Key management
Balancing operational efficiencies and customer satisfaction with costs, resources, and legislative obligations is a challenge faced by every security services provider offering keyholding and alarm response. While mobile security operations must adhere to strict compliance, with BS 7984 standard and SIA licensing for guards at the very core of the operations, security providers are increasingly contending with a wider range of regulations. Among the most pressing are sustainability requirement...
Keycafe, a global pioneer in cloud connected key management, continues to expand the success of its MS5 SmartBox, an advanced solution already trusted by automotive businesses worldwide. Built for teams managing anywhere from a few to hundreds of vehicles, the MS5 has become a new benchmark for key management, control, and traceability. “Every lost or misplaced key can disrupt workflow and damage customer confidence,” said Jason Crabb, CMO and Co-founder of Keycafe. “The MS5...
Keycafe, a pioneer in cloud-connected key management, continues to expand the success of its MS5 SmartBox, an advanced solution already trusted by automotive businesses worldwide. Built for teams managing anywhere from a few to hundreds of vehicles, the MS5 has become a new benchmark for key management, control, and traceability. MS5 SmartBox “Every lost or misplaced key can disrupt workflow and damage customer confidence,” said Jason Crabb, CMO and Co-founder of Keycafe. “...
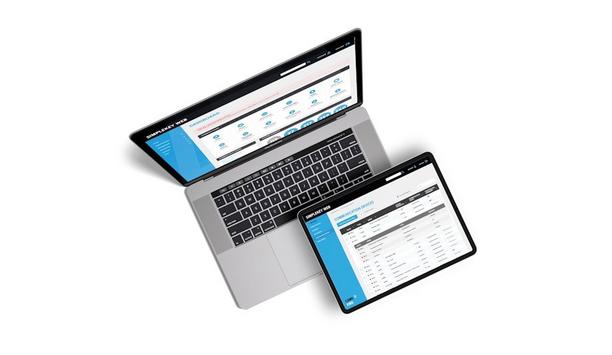
CAME KMS now announced the rollout of a number of quality of life updates to its SimpleKey Web (SKW) platform, designed to provide installers, end users, and advantage residents with new tools, improved usability, and enhanced security — all at no additional cost. October 2025 update The October 2025 update introduces several new features, including: Sign-Off Certificate Email Confirmations: Installers can now generate digitally approved sign-off certificates and send them directly to...
HID, a pioneer in trusted identity solutions, announces it has signed an agreement to acquire IDmelon, a Vancouver-based secure sign-in solution provider that streamlines the adoption of passwordless authentication through its proprietary software platform. IDmelon’s offering allows users to turn existing identifiers, such as a physical credential, smartphone, or biometric, into enterprise-grade FIDO security keys. In addition to its software solution, IDmelon offers hardware that support...
Eviden, the Atos Group product brand, pioneering in advanced computing, cybersecurity products, mission-critical systems, and vision AI announces the strengthening of its cybersecurity product offering through the integration of Cosmian’s Key Management System (KMS). In an era marked by rapidly increasing cyber threats, it is imperative that French and European companies retain control over the security of their most sensitive data, irrespective of deployment environment. Merger between...
News
Morse Watchmans, the industry pioneer in key control and asset management systems, is highlighting its flagship KeyWatcher Touch and full suite of electronic key and asset management solutions at GSX 2025 in New Orleans. Attendees can visit Booth #3713 to explore how Morse Watchmans technologies help organizations secure keys, protect assets, and strengthen operational accountability. “KeyWatcher Touch continues to set the standard in key management, providing organizations with systems that deliver complete confidence and control over key and asset management,” said Tim Purpura, VP of Global Sales and Marketing, Morse Watchmans. Lineup of key management solutions Featured at the booth will be KeyWatcher Touch, a modular and easy-to-scale key control cabinet “At GSX, we’ll showcase our lineup of key management solutions and help attendees to see firsthand how they deliver ROI, accountability, and increased efficiency,” concluded Tim Purpura. Featured at the booth will be KeyWatcher Touch, a modular and easy-to-scale key control cabinet with a touch-screen interface and real-time reporting capabilities. It delivers automated key tracking, detailed audit trails, and integration options with access control and other business systems. When networked, KeyAnywhere enables key returns at any KeyWatcher across the enterprise, while KeyFind can pinpoint a specific key and determine who has checked it out. KeyWatcher is an indispensable platform, allowing management of critical keys for small, medium and enterprise-scale businesses across all vertical markets. Additional products In addition to the KeyWatcher Touch, visitors can explore: SmartKey Electronic Locker Systems: Designed to secure, track, and control access to larger assets, these lockers can integrate across business systems, including access control. This enhances visibility, reduces risk, and improves asset tracking and reporting. KeyBank Touch Key Access Control System: Simplified key management system with a 7-inch touch screen interface and a capacity of up to 18,000 keys and 10,000 users per site. Emergency Key Grab (EKG) System: A trusted solution for ensuring rapid, secure access to facility keys during emergencies or lockdown situations. The color-coded system enables access by only authorized emergency personnel using a unique PIN code or other secure credentials to retrieve keys quickly, resulting in faster response times. Visit GSX Booth #3713 to speak with a Morse Watchmans specialist on how key management systems deliver compliance, efficiency, accountability, and peace of mind across industries.
Anyone responsible for facilities management or security is well aware that access control and keyholding are often challenging and, consequently, can cause a number of operational and even financial issues. Appetite for change Keyholding and access control are dynamic processes that involve daily activity and ongoing management. Keys are frequently stored off-site and exchanged daily. Access cards and fobs require setup. Every lapse creates a chain reaction: replacements, lock changes, risk reporting, all of which consume time, money, and patience. Keyholding and access control are dynamic processes that involve daily activity Against this backdrop, it’s not surprising that more and more organizations of various sizes, both in public and private sectors, are actively seeking alternatives to traditional methods of manned keyholding or manual pen-and-paper visitor logs. There is a clear shift towards technology-led solutions that offer greater reliability, visibility, and scalability. The driving force behind this move is not innovation for its own sake but rising service expectations. Things must be done faster, better,and more efficiently; FM and security tenders outline stricter requirements for alarm response times and service delivery, with little tolerance for service shortfalls and delays, or penalties will follow. Moving beyond the traditional approach As operational demands evolve, security and FM professionals are beginning to ask the same question: Is there a better way? “Over the past couple of years, we have seen a drastic positive change in attitudes towards new methods of keyholding,” says Stuart Wheeler, Managing Director of Keynetics. The incorporated technology enables the management of access to 100 of locations remotely Keynetics is one of the companies pioneering change in this space, offering smart key management solutions such as SentriGuard. With this system, keys are stored at the point of need in key safes with commercial-grade, certified security. They are accessed either using a temporary code or a mobile app. The incorporated technology enables management of access to hundreds of locations remotely, and provides notifications when keys are not returned or the device battery is running low. Adopting new methods Stuart recalls initial resistance to change in the market. “When we started Keynetics, there was hesitation around adopting new methods. I was told more than once, “No way I am storing keys in a key safe”, but that mindset has shifted entirely.” He attributes the change in attitude to a combination of persistent issues with the existing keyholding methods and increased understanding of the benefits that alternative approaches can offer, particularly if they offer adequate security and greater control. Identified the most common considerations “We’re now seeing strong interest from a wide variety of organizations,” he says, “including security service providers, FM companies, and in-house teams operating in a range of sectors.” “Selecting the right system is often the most complex part,” he adds. “Requirements can differ significantly depending on the sector and business model, but there are key areas that tend to come up repeatedly. Over time, we’ve identified the most common considerations raised by both existing customers and those looking for a change.” Access traceability: The top priority While security remains central, the most consistently cited requirement is access traceability, or the ability to see who accessed which property, when, and for how long. In the operating domain, access data is seen as a vital resource, not only for day-to-day management “In many cases, the high