Human identification system
PiLogic Inc., a pioneer in “exact AI” – mathematically precise, expert-guided artificial intelligence – announces the closing of a $4 million seed round to expand its footprint in the aerospace and defense industries to upgrade rules-based systems with the power of exact AI. Scout Ventures and Seraphim Space led the round, which enjoyed significant participation from Sovereign’s Capital, and investment from Flex Capital, FN Fund, and superangel Gokul Rajaram. PiLo...
PlanRadar, a pioneering digital platform for documentation, communication, and reporting in construction, facility management, and real estate, has enabled GSH Projects, a specialist construction and fit-out company, to decrease its project set-up time by 80%. Thus, streamlining processes and supporting scalable growth. GSH Projects originally adopted PlanRadar in January 2024 to help solve persistent inefficiencies as the company expanded, and managing large-scale projects efficiently became...
iDenfy, a US-based fraud prevention and identity verification company best known for its AI-powered RegTech automation solutions, partners with Reppublika Data Analytics & Technologies, a pioneer European software firm providing innovative SaaS solutions to the market research industry. iDenfy’s identity verification software will help the business verify all customers who are conducting surveys online while detecting fraudulent users with fake personal details or other renderings, of...
In a powerful show of solidarity, the U.S. security industry gathered for a crucial information-sharing webcast concerning recovery efforts for the Los Angeles-area wildfires disaster. Hosted by the Security Industry Association (SIA) and coordinated by Elite Interactive Solutions Marketing Director Scott Goldfine — with official endorsements from the Electronic Security Association (ESA), The Monitoring Association (TMA) and PSA Security Network (PSA) Collaborating for wildfire re...
iDenfy, a pioneer in identity verification, compliance, and fraud prevention, has announced a strategic partnership with Business Arena, a pioneering corporate service provider specializing in company registration, licensing, visa assistance, and administrative support. This collaboration enables Business Arena to integrate iDenfy’s advanced identity verification (IDV) and Anti Money Laundering (AML) solutions to enhance the company's security and deliver a seamless onboarding experience...
iDenfy, a global RegTech solutions hub, partnered with Venevo, a Romania-based crowdlending startup that operates as an EU-licensed Crowdfunding Service Provider and focuses on bridging the gap between ideas and investments. iDenfy’s identity verification software, together with built-in AML screening tools, will help approve new entrepreneurs and investors on the Venevo platform quickly, ensuring a fully automated onboarding flow. Financial irregularities Identity fraud and...
News
IDScan.net, the pioneer in AI-powered identity verification technology, proudly announces a year of significant growth in 2024. This success has been driven by product innovation, increased efficacy in the detection of fake IDs, strategic hires, and the establishment of new partnerships, further solidifying IDScan.net’s position as a pioneer in ID scanning and identity verification. Flagging fake and synthetic iDs The organization has capitalized on growing ID fraud across a variety of industries, as fraudsters look to swindle businesses such as dispensaries, car dealerships, big box retailers, manufacturers, and others by using fraudulent credentials. Across IDScan.net’s products, they flagged more than 600,000 fake IDs and synthetic identities in 2024. Growth revenue and verification volume The rising threat of ID fraud has led to more than just growth in revenue and verification volume. In 2024, IDScan.net has also: Grown total customers by 19%. Earned 17 badges from G2, including Best ROI, Highest Customer Satisfaction, and Most Effective. Launched mobile ID acceptance in both VeriScan for iOS and VeriScan for Windows. Spoken at conferences such as HITEC and GSX on trends in mobile ID adoption. Best SaaS Provider The awards are a testament to IDScan.net's cutting-edge advancements in AI-powered identity verification Additionally, IDScan.net was named the Best SaaS Provider at the 2024 Global Tech Awards, and Senior Product Manager, Hannah Ligon was awarded Bronze for Most Innovative Woman of the Year in the Stevie Awards. These awards are a testament to IDScan.net's cutting-edge advancements in AI-powered identity verification technology, the strength of the team, and its significant impact on enhancing security and compliance across various industries. New strategic hires This expansion is supported by ten new strategic hires aimed at enhancing customer support and business development. Notable additions to the team include Dan Kelleher as the new Vice President of Operations, who previously spent 30 years in the finance department of Hertz, and Ayna Verella Lawson, who joins the team after working on identity-related projects at Capital One. Product enhancements Also notable was the launch of ParseLink, a successor to the popular legacy product “WizzForms” Product enhancements have been at the forefront of IDScan.net's 2024 strategy. This innovation has centered around improving the efficacy of fake ID detection, especially tampered and photoshopped IDs, as well as improved BI and analytics for multi-location customers who need a birdseye view into fraud risks across large, distributed organizations. Also notable was the launch of ParseLink, a successor to the popular legacy product “WizzForms” which allows ID data to be automatically ingested into any form or software. Reduce the risk of scams “2024 has been an outstanding year of growth for our business,” said CEO, Terry Slattery. “We have focused on our core mission - to help businesses reduce the risk of scams using fake IDs - with incredible results. We expect to carry the momentum from this banner year forward into 2025 and beyond.” Shifts in ID fraud and identity verification Synthetic identity fraud is projected to become the major type of fraud, mirroring economic pressures Looking ahead to 2025, IDScan.net anticipates significant shifts in ID fraud and identity verification. As mobile IDs continue to roll out, with eight states expected to launch in 2025, the challenge remains for businesses to adapt to these technological advancements. Synthetic identity fraud is projected to become the major type of fraud, mirroring economic pressures that historically correlate with rises in ID fraud. Decentralized identity systems Additionally, societal concerns about AI may prompt anti-deepfake legislation, while discussions around age-restricted access to digital content are likely to intensify, posing implementation challenges. The move towards decentralized identity systems will also gain traction, offering users enhanced control over their data.
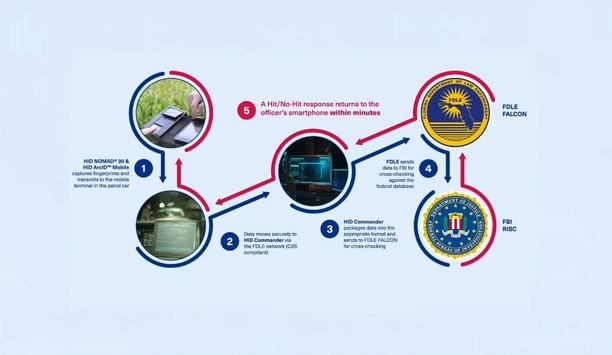
Verifying identities and conducting criminal background checks in the field has traditionally been one of the most time-consuming tasks for law enforcement officers. Real-time mobile biometrics In the past, this often required detaining individuals and transporting them to a station for fingerprint identification. Forward-thinking agencies like the Florida Department of Law Enforcement (FDLE) are tapping into highly accurate, real-time mobile biometric technology — Rapid ID — transforming how officers run ID checks while on patrol. One Officer. Two Fingerprints. Three Easy Steps. The HID Rapid ID solution is FDLE FALCON Rapid ID Certified, empowering Florida law enforcement officers The HID Rapid ID solution is FDLE FALCON Rapid ID Certified, empowering Florida law enforcement officers to conduct mobile biometric identification from any place, at any time. Built with proven fingerprint biometric technology, Rapid ID enables officers to quickly identify subjects with arrest warrants or those with records in Florida’s FALCON Integrated Crime History System and the FBI RISC database. Three easy steps Capture - Capture two fingerprints using the HID NOMAD™ 30 Pocket Reader Submit - Tap HID Commander on the mobile device to submit Review - Review Hit/No-Hit results within minutes Behind the scenes, HID Rapid ID does the heavy lifting by managing and transmitting Electronic Fingerprint Transmission (EFT) records to local, state, and federal agencies for subject identification in the field. Empowering real-time ID verification The FDLE FALCON Rapid ID Certified solution addresses the ongoing challenges of mobile identification in law enforcement, by offering: Plug-and-play mobile fingerprint readers that are easy to use and configure. A rugged design built for frequent use and able to withstand challenging outdoor environments. One-handed ergonomic operation for agility and officer safety. Automated capture and verification process. An FBI-certified (FAP 30, IP 65) & CJIS-compliant platform. Cost-effective solutions designed to work with most mobile devices. Better protect officers by allowing them to perform real-time ID verification while in the field. HID is proud to support Florida’s law enforcement agencies in their mission to maintain law and order. By incorporating Rapid ID technology into FDLE’s daily routines, officers can achieve faster, more accurate ID verification and be more efficient in maintaining public safety across jurisdictions.
