Fingerprint recognition
Suprema, a global pioneer of AI-powered security solutions, has been recognized by A&S magazine as a ‘2025 Global Top 50 Security Company’, marking its fifteenth consecutive year on the prestigious list. This consistent achievement underscores the company’s sustained growth, innovation, and global influence. A&S ranks the world’s top security companies annually based on revenue and profitability. Suprema has secured its place on this list since 2011. asmag.com&r...
Integrated access control and security manufacturer - TDSi has announced the release of GARDiS Pro Version 3.1, the latest enhanced iteration of its GARDiS Access Control Management Software. GARDiS 3.1 introduces expanded biometric support and intelligent credential management, delivering improved hardware reporting capabilities and new third-party integration options to further enhance system performance and flexibility. Latest update for GARDiS Pro Tina Baker, Software Development Man...
NEXT Biometrics, the world pioneer in advanced high-security fingerprint sensor technology, has secured its first mass production order for solutions that will be used in China ID products. The order, for NEXT Basalt FAP 20 sensors, is from an existing China-based OEM distributor and will be integrated into China ID products to support banking use cases. This news follows an initial order from the same distributor, which was announced in Q3 2024. This milestone reflects the growing demand for...
NEXT Biometrics has extended its partnership with a U.S. based, Identity and Access Management (IAM) and biometric authentication solution provider. NEXT’s technology is already embedded in the partner’s existing solutions, and now provides the foundation for the latest solution in its range. These solutions help governments and corporations in the fight against cyber threats, like phishing, by moving to passwordless user identification through zero-trust multi-factor authenticat...
In a world where safety and security are of the utmost importance, it’s crucial to stay updated with the latest technologies that can provide advanced protection. One such innovation that is leading the way in modern security is biometric access control. This groundbreaking technology is transforming the way businesses and individuals safeguard their premises and data. Biometric access control Biometric access control utilizes unique physical or behavioral attributes of individuals, suc...
Michael Marcotte, the founder, chairman, and CEO of enterprise-grade digital authentication firm artius.iD, was warned that a successful biometric data breach at a pioneering bank could put them on the brink of the next global financial crisis. The intervention follows recent comments by the CEO of HSBC UK, Ian Stuart, who last month told UK policymakers the bank is “being attacked all the time” by online criminals, leading to cybersecurity becoming t...
News
In the industrial landscape, ensuring security isn’t just about guarding entry points—it’s about securing processes, assets, and people with intelligence. That’s where the Advanced Access Control system steps in. For manufacturing plants, this system offers more than just card-based entry—they deliver operational safety, traceability, and compliance. Growth in the access control Markets and Data reveals significant growth in the global access control and authentication market An industry report by Markets and Data reveals significant growth in the global access control and authentication market. Starting at $13.2 billion in 2022, it's set to expand to $26.1 billion by 2030, reflecting a robust 8.9% CAGR for the period between 2023 and 2030. In fact, a study by IBM shows that internal threats account for nearly 60% of manufacturing-related data breaches, making identity-based access control a critical need. Why traditional access control isn't enough Manufacturing plants operate with high-value assets, dangerous machinery, and round-the-clock shifts. Legacy access system—limited to basic RFID or PINs—fails to monitor who, where, and when with precision. Most importantly, they can't adapt dynamically to shifts, roles, or emergency overrides The traditional system lacks real-time visibility, contextual intelligence, and scalability to meet these evolving needs. A breach here isn’t just a loss—it could halt production or trigger a safety hazard. Most importantly, they can't adapt dynamically to shifts, roles, or emergency overrides. In an era where cyber-physical threats are rising and compliance audits are tighter, traditional access just isn’t equipped to protect modern manufacturing setups. Types of advanced access control system Modern manufacturing facilities are adopting multiple types of advanced access control system, such as: Biometric Authentication: Fingerprint, iris-based, or facial access control system eliminates the risk of credential sharing. According to the Lift HCM article "Slash Time Theft: Choosing Between Biometric and Digital Time Clocks", for a 100-employee company, a biometric system typically eliminates an average of 2.5 hours of time theft per employee per month, translating to approximately $45,000 in annual savings based on average wage calculations. Multi-factor Authentication (MFA): Combining credentials (card and biometric access control system) to strengthen entry authorization. According to CISA (Cybersecurity and Infrastructure Agency), the use of MFA makes users 99% less likely to be hacked! Mobile-based Access: Access through secure mobile apps enhances user convenience and hygiene. The global mobile access control system market size is predicted to be valued at $1,638,455.4 thousand by 2032, surging from $228,690.0 thousand in 2022, at a noteworthy CAGR of 22.4%, as noted by the research dive, a market research firm. Role-Based Access: Access is customized based on job function or hierarchy to critical zones. According to a report by Tata Communications, Role-Based Access Control (RBAC) is a key practice that limits the potential effect of insider threats by allowing workers the right to do their duties. How Matrix empowers manufacturing security Solutions such as those offered by Matrix provide capabilities like modular, role-based For manufacturing entities seeking to enhance industrial safety and operational excellence, a robust and advanced access control system is paramount. Solutions such as those offered by Matrix provide capabilities like modular, role-based, time and zone-based, and device-based user access control policies, real-time alerts, and tamper detection mechanisms. How advanced access control solutions can enlighten These features are designed to help streamline operations, ensure compliance with regulatory standards, and mitigate security risks, ultimately contributing to optimized efficiency, enhanced safety, and asset protection within a dynamic industrial landscape. Ready to embrace a future where industrial safety and operational excellence harmoniously converge? Discover how advanced access control solutions can enlighten the manufacturing environment with unparalleled security, seamless efficiency, and complete peace of mind.
NEXT Biometrics has launched a new fingerprint sensor in response to customer requirements. The ‘L1 Slim’ is a new addition to its NEXT Basalt FAP 20 product series (formerly NEXT Access 300 series) and is the thinnest sensor of its kind, while maintaining the same security and performance. This optimizes the integration process for identity verification module, point of sale terminal, tablet and other device makers. The sensor is also certified for use in India’s Aadhaar program and countries adopting the Modular Open Source Identity Platform (MOSIP) framework for their national ID programs, reducing time-to-market by up to 12 months. Integration efficiency “We love it when customers come to us with a challenge,” comments Marcus Laurén, Chief Product Officer at NEXT Biometrics. “As devices get more compact and competition is fiercer than ever, integration efficiency can be the difference between commercial success and market follower. Our hardware and software engineers are now poised to help OEMs around the world to integrate this super slim sensor to bring strong biometric authentication to any device.” NEXT’s Active Thermal technology NEXT’s Active Thermal technology uses both heat from the finger and 3D imaging to authenticate the user NEXT’s Active Thermal technology uses both heat from the finger and 3D imaging to authenticate the user. This enables superior liveness detection to combat spoofing attacks, when compared with other fingerprint authentication technologies. With embedded hardware, the overall cost of the solution is reduced, and integration of the hardware and software is simplified. The NEXT Basalt L1 Slim The NEXT Basalt L1 Slim product minimizes sensor thickness and optimizes image resolution and energy consumption, simplifying integration with devices like readers, peripherals, terminals and more. This enables portability of identification devices and exceptional performance in varying light and environmental conditions. Historical growth Over the last 25 years, NEXT Biometrics has shipped more than 10 million sensors. Its Active Thermal® technologies are certified by entities including Aadhaar, FBI-PIV, MOSIP Compliance and NIBSS, and have been implemented in countries including Bangladesh, China, Ghana, India, Malaysia, Pakistan, U.S. and Vietnam.
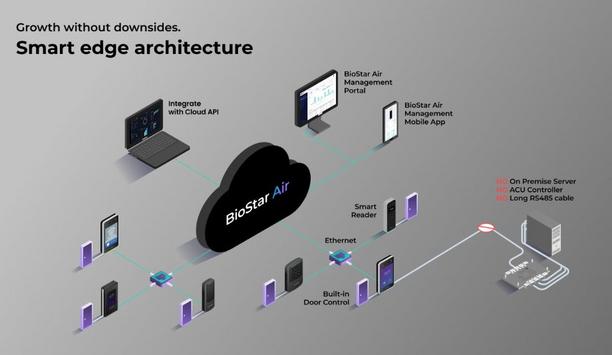
Suprema, a pioneer in AI-powered access control and security solutions, officially announced the launch of BioStar Air, the first and only cloud-based access control platform designed to natively support biometric authentication. Featuring true zero-on-premise architecture, BioStar Air simplifies deployment and scales effortlessly to secure SMBs, multi-branch companies, and mixed-use buildings. Cloud-based access control First showcased at ISC West 2025, BioStar Air sets a new standard for cloud-based access control First showcased at ISC West 2025, BioStar Air sets a new standard for cloud-based access control. Unlike traditional systems tied to on-premise servers and controllers, BioStar Air is built entirely in the cloud. Smart readers with built-in controllers connect directly to the network, streamlining installation, reducing infrastructure costs, and making it simple to scale across multiple locations. Key innovation in BioStar Air A key innovation in BioStar Air is its native biometric support. By processing biometric data at the edge, the platform ensures fast, reliable authentication even during network outages. Thanks to its federated architecture, employees can use the same face or finger template company-wide. BioStar Air supports a wide range of credentials, including facial authentication, RFID cards, mobile access, and QR codes. Fingerprint recognition and Apple Wallet support are coming soon. Intuitive web and mobile interfaces Intuitive web and mobile interfaces give administrators the power to manage users and devices Intuitive web and mobile interfaces give administrators the power to manage users and devices in real time from anywhere. Built for modern, distributed workplaces, BioStar Air helps organizations to centralize access control across multiple sites with minimal hardware, rapid onboarding, and uncompromising security. Future of access control “Building access control infrastructure can be overwhelming, with servers, controllers, and endless IT overhead,” said Hanchul Kim, CEO of Suprema Inc. “With BioStar Air, we’ve thrown all that out to deliver on our vision for the future of access control: cloud first, biometric-native, and effortless to scale. Organizations can finally gain the flexibility and confidence they need to secure today’s mobile, distributed workplaces.”