security rating of the device was accepted without much debate,” Stuart notes. “What proved to be more important was the ability to run real-time audit reports without needing to visit premises and upload visit logs, or complete some other action to get hold of that valuable access data.” This growing focus is understandable. Technology is now expected to take on tasks previously carried out by personnel, but unmanned systems must still provide a high level of oversight and accountability. In the operating environment, access data is seen as a vital resource, not only for day-to-day management, but also for compliance, reporting and service performance evaluation. Security: The most risk-dependent factor Naturally, security is a high-ranking factor when selecting an access control solution. However, the emphasis placed on it varies significantly depending on the sector and the perceived risks. “For obvious reasons, clients in high-risk sectors, such as banking or government, conduct in-depth evaluations and demand robust certification,” Stuart explains. “We’ve attended countless meetings with some clients, continuously providing proof of both physical and digital security. Smaller companies with lower perceived risks, on the other hand, often acknowledged the security rating and focused more on factors like cost.” The takeaway is clear: while security is crucial, the level of scrutiny it receives is relative to the client’s sector and operational risk. Costs: Are they breaking the bank here? In many cases, new systems are executed not because they are cheap, but because the cost of doing nothing is higher It is in human nature to want the best and the shiniest, but the implementation costs may become the stopping point. For many decision-makers, the question often isn’t whether a solution is ideal, it’s whether it aligns with operational needs at a sustainable cost. FM directors work within fixed budgets, often balancing multiple objectives alongside day-to-day operations. Cost isn't just about the system itself, it is about scale. A high-end solution may be entirely feasible for a business with one manufacturing site, while even a budget-friendly option could prove expensive for someone managing hundreds of retail locations. In many cases, new systems are implemented not because they are cheap, but because the cost of doing nothing is higher. A serious issue with the current method may justify investment, where the price of failure outweighs the cost of change. Practical considerations: Installation, hardware, and usability Beyond the top three factors, practicalities such as installation requirements, ease of use, and maintenance also influence the decision-making process. Organizations typically seek systems that can be retrofitted with minimal disruption. Common questions include: Is the unit hardwired? Does it need a power supply or internet connection? How long does installation take? Where installation is overly complex, or the benefits do not clearly outweigh the effort required, adoption may stall. On the other hand, a quick, straightforward setup is often seen as a major advantage. Post-purchase support, including maintenance, training and customer service, is usually discussed later in the process, but remains an important factor in long-term satisfaction. System integrations: A logical next step The ability to manage multiple systems, including access control, alarms and cameras, via one interface They live in a digital age where doorbells can be answered from miles away and kettles are turned on with a tap on the phone screen. So it is no surprise that the security sector is so tech-oriented. System integration is fast becoming a top request. The ability to manage multiple systems, including access control, alarms and cameras, through one interface offers a streamlined and time-saving solution that increases control. Stuart notes, “We’re primarily a software development company, so the digital side of our solutions is built with continuous improvement in mind. Right now, one of our long-standing clients is trialing an integration between our system and AJAX alarms. Since they actively use both SentriGuard and AJAX, it makes perfect sense to manage alarm controls within the same key management platform.” While system integration is often not the top priority, it does indicate a forward-thinking, customer-centric approach. No right or wrong Ultimately, choosing the right keyholding or access control solution depends entirely on the end user’s needs. Factors such as access traceability, security (physical and digital), and implementation costs all play a part. There is no one-size-fits-all answer. Some will retain their current methods. Others will go fully keyless. Many will find a golden middle ground. But the journey doesn’t end at purchase. Continuous evaluation, access management refinement, and user feedback are essential to ensure ongoing effectiveness or to justify the search for an even better solution. After all, the market never stands still.
Allegion US, a pioneering provider of security products, technology, and solutions, announced the launch of Overtur™ Key System Management, a cloud-based subscription solution that offers authorized users a simpler way to view, manage, track, and update a building’s key system – regardless of complexity. Overtur Key System Management is an extension of the Overtur digital environment, which empowers project teams to collaborate in real time on the design, specification, construction, and management of openings – helping them to be more effective and efficient all while improving project outcomes and client satisfaction. Complementary key system design One of the subscription-based levels of Overtur Key System Management can unlock features With the new Overtur Key System Management offerings, facility managers, locksmiths, and distributors can now access complementary key system design tools that empower users to survey conditions, collaborate, filter data, design hierarchies, assign symbols, utilize cloud-based features, and create detailed key schedules. Moving to one of the subscription-based levels of Overtur Key System Management can unlock features that will help protect sensitive information, manage key control and building access, helping to create secure and efficient management of key systems. Use of innovative solutions “Overtur was created to facilitate collaboration, with the mission of making it easier for project teams to design, construct, and manage door openings and the corresponding hardware,” said Holly O’Haver, Overtur Business Pioneer at Allegion. “Overtur Key System Management is the evolution of this vision, offering advanced tools to streamline key system design and management, helping to preserve the integrity and simplify management of the key system through the use of innovation solutions.” Three tiers of Overtur Key System Management Overtur Key System Management is available to security professionals in three tiers: Overtur Key System Design is complementary for Overtur users and streamlines key system design and data capture with features that allow users to: Build and visualize a key system hierarchy and schematic Survey existing conditions on site using the mobile app Conduct key meetings using the collaborative tools and add notes directly within the platform Assign and view as many key symbols as needed per building and per opening Focus on specific data using customizable data filters Enjoy unlimited users, automated updates, and secure cloud storage Generate comprehensive key schedules with fully configured part numbers Level 1: Key System Design + Manage Bitting/Pinning: A level 1 subscription lets you do more by utilizing all the complementary aspects of the Overtur digital environment plus: View available bittings Request next available change keys and get results within minutes Get on-demand bitting lists and pinning charts Import key symbol descriptions and associated openings Get started with an online hour-long training session with an onboarding specialist Level 2: All Level 1 Features + Key Control: The level 2 subscription builds on previous levels with customized onboarding and advanced features that include: Track issuance and return of keys and key rings Upload the key holder list View and manage key holder by opening/associated symbol Create key rings Identify a specific key holder by key assignment using system-designated serial numbers Store key holder agreements as attachments Create and save custom views to quickly filter and search information Enjoy customized training and personalized step-by-step setup assistance for a faster start Significant challenges of the key system management solution Without a proper key system management solution, organizations can face significant challenges such as difficult auditing, security risks, and inefficient tracking of key issuances. Overtur Key System Management addresses these issues by providing a comprehensive, cloud-based solution that provides the tools for secure data storage, efficient key control, and accurate tracking. By leveraging Overtur software, organizations can enhance their security, streamline operations, and maintain precise control over their key systems.