Elite Interactive Solutions, a remote video guarding pioneer using proprietary intelligence and integration to achieve proven crime prevention, is proud to announce its involvement with several prominent organizations to promote the distribution of child identification kits. National Child ID Program Through its long association with FBI-LEEDA, Elite is represented along with the National Child ID Program in partnership with the NFL Alumni Association Pro Football Hall of Fame, and the Safety Blitz Foundation. The initiative includes providing at least one million inkless child identification kits, which allow parents to take, store, and control their children’s fingerprints/DNA in their own homes. Remote video guarding solution “As a company laser-focused on crime prevention, participating in a program predicated on protecting America’s children from harm could not be more in line with what Elite and its remote video guarding solution is all about,” says Elite Interactive Solutions Founder and CEO - Aria Kozak. Aria Kozak adds, “We are grateful to FBI-LEEDA for endorsing Elite when asked for a private safety supporter and honored to be among the other prominent and respected organizations represented for this vitally important program.” Child’s fingerprint copy The group’s safety initiative is dedicated to changing these statistics by providing parents and guardians with a tool According to the National Child ID Program’s (NCIDP) website, up to 1,000 children go missing in the United States every day, yet when its program began less than 2% of parents had a copy of their child’s fingerprints to use in case of an emergency. The group’s safety initiative is dedicated to changing these statistics by providing parents and guardians with a tool they can use to help protect their children. ID kits The ID kits allow parents to collect specific information by easily recording the physical characteristics, fingerprints, and DNA of their children on identification cards that are then kept at home by the parent or guardian. If ever needed, this ID kit gives authorities vital information to assist their efforts to locate a missing child. Since its inception in 1997, the NCIDP has distributed more than 70 million kits throughout North America. The program has been recognized by Congress and works with federal, state, and local pioneers, coaches, athletes, faith-based organizations, and corporate citizens to increase the safety of children in communities across the country.
adCAPTCHA, a new specialist security verification platform, has launched with £1m funding to tackle the ‘bots epidemic’ and protect organizations against cyber fraud. The London-based company, founded by industry veteran and entrepreneur Alfie Scarborough, equips organizations with the capability to identify and block bots through its sophisticated in-house developed patent-pending human verification technology. Layered security solution adCAPTCHA’s layered security solution leverages the infinite variation and constant change of media adCAPTCHA’s layered security solution leverages the infinite variation and constant change of media, generates billions of unique pathways, as well as behavioral analytics capabilities. It is estimated that 50 percent of global web traffic is made up of bots, with leading brands losing millions every day due to fraudulent views and impressions from non-existent customers. Human verification process The platform has been crafted to allow marketers and branding professionals to protect against online fraud, with bot-enabled false impressions repeatedly draining marketing budgets and resources. adCAPTCHA also allows brands to optimize the human verification process for advertising and cross-selling new products and services. The platform’s APIs also provide users with the ability to integrate into CMS and media libraries. Angel investors and entrepreneurs The verification system includes swipe to complete, puzzle piece, and gamification tools The verification system includes swipe to complete, puzzle piece and gamification tools to confirm if the user is human. The company’s £1m funding, provided by a series of angel investors and entrepreneurs, will allow adCAPTCHA to develop its global offering, targeting the UK and US markets as well as Europe. Era of Human Verification Technology Alfie Scarborough, founder and CEO of adCAPTCHA said: “The verification market is plagued by poorly performing products that fail to accurately distinguish between bots and humans. The status quo leaves brands open to major cyber-attacks, unlimited spam as well as decimated marketing budgets." "Our offering will change all that – giving brands a comprehensive solution to identify and block bots, while empowering dynamic brand advertising to engage customers. Our mission is to usher in a new era of human verification technology and set the industry standard for the future.”
Alibaba Cloud, the digital technology and intelligence backbone of Alibaba Group, has announced that the International Olympic Committee (IOC) will deploy its data-driven sustainability solution – Energy Expert – to help measure and analyze the electricity consumption at the competition venues of the forthcoming Olympic Games Paris 2024 ('Paris 2024'). Cloud-based platform By migrating the intelligence related to the power consumption and demand of the competition venues to the cloud-based platform for the first time, the solution aims to enable more accurate analysis and better-informed power consumption planning for future Olympic Games. The deployment of Energy Expert will be applied to all 35 competition venues during Paris 2024. Energy Expert With this solution, the IOC will be able to consolidate all energy-related data during the Olympics and Paralympics With this solution, the IOC will be able to consolidate all energy-related data during the Olympics and Paralympics such as electricity consumption, power demand contingency, venue capacity, competition-related information, and onsite weather conditions into one easy-to-understand dashboard for a user-friendly experience. Based on the integrated cloud-based intelligence and deep-learning-based AI models from Alibaba Cloud, Energy Expert aims to provide more accurate analysis to produce venue-specific forecasts and recommendations, such as power demand optimization to minimize power wastage. Sustainability "Sustainability is one of the three pillars of the Olympic Agenda 2020+5 alongside credibility and youth. With Energy Expert, we can now forecast our energy-related impacts well into the future and accurately measure our progress," said llario Corna, Chief Information and Technology Officer at the International Olympic Committee (IOC). llario Corna adds, "Electricity consumption is a large contributor to the Olympic Games’ carbon emissions. The data-driven insight produced by Energy Expert will help us learn from each Games edition, and apply that knowledge intelligently to make future events even more energy efficient." Real-time electricity consumption Real-time electricity consumption at the level of operational spaces on-venue will be gathered In addition, real-time electricity consumption at the level of operational spaces on-venue will be gathered from a selection of competition venues with 100 smart electric meters installed to gather more comprehensive datasets. For example, real-time electricity consumption from various operational spaces on-venue, including the playing fields, broadcast and media working areas, technology operational spaces and specific equipment, food and beverage equipment, and a host of other temporary operational areas and equipment. Accurate analysis Datasets collected will vary, taking into account temperature conditions and real-time occupancy of the areas at different times of the day. The collection of these detailed datasets will enable a more accurate context for the Organising Committees for the Olympic Games (OCOGs) when referring to the energy consumption data from the Paris Games. To support OCOGs in undertaking a more comprehensive analysis of Games energy consumption trends, electricity data from previous Games, including the Olympic Games London 2012, Olympic Winter Games PyeongChang 2018, and Olympic Games Tokyo 2020, will also be available for analysis within Energy Expert. Energy-related insights "Energy Expert will further prove its value in the most high-profile and challenging arena of all the fast-paced and highly competitive world of international sports," said William Xiong, Vice President of Alibaba Cloud Intelligence and General Manager for International Industry Solutions. William Xiong adds, "The insights Energy Expert delivers will form part of the solution to assist the IOC and future Games to be more sustainable." AI-driven recommendations The semi-open design of the space has contributed to optimizing energy consumption Outside the competition venues, Energy Expert’s AI-driven recommendations have been applied to help Alibaba optimize energy consumption and minimize carbon emissions at its temporary exhibition venues during Paris 2024. For example, at the Alibaba Wonder Avenue in the Avenue des Champs-Élysées, sustainable wooden materials and recyclable steel will be used for the main structure of the venue to cut the carbon footprint. The semi-open design of the space has also contributed to optimizing energy consumption and minimizing carbon emissions, primarily by leveraging natural lighting and ventilation. First application: Olympic Esports Week Introduced in June 2022, Energy Expert’s first application at a sports event was in 2023 at the first Olympic Esports Week in Singapore. The solution was trialed to measure and analyze carbon emissions from temporary constructions built to host the Olympic Esports Week, to generate data-driven insights on the choice of materials and equipment used at the event. A series of metrics including the impact of energy consumption, waste management, signage, and decoration were assessed, enabling the comparison of the relative impacts of several types of materials and equipment used at the event. Energy-saving recommendations Beyond the sports environments and applications, Energy Expert also helps over 3,000 customers worldwide measure, analyze, and manage the carbon emissions of their business activities and products. The solution also provides actionable insights and energy-saving recommendations to help customers accelerate their sustainability journeys.
