioning of the camera and side oblique light source. It enables observation of distortions, pigment clusters, layering, and other physical inconsistencies typical of morphing. Intuitive operation: The Regula 4166 features a straightforward, plug-and-play interface that ensures quick adoption and efficient use without extensive training. Supplied software for instant usage: It comes with easy-to-use software that displays the morphing image from the device in real time and enables quick screenshots—perfect for evidence capture, fast demonstrations, or training. Unified ecosystem: The Regula 4166 is fully compatible with a wide variety of Regula’s forensic devices, including Regula video spectral comparators. Connected to them via Regula Forensic Studio software, the Regula 4166 enables seamless integration into existing forensic setups and creates a streamlined, centralized environment for document authentication and evidence management. Ultra-compact design: Its pen-sized form ensures maximum portability, making it ideal for both stationary and on-the-go document inspections, including first-line border control. Identity document analysis “The Regula 4166 fills a critical gap in identity document analysis. It’s the first tool of its kind designed specifically to expose overprinting traces typical of face morphing—fast, accurately, and informatively." "Whether used on its own or as part of a larger forensic setup, this device empowers border officers, forensic experts, and other document examiners to detect one of today’s most deceptive types of fraud with confidence,” says Alex Lewanowicz, Director of Hardware Engineering at Regula. Regula’s proactive response This launch continues Regula’s proactive response to face morphing risks. Earlier this year, the company introduced the ForensicScope Regula 4125, an all-in-one portable device equipped with a broad range of inspection tools, including face morphing detection. The new Regula 4166 builds on this effort with a focused solution tailored for mitigating this fraud technique, which often goes under the radar.
Cisco unveiled new innovations to help companies adapt and transform in the AI era. Enterprises are under pressure to accelerate secure AI adoption and drive value from AI investments. To help organizations meet these opportunities, Cisco continues to reimagine the datacenters and workplaces of the future. Infrastructure for the AI era “Cisco is delivering the critical infrastructure for the AI era—secure networks and experiences, optimized for AI that connect the world and power the global economy,” said Jeetu Patel, President and Chief Product Officer, Cisco. “We’re witnessing an unprecedented surge in innovation as organizations embrace agentic AI to automate workflows and solve complex problems. Cisco has a rich history of helping companies run their infrastructure; today, we’re building on that foundation to power the next generation of AI.” Cisco’s networking and security solutions Patrick Milligan, chief information security officer, Ford Motor Company, noted, “Agentic AI is being used across Ford’s business, from design to engineering to manufacturing and for customer support." "As we build, deploy, and manage sophisticated AI capabilities at scale, Cisco’s networking and security solutions are an important part of the overall technology infrastructure.” Range of new products and enhancements At Cisco Live, Cisco unveiled a wide range of new products and enhancements to help customers navigate the shift to agentic AI, including: Workplaces for the age of AI: Creating an intelligent workplace relies on modern network infrastructure that adapts to increased traffic, ensures always-on access, and delivers robust security. Meanwhile, organizations must empower people to work smarter and more effectively than ever. To meet these demands, Cisco announced new devices to power campus, branch, and industrial networks, and AI-powered unified management to help organizations move past reactive workflows to conducting autonomous, proactive network management. Additionally, Cisco's AI-powered Room Vision PTZ camera transforms meetings for a more cinematic experience. The Jira Workflow Automation in the Cisco AI Assistant for Webex Suite boosts efficiency, while the Webex AI Agent streamlines customer self-service with industry-specific templates. Read more here: The AI-Ready Enterprise: Building the Intelligent Workplace with Cisco. Simplified Operations for the age of AI with AgenticOps: Cisco is unveiling multiple AI-driven solutions to empower IT teams with simplicity, and automation, including Cisco AI Canvas, an industry-first generative user interface for real-time collaboration between network and security operations teams, and the Cisco AI Assistant, which provides conversational control across the Cisco suite. Core to the new capabilities is Cisco’s Deep Network Model — a domain-specific LLM trained on Cisco’s vast knowledge base, including Cisco U. courseware and Certified Internetwork Expert (CCIE) materials. The result is AI that understands networks and helps IT teams work more efficiently. Read more here: Welcome to the Agentic Era: People + Agents Achieving More, Together. Data Centers for the age of AI: Cisco unveiled continued innovation in its compute and network solutions for datacenters to support agentic AI, which places a premium on network bandwidth, latency, and power efficiency. To help drive adoption of AI solutions to strengthen the power grid, Cisco is joining the EPRI Open Power AI Consortium. Additionally, Cisco is introducing new capabilities to assist service providers to deliver and monetize new AI services. Read more here: Expanding the Edge of Possibility: Cisco Agile Services Networking for the AI Era. Security for the age of AI: Robust security has never been more critical, as enterprises navigate the complexity of a growing number of applications, a highly distributed and mobile workforce, and sophisticated AI-driven threats.Cisco is introducing innovations across its Hybrid Mesh Firewall and Universal Zero Trust Network Access (ZTNA) offerings; announced two new Firewalls, the 6100 series and 200 series, providing customers with best-in-class price performance; and unveiled capabilities across the Cisco Security Cloud to help customers meet the challenges of securing agentic AI. Read more here: Making Agentic AI Work in the Real World and Cisco Hybrid Mesh Firewall: Better Enforcement Points, Smarter Segmentation, and Multi-Vendor Policy. Digital Resilience at the Core: Several AI innovations, including enhanced capabilities in Splunk Observability Cloud and Splunk AppDynamics, along with deeper integrations between Cisco and Splunk solutions, are helping customers gain greater visibility into network health and performance. Key updates include a bidirectional integration between Splunk Observability, Cisco ThousandEyes Assurance and Cisco Enterprise Networks, enabling more resilient, insight-driven digital operations. Read more here: Cisco and Splunk Strengthen Enterprise Digital Resilience in the AI Era. Unified Management for the age of AI: The company is previewing Cisco Cloud Control, a new unified management platform spanning Cisco’s networking, security, and observability portfolios. Cisco Cloud Control will offer a cohesive experience anchored by AI native tools like Cisco AI Canvas, and the Cisco AI Assistant. With Cisco Cloud Control IT will be able to execute cross-product workflows, proactively identify and resolve issues, and manage infrastructure with ease.


