Physical security
Alcatraz, the pioneer in facial biometric authentication for physical access, now announced the successful completion of its SOC 2 examination as of November 7, 2025. The independent audit was conducted by A-LIGN, the pioneering provider in cybersecurity compliance trusted by more than 4,000 global organizations. Biometric access with confidence “Trust in biometric systems depends on strong data stewardship,” said Tina D’Agostin, CEO of Alcatraz. “At Alcatraz, we work...
The Physical Security Interoperability Alliance (PSIA) has now announced the release of a new PKOC Explainer Video, created to offer a clear and visual overview of the Public Key Open Credential (PKOC) specification in comparison to symmetric credential options. The video demonstrates the limitations of symmetric encryption in traditional access control credentials and explains how PKOC’s public/private key model enhances security through asymmetric verification. PSIA specification...
To serve various vertical markets and industries effectively, security professionals must recognize that each sector has unique assets, risks, compliance requirements, and operational needs. Instead of offering a one-size-fits-all solution, security system providers must tailor their products, services, and integration strategies to address the distinct requirements of vertical markets. We asked our Expert Panel Roundtable: Which vertical markets have the greatest growth potential for physical s...
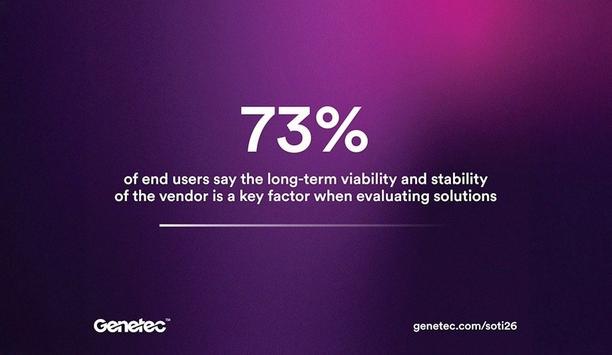
Genetec Inc., the pioneer in enterprise physical security software, now released its sixth annual State of Physical Security report. Based on insights from over 7,300 physical security pioneers worldwide (including end users, channel partners, systems integrators, and consultants), the report shows that physical security is playing a broader strategic role within organizations. The findings highlight closer collaboration across departments and greater interest in technologies that support bette...
Allied Universal®, a pioneering security and facility services provider, now announced that it has sold a majority stake in AMAG Technology to Shore Rock Partners, a critical infrastructure-focused growth investor. AMAG is a pioneer in integrated high-security access control, identity, guest, and video management solutions. The new ownership group led by Shore Rock Partners with strategic backing from BellTower Partners will continue to support enhancements to AMAG’s product portfolio...
Gunnebo Safe Storage has partnered with Jaktia to deliver a tailored storage solution for a new store offering high-tech equipment and ammunition. Designed to integrate seamlessly within a restricted layout, the system was developed to meet all regulatory obligations and Police Preferred standards. As Sweden’s pioneering retailer for hunting, fishing and outdoor activities, a tight schedule for a new store opening meant Jaktia required a secure and certified storage system that could be i...
News
ZBeta, a pioneer in delivering comprehensive physical security consulting services, now announced that senior executives Conal O’Doherty and Jesse “JJ” Knutson have been named principals of the firm. In their respective roles as Chief Growth Officer and Chief Operating Officer, Conal and JJ have been instrumental in shaping ZBeta’s identity by elevating the brand, enriching the client experience, advancing corporate strategy, strengthening operational performance, and unlocking new growth opportunities. As principals, they will continue to work alongside CEO Zack Brunette to chart the firm’s strategic trajectory, guide operational priorities, and advance the evolution of the organization. Transforming the security function ZBeta has long centered its work on the belief that strong security programs should function as seamlessly as great design, reducing friction while enabling organizations to operate at their highest potential. The appointment of JJ and Conal as principals further strengthens this approach and further aligns the firm’s leadership around a shared commitment to transforming the security function into a model of organizational excellence. ZBeta’s leadership team ZBeta’s leadership team boasts a long history of developing security and business consulting programs that meet client needs while enhancing how organizations operate. Over the years, they’ve worked with Fortune 50 organizations like Amazon, Microsoft, Wells Fargo and other well-regarded organizations to create solutions that blend strategy and innovation with practical know-how and world-class delivery. This has shaped the firm into a trusted partner for global security pioneers seeking clarity and confidence in a landscape that grows increasingly complex each day. Prior roles of JJ As Chief Operating Officer, JJ has provided clear direction and operational leadership across ZBeta’s consulting, design, and engineering practices. With more than 25 years of experience spanning systems integration, manufacturing, engineering, and high-level security program design, he has led the development of advanced solutions for environments including corporate security operations centers, data centers, financial institutions, critical infrastructure, and complex network architectures. His direct approach, combined with in-depth technical expertise, has significantly contributed to ZBeta’s reputation for precision and dependability. ZBeta’s success collaboration “ZBeta’s success has always come from a combination of great people, strong collaboration, and a commitment to doing things the right way,” JJ said. “Becoming a principal is an honor, and it reinforces how dedicated we are to helping clients build smarter, more resilient security programs. I’m looking forward to what we can accomplish together in this next chapter.” ZBeta’s strategic direction Conal has been a steady influence on ZBeta’s strategic direction — from corporate strategy and development of the brand to how it approaches it’s Talent and Culture model and how it supports clients and attracts new ones. Throughout his career, he’s helped strengthen organizational performance, build high performance and motivated teams, and create cultures rooted in trust and accountability. His ability to build genuine, long-lasting relationships has been a major driver of ZBeta’s growth and its focus on delivering meaningful, people-first results. ZBeta's enhanced leadership structure “I’m proud of what we’ve built at ZBeta, but even more inspired by where we’re going,” Conal said. “For us, it has always been about attracting the very best talent in the industry and enabling them to do their best work with the best clients and that will continue to be our focus as we move forward. I’m truly grateful for this opportunity to join forces with Zack and JJ and for the trust our clients place in us, and I’m excited to continue strengthening those relationships as we grow together.” With this enhanced leadership structure, ZBeta is reinforcing its long-term vision: to redefine how the security function is designed, implemented, and experienced. ZBeta’s evolution “Conal and JJ have been instrumental in guiding ZBeta’s evolution,” Zack said. “Bringing them on board as principles honors the leadership they’ve shown and solidifies the direction we’re heading." "Their ability to pair strategic insight with client empathy is rare, and it’s at the heart of how we help organizations succeed. I’m looking forward to what the three of us can achieve together as we move into the next evolution of our business.”
A wedge barrier system is one of the most effective physical security measures for stopping unauthorized vehicles from accessing a restricted area. Designed for high-threat environments, these barriers prevent breaches that could cause significant harm to people, property, or critical infrastructure. Understanding what a wedge barrier is will help they determine if it’s the right solution for the security plan. What does a wedge barrier system do? A wedge barrier is a heavy-duty, ground-mounted barricade that rises from the ground into a high-strength, angled plate capable of stopping a moving vehicle. When deployed, the wedge shape creates a nearly impenetrable obstacle, able to bring even large, fast-moving vehicles to a stop within a short distance. What makes wedge barriers stand out from other types of traffic barriers, like bollards, tire shredders, or swing gates, is their combination of low visibility when not in use and high stopping power when deployed. Unlike fixed obstacles, wedge barriers can remain completely hidden below ground level until activated, allowing for unobstructed traffic flow during normal operations. Unlike visual deterrents, wedge barriers are crash-rated to meet rigorous standards, such as ASTM or Department of State (DOS) certifications. This means they’ve been tested to withstand direct impact from vehicles of various sizes and speeds without failing. How does a wedge barricade system work? When a security operator or automated system activates the barrier, hydraulic or electromechanical drives raise the steel plate to its protective position. Once fully deployed, the angled plate acts as a solid wall against an oncoming vehicle. In a breach attempt, the wedge barrier’s structural design forces the vehicle’s front end upward while absorbing and redistributing the energy of the impact. This combination of vehicle immobilization and energy dissipation makes them far more effective than lighter barricades or purely passive deterrents. Additionally, many models are engineered to integrate with advanced access control systems, enabling automated operation based on security alerts or preset protocols. Their rapid deployment speed, typically just a few seconds, makes them ideal for environments where both convenience and immediate threat response are critical. Where should wedge barricades be installed? Wedge barriers are most often used at vehicle access points where security and controlled entry are paramount. Common installations include: Government and Military Facilities: Where vehicle-borne threats are a concern, wedge barriers form part of multi-layered entry control points. Corporate Headquarters and Data Centers: To protect against both targeted attacks and unauthorized intrusion attempts. Airports and Transportation Hubs: To secure restricted zones while maintaining smooth traffic during permitted access times. Stadiums, Arenas, and Event Venues: For crowd safety and prevention of vehicular attacks during large gatherings. Critical Infrastructure Sites: Power plants, refineries, or water treatment facilities, where disruptions could have wide-reaching consequences. It’s important to note that wedge barriers work best as part of an integrated security system. A robust entrance barrier loses effectiveness if the surrounding perimeter is weak, such as a basic chain link fence that can be cut or driven through. Combining a wedge barrier with reinforced fencing, surveillance, and access control systems ensures complete protection rather than a single point of defense. Where are wedge barriers most effective? Wedge barriers are versatile in deployment and can be raised in numerous security scenarios, including: During high-alert security conditions In response to suspicious vehicle activity, such as a vehicle approaching at high speed or refusing to stop at checkpoints To block vehicle entry outside of authorized hours When crowd safety and controlled access are paramount In response to emergency incidents like nearby attacks, riots, or security breaches. By combining operational readiness with rapid activation, wedge barriers ensure that they can respond to both expected and unexpected security threats without compromising day-to-day traffic flow. Choose high-security wedge barriers that they can trust At Delta Scientific, they design and manufacture high-impact protection systems that meet and exceed stringent performance standards. The counter-terrorism barricades are trusted by U.S. government agencies, military installations, and critical facilities worldwide for their reliability, durability, and proven stopping power. Whether they’re securing a sensitive federal site or safeguarding a high-traffic public venue, a wedge barrier can be an essential component of the security strategy. Explore the range of high-security wedge barricades and find the model that best suits their security needs.