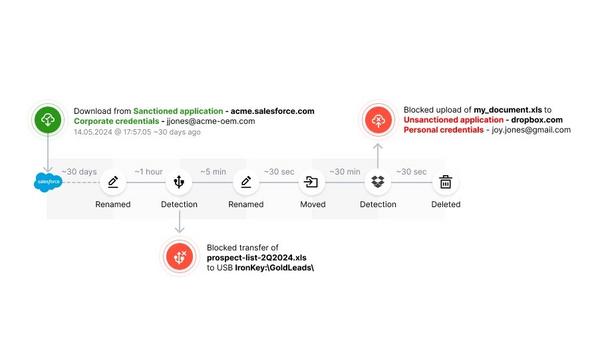
Next DLP (Next), a pioneer in insider risk and data protection announced the launch of Secure Data Flow, a groundbreaking capability within the Reveal Platform that uses the "What, Where, Who and How" of data’s origin, movements and modifications to provide unparalleled protection. Revolutionising data protection In a rapidly evolving digital landscape, legacy data protection technologies are falling short. They rely heavily on pattern matching, regular expressions, keywords, user-applied tags, and fingerprinting, which can only cover a limited range of text-based data types. Secure Data Flow overcomes the limitations and complexities of legacy Data Loss Prevention (DLP) by complementing traditional content and sensitivity classification-based approaches with origin-based data identification, manipulation detection, and data egress controls. This results in an all-encompassing, 100% effective, false-positive-free solution that simplifies the lives of security analysts. Secure Data Flow Employees download an average of 30GB of data each month from SaaS applications to their endpoints Recent studies show that employees download an average of 30GB of data each month from SaaS applications to their endpoints, including mobile phones, laptops, and desktops (Productiv) (Vendr). This staggering volume underscores the critical need for advanced data protection measures. By tracking data from its origin as it flows to sanctioned and unsanctioned egress channels within an organization, Secure Data Flow equips security teams to prevent data theft and misuse effectively. Data protection and risk management “Secure Data Flow is a novel approach to data protection and insider risk management,” said Ken Buckler, Research Director at Enterprise Management Associates. “It not only boosts detection and protection capabilities but also streamlines the overall data management process, enhancing the fidelity of data sensitivity recognition and minimizing endpoint content inspection costs." "This advancement is particularly vital given the limitations and inefficiencies of traditional legacy DLP solutions, providing a much-needed capability to more effectively safeguard sensitive data in today’s diverse technological environments." Key Benefits of Secure Data Flow Comprehensive Data Tracking: Secure Data Flow secures the flow of critical business data from any SaaS application, including Salesforce, Workday, SAP, and GitHub, ensuring that sensitive information is always protected. Enhanced Data Protection: By using data origin and sensitive data identification, Secure Data Flow safeguards your company’s intellectual property and sensitive data from accidental loss and malicious theft. Insightful Investigations: Security analysts investigating malicious data exfiltration gain invaluable contextual insights into data origin, manipulation, and lineage, enabling them to identify, investigate, and report on data security risks and incidents with unprecedented accuracy. A new era in data loss prevention "In current IT environments, Intellectual Property (IP) commonly resides in an organization’s SaaS applications and cloud data stores,” said John Stringer, Head of Product at Next DLP. "The risk here is that high-impact data in these locations cannot be easily identified based on its content. With Secure Data Flow, we help organizations protect their IP by capturing the data’s origin and using that information to track data movement and prevent data theft.” Powerful and easy to use With Secure Data Flow, Reveal sets a new standard for data protection, offering a solution that is both powerful and easy to use. It ensures that organizations can confidently protect their most critical data assets with confidence, regardless of their location or application.


Expert commentary
As we head into a new year, it’s fair to say that it isn’t easy out there for the security integrator community. That’s understandable given the big ruptures felt in the market for physical security in 2023. Typically, Commercial Real Estate (CRE) landlords are the biggest and most influential buyers of physical security hardware and software, but this is starting to wane as heightened borrowing costs and biting inflation cause real estate valuations to plunge. Building security upgrades A lot of CRE landlords are in a fight for survival which unfortunately doesn't leave much room for budget spend on building security upgrades. This state of affairs is a problem for security integrators with extensive connections in the CRE space. Where do they pivot their services to keep their business growing in 2024? From the conversations I’ve been having with integrators and customers alike over the past few months – the answer is that the growth potential lies in the enterprise space. The trajectory of enterprise IT and physical security Aren’t enterprises carrying out cost-cutting efficiency drives and downsizing office space to reflect hybrid working It might initially feel unnatural to see the enterprise segment as a potential driver of demand for physical security services and products. Aren’t enterprises carrying out cost-cutting efficiency drives and downsizing office space to reflect hybrid working habits? These things are true but also present an opportunity for the right physical security proposition. Standardization of enterprise IT Take efficiency drives as an example. A key element of such efforts is an acceleration toward the standardization of enterprise IT platforms, hardware, and solutions, using the cloud. What was once a focus on moving on-prem systems and workloads to the cloud has shifted to efforts to keep cloud OpEx costs down by centralizing as much as possible. Practically, this means utilizing APIs to plug disparate IT applications and services into central platforms that boast a “single pane of glass” view. APIs APIs drive consumption, open new business models, and foster cross-industry partnerships APIs aren’t anything new to enterprises. They drive consumption, open new business models, and foster cross-industry partnerships. However, the use of APIs in the physical security sphere has been surprisingly slow to take off. There are multiple elements to this but a key reason is that some security software products on the market aren’t cloud-based. Adding cloud-based solutions to network Others are cloud-based, however, and these are the solutions that security integrators need in their portfolio to serve the influential enterprise market segment and its approach to IT networks. Selling the value of these solutions requires integrators to take it a step further by speaking the language of the enterprise IT buyer and understanding their goals. The power of Cloud-based access control in the enterprise Hybrid working and the occupancy rate fluctuations it brings require closer monitoring of access events The continued relevance of physical security for enterprises can’t be understated. After all, hybrid working and the occupancy rate fluctuations it brings require closer monitoring of access events – not less. Despite the discourse around office downsizing, the reality for most enterprises is that the office can’t be done away with completely and there’s always going to be growth experienced by successful companies that require an upgrade in physical square footage. Physical security Access control systems that are cloud-based will be preferred by the enterprise to fulfill the essential function of physical security. That’s because they align with the push towards centralization in the cloud that enterprises are carrying out business-wide. Access control has the potential to result in lots of disparate dashboards and apps. Think video management, license plate recognition, building management software, elevator monitoring, hot desking solutions, guest booking software, room booking functions, and more. Uniting all of these functions in one platform suits enterprise security teams well. Access control solutions Linking employee databases to an IAM solution, or creating seamless experiences by tying access credentials But this only scratches the surface. Access control solutions that can be integrated with hugely popular corporate software applications like Okta, Azure Active Directory, and Google Workspace quickly catch the eyes of enterprise IT security teams by pulling in the same direction as the broader tech stack. Whether it’s applying AI analytics to anomaly detection, linking employee databases to an Identity Access Management (IAM) solution, or creating seamless experiences by tying access credentials to things like meeting room bookings, it’s through APIs that cloud-based access control can thrive in an enterprise setting. Security integrators It’s worth also noting that as enterprises grow, access control gets harder. Managing the access requirements of thousands of employees across a global real estate footprint requires the scale that cloud computing is best placed to bring. Security integrators who can join the dots to make that link are well-positioned to pivot toward the enterprise. Broadening horizons Concepts like smart access and applying AI to access data to automate the monitoring of occupancy rates This pivot is understandably a daunting prospect but the potential for natural synergy shouldn’t be overlooked. Concepts like smart access and applying AI to access data to automate the monitoring of occupancy rates and security anomalies won’t be completely alien to cloud-first enterprises. That’s an opportunity for integrators to upsell more sophisticated security set-ups in a way that they may have found more difficult with CRE clients and prospects. Tailored propositions It would be remiss to avoid mentioning that ‘enterprise’ is a very loose term that encompasses businesses across multiple industry verticals. To better pivot, security integrators need to offer tailored propositions specific to set verticals that cover all bases as opposed to offer, for example, piecemeal alarm or video product solutions. Enterprise industry verticals Security integrators should be weary of all-encompassing narratives in 2024. Whether or not the global economic picture darkens, there are always going to be pockets of growth within certain enterprise industry verticals. Plus, anecdotally, the indicators point to enterprises being the driver of demand for cloud-based access control as we head into the new year. Integrators who can dial into that shift have a lot to gain and nothing to lose.
