Security devices
Pioneer wireless fire safety solutions provider Ramtech has established its first international base, opening a new U.S. office in Charlotte, North Carolina. The move reinforces the company’s commitment to delivering modern fire and safety across the construction industry and establishing a full U.S. supply chain. By establishing a permanent presence on the Atlantic coast, Ramtech, which is headquartered in Nottingham, will enhance efficiency, mobilization and reliable delivery of safety...
Iris officially launches today, introducing a platform that transforms how cameras are controlled, and productions are managed. By turning virtually any PTZ camera into a software-connected, remotely controlled device, Iris eliminates the traditional constraints of camera operation, such as hardware dependencies, inconsistent control, and the lack of on-site crews. The platform removes long-standing pain points for production teams: fragmented control tools and protocols across brands, the need...
Verkada, a pioneer in AI-powered physical security technology, announced CapitalG is pioneering an investment at a $5.8 billion valuation - an increase of $1.3 billion since the announcement of its Series E in February. The investment will accelerate Verkada's AI capabilities and may also enable liquidity for employees, and comes as the company surpasses $1 billion in annualized bookings. AI-powered transformation "AI is fundamentally transforming how organizations protect people and places,...
Matrix, a pioneer in Security and Telecom solutions, proudly announces its prestigious recognition at the CII Design Excellence Awards 2025. This honor reinforces Matrix’s commitment to innovation-driven design and its mission to solve complex global challenges through advanced technology. The CII Design Excellence Awards celebrate outstanding contributions to design excellence across industries, recognizing organizations that blend creativity, engineering, and user-centric innovation. M...
Artificial Intelligence Technology Solutions, Inc., a pioneer in AI-driven security and productivity solutions, along with its wholly owned subsidiaries, Robotic Assistance Devices, Inc. (RAD), and Robotic Assistance Devices Group (RAD-G), announced that CEO/CTO and founder Steve Reinharz will present at ISC East in New York City Wednesday afternoon on the rise of agentic AI in real time security. His session will feature SARA™ (Speaking Autonomous Responsive Agent), the Company...
barox Kommunikation AG, will be showcasing the power of their video security networking solutions and game-changing diagnostic tools, at the world famous Etihad Stadium in Manchester, as part of Commend UK’s ‘The Innovation Tour 2025’. Designed for end users, consultants and integrators in all security sectors, ‘The Innovation Tour 2025’ takes place on 12th November, between 10:00am and 4:00pm. Visitors to the event can drop in at any time to see the latest develop...
News
Artificial Intelligence Technology Solutions, Inc., a pioneer in AI-driven security and productivity solutions, along with its wholly owned subsidiary, Robotic Assistance Devices, Inc. (RAD), announced that sales activity through the first two months of the Company’s third fiscal quarter continues to strengthen. RAD has secured dozens of new device orders, including ROSA™, RIO™, ROAMEO™, alongside multiple software license agreements, including SARA™, RAD’s agentic AI-driven autonomous response platform, and several new dealer partnerships. This growing momentum positions the Company for a strong finish to the quarter and reinforces its role as a driving force in the adoption of AI-powered security technologies across multiple sectors. RAD’s integrated AI and robotic solutions Through November 4, 2025, RAD has contracted orders for 64 devices, including eight proof-of-concept deployments, and 46 software licenses spanning SARA, RADGuard™, and Firearm Detection. The Company has also expanded its sales reach with six new authorized dealers and two independent channel partner contractors added to its growing network. These results reflect consistent execution across both product and channel development, as demand for RAD’s integrated AI and robotic solutions continues to accelerate across key markets. RAD’s performance “We’re hitting a strong stride as we move deeper into the second half of the fiscal year,” said Steve Reinharz, CEO/CTO and founder of AITX and RAD. “The market continues to respond to the performance, reliability, and economics of our solutions. Every week we see greater acceptance from new clients, dealers, and enterprise partners who recognize that RAD’s technology is not just innovative, it’s essential. We’re executing with focus and speed for our clients, channel partners and shareholders.” RAD’s performance this quarter reflects balanced growth across its stationary, mobile, and software platforms. The Company’s dealer and independent contractor network is also broadening RAD’s reach into new territories, including Latin America and the United Kingdom, fueling additional pipeline activity and accelerating the path to recurring monthly revenue growth and operational cash flow positivity. Stationary and mobile robotic solutions “As strong as this quarter has been so far, we’re nowhere near done,” added Reinharz. “There are new technologies, partnerships, and market entries coming that will further expand our reach and impact. The team is executing with purpose and intensity, and I’m confident that the results we deliver in the months ahead will speak volumes about what’s next for AITX and RAD.” AITX, through its primary subsidiary, Robotic Assistance Devices, Inc. (RAD), is redefining the nearly $50 billion (US) security and guarding services industry through its broad lineup of innovative, AI-driven Solutions-as-a-Service business model. RAD solutions are specifically designed to provide cost savings to businesses of between 35%-80% when compared to the industry’s existing and costly manned security guarding and monitoring model. RAD delivers these cost savings via a suite of stationary and mobile robotic solutions that complement, and at times, directly replace the need for human personnel in environments better suited for machines. All RAD technologies, AI-based analytics and software platforms are developed in-house. Data protection and security compliance The Company’s operations and internal controls have been validated through the successful completion of its SOC 2 Type 2 audit, which is a formal, independent audit that evaluates a service organization’s internal controls for handling customer data and determines if the controls are not only designed properly but also operating effectively to protect customer data. This audit reinforces the Company’s credibility with enterprise and government clients who require strict data protection and security compliance. RAD is led by Steve Reinharz, CEO/CTO and founder of AITX and RAD, who brings decades of experience in the security services industry. Reinharz serves as chair of the Security Industry Association’s (SIA) Autonomous Solutions Working Group and as a member of the SIA Board of Directors. The RAD team also draws on extensive expertise across the sector, including Mark Folmer, CPP, PSP, President of RAD and Chair of the ASIS International North American Regional Board of Directors, Troy McCanna, former FBI Special Agent and RAD’s Chief Security Officer, and Stacy Stephens, co-founder of security robotics company Knightscope. Their combined backgrounds in security industry leadership, law enforcement, and robotics innovation reinforce RAD’s ability to deliver proven, practical, and disruptive solutions to its clients. Delivery of artificial intelligence-based solutions RAD has a prospective sales pipeline of over 35 Fortune 500 companies and numerous other client opportunities. RAD expects to continue to attract new business as it converts its existing sales opportunities into deployed clients generating a recurring revenue stream. Each Fortune 500 client has the potential of making numerous reorders over time. AITX is an innovator in the delivery of artificial intelligence-based solutions that empower organizations to gain new insight, solve complex challenges and fuel new business ideas. Through its next-generation robotic product offerings, AITX’s RAD, RAD-R, RAD-M and RAD-G companies help organizations streamline operations, increase ROI, and strengthen business. AITX technology improves the simplicity and economics of patrolling and guard services and allows experienced personnel to focus on more strategic tasks. Customers augment the capabilities of existing staff and gain higher levels of situational awareness, all at drastically reduced cost. AITX solutions are well suited for use in multiple industries such as enterprises, government, transportation, critical infrastructure, education, and healthcare.
ASSA ABLOY Opening Solutions will be returning to GlassBuild America, the largest annual trade show in North America for the glass, window, and door industries. Happening November 4-6 at the Orange County Convention Center in Orlando, Florida, GlassBuild America is where buyers and sellers meet and learn how to solve their most pressing challenges. The action-packed event features networking between exhibitors and attendees, and experiencing new technology and products. ASSA ABLOY Opening Solutions will showcase its latest innovations in comprehensive door security and digital access control at booth #15007, which is conveniently located near the front entrances. Innovation in the glass industry “The show provides an excellent opportunity to showcase the creativity and innovation happening in the glass industry,” stated Tyler Baker, Director of Business Development for Glass and Aluminum at ASSA ABLOY Opening Solutions Americas. “It’s always exciting to engage with designers and partners who share our passion for blending aesthetics, performance, and security in modern architectural solutions.” Range of door security solutions ASSA ABLOY continuously expands its range of door security solutions and innovates to improve security, safety, energy efficiency, and convenience. The company focuses on creating designs that integrate aesthetically pleasing elements into the spaces they enhance. The solution lineup at GlassBuild 2025 includes: Rockwood PDU8000 Panic Device The device’s engraved push area and boundary grooves make exit doors stand out in a crowd. Now ANSI/BHMA A156.44, Grade 1 certified, this durable product offers keyed and non-keyed functions, new bent end return and two-piece configuration options, and a selection of finishes, providing a customizable design. Available to pair with manual or electric strikes, this line provides beauty, security, and peace of mind. Bruken DL-GS3550 Digital Glass Door Lock Provide keyless access control to your all-glass interior openings with the Bruken DL-GS3550 Digital Lock from ASSA ABLOY Glass Solutions. This field-reversible device is ideal for retrofit applications and features three modes of access, including fingerprint identification, numeric passcode, and smart card. This multi-user lock requires no glass fabrication for easy installation and is compatible with single or pairs of glass doors that are 3/8" - 1/2" thick. Control iD iDFace Max With its modern design and elegant finish, iDFace Max is the ideal device for monitoring and controlling venue access through facial identification technology. Its advanced algorithm and high-quality cameras allow the identification of up to 100,000 faces (1:N) with face liveness detection and identification of users with and without a mask. iDFace Max has an integrated SIP intercom with TCP/IP, USB, and PoE connectivity. The device also features a large 7-inch LCD touchscreen display, allowing for easy and intuitive navigation to configure access rules and view reports. ASSA ABLOY ACCENTRA nexTouch Cylindrical Lockset Combines a sleek, modern design with advanced access control technology, delivering a stylish yet secure solution for a wide range of facilities. With a heavy-duty construction and ANSI/BHMA Grade 1 certification, nexTouch ensures durable and dependable performance. This standalone electronic lock features modular technology, allowing seamless upgrades to Data-on-Card functionality. Available with either a capacitive touchscreen or pushbutton keypad, nexTouch® provides an ADA-compliant, user-friendly system engineered to safeguard your facility and personnel. Rockwood OptiCoat Finishes Offering realistic wood and marble patterns for door hardware of all kinds, OptiCoat is ideal for elevating projects where every detail matters, including upscale hotels, offices, and multi-family spaces. With 13 readily available finish options, plus custom capabilities, matching opening hardware to the overall style of your facility has never been easier. Centrios Centrios allows small businesses to manage access to their business by connecting their Centrios locks and smart readers with a simple-to-use mobile app. With Centrios, it’s simple to unlock doors with a touch of a phone, manage access for all employees and visitors in one place, and view audit and event reports. ASSA ABLOY is committed to expanding its solution lineup, along with adding top-of-the-line products to its quick shipping programs. ASSA ABLOY experts are here to listen and ensure that they are meeting the industry's needs. Please stop by the booth to meet with experts from ASSA ABLOY Glass Solutions and Rockwood.