Expert commentary
A key characteristic of many successful companies is that good ideas come from everyone, not just specific departments or job titles. What one person sees as obvious may be questioned by someone else who is less familiar with the product or process. This simple interaction can spark a whole new, faster, and better approach. While valuing tradition is important, if someone uses the phrase “that’s how we’ve always done it,” it’s essential to analyze the process to ensure it remains optimal. Business conditions change rapidly, and what was considered a perfect process last week may need adjustments this week. Comprehensive approach to innovation This comprehensive approach to innovation fosters continuous improvement across all aspects of the organization Innovation should permeate every level of an organization, from product development and customer experience to sustainability practices and employee training. This comprehensive approach to innovation fosters continuous improvement across all aspects of the organization, allowing companies to stay agile, competitive, and in tune with their customers' constantly evolving needs. Addressing real-world challenges At the heart of pervasive innovation in the security industry lies the development of smart products and solutions that address real-world challenges. This approach integrates advanced technologies to enhance security while improving user experience. For instance, the integration of mobile credentials, biometrics, real-time wireless locks, intelligent keys, and cloud-connected access control systems exemplifies how technology can streamline operations and provide users with seamless and secure access. Offering user-friendly solutions These advancements reflect a deep understanding of user needs and preferences, offering solutions that are not only secure but also convenient and user-friendly. A notable example is UniKey's Kēvo, the first Bluetooth-enabled touch-to-open smart lock, introduced in 2013. Developed in partnership with Kwikset, this innovative product allowed users to unlock doors simply by tapping the lock with a compatible smartphone. By continuously innovating across various aspects of security products and solutions, companies can ensure that their offerings remain relevant and effective in addressing the evolving challenges of the security landscape. Design-driven features Products designed for quick and straightforward installation reduce labor costs and minimize downtime Innovation extends beyond technology to encompass design-driven features that prioritize user convenience and satisfaction. For instance, ease of installation is a critical factor in the adoption of new door hardware. Products designed for quick and straightforward installation reduce labor costs and minimize downtime, making them more attractive to both installers and end users. For electronic locks, long-lasting battery performance is essential for minimizing maintenance and ensuring reliability. Products with extended battery life reduce the frequency of replacements and enhance user confidence. Incorporating antimicrobial finishes into door hardware addresses growing concerns about hygiene and cleanliness. Taking hygiene a step further, touchless technology in door hardware minimizes physical contact, reducing the potential for cross-contamination and enhancing user convenience. Sustainability initiatives Sustainability initiatives in door hardware have evolved from niche considerations to central pillars of modern product development, not least of which is the growing consumer demand for sustainable products, which is influencing purchasing decisions. According to a Nielsen report, 66% of global consumers are willing to spend more on a product if it comes from a sustainable brand, leading many companies to prioritize the use of recycled and recyclable materials in their products. Beyond material selection, manufacturers are also refining their production processes to minimize environmental impact. Finishing processes are evolving to use non-toxic and low-impact finishing methods, such as powder coating and physical vapor deposition. Energy-efficient door hardware Energy-efficient door hardware plays a significant role in the overall energy conservation of buildings Energy-efficient door hardware plays a significant role in the overall energy conservation of buildings. Properly designed door hardware can help maintain a building’s thermal envelope, reducing heating and cooling demands. For instance, the HID® Signo™ access control reader includes improved power supply technology and energy-saving features that ensure reduced energy consumption when the reader is in a resting state. Environmental Product Declarations To further demonstrate their commitment to sustainability, many manufacturers seek certifications validating their environmental efforts. Environmental Product Declarations (EPD) and Leadership in Energy and Environmental Design (LEED) certifications have become key indicators of a product’s environmental performance. An EPD provides detailed information about the environmental impact of a product throughout its lifecycle, aiding in the transparency that architects and builders require to make informed choices. Similarly, LEED certification emphasises energy savings and broad environmental priorities, including water efficiency, CO₂ emissions reduction, and improved indoor environmental quality. Customer service and training Innovation is also making great strides in the behind-the-scenes efforts of customer service and training. Predictive maintenance technologies are revolutionising how companies manage product performance and customer support. By utilizing data analytics and IoT technologies, companies can offer maintenance alerts, remote diagnostics, and connected support services that anticipate issues and failures before they occur. This shift from reactive to predictive maintenance minimizes service disruptions and enhances customer trust by ensuring products operate at optimal levels. Digital training initiatives Digital training initiatives equip employees and customers with the skills needed to utilize new technologies In parallel, digital training initiatives equip employees and customers with the skills needed to utilize new technologies in a cost-effective and accessible manner. Digital installer certification programs, learning portals, and customer enablement initiatives are all part of a comprehensive strategy to equip stakeholders with the knowledge and skills they need to succeed. By investing in comprehensive training programs, companies foster a culture of adaptability and competence, ensuring that customers can fully leverage technological advancements. This approach not only enhances operational efficiency but also strengthens customer relationships by empowering them with the knowledge to make informed decisions. Incremental improvements While groundbreaking innovations often capture headlines, it’s the steady, incremental improvements that consistently deliver real-world value. Companies can achieve sustained growth and success by focusing on continuous innovation across all facets of the organization. This quiet progress, though less visible, is often more impactful as it builds a solid foundation for long-term achievement. In a world where change is the only constant, fostering a culture of pervasive innovation is the key to sustained relevance and growth.
The physical security industry has been in love with the cloud for quite some time. And understandably so. The promise of instant scalability, centralized access, and simplified maintenance is hard to ignore, especially in an era of remote work and distributed facilities. But reality is catching up to the hype. For many, especially those dealing with video surveillance at scale, the cloud is no longer the catch-all solution it once seemed. Rising costs, bandwidth limitations, and latency issues are exposing its shortcomings. And the more resolution increases, from HD to 4K and beyond, the heavier that burden becomes. Modern security cameras This is where edge computing, specifically AI-enabled edge processing available in modern security cameras, starts to look less like an option and more like a necessity. But it’s not just about adding intelligence to cameras. It’s about how that intelligence is deployed, scaled, and maintained. This leads us to containerization and tools such as Docker, which are a revolutionary piece of the puzzle. When cloud isn't enough Cloud analytics for video sounds great in theory: stream everything to the cloud Let’s start with a basic issue. Cloud analytics for video sounds great in theory: stream everything to the cloud, let powerful servers do the thinking, then serve up results to end-users in real time. However, in practice, this model can break down quickly for many end-users. Raw video is heavy. A single 4K camera streaming 24/7 can generate terabytes of data per month. Multiply that by hundreds or thousands of cameras, and the bandwidth and storage costs become unsustainable. Then there’s latency. If AI needs to detect a person entering a restricted area or identify a license plate in motion, seconds count. Routing video to a cloud server for analysis and waiting for a response can introduce delays. Adding in concerns about uptime, such as what happens if the internet connection goes down, it becomes clear why relying exclusively on the cloud creates friction for mission-critical deployments. The edge advantage Edge processing turns that model on its head. Instead of sending everything out for analysis, edge-enabled cameras do the heavy lifting on-site. AI algorithms run directly on the device, interpreting what they see in real time. They generate metadata—lightweight descriptions of events, objects, or behaviors—rather than raw video. This metadata can be used to trigger alerts, inform decisions, or guide further review. The benefits are obvious: latency drops, bandwidth use plummets, and storage becomes more efficient. Edge processing solves many cloud deployment issues by keeping the compute where the data is generated, on the device. This frees the cloud up to do what it’s best at: providing scalable and centralized access to important footage. But where does the edge go from here? How do we evolve these