Integrated access control and security manufacturer TDSi now announces that from 1st January 2026, it will operate under the new name: TDSi by Hirsch. The change follows the global transformation of its parent company, Vitaprotech, into the Hirsch Group, unifying its security brands worldwide under one trusted name. TDSi’s integrated access control For more than 40 years, TDSi’s integrated access control solutions have been at the heart of thousands of installations across education, healthcare, government, and commercial environments in the UK and around the world. This proven expertise remains the foundation of what we deliver. Building on that strength, our further integration with Hirsch enhances what TDSi already offers. Customers will now benefit from access to Hirsch’s portfolio of high-security Access, Perimeter and Video solutions. Together, these additions create one of the most comprehensive and cohesive security offerings in the UK market, reinforcing and extending the trusted solutions our customers rely on. The new TDSi by Hirsch brand reflects Hirsch Group’s vision of harmonising, innovating, and internationalising its security solutions, while ensuring continuity and reliability for long‑standing customers. Hirsch’s global platform Richard Huison, UK Managing Director of Hirsch Secure and TDSi, commented: “TDSi has built a strong reputation in the UK and beyond, with installations in some of the most demanding environments worldwide. Becoming TDSi by Hirsch strengthens that legacy by combining our proven access control expertise with Hirsch’s global platform." "For our customers, nothing changes in terms of service or support, it is very much business as usual. What does change is the breadth of solutions we can now offer, from perimeter to core security, giving our partners and end‑users access to a truly unified security portfolio that is scalable, interoperable, and future‑ready.” TDSi moves into next chapter TDSi joined Vitaprotech Group in 2019, followed by Hirsch in 2024. The group of security specialists will adopt the globally recognized Hirsch name on 1st January 2026, instantly conveying premium positioning, federal-grade trust, and worldwide ambition. Eric Thord remains CEO, with Steven Humphreys as Deputy CEO, driving a clear vision: global strategy, local execution, delivering innovative, interoperable security solutions precisely tailored to each market. As TDSi moves into this next chapter as TDSi by Hirsch, its commitment to its customers, partners, and the wider security community remains unchanged. All existing products, services, support channels, and points of contact will continue as normal, ensuring complete continuity throughout the transition. Customer-first approach Customers can expect to see the TDSi by Hirsch Logo begin to roll out from early next year, marking the start of a gradual evolution rather than an overnight change. With the strength of the Hirsch Group behind it, TDSi is poised to deliver even greater value while continuing to operate with the same reliability, expertise, and customer-first approach that have defined the business for over four decades.
HiveWatch, the AI-driven physical security platform, announced it has appointed James Segil to its board of directors. Segil joins at a pivotal moment for the company following its recent $33 million Series B funding round, led by Anthos Capital with participation from Harmonic Growth Partners, Across Capital, and existing investors. Segil’s addition to the board brings invaluable strategic guidance from someone who disrupted a major physical security category – turning smartphones into security credentials. His hands-on experience in enterprise sales, partner ecosystems, and go-to-market execution will be instrumental in accelerating HiveWatch’s growth post-raise. Prior roles of Segil Segil is a serial entrepreneur and technology executive with a long track record of building and scaling companies across access control, security, and enterprise infrastructure. Most recently, he served as President and Co-Founder of Openpath Security, a next-generation physical access control provider acquired by Motorola Solutions in 2021. At Motorola Solutions, Segil led marketing and inside sales for the Video Security & Access Control division, helping the organization expand its global footprint and product adoption. next phase of growth Prior to Openpath, Segil co-founded and led multiple technology companies to successful exits, including EdgeCast Networks (acquired by Verizon), KnowledgeBase Solutions (acquired by Talisma), and Virtualis Systems (acquired by Allegiance Telecom). “Physical security is at an inflection point, and HiveWatch is at the forefront of defining what the modern GSOC should look like,” said Segil. “The team has built a platform that solves real-world problems for some of the world’s largest organizations. I’m excited to partner with Ryan, Jordan, and the HiveWatch board as the company accelerates into its next phase of growth.” HiveWatch's disconnected security tools HiveWatch brings together previously disconnected security tools - video, access control, alarms, sensors, threat intelligence, and more - into a single dashboard that fuels a streamlined security program. At the core is the company’s AI Operator, which learns each customer’s environment and dramatically reduces false alarms while accelerating incident response. HiveWatch protects assets across every continent, and an estimated 95% of Americans interact with a product, service, or brand protected by the company’s technology. Most complex enterprises “James has built category-defining companies across multiple verticals, and we welcome his valuable insights as we enter our next phase of growth,” said Ryan Schonfeld, Co-Founder & CEO of HiveWatch. “His track record scaling organizations will help us meet rising demand from many of the world’s most complex enterprises to protect their people and operations.”
Interface Systems, a pioneering managed service provider delivering remote video monitoring, commercial security systems, business intelligence, and network to multi-location enterprises, outlined the security and technology trends expected to define retail, restaurant, and commercial business safety in 2026. The company anticipates an increased shift toward proactive, exterior-focused measures, AI-driven analytics for operational efficiency, broader adoption of human oversight for AI, and heightened regulatory standards. Proactive deterrence will lead security strategy Commercial establishments such as retail and restaurant chains, car washes, automotive service centers, and other consumer-facing businesses are increasingly focused on securing their exteriors through preventive measures that detect and neutralize threats before they escalate. Advanced video analytics will be central to combating loitering, vandalism, and break-ins in real-time. By leveraging AI-driven detection in conjunction with remote video monitoring, businesses can stop crime before it happens and minimize the costs associated with damage and merchandise or equipment loss. Human oversight will enhance AI-enabled security AI-enabled cameras are now highly accurate in detection and classification, continually improving as they learn from data. However, the most resilient security strategies acknowledge that bad actors are also constantly evolving. Hence, businesses are likely to incorporate Security Operations Center (SOC) services to add a critical "human-in-the-loop." This hybrid model ensures expert analysts are available to handle exceptions, investigate persistent threats, and provide the oversight needed for a truly robust security posture. Regulatory Mandates Will Drive Security Upgrades Heightened scrutiny is expected in 2026 as both insurance providers and legislators tighten physical security standards. Retailers failing to demonstrate robust preventive measures face significant financial risks, including potential policy cancellations. For instance, New York jewelers are increasingly at risk of losing insurance coverage if they cannot certify that they have protections against specific high-tech threats, such as cell jamming. Simultaneously, legal mandates are expanding; the New York Retail Worker Safety Act (Senate Bill S.8358-B) now requires retailers to adopt comprehensive violence prevention programs and, for larger employers, install silent response buttons. Consequently, physical security companies must pivot to developing proactive solutions that meet these new regulatory baselines and satisfy insurers' stringent risk requirements. Video Analytics Will See Widespread Adoption Beyond safety, the use of video analytics to improve operational performance is expected to expand. Businesses will more widely adopt applications to monitor the speed of service, drive-thru throughput, food-handling compliance, store layout gaps, checkout wait times, and risk management scenarios such as slip-and-fall detection. These tools will help retailers and restaurants streamline operations, enhance guest experiences, and maintain a competitive edge. “Looking ahead to 2026, businesses that combine proactive deterrence, AI-driven video analytics, and expert human oversight will be best positioned to stay ahead of evolving threats,” said Sean Foley, Chief Revenue Officer at Interface Systems. “To ensure long-term success in retail and restaurant security, our focus remains on developing solutions that prevent crime, enhance efficiency, and maintain compliance.”