Anviz, a pioneer in intelligent security solutions, proudly announces the launch of W2 Face, its latest hybrid biometric access control and attendance terminal. Designed to meet the evolving needs of modern enterprises, the W2 Face combines facial recognition, fingerprint authentication, and RFID capabilities in a compact, intelligent device built for dynamic workplaces. Responding to market evolution As the access control landscape shifts toward integrated multi-biometric solutions, businesses increasingly seek systems that enhance security and operational efficiency. Market analysis conducted by Anviz has revealed key trends driving this demand: A growing preference for contactless and hygienic technologies Small and medium-sized enterprises are prioritizing cost-effective, reliable solutions An increased need for flexible authentication methods Rising expectations for stable, secure access to sensitive areas The W2 Face addresses these demands head-on, delivering a comprehensive, easy-to-deploy solution suited to various professional environments. W2 Face: Key features & innovations 1. Dual Biometric Authentication W2 Face integrates advanced facial recognition and fingerprint scanning, supported by liveness detection, to defend against spoofing via photos or video. This dual-layer security is ideal for high-traffic entry points. 2. Multi-Communication Flexibility With support for both Ethernet and Wi-Fi, the device can function in networked or standalone configurations. Integration with Anviz’s CrossChex Cloud enables remote management, simplifying operations across multiple locations. 3. Optimized for Small and Medium Enterprises 2.8-inch intuitive touchscreen display Capacity for 200 facial templates, 200 fingerprint records, and 200 RFID cards Stores up to 50,000 log entries for robust audit trails Slim design for seamless installation on standard door frames 4. Versatile Access Control Capabilities Customizable relay settings and doorbell integration make the W2 Face adaptable to various access scenarios, from open office environments to restricted zones. Why choose W2 Face? The W2 Face exemplifies Anviz’s ongoing innovation in secure access technology: Integrated Biometric Options: Supports user preferences with multiple authentication methods Enhanced Stability: Built on a proven platform with improved system reliability Modern, Functional Design: Sleek, professional aesthetic ideal for commercial interiors Broad Application Scope: Well-suited for distributed teams, temporary personnel, and multi-location operations Certified for global standards W2 Face complies with CE and FCC certifications, ensuring adherence to the highest international safety and performance standards. Its modular architecture allows for scalable updates, protecting customer investments over time.
NEXT Biometrics, the world pioneer in advanced high-security fingerprint sensor technology, has received the first major purchase order for its FAP 20 sensor in Nigeria. NEXT has already delivered an initial order of NOK 1.7 million during the first quarter of 2025. The NEXT FAP 20 sensor offers unparalleled performance and reliability, setting a new standard for secure identity verification. Integrated into POS terminals Sensor will be integrated into POS terminals to bring strong authentication to a financial inclusion project Already NBISS Biometric certified in Nigeria, the sensor will be integrated into POS terminals to bring strong authentication to a financial inclusion project. This order is the result of a design-win announced in 2022, and the customer estimates future orders of NOK 10-17 million in the year ahead. This milestone reflects the growing demand for trusted authentication in Africa, with several African countries implementing systems similar to India’s widely successful Aadhaar system. This will expand the market for national ID programs, financial services, access control, and more. Integrating biometric authentication into POS terminals “This order has been placed by a Chinese customer integrating biometric authentication into POS terminals in Nigeria. More broadly, we predict future demand for biometric solutions in Africa will be met by Chinese and Indian OEMs, many of which are already customers of NEXT. As a result, NEXT is well positioned to benefit from the developments we are now seeing in Africa,” says Digvijay Singh Kanwar, Senior Vice President and Head of Sales India, USA, EU and Africa (IUEA). He adds, “Our technology continues to make the lives of millions of people safer and more convenient every day. And, as the market for trusted authentication in Nigeria continues to expand, we anticipate growing order volumes, not just in Nigeria, but also in other MOSIP countries where the need for modular and open-source technology for national identity systems is increasing.”
ThreatAware, the pioneering Cyber Asset Attack Surface Management (CAASM) provider, announced the launch of the new version of its cutting-edge platform designed to transform how organizations discover devices and manage their IT assets and security tools. Version 3.0 now enables the remediation of security issues discovered and uncovers previously unknown devices. ThreatAware’s platform ThreatAware’s platform provides a complete view of the IT infrastructure from a single screen Developed to enable users to protect every cyber asset, ThreatAware’s platform ensures complete accuracy through its patent-pending timeline matching technology. This provides real-time monitoring of every device accessing corporate data to ensure security controls are deployed and functioning. With unsecured, unknown devices representing one of the greatest security blind spots, ThreatAware’s platform provides a complete view of the IT infrastructure from a single screen, uncovering hidden risks and previously invisible devices. This enables teams to swiftly identify vulnerabilities and proactively reduce their attack surface. ThreatAware’s innovative design Powered by API’s, ThreatAware’s innovative design integrates seamlessly with existing security tools, standardizing data from endpoints and ensuring organizations can account for every asset, including those previously unknown or lacking security controls. With agentless deployment in under 30 minutes, IT and Security teams have instant visibility without the need for complex configuration. Latest product enhancements Latest launch features product enhancements to provide even greater power, flexibility, and visibility The latest launch features product enhancements to provide even greater power, flexibility, and visibility to organizations of assets across increasingly fragmented IT landscapes. This also ensures teams achieve regulatory compliance through continuous monitoring and detailed cyber risk reports to support more informed decision-making. Key features of Version 3.0 ‘Stealth’ device tracking: the most comprehensive approach to device discovery ThreatAware’s latest launch provides a new way of analyzing previously invisible devices. By creating a timeline fingerprint of activity across every device, the platform can identify if unknown devices are logging on to the corporate network, uncovering the ‘stealth’ devices that may present a security risk. ThreatAware’s own analysis of IT environments shows that, on average, 15% of devices have gaps in security controls. Organizations also typically discover an average of 30% more devices accessing corporate data than previously known. Track Issue Resolution and Remediation New parts in Version 3.0 will make it even easier for teams to identify and track the key New features in Version 3.0 will make it even easier for teams to identify and track the resolution of any security issues identified. The ‘Action Center’ enables teams to automate and assign actions and provides teams with full visibility of workflows from identification to resolution. Control, Customization, and Enriched Data ThreatAware’s proprietary timeline matching technology eliminates duplicate records and provides a real-time asset inventory with enriched, contextual data. Version 3.0 provides even more customizable tagging to deliver a clear, accurate view of the estate and to monitor trends over time, so that teams can make priorities based on their own risk profile. Fragmented IT landscape Commenting on the launch, CEO and Co-founder Jon Abbott said: “Finding and managing all assets across a fragmented IT landscape in which cloud computing and remote access expand the attack surface, is a huge challenge for all organizations. It only takes one unprotected device, one misconfigured control, or one forgotten asset to create an entry point for attackers." "That's why ThreatAware is committed to delivering 100% accuracy and visibility across your IT estate. The power of the platform is not just in the information we track, it’s how we aggregate and analyze this information to highlight risks that simply wouldn’t otherwise be visible." Latest version of the platform Abbott continues: “Cyber risk is no longer just an IT concern, it’s a critical business issue. Organizations need to have the right tools not only to prepare for cyber threats but also to withstand and recover from disruption, should an attack strike." "The latest version of our platform underscores our commitment to supporting organizations with new features and insights which improve efficiencies and workflows and, ultimately, reduce security risks.”