powerful IoT devices to deliver even more situational awareness? Enter Docker: An app store for edge AI They package an app along with everything it needs to run: the code, settings, libraries, and tools This is where the concept of containerization and open development platforms like Docker comes in. Let’s start with an analogy that is helpful for understanding containers. Imagine you're getting ready for a trip. Rather than hoping your hotel has everything you need, you pack a suitcase with all your essentials: clothes, toiletries, chargers, maybe even snacks. When you arrive at your destination, you open the suitcase and you’re ready to go. You don’t need to borrow anything or adjust to whatever the hotel has, since you’ve brought your own reliable setup. Containers in software work the same way. They package an app along with everything it needs to run: the code, settings, libraries, and tools. This means the application behaves exactly the same, whether it’s running on a developer’s laptop, on the edge in an IoT device, or in the cloud. Security camera with a powerful edge processor There’s no last-minute scrambling to make it compatible with the environment it lands in, because it’s self-contained, portable, and consistent. Just like a well-packed suitcase simplifies travel, containers simplify software deployment. They make applications faster to start, easier to manage, and more predictable, no matter where they’re used. For a security camera with a powerful edge processor, it’s like giving the camera its own specialized toolkit that can be swapped out or upgraded without touching the rest of the system. It also means you can run multiple AI applications on a single camera, each in its own isolated environment. Integrators and end-users These applications don’t interfere with each other and can be updated independently Want to add fall detection to a healthcare facility’s camera network? Just deploy the analytics in a container. Need to monitor loading docks for pallet counts at a warehouse? Spin up a different container. These applications don’t interfere with each other and can be updated independently. As a developer, if you use an open container platform like Docker, any system that supports Docker can utilize your software. This removes the need to do expensive custom work for each partner and ecosystem. This is one reason Docker containers are tried and true in the larger IT space and are just starting to get traction in the security sector. Docker also makes this scalable. Developers can build AI tools once and push them out to hundreds or thousands of devices. Integrators and end-users can customize deployments without being locked into proprietary ecosystems. And because containers isolate applications from core system functions, security risks are minimized. Metadata, not megabytes Traditional video analytics systems often require full video streams to be processed One of the most underappreciated aspects of this method is the way it redefines data flow. Traditional video analytics systems often require full video streams to be processed in centralized servers, either on-premises or in the cloud. This model is brittle and costly, and it’s also unnecessary. Most of the time, users aren’t interested in every frame. They’re looking for specific events. Edge AI enables cameras to generate metadata about what they see: “Vehicle detected at 4:02 PM,” “Person loitering at entrance,” “Package removed from shelf.” This metadata can be transmitted instantly with minimal bandwidth. Video can still be recorded locally or in the cloud, but only accessed when needed. This dramatically reduces network load and allows the cloud to be used more strategically: for remote access, long-term archiving, or large-scale data aggregation, without being overwhelmed by volume. Building smarter systems, together A single camera can run analytics from multiple third parties, all within a secure, containerized framework An equally important aspect of containerization is how it opens up the ecosystem. Traditional security systems are often built as closed solutions. Everything—from the cameras to the software to the analytics—comes from a single vendor. While this simplifies procurement, it limits innovation and flexibility. Docker flips that model. Because it’s an open, well-established standard, developers from any background can create applications for edge devices. Integrators can mix and match tools to meet unique customer needs. A single camera can run analytics from multiple third parties, all within a secure, containerized framework. This is a profound shift. Security cameras stop being fixed-function appliances and become software-defined platforms. And like any good platform, their value increases with the range of tools available. Hybrid: The realistic future So, where does this leave the cloud? It is still essential, but in a more specialized role. The most robust, future-proof architectures will be hybrid: edge-first and cloud-supported. Real-time detection and decision-making happen locally, where speed and uptime matter most. The cloud handles oversight, coordination, and data warehousing. Real-time detection and decision-making happen locally, where speed and uptime matter most This hybrid model is especially useful for organizations with complex deployments. A manufacturing plant might retain video locally for 30 days but push older footage to the cloud to meet retention requirements. A retail chain might analyze customer flow on-site but aggregate trend data in the cloud for HQ-level insight. Hybrid gives organizations the flexibility to optimize cost, compliance, and performance. Regulatory realities It’s also worth noting that not every organization can, or should, store data in the cloud. Privacy regulations like GDPR in Europe or similar laws elsewhere require strict control over where data is stored. In many cases, sensitive footage must remain in-country. Edge and hybrid models can make compliance easier by minimizing unnecessary data movement. Conclusion: Smart security starts at the edge The next wave of innovation in physical security won’t come from bigger cloud servers or faster internet connections. It will come from smarter edge devices, with cameras and sensors that don’t just record, but understand and classify events. And the foundation for that intelligence isn’t just AI, but how that AI is deployed. Containerization via platforms like Docker is unlocking new levels of flexibility, security, and scalability for the physical security industry. By embracing open standards, supporting modular applications, and rethinking how data flows through the system, physical security professionals can build solutions that are not only more effective but also more sustainable, secure, and adaptable. The cloud still has its place. But the edge is essential to the future for real-time intelligence, mission-critical uptime, and cost-effective deployment.
In 2021, New Orleans took bold steps to modernize its public safety strategy after experiencing a dramatic increase in criminal activity. The city invested $70M in advanced video security systems, placing smart cameras in high-risk areas like busy transit hubs and crowded public spaces to promote community safety. The cameras weren’t just traditional CCTV setups—they were smart security solutions equipped with real-time alerts that leverage AI-powered analytics, facial recognition and cloud-based technology. Reinforcing public safety Law enforcement agencies improved their response times and investigative outcomes Within months, the impact was clear: theft and burglaries of vehicles, residential and business properties reduced up to 48% total between 2022 and 2023. With 24-hour monitoring and rapid access to critical footage, law enforcement agencies improved their response times and investigative outcomes, reinforcing public safety across the city. The role of video security in community safety One of the most effective ways to keep communities safe is through video security solutions that allow real-time monitoring and provide rapid responses. Modern Video Surveillance as a Service (VSaaS) platforms allow security professionals to monitor spaces continuously, providing instant alerts for any suspicious activities. Advances in this technology are transforming the way businesses and organizations approach community safety, playing a pivotal role in creating safer environments, deterring crime, and enabling faster incident response. Video security solutions Video security solutions also contribute significantly to public safety by monitoring high-traffic areas such as public parks, busy transportation hubs, and crowded city streets. When security cameras are visible, not only do they act as a deterrent to potential criminals, but they can also significantly reduce the likelihood of theft, vandalism, and violent crime. Video security solutions also contribute greatly to public safety by monitoring high-traffic areas Similarly, large gatherings such as concerts, sporting events, and festivals present unique challenges that require a multifaceted approach to security. With thousands of attendees in a confined space, effective security measures are essential to prevent overcrowding, unauthorized access, and potential threats. In situations like these, advanced video security systems can aid in efficient crowd management, allowing event organizers to respond and react quickly in the event of an emergency. The future of smart security solutions Today, video security solutions are becoming smarter and more adaptable than ever before. For example, innovations such as solar-powered security units ensure continuous monitoring even in remote or off-grid locations, contributing to broader, more sustainable coverage. Recent developments like AI-enhanced analytics help filter out false alarms while focusing on threats, improving response times and efficiency. By embracing modern security solutions, municipalities, businesses, and event organizers can take proactive steps to protect their communities when it matters most. Public safety will always be an ongoing challenge for businesses and organizations alike for a multitude of reasons; however, the role of advanced video security systems in promoting public safety is more important than ever before.