Integrated access control and security manufacturer - TDSi has announced the release of GARDiS Pro Version 3.1, the latest enhanced iteration of its GARDiS Access Control Management Software. GARDiS 3.1 introduces expanded biometric support and intelligent credential management, delivering improved hardware reporting capabilities and new third-party integration options to further enhance system performance and flexibility. Latest update for GARDiS Pro Tina Baker, Software Development Manager at TDSi commented, "We are excited to announce this latest update for GARDiS Pro which delivers practical and meaningful upgrades that enhance both day-to-day operations and long-term scalability. Whether you're securing a single site or managing complex, multi-layered environments, GARDiS Pro v3.1 provides the tools to do it more efficiently and confidently than ever." Key enhancements in GARDiS Pro Version 3.1 The latest update to TDSi’s GARDiS Pro Software introduces a range of new features designed to enhance security, performance, and user experience. Version 3.1 adds support for the Digitouch Biometric Reader, enabling fast and cost-effective fingerprint authentication, and introduces automatic credential status updates to strengthen access control management. Administrators also benefit from customizable event log retention, improving compliance and system performance. Duress PIN alert function New third-party integration with Nettla allows facility bookings to automatically trigger secure, time-limited access permissions, while updates such as accented character support, enhanced expander and door status reporting, and lift button press logging further improve system flexibility and monitoring precision. Additional refinements include a new Duress PIN alert function for discreet security responses and multiple backend performance enhancements that deliver greater stability and responsiveness across the platform. Latest version of TDSi’s GARDiS Pro Software The latest version of TDSi’s GARDiS Pro Software builds upon the release of Version 3 earlier this year, which introduced a wide range of new features and enhancements including intuitive access control tools, advanced reporting, streamlined setup processes, a simplified licensing workflow, new multi-factor authentication options, and improved data import and user interface refinements. GARDiS Pro Version 3.1 is available now and can be downloaded from the TDSi Product Registration site. TDSi installers and customers are encouraged to upgrade to Version 3.1 to take full advantage of the latest features and performance improvements.
i-PRO Co., Ltd. (formerly Panasonic Security), a pioneer in professional security, public safety and medical applications, announced that it has signed an agreement with Panasonic Connect Co., Ltd. to take over the wholesale and marketing functions for i-PRO products in the Japanese market, which are currently managed by Panasonic Connect. The transition is scheduled to be completed on March 31, 2026, following the necessary regulatory approvals. Advanced security products Since becoming independent from Panasonic in 2019 through a capital partnership with Polaris Capital Group Co., Ltd., i-PRO has focused on developing and manufacturing advanced security products, while sales in the Japanese market have been conducted through Panasonic Connect. At the same time, they have also made efforts to develop the own sales channels. By taking over the wholesale and marketing functions for the products from Panasonic Connect, i-PRO will strengthen its sales structure in the Japanese market and integrate development, manufacturing, and sales into a unified organization. This integration will enhance responsiveness to market needs, improve operational efficiency, and reinforce competitiveness in the Japanese market. This approach aligns with the regionally integrated management model that i-PRO has been implementing globally since 2019. Expected synergies Expected synergies include the following: Promote collaboration among manufacturing, product development, and sales to swiftly reflect market needs in products. Accelerate the deployment of global solutions in the Japanese market by promoting personnel exchanges with overseas offices. Enhance customer value and strengthen competitiveness through a more efficient and integrated value chain. Improve the quality of sales, proposals, and after-sales service. Increase operational speed by simplifying business processes. i-PRO products via Panasonic Connect As of April 1, 2026, approximately 500 dealers who currently procure i-PRO products via Panasonic Connect will begin conducting business directly with i-PRO. Contracts with end-users purchasing through Panasonic Connect or Electric Works Company (Panasonic Corporation) will remain unchanged. i-PRO will continue to build long-term relationships with customers and deliver reliable, high-quality products and solutions that contribute to a safer and more secure society.
Artificial Intelligence Technology Solutions, Inc., a pioneer in AI-driven security and productivity solutions, now announced that its wholly owned subsidiary, Robotic Assistance Devices, Inc. (RAD), recorded one of the strongest single-day order intakes in Company history. The day’s results included 23 hardware units and 17 software licenses across four unique clients in the construction, banking, healthcare, and logistics sectors. Diversity of RAD’s customer base On October 16, 2025, RAD received orders totaling 16 RIO™ Mini units and SARA™ software licenses from a major construction client, one Firearm Detection (FAD) license from a Community Improvement District, three ROSA™ devices from a banking client, two ROSAs from a healthcare facility, and two TOM units from a pioneering logistics provider. These orders underscore the diversity of RAD’s customer base and the accelerating demand for its AI-driven security and productivity solutions across multiple industries. Adoption of RIO Mini units This surge follows a series of strong sales months as RAD continues to accelerate deployment of its AI-powered security technologies. The Company recently reported record-setting quarters, rapid adoption of RIO Mini units across the construction industry, and growing demand for SARA software licenses among monitoring centers and enterprise clients. “We’re seeing the cracks widen in the dam holding back adoption,” said Steve Reinharz, CEO/CTO and founder of AITX and RAD. “Opportunities are flowing faster every week as organizations recognize the performance and economic advantages of our solutions. This near-record day shows just how much pent-up demand exists across multiple industries. We’re executing aggressively to meet it for our clients, channel partners and shareholders.” SOC 2 Type 2 audit AITX, through its primary subsidiary, Robotic Assistance Devices, Inc. (RAD), is redefining the nearly $50 billion (US) security and guarding services industry through its broad lineup of innovative, AI-driven Solutions-as-a-Service business model. RAD solutions are specifically designed to provide cost savings to businesses of between 35%-80% when compared to the industry’s existing and costly manned security guarding and monitoring model. RAD delivers these cost savings via a suite of stationary and mobile robotic solutions that complement, and at times, directly replace the need for human personnel in environments better suited for machines. All RAD technologies, AI-based analytics and software platforms are developed in-house. The Company’s operations and internal controls have been validated through successful completion of its SOC 2 Type 2 audit, which is a formal, independent audit that evaluates a service organization’s internal controls for handling customer data and determines if the controls are not only designed properly but also operating effectively to protect customer data. This audit reinforces the Company’s credibility with enterprise and government clients who require strict data protection and security compliance. Backgrounds in security industry leadership RAD is led by Steve Reinharz, CEO/CTO and founder of AITX and RAD, who brings decades of experience in the security services industry. Reinharz serves as chair of the Security Industry Association’s (SIA) Autonomous Solutions Working Group and as a member of the SIA Board of Directors. The RAD team also draws on extensive expertise across the sector, including Mark Folmer, CPP, PSP, President of RAD and Chair of the ASIS International North American Regional Board of Directors, Troy McCanna, former FBI Special Agent and RAD’s Chief Security Officer, and Stacy Stephens, co-founder of security robotics company Knightscope. Their combined backgrounds in security industry leadership, law enforcement, and robotics innovation reinforce RAD’s ability to deliver proven, practical, and disruptive solutions to its clients. Delivery of artificial intelligence-based solutions RAD has a prospective sales pipeline of over 35 Fortune 500 companies and numerous other client opportunities. RAD expects to continue to attract new business as it converts its existing sales opportunities into deployed clients generating a recurring revenue stream. Each Fortune 500 client has the potential of making numerous reorders over time. AITX is an innovator in the delivery of artificial intelligence-based solutions that empower organizations to gain new insight, solve complex challenges and fuel new business ideas. Through its next-generation robotic product offerings, AITX’s RAD, RAD-R, RAD-M and RAD-G companies help organizations streamline operations, increase ROI, and strengthen business. AITX technology improves the simplicity and economics of patrolling and guard services and allows experienced personnel to focus on more strategic tasks. Customers augment the capabilities of existing staff and gain higher levels of situational awareness, all at drastically reduced cost. AITX solutions are well-suited for use in multiple industries such as enterprises, government, transportation, critical infrastructure, education, and healthcare.