Expert commentary
In today's rapidly evolving security landscape, facial recognition has become a buzzword that often triggers privacy and data protection concerns. However, many security professionals may not realize that "facial recognition" is an umbrella term encompassing various technologies, each with distinct applications and privacy implications. Let's dive into what these technologies really mean for security system resellers, integrators, and end-users. Facial recognition tech At its core, facial recognition technology re-identifies or verifies individuals based on their facial features, which are used as biometrics. However, not all biometric systems are based on unique identifying features. Some analyze general characteristics like facial hair style or other distinctive marks. Such traits, known as soft biometrics, can aid in identification but aren't unique enough to verify someone's identity uniquely. Personally identifiable information Modern systems incorporate robust safeguards, including data encryption and strict retention policies While facial recognition technology has applications ranging from access control to crime prevention to investigation, its implementation varies widely depending on specific needs. Modern systems incorporate robust safeguards, including data encryption and strict retention policies, to ensure the responsible handling of any personally identifiable information (PII). Understanding key technologies and applications Facial recognition encompasses several distinct technologies, each serving specific purposes. Here's a comprehensive breakdown of these technologies and their real-world applications. Key technologies: Face Verification (1:1): A one-to-one comparison where a person claims an identity (e.g., by showing an ID card), and the system verifies whether the face matches the provided identity. Example: In airports, face verification is used for automated passport control. When a traveler approaches a gate, their face is scanned and compared to the photo stored in the government database. If the face matches, the traveler is allowed through the gate without manual checks. Face Identification (1 to many): A one-to-many comparison, where a face captured by a system is compared to a database of multiple faces and facial features to identify the person. This process is often used in security or surveillance contexts. Example: In the case of a missing child at an airport, a system could scan the faces of all passengers passing through checkpoints and compare them to a photo of the child in a database. If a match is found, it triggers an alert. Face Re-identification (Many to Many): Many-to-many comparisons where multiple faces are compared to multiple other faces. This is typically used to track a person’s movement anonymously across different areas by matching their facial images at different checkpoints, without knowing their identity. Example: In a retail environment, facial re-identification might be used to track how long an anonymous person spends moving from one section of a store to another by re-identifying their face as they enter and leave different camera views. Facial recognition can be used both for real-time and offline applications. Real-Time Facial Recognition: Real-time facial recognition refers to the immediate processing of a live video feed, comparing faces to a database to generate instant alerts when a match is found. Example: At large public events like sports stadiums, real-time facial recognition might be used to detect banned individuals (e.g., known hooligans) as they attempt to enter. Post-Event (Recorded) Facial Recognition: This refers to analyzing video recordings after the event has occurred, rather than in real-time. Facial recognition is applied to recorded data to identify or track individuals. Example: After a crime, investigators could use facial recognition software on recorded video from security cameras to identify suspects by matching their faces to known databases. These definitions cover various aspects of facial recognition technology, its different applications, and how biometrics are used for identification and tracking purposes. Biometrics: Biometric technologies use a person’s distinguishing physical characteristics, such as their face, fingerprint, or iris, to identify them. Example: Fingerprint or face scanning for unlocking a phone or using iris recognition for secure entry at high-security buildings like data centers. Hard Biometrics: Hard biometrics refer to physical characteristics that are sufficiently unique enough to be used for identifying a specific individual, such as a face, fingerprint, or iris. Example: Using iris recognition at airport security checkpoints to confirm the identity of a traveler. Soft Biometrics: Soft biometrics (personal features) include general attributes like height or body shape, which are not unique enough to identify a person on their own but can help narrow down re-identification when combined with other information. Example: Using height and body shape to help identify a suspect in a camera scene when facial features alone are unreliable. Appearance Similarity: This refers to distinguishing between people based on their appearance (e.g., clothing, accessories) rather than biometric features. It’s often used for accelerated investigation and statistical analysis rather than identification. Example: A retail store may track customers based on the clothes they are wearing to monitor how long they stay in the store, without tracking their faces or personal details. Liveness Detection: A method used to determine whether the subject in front of a facial recognition system is a live human being and not a photo or a video recording. Example: In some mobile payment systems, facial recognition requires users to blink or move their head slightly to ensure they are a live person and not someone trying to use a photo for authentication. Mathematical Representation: Non-reversible mathematical representations are lists of numbers based on a person's facial image or appearance based on clothing. These numbers represent characteristics but cannot be easily used to recreate the face. Example: When an organization stores only the mathematical representations from a face rather than an actual image, even if the data is stolen, it is nearly impossible to recreate the person’s face or use the data with another system. Privacy and security considerations Modern facial recognition systems prioritize privacy through various protective measures, moving far beyond the basic security protocols of the past. Solutions integrate multiple layers of protection designed to safeguard personal data while maintaining system effectiveness. These sophisticated privacy controls work in concert to ensure responsible data handling and comply with evolving security standards. Key protective measures include: Biometric template isolation that keeps facial recognition templates separate from other personal data, with dedicated secure storage environments. Template encryption frameworks specifically designed for biometric data, using industry-standard protocols that protect facial features during both processing and storage. Biometric data anonymization that converts facial features into non-reversible mathematical representations – into numbers - prevents the reconstruction of original face images. Cascading deletion protocols automatically remove both raw facial data and derived biometric templates after their authorized use period. Segmented access controls that separate facial recognition administrative functions (like enrollment and template management) from regular system operation. Privacy standards The key is selecting the right tool for each application and ensuring that personal data is collected The security industry continues to evolve, finding innovative ways to balance effective surveillance with privacy protection. By understanding this comprehensive range of technologies, security professionals can better serve their clients with solutions that address specific needs while maintaining appropriate privacy standards. The key is selecting the right tool for each application and ensuring that personal data is collected only when necessary and protected when it is not. Statistical analysis and pattern recognition The variety of facial recognition applications demonstrates that not all systems require storing personal information. Many modern solutions focus on statistical analysis and pattern recognition rather than individual identification, offering powerful security benefits while respecting privacy concerns. This balance of capability and responsibility represents the future of video security technology.
Security technology has witnessed huge advancements in recent years, particularly for those protecting critical assets or information. Facial and fingerprint recognition, ANPR and even 'mac addresses' or a person of interest's gait, now all make up the technology toolbox of forward-thinking organizations' security policy. However, humans remain the weakest link in any security chain, and the only way to correct this is to eliminate the human burden, argues Richard Hilson, head of sales for security access management specialist, Parking Facilities. Here, he examines the pitfalls in relying upon human intervention in critical national infrastructure (CNI) settings, and the future of biometrics to keep assets, information and personnel safe. Recent Verizon report 74 percent of corps are saying that insider threats are becoming more of a concern for them As with any workplace initiative, be it a simple recycling policy or a corporate password protection directive, technology is only as good as those who implement or operate it. While technology can be fallible and gremlins do arise, it’s never as flawed as us mere humans with our unreliable ‘on/off’ switch. Likewise, we carry the ability to reason, to override procedures, or ignore policy, should we wish. Or as it happens, just make mistakes. In fact, according to a recent Verizon report, two out of three insider attacks happen as a result of negligence, and 74 percent of organizations are saying that insider threats are becoming more of a concern for them. Fundamental security practices Security breaches aren’t limited to external threats either, whether intentionally or not, they can come from within. Humans can, and do, ‘go rogue’, whether that’s pre-meditated criminal or malicious intent, or just by taking shortcuts. While data breaches court most news headlines in this digital era, some of the most significant security risks are those posed when employees neglect fundamental security practices such as sharing passwords or access cards. Employee negligence and insider threats Insider negligence remains one of the pioneering causes of security breaches Insider negligence remains one of the pioneering causes of security breaches. Employees who share passwords or access cards may do so out of convenience, ignorance, or a misplaced sense of trust. Unfortunately, this creates vulnerabilities that are left open to exploitation. When multiple employees share credentials, it becomes difficult to trace actions to a single individual. This lack of accountability can complicate incident investigations and allows malicious activities to go undetected. Emergency services resources Furthermore, the sharing of passwords or access cards means inaccurate accounting of personnel, and in the event of an evacuation or major incident, central IT systems will hold misleading information of employees’ locations which could have a huge impact upon safety and potentially emergency services resources. Employees with malicious intent can exploit shared credentials to carry out unauthorized activities while shifting blame to others, increasing the risk of deliberate sabotage or theft of sensitive data. Even when there is no malicious intent, employees who share access credentials risk unintentionally exposing them to unauthorized individuals, such as contractors, visitors, or external attackers. What happens when employees compromise security? Access cards are designed to limit entry to restricted physical locations. When shared, unauthorized personnel could enter secure areas such as control rooms, rail lines, large construction sites, data centers, power plants or indeed any site meant to be kept secure. This creates opportunities for sabotage, theft, or corporate espionage. Sensitive data held within critical sites, such as blueprints, system controls, and customer records Likewise, shared passwords can lead to unauthorized entry into IT systems, allowing hackers to install malware, ransomware, or spyware. For example, a cybercriminal gaining access to an energy grid system could shut down power to entire regions, causing chaos to millions of people, and disrupting essential services. And not all data breaches are caused by online hackers gaining entry through unsecure firewalls. Sensitive information held within critical sites, such as blueprints, system controls, and customer records, becomes vulnerable when access credentials are shared too, and the disclosure of such information can have a serious impact upon a company’s bottom line, operations, and ultimately its reputation. Eliminating the human burden One way to prevent human error, or to thwart malpractice is to reduce the burden upon employees to be compliant, and eliminate our flaws by using technology that requires no intervention, decision-making or reason. Facial recognition is widely used in the civil world now, despite the concerns of various lobbyists. Used correctly it is not a ‘catch all’, but an instant recognition of persons of interest cross referenced against a database of known suspects. Our car parks are governed by automatic number plate recognition (ANPR) to gain access in and out, while border controls are using advanced biometrics for everything from facial and fingerprint recognition, through to recognition of human characteristics and gait, for both entry and to apprehend. The UK Home Office is even accelerating its transition to digital border management, using biometric technology to improve efficiencies, safety, and to track and capture known or illegal persons. What of the CNI sites? But what of the corporate world? What of the CNI sites, our airports, our national construction developments such as HS2 or our high-rise office spaces? We always ask this very question, and also ‘can you afford a security breach’ in whatever environment you’re in? Because the smart, cloud-based technology being used by governments, law enforcement authorities and Border Force have cascaded down through the civil and corporate worlds. Immediate safety and security Security-conscious corps are diligently removing human error, by eliminating the human burden Security-conscious organizations are now diligently removing human error, by eliminating the human burden. With cloud-managed software not only are access points managed through biometric integration, but it also overcomes the issues mentioned earlier around accountability - in that the cloud will always register who has passed through an access point, or out of it. This is critical for both immediate safety and security but also for matters arising from a crisis, or emergency situation. It’s also less admin-heavy, more cost-effective and can manage and store employee records, including background checks. Employee or contractor data is encrypted, their information is safe, their interactions are secure, and businesses are protected. Implement robust access management systems Simple acts of negligence, such as sharing passwords or access cards, can open the door to catastrophic consequences, operational disruption, financial loss, and even, in the case of CNI, national security risks. To mitigate this, organizations can do worse than to implement robust access management systems, and in doing so, release employees from having to be accountable for ensuring the security of the sites in which they work. As artificial intelligence evolves, I see even more robust biometrics coming to the fore, until such time we work and live in environments that are controlled without us even knowing security checkpoints are all around us, and access management happening at every step. It will become as ‘every day’ as an automatic door allowing entry into our local supermarket - but we’re not quite there yet.