Verkada, a pioneer in AI-powered physical security technology, announced CapitalG is pioneering an investment at a $5.8 billion valuation - an increase of $1.3 billion since the announcement of its Series E in February. The investment will accelerate Verkada's AI capabilities and may also enable liquidity for employees, and comes as the company surpasses $1 billion in annualized bookings. AI-powered transformation "AI is fundamentally transforming how organizations protect people and places, and we're leading that transformation," said Filip Kaliszan, Co-Founder and CEO of Verkada. "Today, more than 2 million Verkada devices are online across 171 countries actively turning data into actionable intelligence that makes security and operations faster, smarter, and more efficient. As we continue building this platform for the long term, we want to give the brilliant team driving this AI-powered transformation the chance to realize some of the value they've created and earned today." How organizations protect people and infrastructure The $1 billion milestone reflects the massive market opportunity Verkada is capturing in enterprise physical security, but also underscores something much bigger: the trust, feedback, and partnership of the company's more than 30,000 customers across the world. "Verkada is fundamentally reshaping the future of physical security," said Derek Zanutto, general partner, CapitalG. "By infusing AI-driven intelligence into an industry long constrained by legacy, fragmented systems, Verkada has transformed security from a static cost center into a dynamic source of operational insights and efficiency." "Few companies become as mission-critical as Verkada has for its customers — from Fortune 500 enterprises to schools and hospitals — embedding themselves into the daily fabric of how organizations protect people and infrastructure. Filip and his team have built a category-defining platform with unmistakable product-market fit, and we're proud to back them as they scale their global footprint and extend their lead in this rapidly expanding market." New AI features and platform updates In September, Verkada introduced more than 60 new AI features and platform updates that signal the next chapter of disruption and innovation for the business: powering the entire workflow of security operators with agentic tools like AI-Powered Unified Timeline and Operator View. The customers who have joined Verkada on this journey have deployed over 2 million devices across 171 countries, with impact that is scaling rapidly: Verkada safely checks in 2 million visitors each month, powers 8 million door locks daily, and facilitates 3 intercom calls per second. "Our work is just getting started," added Kaliszan. "We're grateful to our team, our customers, and our investors for believing in this mission – and we're excited for the next chapter of growth."


Expert commentary
A lot has been said about door security — from reinforced door frames to locking mechanisms to the door construction — all of which is crucial. But what security measures are in place beyond the perimeter door in case the worst happens and it’s somehow breached? Hopefully, many more levels of access control are in place to prevent, or at least slow down, a perpetrator’s ability to compromise protected assets. Additional interior layers Interior security measures must operate as an integrated, multilayered system that eliminates single points of failure. These inner protections safeguard not only the physical infrastructure but also the operational integrity, confidentiality, and availability of the systems housed within. Beyond simply preventing unauthorized individuals from getting inside, the goal is to create a controlled, monitored, and resilient environment in which every movement, action, and access attempt is verified, logged, and, when necessary, challenged. As modern buildings, data centers, and infrastructure sites host critical functions and potentially sensitive intellectual property, these additional interior layers become essential to protecting both organizations and their proprietary assets. Interior security controls One of the most important interior security controls is granular access segmentation One of the most important interior security controls is granular access segmentation. While a perimeter door may verify an individual’s right to enter the building, the interior should treat every room, cage, and corridor as its own security zone. Role-based access control and strict least-privilege principles should limit personnel to only the areas they absolutely require. For example, a network engineer may need access to routing equipment but not storage racks; a janitorial contractor might be allowed into shared hallways but not any equipment rooms at all. These access restrictions should be enforced using intelligent keys, biometric scanners, mantraps, and, at particularly sensitive locations, two-factor authentication. Segmenting access in this way limits the potential damage from a single compromised badge or insider threat and ensures that a single breach does not cascade into a total facility compromise. Low-light and infrared capabilities Biometric authentication within a building adds a layer of confidence beyond perimeter controls. Technologies such as facial identification help prevent the use of stolen, cloned, or borrowed credentials. These systems complement anti-tailgating measures, such as sally ports or mantraps, which ensure that only one authenticated person passes through at a time. Interior surveillance is another essential measure. High-resolution cameras equipped with low-light and infrared capabilities should cover every hallway, door, rack row, and logistical pathway. Camera feeds must be continuously recorded, and retention policies must align with regulatory requirements. Intelligent video analytics, such as motion pattern recognition and heat mapping, enable the detection of atypical behaviors — such as someone lingering near a cage they are not authorized to access or movement at odd hours. Physical tamper-detection mechanisms Cabinet security provides a vital layer of granularity in the access hierarchy, ensuring that even within secure facilities Integrating surveillance with access control systems creates a strong correlation; when someone successfully passes through a secured door and enters a room, the system can track whether the number of people seen on camera matches the number authenticated, and alert security if a discrepancy occurs. However, it is increasingly important that access control not stop at the room level, because the most sensitive assets are often housed in cabinets, racks, or storage units within already-secured spaces. Cabinet security provides a vital layer of granularity in the access hierarchy, ensuring that even within secure facilities, assets remain protected. Physical tamper-detection mechanisms on racks, cable trays, and server chassis add another dimension: they can detect if a panel is opened, a cable is unplugged, or a device is removed without authorization. Secure destruction protocols Another internal measure is the use of secure storage and chain-of-custody procedures for any components that contain intellectual property or personally identifiable information. Hard drives, backup media, and even printouts should be stored in locked cabinets accessible only to people with proper clearance. When decommissioning hardware, secure destruction protocols such as shredding or degaussing should be performed in controlled areas and thoroughly logged. Every movement of sensitive equipment should be traceable, from installation through end-of-life disposal. Such processes reduce the risk of data leakage from improperly discarded or undocumented devices. Consequences of improper behavior Staff should be trained to recognize social engineering attempts, unusual behaviors, and procedural deviations Operational security procedures also contribute significantly to interior protection. Background checks, ongoing employee vetting, and mandatory training ensure that individuals with access to sensitive areas understand their responsibilities and the consequences of improper behavior. Staff should be trained to recognize social engineering attempts, unusual behaviors, and procedural deviations. Maintaining a strict visitor escort policy prevents non-employees from wandering unobserved. All visitors should wear highly visible identification badges and be monitored continuously by authorized personnel. The building's interior should be treated as a controlled environment at all times, not merely a workspace. Continuous auditing and logging form Continuous auditing and logging form another pillar of interior security. Access logs from intelligent keys, biometrics, video, and environmental systems must be stored securely and evaluated regularly for anomalies. Automated systems can flag irregular patterns, such as repeated attempts to access unauthorized areas or entering rooms at odd hours. Manual audits validate that the access control list remains accurate, that no inactive or former employees retain credentials, and that documentation matches reality on the floor. These logs are indispensable during investigations, compliance assessments, and incident response efforts. Interior security controls Security networks should be isolated from the main IT networks to prevent a cyber incident Finally, redundancy and resiliency must be built into interior security controls. Electrical power for access control, intelligent keys, biometrics, and video systems should be backed by secondary sources, generators, or uninterruptible power supplies. Security networks should be isolated from the main IT networks to prevent a cyber incident from disabling physical protections. The goal is to ensure that interior security remains functional even during outages, disasters, or cyber disruptions. Multilayered approach Together, these additional interior measures create a layered defense that makes a secure building, data center, or infrastructure site extremely difficult to compromise. Rather than relying on a single barrier at the entrance, the environment becomes an ecosystem of mutually reinforcing controls — physical, operational, digital, and procedural. This multilayered approach allows structures to maintain high levels of protection even as threats evolve, ensuring that the systems inside remain secure, resilient, and trustworthy.