Morse Watchmans, the industry pioneer in key control and asset management systems, invites Apartmentalize 2025 attendees to visit booth #3000 June 11-13 to experience live demonstrations of the award-winning KeyWatcher® Touch system and explore comprehensive key control solutions designed specifically for residential building management. "For residential property managers, effective key control is no longer just good practice, it's essential. We understand the critical demands on residential property operations, and the KeyWatcher® Touch system is purpose-built to meet them," said Tim Purpura, VP of Global Sales and Marketing, Morse Watchmans. "Visit our booth to discover how better key control leads to safer, more efficient building operations.” KeyWatcher® Touch electronic key KeyWatcher® Touch electronic key cabinet is a key control solution mainly designed for corps The KeyWatcher® Touch electronic key cabinet is a scalable key control solution specifically designed for organizations managing multiple keys across residential properties. Featuring a 7-inch touchscreen interface and patented SmartKey® system with KeyAnywhere® technology, the system enables secure key withdrawal and return to any connected cabinet within a network. KeyWatcher® Touch seamlessly integrates with pioneering access control systems, creating comprehensive layered security ideal for residential building management. Efficient key management operations Residential buildings—from gated townhome communities to high-rise towers—depend on secure, efficient key management to protect tenants and maintain operations. Whether the property is brand-new or decades old, building managers are responsible for tracking dozens to thousands of physical keys every day. Common access scenarios include: Contractors entering units for repairs or renovations Emergency responders needing rapid access in a crisis Tradespeople like plumbers or HVAC technicians requiring localized entry Delivery services accessing secure interior drop-off points KeyWatcher® Touch system The KeyWatcher® Touch system is built to streamline these operations. Property managers can attach detailed notes to each key transaction, receive real-time alerts when keys are removed or returned, and manage access across multiple properties from a centralized database. With flexible, scalable deployment, it’s an ideal solution for managing single properties, multi-building sites, and complex residential portfolios. Stop by the Morse Watchmans Apartmentalize booth #3000 to experience this solution firsthand.
Camden Door Controls has announced a number of enhancements to its popular CX-DE1200 Series EXIT WATCH™ delayed egress magnetic locks. These include a louder 75 dB voice annunciation, packaging the lock with a 90 dB remote sounder, and adding the option for a cost-effective kit that includes the maglock, remote sounder, and a remote reset key switch. Camden EXIT WATCH™ series Camden EXIT WATCH™ series delayed egress magnetic locks feature a 1200 lb. holding force, rugged aluminum construction, voice, and LED count-down annunciation, with anti-tailgating and anti-passback. They are available in single and two-door models that are UL-listed and comply with NFPA, IBC, IFC, UBC, and CPC code requirements.
Powering digital access with energy-harvesting technology frees organizations from wiring and even batteries. However, to meet the challenges of the future, digital access needs more. It needs technologies and software platforms flexible enough to grow and adapt with the evolving needs of each organization, protecting their investment in digital access while delivering an ROI every day. Digital access solutions Kinetic energy generated by inserting the intelligent key is harvested to power the lock’s security features Using decades of expertise in designing and engineering key-based access cylinders and solutions, ASSA ABLOY developed PULSE, key-based digital access powered by innovative energy-harvesting technology and part of ASSA ABLOY's suite of digital access solutions. With ABLOY PULSE, the kinetic energy generated by inserting the intelligent key is harvested to power the lock’s encrypted digital security. This energy source – keyholder input – is completely renewable and contributes to building sustainability goals. Latest generation of technology Building users enjoy everyday convenience. They carry one PULSE key pre-programmed with all their access rights. It has an RFID tag inside and can also operate readers, whether on wireless locks or wall-mounted beside an electrified opening. Building users do not need to carry two credentials. To enhance site security and user privacy, PULSE credentials are powered by Seos®, the latest generation of technology with the highest encryption and authentication standards. ABLOY PULSE building managers PULSE locking cylinders and keys are self-powered by reliable energy-harvesting technology ABLOY PULSE offers building managers reliable security they can trust. They can equip almost any opening with a device range which includes door cylinders, cam-locks, furniture locks, and padlocks for indoor and outdoor use. There is no cabling, wiring, or batteries required: PULSE locking cylinders and keys are self-powered by reliable energy-harvesting technology. Integrate with building solutions “ABLOY PULSE offers customers a flexible solution to digitalize their access management and make their access ready for what’s ahead. It has been developed to integrate easily with their building solutions,” says Jarno Onnela, PULSE Product Manager at ABLOY. “PULSE cylinders are fast and cost-efficient to install, because they require no major adjustments to a door. An installer simply swaps out an existing mechanical cylinder.” ASSA ABLOY Access® software ABLOY PULSE can be managed from cloud-based ASSA ABLOY Access® software ABLOY PULSE can be managed from cloud-based ASSA ABLOY Access® software. This intuitive solution enables organizations to manage access from anywhere. Both keys and cylinders are reusable and reprogrammable: managing staff turnover becomes faster and simpler for facilities teams. Security staff can issue access and block lost keys from wherever they are. Advantages of PULSE technology The unique advantages of PULSE technology have already been recognized by awards juries in Europe, the Middle East, and beyond. It was named the Sustainability Champion Award winner at Intersec 2024, Dubai. In 2022, PULSE cylinders’ energy-harvesting performance earned the Construction Energy Award at the BYGGERI fair in Denmark. ABLOY PULSE commercial buildings The unique advantages of PULSE technology have already been recognized by awards juries in Europe “ABLOY PULSE already protects many different types of site, from commercial buildings and multi-residential housing, to education and healthcare premises,” adds Jarno. “New functionalities in ASSA ABLOY Access management software, such as support for reservation systems, continue to further expand use-cases. We have also extended the availability of this innovative solution to new markets including Scandinavia, France, the UK, Poland, Singapore, Hong Kong, and the Benelux countries.” Extend the range of locking solutions with ASSA ABLOY Access ASSA ABLOY Access also integrates seamlessly with the ABLOY CUMULUS mobile and keyless access solution. Completely customizable, with intuitive APIs and SDKs for app development, CUMULUS becomes part of each customer’s individual workflows in a way specific to their own organization. In addition, the revolutionary CUMULUS Controller adds mobile access capability to any electric or electronic lock – from any brand. ABLOY CUMULUS instantly makes digital access mobile-ready. It can go wherever the customer needs.


Expert commentary
Amidst the challenges of a prevailing economic downturn, the retail sector finds itself grappling with an unparalleled rise in incidents of shoplifting, theft, and burglaries. The disconcerting scenes witnessed on London’s Oxford Street in August 2023, where crowds gathered, looting as many stores as possible, sent shockwaves across the nation’s retailers. This alarming surge in retail crime has put retailers on high alert, as they contend with a rising tide of security concerns. Shoplifting concerns Recent data from the Union of Shop Distributive and Allied Workers (USDAW), has raised alarming concerns: shoplifting rates have surged by an unprecedented 24%. In the first half of 2023 alone, there were approximately 8 million reported shoplifting incidents. With the ongoing burden of the cost of living crisis and the approaching festive season, it is expected that these figures will keep surging. Implementing robust security measures Theft and prevention strategies cost retailers approximately £2 billion in 2021/2022 While more help from the Government to support retail workers and the businesses shoplifters target is certainly needed, the implementation of robust security measures will significantly contribute to deterring these crimes from occurring in the first place. British retailers spend millions on tools to deter and catch shoplifters inside stores, from CCTV and security guards to electronic tagging and alarms. The Grocer reported that theft and prevention strategies cost retailers approximately £2 billion in 2021/2022. Despite these initial costs, other threats are at play beyond the shop floor. Break-ins by criminal gangs For many large town center stores and supermarkets, and units in retail parks, the rear doors and delivery areas are commonly targeted by criminal gangs. It’s not uncommon for thefts to occur from pallets or cages that have been unloaded from lorries and sit waiting to be moved into the building. After-hours break-ins are a risk for all store owners too, particularly over the festive season when a lot of high-value stock has been delivered to shops and supermarkets. Addressing anti-social behaviour The additional fencing was deemed an essential measure to safeguard the community Anti-social behavior also poses a challenge for retailers. In 2022, an Aldi based in Derby invested in security fencing to protect staff and deter loitering groups. The additional fencing was deemed an essential measure to safeguard the community, as dangerous items were frequently found outside the store, including weapons and hypodermic needles. So how do physical security solutions such as fencing and gates help better protect retail establishments such as supermarkets and edge-of-town retail park shops? Fencing and gates: a critical component of retail security 1. Risk assessment and target hardening A thorough risk assessment will identify potential weak spots that require protection. ‘Target hardening’ involves implementing physical security measures that become more robust as they approach the target. This helps deter intruders while ensuring ease of access for customers and staff. 2. Effective perimeter security Opt for difficult-to-climb security fencing that provides a robust obstacle against thieves, vandals, and intruders Selecting fencing solutions according to the potential threats, site characteristics, and topography is crucial. It is important to specify fencing that strikes a balance and maintains a welcoming appearance while safeguarding external areas of the store or warehouse from potential harm and unauthorized access. Solid fencing which provides concealment can help to conceal expensive goods and remove them as a target for opportunistic theft. Opt for difficult-to-climb security fencing that provides a robust obstacle against thieves, vandals, and intruders. I recommend selecting a sufficiently tall and robust fence such as an acoustic barrier. Its noise-reducing properties are often beneficial for these types of sites too. 3. Controlling vehicular speeds and access To enhance security, consider controlling vehicular speeds and access. One effective approach is the installation of bollards at the ends of traditional high streets. This practice is already commonplace as a means of safeguarding against hostile vehicle attacks, but it can also play a pivotal role in preventing quick getaways of vehicles involved in potential heists. Additionally, employing road blockers and sliding gates at the rear entrances of delivery areas would serve to fortify security further. These measures can help in delaying vehicles, allowing for necessary checks to be conducted. 