In the ongoing implementation of the EU’s NIS2 Directive, much attention has been paid to its implications for cybersecurity. Yet, arguably, the impact on organizations’ physical security and access strategy is just as important. In fact, NIS2 ushers in a new degree of focus on cyber–physical resilience – with significant potential penalties for organizations which do not comply with the framework’s demands. NIS2 replaces 2016’s original NIS Directive on Network and Information Security. It represents a major legislative tightening of the minimum requirements for IT security in critical infrastructure and expands them to include several new sectors. The European Commission estimates that around 160,000 organizations will be impacted by NIS2 right away. Important change for security The most important change for security and facilities managers to digest is the switch to an “all-hazards approach” to regulation. In practice, this approach compels impacted organizations to reinforce their digital security measures with additional processes and devices which physically protect the security of their digital infrastructure. Thus, cyber–physical resilience – and increased convergence between the operations and goals of cyber and physical security teams – becomes a key element in the response to a increase in both the volume and the sophistication of hybrid cyber–physical attacks. NIS2 and physical security: scope, compliance, financial penalties The potential scope of NIS2 regulations encompasses a much-expanded range of organizations and sectors. Alongside the typical infrastructure sub-sectors such as energy and utilities, transport, telecoms, waste management, data centers and the like, is added a broader understanding of what constitutes “critical” national infrastructure: healthcare (including research), digital services and a range of manufacturing businesses including food, chemicals, automotive and more. Organizations which operate in any of these sectors should consult the directive to ascertain whether they, too, face NIS2 obligations. A significant element of the new obligations is the extended all-hazards approach, referenced above. According to Article 21 of the directive, entities must “take appropriate and proportionate technical, operational, and organizational measures to manage the risks to the security of network and information systems [...] and to prevent or minimize the impact of security incidents on the recipients of their services and on other services.” Physical access to digital infrastructure In other words, any areas of a site where malicious actors may gain physical access to digital infrastructure, whether IoT devices, access management terminals, servers or anything else, must now have appropriate protection against digital, physical and hybrid attack. Access control devices and protocols must be up to this task. Potential punishments for non-compliance with NIS2 can be severe. According to the directive’s text, organizations may face fines of up to €10 million, or 2% of their global annual turnover. Older locking systems therefore represent a major liability risk for many organizations. NIS2 impact on access control workflows Thus, NIS2’s implications for security and facilities management – and potential financial penalties for organizations – are significant. The all-hazards approach is especially important here. Measures to implement and monitor “all-hazards” compliant processes include the fine-tuning of risk analysis for on-site digital devices; supply-chain security measures including safer procurement and data handling; physical access for personnel, including employees and visitors; cyber-hygiene training; planning for business continuity in the event of a breach; and more. Security teams should urgently evaluate their existing cyber–physical resilience to quickly identify areas where additional measures or upgrades are needed. NIS2 compliance efforts Access management is a key element in any impacted organization’s NIS2 compliance efforts. Intelligent access solutions can contribute to improving cyber–physical resilience with, for example, enhanced identity management, auditability, and round-the-clock remote building control. Credentials which require regular revalidation and/or expire automatically drastically reduce the risk of unauthorized keys in circulation – another potential vulnerability for digital infrastructure. Digital access solutions from ASSA ABLOY empower them to secure every layer and can contribute significantly to achieving compliance with the NIS2 Directive. They help protect organizations and data by enabling control over who goes where and when for each user, with the ability to cancel lost credentials instantly. They support both online and offline access control, improving workflows through flexible management—whether remotely or on-site. ASSA ABLOY specific features and benefits The offering includes digital access systems or access hardware to upgrade existing setups, providing scalable control over access points that were previously unreachable and securing protection classes 1 to 4. Wireless solutions are simple to install and require no wiring or structural modifications. Physical access is often considered one of the biggest backdoors for cyber criminals in an era of growing hybrid attacks. Closing it with digital access enhancements will ensure NIS2 obligations are met – and free security decision-makers from compliance worries. ASSA ABLOY experts are available to guide them through the specific features and benefits that align with the directive’s requirements and enhance the organization’s cyber–physical security framework.


Expert commentary
The healthcare infrastructure is ever evolving. Facilities are no longer single entities for one, they are sprawling ecosystems that serve a wide range of users, from medical staff and administrators to vulnerable patients, visitors and maintenance personnel. Safeguarding their safety and security, while providing seamless operation is a complex challenge - one frequently solved by access control. Use of access control Today’s security solutions play a central role in protecting people and mitigating risk across much of our built environment. An appropriately specified system is effective at regulating, monitoring and restricting entry and exits, and allows users to navigate an integrated network and its hardware to ensure the right access is provided to the right person at the right time. In healthcare buildings, the use of access control expands further, whereby a system can tackle a host of unique operational challenges - significantly contributing to fire safety, ease of movement and the theft prevention of equipment, medicine and sensitive patient data, and all while protecting human life and preserving privacy and dignity. In healthcare buildings, the use of access control expands. In doing so, access control can become the cornerstone of functionality, compliance and organization in any healthcare environment. Though, as the complexity of projects deepen, decision makers are reminded that coordination is key. Preparing and empowering users Between January and March 2025, there were over 832,000 patient safety events recorded in the NHS. While each of these events may not be directly linked to building security specifically, the healthcare industry is faced with a considerable number of safety incidents, which suggests greater monitoring and mitigation is needed across the board. Access control often provides staff with the vital means of retaining control without impeding care Patient well-being and security will always remain paramount in the sector, and access control often provides staff with the necessary means of retaining control without impeding care. Hospitals for example, sustain a high level of footfall across large campuses with multiple points of entry and on-site patient record systems, presenting a number of simultaneous security tests as a result. Though, unlike other public buildings, where rigid security measures are active at all times, many healthcare environments must strike a balance throughout their security framework to meet a host of one-of-a-kind demands. Use of access credentials With a continuous influx of patients, staff and visitors, healthcare groups are habitually required to remain accessible and inviting around the clock. At the same time, they must also be prepared to deter unwanted visitors in areas of restricted access and lock down intensive wards to ensure patients remain safe and secure under periods of monitoring. For this, the use of access credentials is critical and provides a regulated system for sensitive staff-controlled areas such as pharmacies, wards, and server rooms. By applying role, zone, or schedule-based access, decision makers can authorize personnel seamlessly, empowering facilities to manage patient care without compromising security in the process. Use of access credentials is critical and provides a regulated system for staff. Implementation of AI-powered tools and devices Modern systems may incorporate the use of keycards, biometric scanners, and mobile credentials When it comes to the operation of these systems, training gaps are a concern, however. Over the five years up to February 2025, numbers of NHS doctors rose by 26%, with nurses also up 25%, and this influx of new staff requires education towards the usage of access control. Modern systems may incorporate the use of keycards, biometric scanners, mobile credentials and in some cases, voice-activation, with the implementation of AI-powered tools and devices set to play a more prevalent role in the future. Each system presents its own benefits and may be better suited to certain projects and areas, but without consultation and proper user education, they can instead become a barrier. Strategy, scalability, performance To alleviate these operational threats, early-stage planning is fundamental. Just as end-user education and training should be built into project timelines, it’s important to consider the growing need for cooperation throughout the entire supply chain of an access control project. A collaborative approach becomes even more critical when innovative solutions enter the market All too often, a lack of evidence-based decision making can hinder the specification of a scheme and its accompanying hardware, whereby choices are made without understanding long-term performance or compliance requirements. Whether approaching a new or retrofit development, ongoing communication allows experts to come together and ensure that product decisions are aligned with the buildings intended use and user base. This collaborative approach becomes even more critical when innovative solutions enter the market and new sector challenges arise. Latest access control products With this in mind, trusted manufacturers will no longer simply deliver the latest access control products, but will aim to work alongside the architects, specifiers, contractors, and facility managers at each stage of the building’s lifecycle to ensure touchpoints are addressed. This is crucial in modern healthcare environments, where the added layer of complexity requires tailored security measures. One area that is often neglected is scalability, for example. As healthcare facilities manage fluctuating patient numbers and a growing level of patient data, along with new regulations, systems must be adaptable and allow for ongoing improvements and updates to the security infrastructure without the need for a complete overhaul. By adopting a scalable system that combines technology integration with ease of use, decision makers can future-proof their building’s security. Manufacturers will no longer simply deliver the latest access control products Complexity of the healthcare industry In truth, access control has become more than a means of restricting access. Modern systems are more equipped than ever before to deliver environments that support care, safety, and operational excellence. Nonetheless, the complexity of the healthcare industry and its buildings demands more than product innovation - it requires an industry-wide commitment to collaboration, from project conception to product installation and beyond.