Security systems represent a significant investment, yet many organizations still only use a small percentage of their physical security systems’ capabilities. That’s before we even begin to consider the different ways that the likes of video, access control, and ANPR can add additional value beyond security by serving the needs of other business functions. Whether that be to obtain additional insight, streamline compliance, or drive operational efficiencies. Consumption gap When users aren’t tapping into the full power of the solution they bought, they aren’t realizing their full return on investment. This creates a consumption gap. It’s a situation that has the potential to go in one of two very different directions. A misunderstanding of a system, its capabilities and functionality can quickly result in user dissatisfaction Left unchecked a consumption gap can create frustration for system integrators, manufacturers, and end users alike. A misunderstanding of a system, its capabilities and functionality can quickly result in user dissatisfaction. Leading to a greater likelihood that they’ll look to change or focus investment into overlapping and likely competing solutions. Customers’ security goals Addressed appropriately it can help manufacturers, system integrators, and end users to build trusted partnerships in which everybody wins. Understandably, systems integrators are primarily focused on installation—delivering reliable solutions that meet customers’ security goals to ensure their long-term success. However, engagement can go beyond deployment. Closing the consumption gap can be a strategic way to differentiate yourself from competitors. The deeper you understand your customer’s business, the better advice you’re able to offer—and the stronger the partnership you form. Why do consumption gaps exist? For customers, finding the time to learn multiple capabilities of a security system can be time-consuming. Often, taking advantage of new tools and solutions takes a backseat to the urgency of daily tasks. Often, taking advantage of new tools and solutions takes a backseat to the urgency of daily tasks There are many reasons why customers may not be taking full advantage of the features available to them in their security platform. They may feel overwhelmed by a steep learning curve after deployment and might delay diving into the additional system features. Sometimes, there might be a lack of awareness of the technology’s full capabilities, and despite a willingness to learn, there are few options for training. Often, it can simply be they are not aware of the benefits of their system or are too busy with day-to-day and urgent tasks to learn other features. Bridging the consumption gap Systems are built to deal with a wide variety of use cases and broaden market appeal, but the goal isn’t to get everyone to use all the features of every product. You want to guide your customers toward the features and functionality that best meet their needs. This could entail reducing the friction they experience in their day-to-day operations, solving unique issues related to their business, or addressing their most important challenges. Having these conversations with your customers deepens your relationship and can organically open up new revenue streams. Continuous engagement allows you to recommend other relevant products or services that they may find helpful. Customized training plan Customers can learn at their own pace and gradually expand their understanding of their system Furthermore, customers are often not able to implement all features at once. You can help by proposing a plan to gradually evolve systems and processes over time. This could include a customized training plan to get the most value from their investment. Some manufacturers are also now providing learning management tools that system integrators can pass on to their customers. Customers can learn at their own pace and gradually expand their understanding of their system in accordance with their bandwidth. This allows them to get more out of their system. Simplifying deployment With the right software partners, systems integrators can focus on solving customer problems, not reactively troubleshooting issues. Look for manufacturers who offer good support systems for integrators. This includes not only quality technical support but also configuration and training services you can build on. Look for partners that offer tools and consultation services you can use to complement your value-added services, either to spend less time on the basics or for specialized expertise on complex projects. Beyond support and services, one telling sign is the configuration interface and tools that you as an integrator will primarily interact with. Ask yourself whether the manufacturer invests in their back-end tools and their primary user interface. Is there a noticeable difference between these two interfaces in terms of look and feel? Does one feel more dated? Widening consumption gap The harder it is to implement upgrades, the more reticent customers are to make the changes If the end user interface is easy to use but changes on the back end are difficult, the resulting friction can contribute to the widening consumption gap. It can become too time-consuming or difficult to upgrade or make changes to the system. The harder it is to implement upgrades, the more reticent customers are to make the changes. Configuration should be painless. If the system has a solid graphical user interface, you’ll be able to interact with the software in a fluid and intuitive way. When the system is intuitive for both you and your customers, you spend less time on setup and training. You can invest more attention in value-added activities. Conclusion A consumption gap could be a sign that technological innovation is outpacing people's ability to implement them in their day-to-day lives. You can work with your customers to simplify the adoption of the innovations so they can more easily implement them and realize the full value of their investment. By reviewing opportunities to bridge the consumption gap for your customers, you increase the likelihood of growing and renewing your system and service contracts. You also build relationships as a trusted partner. Customers will turn to you when looking to expand their security system and proactively solve new and incipient problems.
Global transportation networks are becoming increasingly interconnected, with digital systems playing a crucial role in ensuring the smooth operation of ports and supply chains. However, this reliance on technology can also create vulnerabilities, as demonstrated by the recent ransomware attack on Nagoya Port. As Japan's busiest shipping hub, the port's operations were brought to a standstill for two days, highlighting the potential for significant disruption to national economies and supply chains. Transportation sector The attack began with the port's legacy computer system, which handles shipping containers, being knocked offline. This forced the port to halt the handling of shipping containers that arrived at the terminal, effectively disrupting the flow of goods. The incident was a stark reminder of the risks associated with the convergence of information technology (IT) and operational technology (OT) in ports and other critical infrastructures. This is not an isolated incident, but part of a broader trend of escalating cyber threats targeting critical infrastructure. The transportation sector must respond by bolstering its defenses, enhancing its cyber resilience, and proactively countering these threats. The safety and efficiency of our transportation infrastructure, and by extension our global economy, depend on it. Rising threat to port security and supply chains XIoT, from sensors on shipping containers to automatic cranes, are vital to trendy port functions OT, once isolated from networked systems, is now increasingly interconnected. This integration has expanded the attack surface for threat actors. A single breach in a port's OT systems can cause significant disruption, halting the movement of containers and impacting the flow of goods. This is not a hypothetical scenario, but a reality that has been demonstrated in recent cyberattacks on major ports. Adding another layer of complexity is the extended Internet of Things (XIoT), an umbrella term for all cyber-physical systems. XIoT devices, from sensors on shipping containers to automated cranes, are now integral to modern port operations. These devices are delivering safer, more efficient automated vehicles, facilitating geo-fencing for improved logistics, and providing vehicle health data for predictive maintenance. XIoT ecosystem However, the XIoT ecosystem also presents new cybersecurity risks. Each connected device is a potential entry point for cybercriminals, and the interconnected nature of these devices means that an attack on one, which can move laterally and can have a ripple effect throughout the system. The threat landscape is evolving, with cybercriminals becoming more sophisticated and their attacks more damaging with a business continuity focus. The growing interconnectivity between OT and XIoT in port operations and supply chains is also presenting these threat actors with a greater attack surface. Many older OT systems were never designed to be connected in this way and are unlikely to be equipped to deal with modern cyber threats. Furthermore, the increasing digitization of ports and supply chains has led to a surge in the volume of data being generated and processed. This data, if not properly secured, can be a goldmine for cybercriminals. The potential for data breaches adds another dimension to the cybersecurity challenges facing the transportation sector. Role of Cyber Resilience in Protecting Service Availability Cyber resilience refers to organization's ability to prepare for, respond to, and recover from threats As the threats to port security and supply chains become increasingly complex, the concept of cyber resilience takes on a new level of importance. Cyber resilience refers to an organization's ability to prepare for, respond to, and recover from cyber threats. It goes beyond traditional cybersecurity measures, focusing not just on preventing attacks, but also on minimizing the impact of attacks that do occur and ensuring a quick recovery. In the context of port operations and supply chains, cyber resilience is crucial. The interconnected nature of these systems means that a cyberattack can have far-reaching effects, disrupting operations not just at the targeted port, but also at other ports and throughout the supply chain. A resilient system is one that can withstand such an attack and quickly restore normal operations. Port operations and supply chains The growing reliance on OT and the XIoT in port operations and supply chains presents unique challenges for cyber resilience. OT systems control physical processes and are often critical to safety and service availability. A breach in an OT system can have immediate and potentially catastrophic physical consequences. Similarly, XIoT devices are often embedded in critical infrastructure and can be difficult to patch or update, making them vulnerable to attacks. Building cyber resilience in these systems requires a multi-faceted approach. It involves implementing robust security measures, such as strong access controls and network segmentation, to prevent attacks. It also involves continuous monitoring and detection to identify and respond to threats as they occur. But perhaps most importantly, it involves planning and preparation for the inevitable breaches that will occur, ensuring that when they do, the impact is minimized, and normal operations can be quickly restored. Building resilience across port security and supply chains In the face of cyber threats, the transport sector must adopt a complete method of cybersecurity In the face of escalating cyber threats, the transportation sector must adopt a comprehensive approach to cybersecurity. This involves not just implementing robust security measures, but also fostering a culture of cybersecurity awareness and compliance throughout the organization. A key component of a comprehensive cybersecurity strategy is strong access controls. This involves ensuring that only authorized individuals have access to sensitive data and systems. It also involves implementing multi-factor authentication and regularly reviewing and updating access permissions. Strong access controls can prevent unauthorized access to systems and data, reducing the risk of both internal and external threats. Network segmentation Network segmentation is another crucial measure. By dividing a network into separate segments, organizations can limit the spread of a cyberattack within their network. This can prevent an attack on one part of the network from affecting the entire system. Network segmentation also makes it easier to monitor and control the flow of data within the network, further enhancing security. Regular vulnerability assessments and patch management are also essential. Vulnerability assessments involve identifying and evaluating potential security weaknesses in the system, while patch management involves regularly updating and patching software to fix these vulnerabilities. These measures can help organizations stay ahead of cybercriminals and reduce the risk of exploitation. EU’s NIS2 Directive EU’s NIS2 Directive came into effect, and member states have until October 2024 to put it into law The transportation sector must also be prepared for greater legislative responsibility in the near future. The EU’s NIS2 Directive recently came into effect, and member states have until October 2024 to put it into law. The Directive aims to increase the overall level of cyber preparedness by mandating capabilities such as Computer Security Incident Response Teams (CSIRTs). Transport is among the sectors labeled as essential by the bill, meaning it will face a high level of scrutiny. Getting to grips with the complexities of XIoT and OT integration will be essential for organizations to achieve compliance and avoid fines. Global transportation infrastructure Finally, organizations must prepare for the inevitable breaches that will occur. This involves developing an incident response plan that outlines the steps to be taken in the event of a breach. It also involves regularly testing and updating this plan to ensure its effectiveness. A well-prepared organization can respond quickly and effectively to a breach, minimizing its impact and ensuring a quick recovery. In conclusion, mastering transportation cybersecurity requires a comprehensive, proactive approach. It involves implementing robust technical measures, fostering a culture of cybersecurity awareness, and preparing for the inevitable breaches that will occur. By taking these steps, organizations can enhance their cyber resilience, protect their critical operations, and ensure the security of our global transportation infrastructure.