The terrorism threat in the UK is very real. In fact, since July 2019, the threat level has never dropped lower than “substantial” or “severe.” To ensure preparedness across public places and events, the UK government has introduced the new Terrorism (Protection of Premises) Act 2025, more commonly known as Martyn’s Law in memory of Martyn Hett, a victim of the 2017 Manchester Arena bombing. Overarching aim The new legislation requires operators of public spaces and events to immediately assess and improve their readiness to respond to a terrorist attack. The overarching aim: being better prepared, protected and ready to respond should an attack occur. Everything from busy shopping centers to large stadiums must comply with Martyn’s Law by April 2027, and the Security Industry Authority (SIA) is charged with enforcing the rules. Upgraded security systems The smaller venues and events are only required to enforce low-cost solutions with no physical measures There are different rules depending on the capacity of public premises or the event, ranging from a standard-duty premises (200 – 799 people, including staff) to an enhanced-duty premise (over 800). The smaller venues and events are only required to implement low-cost solutions with no physical measures. Enhanced environments, however, must provide monitoring in and around the facility and document public protection measures. Many organizations will likely invest in upgraded security systems. However, effective responses depend not only on hardware but also on situational awareness and training, helping staff identify potential threats and respond effectively under pressure. Physical security information management systems Terror-related attacks are rare and unpredictable, and the most experienced personnel are not always on shift when something does occur. Even if they are, the most seasoned security professionals can’t ensure every decision they make is the right one. One solution gaining attention is physical security information management (PSIM) systems, which integrate siloed security tools — such as CCTV, access control, and fire sensors — into a unified platform. PSIMs enable rapid information processing, automated workflows and coordinated responses to incidents, whether routine or critical. Use PSIMs to handle emergencies PSIM systems have been around for many years and have been embraced by large airports and mass transit organizations PSIM systems have been around for many years and have been embraced by large airports, mass transit organizations and critical infrastructure companies. However, these systems are ideally suited to any larger-scale environment, such as those classified as an enhanced-duty premise by Martyn’s Law. For example, airports use PSIMs to handle emergencies, locate missing persons or assess potential threats like unattended luggage. Similarly, PSIMs can improve situational awareness for stadiums, shopping centers and event venues, aiding crowd management, emergency evacuations and collaboration with police or emergency services. External stakeholder intervention Should an incident require external stakeholder intervention, the PSIM becomes a mission-critical collaboration tool, enabling real-time information (including video footage) to be shared with decision-makers, emergency control rooms and first responders en route to the scene. This ensures they arrive with the appropriate resources and can deploy faster to the right places. PSIM systems also facilitate post-incident analysis, helping organizations improve protocols, demonstrate compliance and fulfill their duty of care. Impacted by terror-related tragedies Martyn’s Law aims to eliminate the complacent mindset of “it won’t happen here” when assessing the risks associated with public gatherings. Communities impacted by terror-related tragedies serve as a stark reminder that such incidents can and do occur. Within the security sector, it is crucial to promote discussions on how new approaches, technologies, and training can enhance preparedness. Equally important is the responsibility to raise awareness about Martyn’s Law and its role in fostering safer public spaces.
The sheer volume of smart locks, lock management systems, connected readers and an increasing array of Internet of Things (IoT) devices complicates the issuance and management of certificates that are foundational to establishing trust between a device and the credential used to access it. That’s why more companies are turning to PKIaaS for IoT devices. But there’s another reason to consider PKIaaS: the rise of quantum computing. Secure digital communications Gartner predicts that the pace of quantum computing will render asymmetric cryptography systems PKI certificates form the backbone of secure digital communications, but Gartner predicts that the pace of quantum computing will render asymmetric cryptography systems unsafe by 2029 and could render all current cryptography unsafe by 2034. As with any software implementation, there are pitfalls to avoid, including vendors that use proprietary technology that’s incompatible with other systems and “gotcha” pricing tactics where a slight increase in certificate usage triggers a massive increase in pricing. However, the time to implement PKIaaS is now. Physical security faces growing cyber threats Although ransomware attacks directly on computing infrastructure dominate business headlines, physical security systems are also under threat. An HID survey of over 1,200 security professionals, end-users and executives shows that 75% reported threats to their physical security systems in the past year, as these systems are more tightly integrated with company IT networks. Until recently, most physical access control systems (PACS) were proprietary and worked only on the specific systems they were designed to interact with. However, the movement toward open supervised device protocol (OSDP) revolutionized the field, allowing companies to integrate and control devices from different vendors while improving compatibility and security. PACS and IoT devices PKIaaS makes sense as the number of digital certificates needed to power PACS and IoT devices As a result, 40% of companies plan to either update or change access control systems in the next year, with 21% emphasizing the need for open standards like OSDP to both improve interoperability and future-proof their systems. When asked about reasons for a proposed upgrade, more than half cited convenience, while another 40% sought to improve their overall security posture. PKIaaS makes sense as the number of digital certificates needed to power PACS and IoT devices continues to increase, promoting security and reducing manual processes related to tracking certificates. Regulatory compliance demands automation and agility Companies also face increased regulatory pressures regarding technology in general — and certificates in particular. The European Union’s Cyber Resilience Act sets mandatory cybersecurity standards for manufacturers and retailers, covering the planning, design, development and maintenance of products throughout the entire value chain. Certain high-risk products must undergo third-party evaluation by an authorized body before being approved for sale in the EU. EU Cybersecurity Act shows a unified certificate framework for ICT products, services, and processes More specifically, the EU Cybersecurity Act establishes a unified certification framework for information and communications technology (ICT) products, services, and processes. Businesses operating in the EU will benefit from a “certify once, recognized everywhere” approach, meaning that approved ICT offerings will be accepted across all EU member states. Given the global nature of PACS, these regulations likely will impact companies well beyond the EU, much like the general data protection regulation on websites has. These changes, when considered together with rapid advancements in quantum computing, underscore the need for a unified certification solution such as PKIaaS to handle increased — and increasingly complex — certificate compliance. A path to PKI modernization Modernizing PKI through a PKIaaS model doesn’t have to be difficult. With a clear and phased approach, most organizations can transition smoothly while reducing risk and improving efficiency. It starts with a quick assessment of current certificate usage to understand where certificates are issued, how they’re renewed and any gaps in coverage. From there, it's about defining what you need and selecting a trusted partner. Look for a solution that integrates well with your existing systems, supports automation and scales as your needs grow. In terms of partners, not all PKIaaS vendors are the same. Look for one with a strong security track record and predictable pricing, which will simplify both onboarding and long-term management. When it comes to vetting vendors, ask the following questions: Is the solution scalable? The trend toward future-proof installations has never been greater. As the number of certificates increases, any PKIaaS solution must be able to grow in concert. How will pricing change as certificate volume grows? Some solutions are priced in tiers by the number of certificates. If a company exceeds that maximum by even a single certificate, it owes not only the price difference between tiers, but it will also be expected to pay for that tier the following year, which can bring a significant financial surprise. How are CAs accessed and stored? Look for companies that can provide long-term offline secure storage of certificates that can also track when CA keys are accessed. What support is included in the PKIaaS? Specifically ask vendors about up-front costs for implementation and onboarding to get a real apples-to-apples comparison among partners. Step-by-step replacement of manual processes A pragmatic approach allows corps to move quickly and confidently from legacy PKI to a scalable Once a vendor in place, start with a focused rollout, e.g., automating certificate renewals for internal systems or a specific business unit. Once the pilot is complete, expand automation with a step-by-step replacement of manual processes to limit operational disruptions. Finally, as PKIaaS becomes embedded in day-to-day operations, it’s important to align it with broader security governance. Establishing regular reporting and clear policies, as well as future-proofing for quantum-safe cryptography to ensure long-term resilience and compliance without adding complexity. This phased, pragmatic approach allows organizations to move quickly and confidently from legacy PKI to a scalable, secure and future-ready solution. A necessary upgrade According to an analyst report, manual certificate management can cost organizations up to $2.5 million annually in labor and outage-related expenses. While automation reduces these costs by up to 65%, the real challenge in IoT environments lies in managing scale. With device lifecycles often spanning decades and certificate volumes reaching millions — especially across distributed, resource-constrained endpoints — manual PKI processes and legacy infrastructure simply can't keep up. The convergence of regulatory mandates, quantum computing threats and rising cyber risks to connected physical systems makes scalable, cloud-based PKIaaS not just a strategic advantage, but a foundational requirement for secure IoT deployments.