It’s no secret that the data security sector is constantly changing. It has an annual CGR of about 12.3%. Future trends in data security Much of this has to do with the rise of cybercrime in recent years, with reports showing that cyberattacks happen as often as every 39 seconds. To combat the growing rate of cybercrime, data security has been on the rise. As we journey further into this era, it becomes evident that a spectrum of significant trends is molding the future of data security. This exploration delves into a selection of these trends, unraveling their importance and the potential implications they carry 1. AI security tools will increase Artificial Intelligence is also being used in the development of smart attacks and malware The introduction of Artificial Intelligence in the data security industry brought significant changes, especially in cybersecurity. AI has been the golden standard for face detection, natural language processing, automated threat detection, and automated security systems. Additionally, Artificial Intelligence is also being used in the development of smart attacks and malware, bypassing even the latest security protocols in data control. And as time progresses, AI security tools will flourish and dominate the scene. Let’s take a more in-depth look at three of the top AI security tools. Targeted attack analysis tool Manufacturers utilize targeted attack analysis tools to uncover targeted and stealthy attacks. Artificial Intelligence can be applied to the program’s capabilities, processes, and knowledge. For instance, Symantec launched this tool to combat the Dragon 2.0 attack in 2022. The phishing attack reprimanded multiple energy companies while trying to gain access to their operational networks. Targeted Attack Analysis Tools can analyze incidents and look for similarities from previous situations. They also help detect suspicious activities and collect all the necessary data to determine whether a specific action is malicious. Intercept X tool Results from the Intercept X Tool feature high accuracy and a low false positive rate Sophos, a British security hardware and software company, launched the Intercept X Tool. It engages a neural network that records and analyses data like a human brain. Sophos’ Intercept X Tool can extract features from a single file and perform a deep analysis. It detects malicious activities within 20 milliseconds. Plus, it’s also trained to work on bi-directional sharing and real-world feedback of threat intelligence. Results from the Intercept X Tool feature high accuracy and a low false positive rate. IBM Watson Technology IBM’s QRadar Advisor uses IBM Watson Technology, a unique AI tool for fighting cyber attacks. Artificial Intelligence can auto-investigate activities and indicators for potential exploitation or compromise. With cognitive reasoning, IBM Watson Technology can present critical insights to accelerate the response cycle. Security analysts can utilize this technology to search for threat incidents, reducing the risk of letting them fly under the radar. 2. Blockchain as a security solution It guarantees no points of failure or hackable entrances that can expose datasets inside the system Blockchain is a type of distributed ledger technology (DLT) that aims to establish trust within an untrusting ecosystem. Today it’s one of the most robust cybersecurity technologies in the industry. Blockchain utilizes a decentralized ledger system, but your team members can still gain access to transparent information in the cloud. Members can also record, pass along, and view necessary transactional data in the blockchain. The entire blockchain process maintains data integrity within the system while establishing trust among team members. It guarantees no points of failure or hackable entrances that can expose datasets inside the system. Cybersecurity, biometrics Cybersecurity primarily benefits from these features because blockchain can create a secure and robust wall between data and hackers. On top of that, blockchain ledgers can include biometrics like fingerprints and retina scans. These prevent hackers from accessing any private data. Because blockchain is decentralized, it also limits hackable data. Together with the technology’s record-keeping system, each node is provided insight into data manipulation exposing real-time cybercrime attempts. 3. Increased and widened access control Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data Access control is critical in data security. More than a valuable security tool, business leaders can use access control to regulate people accessing any given resource. A company with an IT security setting can control who has the liberty to edit certain files. One of the primary goals of access control is to minimize threats or attacks to organizations and businesses to keep people and data secure. Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data protection laws. Benefits The benefits of increased and widened access control include: Identifying who can access and control your data at specific time intervals. Protecting data from overwriting, accidental deletion, and malicious intent. User permissions that can be readily changed. Compliance and regulation with data privacy laws. Central management of access to data through a reporting portal or a dashboard. Multi-factor authentication Access control comes in various types and systems, so it’s critical to know the features of what you’re looking for. The most common type is multi-factor authentication or MFA. It involves multiple steps before logging in, requiring the user to enter other relevant information besides the password. Some other examples of information include biometrics, answering a security question, or entering a code sent to the user’s email address. Two-factor authentication, role-based access control Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession. Another type of access control is role-based access control. In this setup, only one individual can set up access guidelines and grant permissions to specific team members within an organization. 4. Greater use of the zero-trust security model The zero-trust security model is a framework that requires every user within and outside the organization to undergo authentication, authorization, and validation. These are all essential to ensure proper security configuration before access is granted to the company’s applications and data. A zero-trust model assumes that anyone can cause data breaches and that a traditional network edge is not taken into effect. Moreover, it addresses the following modern-day challenges: Hybrid cloud environments. Security of remote workers. Ransomware threats. This framework utilizes the combination of multiple advanced technologies, including: A risk-based multi-factor authentication. Endpoint security. Identity protection. Cloud workload technology. The zero-trust model uses all these innovative tools for system identification, user verification, access consideration, and system security maintenance. Constant validation and monitoring Enforcing strict policies and compliance with data privacy laws are also essential Additionally, it also considers data encryption, email security, and asset verification before establishing connections with applications. The architecture of a zero-trust framework requires constant validation and monitoring of the users and the devices they are using. Enforcing strict policies and compliance with data privacy laws are also essential. More importantly, the zero trust architecture requires all organizations to be aware of all their available services and accounts to gain complete control of data handling and manipulation. 5. Increased privacy regulations Privacy regulations and policies guide organizations in proper data control, handling, and security. These policies guide organizations in proper data control, handling, and security. As a responsible business owner, you must comply with these regulations to avoid legal issues. With cybersecurity attacks becoming common, expect increased and stricter privacy regulations to be released in the next few years. While current policies are still taken into effect, various modifications and adjustments will occur to compete with the rising numbers of data breaches, thefts, data loss, and more. California Privacy Rights Act (CPRA) Currently, the California Privacy Rights Act (CPRA) is the most comprehensive legislation on state data privacy. It only started to take effect on January 1, 2023. The CPRA introduces the following principles: Broad individual consumer rights. Significant duties of people who need to collect sensitive and personal information. Additional definitions of data privacy and security. An individual’s duties include releasing information about data collection to concerned data subjects and proper access, correction, and deletion of information. Final thoughts 2023 is a big year for data security. Trends such as increased adoption of zero-trust policies, a greater reliance on AI security tools, and the implementation of blockchain as a security solution are all things we expect to see shortly. Staying up-to-date with these trends is important for keeping your business current and ensuring that you’re adhering to new and changing regulations. Doing so can give you an edge over the competition and keep you out of legal hot water.
