As police use of live facial recognition (LFR) is called into question in the United Kingdom, the concerns can overshadow another use of facial recognition by police officers. Facial recognition is incorporated into day-to-day police operations to identify an individual standing in front of them.
This more common usage should not be called into question, says Simon Hall, CEO of Coeus Software, which developed PoliceBox, a software that enables police officers to complete the majority of their daily tasks from an app operating on a smart phone.
Time-Consuming Process
“Verifying the identity of an individual standing in front of you via facial recognition should be no more controversial than taking a fingerprint for the same purpose,” says Hall. “We are not talking about mass surveillance here, but the opportunity to use technology to make an officer’s day more efficient. Verifying a person’s ID is a time-consuming process if you have to take them to the station, so being able to do this more quickly should be welcomed as a positive step to modernize policing.”
Because the use of facial recognition by police has proven to be a divisive topic, Simon is eager to highlight the distinction between the use of facial recognition for ID verification and the more controversial mass surveillance that some police forces have trialed. “There are two different use cases for facial recognition in the context of law enforcement,” says Hall.
Number-Plate Recognition
“Firstly, there is facial recognition to verify a person’s identity (typically done face-to-face with the individual concerned and using the Police National Computer [PNC] database). This is no more controversial than taking an individual’s fingerprint to verify their ID but can be conducted more quickly if the officer has the capability on their smart phone. The second common use of facial recognition is to identify suspects quickly via mass surveillance. This is more controversial.” The focus for PoliceBox is ID verification only, he adds.
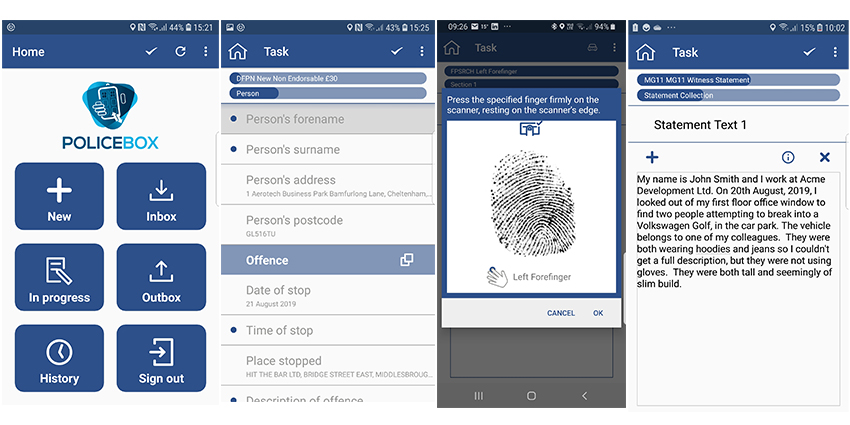 |
| The focus of facial recognition for PoliceBox is ID verification only |
First, there is the matter of consent. In the context of facial recognition in public situations, it is very difficult to inform everyone that they are being observed, so they cannot give their informed consent, says Hall. Then there is the inability for people to ‘opt out’ of the process. Unlike with driving a car, where one can technically opt-out of the rules of the road (and avoid technologies like number-plate recognition) by choosing not to drive, there is no such option for facial recognition.
National Surveillance System
Secondly, many-to-many matching (matching lots of images to lots of database records) is more likely to produce false matches, resulting in possible perceived harassment of individuals who happen to match a person of interest, notes Hall.
The government is openly exploring plans to develop a national surveillance system using facial recognition
Lastly, Hall says there are legitimate concerns that the technology could be misused for discrimination or exerting control over populations. In China, for example, where facial recognition technology is already widely used in the commercial sector, the government is openly exploring plans to develop a national surveillance system using facial recognition. “Mass surveillance can be used in two ways; real-time, whereby ‘people of interest’ are flagged up as soon as a match is detected, and historical, where the movements of individuals around the time of a reported crime are established after the event,” says Hall.