Security beat
Drones are poised to fill long-standing gaps in physical security. Fixed cameras leave blind spots, and human guards cannot quickly cover large or complex properties during high-risk moments. Drones fill the gaps, providing a missing mobile layer, offering unmatched speed, broad aerial visibility, and proactive coverage that elevates security from reactive to truly responsive and deterrent. As an added element in security systems, drones complement fixed cameras, access control, and license plate recognition (LPR) systems by serving as dynamic, rapid-response assets that reach areas other technologies cannot. Integrated with existing alarms and sensors, drones can auto-launch on triggers to deliver near-instant, real-time aerial video for accurate threat verification, giving security teams critical information before taking action. Drones as first responders Drones as first responders (DFR) are a new tool in Flock’s suite of security technologies “Drones are a natural fit for physical security because they provide teams with fast, flexible visibility that fixed cameras and human patrols cannot always deliver, especially on large properties,” says Keith Kauffman, Senior Director of DFR Strategy at Flock Safety. Drones as first responders (DFR) are a new tool in Flock’s suite of security technologies, which includes LPR, video surveillance, and gunshot detection systems. “Drones act as a force multiplier, improving coverage without increasing head count,” says Kauffman. “Scaling is easy with the ability for one pilot to control multiple drones stationed at multiple locations.” Drones as a force multiplier Drones reduce manpower needs by offering wide-area coverage that would normally require several guards or patrol vehicles. Drones boost security team productivity and safety by automating the most dangerous and tedious tasks, such as alarm verification. Acting as a first responder, a drone can clear a significant portion of false alarms, allowing human guards to concentrate on high-priority roles, complex issues, or confirmed intrusions with real-time aerial intelligence. This improves personnel deployment and cuts down workload, risk, and costly overtime. Drones also significantly improve efficiency and safety for security personnel, says Kauffman. A drone system delivers real-time aerial intelligence in seconds, enabling guards to respond wisely and safely. Initial threat verification Some drone systems' yearly costs are similar to a single mid-level guard's salary Some drone systems' yearly costs are similar to a single mid-level guard's salary, but they can cover up to 38 square miles. This investment provides ROI by reducing large-scale losses and allowing human guards to focus on high-touch roles, while the drone handles initial threat verification. Flock Safety entered the drone space after acquiring Aerodome DFR in October 2024, with their private-sector drone as automated security (DAS) system rolling out in Q3 2025. And because the drones plug directly into FlockOS and work alongside other tools like license plate recognition (LPR) and gunshot detection, they can launch automatically on alerts, creating a smarter, faster response workflow. Immediate intelligence to combat false alarms Drones fundamentally change false alarm management by providing security teams with immediate, real-time aerial intelligence. When an alarm triggers, the drone can be dispatched to the exact location in seconds, allowing operators to verify instantly the threat's legitimacy via a live HD or thermal video feed. This capability enables staff to safely clear or ignore false alarms remotely, preventing guards from wasting time and resources on unnecessary, lengthy, or potentially dangerous physical checks. This process can significantly reduce alarm fatigue and allow personnel to reallocate their time to genuine security threats. Emerging drone use cases enhance security operations Emerging drone use cases enhance security operations by integrating with existing systems and enabling novel applications. One key area is Post-Storm Damage Assessment, where drones provide rapid, safe aerial visuals of expansive sites, documenting damage for insurance claims far faster than ground inspections. Another area is Ecosystem Integration via platforms such as FlockOS, where the drone automatically launches in response to alerts from other security sensors (LPR, gunshot detection). This creates a powerful, automated workflow that unifies responses, enabling quicker incident interruption, better evidence capture, and a proactive security posture without increasing the number of human patrol staff. Evolving regulations expanding drone usage Evolving FAA regulations and corporate airspace policies impact the usage of drones Evolving Federal Aviation Administration (FAA) regulations and corporate airspace policies impact the usage of drones. Today, operating drones beyond the visual line of sight (BVLOS), at night, and over-people/roadway operations requires special FAA waivers. However, the trend — Remote ID, expanded FAA Part 107 allowances, and growing BVLOS exemptions proven in drones as first responders (DFR) — reduces overhead and allows more automation. Combined with enterprise standard operating procedures (SOPs), geofencing, and data governance, drone adopters can standardize flights, minimize risk, and integrate with other technologies. “In practice, that means automated dock-based dispatch on verified alerts, scheduled perimeter sweeps, and incident-to-incident coverage without on-site pilots,” says Kauffman. “The results are faster detection-to-dispatch, stronger evidentiary chains, and lower costs per incident — unlocking 24/7 remote operations across campuses, logistics, and sites.” Winning Over Public Acceptance Public perception plays an important role in how communities embrace drone technology, which is why transparency and clear policy are essential. When employees and community members understand the drone’s purpose — responding to alarms, patrolling after hours, and deterring crime — they tend to view it much as they do security cameras or access control: a safety tool, not surveillance. Flock’s system is event-driven, privacy-minded, and used only by authorized personnel, and every flight is logged, documented, and fully audit-traceable for accountability. “With clear communication and responsible use, drones become a reassuring layer of protection rather than a cause for concern,” says Kauffman. Drones are extremely safe, actually reducing human risk by acting as a first responder to scout ahead of personnel. They come with layers of protection, such as geofencing, obstacle avoidance, precision landing, autonomous deconfliction with aircraft, and automated safety modes. Smartest approach For security teams considering adding drones, the smartest approach is to choose a system built specifically for 24/7 security operations. That usually means the drone provider handles FAA paperwork, writes clear procedures, develops sound policy, and trains customers’ staff so everything runs smoothly. “With the right partner, drones become a safe, compliant, and incredibly helpful part of your security toolkit,” says Kauffman. Flock ramps up drone production Flock Safety’s immediate focus is ramping production of its U.S.-designed and assembled Flock Alpha hardware, which is already NDAA-compliant and built to meet the growing demand for American-made drone solutions. At the same time, the next six to 12 months will center on releasing key software updates, such as automated scheduled patrols. Together, increased hardware production and these software advancements will move the DAS product line toward full capability and broader commercial availability. Flock DAS Flock DAS essentially provides a guard’s vantage point from above, with the ability to instantly fly to any corner of a property. “And it doesn’t sleep on duty or call in sick,” says Kauffman. “Picture your traditional security measures: cameras are your static sentries; guards are your roaming patrollers. Now add Flock DAS: it’s your mobile, flying camera that can respond anywhere, anytime.” Just as a dispatcher coordinates police calls, Flock DAS serves as an aerial dispatcher for the security team, triaging alerts and providing eyes on the scene before anyone sets foot into potential danger. It gives the security team immediate, property-wide awareness so they can make safer, more informed decisions during any incident.
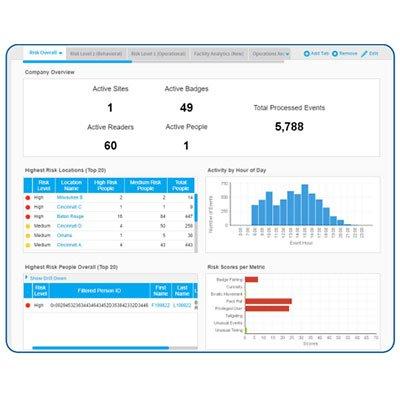
Multiple technology trends are transforming the physical access control market. There is a fundamental shift away from physical cards and keys toward digital identities — mobile credentials, digital wallets, biometrics, and cloud-native access platforms. These next generation access solutions are radically reshaping how buildings operate, protect staff, and perform functionally. At the same time, AI and analytics solutions are being layered onto these physical access control systems to support predictive threat detection and behavioral insights. Access data itself is becoming an asset for sustainability, space optimization, and smart building initiatives. Risk, impact operations and experience The annual HID Global Security and Identity Trends Report highlights these and other issues The annual HID Global Security and Identity Trends Report highlights these and other issues. The survey cites improving user convenience as a priority for nearly half of organizations, while 41% are focused on simplifying administration, and 28% struggle with system integration. These are not theoretical challenges, they are day‑to‑day friction points that add cost, increase risk, impact operations and experience, and, of course, must be addressed. HID Global’s commercial focus HID Global’s commercial focus is to help organizations digitize their access control — with mobile identities, biometrics, and cloud platforms — and then to use the data to deliver more value. “We are turning access control from an operational cost into a software-driven asset that improves efficiency, supports Environmental, Social, and Governance (ESG) goals and even creates new revenue opportunities,” says Steven Commander, HID Global’s Head of Consultant Relations. The impact of digital transformation Digital transformation is the method of moving access control from hardware and physical credentials Digital transformation is in the process of moving access control from hardware and physical credentials to a software-driven, integrated experience. The transformation strengthens security while also improving user convenience — transforming the “pavement to the desk” journey. HID enables this shift through mobile credentials, biometrics, cloud-native platforms, and solutions that allow third-party applications to run on door hardware. “This helps customers turn access data into operational and commercial outcomes, while also improving the overall user experience,” says Commander. Digital transformation in access control is not focused on chasing the latest trends. Rather, transformation is about turning software, data and integration into outcomes that matter to customers, says HID. “Security becomes stronger and more adaptive,” says Commander. “Operations become simpler and more cost‑effective. Experiences become seamless and consistent. Sustainability moves from ambition to action. And the financial case becomes clearer as efficiencies are banked and new value streams emerge.” The challenge of futureproofing with long lifecycles Given that physical security technologies will be in place for 15 to 20 years, it is important to plan for how systems can evolve over time. Considering how rapidly security threats, compliance standards, and user expectations change, 15 to 20 years is a long time. The decisions made at the beginning of a system’s lifecycle can either limit flexibility later (which will be costly) or enable long-term adaptability. Support for open standards such as Open Supervised Device Protocol (OSDP) is therefore important Choosing products and platforms that are