Security beat
As the deal/no deal prospects of Brexit are tossed in a whirlwind of UK and EU politics, the uncertainty of the back-and-forth has broadly impacted general economic trends, and by extension, the physical security market. The new deadline for a Brexit agreement is October 31, already postponed six months from the scheduled April 12 departure date. Numbers show that Britain’s GDP shrank in the second quarter, possibly reflecting fewer exports because of Brexit uncertainty. And beyond the current indecision lies the long-term impact of a possible change in trading status between the United Kingdom and continental Europe. Other issues include capital flow and labor mobility. Brexit uncertainty leading to security concerns Loss of shared information with the EU will make the UK less safe “Companies … are unclear about their future,” comments Martin Warren of the Institute of Chartered Accountants in England and Wales. “Companies are making decisions now about jobs, supply chains, headquarters and asset locations, incurring significant, and possibly unnecessary, cost and upheaval.” Warren fears the destructive effects of a ‘no deal’ outcome and hopes politicians will break the deadlock and restore business confidence. Security implications of Brexit extend beyond economics. Loss of shared information with the EU will make the UK less safe. Extradition across EU borders will be more difficult, and exchange of data such as fingerprints and vehicle registrations is at risk. The Irish border after Brexit is of particular concern to security professionals. Countering threat of international terrorism Robert Hall of London First and Alison Wakefield of Security Institute say the security impact of departing the EU will be long lasting and profound. “In security terms, the UK will still have to contend with international terrorism, transnational crime and the global movement of people, all challenges that require wide scale cooperation.” They add that leaving the EU will require “a significant investment in people, resources and databases to cope with the anticipated volumes of traffic through ports, airports and tunnels.” Analyst company IHS Markit earlier commented about the impact on the security industry of Brexit’s drag on the UK economy, “Access control, intruder and fire alarm markets typically track construction rates closely and are forecast to be affected most. However, a large cut to infrastructure spending would be just as damaging to the video surveillance market.” UK security companies Prefer ‘soft exit’ from EU If a ‘soft exit’ trade deal is not negotiated, the UK would have to revert to WTO trade rules If a ‘soft exit’ trade deal is not negotiated, the UK would have to revert to World Trade Organization (WTO) trade rules, which means tariffs on trade between the UK and the EU, says IHS Markit. There are five British-based access-control and intruder-alarm vendors supplying the European market in significant quantity – each with revenue exceeding $10 million. IHS Markit estimates these companies combined account for less than 10 percent of total European, Middle-Eastern and African (EMEA) market revenues for both industries. Uncertain future of UK security marketplace Asset protection specialist VPS Security Services has warned that the ongoing Brexit saga will likely lead to a rise in vacant commercial and residential properties as developers and investors are more reluctant to move forward with their UK real estate strategies. Seemingly endless machinations and shifting proposals are making the eventual outcome of Brexit very much a guessing game. Uncertainty translates into a volatile and changing outlook, and the eventual impact on the broader economy is an open question. As a reflection of that economy, the security marketplace will inevitably feel the economic impact, too, not to mention the new security challenges likely to ensue.
Effective access control can be achieved without the use of cards using a new generation of secure facial authentication enabled by artificial intelligence and machine learning. Alcatraz AI is introducing a system that deploys a sensing device, about the size of a badge reader, with multiple color and infrared cameras that can detect facial features and confirm an identity. Real-time 3-D facial mapping avoids anyone using a photograph, video or mask to spoof the system and confirms there is a real person that matches the stored facial image. System Helps In Tailgating Mitigation Deep neural networks, powered by NVIDIA, enable the system to achieve new levels of frictionless access control, says Vince Gaydarzhiev, CEO of Alcatraz AI. Computer processing is achieved at the edge to ensure speedy and secure access control. We saw an opportunity to create a system that solves issues of tailgating and addresses the need for security without increasing friction"“We saw an opportunity to create a system that solves issues of tailgating and addresses the need for security without increasing friction,” says Gaydarzhiev. The accuracy of the system lessens the need for security guards, he says. The Silicon Valley startup, currently with 20 employees, was founded in early 2016 by a team from Apple, NVIDIA and Lily Robotics with a goal of targeting mid- to large-sized corporations that currently have deployed badging systems. The company has raised close to $6M from venture capital firms and individuals, and Johnson Controls/Tyco has invested in the startup. Alcatraz AI’s sensor device, mounted near a door, confirms a user’s identity and communicates the user’s badge number to the existing access control infrastructure. “The system improves the facial profile every time, using the neural network to be even more accurate in the future,” says Gaydarzhiev. He says it is the industry’s first “instant one-factor authentication for multi-person in-the-flow sensing.” The system is less expensive than previous facial authentication systems and does not require users to be very close to the reader Easy Enrollment And Deployment Enrollment in the system is easy. Companies can deploy a separate enrollment station, or any reader can be used for enrollment. After badging in a couple of times, the face matching system “enrols” the face with the associated badge number, thus allowing the user to dispense with the badge altogether. In the future, the frictionless system simply recognises the user and opens the door. A user company can quickly deploy the system at locations where thousands of employees have access, without requiring employees to go to HR for enrollment. Gaydarzhiev says accuracy of the system is no less than that of iris scanning, and the accuracy is configurable for specific needs. He says the system is less expensive than previous facial authentication systems and does not require users to be very close to the reader. Facial authentication is also more flexible than iris scanning or fingerprinting. Detecting Intent From Positioning Of Eyes The system detects intent from the positioning of the eyes and body to avoid opening a door unintentionallyIn contrast to near field communication (NFC) or Bluetooth systems, the technology does not require a compatible smart phone or have issues of communication range. There is no need for users to stop and perform an action or gesture to signal intent. The system detects intent from the positioning of the eyes and body to avoid opening a door unintentionally, says Gaydarzhiev. Alcatraz AI is targeting high-tech enterprises, including healthcare, government and eventually banks. Currently they have three pilot installations among large global software companies and are undergoing trials with some government agencies. Today, they sell direct to end users, but the intent is to develop a dealer channel that will account for most of the sales.
Activity slowed on the last day of ISC West in Las Vegas, but there was plenty of momentum remaining and plenty more to see. In the end, Reed Exhibitions declared 2018 the biggest and most successful year to date for the show. There were an additional 4,000 square feet of exhibit space compared to last year and a 6 percent growth in overall attendance, according to Reed. The cloud, biometrics, deep learning and other technologies were among the big topics at the show, and even smaller exhibitors were pleased with the results. In particular, emerging technologies were successfully highlighted. Cloud-based Video Systems Cloud video company Eagle Eye Networks announced multiple new offerings at ISC West. One was the first cloud-based video system that accommodates HD-over-coax cameras using the HD-TVI protocol to operate over existing coaxial cabling. In effect, cameras connect with an HD-TVI recorder, which plugs into Eagle Eye Networks’ on-site hardware “bridge” connecting to the Internet. Eagle Eye Networks has also integrated Hikvision body-worn cameras into their cloud system; transmitting video using the Eagle Eye Bridge ensures end-to-end encryption and the evidentiary integrity of the video. Analytics in the cloud can be turned on and off at will for each camera, and could be deployed over a weekend and switched off the following week “A few years ago, fewer customers were ready to adopt the cloud,” says Ken Francis, President of Eagle Eye Networks. “Now market adoption is changing, and customers don’t want on-site hardware. End-users are driving the move to cloud systems.” He estimates the evolution is about halfway complete, and Eagle Eye Networks continues to sign up new dealers every month because their customers are asking for the cloud. Eagle Eye Networks’ third new offering at ISC West is “analytics in the cloud,” including familiar analytics such as intrusion, people counting and loitering. Francis says the economics of the cloud make implementation of analytics much more affordable – about $4 per camera. The economics of the cloud make implementation of analytics much more affordable Augmented Identity: Biometrics In Security Analytics in the cloud can be turned on and off at will for each camera. For example, analytics could be deployed over a weekend and then switched off the following week. “It’s a far more economically attractive and cost-effective service than on-site,” says Francis. Biometrics continue to make their way into the mainstream of the security market, and IDEMIA brought its message of “augmented identity” to ISC West. IDEMIA (formerly OT-Morpho) provides systems to the largest biometrics users in the world, including big customers such as the FBI and Interpol, and large-scale government projects around the globe. “If you can handle projects that big, enterprise applications are no problem,” says Gary Jones, Vice President, Global Channel & Marketing, Biometric Access & Time Solutions. He says that the company’s technologies apply to any vertical market, and they are especially common in major airports and big financial institutions, in addition to government. The company’s MorphoWave product allows users to wave their hand, and the system captures a three-dimensional shape of fingerprints. The touchless system is also “frictionless” -- it enables fast