4. Balancing security with aesthetics The presence of high-security fencing can also make a site more of a target for vandals and burglars Another challenge is avoiding creating an imposing presence, especially important for areas situated near residential communities. The presence of high-security fencing can also make a site more of a target for vandals and burglars. To minimize this risk consider specifying timber fencing and traffic barriers to secure car parks, providing both security and a welcoming atmosphere for shoppers. Taking an integrated approach Combine secure perimeter fencing with effective lighting in places with shaded areas and at doors, gates, and shop windows, alongside Perimeter Intrusion Detection Systems (PIDS), and strategically placed CCTV. These measures will hinder unauthorized entry and escape, increasing the likelihood of detection and apprehension. Prioritising employee wellbeing Installing robust security fencing, complemented by CCTV, good lighting, and guarding, creates a safe environment Installing robust security fencing, complemented by CCTV, good lighting, and guarding, creates a safe environment for employees. This not only safeguards their well-being but also provides peace of mind that they are protected effectively in the case of a burglary or crime. When selecting security products for retail sites, it is advisable to opt for items that have undergone rigorous testing and carry relevant certifications for their security level. Each component should meet industry-specific standards for its intended purpose and originate from manufacturers accredited under ISO 9001:2015. This ensures a high standard of quality and reliability in safeguarding the premises. High-quality security fencing As the cost-of-living crisis continues, crime rates increase, and the festive season approaches, the time to act and implement on-site security is now. By investing in comprehensive security measures, retailers can protect their assets, employees, and customers, ensuring a safer and more secure shopping environment for all. High-quality security fencing is also a sound investment, that requires little or no maintenance once installed. The best fencing solutions are extremely weather-resistant, and won’t suffer from rust or corrosion. With all sectors preparing to ride the rapids of recession in the coming year, improving on-site security while selecting cost-effective measures, is one surefire way to protect your people, your property, and your profits from harm.
Global transportation networks are becoming increasingly interconnected, with digital systems playing a crucial role in ensuring the smooth operation of ports and supply chains. However, this reliance on technology can also create vulnerabilities, as demonstrated by the recent ransomware attack on Nagoya Port. As Japan's busiest shipping hub, the port's operations were brought to a standstill for two days, highlighting the potential for significant disruption to national economies and supply chains. Transportation sector The attack began with the port's legacy computer system, which handles shipping containers, being knocked offline. This forced the port to halt the handling of shipping containers that arrived at the terminal, effectively disrupting the flow of goods. The incident was a stark reminder of the risks associated with the convergence of information technology (IT) and operational technology (OT) in ports and other critical infrastructures. This is not an isolated incident, but part of a broader trend of escalating cyber threats targeting critical infrastructure. The transportation sector must respond by bolstering its defenses, enhancing its cyber resilience, and proactively countering these threats. The safety and efficiency of our transportation infrastructure, and by extension our global economy, depend on it. Rising threat to port security and supply chains XIoT, from sensors on shipping containers to automatic cranes, are vital to trendy port functions OT, once isolated from networked systems, is now increasingly interconnected. This integration has expanded the attack surface for threat actors. A single breach in a port's OT systems can cause significant disruption, halting the movement of containers and impacting the flow of goods. This is not a hypothetical scenario, but a reality that has been demonstrated in recent cyberattacks on major ports. Adding another layer of complexity is the extended Internet of Things (XIoT), an umbrella term for all cyber-physical systems. XIoT devices, from sensors on shipping containers to automated cranes, are now integral to modern port operations. These devices are delivering safer, more efficient automated vehicles, facilitating geo-fencing for improved logistics, and providing vehicle health data for predictive maintenance. XIoT ecosystem However, the XIoT ecosystem also presents new cybersecurity risks. Each connected device is a potential entry point for cybercriminals, and the interconnected nature of these devices means that an attack on one, which can move laterally and can have a ripple effect throughout the system. The threat landscape is evolving, with cybercriminals becoming more sophisticated and their attacks more damaging with a business continuity focus. The growing interconnectivity between OT and XIoT in port operations and supply chains is also presenting these threat actors with a greater attack surface. Many older OT systems were never designed to be connected in this way and are unlikely to be equipped to deal with modern cyber threats. Furthermore, the increasing digitization of ports and supply chains has led to a surge in the volume of data being generated and processed. This data, if not properly secured, can be a goldmine for cybercriminals. The potential for data breaches adds another dimension to the cybersecurity challenges facing the transportation sector. Role of Cyber Resilience in Protecting Service Availability Cyber resilience refers to organization's ability to prepare for, respond to, and recover from threats As the threats to port security and supply chains become increasingly complex, the concept of cyber resilience takes on a new level of importance. Cyber resilience refers to an organization's ability to prepare for, respond to, and recover from cyber threats. It goes beyond traditional cybersecurity measures, focusing not just on preventing attacks, but also on minimizing the impact of attacks that do occur and ensuring a quick recovery. In the context of port operations and supply chains, cyber resilience is crucial. The interconnected nature of these systems means that a cyberattack can have far-reaching effects, disrupting operations not just at the targeted port, but also at other ports and throughout the supply chain. A resilient system is one that can withstand such an attack and quickly restore normal operations. Port operations and supply chains The growing reliance on OT and the XIoT in port operations and supply chains presents unique challenges for cyber resilience. OT systems control physical processes and are often critical to safety and service availability. A breach in an OT system can have immediate and potentially catastrophic physical consequences. Similarly, XIoT devices are often embedded in critical infrastructure and can be difficult to patch or update, making them vulnerable to attacks. Building cyber resilience in these systems requires a multi-faceted approach. It involves implementing robust security measures, such as strong access controls and network segmentation, to prevent attacks. It also involves continuous monitoring and detection to identify and respond to threats as they occur. But perhaps most importantly, it involves planning and preparation for the inevitable breaches that will occur, ensuring that when they do, the impact is minimized, and normal operations can be quickly restored. Building resilience across port security and supply chains In the face of cyber threats, the transport sector must adopt a complete method of cybersecurity In the face of escalating cyber threats, the transportation sector must adopt a comprehensive approach to cybersecurity. This involves not just implementing robust security measures, but also fostering a culture of cybersecurity awareness and compliance throughout the organization. A key component of a comprehensive cybersecurity strategy is strong access controls. This involves ensuring that only authorized individuals have access to sensitive data and systems. It also involves implementing multi-factor authentication and regularly reviewing and updating access permissions. Strong access controls can prevent unauthorized access to systems and data, reducing the risk of both internal and external threats. Network segmentation Network segmentation is another crucial measure. By dividing a network into separate segments, organizations can limit the spread of a cyberattack within their network. This can prevent an attack on one part of the network from affecting the entire system. Network segmentation also makes it easier to monitor and control the flow of data within the network, further enhancing security. Regular vulnerability assessments and patch management are also essential. Vulnerability assessments involve identifying and evaluating potential security weaknesses in the system, while patch management involves regularly updating and patching software to fix these vulnerabilities. These measures can help organizations stay ahead of cybercriminals and reduce the risk of exploitation. EU’s NIS2 Directive EU’s NIS2 Directive came into effect, and member states have until October 2024 to put it into law The transportation sector must also be prepared for greater legislative responsibility in the near future. The EU’s NIS2 Directive recently came into effect, and member states have until October 2024 to put it into law. The Directive aims to increase the overall level of cyber preparedness by mandating capabilities such as Computer Security Incident Response Teams (CSIRTs). Transport is among the sectors labeled as essential by the bill, meaning it will face a high level of scrutiny. Getting to grips with the complexities of XIoT and OT integration will be essential for organizations to achieve compliance and avoid fines. Global transportation infrastructure Finally, organizations must prepare for the inevitable breaches that will occur. This involves developing an incident response plan that outlines the steps to be taken in the event of a breach. It also involves regularly testing and updating this plan to ensure its effectiveness. A well-prepared organization can respond quickly and effectively to a breach, minimizing its impact and ensuring a quick recovery. In conclusion, mastering transportation cybersecurity requires a comprehensive, proactive approach. It involves implementing robust technical measures, fostering a culture of cybersecurity awareness, and preparing for the inevitable breaches that will occur. By taking these steps, organizations can enhance their cyber resilience, protect their critical operations, and ensure the security of our global transportation infrastructure.