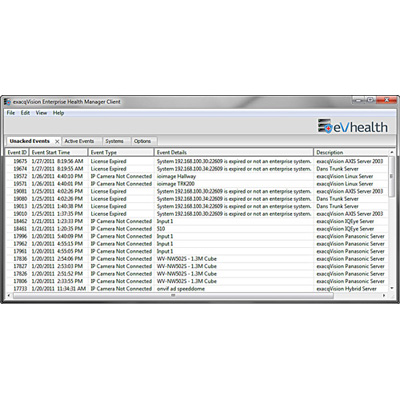
In today’s world, almost any electronic security system holds the potential to become a gateway for cybercriminals. With physical security and cybersecurity increasingly entwined, security professionals aren’t doing their job unless they take all possible precautions to lock down unauthorized access to camera systems, access control platforms, intercoms, and other network-based security devices and solutions. Let’s explore the many steps companies should take throughout their security technologies’ lifecycle – from choosing a vendor all the way through device decommissioning – to avoid making the common mistakes that leave systems, and the networks they reside on, vulnerable to attack and sabotage. Prepurchase Phase: Laying the Groundwork for Cybersecurity 1. Conduct a Vendor Risk Assessment IT departments often rely on the same Vendor Risk Assessment criteria they use for evaluating IT equipment manufacturers when considering the suitability of physical security vendors. While commonalities exist between how to assess these disparate solutions, there are also differences that require distinct scrutiny. For example, device endpoints within physical security systems run on custom Linux Kernels and therefore do not utilize standard Linux distributions like Red Hat, Ubuntu, or Debian. IT divisions often rely on the same Vendor Risk Assessment criteria they use for evaluating IT kit A comprehensive evaluation should examine how each security solutions manufacturer handles its software development life cycles. Ideally, vendors should adhere to a recognized framework when developing both their platform management and device-specific software. In 2021, Executive Order 14028 made it a bit easier for companies to evaluate vendors by providing guidelines for evaluating software security, the practices of the software developer, and methods to demonstrate conformance with secure practices, specifically referencing the NIST SP 800-218 Secure Software Development Framework. In short, a good vendor should have documentation that explains everything it’s doing to address cybersecurity from development, through releases and ongoing maintenance. 2. Obtain Software Update Schedules The frequency with which manufacturers update their software varies. Each company is different. If you’re their customer, it shouldn't matter whether the vendor schedules updates every six months, three months, or more often than that. What does matter is that you know what to expect and have a plan for how to deal with that reality. For example, if updates only occur every six months, under what conditions are patches released to address vulnerabilities that emerge between updates? Customers must understand how often they'll be updating the software on their devices and ensure they have the resources to make it happen. Make sure stakeholders agree, upfront, who will be performing the software updates. Will it be the integrator who installed the system, the physical security system staff, the IT team, or the end user? Keeping an entire system current is a huge challenge, but a non-negotiable responsibility. Manufacturers who don't issue frequent releases and patches put the onus on customers to handle mitigation efforts on their own. In these instances, IT departments must be prepared to employ network segmentation, firewalls, security whitelists/blacklists, and other methods to protect their systems until a patch is released. If a company's security team has typically updated firmware only when something breaks, these additional responsibilities most likely require greater collaboration with IT departments and a shift in how security systems are managed. 3. Know the Warranty Terms and Duration of Software Support Organizations should understand the warranty policies for the devices they purchase Organizations should understand the warranty policies for the devices they purchase. Even more important is knowing when a device's software support will expire. Software support should extend well beyond hardware coverage. For example, if a camera has a five-year hardware warranty, customers should reasonably expect an additional five years of software support. When that period ends, companies must plan on replacing the device – even if it still works well. Without software updates, the device lacks vulnerability support and becomes too risky to remain on the network. Manufacturers should be transparent about their warranty and software support policies, helping organizations plan for device replacements that align with cybersecurity needs. 4. Request a Software Bill of Materials (SBOM) During the pre-discovery process, customers should request a Software Bill of Materials (SBOM) that provides a detailed inventory of the software running on each device, including open-source components. By revealing what software is "under the hood," the SBOM allows IT departments to be vigilant in protecting the company's systems from exposed vulnerabilities. For example, a customer should understand how Transport Layer Security (TLS) is being handled to secure a security solution's web server if it’s an open-source component like OpenSSL. 5. Assess Vulnerability Disclosure Practices CNA manufacturers represent the gold standard in cybersecurity practices Understanding how a manufacturer handles vulnerabilities is essential. Ideally, they should be a Certified Naming Authority (CAN) and report common vulnerabilities and exposures (CVEs) to national vulnerability databases such as NIST and MITRE. Doing so automatically includes any disclosed vulnerabilities associated with their devices in vulnerability scanners' databases. CNA manufacturers represent the gold standard in cybersecurity practices, but most security manufacturers do not reach this level. At a minimum, the vendors you choose to work with should have an email notification system in place to alert customers to new vulnerabilities. Remember – email notifications are only as reliable as the employees managing them, so investigate whether the manufacturer has a strong track record of keeping up with such communications. Ask to speak with customer references who have been using the solution for an extended period to ensure the vendor is diligent in its communications. Configuration Phase: Ensuring a Secure Setup 1. Use Hardening Guides Once a device is purchased, configuring it securely is the next critical step. Manufacturers should publish hardening guides that detail the security controls available for their products and recommended practices for implementation. Between the features offered by the vendor and your company's own cybersecurity policies, make sure all possible encryption options are activated. Using HTTPS is vital for ensuring secure communication with devices. Many physical security devices default to HTTP to accommodate customer-specific network topologies and certificate management. Failing to implement HTTPS can leave sensitive metadata unencrypted and vulnerable to interception. 2. Consider Advanced Encryption Protocols Protocols are necessary to protect video data in transit from cameras to the VMS Some solutions offer built-in encryption protocols, like MACsec, which makes it impossible for data to be compromised as it is transmitted over the network. HTTPS is still necessary to secure the connection to the devices’ webservice, but while customers set up and configure their devices, MACsec will keep network data safe. Additionally, if you want to encrypt video streams, consider protocols such as Secure Real-Time Transport Protocol (SRTP), which secures the transmission of audio and video data over the Internet, or tunneling methods like Secure Socket Tunneling Protocol (SSTP), which encapsulate data packets for safe transmission between two points, even if the network is insecure. Such protocols are necessary to protect video data in transit from cameras to the Video Management System (VMS). Encryption should also extend to the VMS hard drive where video is stored. There are different methodologies to do that, but ultimately the goal is to encrypt data in transit and in storage. 3. Implement Remote Syslog In the case of a breach, each device maintains a set of logs that are useful for forensic investigations. However, if a device gets hacked, its log may not be accessible. Best practices dictate that companies should set up a remote Syslog server that maintains a copy of all device logs within a central repository. In addition to providing redundant data for investigations, a Syslog offers IT systems an efficient way to look for anomalies. Cybersecurity teams will receive immediate notification for events like unsuccessful login attempts so they can quickly figure out what's happening. Who is trying to log in? Why on that particular device? 4. Practice Healthy Password Hygiene Ideally, organizations should move towards using Active Directory or Single Sign-On (SSO) solutions One of the most basic and yet overlooked aspects of cybersecurity is the failure to manage user accounts meticulously. Many organizations use the same username and password for all security devices because it's simply too cumbersome to manage a network of devices in which each requires a separate, unique login. It's assumed that the system's primary administrators are the only ones who know the universal password. However, the system becomes vulnerable if anyone within this select group leaves the company and the password isn't changed or deleted right away. Ideally, organizations should move towards using Active Directory or Single Sign-On (SSO) solutions. This approach ensures that employees throughout a company are each assigned a unique login credential that they use for any systems they use throughout the organization. When they leave, their passwords and access are universally terminated along with their accounts. If SSO is not an option, regular password changes and prompt account deactivation are critical. Decommissioning Phase: Securely Retiring Devices At some point, physical security devices will reach the end of their useful life. When that time comes, companies must take care in how they dispose of their devices. A good vendor will provide guidance on how to clear memory chipsets and restore factory defaults. Improper decommissioning can lead to severe risks. For example, if an improperly decommissioned device is sold on the secondary market or retrieved from a dumpster, an attacker could gain access to sensitive network configurations and use this information for malicious purposes. Conclusion Deploying physical security solutions involves more than just securing buildings and assets; it also requires robust measures to protect against cybersecurity threats. From assessing vendors and understanding update policies to configuring devices securely and managing decommissioning processes, each step presents potential pitfalls that, if overlooked, could expose organizations to significant risks. By incorporating the techniques discussed into their deployment protocols, organizations can ensure their physical security solutions provide comprehensive physical and digital protection.
Rapid technological advancement, artificial intelligence (AI) and machine learning (ML) are revolutionizing traditional on-premises video security systems. These next-level tools are not just enhancing video data capabilities; they're transforming how businesses approach security, operational efficiency, and information analysis. Video analytics have been a part of security systems for many years, but the arrival of deep learning in 2009 marked a turning point. By training neural networks, basic analytics tasks like motion detection, object detection, and tracking objects within scenes have become commonplace. This leap forward has paved the way for more sophisticated AI and ML applications in video security. Proactive security measures AI-powered systems can perform complex tasks such as pose estimation and anomaly detection Today's AI-powered systems can perform complex tasks such as pose estimation, anomaly detection, and behavior analysis. These capabilities extend far beyond simple, passive monitoring, offering organizations rich insights and proactive security measures. For instance, analytics can now determine whether people are engaged in hostile or benign interactions, recognize unusual events that may signal safety hazards, and even predict potential security breaches before they occur — all based on analyzing massive amounts of data that humans alone could never process. Enhancing on-premises infrastructure While the power of AI and ML in video security is clear, integrating these technologies into existing on-premises systems presents both opportunities and challenges. One of the primary considerations is the increased demand for processing power and storage capacity. As solution technology expands, hardware requirements will increase. This reality necessitates a strategic approach to system design and implementation. Organizations must carefully evaluate their current infrastructure and plan for future needs to ensure their on-premises systems can handle the computational demands of AI and ML tools. However, the benefits often outweigh the challenges. AI-enhanced on-premises systems offer several advantages: Real-time processing: On-premises AI can analyze video feeds in real-time, allowing for immediate response to security threats. Data privacy: Keeping data processing on-site can help organizations meet strict data privacy regulations and protect sensitive information. Customization: On-premises systems allow for greater customization of AI models to meet specific security needs. Reduced latency: Processing data locally eliminates the need for constant cloud communication, reducing latency in critical security applications. The role of open platform video technology To fully leverage AI and ML capabilities in on-premises video security systems, open-platform video management software (VMS) plays a crucial role. An open platform VMS allows for seamless integration of various AI and ML tools, cameras, and other security devices, creating a highly flexible and scalable system. An open VMS can integrate thousands of cameras and sensors, allowing for centralized management and analysis of vast amounts of data. This approach enables security teams to quickly adapt to new threats and implement new and unplanned AI and ML solutions as they become available. Video system management The hybrid approach to video system management combines on-premises infrastructure with cloud services It's important to note that many organizations choose to deploy a hybrid approach to video system management that combines on-premises infrastructure with cloud services. This strategy can offer the best of both worlds: the control and low latency of on-premises systems with the scalability and advanced capabilities of cloud-based AI and ML tools. For example, some cities have implemented hybrid data storage models, hosting critical real-time data on local servers while leveraging cloud services for long-term storage and advanced analytics. This approach allows for efficient management of large amounts of high-resolution video data while reducing costs associated with on-premises storage expansion. Practical applications and benefits The integration of AI