Security beat
For all the emphasis on cloud systems and centralized servers at ISC West, a lot of innovation in security video systems is happening at the edge. New advancements inside video cameras are boosting capabilities at the edge, from advancements in processing power to artificial intelligence (AI) and machine learning (ML) algorithms that can now be deployed directly on the cameras or edge devices. Advancements in AI algorithms The progress of video systems becoming smarter at the edge is driven by the need for real-time insights, lower latency, bandwidth efficiency, enhanced privacy, and improved reliability. Advancements in edge computing hardware and AI algorithms are enabling a range of intelligent video applications across various industries, including physical security. Smarter functionality at the edge is a benefit of new computer systems-on-chips (SoCs) that are driving new heights of performance for today’s cameras. Axis Communications’ ARTPEC-9 Axis Communications’ new ARTPEC-9 SoC offers advanced video compression to reduce bandwidth Axis Communication’s new ARTPEC-9 system-on-chip (SoC) offers advanced video compression to reduce bandwidth and storage needs. With a low bitrate, the SoC helps deliver high-quality imaging with outstanding forensic detail. ARTPEC-9 also offers enhanced deep learning capabilities to allow users to leverage the latest video analytics and accelerate the implementation of AI technology. Axis maintains control over all aspects of the chip’s development to ensure high quality and cybersecurity. Among the benefits of ARTPEC-9 are better AI and deep learning, better image quality, better cybersecurity, and AV1 license-free video compression (see below). Hanwha Vision’s Wisenet 9 Hanwha Vision has launched Wisenet 9, its most advanced AI-powered System on Chip (SoC). Wisenet 9’s enhanced edge AI capabilities increase performance as the volume and complexity of security threats demand real-time, accurate analysis. By elevating edge-device performance, AI empowers systems to quickly analyze vast amounts of video data and discern crucial patterns and anomalies. A key differentiator driving Wisenet 9 is deployment of two Neural Processing Units (NPUs), which improve performance three-fold compared to Wisenet 7, the previous SoC generation. While one NPU handles image processing, the other focuses on object detection and advanced analytics. This dual NPU concept was introduced to ensure video quality and analytics have independent resources, thus preventing one function from impacting the performance of the other. The latest from Ambarella Ambarella is a supplier of edge AI systems-on-chips to multiple video camera manufacturers Off the ISC West trade show floor in a nearby meeting room, semiconductor company Ambarella demonstrated how it will continue to push the envelope of what is possible with generative AI at the edge. Ambarella is a supplier of edge AI systems-on-chips to multiple video camera manufacturers and recently achieved the milestone of 30 million cumulative units shipped. The demonstrations highlight Ambarella’s ability to enable scalable, high-performance reasoning and vision AI applications across its ultra-efficient, edge-inference CVflow 3.0 AI SoC portfolio. The company’s DeepSeek GenAI models run on three different price/performance levels of its SoC portfolio. In addition to advancements in GenAI processing at the edge, Ambarella integrates image processing, encoding and system-level functions into all its AI SoCs. New standard for video encoding: AV1 AV1 compression is a next-generation video coding technology that offers significant improvements in compression efficiency and video quality, especially at lower bitrates. Its royalty-free nature positions it as a crucial codec for the future of internet video. AV1 compression is a next-generation video coding technology. Axis Communication’s ARTPEC-9 chip now supports the AV1 video encoding standard. By embracing this standard, which is new to the physical security market although it was introduced in 2018, Axis sets the stage for AV1 compression to eventually become the industry standard, replacing H.264 and H.265. Network video transmission AV1 is an open-source, license-free coding format designed mainly for efficient network video transmission AV1 is an open-source, license-free coding format designed specifically for efficient network video transmission. It delivers high-quality video at low bitrates, reducing bandwidth consumption and storage costs. The codec was developed by the Alliance for Open Media (AOM), a nonprofit organization founded in 2015 by Google, Intel, Amazon, Microsoft, Netflix, and Mozilla (among others), to provide open-standard, next-gen video coding technology. AV1 is ideal for cloud solutions—making streaming applications more robust, scalable, and capable of delivering real-time insights. Now the ARTPEC-9 chipset brings these benefits to the surveillance industry, and AV1 is currently supported by AXIS Camera Station. Providers of major video management solutions (VMS) such as Genetec and Milestone will be adding support for AV1, with further developments already underway. More intelligence at the edge Intelligence inside video cameras comes from the processing power and algorithms that enable them to perform tasks beyond simply capturing and recording images. This "intelligence" allows cameras to analyze the video stream in real-time, identify objects, detect events, and make decisions or provide alerts based on what they "see." New and improved SoCs are driving performance improvements at the edge. The increasing power of embedded processors and advancements in AI are continuously expanding the capabilities of intelligent video cameras.
Anyone who has been in a proverbial cave for the last couple of years faced a language barrier at this year’s ISC West 2025 trade show. The industry’s latest wave of innovation has brought with it a new bounty of jargon and buzzwords, some of which I heard at ISC West for the first time. As a public service, we are happy to provide the following partial glossary to promote better understanding of the newer terms. (Some are new to the security industry but have been around in the IT world for years.) Obviously, if we can’t understand the meaning of the industry’s lexicon (and agree on the meaning of terms!), we will struggle to embrace the full benefits of the latest industry innovation. Not to mention we will struggle to communicate. Generative AI Generative AI can identify an object in an image based on its understanding of previous objects This was perhaps the most common new(ish) term I heard bouncing around at ISC West. While the term artificial intelligence (AI) now rolls off everyone’s tongue, the generative “version” of the term is catching up. Generative AI uses what it has learned to create something new. The name comes from the core function of this type of artificial intelligence: it can generate (or create) new content. It doesn’t just copy and paste; it understands the underlying patterns and creates something original based on that understanding. In the case of video, for example, generative AI can identify an object in an image based on its understanding of previous objects it has seen. Video and security Generative AI can tell you something digitally about what is happening in an environment. There is no longer a need to write “rules;” the system can take in data, contextualize it, and understand it, even if it does not exactly match something it has seen before. In the case of video and security, generative AI offers more flexibility and better understanding. From 2014 to 2024, the emphasis was on detecting and classifying things; today AI is expanding to allow new ways to handle data, not so prescriptive and no more rules engines. Agentic AI Agentic AI refers to artificial intelligence systems that can operate autonomously to achieve specific goals Agentic AI refers to artificial intelligence systems that can operate autonomously to achieve specific goals, with minimal to no direct human intervention. In addition to the capabilities of generative AI, agentic AI can take action based on what it detects and understands. Use of agentic AI typically revolves around an if/then scenario. That is, if action A occurs, then the system should proceed with action B. For example, if an AI system “sees” a fire, then it will shut down that part of the building automatically without a human having to initiate the shutdown. There is a lot of discussion in the industry about the need to keep humans involved in the decision-making loop, so use of truly autonomous systems will likely be limited in the foreseeable future. However, the ability of agentic AI to act on critical information in a timely manner, in effect to serve as an “agent” in place of a human decision-maker, will find its place in physical security as we move forward. Inference Inference is another common term related to AI. It refers to the process by which an AI model uses the knowledge it gained during its training phase to make predictions, classifications, or generate outputs on new, unseen data. The direct relationship of this term to physical security and video is obvious. In the simplest terms, an AI system is “trained” by learning patterns, relationships, and features from a large dataset. During inference, the trained model is presented with new questions (data it hasn't seen before), and it applies what it learned during training to provide answers or make decisions. Simply put, inference is what makes AI systems intelligent. Containerization Dividing a massive security management system into several separate containers enables management of the various parts In IT, containerization is a form of operating system-level virtualization that allows you to package an application and all its dependencies (libraries, binaries, configuration files) into a single, portable image called a container. This container can then be run consistently across any infrastructure that supports containerization, such as a developer's laptop, a testing environment, or a server in the cloud. In the physical security industry, you hear “containerization” used in the context of separating out the various components of a larger system. Dividing a massive security management system into several independent containers enables the various parts to be managed, updated, and enhanced without impacting the larger whole. Genetec’s SecurityCenter cloud platform Think of it like shipping containers in the real world. Each container holds everything an application needs to run, isolated from other applications and from the underlying system. This ensures that the application will work the same way regardless of the environment it is deployed in. “It took us five years to containerize Genetec’s SecurityCenter cloud platform, but containerization now simplifies delivering updates to products whenever we want,” says Andrew Elvish, Genetec’s VP Marketing. Among other benefits, containerization enables Genetec to provide more frequent updates--every 12 days. Headless appliance Headless appliance is a device that is managed and controlled remotely through a network or web interface A headless appliance is a device that is managed and controlled remotely through a network or web interface. The device is like a “body without a head” in the traditional sense of computer interaction: It performs its intended function, but without any visual output or input device for local interaction. In physical security, such devices are increasingly part of cloud-based systems in which the centralized software manages and operates all the disparate “headless” devices. A headless appliance does not have a Windows management system. “The whole thing is managed through the as-a-service cloud system,” says Elvish. With a headless device, you just plug it into the network, and it is managed by your system. You manage the Linux-based device remotely, so configuring and deploying it is easy. Democratizing AI You hear the term democratizing AI used by camera manufacturers who are looking to expand AI capabilities throughout their camera lines, including value-priced models. For example, even i-PRO’s value-priced cameras (U series) now have AI – fulfilling their promise to democratize AI. Another approach is to connect non-AI-equipped cameras to the network by way of an AI-equipped camera, a process known as “AI-relay.” For instance, i-PRO can incorporate non-AI cameras into a system by routing/connecting them through an X-series camera to provide AI functionality. Bosch is also embracing AI throughout its video camera line and enabling customers to choose application-specific analytics for each use case, in effect, tailoring each camera to the application, and providing AI to everyone. Context Cloud system also enables users to ask open-ended queries that involve context, in addition to detection Context refers to an AI system that can understand the “why” of a situation. For example, if someone stops in an area and triggers a video “loitering” analytic, the event might trigger an alarm involving an operator. However, if an AI system can provide “context” (e.g., he stopped to tie his shoe), then the event can be easily dismissed by the automated system without involving an operator. Bosch’s IVA-Pro Context product is a service-based model that adds context to edge detection. The cloud system also enables users to ask open-ended questions that involve context in addition to detection. For example, rather than asking "do you see a gas can?" you can ask "do you see any safety hazards in this scene?" The pre-trained model understands most common objects, and understands correlations, such as "a gas can could be a safety hazard.” A scaled-down on-premise version of the IVA Context product will be available in 2026. Bosch showed a prototype at ISC West. Most video data is never viewed by an operator. Context allows a system to look at all the video with "almost human eyes." Cameras are essentially watching themselves, and understanding why something happened and what we can do. All that previously unwatched video is now being watched by the system itself, boosted by the ability to add “context” to the system. Any meaningful information based on context can trigger a response by an operator. Data lake A data lake is a centralized repository that allows one to store vast amounts of structured, semi-structured, and unstructured data in its native format. In the case of the physical security marketplace, a data lake includes data generated by systems outside the physical security infrastructure, from inventory and logistics systems, for example. A data lake is where an enterprise can accumulate all their data, from the weather to Point-of-Sale information to logistics, to whatever they can gather. Putting the data in one place (a “data lake”) enables them to mine that data and parse it in different ways using AI to provide information and insights into their business. Notably, a data lake contains all a company’s data, not just security or video data, which opens up new opportunities to leverage the value of data beyond security and safety applications. Crunching the various information in a data lake, therefore, security technology can be used to maximize business operations.