Physical security is essential for a modern production facility, users don’t want just anyone entering the building or accessing secure areas. But what about production machinery? Machine authentication is often a missing link in the security plan for manufacturers. Why machine authentication? Most manufacturers have made significant investments in physical access control (PAC) for production facilities. Few shops currently hand out physical keys to employees or leave the building unlocked during production hours. For all but the smallest shops, front-door access typically involves individual radio-frequency identification (RFID) badges that enable tracking of who is coming and going and at what times. Use of physical keys, password login It is simply assumed that anyone who has access to the factory floor has the knowledge, authority, and training But when it comes to production machinery, many manufacturers still rely on physical keys, password login on the human-machine interface (HMI), or a shared PIN to unlock machine access. In some shops, machines may not be secured at all, it is simply assumed that anyone who has access to the factory floor has the knowledge, authority, and training to use the machines responsibly. However, this is not necessarily a good assumption, especially in a larger manufacturing plant where many people can access the production floor. Valuable and sensitive equipment CNC machines, robotic welders, process equipment, and other production machinery can cost anywhere from $5,000 to half a million or more, depending on their size and function. They also have significant safety risks for untrained users and may hold valuable and sensitive IP (such as customer design specs or batch recipes). User authentication Authenticating users at the machine level closes an important security loophole and makes plants safer and more productive. Machine authentication prevents untrained or unauthorized users from accessing production machinery. The right authentication system also allows access levels to be tailored for different users based on training credentials, job roles, or even projects. Machine authentication benefits A strong machine authentication solution provides several benefits for manufacturers: Minimizes unplanned downtime and expensive damage to machines caused by untrained operators. Enables tracking of production outcomes by machine operator for better quality control and troubleshooting. Protects company and client IP held on the machine by preventing unauthorized access to machine controls and memory. Enhances plant safety and compliance by limiting machine access to operators with the appropriate credentials. Reduces the risk of deliberate sabotage by unauthorized operators, including damage to machines and production facilities and data theft or corruption. Mark Merino, the Director of the Digital Factory Group for Polaris Automation, explains, “Machine authentication allows us to identify which people are logged into different pieces of equipment and make sure they are trained appropriately for the machine and have the right clearances for the data they are trying to access.” Choosing the right machine authentication solution Access control for production machinery can be accomplished by various means, including password and PIN systems, physical keys or fobs, RFID badges, or smartphone-based mobile credentialing systems. The best machine authentication system will: Be highly reliable and secure to protect the machine from unauthorized access. Enable identification of individual operators and tracking of who has used the machines, at what times, and for what projects. Allow access levels to be differentiated by the user. Be easy to implement and administer. Discourage sharing or cloning of credentials. RFID readers An RFID reader can be easily connected to or integrated with the HMI for the machine In most manufacturing environments, the simplest solution for machine authentication is the RFID badge employees already carry for building entry. An RFID reader can be easily connected to or integrated with the HMI for the machine. All users must do to authenticate themselves is swipe their badge over the reader to unlock machine controls. RFID benefits RFID provides multiple benefits for end users, IT, and managers: It leverages technology already widely used, so users do not have to carry a separate key or fob to access machine controls. It is more secure and easier to manage than a password system, as passwords are frequently forgotten, shared, or hacked. Unlike shared PINs, physical keys, or fobs, user authentication via an ID badge enables accurate identification of who is logging into the machine. Users are much less likely to share their picture ID badge (which is often also linked to HR functions such as time and attendance) than a machine password, PIN, or key. If an ID badge is lost or stolen, or an employee leaves the company, IT can easily disable access to the card. RFID credentials are very difficult to hack or clone. Transmission between the reader and card can be encrypted for added security. Unlike biometric options, RFID is highly reliable even in hot, dirty, or humid environments and does not require workers to remove gloves, safety goggles, or masks. Getting started with machine authentication Machine authentication starts with selecting the right RFID reader. A universal RFID reader supports easy implementation, integration with other building systems, and scaling. A universal reader also provides flexibility for the future in case companies want to change transponder technologies or allow for user authentication using mobile credentials on a smartphone. IIoT model User authentication must be designed within the context of the wider security ecosystem of the plant To ensure the security of production machinery, user authentication must be designed within the context of the wider security ecosystem of the plant. Modern production machines are increasingly networked and connected in an “Industrial Internet of Things” (IIoT) model. That means machines are not only vulnerable themselves but are also endpoints in the broader IT landscape of the plant. Machine authentication systems must incorporate best practices for endpoint security, such as those outlined by ISO (International Organization for Standardization), NIST (National Institute of Standards and Technology), and other industry organizations. Best practices: The reader installation should be tamper-proofed to prevent physical disruption of the authentication system. Use an encryption standard suitable for the security level of the application. Encryption prevents data interception or card cloning. If higher security is desired, RFID can be implemented as part of a multi-factor authentication system along with biometrics and/or a password or PIN. The authentication system should support different access levels for different users or classes of users. A role-based permission system allows for different levels of access for line operators, supervisors, IT, and maintenance, for example. For maximum safety and security, individual users should only have the minimum access required to do their jobs. With secure machine authentication, manufacturers can protect people, production equipment, and IP, while enabling smooth operations. It all starts with an authentication system that supports reliable and secure operator identification at the machine level.