Security beat
A pioneer in the access control sector since 1971, AMAG Technology is looking to the future and the next generation of products that will expand its services to customers. “In our vision, we have advanced approaches that will not only provide our partners with advanced technologies but also ones that are easier to install with tools to expand their services,” says David Sullivan, who was appointed President of the venerable access control company in September 2022. New challenges at AMAG Sullivan brings a new outlook to the AMAG business, a part of Allied Universal, and a new vision to lead the company into the future. We caught up with David Sullivan to discuss his new challenges at AMAG and the journey ahead as the company looks to the future. Q: How does your background inform your approach to leading AMAG? I believe that it helps me to define a vision for AMAG that will be unique and on the leading edge of our industry David Sullivan: With the exception of only a few short years, my career has been in access control. I have experience with several systems and have had the privilege to manage several successful access control companies. As a result, I bring a great deal of experience into my role at AMAG. I believe that it helps me to define a vision for AMAG that will be unique and on the leading edge of our industry. Q: How would you describe AMAG’s journey over the last several years and how do you see the future? Sullivan: Prior presidents of AMAG always shared their leadership vision and direction with senior leaders located in the United Kingdom. This had an impact on the full direction of the business, sometimes limiting its ultimate success. Before I became a part of AMAG, these senior leaders that were located in the UK retired, placing for the first time the full management responsibilities of the president. This has allowed me to integrate the business into a single team, with single objectives, and a single vision. We expect to begin to reveal this new vision in the coming weeks. We are excited about the future of AMAG and believe we will surprise the industry with our new products and approach in the coming months and years. Q: How important is it that a manufacturer provides both hardware and software solutions? How does AMAG’s approach (in general) differentiate it in the market? We can design the complete solution, providing functionality that others may find more difficult to accomplish Sullivan: Regardless of the manufacturer, we all provide hardware and software. An access control solution is not complete without both. Some of us choose to make our panels, and others do not. Those who are dependent on third-party suppliers are restricted to the developments and direction of that company, and while it might be perceived to be an open technology, it still is proprietary to the hardware manufacturer. AMAG has controlled its manufacturing of panels from day one. The result means that we can design the complete solution, providing functionality that others may find more difficult to accomplish. Q: How does the breadth of AMAG’s product suite provide advantages to customers and/or integrators? Sullivan: AMAG’s product portfolio is unique and provides the end user with an end-to-end identity management solution from one company. Our Control Room PSIM, Symmetry CONNECT Identity Management Solution, Symmetry Access Control, and Symmetry GUEST solutions all integrate to provide the user with a broad set of features and capabilities from a single provider. There is no finger-pointing when we come to support your system. We hold full responsibility for making it work and can quickly provide a resolution to any application difficulties the user may be experiencing. Q: How does AMAG address the divide between on-prem and cloud systems? How do you help customers make the transition and/or plan for the future? We are in the early stages of developing our next generation of access control in which we intend to provide on-prem Sullivan: In our current product portfolio, we have three products that are cloud-based. Our mobile credential platform (Symmetry Mobile), our visitor management solution (Symmetry GUEST), and our physical identity and access management solution (Symmetry CONNECT) are all offerings that operate in the cloud. We are in the early stages of developing our next generation of access control in which we intend to provide on-prem, web client, and cloud-based offerings. One of the primary objectives is to ensure that the large installed base of systems that are out there today will be able to migrate not only to our next generation but as well to the cloud if the client so desires. Q: What is AMAG’s approach to mobile credentialing? Sullivan: As an access control provider, adding Symmetry Mobile credentialing to our portfolio just made sense. We want our customers to have a forward-thinking solution with the opportunity to save money not only on the physical badges but the cost of printing and distributing badges. Mobile credentials can be easily issued and revoked remotely, reducing administrative overhead, and eliminating the need for physical inventory management. Organizations can centrally configure what devices are used and the read range for each type of device and operating system, thus providing flexibility. Symmetry Mobile offers a customized questionnaire that controls access and reduces liabilities. Q: What has surprised you the most in your first year or so leading AMAG? Not many companies are blessed with such a broad portfolio that is supported by a resource-rich company Sullivan: I wouldn’t say I was surprised by this as much as happy to see, but I would say that the quality of our people was a pleasant surprise. As well, the AMAG product offering is broad and has some unique elements. When coupled with the depth of the resources that we have in AMAG, I know that we are second to none. Not many companies are blessed with such a broad portfolio that is supported by a resource-rich company that has so many talented people. Q: Please describe your dealer channel, and how you are seeking to expand it. Sullivan: The AMAG products are sophisticated and typically are installed for higher-end applications. With this sophistication comes a need to be well able to install such a solution. We have a strong group of certified and loyal partners who help us to deliver these enterprise solutions. We desire to provide our existing partners with updated and competitive systems to offer to their end users. Q: What is the security industry’s (and/or AMAG’s) biggest challenge in the next five years? We need to find ways to provide both our channel partners and the customers with solutions that are easily integrated Sullivan: I believe that the advancements that we are seeing in technology provide our industry with the opportunity to truly change how security is provided to our collective customers. As we advance these solutions, we will need to do so responsibly and in a way that helps the channel’s abilities. We need to find ways to train our partners to both install and support these more complex solutions. At the same time, we need to find ways to provide both our channel partners and the customers with solutions that are easily integrated, moving away from proprietary closed systems to open and cohesive solutions. This will ensure that the users get the best, and most complete solutions. Q: What does the industry as a whole misunderstand about AMAG -- time to set the record straight! Sullivan: Well, I am not ready to openly share where we are heading. We are in the process of putting together some advanced approaches to how we will do business with our partners. We are focused on providing tools that will enhance their services to their customers, and with products that are leading edge. I can only state that all should keep their eyes on AMAG, because over the next few years, we are going to surprise some people, and more importantly make our loyal partners quite powerful.