As the pioneering security event in the United States, ISC West is truly the global focal point for bringing together professionals across the physical and cybersecurity landscape. The event seeks to showcase innovation in security technology, nurture professional development, and explore the security implications of today’s connected world. Future of security With the growth of cybersecurity programming and the established Cybersecurity & Connected Internet of Things (IoT) pavilion, ISC West is addressing the future of security head-on. “As the lines between the digital and physical worlds blur, collaboration and shared learning among defenders have never been more critical,” says Mary Beth Shaughnessy, Event Vice President at RX USA, who oversees all aspects of the ISC brand. Shaughnessy previews what’s new at ISC West 2025 and shares other insights in our interview. Q: For long-time attendees at ISC West, what will be the biggest surprise at the 2025 show? Shaughnessy: Long-time attendees know to expect top-tier educational content through the SIA Education@ISC West program (produced by the Security Industry Association (SIA)) in addition to cutting-edge security innovations showcased by 700+ exhibitors. New this year is our focus on technology, training, and education around cyber-physical threats. In today’s connected world, physical and cybersecurity defenders must take a unified, holistic approach to protecting their people, assets, and data. ISC West serves as a bridge between those two worlds, helping organizations tackle the complex security landscape. Q: Presenting a high-profile music concert as part of ISC West is a fun value-add for attendees. Describe how this feature has been embraced by longtime attendees, and the plans for 2025. Shaughnessy: We’re thrilled to announce that the legendary Gin Blossoms will headline the ISC West Concert, sponsored by Wavelynx. This tradition began last year and became a celebrated highlight, offering professionals a chance to unwind and connect with colleagues and peers after a productive day on the show floor. When choosing a performer, we focus on acts that resonate across generations, making the experience both entertaining and memorable for our diverse audience. We are excited to continue this fun and exciting event and networking opportunity. Q: In the past, the education program at ISC West has been seen as secondary to the Expo event. How have you sought to increase the profile of the education program, and what new features will attract more attendees in 2025? Shaughnessy: We’ve expanded the SIA Education@ISC programming from three to four days, now beginning two days before the expo hall opens. These dedicated education days ensure professionals can engage in thoughtful discussions and gain actionable insights without overlapping with the Expo. This year, we’re proud to partner with RSA to introduce a new “IT for Security Professionals” track while also offering our core tracks, including AI & Digital Transformation, Critical Infrastructure & Data Protection, Cybersecurity & IT, InfraGard National Members Alliance @ ISC, and Video Surveillance. We will also be welcoming powerful keynote speakers — Rachel Wilson, Director of Cybersecurity, Morgan Stanley Wealth Management; Will Bernhjelm, Vice President of Security, Mall of America; and Kate Maxwell, Chief Technology Officer, Worldwide Defense & Intelligence, Microsoft. Q: What else is “new” at ISC West in 2025? Shaughnessy: Our educational programming has grown significantly — this year’s SIA Education@ISC program is our most extensive yet, offering more than 115 sessions led by over 200 distinguished experts. With broader and deeper topics, the program emphasizes the critical convergence of cyber and physical security, providing unparalleled insights for today’s security professionals. We are also significantly ramping up our cybersecurity offerings and expect to have more than 50 exhibitors in our Cybersecurity & Connected IoT pavilion with names such as Entrust and Ontic. Q: Networking is a critical aspect of ISC West. How are show organizers working to increase networking opportunities? Shaughnessy: Networking remains a top priority at ISC West, with countless opportunities to build valuable connections. Professionals can join peers at popular spots like The Bridge, The Cyber Hub, and the Career Zone (sponsored by: TEECOM). These spaces offer the chance to learn from industry experts, explore the challenges and innovations shaping the security workforce, and engage in dynamic discussions with peers. Also, returning by popular demand, the ISC West Concert, proudly sponsored by Wavelynx, delivers a vibrant evening of music and networking in a relaxed atmosphere. Together, these experiences ensure networking at ISC West is both impactful and memorable. Q: What is the biggest challenge for organizers of ISC West (and related events), and how are the organizers seeking to address the challenges? Shaughnessy: As with most events, there is a lot of pressure on organizers to ensure there’s “something for everyone,” add meaningful value, and introduce fresh, exciting features. At ISC West, we work to raise the bar each year by expanding our content with more thought pioneers, showcasing a broader range of innovative technologies, and fostering additional networking opportunities. Achieving top-quality results is no small task — it demands careful planning, collaboration, and a dedication to continuous improvement. This means actively listening to the needs of our attendees and exhibitors, staying ahead of industry trends, and ensuring we provide an experience that informs, inspires, and connects the security community.