open, interoperable, and designed for updates can enable future-proof projects. Support for open standards such as Open Supervised Device Protocol (OSDP) is therefore important. In addition, systems built on open controller platforms — such as Mercury — enable organizations to switch software providers or expand functionality without replacing core door hardware. Architectural openness is key to system lifecycles and maximizing the return on investment (ROI) from a chosen solution. Digital credentials and mobile access Flexibility and upgradeability should also be top of mind when it comes to endpoints like access control readers. While RFID cards are still commonplace, there is a clear trend toward digital credentials and mobile access. Readers that support both allow organizations to transition at their own pace, without committing to a full system overhaul. A long system lifecycle does not mean technology should remain static. Security, particularly cybersecurity, demands more frequent updates. Technologies that support firmware upgrades in the field extend the value of a deployment while helping organizations keep pace with emerging threats. In that sense, lifecycle thinking is not just about longevity — it’s about maintaining resilience and readiness over time. Applying biometrics and mobile identities Biometrics is becoming mainstream as a credential alternative, strengthening security without adding friction Biometrics is becoming mainstream as a credential alternative, strengthening security without adding friction. Many organizations are now deploying biometrics to support fast, seamless access journeys, with adoption already around 39% in access control according to HID’s recent research. In addition, 80% of organizations surveyed expect to deploy mobile identities within the next five years. Full technology integration enables tap‑to‑access without opening an app; the user journey becomes faster, safer, and more convenient. “It is where the industry is headed and we are at the vanguard of this,” says Commander. Ongoing challenge of cybersecurity At HID Global, cybersecurity is embedded into everything, from corporate processes and development practices to the solutions they bring to market. “Our approach ensures that customers can strengthen their overall security posture, not only by deploying secure products but by benefitting from HID’s commitment to the highest industry standards,” says Commander. HID holds multiple globally recognized certifications, including ISO 27001, ISO 14298, SOC Type 2, and CSA STAR, which demonstrate their robust information security and cloud security practices. In addition, HID’s SEOS® secure chipset is independently SEAL-certified, providing one of the most advanced levels of protection available on the market today. “Ultimately, this means organizations are not just purchasing isolated secure products; they are implementing solutions developed and delivered within a comprehensive, cybersecure framework,” says Commander. “When deployed according to best practices, HID solutions enable customers to achieve the highest levels of resilience against evolving physical and cyber threats.” Developing green and sustainable solutions A huge amount of waste is generated from the manufacture of plastic RFID access cards Digital credentials align with the sustainable solutions that everyone wants. A huge amount of waste is generated from the manufacture of plastic RFID access cards. Over 550 million access cards are sold annually. This creates 2,700 tons of plastic waste and 11,400 tons of carbon, based on a PVC card weighing 5 grams. Therefore, digital credentials self-evidently reduce the reliance on plastic cards (helping reduce carbon emissions by up to 75% according to HID’s research), while leveraging access control system data supports energy optimization by shutting down or reducing systems in unused spaces. Energy use and CO₂ emissions can be cut dramatically, showing how access systems can contribute to sustainability goals and green building certification. What is the latest in smart buildings? Smart buildings increasingly rely on mobile access control as the backbone for digital services. Real-time access data enables new services such as automated room bookings, HVAC control, lift/elevator calling, e-bike hiring, and so on. Smart buildings increasingly rely on mobile access control as the backbone for digital services The financial upside is clear; smart, digitally transformed buildings can deliver around 8% higher yields per square foot versus traditional office space. Operational savings accrue from reduced administration, the removal of card production and shipping, and lighter IT support. This creates a value cycle — better experiences drive adoption, adoption fuels monetization, and monetization funds further improvements. Achieving technology impact in the real world One standout project is One Bangkok – a $3.9 billion mixed-use development in Thailand – which demonstrates the scale of what can be achieved when access control data is used for optimization, particularly when it comes to monitoring facilities usage and occupier behaviors. By switching lights off or lowering the temperature in unused rooms, for example, the One Bangkok building demonstrates this potential with a 22% reduction in energy consumption, saving 17,000 MWh and 9,000 tons of CO₂ annually. Sustainability is a key factor in contributing to how properties are valued. And sustainability extends far beyond digital credentials having a lower environmental impact than plastic cards. Buildings with recognized sustainability certifications often command rental premiums of around 6%, and three‑quarters of security decision‑makers now consider environmental impact in their procurement assessments.
The speed, scale and sophistication of today's safety threats can outpace human capacity to keep up. The implementation of artificial intelligence (AI) is essential to keep people safer and must be designed and deployed transparently. The complexity of today’s AI applications is expanding in physical security, with more AI models leveraging data to tune performance and using third-party application programming interfaces (APIs). In this context, it can be difficult to find clear, consolidated, transparent information about AI’s use in enterprise security technologies. How AI is used across the company’s technologies Motorola Solutions is taking a layered approach to help users easily understand how AI is used Motorola Solutions is taking a layered approach to help users easily understand how AI is used across the company’s technologies, starting at a high level with AI labels affixed to products, and getting more granular with structured information about AI testing, assessments and more. “We are aiming to provide clarity to the user and those they help protect to increase trust and transparency in AI innovation,” says Hamish Dobson, Corporate Vice President, Avigilon and Pelco Products, Motorola Solutions. Importance of AI transparency The AI labels, which have been compared to nutrition labels used on consumer products, are designed to be clear and easy-to-read at a glance. Each label explains the type of AI used, who owns the data processed, human controls, and the purpose behind the product’s specific application of AI. “We regularly seek input from external stakeholders – including customers, partners, consultants, investors, policymakers, and community members – on many aspects of our business,” says Dobson. “We briefed select customers and industry groups on our AI labels initiative and received positive feedback.” He continues: “Like us, customers and industry groups understand the importance of AI transparency and are looking for ways to clarify AI usage in public safety and enterprise security.” AI transparency efforts AI transparency efforts have taken on a variety of forms such as model cards, transparency notes Across industry, AI transparency efforts have taken on a variety of forms such as model cards, transparency notes and, in Motorola’s case, AI labels. The company pledges to continue to engage with industry participants on efforts to advance the overall pace, adoption, and maturity of responsible innovation initiatives across the industry, says Dobson. The AI labels help to increase dialogue and understanding of AI’s use in the security technologies that help to keep people safer. Motorola Solutions is looking to inform customers about how AI is being used to automate mundane tasks and prioritize information that may be critical to performing their roles. Motorola’s L6Q license plate recognition For example, a business using Motorola’s L6Q license plate recognition camera in its parking lot could view the AI label and see that AI is used to help recognize license plate characteristics of vehicles within its view. The label would also help the customer understand that they maintain ownership and control of the data AI can process and can determine the data retention period. What type of AI is being used AI outputs should have human oversight, and a user should understand the sources of data “By providing knowledge of where and what type of AI is being used, our customers can better understand what they are deploying, configure settings appropriately and inform their constituents,” says Dobson. AI-assisted experiences should be designed to be accountable and transparent, according to Motorola Solutions. AI outputs should have human oversight, and a user should understand the sources of data from which suggestions were drawn. AI labels highlight that the data AI can access is customer-owned and controlled, helping to increase confidence that AI outputs are based on that customer's specific data. Responsible and ethical use of technologies The AI label’s “first or third party model” section explains the source of the AI model. A first-party model is developed in-house by Motorola Solutions. A third-party model is developed outside of Motorola Solutions and made available by a third-party vendor; however, it may be customized by Motorola Solutions. MTAC is a multidisciplinary group that advises the company on the reliable and ethical use of technologies “This section aims to foster dialog with our customers around Motorola Solutions’ role in testing, training, and refining the AI model or models used in our products,” says Dobson. Helping to propel the AI Label initiative, the Motorola Solutions Technology Advisory Committee (MTAC) is a multidisciplinary group that advises the company on the responsible and ethical use of technologies, including data and AI. Industry trends in technology’s responsible design MTAC continuously explores new ways to enhance trust with customers and the communities they serve, while helping to keep Motorola Solutions a step ahead of industry trends in technology’s responsible design, development, and use, according to the company. The MTAC “Blueprint” sets out the core principles that drive the approach. “We’re excited by the opportunity to continue to lead in this area through additional innovation, thought leadership, and stakeholder engagement,” says Dobson. Human-centered design New capabilities specifically augment human skills and capacity with the goal of helping humans Rather than replacing human decision-making, AI technologies will, in fact, augment it. Human-centered design is a core principle of the responsible technology “Blueprint” Motorola Solutions is developing. New capabilities specifically augment human skills and capacity with the goal of helping humans spend time on what matters most during a safety or security incident, applying their unique judgment, knowledge, and oversight in high-stakes environments. AI’s recommendations “We purposefully deploy AI to augment human focus, effort and performance,” says Dobson. “We design AI to maximize human strengths like judgment and reasoning and to adapt to changing roles, tasks, risk levels, and cognitive states while keeping AI outputs traceable and transparent, whereby the user can easily see, check and override AI’s recommendations.”