and ML into on-premises video security systems is transforming security practices across industries, offering benefits that extend beyond traditional surveillance. These advanced technologies enhance security measures while providing valuable insights for operational efficiency and strategic decision-making. By analyzing video data in real-time, AI and ML-powered systems can detect patterns and automate responses in unprecedented ways. Here are some key examples of sector-specific benefits: Retail: AI-powered analytics can optimize product placement, track shopping patterns, and enhance loss prevention efforts. Education: K-12 schools can use advanced video analysis to address issues like vaping and bullying, monitor traffic, ensure that proper procedures are followed, and provide enhanced safety and security. Manufacturing: AI can streamline quality control processes, detect safety violations, and optimize production line efficiency. Healthcare: Intelligent video systems can monitor patient safety, manage access control, and even assist in documenting and verifying that procedures and protocols are followed appropriately. Transportation: AI-enhanced video systems can improve traffic management, enhance security in transit hubs, and assist in incident response. Challenges and considerations Ensuring access to robust, diverse, and representative data sets is essential for training AI models effectively AI and ML hold great promise for on-premises video security, but organizations may encounter challenges during implementation. The considerable upfront costs could discourage smaller businesses or those with tight budgets. Nevertheless, this should be viewed as a long-term investment with significant returns in enhanced security and operational efficiency. Implementing AI-powered systems in video security can be complex, often requiring specialized skills, potentially creating a gap within existing IT or security teams. To bridge this skills gap, organizations may need to invest in training or partner with external experts to address this challenge. Additionally, the quality of data is crucial for effective AI and ML implementation; poor or insufficient data can result in inaccurate analyses and unreliable results. Ensuring access to robust, diverse, and representative data sets is essential for training AI models effectively. Benefits of integrating AI and ML Ethical considerations surrounding privacy, consent, and potential algorithmic bias are also critical. Organizations must strike a balance between enhancing security and safeguarding individual privacy rights to maintain public trust in these technologies. Despite these challenges, the benefits of integrating AI and ML into on-premises video security systems often outweigh the difficulties. Careful planning, resource investment, and a strong focus on ethical and regulatory compliance can lead to more effective, efficient, and intelligent security solutions. Future outlook Edge computing capabilities will enable sophisticated AI processing directly on cameras The future of AI and ML in on-premises video security promises significant advancements that will address current limitations and unlock new possibilities. Edge computing capabilities will enable sophisticated AI processing directly on cameras and other security devices, reducing strain on central servers and potentially lowering hardware requirements. This, combined with more efficient AI algorithms, will democratize access to advanced AI and ML capabilities for organizations of all sizes. AI-powered analytics Predictive analytics will become a cornerstone of future video security systems, marking a shift from reactive to proactive security measures. As AI models become more sophisticated, their ability to anticipate and prevent security incidents will improve dramatically, revolutionizing risk management and incident response. The integration between video security and other business systems will deepen, with AI-powered analytics providing insights beyond security into business operations and strategic decision-making. Data for training AI models Explainable AI will become more overall, which is vital for building trust in automated systems Automation of security processes will reach new heights, freeing human operators to focus on high-level decision-making and complex situations. To support this evolution, we'll likely see increased use of synthetic data for training AI models, addressing privacy concerns, and improving model robustness. Explainable AI will become more prevalent, which is crucial for building trust in automated systems and meeting regulatory requirements. For security professionals, embracing these technologies is no longer optional but necessary to remain competitive and provide the best possible service to clients. By leveraging open platform VMS and carefully planning system architectures, organizations can create flexible, scalable, and powerful video security solutions that not only protect assets but also drive business value. Enhanced video security systems The key to success will be finding the right balance between on-premises control and cloud-based capabilities while addressing important considerations around privacy, ethics, and regulatory compliance. With thoughtful implementation and ongoing adaptation, AI and ML-enhanced video security systems will continue to play an increasingly central role in safeguarding our businesses, institutions, and communities.
Security beat
Companies at GSX 2023 emphasized new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the security market. Today, more than half of the company’s lineup supports AI at the edge so the customer has a wide choice of form factors when seeking to leverage the feature set. AI processing relay, extended warranty i-PRO is increasing their warranty period from 5 to 7 years, which could be a lifetime warranty in some cases I-PRO also has an “AI processing relay” device that accepts non-AI video streams and applies edge analytics. AI has progressed from a high-end technology to a feature available in a variety of cameras at different price points. i-PRO is also increasing its warranty period from 5 to 7 years, which could be a lifetime warranty in some cases depending on a customer’s refresh schedule and lifecycle management. Active Guard, MonitorCast The company’s video management system (Video Insight) is continuing to build new features including “Active Guard,” an integrated metadata sorter. Their access control platform, MonitorCast, is a Mercury-based solution that is tightly integrated with Video Insight. Their embedded recorders now have PoE built in. “We can move at a faster pace to fill out our product line since leaving Panasonic,” says Adam Lowenstein, Director of Product Management. “We can focus our business on adapting to the market.” Emphasis on retail and other verticals Shoplifting is a timely issue, and retail is a vertical market that got a lot of attention at GSX 2023. “We see a lot of retailers who are primarily interested in protecting employee safety, but also assets,” says Brandon Davito, Verkada’s SVP of Product and Operations. “Shrinkage is a CEO-level priority.” “Retailers are getting more engaged with security posture, instead of letting perpetrators walk,” Davito adds. Intrusion detection Verkada has an intrusion product that will notify a central station if there is an alarm On the alarm side, Verkada has an intrusion product that will notify a central station if there is an alarm, and operators can review videos to confirm the alarm. Other capabilities seeking to discourage trespassers include sirens, strobes, and “talkdown” capabilities. International expansion Verkada continues to expand internationally with 16 offices in all, including Sydney, Tokyo, and London. The core value proposition is to enable customers to manage their onsite infrastructure more simply, including new elements such as PTZ cameras, intercoms, and visitor management. Verkada emphasizes ease of use, including a mobile application to allow access to be managed across the user base. Forging partnerships “We are committed to the channel and industry, and we continue to build relationships and expand our reach,” says Davito. Among the industry relationships is a new partnership with Convergint, which was hinted at during the show and announced later the same day. They are also expanding their partnerships with Schlage, Allegion, and ASSA ABLOY. Working with other verticals They offer new features for K -12 schools, and a new alarm platform is easier to deploy and manage Verkada has also found success across multiple other verticals, notably healthcare, where they integrate with an electronic medical records system. They offer new features for K-12 schools, and a new alarm platform is easier to deploy and manage. They are integrating wireless locks to secure interior doors in schools, looking to secure the perimeter, and installing guest management systems. Transitioning the Mid-Market to the Cloud Salient is squarely focused on the “mid-market,” a large swath of systems somewhere between small businesses and enterprise-level systems. Pure cloud systems are not as attractive to this market, which has a built-out infrastructure of on-premise systems. Adding a camera to an existing system is easier and less expensive than tying it to the cloud. Benefits of cloud It’s a market that may not be ready for pure cloud, but there are benefits to be realized from adding a cloud element to existing systems. “We are continuing to augment our premise-based solutions with added cloud capabilities and flexibility,” says Sanjay Challa, Salient’s Chief Product Officer. The feedback Salient hears from their customers is “I want to own my data.” The hybrid cloud approach offers the right mix of control, flexibility, and unit economics. Cloud add-on capabilities We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive" Cloud add-on capabilities include bringing more intelligence about system operation to the user via the cloud. Over time, Salient expects to sell more cloud-centric offerings based on feedback from integrators and customers. “We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive over time,” says Challa. Vaidio AI technology Salient seeks to be a transition pioneer to help customers realize the path to the cloud. Their approach is “crawl, walk, run,” and helping customers make the transition at each stage. Salient has added AI to its product offering, incorporating Vaidio AI technology from IronYun into a powerful suite and broad array of on-premise analytics, which are gaining traction. The seamless approach makes it easy for customers to embrace AI analytics, although Salient remains broadly committed to open systems. Addressing ‘Soft’ Features for Integrators AMAG is in the process of enhancing its product line with the next generation of access control panels. However, “product” is just part of the new developments at AMAG. In addition to “hard” features (such as products), the company is looking to improve its “soft” features, too; that is, how they work with the integrator channel. Integrator channel Rebuilding a process to make your organization more efficient, is relatively easy; it just takes a lot of persistence" “We have the depth of our legacy customer base we can learn from, we just need to close the feedback loop quicker,” says Kyle Gordon, AMAG’s Executive Vice President of Global Sales, Marketing, and commercial Excellence, who acknowledges the value of reinstating face-to-face meetings after COVID. “We are laser-focused on nurturing our integrator channel,” he says. “Developing new features takes time, but rebuilding a process to make your organization more efficient, that’s relatively easy; it just takes a lot of persistence,” says Gordon. More cohesive internal communication is another useful tool, he says. Disrupting the cloud based on price Wasabi is working to make cloud applications less expensive by offering a “disruptive” price on cloud storage, $6.99 per terabyte per month (80% less than hyperscalers). Contending “hyperscalers” like AWS are charging too much for cloud storage, Wasabi is using its own intellectual property and server equipment co-located in data centers around the world. Wasabi sells “hot cloud storage,” which refers to the fact that they only have one tier of storage and data is always accessible. In contrast, a company such as AWS might charge an “egress fee” for access to data stored in a “colder” tier. Cloud storage “We saw that several video surveillance companies had not yet adopted cloud storage, and we saw an opportunity to make it easy to use,” said Drew Schlussel, Wasabi’s Senior Director of Product Marketing. “We just install a little bit of software that allows them to store data in the cloud and bring it back from the cloud.” Performance, protection (cybersecurity), and price Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies such as Genetec and Milestone. Emphasizing performance, protection (cybersecurity), and price, their data centers are certified to SOC 2 and ISO 27001 standards. Faster throughput for weapons detection Xtract One is a young company focusing on weapons detection in a time of accelerated concern about gun issues post-COVID. Founded in Canada and based on technology developed at McMaster University, Xtract One has found a niche in providing weapons detection at stadiums and arenas. These customers already have budgets, and it is easy to shift the money to a newer, faster technology. Madison Square Garden in New York City is among its customers. Cost savings solution Xtract One can increase throughput to 30 to 50 people per entrance per minute (compared to 5 to 6 people per minute when using metal detectors). The solution doesn’t require anyone to empty their pockets and the system alarms on items beyond guns and knives. Using Xtract One allows customers to reduce the number of screening lanes and security staff, providing additional cost savings, all while getting fans through the screening process in half the time. Purpose-built sensors The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties In addition to stadiums and arenas, Xtract One, formerly Patriot One, is also getting “inbound” interest from schools, hospitals, manufacturers, and other verticals that makeup 50% of their business. “We’re on a rocket ride, mainly because the weapons issues are not going away,” says Peter Evans, CEO and Director at Xtract One. The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties, all correlated by an AI engine. Providing early warning of violence ZeroEyes is another company focused on weapons detection. Their AI gun detection system works with video images to identify if someone is “brandishing” (carrying) a weapon. In other words, the system does not detect concealed weapons. Identifying someone carrying a weapon provides early warning of a possible violent act. Increased response with AI-enables images Images are identified by AI and sent to a monitoring center where a human confirms the image before contacting first responders. Knowing the location of a shooter enables staff to lock entry points, move people to safety, and direct first responders. The company was founded to leverage existing camera views to stop mass shootings and gun violence by reducing response times.