Matter is a new open-source interoperability standard that will simplify the connectivity of smart home systems, including security. The growing popularity of the Matter 1.0 standard was evident at the large Consumer Electronics Show (CES) in January in Las Vegas, where the standard was heavily promoted by companies including Google, Amazon, and Samsung. A flood of Matter-connected products is on the horizon for ship dates in the second half of 2023. Evolve, and manage IoT standards Creating the standard is the Connectivity Standards Alliance (CSA), formerly the Zigbee Alliance, which changed its name in May 2021. With 300 companies as members, CSA seeks to create, evolve, and manage Internet of Things (IoT) technology standards through a well-established, collaborative process. CSA promotes the benefits of global, open standards, and the value of the IoT to customers and consumers, and seeks to break down the barriers to broad access and adoption of IoT technologies and solutions. Matter The new brand name Matter was launched in May 2021 to designate the standard formerly known as Project CHIP (Connected Home over IP), developed by CSA member companies including Apple, Google, Samsung, and Amazon. There are currently 800 devices and apps certified to the new smart home standard, including various smart home equipment (except video cameras, which will be included in a major release in the fall of 2023). Matter version 1.0 was initial launch in October 2022. Matter 1.0 release Twice a year moving forward, Matter plans a minor release each spring and a major release each fall As part of the Matter 1.0 release, authorized test labs are open for product certification, the test harnesses and tools are available, and the open-source reference design software development kit (SDK) is complete, thus enabling new products to be brought to market. Twice a year moving forward, Matter plans updated releases, a minor release each spring and a major release each fall. Smart home interoperability Currently, a variety of CSA working groups are addressing various aspects of interoperability in the smart home, including issues such as data privacy, security, energy management, and health and wellness, says Christopher LaPré, CSA’s Head of Technology. “Implementing elements requires that the standards alliance be able to multitask on several tracks,” says LaPré. Some development is centering around connectivity and the need for a “hub” to which multiple systems can communicate and incorporate an “identity” to regulate the availability of information to various systems. The standards will enable both do-it-yourself (DIY) systems and devices deployed by professional installers. Addressing privacy requirements The new development will be guided by what installers need to succeed in the home automation" Ecosystems depend on the availability of some type of “identity” to meet privacy requirements. Rules must be implemented across the ecosystem that deploys a “trust system” to ensure privacy. Solving the challenge involves getting all the major players to the table at the technical level to meet the bar from the business and technology perspective. “Integrators and retailers will play a role as Matter continues to evolve,” says LaPré. “New development will be guided by what installers need to succeed in the home automation market.” Matter-certified devices There is still work to be done to expand the 800 certified devices to function throughout the Matter ecosystem and to add new devices over time. One goal is to simplify an integrator’s solution using fewer hubs (and possibly a single hub) to provide a wide variety of services. The timeline of adding new Matter-certified devices may be delayed by the availability of equipment in the global supply chain, says LaPré. Flexibility Multi-admin provides for the simultaneous operation of devices in multiple smart home systems A multi-admin feature of Matter enables more flexibility for multiple ecosystems. A core feature of Matter, multi-admin provides for the simultaneous operation of devices in multiple smart home systems. Accordingly, family or household members could operate the device with the digital assistant or smartphone app of their choice. A bridging protocol helps to tie existing systems together. Amazon, Apple, Comcast, Google, SmartThings, and the Connectivity Standards Alliance came together in 2019 to develop and promote this new standard, joined by fellow Alliance board member companies IKEA, Legrand, NXP Semiconductors, Resideo, Schneider Electric, Signify, Silicon Labs, Somfy and Wulian. Smart device communication Currently, member organizations span all sizes, across a range of business categories. More than 1,700 Member individuals participate in bringing the Matter specification, reference implementations, testing tools, and certification programs to life. Matter's underlying network technologies are Wi-Fi and Thread. Wi-Fi enables Matter devices to interact over a high-bandwidth local network and allows smart home devices to communicate with the cloud. Thread provides a mesh network within the home. Both the Wi-Fi Alliance and Thread Group partnered with the Connectivity Standards Alliance to help realize the vision of Matter.
Facial recognition continues to be a political football and a target of privacy activists in the United States. For example, San Diego has suspended its use of facial recognition scanners by law enforcement after a campaign by civil rights groups. The San Diego Tactical Identification System (TACIDS) program included a database of facial recognition scans shared by 30 local, state and federal agencies. A California law, passed in the fall, puts a three-year moratorium on law enforcement use of face recognition technology. A proposal in Congress would prohibit use of biometric recognition technology in most public and assisted housing units funded by the Department of Housing and Urban Development (HUD), thus protecting the more than two million public housing residents nationwide from being “over-surveilled.” The “No Biometric Barriers to Housing Act” is supported by the NAACP, the National Housing Law Project, National Low-Income Housing Coalition, National Action Network, Color of Change, and the Project on Government Oversight. The problems of Facial Recognition "Studies that show that facial recognition systems may misidentify many individuals including women and people of colour" A letter from seven members of Congress to HUD Secretary Ben Carson questioned the use of facial recognition in federally assisted housing because it “could be used to enable invasive, unnecessary and harmful government surveillance of…residents.” The letter cites studies that show that facial recognition systems may misidentify many individuals including women and people of color, thus “exacerbating vulnerabilities that marginalized groups already face in life.” In June, Somerville, Mass., became the second U.S. city to ban the use of facial recognition technology in public spaces. The first was San Francisco. A coalition of organizations and trade associations has issued a letter to Congress outlining concerns with “blanket prohibitions” or moratoriums on facial recognition technology and listing beneficial uses for public safety, national security and fighting fraud. The Security Industry Association (SIA) is part of the coalition, the Information Technology and Innovation Foundation. A letter from seven members of Congress to HUD Secretary Ben Carson questioned the use of facial recognition in federally assisted housing Facial recognition technology has benefited Americans in many ways, such as helping to thwart identity thieves" The letter says: “While polls consistently show that Americans trust law enforcement to use facial recognition technology responsibly, some groups have called for lawmakers to enact bans on [the] technology. While we agree that it is important to have effective oversight and accountability of these tools to uphold and protect civil liberties, we disagree that a ban is the best option.” Development and guidance As alternatives to outright bans, the letter proposes expanded testing and performance standards, develop of best practices and guidance for law enforcement, and additional training for different uses of the technology. “Facial recognition technology has benefited Americans in many ways, such as helping to fight human trafficking, thwart identity thieves and improve passenger facilitation at airports and enhance aviation security,” says Don Erickson, CEO of SIA. “SIA believes this advanced technology should be used in a safe, accurate and effective way, and look forward to working with Congress to help the U.S. set the example on how to ethically and responsibly govern this technology.” SIA has produced a document called “Face Facts: Dispelling Common Myths Associated with Facial Recognition Technology.”
Case studies
With the market constantly demanding security changes, Anviz has taken a bold step forward with the launch of the M7 Palm—a groundbreaking smart biometric access control terminal that harnesses the power of palm vein recognition technology. As the need for intelligence and security in building spaces continues to evolve, the demand for more compatible yet user-friendly access control solutions has never been stronger. The M7 Palm represents our answer to this challenge, offering a unique blend of advanced palm vein recognition technology and practical functionality. With Palm Vein, the M7 Palm rejects all threats and provides absolute security for peace of mind. It is also adapted to all conditions without being affected by external factors. From concept to reality Understanding that real-world performance is the true measure of any security solution, Anviz initiated a comprehensive customer program shortly after the M7 Palm's development. The process began with an engaging webinar series, where potential partners and customers got their first glimpse of the technology. During these sessions, Anviz not only demonstrated the M7 Palm's capabilities but also discussed specific implementation scenarios and potential use cases with the partners. Regular remote support sessions Through regular remote support sessions, Anviz helped partners optimize their usage processes Following the webinars, selected partners received M7 Palm prototypes for hands-on usage. The technical team provided detailed installation guidance and used protocols, ensuring that partners could effectively evaluate the system in their specific environments. Through regular remote support sessions, Anviz helped partners optimize their usage processes to gather the most valuable insights about the M7 Palm's performance across different settings and user groups. Partnership spotlight: Portenntum's vision for the future Among the valued testing partners, Portenntum has emerged as a particularly enthusiastic advocate for palm vein technology. As a security solutions provider in Latin America, Portenntum brings years of expertise in implementing cutting-edge access control systems. Their thorough usage approach, including detailed video documentation of user interactions, has provided invaluable insights into real-world usage scenarios. Security with convenience "The future of access control lies in technologies that combine security with convenience," notes the Portenntum team. Their forward-thinking approach and willingness to explore new solutions make them an ideal partner in refining the M7 Palm's capabilities. Through their extensive client network, they've helped us understand how palm vein technology can address various security challenges across different industries. Voice of users: real-world experiences Their hands-on experience with the M7 Palm has revealed both immediate strengths and opportunities Anviz's comprehensive customer program has brought valuable insights from multiple partners, including Portenntum, SIASA, and JM SS SRL. Their hands-on experience with the M7 Palm has revealed both immediate strengths and opportunities for enhancement. Success stories in daily use Portenntum's usage team highlighted one of the system's key strengths, "In the second stage, when identifying once the palm was already registered, the process was very fast, even putting the palm in different positions." This flexibility in daily use demonstrates the M7 Palm's practical value in real-world applications. User-friendly SIASA's comprehensive usage, which involved enrolling their entire team, found the system "quite user-friendly." This broad-based usage provided valuable insights into how different users interact with the technology. JM SS SRL's implementation showed promising initial results, with the report that "all the personnel could register their palms to perfection" during the first phase of usage. Making palm recognition more intuitive Its user manual includes clear, step-by-step guidance for optimal palm positioning Based on SIASA's feedback, Anviz recognized an opportunity to make the palm positioning process more user-friendly. Its user manual includes clear, step-by-step guidance for optimal palm positioning. These instructions will help users quickly master the correct positioning technique, ensuring a smooth and efficient authentication process right from the start. Looking ahead: Heading the biometric revolution As Anviz prepares to roll out the M7 Palm more widely, they are already incorporating the insights gained from the customer program into product improvements. The development team is working on enhanced user guidance systems, refined recognition algorithms, and comprehensive documentation to ensure smooth implementation for future users. Operational efficiency The feedback suggests that palm vein technology could become a new benchmark in biometric security Industry pioneers among its partners have highlighted the M7 Palm's potential to transform access control standards, particularly in environments requiring high security and operational efficiency. Their feedback suggests that palm vein technology could become a new benchmark in biometric security solutions. Biometric access control The M7 Palm represents more than just a new product – it begins a new chapter in biometric access control. By combining cutting-edge palm vein recognition technology with real-world usability insights, Anviz is positioning itself at the forefront of the next generation of security solutions. This journey with the M7 Palm reinforces its commitment to innovation in the security industry. As Anviz continues to gather feedback and refine its technology, they are not just developing a product – they are helping shape the future of access control, one palm scan at a time.