Security beat
Companies at GSX 2023 emphasized new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the security market. Today, more than half of the company’s lineup supports AI at the edge so the customer has a wide choice of form factors when seeking to leverage the feature set. AI processing relay, extended warranty i-PRO is increasing their warranty period from 5 to 7 years, which could be a lifetime warranty in some cases I-PRO also has an “AI processing relay” device that accepts non-AI video streams and applies edge analytics. AI has progressed from a high-end technology to a feature available in a variety of cameras at different price points. i-PRO is also increasing its warranty period from 5 to 7 years, which could be a lifetime warranty in some cases depending on a customer’s refresh schedule and lifecycle management. Active Guard, MonitorCast The company’s video management system (Video Insight) is continuing to build new features including “Active Guard,” an integrated metadata sorter. Their access control platform, MonitorCast, is a Mercury-based solution that is tightly integrated with Video Insight. Their embedded recorders now have PoE built in. “We can move at a faster pace to fill out our product line since leaving Panasonic,” says Adam Lowenstein, Director of Product Management. “We can focus our business on adapting to the market.” Emphasis on retail and other verticals Shoplifting is a timely issue, and retail is a vertical market that got a lot of attention at GSX 2023. “We see a lot of retailers who are primarily interested in protecting employee safety, but also assets,” says Brandon Davito, Verkada’s SVP of Product and Operations. “Shrinkage is a CEO-level priority.” “Retailers are getting more engaged with security posture, instead of letting perpetrators walk,” Davito adds. Intrusion detection Verkada has an intrusion product that will notify a central station if there is an alarm On the alarm side, Verkada has an intrusion product that will notify a central station if there is an alarm, and operators can review videos to confirm the alarm. Other capabilities seeking to discourage trespassers include sirens, strobes, and “talkdown” capabilities. International expansion Verkada continues to expand internationally with 16 offices in all, including Sydney, Tokyo, and London. The core value proposition is to enable customers to manage their onsite infrastructure more simply, including new elements such as PTZ cameras, intercoms, and visitor management. Verkada emphasizes ease of use, including a mobile application to allow access to be managed across the user base. Forging partnerships “We are committed to the channel and industry, and we continue to build relationships and expand our reach,” says Davito. Among the industry relationships is a new partnership with Convergint, which was hinted at during the show and announced later the same day. They are also expanding their partnerships with Schlage, Allegion, and ASSA ABLOY. Working with other verticals They offer new features for K -12 schools, and a new alarm platform is easier to deploy and manage Verkada has also found success across multiple other verticals, notably healthcare, where they integrate with an electronic medical records system. They offer new features for K-12 schools, and a new alarm platform is easier to deploy and manage. They are integrating wireless locks to secure interior doors in schools, looking to secure the perimeter, and installing guest management systems. Transitioning the Mid-Market to the Cloud Salient is squarely focused on the “mid-market,” a large swath of systems somewhere between small businesses and enterprise-level systems. Pure cloud systems are not as attractive to this market, which has a built-out infrastructure of on-premise systems. Adding a camera to an existing system is easier and less expensive than tying it to the cloud. Benefits of cloud It’s a market that may not be ready for pure cloud, but there are benefits to be realized from adding a cloud element to existing systems. “We are continuing to augment our premise-based solutions with added cloud capabilities and flexibility,” says Sanjay Challa, Salient’s Chief Product Officer. The feedback Salient hears from their customers is “I want to own my data.” The hybrid cloud approach offers the right mix of control, flexibility, and unit economics. Cloud add-on capabilities We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive" Cloud add-on capabilities include bringing more intelligence about system operation to the user via the cloud. Over time, Salient expects to sell more cloud-centric offerings based on feedback from integrators and customers. “We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive over time,” says Challa. Vaidio AI technology Salient seeks to be a transition pioneer to help customers realize the path to the cloud. Their approach is “crawl, walk, run,” and helping customers make the transition at each stage. Salient has added AI to its product offering, incorporating Vaidio AI technology from IronYun into a powerful suite and broad array of on-premise analytics, which are gaining traction. The seamless approach makes it easy for customers to embrace AI analytics, although Salient remains broadly committed to open systems. Addressing ‘Soft’ Features for Integrators AMAG is in the process of enhancing its product line with the next generation of access control panels. However, “product” is just part of the new developments at AMAG. In addition to “hard” features (such as products), the company is looking to improve its “soft” features, too; that is, how they work with the integrator channel. Integrator channel Rebuilding a process to make your organization more efficient, is relatively easy; it just takes a lot of persistence" “We have the depth of our legacy customer base we can learn from, we just need to close the feedback loop quicker,” says Kyle Gordon, AMAG’s Executive Vice President of Global Sales, Marketing, and commercial Excellence, who acknowledges the value of reinstating face-to-face meetings after COVID. “We are laser-focused on nurturing our integrator channel,” he says. “Developing new features takes time, but rebuilding a process to make your organization more efficient, that’s relatively easy; it just takes a lot of persistence,” says Gordon. More cohesive internal communication is another useful tool, he says. Disrupting the cloud based on price Wasabi is working to make cloud applications less expensive by offering a “disruptive” price on cloud storage, $6.99 per terabyte per month (80% less than hyperscalers). Contending “hyperscalers” like AWS are charging too much for cloud storage, Wasabi is using its own intellectual property and server equipment co-located in data centers around the world. Wasabi sells “hot cloud storage,” which refers to the fact that they only have one tier of storage and data is always accessible. In contrast, a company such as AWS might charge an “egress fee” for access to data stored in a “colder” tier. Cloud storage “We saw that several video surveillance companies had not yet adopted cloud storage, and we saw an opportunity to make it easy to use,” said Drew Schlussel, Wasabi’s Senior Director of Product Marketing. “We just install a little bit of software that allows them to store data in the cloud and bring it back from the cloud.” Performance, protection (cybersecurity), and price Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies such as Genetec and Milestone. Emphasizing performance, protection (cybersecurity), and price, their data centers are certified to SOC 2 and ISO 27001 standards. Faster throughput for weapons detection Xtract One is a young company focusing on weapons detection in a time of accelerated concern about gun issues post-COVID. Founded in Canada and based on technology developed at McMaster University, Xtract One has found a niche in providing weapons detection at stadiums and arenas. These customers already have budgets, and it is easy to shift the money to a newer, faster technology. Madison Square Garden in New York City is among its customers. Cost savings solution Xtract One can increase throughput to 30 to 50 people per entrance per minute (compared to 5 to 6 people per minute when using metal detectors). The solution doesn’t require anyone to empty their pockets and the system alarms on items beyond guns and knives. Using Xtract One allows customers to reduce the number of screening lanes and security staff, providing additional cost savings, all while getting fans through the screening process in half the time. Purpose-built sensors The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties In addition to stadiums and arenas, Xtract One, formerly Patriot One, is also getting “inbound” interest from schools, hospitals, manufacturers, and other verticals that makeup 50% of their business. “We’re on a rocket ride, mainly because the weapons issues are not going away,” says Peter Evans, CEO and Director at Xtract One. The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties, all correlated by an AI engine. Providing early warning of violence ZeroEyes is another company focused on weapons detection. Their AI gun detection system works with video images to identify if someone is “brandishing” (carrying) a weapon. In other words, the system does not detect concealed weapons. Identifying someone carrying a weapon provides early warning of a possible violent act. Increased response with AI-enables images Images are identified by AI and sent to a monitoring center where a human confirms the image before contacting first responders. Knowing the location of a shooter enables staff to lock entry points, move people to safety, and direct first responders. The company was founded to leverage existing camera views to stop mass shootings and gun violence by reducing response times.