Repeated False Matches
“These two modes probably require different types of safeguards. For example, it may be appropriate to obtain a warrant to search historical data, to prevent Cambridge-Analytica style mining of personal data. For real time data, safeguards against repeated false matches are needed to prevent harassment of falsely matched individuals.”
Properly implemented, facial recognition can be consistent with the GDPR. The principles are no different from obtaining a fingerprint to confirm identity, where consent would normally be given. For PoliceBox, using fingerprint or facial identification is typically a time-saving solution, benefitting both parties, instead of going to the police station and establishing identity there. Signed consent can be obtained on the spot using a secure on-screen signature.
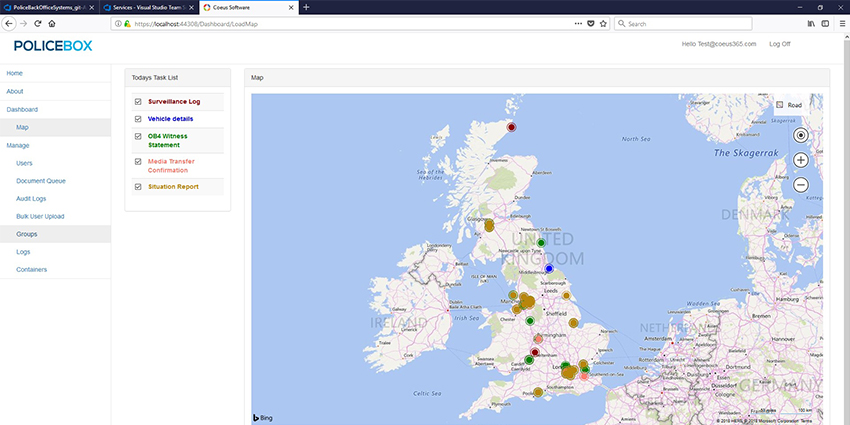 |
| The PoliceBox solution is based on the UK legal framework and would also be appropriate for countries whose laws are similar to the UK |
Facial Recognition Algorithms
Fingerprints and facial images can be automatically deleted once used to establish identity. There are special provisions for the collection of personal data for law enforcement purposes without consent, and some test cases for mass surveillance could go through the Information Commissioner’s Office (ICO). This is particularly significant where private operators are concerned.
The PoliceBox solution is based on the UK legal framework and would also be appropriate for countries whose laws are similar to the UK. It is also internationalized and can be used in different languages. Facial recognition algorithms and databases are typically implemented by the relevant law enforcement body (such as the Home Office) and not directly within the product, which acts as a front-end to those systems.
Hall sees several remaining challenges related to police use of facial recognition:
- The adoption of cloud-based software-as-a-service (SaaS) solutions within the public sector. The existing infrastructure in the public sector has evolved over a number of years and there are significant legacy systems in place that need to be refreshed/replaced;
- Need for proven technology. Public sector organizations are risk-averse and often insist on being able to reference existing installations, which creates a Catch 22 problem when introducing new technology as someone has to be first;
- Interrupting business-as-usual. Most organizations already have some form of an existing solution. Even if this system provides poor ROI and is extremely dated, one must still overcome ‘the better the devil you know’ policy;
- A reluctance by some suppliers to share information with other solutions via APIs. This has stifled innovation for some time.
Improving Officers’ Wellbeing
These challenges are slowly being overcome. “I am confident we will soon see an accelerated adoption of platforms such as ours to deliver the financial and efficiency savings that are needed to bring the public sector into the 21st century,” says Hall.
One of the biggest themes to come out of the recent Home Office Review into frontline policing was the need to improve officers’ wellbeing. Law enforcement has to deal with some of the most difficult and harrowing situations on an almost daily basis. The administrative burden can also be problematic, says Hall. “If we can help to reduce the administrative burden placed on officers – even by a little bit – the overall improvements in effectiveness and well-being when magnified across a whole force will be significant.”
From facial recognition to LiDAR, explore the innovations redefining gaming surveillance