Case studies
Xtract One Technologies announced its SmartGateway has been selected by Nova Scotia Health to strengthen security measures and provide AI-powered weapons detection across facilities province-wide, with an initial order of 25 systems. Nova Scotia Health, in tandem with its nurses’ union, is working to modernize and strengthen security across its facilities to ensure a safe environment for all patients, visitors, and staff. Adopting and deploying advanced technologies like SmartGateway is an important step toward achieving that goal. Safe and secure health care By helping to limit the number of potentially dangerous items entering their hospitals, this technology supports its commitment to providing safe and secure health care. Xtract One was selected for its proven efficacy to accurately detect knives, a top priority for the organization. Previously tested in Truro, Nova Scotia, over a 12-day trial period, SmartGateway successfully scanned 7,400 individuals entering the facility and detected 49 prohibited items during that period, mostly pocket knives and box cutters. Deploying SmartGateway “Violence against healthcare workers is a challenge that persists and demands addressing. By deploying SmartGateway, Nova Scotia Health is setting an important example for what it means to take meaningful action to protect frontline healthcare workers, patients, and visitors,” said Peter Evans, CEO of Xtract One. “This installation marks another key step in our expanding work with Canadian healthcare organizations, having deployed in Manitoba earlier this year. We look forward to continuing to deliver effective threat detection as more providers take proactive measures to prioritize security and peace of mind for their teams.” Overall approach to security “Our goal is to deliver first class healthcare, and ensuring the safety of all who enter our facilities is a critical step in providing that service,” said Dean Stienburg, Director of Security for Nova Scotia Health. “With SmartGateway, we’re making tangible strides in bolstering our overall approach to security. We were impressed by the system’s effectiveness during the trial period and are looking forward to the deployment helping us mitigate and respond to the threats of today’s environment.” Maximising security screening outcomes SmartGateway delivers fast, discreet, and accurate individual screening, utilizing AI-powered sensors to unobtrusively scan for weapons and other prohibited items upon entry. This technology replaces intimidating, traditional metal detectors and mitigates the need for individuals to remove personal items. This prioritizes individual privacy and comfort, all while maximizing security screening outcomes. SmartGateway is designed to enable seamless passage through checkpoints and promote the uninterrupted flow of movement.
Set in 33 hectares of woodland on the edge of Dartmoor National Park, the zoo is home to an impressive variety of exotic and native animals, including Amur tigers, African lions, and Amur leopards. New patented master key system On-site challenges before the introduction of the new patented master key system. Before implementing the new master key system, the zoo faced the challenge of ensuring secure and efficient access control to sensitive areas, particularly enclosures with potentially dangerous animals. The previous master key systems were outdated and did not provide the necessary security and flexibility required for the zoo's daily operations. Installation of EPS NP and its advantages The EVVA EPS NP system was installed in collaboration with local partner Sir Fix-a-Lock. This system offers robust patent protection, long-term key control and high reliability in demanding environments. A total of 192 Asec weatherproof padlocks were installed in a 6-level master key system. The flexibility of EPS NP enabled graduated key control across the entire site, including special levels for animal care. Advantages of the new patented key system for the zoo Thanks to the new master key system, the zoo has been able to implement a secure and practical solution that enables staff to work efficiently while maintaining strict access controls. The color-coded keys make it easy to quickly identify access authorisations, which is particularly advantageous in security-critical areas. The Asec weatherproof padlocks also offer high resistance to environmental influences, ensuring the longevity of the system. "EPS has revolutionized our access control and gives us the security and flexibility we need." The project at Dartmoor Zoo impressively demonstrates how EVVA's flexible master key systems can be adapted to specific requirements to ensure security, control and long-term protection.
Crime analysts at DeterTech, a trusted security partner to critical infrastructure and law enforcement, are warning of a major rise in reported incidents of copper and cable theft across Greater Manchester and Lancashire. Believed to be orchestrated by Organized Crime Groups (OCGs), the direct to threat to UK infrastructure is being driven by the sustained high price of copper, which hit $10,300 per ton on 25th September 2025 – the highest recorded price since April 2024. Cable theft from rail network Cable theft from the rail network in Wigan resulted in widespread passenger disruption There have been six key incidents reported in the North-West of England since 14th September, impacting energy, transport, utilities and renewables infrastructure. For example, in Bolton a site was targeted for 33 kv copper cable valued at just under £500,000. Meanwhile, the theft of a significant quantity of string cable from a solar farm near Preston reduced the site’s energy output by around 40% risking the local power supply. Back in August, cable theft from the rail network in Wigan resulted in widespread passenger disruption and estimated losses to the UK economy of more than £1million. Deal with the threats Rachael Oakley, Head of Crime Intelligence, DeterTech, says: "The substantial price of copper is unfortunately driving high rates of offending across all forms of critical infrastructure. In order to protect energy, utilities, transport, and renewable infrastructure, it is imperative that fence lines are checked regularly, CCTV cameras are functioning correctly, and alarm monitoring centers are correctly equipped to deal with the threats posed." Critical infrastructure providers, particularly those with sites in the North-West of the UK, are urged to audit site security plans and to consider taking additional steps to deter unwanted attention from OCGs. Direct threat to infrastructure The current intelligence picture points toward an on-going direct threat to infrastructure, with implications for asset loss service disruption, regulatory penalties and public safety. Operators are reminded to continue reporting all incidents of theft, suspicious vehicles, and hostile reconnaissance to DeterTech and Opal, the national police intelligence unit focused on serious organized acquisitive crime.
Rhombus, a pioneer in cloud-managed physical security solutions, announced the launch of Rhombus Insights, an AI-powered solution that empowers businesses to measure virtually anything their cameras can see and automate responses based on those specific observations. The launch is a significant expansion of Rhombus’ AI analytics capabilities, giving organizations complete customization over what they track and how they respond to operational situations. Rhombus's physical operations Businesses can now create tailored measures and automatic replies designed for their specific active needs Rhombus Insights addresses a fundamental challenge companies have faced: the inability to answer questions about their physical operations without ongoing and time-intensive human intervention. Whether tracking parking availability, observing equipment placement, verifying safety protocols, or measuring inventory levels, businesses can now create tailored measurements and automated responses designed for their specific operational needs. How businesses continually optimize and secure “Companies have been limited to predefined analytics that couldn’t really address what they need to know about what’s going on at their store, their campus, their factory, or other physical space at any given moment,” said Rickey Cox, VP of Product at Rhombus. “Rhombus Insights changes that completely. If your Rhombus cameras can see it, you can now measure it, track it, and automate responses to it. This level of complete customization unlocks entirely new possibilities for how businesses continually optimize and secure their physical spaces.” Transforming visual data into actionable intelligence Rhombus Insights works through an intuitive setup process where users simply create prompts Rhombus Insights works through an intuitive setup process where users simply create prompts describing what they want to measure, specify the measurement type (numerical, percentage, or true/false), and set monitoring frequency. The solution then continuously analyzes camera footage to provide real-time data visualization, exportable reports, and API access for integration with existing business systems. Instant alerts and automated actions Going beyond passive monitoring, Rhombus Insights enables organizations to configure instant alerts and automated actions whenever specific conditions are met. When triggers are detected, the system can send notifications via email, text, or push notification, and execute custom actions such as playing audio announcements or activating third-party devices (such as lights or alarms) through relay triggers. Cross-industry applications drive operational excellence Educational clubs can verify safety protocol compliance, such as confirming lifeguard presence The flexibility of Rhombus Insights supports diverse use cases across industries. In manufacturing environments, companies can track forklift counts on warehouse floors and automate safety alerts when equipment exceeds safe density levels. Retail businesses can observe queue lengths and automatically notify staff when customer wait times become problematic. Educational institutions can verify safety protocol compliance, such as confirming lifeguard presence at pool facilities. Operational leverage and increased efficiency “Like many businesses, our operations have unique characteristics that require specialized knowledge and measurement capabilities,” said Kevin Bush, Chief Strategy Officer at Fresh Dining Concepts, the largest franchisee group of brands like Cinnabon and Auntie Anne’s. “Being able to use our cameras to extract actionable information and automate business response gives us an incredible amount of operational leverage and increased efficiency across our locations.” Seamless integration with existing infrastructure Rhombus’ strategic growth of purposeful AI features built into its cloud-based physical security system Rhombus Insights works with existing Rhombus camera infrastructure or 3rd party cameras and integrates seamlessly with the company’s unified Rhombus Console. Organizations can configure their choice of large language model (LLM) to power the AI analytics, with options including Rhombus’ provided solution or integration with pioneering AI platforms such as ChatGPT, Claude, Gemini, and Grok. This launch continues Rhombus’ strategic expansion of purposeful AI features built into its cloud-based physical security system, following recent introductions of natural language video search and operational analytics capabilities that include line crossing and occupancy counting. Driving cost efficiency and strategic decision-making By automating previously manual monitoring processes, Rhombus Insights delivers significant cost savings while providing organizations with data-driven insights that influence site planning, budget allocation, and operational strategy. The solution's automated response capabilities ensure critical conditions are addressed immediately without requiring constant human oversight. Availability Rhombus Insights is now available to companies with existing Rhombus deployments. Organizations interested in exploring how AI-powered custom analytics and response triggers can optimize their physical spaces