When it comes to security cameras, the end user always wants more—more resolution, more artificial intelligence (AI), and more sensors. However, the cameras themselves do not change much from generation to generation; that is, they have the same power budgets, form factors and price. To achieve “more,” the systems-on-chips (SoCs) inside the video cameras must pack more features and integrate systems that would have been separate components in the past. For an update on the latest capabilities of SoCs inside video cameras, we turned to Jérôme Gigot, Senior Director of Marketing for AIoT at Ambarella, a manufacturer of SOCs. AIoT refers to the artificial intelligence of things, the combination of AI and IoT. Author's quote “The AI performance on today’s cameras matches what was typically done on a server just a generation ago,” says Gigot. “And, doing AI on-camera provides the threefold benefits of being able to run algorithms on a higher-resolution input before the video is encoded and transferred to a server, with a faster response time, and with complete privacy.” Added features of the new SOC Ambarella expects the first cameras with the SoC to emerge on the market during early part of 2024 Ambarella’s latest System on Chip (SOC) is the CV72S, which provides 6× the AI performance of the previous generation and supports the newer transformer neural networks. Even with its extra features, the CV72S maintains the same power envelope as the previous-generation SoCs. The CV72S is now available, sampling is underway by camera manufacturers, and Ambarella expects the first cameras with the SoC to emerge on the market during the early part of 2024. Examples of the added features of the new SOC include image processing, video encoders, AI engines, de-warpers for fisheye lenses, general compute cores, along with functions such as processing multiple imagers on a single SoC, fusion among different types of sensors, and the list goes on. This article will summarize new AI capabilities based on information provided by Ambarella. AI inside the cameras Gigot says AI is by far the most in-demand feature of new security camera SoCs. Customers want to run the latest neural network architectures; run more of them in parallel to achieve more functions (e.g., identifying pedestrians while simultaneously flagging suspicious behavior); run them at higher resolutions in order to pick out objects that are farther away from the camera. And they want to do it all faster. Most AI tasks can be split between object detection, object recognition, segmentation and higher-level “scene understanding” types of functions, he says. The latest AI engines support transformer network architectures (versus currently used convolutional neural networks). With enough AI horsepower, all objects in a scene can be uniquely identified and classified with a set of attributes, tracked across time and space, and fed into higher-level AI algorithms that can detect and flag anomalies. However, everything depends on which scene is within the camera’s field of view. “It might be an easy task for a camera in an office corridor to track a person passing by every couple of minutes; while a ceiling camera in an airport might be looking at thousands of people, all constantly moving in different directions and carrying a wide variety of bags,” Gigot says. Changing the configuration of video systems Low-level AI number crunching would typically be done on camera (at the source of the data) Even with more computing capability inside the camera, central video servers still have their place in the overall AI deployment, as they can more easily aggregate and understand information across multiple cameras. Additionally, low-level AI number crunching would typically be done on camera (at the source of the data). However, the increasing performance capabilities of transformer neural network AI inside the camera will reduce the need for a central video server over time. Even so, a server could still be used for higher-level decisions and to provide a representation of the world; along with a user interface for the user to make sense of all the data. Overall, AI-enabled security cameras with transformer network-based functionality will greatly reduce the use of central servers in security systems. This trend will contribute to a reduction in the greenhouse gases produced by data centers. These server farms consume a lot of energy, due to their power-hungry GPU and CPU chips, and those server processors also need to be cooled using air conditioning that emits additional greenhouse gases. New capabilities of transformer neural networks New kinds of AI architectures are being deployed inside cameras. Newer SoCs can accommodate the latest transformer neural networks (NNs), which now outperform currently used convolutional NNs for many vision tasks. Transformer neural networks require more AI processing power to run, compared to most convolutional NNs. Transformers are great for natural language processing (NLP) as they have mechanisms to “make sense” of a seemingly random arrangement of words. Those same properties, when applied to video, make transformers very efficient at understanding the world in 3D. Transformer NNs require more AI processing power to run, compared to most convolutional NNs For example, imagine a multi-imager camera where an object needs to be tracked from one camera to the next. Transformer networks are also great at focusing their attention on specific parts of the scene—just as some words are more important than others in a sentence, some parts of a scene might be more significant from a security perspective. “I believe that we are currently just scratching the surface of what can be done with transformer networks in video security applications,” says Gigot. The first use cases are mainly for object detection and recognition. However, research in neural networks is focusing on these new transformer architectures and their applications. Expanded use cases for multi-image and fisheye cameras For multi-image cameras, again, the strategy is “less is more.” For example, if you need to build a multi-imager with four 4K sensors, then, in essence, you need to have four cameras in one. That means you need four imaging pipelines, four encoders, four AI engines, and four sets of CPUs to run the higher-level software and streaming. Of course, for cost, size, and power reasons, it would be extremely inefficient to have four SoCs to do all this processing. Therefore, the latest SoCs for security need to integrate four times the performance of the last generation’s single-imager 4K cameras, in order to process four sensors on a single SoC with all the associated AI algorithms. And they need to do this within a reasonable size and power budget. The challenge is very similar for fisheye cameras, where the SoC needs to be able to accept very high-resolution sensors (i.e., 12MP, 16MP, and higher), in order to be able to maintain high resolution after de-warping. Additionally, that same SoC must create all the virtual views needed to make one fisheye camera look like multiple physical cameras, and it has to do all of this while running the AI algorithms on every one of those virtual streams at high resolution. The power of ‘sensor fusion’ Sensor fusion is the ability to process multiple sensor types at the same time and correlate all that information Sensor fusion is the ability to process multiple sensor types at the same time (e.g., visual, radar, thermal, and time of flight) and correlate all that information. Performing sensor fusion provides an understanding of the world that is greater than the information that could be obtained from any one sensor type in isolation. In terms of chip design, this means that SoCs must be able to interface with, and natively process, inputs from multiple sensor types. Additionally, they must have the AI and CPU performance required to do either object-level fusion (i.e., matching the different objects identified through the different sensors), or even deep-level fusion. This deep fusion takes the raw data from each sensor and runs AI on that unprocessed data. The result is machine-level insights that are richer than those provided by systems that must first go through an intermediate object representation. In other words, deep fusion eliminates the information loss that comes from preprocessing each individual sensor’s data before fusing it with the data from other sensors, which is what happens in object-level fusion. Better image quality AI can be trained to dramatically improve the quality of images captured by camera sensors in low-light conditions, as well as high dynamic range (HDR) scenes with widely contrasting dark and light areas. Typical image sensors are very noisy at night, and AI algorithms can be trained to perform excellently at removing this noise to provide a clear color picture—even down to 0.1 lux or below. This is called neural network-based image signal processing, or AISP for short. AI can be trained to perform all these functions with much better results than traditional video methods Achieving high image quality under difficult lighting conditions is always a balance among removing noise, not introducing excessive motion blur, and recovering colors. AI can be trained to perform all these functions with much better results than traditional video processing methods can achieve. A key point for video security is that these types of AI algorithms do not “create” data, they just remove noise and clean up the signal. This process allows AI to provide clearer video, even in challenging lighting conditions. The results are better footage for the humans monitoring video security systems, as well as better input for the AI algorithms analyzing those systems, particularly at night and under high dynamic range conditions. A typical example would be a camera that needs to switch to night mode (black and white) when the environmental light falls below a certain lux level. By applying these specially trained AI algorithms, that same camera would be able to stay in color mode and at full frame rate--even at night. This has many advantages, including the ability to see much farther than a typical external illuminator would normally allow, and reduced power consumption. ‘Straight to cloud’ architecture For the cameras themselves, going to the cloud or to a video management system (VMS) might seem like it doesn’t matter, as this is all just streaming video. However, the reality is more complex; especially for cameras going directly to the cloud. When cameras stream to the cloud, there is usually a mix of local, on-camera storage and streaming, in order to save on bandwidth and cloud storage costs. To accomplish this hybrid approach, multiple video-encoding qualities/resolutions are being produced and sent to different places at the same time; and the camera’s AI algorithms are constantly running to optimize bitrates and orchestrate those different video streams. The ability to support all these different streams, in parallel, and to encode them at the lowest bitrate possible, is usually guided by AI algorithms that are constantly analyzing the video feeds. These are just some of the key components needed to accommodate this “straight to cloud” architecture. Keeping cybersecurity top-of-mind Ambarella’s SoCs always implement the latest security mechanisms, both hardware and software Ambarella’s SoCs always implement the latest security mechanisms, both in hardware and software. They accomplish this through a mix of well-known security features, such as ARM trust zones and encryption algorithms, and also by adding another layer of proprietary mechanisms with things like dynamic random access memory (DRAM) scrambling and key management policies. “We take these measures because cybersecurity is of utmost importance when you design an SoC targeted to go into millions of security cameras across the globe,” says Gigot. ‘Eyes of the world’ – and more brains Cameras are “the eyes of the world,” and visual sensors provide the largest portion of that information, by far, compared to other types of sensors. With AI, most security cameras now have a brain behind those eyes. As such, security cameras have the ability to morph from just a reactive and security-focused apparatus to a global sensing infrastructure that can do everything from regulating the AC in offices based on occupancy, to detecting forest fires before anyone sees them, to following weather and world events. AI is the essential ingredient for the innovation that is bringing all those new applications to life, and hopefully leading to a safer and better world.