RecFaces, a facial recognition software company, has announced the successful deployment of its flagship product, Id-Guard at Jorge Chávez International Airport in Lima, Peru. This implementation marks a significant milestone in bolstering security measures at one of South America's busiest airports, underscoring the importance of maintaining a high level of safety at public transportation hubs. Jorge Chávez International Airport Jorge Chávez International Airport serves as a vital gateway for travelers and cargo, welcoming more than 20 million international and national passengers every year. With such a high flow of people, ensuring the safety and security of passengers and airport personnel becomes crucial. Recognizing this need, RecFaces collaborated with airport authorities to implement their state-of-the-art Id-Guard solution and help ensure the safety of the facility. Enhanced security measures The solution's features enable airport authorities to prevent suspicious individuals from accessing the site The implementation of Id-Guard has significantly enhanced security measures, allowing for proactive monitoring and rapid response to potential security threats. The solution's features enable airport authorities to prevent suspicious individuals from accessing the site, thereby safeguarding the safety of passengers and staff. Highest level of security “Airport representatives felt the need for facial recognition to strengthen the security structure within the airport as a whole,” notes Maria Kazhuro, Business Development Director for the LATAM region, RecFaces. Maria Kazhuro adds, “Our goal was not only to provide the highest level of security but also to simplify work processes for security guards. We can confidently say that the installation of an ID guard has significantly improved security in the facility. Now both airport visitors and employees can be sure that they are under even greater protection than before.” Id-Guard facial recognition The deployment of Id-Guard at the Peruvian airport demonstrates RecFaces' dedication to excellence and innovation in the field of facial recognition technology. As airports worldwide continue to prioritize security and passenger experience, RecFaces remains at the forefront of delivering advanced biometric solutions tailored to the evolving needs of the aviation industry.
Munich’s Hofbräuhaus enjoys an iconic status, as both a heritage property and a spiritual home for lovers of German beer. “In this historic building is the world’s most famous tavern,” explains its Security Manager, Robert Graßl. “The whole world goes in and out. Security is very important.” Hofbräuhaus Bavarian Duke Wilhelm V commissioned Munich’s original Hofbräuhaus in 1589, initially as a brewery to supply the Wittelsbacher Hof. Moved at the end of the 19th century and severely damaged during World War II, it underwent reconstruction in 1958. It currently attracts tourists and city locals, seating up to 3,000 guests indoors and a further 400 in the beer garden. Need for digital access Inobtrusive digital devices and low-impact installation were a necessity to ensure compliance Although the building is an important heritage monument, it requires 21st-century digital access to keep site users safe and streamline day-to-day operations. They wanted fast, secure access rights management for employees and service providers including up to 100 waiters working each shift within a unified system that could authorize access at both the Hofbräuhaus and their food production facility in Brunntal. Of course, inobtrusive digital devices and low-impact installation were necessary to ensure compliance with heritage preservation regulations. eCLIQ key-based digital access solution Many electronic access products and technologies are not appropriate for historic buildings. An eCLIQ key-based digital access solution is different: eCLIQ cylinders are compatible with the strict monument preservation requirements at the Hofbräuhaus. They have a flush fit, so they don’t even appear to be part of an electronic locking system. With wireless installation at the doors, devices blend with the building interior. Programmable keys for staff management ASSA ABLOY fitted around 100 eCLIQ locking cylinders and supplied 340 eCLIQ programmable keys “We can exchange a mechanical cylinder 1:1 with an eCLIQ cylinder without having to modify anything on the door or install cables,” confirms Miriem Hammoudi, Business Development Manager at ASSA ABLOY Sicherheitstechnik GmbH. ASSA ABLOY fitted around 100 eCLIQ locking cylinders and supplied 340 eCLIQ programmable keys for Hofbräuhaus managers to issue to relevant staff and service contractors. Easy operation for flexible, cost-efficient management Every eCLIQ key has an integrated chip and is programmable individually for the keyholder. The versatility of eCLIQ is demonstrated when a key is lost: Access authorizations are removed rapidly, simply by reprogramming cylinders ensuring security is maintained. The eCLIQ system also helps manage workflows for service providers such as cleaners: Their access is enabled on a time-limited basis. A standard battery inside each programmable electronic key powers the cylinder or padlock on insertion and encrypts the data transfer between the cylinder, key, and system so no external power source or wiring is needed. Scalable web-based platform The Hofbräuhaus team manages their system via a flexible, scalable web-based platform, CLIQ Web Manager, “I can program keys from anywhere or also block them quickly if a key has been lost or if someone is no longer allowed to enter,” says Robert Graßl. “And I can install any cylinder in any door by adjusting the length. I don’t have to carry extra stock which is really cost effective.” Anytime, anywhere access The system is easy to expand anytime, future-proofing Hofbräuhaus access With the hosting solution chosen, access data is stored securely at ASSA ABLOY, accessible anytime and from any location, which is an ideal configuration for managing large systems or multiple locations. Their system is easy to expand anytime, future-proofing Hofbräuhaus access. Master key system “The situation before the new master key system was installed was problematic,” says Robert Graßl. “Keys were distributed and nobody knew who held them. Everyone carries only one key programmed with details of where and when they can enter. It’s perfect.”
The Rewley Road Swing Bridge, an integral part of Oxford's industrial history, underwent a remarkable transformation in 2023 from rusting to restoration. Through a collaborative effort between the Oxford Preservation Trust, the Railway Heritage Trust, Historic England, and input on security solutions from Jacksons Fencing, this iconic landmark was meticulously restored and safeguarded for the enjoyment of present and future generations. A journey through time Dating back to 1851, the Rewley Road Swing Bridge played a pivotal role in the movement of goods and people during the 19th century in Oxford. However, changing times lead to its disuse and subsequent state of disrepair. By the 1980s, the bridge stood permanently fixed in an open position. Recognizing the historical and cultural significance of the bridge, the Oxford Preservation Trust embarked on a restoration journey to bring this historical treasure back to life. Jacksons Fencing was specified by the Railway Heritage Trust and Historic England to provide demarcation fencing around the landmark, playing a vital role in ensuring the successful establishment of the bridge as a visitor attraction. Modern security meets historical elegance Fencing's unique vertical bar design not only exudes visual grace but also serves as a robust barrier To ensure the safety of visitors and protect the bridge from potential vandalism, Jacksons Fencing provided a thoughtful protection plan that seamlessly integrated modern security features with the bridge’s historical esthetic. In the pursuit of safeguarding the Rewley Road Swing Bridge, Jacksons Fencing introduced a total of 57 meters of 1.25 m high Barbican Imperial® fencing which seamlessly harmonized security with the bridge's historical charm. The fencing's unique vertical bar design not only exudes visual elegance but also serves as a robust barrier against unauthorized access. This fence choice is ideal for a heritage project as it offers the look of traditional metal railings but with a modern, stronger, and more sustainable tubular design. Barbican Imperial fencing Concealed connectors and the absence of visible bolts or fixings further amplify the fencing's security prowess while maintaining a clean and uncluttered appearance. As an integral part of the protection strategy, a 3.6 m wide double leaf gate was integrated, complete with a pad-lockable slide latch. This innovative latch ensures controlled access, reinforcing security without compromising convenience. The specification of high-quality materials was paramount for this project. The selected Barbican Imperial fencing was meticulously crafted from high-quality hot dip galvanized steel, equipping it with exceptional strength and resistance against the corrosive forces of time. To ensure the bridge's appearance would not wither, a black polyester powder coating was applied. This not only adds a touch of timeless sophistication but also guarantees durability and a long-lasting finish. By embracing modern techniques, the bridge's protective features are seamlessly integrated into its historic context, allowing it to confidently stand the test of time. A safe haven for local wildlife Gaps between the pales of the fencing facilitate the free movement of animals through the site Jacksons Fencing's commitment extended beyond human safety to encompass the thriving local ecosystem. With a profound understanding of the importance of coexistence with nature, the new security solution was intentionally designed to accommodate the movement of local wildlife. Gaps between the pales of the fencing facilitate the free movement of animals through the site ensuring that while security remains uncompromised, the natural ecosystem can flourish undisturbed. Now fully restored, a new life has been breathed into the Rewley Road Swing Bridge. Beyond its full restoration, the bridge now symbolizes a link between the past and the future. Author's quote Peter Jackson, Managing Director, Jacksons Fencing, comments: "We're thrilled to have been part of restoring the Rewley Road Swing Bridge's historic charm while infusing modern security. Our commitment to eco-conscious solutions mirrors the Oxford Preservation Trust's vision for a biodiverse landscape. He adds, "By strategically integrating wildlife-friendly features, we've created a haven for both heritage and nature. The bridge's removal from the Heritage at Risk Register and its recognition with the Railway Heritage Trust Conservation Award in 2022 spotlight our collective dedication to preserving history while embracing security and sustainability."