decision-making that promotes high throughput rates. Artificial Intelligence Applications AI and deep learning have been big topics of conversation at ISC West, and I saw a company on the last day of the show with a different take on the subject. BrainChip uses a type of AI called “spiking neural networking” that models the operation of neurons in the human brain - in contrast to “convolutional neural networks,” which use a series of math functions to train from pre-labelled data sets. The BrainChip Studio software can search vast amounts of video footage rapidly to identify either faces, patterns or objects. Applications are in law enforcement, counter-terrorism and intelligence agencies.The BrainChip Studio software can search vast amounts of video footage rapidly to identify either faces, patterns or objects “We search for specific things,” said Bob Beachler, Senior Vice President, Marketing and Business Development. The software can search hundreds of live or recorded camera feeds for a unique graphic pattern on an item of clothing or on a bag carried by a person, for example. The technology only requires modest processing power and consumes little energy, so it can be used with legacy systems without requiring hardware or infrastructure upgrades. Emerging Technology Zone A new Emerging Technology Zone at ISC West included participation by around 40 companies that are startups and/or new to the security industry. The section opened an hour before the main show floor and was located near the registration area, which increased traffic. “Generally speaking some people said it was hard to find, but I think it’s better for us as someone new to the market, rather than being on the main floor where you can get lost in the shuffle,” said Jeffrey Weiner, Vice President, Networks & Business Solutions, at Mersoft. “It was really smart that they opened this an hour earlier.” Mersoft, one of the Emerging Technology Zone exhibitors, has developed a software product to help the security industry do a better job of streaming live video. The software eliminates the startup delay and lag in live video. With dedicated software, video can be consumed by a browser or mobile app more easily Live Video Streaming “We accomplish that in two ways,” says Weiner. “One, we don’t trans-code the video into another format. Instead, we convert a security camera’s video from RTSP (real time streaming protocol) to WebRTC (Web Real-Time Communication), an open-source technology that has been used extensively in video conferencing, but not so much in security. The video can be consumed by a browser or mobile app more easily, and we don’t need a player on the client, which is another way we reduce lag.” Another advantage is that WebRTC is natively encrypted; every packet is encrypted. In contrast, applications that transmit RTSP have to be wrapped in a VPN (virtual private network) tunnel, which takes some effort to maintain and is a battery hog on a mobile device. Also, multi-casting of video is easier, even using streams of various resolutions. Mersoft works through partnerships, offering a cloud-hosted service on Amazon and a version that can be installed on a local server. They have worked with several DIY camera sellers (who use cloud services), and with some major commercial service providers. “A new partnership strategy we are exploring is with systems integrators, who can incorporate Mersoft and provide a differentiator by improving their video performance,” says Weiner. The 22-year-old company is new to security, and ISC West provides opportunities for in-depth conversations preparing for a future in the security sector. Customizable Turnstile Solutions Delta highlighted their new designer series turnstiles, whose colorful appearance led booth visitors to ask about customization Even the smaller companies, located toward the back of the hall, were enthusiastic about ISC West this year. “The show has been great,” says Vanessa Howell, project manager of Delta Turnstiles. “We did get a lot of traffic. I am a niche product, so it’s not so much about quantity as quality [of leads]. I had great quality at the show.” Being away from competitors, which are grouped next to each other in the front of the hall, was an upside of the turnstile company’s booth location toward the back. Delta highlighted their new designer series turnstiles, whose colorful appearance led booth visitors to ask about customization. “They ask: ‘Why are turnstiles only sold in basic models?’” says Howell. “’Why can’t they look like a piece of art since they are the first thing people see when they enter a building?’ People are very open to making them prettier.” Delta Turnstiles has been coming to ISC West since 2006. “I have manufacturer’s reps, and this is one of two times I get to see them in one place, and they bring a lot of customers to me at the booth,” says Howell. “This is my only face-to-face meetings with some customers. I speak mostly over the phone.” Valuable face-to-face engagement was a benefit of ISC West, and many of those meetings will likely set the stage for continuing successes in our vibrant market. Until next year.
Case studies
For years, the Civil Police of the State of São Paulo, Brazil’s largest state police force faced significant challenges with criminal bookings and identification, including: A Fragmented Identity System - Each of Brazil’s 27 states has its own siloed program that does not interconnect. This not only hinders statewide criminal booking but also undermines the community’s confidence in the criminal justice system. Identity Fraud With Multiple IDs - Imagine having 43 identities. This was the case for one unlawful Brazilian. The prevalence of identity fraud is extremely high across the country. If a person wants to hide their identity, it’s common for them to simply move to another state and set up a new profile. Manual Ink-and-Paper Fingerprinting Techniques - Many law enforcement departments across Brazil administered manual fingerprinting techniques, resulting in inaccuracies and low matching rates. Slow, Inefficient Criminal Booking Processes - Inefficiency was another setback for justice. It took numerous steps to confirm one’s identity and, on average, a whole workweek to get matching results returned. Biometric National ID Compliance - The civil police must modernize systems to comply with the Brazilian government’s mandates for all citizens to tie biometrics to their IDs. The Civil Police of the State of São Paulo needed a more reliable and efficient solution to break down identification silos and put the agency on the path toward a unified, national system rooted in the power of biometrics. HID's solution The HID ten-print scanner is designed to quickly capture flat and rolled fingerprints for background checks Working through HID’s partner, Golden Distribuidora, one of Brazil’s largest distributors of IT products, the Civil Police of the State of São Paulo selected a comprehensive biometrics-based identification system called BioKit, featuring HID’s ten-print scanner. The HID ten-print scanner is designed to quickly capture flat and rolled fingerprints for background checks and identity validation programs. It is also certified for FBI Appendix F (FAP 60) and offers an economical approach to fingerprint acquisition without sacrificing image quality. Automated Biometric Identification System The criminal booking process at São Paulo civil police stations is simplified and can be accomplished in minutes not days. First, agents use HID’s ten-print scanner to capture fingerprints and determine if the individual has a biometric file on record. The fingerprint images are compared against the state-run Automated Biometric Identification System (ABIS). If there is a match, the civil police move forward with their investigation. If there is no match, the officer then creates a new biographic/biometric profile for the individual in question and enrolls them into the ABIS. HID ten-print scanner HID ten-print scanners deliver superior performance and reliability at a competitive price point. Key advantages include: High-Quality Tenprint Capture - The scanner is FBI Appendix F (FAP 60) certified and can quickly capture high-resolution rolled and flat fingerprints. Ease of Use - User-friendly pictographs and LED indicators simplify the process for operators. Automatic Capture - Patented “Auto-Capture” offers fast and error-free image capture. Difficult Fingerprint Capability - An optional silicone membrane improves image quality for dry or damaged skin ensuring consistent results. ABIS Integration - The scanner seamlessly integrates with Brazil’s Automated Biometric Identification System (ABIS) to enable quick and accurate background checks. Results delivered Using the BioKit system, featuring the HID ten-print scanner significantly streamlines the criminal booking Using the BioKit system, featuring the HID ten-print scanner significantly streamlines the criminal booking process and improves matching accuracy for the State of São Paulo Civil Police. “Working with criminals can be difficult and dangerous, and the HID ten-print scanners help us identify and book criminals quickly and simply,” said Dr. Luiz Ortiz, Chief Delegate, Civil Police of the State of São Paulo. Easy to use Dr. Luiz Ortiz adds, “The HID ten-print scanner is easy to use and provides clear direction through pictographs, which is a big differentiator from other offerings.” To date, the BioKit system with HID’s print scanners is deployed in 500 civil police stations throughout São Paulo. This system has transformed criminal booking and identification processes, resulting in an increase in solved criminal cases and a steep reduction in identity fraud. HID fingerprint technology “What used to take 4 to 5 days is now done in minutes using the BioKit system and HID fingerprint technology,” said Dr. Ortiz. Dr. Ortiz adds, “Our agents can accurately identify or onboard suspects, and each new biometric enrollment into the centralized ABIS contributes to strengthening our country’s overall identity system and ability to bring about justice faster and smarter.” Biometric enrollment and verification “Each individual the Civil Police of the State of São Paulo onboards ties to a single set of fingerprints that verifies their true identity,” said Danilo Fernandes, Business Development Manager at Golden Distribuidora. Danilo Fernandes adds, “Utilizing biometric enrollment and verification, our nation has the potential to streamline millions of records, while preventing countless cases of fraud. This establishes a fierce force to fight fraud here in Brazil.” A simple, fast, and trusted experience Additional use cases for the BioKit + HID ten-print scanner, beyond criminal bookings, include border control, background checks, correctional centers, courtrooms, voter registration, and national ID programs. The team at Golden Distribuidora expects to continue distributing these biometric systems throughout the country to support Brazil in combating fraud and making biometric enrollment and identification a simple, fast, and trusted experience for all citizens and stakeholders.