GSX 2023 has its share of new product announcements, although many of the new products are enhancements to technologies shown at last spring’s ISC West show in Las Vegas. Booth traffic on the first day seemed busy at the Kay Bailey Hutchison Convention Center in Dallas, although one exhibitor complained that it takes some time for the traffic to make its way to the farthest areas of the show floor. Apparent throughout the GSX show is an expanding idea of what constitutes security. Increasingly, ‘security’ technologies offer benefits throughout other parts of a company or institution. Security is also being broadened to encompass ‘safety,’ including emergency response and wider issues of keeping a company safe. Managing multiple systems People look at the systems they have, and they are looking for more information" Manufacturers at GSX are talking about more than new products. Rather, they are offering new approaches to turn products into ‘solutions’ for customers. Among the benefits of new systems is the availability of more data. “People look at the systems they have, and they are looking for more information and data and insights from their systems,” says Kyle Hurt, Genetec’s Area Vice-President of Sales for the US and Canada. “In the past, if I’m managing multiple systems and spending time and resources, I am making sure systems are operational. Today, it’s more like: How do I make my enterprise more efficient? I spend less time on making sure systems are working together but more time on how we can use the information.” Manufacturers at GSX are talking about more than new products Security control room Genetec is enhancing its Security Center 5.11 version with a newly redesigned web client that provides new capabilities related to system audio, including the ability to trigger a public address from a mobile device in an emergency, two-way audio to and from the security operations center, and the ability to record an incident. The new web client offers new levels of “Security on the go,” says Hurt. A mobile device becomes an extension of the security control room. “Customers want to have more remote capabilities and have their security personnel out and about, not tied to a desk,” says Hurt. The new web client works to unify the four pillars of the Security Center— video, access control, license plate recognition, and now audio. Single source manufacturer Audio can now be used to broadcast a message, respond to an incident, and notify people" “Audio has taken time to develop legs in our ecosystem,” says Hurt. “We have been developing partnerships and use cases beyond an intercom at the door. Audio can now be used to broadcast a message, respond to an incident, and notify people en mass of what’s going on.” Manufacturers are also fine-tuning how they work to meet customers’ needs. “Customers want one point of contact, a single source manufacturer, and a solution that reflects the manufacturer is listening to the voice of the customer,” says Jerry Burhans, Managing Director of ASSA ABLOY Global Solutions - Critical Infrastructure, which seeks to be a global partner to critical infrastructure industries. The Critical Infrastructure business works across the various product groups of the notoriously siloed company to bring together solutions aimed at meeting each customer’s need. Manufacturers are also fine-tuning how they work to meet customers’ needs Best-in-class technology “We try to have best-in-class technology and collaborate within ourselves to make sure we have what customers need,” says Burhans. Critical infrastructure industries such as water, power and energy, oil and gas are developing standards to help support preparedness of the nation’s infrastructure, and ASSA ABLOY Global Solutions is helping operators secure access and provide audit trails on locking hardware and keys within their security perimeters. Managing customer assets Johnson Controls’ new OpenBlue Service for the security device market seeks to proactively manage customer assets (equipment) as a service. The company’s software platform of connected solutions monitors and manages security devices across vendors and provides remote support services including skilled engineers who can work to ensure that a company’s assets, including cameras and access control readers, operate dependably. Working remotely, OpenBlue analyzes the performance of each system component Johnson Controls estimates that, unfortunately, up to 25% of a company’s security assets may not be working as intended, whether they lack the latest firmware update or are not connected. Working remotely, OpenBlue analyzes the performance of each system component and responds to ensure equipment operates as intended. “We believe we can close that gap with our solutions,” says Greg Parker, Vice President, Innovation & Portfolio Management for Johnson Controls. Physical security equipment A big advantage of OpenBlue for security customers is the ability to manage cybersecurity and threats at the edge, which may not currently be addressed by the IT department. The OpenBlue offering includes an embedded ‘air wall,’ which is a zero-trust architecture for physical security equipment. OpenBlue also helps customers manage the ever-changing lifecycles of various assets. Another concept prompting discussion at GSX 2023 is the gap between what a customer expects from a product and what the product can realistically deliver. With endless promotion in the last several years centering on concepts such as artificial intelligence (AI), is it any wonder that customers may sometimes have unrealistic expectations about what a technology can accomplish? The good news at GSX is that, as progress marches on, newer technologies are getting closer and closer to delivering on customers’ most ambitious expectations. The forward momentum of technology development is evident throughout the GSX 2023 show floor, reflecting the promise of even greater product capabilities in months and years to come.
A pioneer in the access control sector since 1971, AMAG Technology is looking to the future and the next generation of products that will expand its services to customers. “In our vision, we have advanced approaches that will not only provide our partners with advanced technologies but also ones that are easier to install with tools to expand their services,” says David Sullivan, who was appointed President of the venerable access control company in September 2022. New challenges at AMAG Sullivan brings a new outlook to the AMAG business, a part of Allied Universal, and a new vision to lead the company into the future. We caught up with David Sullivan to discuss his new challenges at AMAG and the journey ahead as the company looks to the future. Q: How does your background inform your approach to leading AMAG? I believe that it helps me to define a vision for AMAG that will be unique and on the leading edge of our industry David Sullivan: With the exception of only a few short years, my career has been in access control. I have experience with several systems and have had the privilege to manage several successful access control companies. As a result, I bring a great deal of experience into my role at AMAG. I believe that it helps me to define a vision for AMAG that will be unique and on the leading edge of our industry. Q: How would you describe AMAG’s journey over the last several years and how do you see the future? Sullivan: Prior presidents of AMAG always shared their leadership vision and direction with senior leaders located in the United Kingdom. This had an impact on the full direction of the business, sometimes limiting its ultimate success. Before I became a part of AMAG, these senior leaders that were located in the UK retired, placing for the first time the full management responsibilities of the president. This has allowed me to integrate the business into a single team, with single objectives, and a single vision. We expect to begin to reveal this new vision in the coming weeks. We are excited about the future of AMAG and believe we will surprise the industry with our new products and approach in the coming months and years. Q: How important is it that a manufacturer provides both hardware and software solutions? How does AMAG’s approach (in general) differentiate it in the market? We can design the complete solution, providing functionality that others may find more difficult to accomplish Sullivan: Regardless of the manufacturer, we all provide hardware and software. An access control solution is not complete without both. Some of us choose to make our panels, and others do not. Those who are dependent on third-party suppliers are restricted to the developments and direction of that company, and while it might be perceived to be an open technology, it still is proprietary to the hardware manufacturer. AMAG has controlled its manufacturing of panels from day one. The result means that we can design the complete solution, providing functionality that others may find more difficult to accomplish. Q: How does the breadth of AMAG’s product suite provide advantages to customers and/or integrators? Sullivan: AMAG’s product portfolio is unique and provides the end user with an end-to-end identity management solution from one company. Our Control Room PSIM, Symmetry CONNECT Identity Management Solution, Symmetry Access Control, and Symmetry GUEST solutions all integrate to provide the user with a broad set of features and capabilities from a single provider. There is no finger-pointing when we come to support your system. We hold full responsibility for making it work and can quickly provide a resolution to any application difficulties the user may be experiencing. Q: How does AMAG address the divide between on-prem and cloud systems? How do you help customers make the transition and/or plan for the future? We are in the early stages of developing our next generation of access control in which we intend to provide on-prem Sullivan: In our current product portfolio, we have three products that are cloud-based. Our mobile credential platform (Symmetry Mobile), our visitor management solution (Symmetry GUEST), and our physical identity and access management solution (Symmetry CONNECT) are all offerings that operate in the cloud. We are in the early stages of developing our next generation of access control in which we intend to provide on-prem, web client, and cloud-based offerings. One of the primary objectives is to ensure that the large installed base of systems that are out there today will be able to migrate not only to our next generation but as well to the cloud if the client so desires. Q: What is AMAG’s approach to mobile credentialing? Sullivan: As an access control provider, adding Symmetry Mobile credentialing to our portfolio just made sense. We want our customers to have a forward-thinking solution with the opportunity to save money not only on the physical badges but the cost of printing and distributing badges. Mobile credentials can be easily issued and revoked remotely, reducing administrative overhead, and eliminating the need for physical inventory management. Organizations can centrally configure what devices are used and the read range for each type of device and operating system, thus providing flexibility. Symmetry Mobile offers a customized questionnaire that controls access and reduces liabilities. Q: What has surprised you the most in your first year or so leading AMAG? Not many companies are blessed with such a broad portfolio that is supported by a resource-rich company Sullivan: I wouldn’t say I was surprised by this as much as happy to see, but I would say that the quality of our people was a pleasant surprise. As well, the AMAG product offering is broad and has some unique elements. When coupled with the depth of the resources that we have in AMAG, I know that we are second to none. Not many companies are blessed with such a broad portfolio that is supported by a resource-rich company that has so many talented people. Q: Please describe your dealer channel, and how you are seeking to expand it. Sullivan: The AMAG products are sophisticated and typically are installed for higher-end applications. With this sophistication comes a need to be well able to install such a solution. We have a strong group of certified and loyal partners who help us to deliver these enterprise solutions. We desire to provide our existing partners with updated and competitive systems to offer to their end users. Q: What is the security industry’s (and/or AMAG’s) biggest challenge in the next five years? We need to find ways to provide both our channel partners and the customers with solutions that are easily integrated Sullivan: I believe that the advancements that we are seeing in technology provide our industry with the opportunity to truly change how security is provided to our collective customers. As we advance these solutions, we will need to do so responsibly and in a way that helps the channel’s abilities. We need to find ways to train our partners to both install and support these more complex solutions. At the same time, we need to find ways to provide both our channel partners and the customers with solutions that are easily integrated, moving away from proprietary closed systems to open and cohesive solutions. This will ensure that the users get the best, and most complete solutions. Q: What does the industry as a whole misunderstand about AMAG -- time to set the record straight! Sullivan: Well, I am not ready to openly share where we are heading. We are in the process of putting together some advanced approaches to how we will do business with our partners. We are focused on providing tools that will enhance their services to their customers, and with products that are leading edge. I can only state that all should keep their eyes on AMAG, because over the next few years, we are going to surprise some people, and more importantly make our loyal partners quite powerful.