DeterTech, a pioneer in intruder detection and site security, is proud to announce its involvement with the latest series of DIY SOS: The Big Build Ireland, with the next episode due to air on Sunday 5th October on RTÉ One. One episode this series focuses on a life-changing project in Killinarden, Tallaght to adapt the home of nine-year-old Cayden and his family into a safe and accessible space that is tailored to their needs. Cayden was born with Arthrogryposis and is fully dependent on a wheelchair. The DIY SOS team stepped in after learning he was largely confined to the living room and needed to be carried upstairs, to and from his bedroom and to the toilet affecting his and his family’s qualities of life. Seeing so many volunteer tradespeople and suppliers come together to transform the terraced house was a truly special moment and makes for a spectacular reveal. DeterTech volunteers Members of DeterTech volunteered alongside more than 90 incredible tradespeople and suppliers Members of DeterTech volunteered alongside more than 90 incredible tradespeople and suppliers – from builders and electricians through to landscapers and gardeners. DeterTech also supplied the site security solutions necessary to protect people, tools and materials throughout the build. Speaking about the project Michael Kennedy, CFO, DeterTech, says: “We pride ourselves on bringing greater peace of mind to people and communities every day. Being there on reveal day to see the reaction is something I’ll never forget. I’d like to pay huge thanks to the entire DIY SOS family for involving us, and to all the volunteers, suppliers and organizers who worked so hard to create a better future for Cayden and his family.” DeterTech on board Helena Ryan, Managing Director Cooga Safety Services Group and Safety Supervisor for DIY SOS: The Big Build Ireland, adds: “One of the builds that features this series had 1,346 people on site, all of whom benefitted from the services DeterTech provides. DeterTech went above and beyond, did phenomenal work and I look forward to collaborating again in the future.” Orlagh Murphy of indiepics, the production company behind the show, concludes: “Having DeterTech on board has been a game-changer for our site safety and security. It gives our crew, contractors and volunteers the confidence they need to press on and transform the homes of our very deserving recipients.”
Boon Edam Inc., a global pioneer in physical security entrance products, is excited to share that American University in Washington, D.C., has completed the installation of five Lifeline Speedlane Compact turnstiles and one Winglock Swing Gate as part of a comprehensive renovation of its Terrace Dining Room (TDR), the university’s main dining hall serving thousands of students, faculty, and staff each day. Improved systems Manual point-of-sale card swipes slowed entry, resulted in higher-than-normal error rates At a university where thousands of students move through campus each day, the entrance to the Terrace Dining Room had become a frequent source of crowding and delays. Long lines routinely snaked up the stairs from the entryway during peak meal times, frustrating community members. Manual point-of-sale card swipes slowed entry, resulted in higher-than-normal error rates, and created demand-based planning challenges. With improved systems, staff can prioritize exceptional guest service rather than managing long lines. Seamless integration Seamless integration with the campus meal plan transaction system eases congestion Seamless integration with the campus meal plan transaction system eases congestion, allowing for more meaningful guest interactions. Additionally, real-time data on guest traffic enables better staffing and demand forecasting, ensuring the right team is in place to elevate the overall experience. The university needed a more intelligent, streamlined solution that could improve flow, enable better planning, and support a better dining experience for its students, faculty, staff, and guests. Comprehensive transformation As part of a comprehensive transformation of the TDR, American University (AU) selected Boon Edam’s Lifeline Speedlane Compact turnstiles to deliver a secure, modern access solution that aligned with the dining hall’s upgraded design and high traffic demands. From the earliest planning phases, access management and control were a top priority. Working closely with the university’s OneCard, auxiliary services technology, and planning and project management teams, Chartwells Higher Education, and the Atrium Campus support team, Boon Edam provided a solution that met the university’s vision for fast, intuitive, and secure student entry. Students now tap their AU OneCard to gain immediate access with real-time verification of meal plan status and account balances. The system has been fully integrated with the Atrium Campus meal plan system, delivering a seamless user experience. Speedlane design The system enables seamless movement, improving security and meal plan integrity Boon Edam’s sleek, low-profile Speedlane design complements the architectural aesthetic of the new space, while advanced security measures ensure only authorized users gain entry. The system enables seamless movement, improving security and meal plan integrity without creating a restrictive feel. “This was a strategic effort to blend security, efficiency, and design,” said Michael LoBasso, Associate Director of Auxiliaries Technology at American University. “It was a true collaboration with Boon Edam, Chartwells, our campus partners, and Atrium Campus to create a dining experience that’s secure, smart, and seamless.” Enhanced efficiency With thousands of students passing through the Terrace Dining Room during peak hours, American University needed a solution that could keep pace with real-world campus demand. Boon Edam’s Lifeline Speedlane Compact turnstiles delivered, combining bi-directional access control, intuitive LED guidance, and fast user identification to eliminate bottlenecks and maintain steady throughput during the day. Two Speedlane Compacts serve as dedicated entrances, three more manage exit flow, and a Winglock Swing gate provides additional flexibility for deliveries and large group access. Operational oversight This layout enables smooth, consistent movement in and out of the facility, freeing staff from manual enforcement and allowing them to focus on service and hospitality. The system has proven reliable under pressure, handling volume efficiently while supporting the university’s goals around student satisfaction and operational oversight. Accessibility and modernization The new layout supports smoother traffic flow, more inclusive dining options The renovation of the Terrace Dining Room was more than a visual upgrade. It was an investment in the student experience, operational efficiency, and forward-thinking design. The new layout supports smoother traffic flow, more inclusive dining options, and a welcoming space where students can gather, recharge, and connect. American University’s focus was on accessibility and modernization, and Boon Edam’s Speedlane Compact turnstiles contributed meaningfully to that vision. They helped to improve secure access with low energy consumption and a minimal operational footprint. The result is an access solution that fits seamlessly into a high-volume environment while aligning with long-term sustainability goals.


Round table discussion
Transportation systems need robust physical security to protect human life, to ensure economic stability, and to maintain national security. Because transportation involves moving large numbers of people and critical goods across vast, often interconnected infrastructure, it presents a highly attractive target for various threats. More threats equate to a greater need for security. We asked our Expert Panel Roundtable: What are the emerging applications of physical security in the transportation market?
Installing physical security systems requires integrating diverse technologies (e.g., cameras, access control, alarms) that often use different protocols and must be adapted to a building's unique physical layout and legacy infrastructure. Specialized technical expertise is required for seamless networking and proper configuration. Hopefully, no important factors are overlooked in the installation process. We asked our Expert Panel Roundtable: What is the most overlooked factor when installing physical security systems?
The healthcare industry faces unique and significant security challenges. Healthcare security professionals must balance an open, welcoming environment for patients and visitors with the need to protect valuable assets and personnel in a high-stress, 24/7 setting. These requirements direct the physical security technologies deployed in medical facilities. We asked our Expert Panel Roundtable: What are the unique aspects of the healthcare market, and how should the physical security industry adapt?
Products


White papers

Combining Security And Networking Technologies For A Unified Solution
Download
What is a universal RFID reader?
Download
Maximizing Enterprise Security Systems In The Cloud
Download
The Power Of Integration In Physical Security Systems
Download
Preventing Loss, Securing Assets
Download
Using Artificial Intelligence (AI) To Automate Physical Security Systems
Download
Integrating IT & Physical Security Teams
Download
Verkada Workplace Safety Survey
Download
How To Create A Successful Physical Security Roadmap
Download
5 Easy Steps To An Upgraded Video Surveillance System
Download
Improving City Mobility Using Connected Video Technology
Download
5 Ways To Strengthen Physical Security With An Integrated System
Download
The Benefits of Edge AI + Cloud For Security Systems
Download
Unified Physical Security
Download
Integrated Access Control: Reap The Benefits Of Connected Security
Download