When a child goes missing in a large, crowded mall, we have a panicking mom asking for help from the staff, at least a dozen cameras in the area, and assuming the child has gone missing for only 15 minutes, about 3 hours’ worth of video to look through to find the child. Typical security staff response would be to monitor the video wall while reviewing the footage and making a verbal announcement throughout the mall so the staff can keep an eye out for her.
There is no telling how long it will take, while every second feels like hours under pressure. As more time passes, the possible areas where the child can be will widen, it becomes more time-consuming to search manually, and the likelihood of finding the child decreases. What if we can avoid all of that and directly search for that particular girl in less than 1 second?
Artificial neural networks are improving every day and now enable us to search for a person across all selected camera streamsWith Artificial intelligence, we can. Artificial neural networks are improving every day and now enable us to search for a person across all selected camera streams in a fraction of a second, using only one photo of that person.
The photo does not even have to be a full frontal, passport-type mugshot; it can be a selfie image of the person at a party, as long as the face is there, the AI can find her and match her face with the hundreds or thousands of faces in the locations of interest. The search result is obtained in nearly real time as she passes by a certain camera.
Distinguishing Humans From Animals And Statues
The AI system continuously analyzes video streams from the surveillance cameras in its network, distinguishes human faces from non-human objects such as statues and animals, and much like a human brain, stores information about those faces in its memory, a mental image of the facial features so to speak.
When we, the system user, upload an image of the person of interest to the AI system, the AI detects the face(s) in that image along with their particular features, search its memory for similar faces, and shows us where and when the person has appeared.
We are in control of selecting the time period (up to days) and place (cameras) to search, and we can adjust the similarity level, i.e., how much a face matches the uploaded photo, to expand or fine-tune the search result according to our need. Furthermore, because the camera names and time stamps are available, the system can be linked with maps to track and predict the path of the person of interest.
 |
| AI Face Search is not Face Recognition for two reasons: it protects people’s privacy, and it is lightweight |
Protecting People’s Privacy With AI Face Search
All features of face recognition can be enabled by the system user, such as to notify staff members when a person of interest is approaching the store AI Face Search is not Face Recognition for two reasons: it protects people’s privacy, and it is lightweight. First, with AI Face Search, no names, ID, personal information, or lists of any type are required to be saved in the system. The uploaded image can be erased from the system after use, there is no face database, and all faces in the camera live view can be blurred out post-processing to guarantee GDPR compliance.
Second, the lack of a required face database, a live view with frames drawn around the detected faces and constant face matching in the background also significantly reduces the amount of computing resource to process the video stream, hence the lightweight.
Face Search Versus Face Recognition
| AI Face Search | Face Recognition |
| Quick search for a particular person in video footage | Identify everyone in video footage |
| Match detected face(s) in video stream to target face(s) in an uploaded image | Match detected face(s) in video stream to a database |
| Do not store faces and names in a database | Must have a database with ID info |
| Automatically protect privacy for GDPR compliance in public places | May require additional paperwork to comply with privacy regulations |
| Lightweight solution | Complex solution for large-scale deployment |
| Main use: locate persons of interest in a large area | Main use: identify a person who passes through a checkpoint |
Of course, all features of face recognition can be enabled by the system user if necessary, such as to notify staff members when a person of interest is approaching the store, but the flexibility to not have such features and to use the search tool as a simple Google-like device particularly for people and images is the advantage of AI Face Search.Because Face Search is not based on face recognition, no faces and name identifications are stored
Advantages Of AI Face Search
Artificial Intelligence has advanced so far in the past few years that its facial understanding capability is equivalent to that of a human. The AI will recognise the person of interest whether he has glasses, wears a hat, is drinking water, or is at an angle away from the camera.
In summary, the advantages of Face Search:
- High efficiency: a target person can be located within a few seconds, which enables fast response time.
- High performance: high accuracy in a large database and stable performance, much like Google search for text-based queries.
- Easy setup and usage: AI appliance with the built-in face search engine can be customised to integrate to any existing NVR/VMS/camera system or as a standalone unit depending on the customer’s needs. The simple-to-use interface requires minimal training and no special programming skills.
- High-cost saving: the time saving and ease of use translate to orders of magnitude less manual effort than traditionally required, which means money saving.
- Scalability: AI can scale much faster and at a wider scope than human effort. AI performance simply relies on computing resource, and each Face Search appliance typically comes with the optimal hardware for any system size depending on the customer need, which can go up to thousands of cameras.
- Privacy: AI Face Search is not face recognition. For face recognition, there are privacy laws that limits the usage. Because Face Search is not based on face recognition, no faces and name identifications are stored, so Face Search can be used in many public environments to identify faces against past and real-time video recordings.
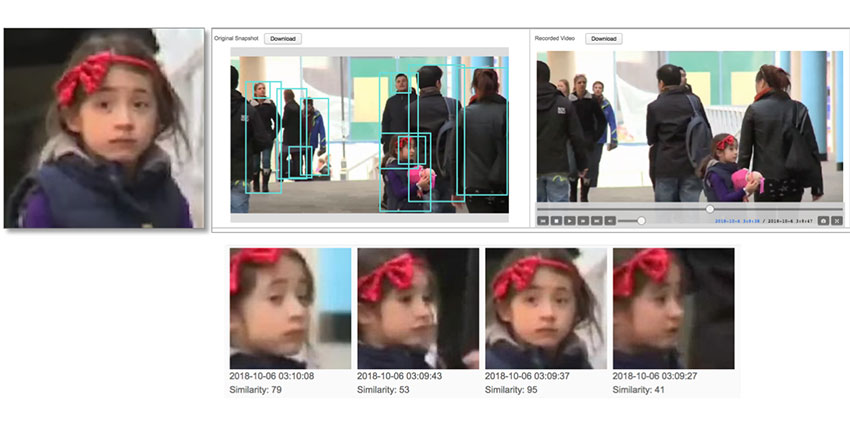 |
| AI Face Search match detected face(s) in video stream to target face(s) in an uploaded image |
Common Use Cases Of AI Face Search
In addition to the scenario of missing child in a shopping mall, other common use cases for the AI Face Search technology include:
- Retail management: Search, detect and locate VIP guests in hotels, shopping centres, resorts, etc. to promptly attend to their needs, track their behaviour pattern, and predict locations that they tend to visit.
- Crime suspect: Quickly search for and prove/disprove the presence of suspects (thief, robber, terrorist, etc.) in an incident at certain locations and time.
- School campus protection: With the recent increase in number of mass shootings in school campuses, there is a need to identify, locate and stop a weapon carrier on campus as soon as possible before he can start shooting. Face Search will enable the authorities to locate the suspect and trace his movements within seconds using multiple camera feeds from different areas on campus. Only one clear image of the suspect’s face is sufficient.
In the race of technology development in response to business needs and security concerns, AI Face Search is a simple, lightweight solution for airports, shopping centres, schools, resorts, etc. to increase our efficiency, minimise manual effort in searching for people when incidents occur on site, and actively prevent potential incidents from occurring.
By Paul Sun, CEO of IronYun, and Mai Truong, Marketing Manager of IronYun
From facial recognition to LiDAR, explore the innovations redefining gaming surveillance


