Established in 1997, Dubai-based BMA International operates fashion retail in the Middle East and Asia across the Kingdom of Saudi Arabia (KSA), United Arab Emirates (UAE), Bahrain, Oman, Kuwait and Qatar with more than 250 stores offering two major brands — Redtag and twenty4. BMA’s steady growth is a testament to its focus on building trust with its shoppers, employees, suppliers and stakeholders to create a company that is people-centric, ambitious and results-oriented. Challenge Fraud is a common problem in the retail sector, particularly within large chains with hundreds of locations and tens of thousands of employees. BMA’s retail stores were no exception. Following an internal audit, security of point-of-sale (POS) terminals in retail outlets were identified as a serious concern, particularly the misuse of floor supervisors’ credentials to access terminals and modify or cancel transactions. The problem persisted even after BMA switched from passwords to a smart card-based authentication system The problem persisted even after BMA switched from passwords to a smart card-based authentication system. The most common issues involved supervisors leaving smart cards with cashiers to use in their absence and failing to return the cards when separation from an employer occurs — a frequent occurrence as many of BMA’s retail employees are expatriates who often return to their home countries. Fraudulent use of the smart card was also a common problem. Once a sale was completed and the customer had left the store with their purchased items, the smart card could be used to improperly access the system so the cashier could void the transaction and pocket the “refund,” resulting in both monetary and inventory losses. Biometric-based system “BMA’s internal auditors were concerned with the lack of control over the cards and the potential for fraudulent transactions due to their mishandling. They observed clear gaps in security and authentication practices that led directly to fraud and revenue leakage, resulting in the Internal Audit Committee recommending to the BMA Board of Directors that action be taken to plug the security holes by tightening the authentication process,” said Nainan M. Kurian, CEO of Technowave International LLC. The decision was made to transition authentication to a biometric-based system that would provide the required security at a competitive price that aligned with the esthetics of the retail stores. The system also needed to be compatible with the Oracle Retail Xstore Office Cloud Service, which BMA International was adopting across its brands. Solution A fingerprint reader from HID is ideal for use by multiple people in a shared environment BMA International and its technology partner, Technowave International LLC, determined that the HID DigitalPersona® 4500 Fingerprint Reader met all their requirements — a decision supported by recommendations from other retailers that had deployed the product, and by the fact that competitive solutions were incompatible with Oracle Retail Xstore, a crucial requirement. A USB peripheral with a compact design to conserve space, this fingerprint reader from HID is ideal for use by multiple people in a shared environment. Its professional, modern design looks elegant in retail settings while offering superior authentication control via biometric functionality that uses optical scanning technology to achieve excellent image quality and reliability. HID DigitalPersona 4500 Fingerprint Reader With this easy-to-use technology, floor supervisors simply place their finger on the reader window, which rapidly captures and encrypts the fingerprint image, and then provides a red flash as a visual cue indicating that it was properly captured. That image is sent to the DigitalPersona FingerJetTM biometric engine for verification, and once the user has been authenticated, access to the POS terminal is granted. “Deploying the HID DigitalPersona 4500 Fingerprint Reader was simple and caused no disruption to retail operations. It paved the way for significant reduction in the malpractice that had been occurring with the smart card system,” said Kurian. Result Since deploying more than 1,100 HID fingerprint readers in retail outlets across KSA, UAE, Oman, Bahrain, Kuwait and Qatar, BMA has eliminated nearly all POS fraud and abuse. The system has also driven tangible improvements in the attendance and punctuality of floor supervisors, who must now be physically present in the store for authentication to take place. The HID authentication system is also capable of multiple types of authentications — providing flexibility that is appreciated by users who work at multiple locations. “Because the HID DigitalPersona 4500 Fingerprint Reader requires proof of presence for authentication, there is greater accountability among supervisors which resulted in immediate cessation of POS fraud and stopped both revenue and inventory leakage. The exceptional support provided by HID Global has also allowed BMA to take full advantage of the system’s functionality and flexibility,” said Kurian.
Biometrics company, Fingerprint Cards AB (Fingerprints™), has upgraded the physical access security of its Gothenburg HQ. S-Key biometric access cards from Freevolt Technologies Limited, which embed Fingerprints’ own T2 sensors, have been implemented across the entire Gothenburg site. The updated authentication system further strengthens Fingerprints’ workplace security and enables role-based access control, while ensuring a convenient and easy-to-use experience. Role-based access control Fingerprints’ Gothenburg HQ has security gates to enter and exit the building, and restricted areas for hardware and software R&D. By replacing access keyfobs with biometrics access cards, site-wide security has been enhanced and role-based access control has been enabled to better control access to sensitive areas of the site. By replacing traditional security methods based on something they know/have with something they are, multi-factor authentication has been enabled while maintaining convenience for employees. Fingerprints’ latest ‘T2’ sensors Solution eliminates the security risk of lost or stolen cards, without adding infrastructure costs Caroline Krüger, CHRO of Fingerprints comments: “The workplace has evolved significantly in recent years. At Fingerprints, we offer hybrid working while still ensuring our workforce has 24/7 access to HQ. Amidst this dynamic working environment, it is essential our team feels the workplace is accessible and safe. This requires a flexible, secure, and convenient access control solution.” Fingerprints has implemented Freevolt’s flagship biometric access card solution, S-Key. The solution eliminates the security risk of lost or stolen cards, without adding infrastructure costs. The card incorporates Fingerprints’ latest ‘T2’ sensors which deliver optimized image quality, processing speed, and power efficiency. Traditional security methods Adam Philpott, CEO of Fingerprints comments: “To meet today’s security challenges we must move away from traditional security methods. And, as a biometrics company, it is important that we lead the way in ensuring robust, frictionless security in our own operations." "There is an opportunity here too; what can we learn, what innovations will we identify by using these systems day to day? I look forward to continuing our strong and innovative collaboration with Freevolt technologies.” Energy harvesting technology Gonzalo de Gisbert, Head of Product & Business Development at Freevolt Technologies, adds: “Fingerprints are pioneers in biometrics, with sensors in billions of products, so they know what makes a good biometric solution. We’re therefore thrilled that Fingerprints has chosen S-Key to strengthen security at their global headquarters, in Gothenburg." "Our pioneering radio frequency energy harvesting technology combined with Fingerprints’ ‘T2’ sensors, known as FPC 1323, enables S-Key to be completely battery-less, lasting for many years. Roll-out was seamless, with everyone set up in less than 1 hour. That’s simple, safe, and secure biometrics, powered by Freevolt.”
Situated in Vadodara, Gujarat, India, this venerable university stands as one of the oldest in the country, tracing its roots back to 1881. Honoring a forward-thinking ruler, it has evolved into a prominent public institution that provides a diverse array of academic programs spanning arts, sciences, engineering, and management. Dedicated to delivering top-notch education and cultivating a culture of research and innovation, the university features a sprawling campus and holds a distinguished position for its commitment to excellence in the realm of Indian education. Project Overview Confronted with a significant hurdle in the form of a competitor's attendance tracking system for its teaching staff, the university embarked on a quest for a more precise and streamlined method to record daily attendance across its various campuses. The primary goal was to establish a centralized platform dedicated to attendance management, focusing on improving employee access to attendance records and facilitating efficient leave request management. A key consideration was the necessity for a tailored provision to accommodate professors frequently moving A key consideration was the necessity for a tailored provision to accommodate professors frequently moving across campuses for lecture commitments. This case study explores the university's journey in pursuit of a robust attendance management solution catering to 3000 users, addressing specific challenges and optimizing operational efficiency. University challenges The university encountered significant challenges in ensuring the smooth operation of its Attendance Management System, including: Inefficiency in the Existing Attendance Management Solution: The university grappled with issues stemming from an ineffective competitor's attendance management system, adding complexity rather than facilitating streamlined operations. This inefficiency extended to the complexities of managing attendance across diverse faculties, further complicating university-level payroll processing. Inconsistencies in Daily Attendance Recording for Teaching Staff: A crucial necessity for the university was the seamless daily recording of professors' attendance. The imperative for a well-organized system became evident to ensure accurate tracking and efficient payroll management. Lack of Proper Attendance Management Across Multiple Campuses: With campuses spread across different locations, the university faced the pressing need to centralize attendance data. This centralization was crucial for the effective management of attendance records across all campus locations. Delayed Data Transmission from Devices: The existing solution encountered difficulties as punch data from devices experienced delays in reaching the system promptly. This lag resulted in complications, necessitating manual synchronization efforts to rectify the issue. Employee Accessibility Issues for Attendance Data and Leave Management: Staff members encountered limitations in accessing their attendance data through the current system. Furthermore, the absence of support for submitting leave requests contributed to inefficient leave management practices, prompting a demand for more effective solutions. Faced with these operational challenges, the university embarked on a quest for innovative solutions to improve its attendance management processes' overall efficiency and effectiveness. Matrix's solution To address the critical issues faced by the client, Matrix successfully implemented a comprehensive solution that effectively resolved the organizational challenges they were encountering. Matrix executed its Attendance Management System to achieve: Deployment of a Comprehensive Attendance Management System: Matrix effectively implemented an enterprise-grade Time-Attendance Solution, successfully tackling the client's organizational hurdles in attendance management. This solution streamlined the entire attendance process, simplifying complexities across various campuses. Seamless Attendance Recording for Teaching Staff: Matrix introduced biometric devices across different faculties, enabling effortless attendance logging for teaching staff. The widespread availability of devices ensured accurate tracking and efficient payroll management. Centralized Attendance Management Across Multiple Campuses: Matrix established a centralized solution for attendance management, consolidating data from various campuses. This centralized approach facilitated