Located in Kerala, India, the Somatheeram Ayurveda Hospital with a Resort Ambiance is the best place for not only visual rejuvenation but also physical and mental rejuvenation. Through Ayurveda, Somatheeram provides a means to shed all worries, anxieties, and illnesses. With the objective of combining Ayurveda and Tourism, the Somatheeram Research Institute & Ayurveda Hospital was founded in the year 1985, thus making it the world’s first-ever Ayurvedic Hospital in a Resort Ambiance. The Somatheeram Group of Companies came into being with the efforts of the Founder Managing Director, and Architect Mr. Baby Mathew. Challenges Multi-location transmission proves to be an expensive affair if devices are not chosen wisely Somatheeram has multiple resorts, located at different locations. Multi-location communication can prove to be an expensive affair if communication devices are not chosen wisely. Their dependence on public service providers for communication added to their woes of communication between their resorts. To elaborate: Feasibility of existing telephony: Existing telephony became impracticable considering the frequent communication between multi-located properties. Managing different protocols: Interface with different telecom networks requires managing different protocols, which can be cumbersome, time, and energy-consuming. Absence of modern phone features: The lack of advanced features like abbreviated dialing, call pick up, and internal call restriction, prevented them from becoming efficient in day-to-day operations. Transition to modern communication with existing infrastructure: Their investment in existing infrastructure needed protection while also a provision had to be made to modernize the communication using existing infrastructure. Solution The solution offered was based on the fundamentals of multi-location communication solutions Matrix analyzed the challenges of communications for Somatheeram and crafted a solution that was the best fit. The solution offered was based on the fundamentals of multi-location communication solutions. This included the Matrix range of IP-PBX (ETERNITY GENX12S) and GSM Gateway (SIMADO GFX11 and SIMADO GFX11 4G) that optimized the feasibility of communication and helped the firm become more efficient. Solution includes: The Hybrid IP-PBX included ETERNITY GENX12SAC, which enabled them up to 240 Analog users with 64 CO Ports. Another Hybrid IP-PBX included ETERNITY PENX, which allowed them access to 100 IP Users, onboard IP User Support, LDAP Client support, support of 4G VoLTE ports, COSEC Door Integration, and much more. The GSM gateway included SIMADO GFX11 and SIMADO GFX11 4G which enabled them to make and receive calls from analog extensions. The capability to integrate with almost all industry-pioneering PBXs enabled them a smooth transition to modern communication while maintaining existing infrastructure. Results The solution so implemented enabled all properties to work as a single communication platform and proved to be beneficial for Somatheeram and its properties in more than one way. The Hybrid IP-PBX enabled them, unified communication facilities like Email to SMS, audio/video calling, unified messaging facilities, and multi-location collaboration features like UC client integration, one-number reach, etc. The Hybrid IP-PBX also enabled, investment optimization through universal network connectivity, easy and centralized phonebook management through LDAP client support, mobility convenience through 4G VoLTE support, and much more. The GSM/4G gateway enabled them, GSM/4G connectivity to existing infrastructure, hotline extension dialing, emergency number dialing even in the absence of a sim card, etc. through secure network bridging.
Artificial Intelligence Technology Solutions, Inc., a pioneer in AI-driven security and productivity solutions along with its wholly owned subsidiary, Robotic Assistance Devices, Inc. (RAD), published a case study reviewing the overwhelmingly positive results from the successful deployment of multiple ROSA security robots at a multi-family community in San Jose, California. Innovative security technology The case study titled "From Break-Ins to Breakthroughs: How a Multiple RAD ROSA System Reshaped an HOA Community’s Security" highlights the transformation of Westside Manor Homeowners Association from a vulnerable community plagued by often dangerous break-ins to a secure environment through the adoption of RAD’s innovative security technology. Struggling with limited funds and frustrated with previously ineffective measures Struggling with limited funds and frustrated with previously ineffective measures, the HOA partnered with EPIC Security Works, a RAD-authorized dealer, to deploy multiple ROSA devices equipped with AI analytics, lights, audio, and visual messaging. This innovative approach led to a significant reduction in break-ins, effectively transforming the community's security landscape. Author's quote “This case study summarizes the detailed and coordinated efforts that RAD, its dealers, remote monitoring partners, property managers, and end users perform as we successfully disrupt the security and #proptech marketplaces,” said Steve Reinharz, CEO of AITX and RAD. “I am so proud of this winning combination where everything and everybody worked together enabling a safe and more secure environment for the community’s residents.” RAD’s software suite notification ROSA is a multiple award-winning, compact, self-contained, portable, security and communication solution that can be deployed in about 15 minutes. Like other RAD solutions, it only requires power as it includes all necessary communications hardware. ROSA’s AI-driven security analytics include human, firearm, vehicle detection, license plate recognition, responsive digital signage and audio messaging, and complete integration with RAD’s software suite notification and autonomous response library. RAD has published four Case Studies detailing how ROSA has helped eliminate instances of theft Two-way communication is optimized for cellular, including live video from ROSA’s dual high-resolution, full-color, always-on cameras. RAD has published four Case Studies detailing how ROSA has helped eliminate instances of theft, trespassing and loitering at multi-family communities, car rental locations, and construction sites across the country. RAD solutions AITX, through its subsidiary, Robotic Assistance Devices, Inc. (RAD), is redefining the $25 billion (US) security and guarding services industry through its broad lineup of innovative, AI-driven Solutions-as-a-Service business model. RAD solutions are specifically designed to provide cost savings to businesses of between 35% and 80% when compared to the industry’s existing and costly manned security guarding and monitoring model. RAD delivers this tremendous cost savings via a suite of stationary and mobile robotic solutions that complement, and at times, directly replace the need for human personnel in environments better suited for machines. All RAD technologies, AI-based analytics, and software platforms are developed in-house.


Products
Round table discussion
Historically, the emphasis of security systems has been on reactivity, whether it’s providing video evidence of an incident or data to support a resulting investigation. Reactivity is core to impactful security, but increasingly, systems are also seeking to be more proactive. A proactive system seeks to prevent events from happening in the first place, thus mitigating the harm to an organization, and making the need for a reactive response moot. We asked this week’s Expert Panel Roundtable: How can security systems be proactive? Please provide a couple of examples.
The upcoming ISC West trade show in Las Vegas will offer innumerable networking and learning opportunities for attendees. Manufacturers will take the opportunity to promote their businesses and showcase products and services to a targeted audience. Best of all, the event will be "in person," an advantage we should never again take for granted. We asked this week's Expert Panel Roundtable: What big announcements do you expect at ISC West 2023?
There’s always more to talk about in our Expert Panel Roundtable discussions, and we appreciate the variety of opinionated responses offered throughout the year. Looking back at 2022, we found several random and uncategorized Expert Panel responses that were not previously published. We have rescued these responses from our cutting-room floor and present them here in the interest of generating even more discussion.