Case studies
Gunnebo Entrance Control has partnered with Queenstown Airport (ZQN) and Custom Technology Systems Ltd to elevate the domestic departure experience, providing greater convenience and security for passengers. Queenstown Airport, a key gateway to New Zealand’s South Island and the country’s fourth-busiest airport, has evolved continuously since opening in 1935. Now serving more than 2.6 million passengers each year, it connects major domestic destinations and east coast Australia, driving ongoing improvements to passenger facilities and operational efficiency. Entrance control solution As part of a dedicated program to enhance the domestic departures journey, ZQN reworked existing café space. A glass wall was installed to relocate the café airside, integrating it with the gate lounge. This provided direct food and beverage access for passengers and created additional seating, all within the same footprint. To support the new layout, Custom Technology Systems Ltd and Gunnebo Entrance Control worked closely with the on-site teams to deliver a tailored entrance control solution that balanced security and passenger flow while accommodating spatial limitations. Adapting to unexpected challenges “The success of this project was achieved by working together, adapting to unexpected challenges, and staying focused on delivering a secure, seamless journey for every passenger,” said Chris Walker, Project Manager at Queenstown Airport. “Every challenge we encountered was met together. Whether it was refining the design, resolving compliance issues, or adapting to the space, we relied on each other’s strengths to get it right.” Gunnebo Entrance Control’s PasSec solution To optimize style, security and passenger movement, the team installed Gunnebo Entrance Control’s PasSec solution, a sleek one-way corridor system designed to prevent backflow while maintaining compliance with strict local and international aviation regulations. Brett Copeland, Managing Director at Custom Technology Systems Ltd, added: “For this works programme, there was a genuine sense of problem-solving together. It wasn’t about one party leading and others following but instead a collaborative process from initial design and specification through to project completion. We each brought ideas, worked through constraints and stayed focused on making the solution fit.” Challenges together to deliver smarter Clive Dillen, Regional Manager at Gunnebo Entrance Control, concluded: “We’re proud of what we achieved here, and the result reflects the true essence of coordination, discussion and trust. That’s what true partnership looks like and marks a major step forward in Queenstown Airport’s continued development." "It stands as a clear example of what can be accomplished when organizations work through challenges together to deliver smarter, more effective outcomes for passengers and operators.”
Hotel Montresor Tower, a stylish four-star destination just outside Verona, Italy, has successfully upgraded its fire detection infrastructure with Hochiki's advanced Latitude life safety platform. As part of a comprehensive refurbishment, the hotel partnered with installer TOLA & C. SRL to install a new Latitude 8‑loop control panel, complemented by voice alarm devices (VADs), call points, and ESP sensors. Black‑finished ESP detectors Legacy sensors were updated to the ESP range to comply with the Italian standard UNI11224 The Latitude system was chosen for its intuitive programming and powerful Hotel Mode, which offers controlled alarm delays, minimizing unnecessary disruption while maintaining strict safety compliance in guest rooms. To preserve the venue’s contemporary aesthetic, sleek black‑finished ESP detectors were installed in the newly renovated conference center. Elsewhere, legacy sensors were updated to the ESP range to comply with Italian standard UNI11224, which mandates system upgrades every 12 years to ensure reliability and performance. Integrating the Latitude panel and ESP devices Director Luca Montresor commented on the upgrade: “We’ve been extremely satisfied with Hochiki’s technology over the years—it’s reliable, easy to maintain, and straightforward for our staff to operate. When it was time to expand and refurbish, there was no question we’d stay with Hochiki for the new system too.” By integrating the Latitude panel and ESP devices, Hotel Montresor Tower has not only elevated its life safety infrastructure but ensured seamless visual integration and enhanced operational efficiency, future‑proofing the guest experience without compromise.
Climate and weather can have a damaging impact on digital devices, especially in locations where extremes in summer and/or winter are common. This may be an obstacle to implementing digital technologies or digitalizing outdoor workflows. For controlling access, it can prevent organizations from realizing the benefits of digital access at remote and/or outdoor sites. Intelligent digital locking, which meets the highest standards of durability and reliability, is required. Expansion of infrastructure OXG builds and operates a high-speed fiber optic network designed to meet the digital needs OXG Glasfaser GmbH is a joint venture founded in 2023 by Vodafone and Altice. Their goal is to make a significant contribution to the expansion of infrastructure throughout Germany. OXG builds and operates a high-speed fiber optic network designed to meet the digital needs of individuals and companies. In the next few years, they aim to connect 7 million households with fiber optic. An investment of up to €7 billion is being made for broadband solutions and innovative FTTH (Fiber to the Home) expansion. Modern access solution They sought a modern access solution suited to securing the stations required for the expansion of their network: a locking system able to provide flexible security for their fiber optic stations. Of course, these stations are outdoors, often in public spaces, and exposed around the clock to wind and weather. Reliable security and outdoor operation are a must. They are also dispersed nationwide, which means frequent maintenance visits would represent a drain on time and money. OXG sought devices that were easy to install and would require as little maintenance as possible over their working lifetime. ECLIQ solution An eCLIQ system can be expanded, combined, and retrofitted according to its evolving needs With the programmable key-based eCLIQ solution, part of a suite of Digital Access Solutions from ASSA ABLOY, OXG chose digital access, which is reliable, robust, and suitable for environments with demanding climate conditions. An eCLIQ system can be expanded, combined, and retrofitted according to its evolving needs. “In addition to the flexibility, the resistance and durability of eCLIQ are particularly advantageous. That convinced us,” explains Markus Walther, Senior Manager Deployment Aggregation Network at OXG Glasfaser. Digital access With around 2,500 wireless cylinders, OXG’s eCLIQ solution provides an efficient, effective way to fit digital access. Installers simply slot in one of more than 60 different eCLIQ cylinder types instead of a mechanical cylinder. These innovative cylinders operate maintenance-free for up to 200,000 cycles. For system administrators, eCLIQ is easy to operate and program. They benefit from the convenience of digital management. For instance, they do not need to activate every locking cylinder individually. Lock power supply and communication with the cylinder are conducted via battery-powered user and programming keys only. Award-winning CLIQ technology upgrades security by making it simpler to issue individual access authorizations. If a key is lost, its access permissions are simply deleted from the system with a few clicks in the intuitive software.
