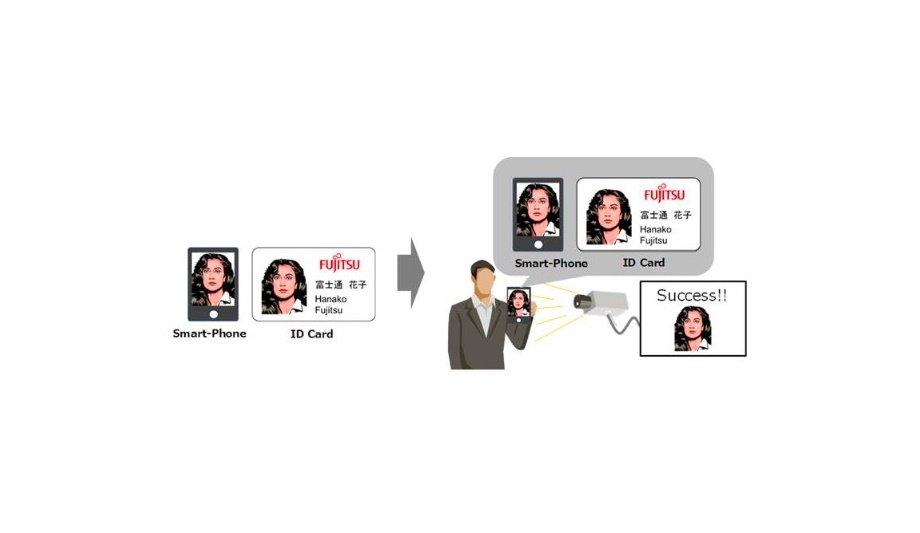
Fujitsu Laboratories Ltd. announces the development of a facial recognition technology that uses conventional cameras to successfully identify efforts to spoof authentication systems. This includes impersonation attempts in which a person presents a printed photograph or an image from the internet to a camera.
Conventional technologies rely on expensive, dedicated devices like near-infrared cameras to identify telltale signs of forgery, or the user is required to move their face from side to side, which remains difficult to duplicate with a forgery. This leads to increased costs, however, and the need for additional user interaction slows the authentication process.
Convenience of face authentication
To tackle these challenges, Fujitsu has developed a forgery feature extraction technology that detects the subtle differences between an authentic image and a forgery, as well as a forgery judgment technology that accounts for variations in appearance due to the capture environment.
Fujitsu's new technology ultimately makes it possible to prevent impersonation with forgeries using only face images taken at the time of authentication, enhancing security without sacrificing the convenience of face authentication and contributing to the DX (digital transformation) of operations with improved personal authentication technologies.
Other authentication methods
It has proven difficult to determine the authenticity of a face by relying on a facial image alone
While biometric authentication continues to grow in popularity, many risks remain. In some cases, when facial images are disclosed on the Internet via SNS, etc., the possibility emerges that the image may become the target of malicious users if stolen due to the loss of an ID card with a facial photograph, etc.--because of the prevalence of such images, this makes facial authentication more vulnerable than other authentication methods, such as fingerprints or palm veins.
Smartphone screens, ID cards, and face images printed on paper vary in their appearance due to factors like reflections or blurring on a smartphone screen. It has proven difficult to determine the authenticity of a face by relying on a facial image alone because of the effects of similar fluctuations, such as reflections caused by fluorescent lights or sunlight, or blurring caused by facial movement.
General-Purpose cameras
For this reason, special cameras like near-infrared cameras or depth cameras that measure the distance between the subject and the camera are used to catch typical signs of forgery. These methods remain imperfect, however, and lead to issues including increased costs for dedicated cameras and reduced convenience due to the addition of motion information required when using general-purpose cameras.
The development of technologies that can conveniently and inexpensively detect spoofing with general-purpose cameras has become a topic of consideration. Fujitsu has developed a technology that can detect the impersonation of others through photographs, etc. from face images taken with a general-purpose camera. The features of the developed technology are as follows.
Forgery feature extraction
Image processing technology is used to digitize the characteristic features of forgery
Various features characteristic of a forgery remains in images obtained by presenting the forgery to the camera, such as reflections on the terminal screen of a smartphone, and distortion of the shape of the face caused by taking a planar forgery. Fujitsu has developed a forgery feature extraction technique to express the difference between the forgery's characteristic features and the real face as determinable values.
First, the face image captured by the camera is separated into various elements that exhibit the characteristic features of forgery, such as reflection elements and shape elements. Next, image processing technology is used to digitize the characteristic features of forgery for each of the separated elements, and the characteristics of each element are combined to generate a characteristic for judgment. This makes it possible to identify counterfeits without information based on user operations.
Deep learning techniques
In the past, in order to respond to variations in image appearance caused by the capture environment, a single determination model was generated by training a system with face images containing various variations using machine learning. However, the wide range of variations in the way images are taken, depending on the type of forgery, such as a smartphone screen or ID card, complicates the boundary between the real face and the forgery, making it difficult to identify the forgery even with the latest Deep Learning techniques.
Therefore, Fujitsu has developed a technology that can correctly identify counterfeits by generating determination models that reduce the influence of variations by learning the categories of face images that have similar variations, such as face images taken at the office or face images taken by a window.
Counterfeit with machine learning
The development technology steps are divided into a training phase and a judgment phase. In the training phase, face images acquired in various environments are classified into categories such as window, backlight, and normally based on the capture environment, such as the intensity of light and the direction of light.
Next, a judgment model is made for determining whether the target is a real face or a counterfeit with machine learning, using the decision features generated by the forgery feature extraction technology for each category.
Inexpensive spoofing detection
The similarity between the input image and each category is calculated dynamically
In the judgment phase, in order to estimate which of the categories defined in the training phase the input image capture environment is close to, the similarity between the input image and each category is calculated dynamically. Next, in order to emphasize the result of the determination model of the category in which the input image and the environment are close to each other, a value obtained by multiplying the score indicating the authenticity output from each determination model by the weight based on the similarity with each category is used to determine whether or not the object is a fake.
By using these technologies, it becomes possible to identify counterfeits using only the information of face images taken by a general-purpose camera and to realize relatively convenient and inexpensive spoofing detection.
Personal authentication technology
Fujitsu reviewed its own evaluation data set collected in a general office environment or an environment where telework outside the office is assumed and confirmed that spoofing attempts can be detected with the same level of accuracy as before, even when there is no specified movement by a dedicated camera or a user. This makes it possible to prevent unauthorized access at a low cost without sacrificing convenience.
The technology offers the potential to improve security for workers remotely accessing company systems from offsite and to contribute to the digital transformation of operations through the advancement of enhanced personal authentication technology. Fujitsu aims to further improve the accuracy of its forgery detection technology with the aim of putting it into practical use by the end of the fiscal 2020 in March 2021.
Discover how AI, biometrics, and analytics are transforming casino security