Case studies
Elegance, design and entertainment – that’s what the new Grand Sapphire Resort & Casino in Iskele, in the east of the Turkish Republic of Northern Cyprus (TRNC), stands for. This exclusive hotel complex, located directly on the beach of the Karpaz Peninsula, offers guests top-level service, stunning architecture and a very special highlight: a casino with 42 live game tables and over 300 slot machines across a 2,700 m² gaming area. To ensure that guests not only have an impressive but also a safe experience, Grand Sapphire relies on a customized video surveillance solution from Dallmeier. The “Made in Germany” video technology ensures around-the-clock security and efficient processes – not only through high product quality, but also through the highest standards for data protection and data security. Data protection requirements One of the main requirements was the complete monitoring of gaming areas When the casino was opened, the security team at the Grand Sapphire Resort faced the task of implementing a modern casino security solution that would ensure both guest safety and smooth operations. “Our goal was to create a top-tier casino environment – and that includes a security concept that combines quality, data protection and efficiency,” explains Bayram Tegay, General Manager at Grand Sapphire. One of the main requirements was the complete monitoring of gaming areas, especially the live game tables, without interfering with day-to-day operations. At the same time, an exceptionally high level of data protection had to be maintained. Strict compliance regulations “In Northern Cyprus, casinos face especially strict compliance regulations,” says Yücel Çalişkan, Surveillance Manager at the resort. “Our department operates in full isolation from the rest of the organization. Protecting sensitive data is not optional for us – it is the very foundation of our work.” Integrated surveillance concept The team opted for a comprehensive video surveillance system from Dallmeier The team opted for a comprehensive video surveillance system from Dallmeier, planned and implemented by Dallmeier Türkiye. The customized security concept was visualized and preconfigured using the 3D camera planning tool PlanD. “PlanD offered the customer 100% planning reliability,” says Orhan Yörükoğlu, Director of Dallmeier Türkiye A.Ş. “Project stakeholders could see in advance exactly which camera would cover which area and what the overall project scope would be. That was enormously helpful for decision-making.” Precision from eight meters above All cameras were installed at a height of approximately eight meters on the ceiling All cameras were installed at a height of approximately eight meters on the ceiling – a technical challenge solved through the use of high-resolution cameras with suitable optics. For seamless surveillance of the 42 live game tables, slot areas and entrances, the installation combines Dallmeier PTZ and dome cameras. To provide a full overview of the gaming floor, a Panomera S8 multifocal sensor system is used. Thanks to its unique optical design, Panomera delivers a complete overview of the casino floor while still allowing detailed zoom-in views where needed. Central control room In the central control room, four operators work per shift on three 27-inch monitors each, while 18 large-format monitors provide overall visual control. Recording is handled redundantly via IPS 10000 network video recorders. The entire system is managed using the Hemisphere VMS platform operated on four VMC Touch workstations. For non-public areas, ONVIF-compatible third-party cameras are used, and their data is also fully integrated into the Dallmeier system thanks to Hemisphere’s open system architecture. Facial recognition Another key feature is the integration of a Corsight facial recognition system, operated on dome cameras Another key feature is the integration of a Corsight facial recognition system, operated on dome cameras. The system automatically identifies blacklisted individuals when they approach the casino entrance and notifies both front desk and security personnel in real time. “This feature not only helps us enforce bans, but also strengthens our guests’ sense of security,” says Çalişkan. “We receive alerts within seconds if a blacklisted individual tries to enter the casino.” Although the casino is open from 12:00 noon to 6:00 am, the surveillance system operates 24/7. This ensures that potential threats such as break-ins or tampering outside of business hours are reliably detected. In day-to-day operations, the system significantly speeds up incident resolution – for example, in the case of misunderstandings between dealers and guests. Closed network architecture The entire system operates within a completely closed network – with no physical or wireless interfaces to other systems, no cloud connectivity, and no mobile access. This architecture ensures full data security and regulatory compliance. Internally, strict policies are in place: surveillance staff are not permitted to have contact with employees from other departments. This underscores the critical role of data protection in the casino environment of Northern Cyprus. The current system architecture is designed for seamless future expansion. AI-based functions and video content analytics (VCA) can be integrated at any time if required. Security meets efficiency With the Dallmeier solution, Grand Sapphire benefits from a state-of-the-art surveillance system that not only meets the highest security standards but also supports operational efficiency. Casino Manager Bayram Tegay concludes: “The image quality, system responsiveness and support have really convinced us. For us, it was absolutely the right decision. Thanks to Dallmeier, we can make well-founded decisions at any time – quickly, reliably and based on high-quality data.”
Nizam Zachman Port, one of Indonesia's most important fishing hubs, supports thousands of local fishermen and maritime businesses. Recognizing the potential to enhance operations and better serve the community, the port management deployed Hikvision’s AIoT (AI-powered Internet of Things) technologies to make the port smarter and more efficient. Standard AIS signaling Port management identified several key areas where they believed technology could make a significant difference Every day, Nizam Zachman Port handles huge volumes of fish destined for both the Indonesian domestic market and for export around the world. Such an operation relies heavily on technologies that can make the port safer, more efficient, and more secure. Recently, the port management identified several key areas where they believed technology could make a significant difference. The first was to develop comprehensive capabilities to identify ships entering their waters, including unregistered fishing boats that don't use standard Automatic Identification System (AIS) signaling. They wished to adopt a unified detection approach that would operate effectively in all weather conditions, from foggy mornings to dark nights. Traditional communication methods The management team also recognized the value of upgrading their ship-counting and reporting systems. While their experienced staff performed excellent manual counting, management knew that combining human expertise with automated technology could deliver even more accurate records. This would be particularly valuable during busy periods, and when ships arrive at night and depart before dawn. Another area for improvement was communication. Here, the management team wanted to replace traditional communication methods with a modern audio system for efficient message delivery across the harbor. Innovative technologies for a smarter port To put their plans into action, Nizam Zachman Port partnered with PT. Dea Global Niaga, who designed a comprehensive system that perfectly matched the port's ambitious goals. Ship detection and identification: At the heart of the new system is an Anti-corrosion Thermal & Optical Bi-spectrum Network Positioning System (DS-2TD6267-100C4L/WY). This specialized camera uses thermal imaging to detect heat signatures from ship engines and hulls up to 2 km away and works equally well in fog, rain, or darkness. The casing meets the NEMA-4X anti-corrosion standard, ensuring durability in the salty sea environment. The camera is complemented by a Security Radar (DS-TDSB0W-FK/2km). At any point in time, this can identify and track the movement of up to 32 vessels in the harbor, providing detailed speed and distance information. When the radar detects movement, it automatically directs the camera system for seamless coordination. Enhancing perimeter security: To enhance perimeter security, two DarkFighter IR Network Speed Domes (DS-2DE5425IW-AE(T5)) have been installed. These cameras, with their Pan-Tilt-Zoom (PTZ) functionality, offer flexible movement and orientation. They come equipped with a 25x optical zoom, enabling them to provide detailed views of the port’s perimeter, ensuring that any incidents are quickly identified, even in low-light conditions. Improving communications across the port: For communication, seven Network Speakers (DS-QAZ1310G1T-E) have been installed across the port. These speakers allow the command center to broadcast announcements and alerts much more efficiently than before. Centralized intelligence: Everything connects through Hikvision’s 64-Channel 8K Network Video Recorder (DS-9664NI-M16/R), to the HikCentral Professional Platform. This video management platform serves as the system’s brain, automatically counting ships, analyzing patterns, and generating comprehensive reports that provide valuable insights into port traffic. Enhanced efficiency, accuracy, and community safety According to Mr. Al Fajar Alam, a Port Master at Nizam Zachman Port, the results have been remarkable. “The capability to maintain high performance in all-weather ensures that no ship goes undetected,” he said. The automated ship counting system delivers accurate information that improves everything from fee collection to capacity planning. As a result, port operations became significantly more efficient, with automated systems handling routine monitoring while staff focus on higher-value activities. Benefit from enhanced security and smoother processes For the broader fishing community, these advances mean a safer, more organized port experience “Communication has also been improved dramatically,” Mr. Alam added, “Port staff can now deliver clear messages instantly throughout the harbor. Emergency announcements, docking instructions, and routine communications now flow smoothly through the IP speaker system.” For the broader fishing community, these improvements mean a safer, more organized port experience. Fishing operations benefit from enhanced security and smoother processes, while the entire local maritime economy gains from having a truly modern facility. Maritime tradition meets AIoT The transformation showcases what's possible when maritime tradition meets AIoT. Nizam Zachman Port hasn't just upgraded technology–they've reimagined how a fishing port operates in the modern era. As other ports across Indonesia seek modernization, this project stands as an inspiring example of how AIoT can enhance community-focused maritime facilities while preparing them for future growth.