Ecuador’s border control authorities have significantly enhanced their identity verification capabilities by deploying a suite of advanced document examination devices from Regula. The nationwide upgrade, supported by the International Organization for Migration (IOM) and local partner INSETK, brings automation, precision, and speed to the country’s border checkpoints, which collectively process nearly 1.5 million travelers annually. Regula’s advanced forensic devices The project is a major step in Ecuador’s mission to modernize all land, air, and maritime entry points The project is a major step in Ecuador’s mission to modernize all land, air, and maritime entry points, including key international airports in Quito and Guayaquil, as well as northern and southern border crossings. These strategic locations now benefit from Regula’s advanced forensic devices, which enable fast and reliable detection of fraudulent documents—critical in the fight against identity-related crime. Closing the gap with a set of forensic devices Previously, document checks at Ecuador border crossings were largely manual and supported by outdated equipment, often handled by just two officers per site. This made the process slow, error-prone, and vulnerable to sophisticated fraud. To address this, Ecuador’s border checkpoints were equipped with the following Regula solutions: Regula 4308 at Quito International Airport: Ideal for high-traffic airports, this dual-video spectral comparator supports the full spectrum of light sources and optical filters. It also offers high-quality image capture capabilities thanks to its up to 320x optical zoom and up to 140,000 ppi resolution. As a result, border officers can thoroughly inspect all of the ID security features, including printing techniques, holograms, optically variable inks, and more. Regula 4306 at Guayaquil International Airport and major land borders: A space-saving device with an 8 MP high-resolution camera and over 40 LED light sources for analyzing document authenticity, just like its counterpart, the Regula 4308. Regula 4205D at frontline checkpoints: A multi-functional device tailored for primary control zones. It includes 12 light sources, automated cross-checks, and up to 30x on-screen magnification for thorough document authentication. Regula 8333M at mobile checkpoints: Designed for remote or non-standard border control situations, such as processing charter flights or cruise ship passengers, this compact mobile document reader ensures that ID checks remain reliable and consistent outside traditional migration offices. Regula’s Information Reference System Regula’s video spectral comparators are controlled via Regula Forensic Studio (RFS), a cross-platform software solution for advanced document checks. It enables precise measurements, image comparison, report generation, and scripted workflows for faster, consistent inspections. With RFS, officers can also verify MRZs, RFID chips, barcodes, and IPI—all without extra tools. For deeper document examination, border control officers have real-time access to Regula’s Information Reference System (IRS), which provides synchronized reference images and lighting presets for fast, precise comparison of travel documents. Data cross-verification and robust authenticity checks RFS also integrates with Regula Document Reader SDK to automate travel document verification RFS also integrates with Regula Document Reader SDK to automate travel document verification and prevent fraud through data cross-verification and robust authenticity checks. Importantly, Regula’s software is backed by its proprietary identity document template database—the world’s largest—featuring over 15,000 templates from 252 countries and territories, ensuring reliable validation at border checkpoints. Trusted results, faster than ever Since implementing Regula’s solutions, Ecuadorian border control authorities have noticed notable improvements: Document authentication now takes minutes instead of hours. Detection of forged documents has significantly increased. Automation reduces human error and increases operational efficiency. Officers have more time to focus on complex cases and decision-making. Technology upgrade and fraud detection “Apart from the technology upgrade and fraud detection improvement at the border crossings, our collaboration with Regula demonstrated another success." "The project was fulfilled very smoothly. From the beginning, we’ve received full support from Regula’s team—they were always ready to help with any issue, even those caused by users on the ground. It’s definitely a level of service that makes a real difference,” says Diego Calderon, Chief Executive Officer at INSETK. How technology can turn critical inspection tasks “Border security is where precision, speed, and trust must converge. We're proud to support Ecuador in modernizing its checkpoints with tools that meet forensic standards while being easy to use in the field." "This project shows how technology can turn critical inspection tasks from time-consuming to streamlined, without compromising security,” comments Arif Mamedov, CEO at Regula Forensics, Inc.
In 1979, nine districts and five cities in Bavaria, Germany, founded a joint association for the disposal of residual waste. They targeted future-oriented, environmentally friendly and economical fulfillment of local statutory obligations. Now with 17 association members, ZMS (Zweckerverband Müllverwertung Schwandorf) disposes waste for around a fifth of Bavaria, almost two million citizens. They also use the energy generated by the waste power plant as efficiently as possible. Different levels of security Devices and other access hardware also need high weather resistance, for deployment outdoors In the past, a mechanical locking system was used on all ZMS properties. The association planned a digital upgrade to boost flexibility over their existing mechanical locking. Their principal site at Schwandorf has areas requiring different levels of security. Devices and other access hardware also need high weather resistance, for deployment outdoors. Managers also considered workflow efficiency. They wanted a way to manage access authorisations more flexibly and align security infrastructure with upcoming IT security laws such as NIS2. Digital Access Solutions from ASSA ABLOY The company chose eCLIQ, part of the suite of Digital Access Solutions from ASSA ABLOY. This innovative, programmable key-based solution now equips not only the power plant and headquarters in Schwandorf, but also buildings across eastern Bavaria, including transfer stations, a waste disposal site, a sorting plant in Bodenwöhr, and a sludge drying plant, as well as all technical and commercial offices, gate control systems and local control points. Because eCLIQ offers a broad range of digital cylinders within its single ecosystem, it suits diverse and complex organizations like ZMS. The benefits of programmable key-based digital access These Wall PDs also make it easy to set limited access time windows for fitters or maintenance contractors The digitally networked eCLIQ system allows access rights and security levels to be defined and assigned flexibly and precisely. A total of 20 Wall Programming Devices (Wall PDs) installed in the head office and branch offices ensure that only authorized employees gain access. These Wall PDs also make it easy to set limited access time windows for fitters or maintenance contractors. If a key is lost, it can be programmed out immediately to prevent misuse. Standard eCLIQ keys “Now we are going with the times and can conveniently enjoy a wide range of advantages,” says Manuel Emerich, Project Manager at ZMS. “As a critical infrastructure company, we can also react very rapidly and flexibly to future requirements.” The solution offers the advantage that a depleted battery does not render a cylinder useless With eCLIQ, each of ZMS’s approximately 1,000 wireless digital cylinders is powered by a battery inside the keyholder’s personalized key. Standard eCLIQ keys have a battery life of 10 years with typical usage. The solution offers the advantage that a depleted battery does not render a cylinder useless. The key is simply fitted with a spare battery, saving time and effort. Future of evolving physical and cyber-security threats Security is a critical concern at municipal and infrastructure sites: every eCLIQ device offers reliable protection against manipulation and intelligent break-in attempts. Keys are robust, with a waterproof casing, and operate reliably in the most challenging environmental conditions. With eCLIQ, ZMS feel ready to face a future of evolving physical and cyber-security threats. “For us, the introduction of digital locking technology and the ability to respond quickly and specifically to security incidents is a decisive step towards a holistic and future-proof system to defend against cyber–physical threats,” adds Manuel Emerich.
Amthal Group Companies has supported Tradestars’ new Hackney Wick site with a comprehensive, ground-up technology stack, incorporating integrated smart security and fire safety for the benefit of the thriving entrepreneurial community. Tradestars offers flexible co-warehousing facilities for entrepreneurs looking for collaborative workspaces and shared resources to foster innovation and growth. Its newest location presents spaces in Hackney Wick to suit individual business needs. Integrated security solution Amthal to design a fully integrated security solution that was installed, monitored and maintained With the site spread out across multiple blocks and topped with residential accommodation, Tradestars worked directly with Amthal to design a fully integrated security solution that was installed, monitored and maintained for the benefit of the growing community. The result is a secure, technology-led site with members able to book facilities, and open doors to access offices, meeting rooms and amenities via their phone, whilst giving community managers centralized control over the building. Security and fire safety measures Says Jonathan Marriott, Construction Director at Tradestars: “Our work with Amthal has been instrumental in elevating our Hackney Wick site into a secure, cowarehousing business environment." “With their expertise, we’ve seamlessly integrated comprehensive security and fire safety measures, ensuring the safety and peace of mind of our thriving entrepreneurial community. The ability for our members to effortlessly book facilities and access various amenities via their phones, all while providing our community managers centralized control, truly enhances the Tradestars experience.” Advanced technology features of Amthal Amthal designed and installed a fully integrated, ground-up technology stack – from fiber connectivity Following a detailed risk assessment across the site facilities, in cooperation with main contractors, Amthal designed and installed a fully integrated, ground-up technology stack – from fiber connectivity, Wi-Fi, audiovisual and space management solutions, to fire, security and access control. Paul Rosenthal, Amthal Group Business Development Director added: “Being involved right from the initial design stages of the building site, enabled us to create a system to encourage connectivity, collaboration and innovation. One where members enjoy streamlined access, advanced technology features, and a safe working environment." Integrating fire safety and security systems Rosenthal added: “The focus on integrating fire safety and security systems means the growing community can focus on building their business vision, safe in the knowledge that they are powered and protected wherever they are on site, fitting today’s mobile-connected lifestyle." "This is complemented by fully managed services and support to ensure the continuous operation and maintenance of the complete ecosystem.”


Round table discussion
The Internet of Things (IoT) is having a profound impact on businesses across various industries, including security. In physical security as in other business environments, the IoT is changing how systems operate, interact, and create value. In the process, the IoT is driving efficiency, reducing costs, and opening up new avenues for innovation and growth. We asked our Expert Panel Roundtable: How is the Internet of Things (IoT) transforming how security systems are deployed?
In the past, security installers and integrators were used almost exclusively to install hardware. However, the role is changing and expanding along with the technologies used in the physical security industry. Nowadays, an installer or systems integrator is much more likely to use a strategic, IT-centric, and data-driven approach. To gain additional insights, we asked our Expert Panel Roundtable: How is the role of the security installer/integrator changing?
In many cases, architectural design and layout dictate optimal placement of security devices like cameras, access control readers, and sensors. Poor design can lead to blind spots, reduced coverage, and ineffective surveillance. However, planning that involves all the various stakeholders can maximize both security and design elements. We asked this week’s Expert Panel Roundtable: When are building design and physical security systems complementary? When are they at odds?
Products


White papers
Preventing Loss, Securing Assets
Download
Safeguard Students With New Techniques And Technology
Download
5 Ways To Strengthen Physical Security With An Integrated System
Download
The Benefits of Edge AI + Cloud For Security Systems
Download
Smart Security Cameras: Excellence in Retail
Download
Is Access Control In The Cloud More Cost Effective?
Download
Innovative Edge Storage Solutions For The Video Surveillance Industry
Download
Enhanced Ethernet Technology (ePoE)
Download
Do You Know The Weakest Link Of Your Access Control System?
Download

Videos
Security devices: Manufacturers & Suppliers
- Dahua Technology Security devices
- Vicon Security devices
- Bolide Security devices
- Seagate Security devices
- Vanderbilt Security devices
- Bosch Security devices
- Hanwha Vision Security devices
- Aritech Security devices
- Parabit Security devices
- LILIN Security devices
- VIVOTEK Security devices
- Hikvision Security devices
- BCDVideo Security devices
- Sony Security devices
- ComNet Security devices
- Videotec Security devices
- CEM Security devices
- Aiphone Security devices
- Pelco Security devices
- AV Costar Security devices