The ID badge has become a nearly universal emblem of corporate life. In companies large and small, new employees are issued a radio-frequency identification (RFID) card that provides visual identification and unlocks the door when they arrive at work.
RFID cards provide employees with secure 24-7 access to the workplace while maintaining a record of exactly who has entered the building and when. They are cheaper, easier to manage and more secure than physical keys; if they are lost or an employee is terminated, card access can simply be turned off.
Protecting sensitive information
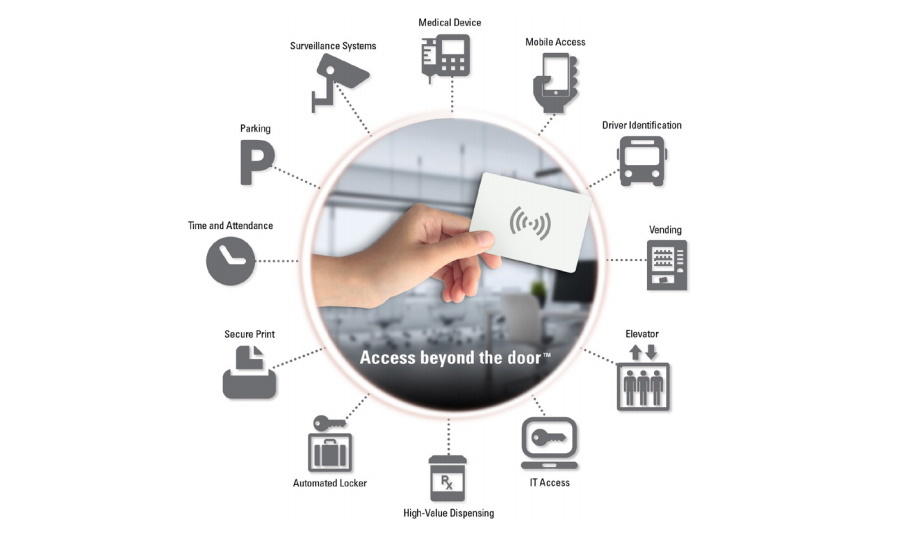
The same cards can be used to enable access to all kinds of business systems beyond the front door
The same cards can be used to enable access to all kinds of business systems beyond the front door. Companies can leverage the cards employees are already carrying to control access to the information, systems, materials and devices their employees use at work. Companies need systems in place to ensure that authorized employees have access to the information, business systems, materials and equipment they need, while keeping unauthorized users out.
Effective access control and user authentication helps companies protect sensitive information (such as financials, HR data or company IP), control material and supply costs, improve safety and streamline workflows.
- User authentication is the ability to correctly identify an individual user and match their information to the devices or systems they are using.
- Access control is the ability to ensure that only authorized users are able to gain access to an asset or system.
User authentication and access control
Companies may use a variety of strategies for user authentication and access control, including physical keys, passwords and PINs. However, these methods are often less than ideal, especially when employees have to manage multiple keys or remember different passwords and PINs for different systems.
Using an employee ID badge to access all of the other systems and materials they need during their workday is faster and easier for employees and simpler for business IT departments to manage. RFID systems for user authentication and access control can be used across a variety of business systems and devices. For example:
Single sign-On (SSO) systems
They also eliminate the IT headache of resetting forgotten passwords and PINs
SSO systems allow a user to sign into the company network and access all of the software systems and records they are authorized to use and view. An RFID reader can be attached to, or embedded in, each workstation to enable fast and easy sign-on with an employee ID badge. RFID is more secure than password or PIN systems, as employees generally keep their ID badge on their person and are less likely to share a badge than a password.
They also eliminate the IT headache of resetting forgotten passwords and PINs. RFID is especially valuable in settings where multiple employees may utilize the same workstation, as in call centers with multiple shifts or companies with hot-desking arrangements. The employee can easily gain access to all of their systems and files from any workstation by simply swiping their ID card to sign onto the network.
Secure print Management
Secure printing is beneficial for both cost-control and information management. Employees can send a print job from their desk at any time. The printer will only start printing when the employee signs in to start the job.
This ensures that sensitive information will not be left lying on an unattended printer if there is a delay between the employee hitting ‘send’ from their desk and picking up the printout. Print management also reduces waste and provides accountability by tracking how much each employee is printing. RFID access for print management is faster, easier and more secure than entering login credentials into a small printer interface.
Meeting check-In and scheduling
Electronic displays are now used for scheduling, tracking attendance and controlling AV equipment
Meeting room displays can now do a whole lot more than simply announce which meetings are scheduled for the day. Sophisticated electronic displays are now used for scheduling, tracking attendance and controlling AV equipment.
Integrating RFID into a meeting room display allows employees to quickly check in to their meeting as they walk through the door. Systems can even be set to recognize the meeting organizer and automatically launch presentations or conference calls when they arrive.
RFID user authentication
Industrial vending machines and kiosks: Industrial vending machines and kiosks are an increasingly popular solution for providing employee access to necessary materials and equipment, from lab chemicals to safety gear. RFID user authentication and access control ensure that only authorized employees can get access to materials and supplies. They also link user identities to the materials they are using for increased accountability and better materials management
Materials handling and manufacturing equipment: RFID can be used to control access to expensive and potentially dangerous equipment such as forklifts or robots. User authentication and access control ensure that only trained and authorized users are able to operate the equipment or make changes to their programming. RFID is simpler and more secure than a key system and provides a record of who has used the equipment.
Discover how AI, biometrics, and analytics are transforming casino security