The Chiba Taxi Association manages over 5,000 taxi vehicles across its eight branches in Chiba Prefecture. Among them, the Keiyo Branch and the Keiyo District Taxi Operations Council have led efforts to install network cameras at key terminal stations for the past 18 years. These systems have supported the monitoring of taxi stand congestion, crime prevention, and emergency response, including the identification of stranded commuters during disasters. Network camera systems Initially, this operation was manually handled by on-site traffic supervisors In response to taxi deregulation by the national government in 2002, large numbers of taxis began flocking to station stands, creating serious congestion. To address this, the association introduced its first “Taxi Satellite System,” which temporarily redirects waiting taxis to offsite parking areas and calls them back via radio when space becomes available at the station. Initially, this operation was manually handled by on-site traffic supervisors, but over time, it transitioned to camera-based monitoring using network camera systems. New monitoring system At the time, deploying network cameras to support such a system was a groundbreaking move in Japan—considered both advanced and innovative. This camera-based approach helped reduce congestion and wait times while also contributing to public safety and convenience. Building on this long-standing commitment to safer and more efficient taxi operations, the association has now introduced a new monitoring system powered by VIVOTEK cameras at JR Maihama Station—a station widely known as the gateway to Tokyo Disney Resort. The goal is to visualize and manage congestion caused by overtourism in the area. Challenges Overcrowding Around a Major Tourist Hub Buses and taxis were unable to access the station due to heavy traffic caused by private vehicles JR Maihama Station serves tens of thousands of passengers daily, many of whom visit Tokyo Disney Resort, located just a five-minute walk away. Adding to the strain, inbound tourism surged in Japan after COVID-19, making evening hours—especially after 8 PM—particularly congested. In some cases, buses and taxis were unable to access the station due to heavy traffic caused by private vehicles. Staff Shortages from an Aging Workforce In the past, supervisors were stationed at major terminals to monitor congestion, maintain order at the rotary, and prevent unauthorized taxi operations—particularly by Tokyo-based taxis operating outside their jurisdiction. However, in recent years, the association has faced increasing challenges due to an aging workforce and a declining pool of available personnel. Solutions Full-Surround Coverage with Fewer Cameras The wide field of view from a single camera helps reduce both installation and maintenance costs VIVOTEK’s fisheye cameras provide seamless 360° coverage, eliminating blind spots and enabling comprehensive monitoring of the taxi stand area with fewer units. This not only enhances situational awareness but also proves valuable during investigations and when sharing footage with law enforcement. The wide field of view from a single camera helps reduce both installation and maintenance costs. Additionally, the camera’s built-in IR illuminator ensures clear video even low-light conditions—an essential feature for round-the-clock taxi operations. Remote Monitoring for Smarter Dispatching Live footage from the cameras is streamed directly to taxi and bus company dispatch centers, enabling remote monitoring of congestion at taxi stands without the need for on-site staff. This has streamlined the dispatching process and helped alleviate overcrowding. By gradually shifting from manual patrols to camera-based monitoring, the association has also mitigated labor shortages while achieving significant improvements in both cost saving and operational efficiency. Benefits The association continues to leverage both new and existing camera systems Camera footage is also shared with local law enforcement. Under a crime prevention agreement with the Urayasu Police Station of the Chiba Prefectural Police, the footage has been utilized for both investigation and deterrence. The association continues to leverage both new and existing camera systems—not only to ease congestion at taxi and bus stands but also to help maintain a peaceful environment and support the creation of a safer society. Results and customer feedback In February 2025, the association began full operation of its new “Taxi Stand Digital Signage & Monitoring System” at JR Maihama Station. As a key component of the system, the association selected VIVOTEK’s FE9382-EHV-V2 fisheye cameras. “Our first encounter with VIVOTEK was at IBS Japan’s booth during the Mass-Trans Innovation Japan exhibition, where we were impressed by the camera’s performance. Since then, we have consistently relied on VIVOTEK cameras for crowd monitoring, digital signage condition monitoring, and taxi stand security,” Mr. Kumagai, Deputy Director, Keiyo Branch, Chiba Taxi Association/Keiyo District Taxi Operations Council.
Iveda®, a pioneer in AI-driven video surveillance and smart-city technologies, announced that Subic Sun Development, Inc. has chosen the IvedaAI™ platform as the video surveillance solution for the soon-to-open Subic Sun Resort, Convention & Casino. IvedaAI was selected early in the build-out to inform camera placement and ensure frictionless integration with future-ready, AI-powered analytics. Focus on safety and service Located on the former U.S. naval base in the Subic Bay Freeport Zone—a special economic hub that hosts thousands of international and local businesses—the resort will feature 500 guest rooms, a state-of-the-art convention center, a luxury casino, and two Accor-brand hotels, Ibis Styles and Mercure, scheduled to open in December 2025. The decision comes as global resort operators sharpen their focus on safety, service, and operational efficiency. The global resort market generated $347 billion in 2024 and is projected to reach nearly $945 billion by 2030, an 18.5% CAGR. IvedaAI’s AI-enabled video analytics IvedaAI’s AI-enabled video analytics will help property staff lower security costs, respond to incidents faster IvedaAI’s AI-enabled video analytics will help property staff lower security costs, respond to incidents faster and unlock data-driven insights that boost both guest satisfaction and bottom-line performance. “Iveda being selected as a premier security and surveillance provider before the first Subic Sun Resort guest ever checks in is a powerful endorsement of our commitment to providing state-of- the-art monitoring technology,” said David Ly, CEO and Founder of Iveda. IvedaAI’s real-time analytics Ly added: “By designing camera layouts around IvedaAI’s real-time analytics, Subic Sun can optimize coverage, reduce blind spots, and deliver safer, smoother guest experiences—without a costly equipment overhaul. We expect more ground-up projects to follow this blueprint.” Iveda Philippines—Iveda’s joint venture focused on nationwide smart-city deployment—secured the Subic Sun contract and will oversee the on-site rollout. The win represents the team’s first major hospitality project and advances its plan to generate US$ 3 million in smart-city revenue by FY 2026, building on the broader initiative it announced last year.
In 1979, nine districts and five cities in Bavaria, Germany, founded a joint association for the disposal of residual waste. They targeted future-oriented, environmentally friendly and economical fulfillment of local statutory obligations. Now with 17 association members, ZMS (Zweckerverband Müllverwertung Schwandorf) disposes waste for around a fifth of Bavaria, almost two million citizens. They also use the energy generated by the waste power plant as efficiently as possible. Different levels of security Devices and other access hardware also need high weather resistance, for deployment outdoors In the past, a mechanical locking system was used on all ZMS properties. The association planned a digital upgrade to boost flexibility over their existing mechanical locking. Their principal site at Schwandorf has areas requiring different levels of security. Devices and other access hardware also need high weather resistance, for deployment outdoors. Managers also considered workflow efficiency. They wanted a way to manage access authorisations more flexibly and align security infrastructure with upcoming IT security laws such as NIS2. Digital Access Solutions from ASSA ABLOY The company chose eCLIQ, part of the suite of Digital Access Solutions from ASSA ABLOY. This innovative, programmable key-based solution now equips not only the power plant and headquarters in Schwandorf, but also buildings across eastern Bavaria, including transfer stations, a waste disposal site, a sorting plant in Bodenwöhr, and a sludge drying plant, as well as all technical and commercial offices, gate control systems and local control points. Because eCLIQ offers a broad range of digital cylinders within its single ecosystem, it suits diverse and complex organizations like ZMS. The benefits of programmable key-based digital access These Wall PDs also make it easy to set limited access time windows for fitters or maintenance contractors The digitally networked eCLIQ system allows access rights and security levels to be defined and assigned flexibly and precisely. A total of 20 Wall Programming Devices (Wall PDs) installed in the head office and branch offices ensure that only authorized employees gain access. These Wall PDs also make it easy to set limited access time windows for fitters or maintenance contractors. If a key is lost, it can be programmed out immediately to prevent misuse. Standard eCLIQ keys “Now we are going with the times and can conveniently enjoy a wide range of advantages,” says Manuel Emerich, Project Manager at ZMS. “As a critical infrastructure company, we can also react very rapidly and flexibly to future requirements.” The solution offers the advantage that a depleted battery does not render a cylinder useless With eCLIQ, each of ZMS’s approximately 1,000 wireless digital cylinders is powered by a battery inside the keyholder’s personalized key. Standard eCLIQ keys have a battery life of 10 years with typical usage. The solution offers the advantage that a depleted battery does not render a cylinder useless. The key is simply fitted with a spare battery, saving time and effort. Future of evolving physical and cyber-security threats Security is a critical concern at municipal and infrastructure sites: every eCLIQ device offers reliable protection against manipulation and intelligent break-in attempts. Keys are robust, with a waterproof casing, and operate reliably in the most challenging environmental conditions. With eCLIQ, ZMS feel ready to face a future of evolving physical and cyber-security threats. “For us, the introduction of digital locking technology and the ability to respond quickly and specifically to security incidents is a decisive step towards a holistic and future-proof system to defend against cyber–physical threats,” adds Manuel Emerich.