effective control and oversight of attendance across diverse locations. Automated Data Transmission from Devices: Matrix Time-Attendance terminals were equipped with automated data push technology. This feature ensured timely and automated data transfer from devices to the server, eliminating the need for manual synchronization and enhancing operational efficiency. User-Friendly Employee Self-Service Portal: Matrix provided a comprehensive solution, including an Employee Self-Service portal. This portal enabled users to access attendance data on their devices and submit leave requests. With its hierarchy-based approval system, Matrix streamlined the leave management process. Improved efficiency The innovative solutions offered by Matrix not only resolved the client's challenges but also significantly enhanced attendance operations, promoting improved efficiency throughout the organization. This case study highlights Matrix's capability to tailor solutions to meet unique client needs, ultimately optimizing business processes. Results achieved Matrix successfully streamlined the entire process, introducing clarity in payroll processing and simplifying attendance Matrix's deployment of its Enterprise-grade Time-Attendance Solution brought about a remarkable transformation in the operations of the historic university based in Vadodara. Confronting challenges posed by an inefficient attendance management system, Matrix successfully streamlined the entire process, introducing clarity in payroll processing and simplifying attendance tracking across diverse faculties. The use of Matrix biometric devices facilitated seamless attendance marking for teaching staff, contributing to efficient payroll management. Centralized attendance management The implementation of a centralized attendance management system across multiple campuses significantly improved control and efficiency in handling attendance data. Matrix addressed delays in data transmission by deploying terminals equipped with automated data push technology, eliminating the need for manual synchronization. Employee Self-Service Portal Matrix's provision of a hierarchy-based approval system streamlined the client’s leave management requirements Furthermore, the implementation included a user-friendly Employee Self-Service Portal, allowing staff to effortlessly view attendance data and submit leave requests. Matrix's provision of a hierarchy-based approval system streamlined the client’s leave management requirements. These tailored solutions markedly enhanced operational efficiency, resulting in a more streamlined, accurate, and transparent organizational operation. Matrix's success in optimizing attendance processes underscores its commitment to delivering innovative solutions tailored to the unique requirements of its clients. Products Offered COSEC VEGA FOT: Fingerprint and RFID card-based Time-Attendance Terminal COSEC CENTRA PLT: Platform-based User License COSEC CENTRA TAM: User License for Time-Attendance Management COSEC CENTRA ESS: User License for Employee Self-Service Management
IDEMIA has been selected by ACSA to implement its solution in South Africa’s three main international airports: OR Tambo, Cape Town, and King Shaka including the border clearance process using the latest e-Gates technologies. Interconnected with all the major airlines in the world, South Africa is a key country when it comes to air transportation in Africa. ID2Travel The four-year project started in October 2023 and will be deployed in three phases. As soon as 2026, nine South African airports will be equipped with IDEMIA’s end-to-end PFF solution: ID2Travel. IDEMIA’s win was made possible by the long-standing relationship with South Africa and in particular the successful implementation of the ABIS program with the Department of Home Affairs (DHA). Biometric solutions IDEMIA’s expertise and solutions regarding its biometric technologies, combine efficiency, accuracy, and equity The biometric solutions deployed in these airports (three international and six domestic) will enhance the quality of services offered to passengers all along their journey, from the check-in to the boarding of the plane. IDEMIA’s expertise in biometrics, repeatedly recognized in industry rankings, enables it to offer advanced fingerprint, facial, and iris biometric technologies that enhance passenger security while making their experience more seamless. The National Institute of Standards and Technology (NIST) latest test results underscore IDEMIA’s outstanding expertise and solutions regarding its biometric technologies, combining efficiency, accuracy, and equity. Facial recognition technology This partnership with ACSA builds on IDEMIA’s long-standing expertise in equipping world-class airports around the globe with its cutting-edge technologies. From Singapore’s Changi airport, which facilitates passenger flow from baggage check-in to boarding the plane, to India’s Delhi, Hyderabad, and Goa airports where facial recognition technology verifies the identity of domestic flyers, to trials at Lyon-Saint Exupéry and Paris-Orly (France), IDEMIA’s solutions are proven to be highly accurate, thereby offering the best security and an efficient and smooth passenger journey. Passenger facilitation solution This new solution will offer our passengers a seamless, unique, and secure new airport experience" "We are thrilled to be launching a new passenger facilitation solution at our nine ACSA airports, and for the first time in Southern Africa. Based on biometrics, airport processes will be automated using state-of-the-art technology from our partner IDEMIA," said Mthoko Mncwabe, Chief Information Officer, ACSA. "This new solution, which we are currently deploying in our airports, will offer our passengers a seamless, unique, and secure new airport experience. In line with our Sustain, Grow, and Digitise strategy, this solution positions ACSA as the pioneering airport management services company in Africa." Safe and smooth passenger experience "We are delighted to have been awarded this landmark contract for IDEMIA in Africa, which demonstrates the competitiveness and quality of the solutions that we provide to our clients worldwide," said Matt Cole, IDEMIA Executive Vice President of Public Security and Identity. "We are looking forward to working with ACSA on this historic and ambitious partnership, which will ultimately ensure a safer and smoother passenger experience at these nine South African airports."
On the occasion of INTERPOL’s 91st General Assembly – and 100th anniversary – the world’s largest international police organization announces the launch of its enhanced BioHUB, powered by IDEMIA’s newest Multibiometric Identification System (MBIS). Multibiometric Identification System This latest version, MBIS 5, integrates new generation algorithms, which provide a higher matching accuracy rate with a shorter response time and a more user-friendly interface. The first phase of its deployment to enhance the identification of potential Persons of Interest (POIs) for police investigations has already been operational since October 2023. The second phase, which will be rolled out over the next two years, will extend this tool to border control points. The system will then be able to perform up to 1 million forensic searches per day, including fingerprints, palm prints and portraits, making it the top performing automated biometric identification system on the market. Cutting-edge technology to help law enforcement IDEMIA still leads the biometric tech race covering iris, fingerprint and face recognition IDEMIA’s commitment to excellence is reflected in its consistently top-ranked identity and security technologies. IDEMIA still leads the biometric tech race covering iris, fingerprint and face recognition. NIST’s (National Institute of Standards and Technology) latest test results underscore IDEMIA’s outstanding expertise and solutions combining efficiency, accuracy and equity. INTERPOL, creating a safer world INTERPOL currently has 196 member countries and enables law enforcement agencies from around the world to work together to make the world a safer place. INTERPOL’s high-tech infrastructure of technical and operational support helps meet the growing challenge of combating crime in the 21st century. Facial recognition is an important and rapidly evolving technology that has opened up many new opportunities to identify individuals and solve crimes. In 2016, INTERPOL opted for IDEMIA’s advanced facial recognition capabilities to create the INTERPOL Face Recognition System (IFRS). INTERPOL Face Recognition System (IFRS) The IFRS contains face images from more than 170 countries, and since its launch, thousands of terrorists, criminals, fugitives, POIs, and missing persons have been identified. In 2019, INTERPOL renewed its contract with IDEMIA to upgrade the current system and transform it into a Multibiometric Identification System (MBIS). IDEMIA and INTERPOL first began their collaboration in 1999, when IDEMIA delivered the original Automated Fingerprint Identification System (AFIS). Automated Fingerprint Identification System (AFIS) AFIS was designed to make cooperation easier between police forces from member countries The Automated Fingerprint Identification System (AFIS) was designed to make cooperation easier between police forces from member countries, by giving them access to global police tools and services, namely forensics, fingerprint evidence and the exchange of forensic data to support international investigations. Through AFIS, authorized users in member countries can view, submit, and cross-check these records using INTERPOL’s secure global police communications network. IDEMIA and INTERPOL share enhanced partnership Cyril Gout, INTERPOL’s Director of Operational Support and Analysis, said “In the same way that criminals use ever more innovative and sophisticated ways to avoid detection, law enforcement must also leverage the latest advances in technology, especially in biometric security, to better combat all forms of transnational crime. INTERPOL’s enhanced partnership with IDEMIA will further help our member countries better protect their borders and communities.” Matt Cole, Group Executive Vice President, Public Security and Identity at IDEMIA, said “IDEMIA is proud to be collaborating with INTERPOL again and to continue making the world a safer place for all. This project reinforces our longstanding partnership with INTERPOL, which has been going strong for over 20 years.” INTERPOL receives delivery of the new MBIS Matt Cole adds, “With the delivery of the new MBIS, developed thanks to our strong dedication to R&D, INTERPOL will have access to cutting-edge fingerprint, palm print and face identification technologies, enabling it and member countries to identify persons of interest faster than ever before.” He continues, “We look forward to many more years of supporting INTERPOL to ensure the safety of potentially billions of citizens around the world.”


Round table discussion
Historically, the emphasis of security systems has been on reactivity, whether it’s providing video evidence of an incident or data to support a resulting investigation. Reactivity is core to impactful security, but increasingly, systems are also seeking to be more proactive. A proactive system seeks to prevent events from happening in the first place, thus mitigating the harm to an organization, and making the need for a reactive response moot. We asked this week’s Expert Panel Roundtable: How can security systems be proactive? Please provide a couple of examples.
Biometrics is both a mature technology in the physical security world and an innovation perpetually on the cutting edge. Biometric technologies received a boost during the COVID pandemic when “touchless” became a buzzword with particular relevancy to the world of biometrics. Higher security needs, such as “two-factor authentication,” are also driving demand for biometric products. We asked this week’s Expert Panel Roundtable: What are the latest technology trends in biometrics?
It’s safe to say there has been more change in the workplace in the last two years than ever before. Driven by the pandemic, technology has both allowed greater flexibility for employees and enabled continuing prosperity for many companies that otherwise would have had to cease operation. But have security protocols and practices done enough to enable companies to keep pace with the changes? We asked this week’s Expert Panel Roundtable: Have security protocols and practices kept up with the changing ways people work?
Products