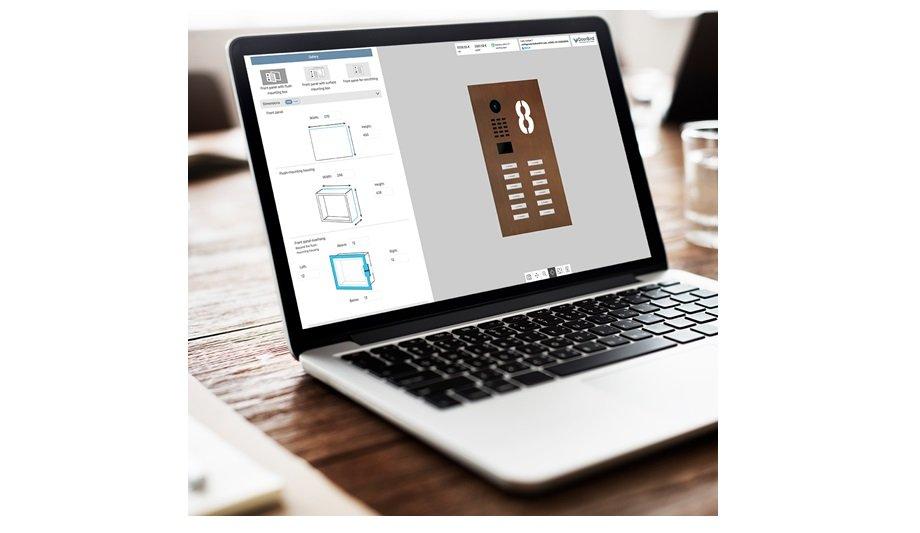
DoorBird's 3D configurator allows user to design their very own customized DoorBird in just a few steps and to create specific dimensions, surfaces, and features according to their wishes.
High-quality mailbox and doorbell systems are combined with IP video technology from DoorBird.
Key features
No matter if it’s a wall drop box, a fence-mounted mailbox, an intercom column, or a buzzer panel, every IP system is manufactured by user specifications. There are a variety of modules to select from, such as a keypad, fingerprint reader, or display.
- Over 50 RAL colors and surfaces are available to choose from here.
- DoorBird door station is displayed directly in 3D and updated, together with price and delivery time, with every step.
- The Augmented Reality function makes it possible to visualize the intercom where it will be installed. The comparison can be done by uploading a photo or live with an activated smartphone camera. The system and the technical drawing can be saved for the configuration later.
- The fully configured IP video door station can be ordered directly in the planning tool.
For custom products or requests not possible in 3D Configurator’s configuration system, feel free to contact DoorBird so it can find the right solution.