The port city of Imperia in north-west Italy has become a popular tourist destination over the years. In order to better secure both the city and the port area, Imperia decided to expand its video surveillance system. At the heart of the system are Dallmeier’s Panomera® multifocal sensor cameras. Imperia is a pretty city in the province of Liguria and is located in the northwest of Italy on the Riviera di Ponente. Originally an industrial town, Imperia has developed over the years into a popular tourist destination, whilst retaining the character of a small fishing village. Picturesquely situated between the sea and the hills, it offers a wide range of leisure activities for both locals and visitors: One can stroll through the small, narrow streets of the town called “carruggi”, relax on the beaches with crystal clear waters or explore one of the many museums in the area. Video technology for critical places There have been repeated incidents of inappropriate behavior, vandalism and crime Like many places, Imperia faces the challenges of being a vibrant and busy city. There have been repeated incidents of inappropriate behavior, vandalism and crime. Particularly critical areas, such as the access area to the marina, required an upgrade of the video security system. “One of the main requirements for the system was to be able to reconstruct events of interest with high reliability and high resolution,” says Daniele Sisinio, Director Dallmeier Italia, explaining the customer’s requirements. Integration into a management system Imperia has been using video surveillance technology for many years. The original system was based on a marina system with numerous cameras from different manufacturers, which were finally integrated into a Dallmeier management system. Later, the marina and city surveillance systems were unified. As a result, not only were additional cameras from other manufacturers integrated into the management system, but a selection of state-of-the-art Dallmeier cameras were also added to the infrastructure. Everything under the eye Dallmeier’s Panomera® multifocal sensor technology is at the heart of the system In addition to numerous single-sensor cameras, Dallmeier’s Panomera® multifocal sensor technology is at the heart of the system. This offers many advantages, especially when monitoring large areas or long distances. The patented Panomera® technology combines several lenses and sensors with different focal lengths in one optical unit. Thus, Panomera® cameras also capture rear and middle image areas with the same high resolution as scenes in the foreground. Benefits of Panomera® technology Not only does this mean that significantly fewer cameras are needed than with conventional technology, which naturally leads to savings in the necessary infrastructure such as cables, masts, etc. The system is also much easier and less complicated to operate: security personnel always have a complete overview of the scene, while at the same time any number of detailed views can be displayed in high resolution. The detail zooms can be opened with a simple mouse click in the overall image, like “virtual” PTZ cameras – both live and in recording. This allows any number of operators to view the footage simultaneously. Additionally, everything is always recorded at the highest resolution. This means that incidents can be traced and reconstructed for use in court, and perpetrators identified, even after the fact. Dependable on-site recording The high reliability of the data recording was extremely important to the security managers at Imperia In addition to the high image quality, the high reliability of the data recording was extremely important to the security managers at Imperia. “By using the very flexible and scalable SeMSy® management system from Dallmeier, we were able to create a client-server architecture that is exactly tailored to our needs. We use IPS 10000 appliances to store images from a large number of cameras,” explains Alessio Meneghello, CEO of High Intelligence. "At the same time, we were able to place compact recording devices on site with the VideoNetBox to ensure local data recording without necessarily relying on radio links.” Strict data protection requirements The city of Imperia attached great importance to secure data management. In accordance with the “Privacy & Security by Design” guideline, products from Dallmeier have the highest level of technical precautions with which customers can easily implement video security solutions that comply with data protection regulations – from setting up “private zones” to sophisticated access concepts and secure authentication procedures in accordance with IEEE 802.1X. The video system also meets all requirements for evidence in court and has been tested for image quality, security against tampering and protection against unauthorized access by LGC Forensics Certification. Smooth operation Dallmeier Italia implemented the project in close cooperation with its certified partner High Intelligence Dallmeier Italia implemented the project in close cooperation with its certified partner High Intelligence. Dallmeier actively supported High Intelligence during the planning phase and on-site demonstrations to ensure that the solution was optimally tailored to the customer’s needs. High Intelligence took care of the complete installation, configuration and calibration of the video surveillance system. With many years of experience in managing high quality video surveillance systems, the company is able to ensure the smooth operation of the system 24/7. This results in an optimization of the security work carried out by the operators and the law enforcement agencies and increases the security of visitors to the city. Reduction of incidents The use of the video surveillance system is showing positive results. “By installing the cameras in several strategic locations, such as the roads and access routes to the marina and the city of Imperia, we have been able to consistently reduce the occurrence of critical incidents”, says a satisfied Dr. Hon. Claudio Scajola, Mayor of Imperia.


Round table discussion
Access control, video surveillance, and intrusion detection systems evolved largely independently in the physical security industry. Integrating those systems to the benefit of an enterprise's overall security has traditionally fallen on security integrators working in cooperation with manufacturers. However, today's market has also evolved to include companies that provide "unified platforms,” bringing together various disparate security systems and functions under a single, centralized management interface. We asked our Expert Panel Roundtable: What are the advantages of installing physical security systems as a unified platform?
The role of audio in physical security is multifaceted and increasingly vital, offering a layer of intelligence and interaction that access control and/or video surveillance alone cannot provide. Sounds provide crucial context to visual events. For instance, someone running might appear suspicious on video, but audio could reveal they are shouting for help, changing the interpretation entirely. Even so, historically speaking, audio has been an underused component in physical security. How is the situation changing? We asked our Expert Panel Roundtable: Is audio an underused component in today’s physical security systems? What obstacles are keeping audio from expanding?
A software platform designed to centralize and manage various physical security systems within an organization used to be called a PSIM (physical security information management) system. Generally speaking, however, the PSIM term has fallen out of favor because the systems were seen as expensive and difficult to manage. The phrase has been replaced by command-and-control, referring to software that combines access control, video surveillance, intrusion detection, and other systems into a unified platform. It’s a ripe area for innovation in the physical security space. We asked this week’s Expert Panel Roundtable: What’s new in command-and-control systems, and what is the impact?
Products


White papers

Combining Security And Networking Technologies For A Unified Solution
Download
Selecting The Right Network Video Recorder (NVR) For Any Vertical Market
Download
Improving City Mobility Using Connected Video Technology
Download
Video Technology: Making Cities Safer & Improving Lives
Download
Protecting Dormitory Residents and Assets
Download
Choosing the Right Storage Technology for Video Surveillance
Download
Video Surveillance As A Service: Why Are Video Management Systems Migrating to the Cloud?
Download
11 Reasons Video Surveillance Is Moving To The Cloud
Download
The Borderless Control Room
Download
Wireless Access Control eBook
Download
Six Things To Look For When Adding AI Cameras To Your Operation
Download
The Inevitability of The Cloud
Download
Security Investments Retailers Should Consider For Their 2021 Budget
Download
Enhanced Ethernet Technology (ePoE)
Download
IP In A Box: The Advantages Of Embedded Network Video Recorders
Download

Videos
Network Video Recorders: Manufacturers & Suppliers
- Hikvision Network Video Recorders
- Dahua Technology Network Video Recorders
- exacqVision Network Video Recorders
- ADPRO Network Video Recorders
- Vicon Network Video Recorders
- Hanwha Vision Network Video Recorders
- Axis Communications Network Video Recorders
- Avigilon Network Video Recorders
- Milesight Network Video Recorders
- LILIN Network Video Recorders
- IDIS Network Video Recorders
- MOBOTIX Network Video Recorders
- Verkada Network Video Recorders
- Illustra Network Video Recorders
- Bosch Network Video Recorders
- FLIR Systems Network Video Recorders
- AV Costar Network Video Recorders
- Milestone Network Video Recorders
- BCDVideo Network Video Recorders
- Speco Technologies Network Video Recorders