Large-scale events, including both corporate and sporting events, are coming back strongly in the aftermath of the pandemic. With the increase in activity comes more demand for oversized credentials preferred by many event planners and end users. Pent-up demand due to the pandemic has caused a tremendous uptick in the entire ID card industry in 2022. The return of large-scale events and in-person trade shows will extend the higher demand for cards well into 2023 and beyond, says Andrew Schonzeit, President of Idesco, a provider of ID card solutions. Supply chain concerns Supply chain concerns will continue as companies seek to upgrade and purchase new ID printers and badges An impact of the pandemic was a shortage of supplies related to the ID card industry, says Schonzeit. Like other industries, several leading ID card and printer manufacturers had supply chain issues, and some deliveries were delayed at times for more than six months. Supply chain concerns will continue into 2023 as more companies return to the workplace and others seek to upgrade their current systems and purchase new ID printers and badges. Persistent price increase concerns “The shortage created hardships for end users and often resulted in them purchasing any solution that was readily available even if it was not the preferred one,” says Schonzeit. Another issue during the pandemic was persistent price increases, due both to inflationary pressures and a shortage of products. The industry was used to stable prices with infrequent increases, but the pandemic changed this quickly. Some companies also decided to upgrade their entire system as employees returning to the office increased demand. Oversized credentials advantages Among the advantages of oversized credentials is the ability to print more information on the card, says Schonzeit. For example, a larger credential allows event organizers to preprint the corporate agenda on the back of the card to increase efficiency. In addition, companies can enhance their brand presence by distributing a nice thick plastic badge to attendees. Two categories Standard credit card size These are generally CR100 size, which is around 40% larger than the standard credit card Oversized badges fall into two main categories. One category is for cards that are larger than the standard credit card size (CR80), but smaller than event badges. These are generally CR100 size, which is around 40% larger than the standard credit card. They are generally used by law enforcement or healthcare institutions. It is easier to see an oversized badge more clearly from a distance than a regular-sized badge. Oversized ID badges The other category of oversized ID badges is used for events, these badges are typically 3.5” by 5.5” and are usually worn around the neck. These events include categories such as sporting events, corporate events, music festivals, and trade shows. The badges are generally used only for the duration of the event and are often kept as souvenirs. Anticipating the needs “My advice for event planners is to manage your expectations about badges as it is very hard to order extra badges at the last minute,” says Schonzeit. “It is important to plan well in advance and anticipate your needs upfront to help avoid a shortage.” Idesco often gets requests from customers to include some type of technology on the credentials. The most common technologies are proximity cards, NFC, and/or UHF. “It is a much ‘cleaner’ and safer solution if the chip can be embedded within the credential as opposed to putting a sticker on the outside of the credential,” says Schonzeit. Additional technologies in credentials Customers wanting technology in their credentials should allow additional lead time Generally, these additional technologies are used for gaining entry to a location (access control), or they can be used for gathering valuable information regarding an event, including attendance at seminars, crowd flow, vending, and food services information, among others. Supply chain issues have led to less availability of many of the most common chips, which can impact delivery times. Customers wanting technology in their credentials should allow additional lead time, says Schonzeit. Applications In addition to corporate events, sporting events, and trade shows, other markets can also benefit from oversized ID badges. Industries include healthcare, government, and law enforcement. Oversized badges are becoming more popular in hospitals, for example, where color coding can make it easy to identify doctors, nurses, and hospital personnel from a distance, even in congested hospital spaces. ID card necessity Could there be a negative impact on the ID card industry if more companies allow employees to work from home? It’s always a possibility, says Schonzeit. “However, with many hybrid options out there, most employees are required to come to the office either one or two days a week,” he says. “Employees will still need a way to access their workplace for meetings, conferences, etc., and will require an ID card to do so.” Mobile vs. physical credentials The growing popularity of mobile credentials has created some concerns in the ID card marketplace The growing popularity of mobile credentials has created some concerns in the ID card marketplace about the continuing need for a physical credential. So far it has not been an issue. “[Mobile credentials] have not had any type of meaningful effect on the physical ID card market,” says Schonzeit. Relying on smartphones “Sometimes these disruptive technologies can linger in the background for some time and then suddenly have a massive effect on the market. This is something to be concerned about, but I don’t think there is an imminent threat.” A big issue with using only mobile credentials is the need for a backup plan rather than relying only on a smartphone to enter a facility. Also, for mobile credentials to work, specialized readers are required, which requires a large investment. “In my opinion, ID badges are here to stay for the long haul,” says Schonzeit.
Case studies
Set in 33 hectares of woodland on the edge of Dartmoor National Park, the zoo is home to an impressive variety of exotic and native animals, including Amur tigers, African lions, and Amur leopards. New patented master key system On-site challenges before the introduction of the new patented master key system. Before implementing the new master key system, the zoo faced the challenge of ensuring secure and efficient access control to sensitive areas, particularly enclosures with potentially dangerous animals. The previous master key systems were outdated and did not provide the necessary security and flexibility required for the zoo's daily operations. Installation of EPS NP and its advantages The EVVA EPS NP system was installed in collaboration with local partner Sir Fix-a-Lock. This system offers robust patent protection, long-term key control and high reliability in demanding environments. A total of 192 Asec weatherproof padlocks were installed in a 6-level master key system. The flexibility of EPS NP enabled graduated key control across the entire site, including special levels for animal care. Advantages of the new patented key system for the zoo Thanks to the new master key system, the zoo has been able to implement a secure and practical solution that enables staff to work efficiently while maintaining strict access controls. The color-coded keys make it easy to quickly identify access authorisations, which is particularly advantageous in security-critical areas. The Asec weatherproof padlocks also offer high resistance to environmental influences, ensuring the longevity of the system. "EPS has revolutionized our access control and gives us the security and flexibility we need." The project at Dartmoor Zoo impressively demonstrates how EVVA's flexible master key systems can be adapted to specific requirements to ensure security, control and long-term protection.
With a capacity of 66,500 spectators, the MERKUR SPIEL-ARENA is the largest multi-purpose venue in Düsseldorf and home to the city’s main football team, Fortuna. Regular and constantly changing major events, both matches and concerts, present an ever-evolving security and access challenge. Stadium managers D.LIVE sought a secure, reliable replacement for their mechanical master key system; comprehensive, flexible security which would no longer create the problems and inconvenience of mechanical keys. Digital locking system Due to frequently changing event formats and service providers, keys were often lost, causing considerable administrative work and financial expense. Due to the large number and size of the areas to be secured, it became clear that only a digital locking system would combine the required performance features in a convenient solution. Another critical requirement was for robust devices which did not protrude from doors: football and music events can sometimes be a little rough. The technology installed needed to be tough and reliable enough to withstand the odd kick. Key requirements for the new system Finally, the solution would also need to simplify the management and rental of multiple private spaces inside the building, including the Promenade, Merkur Business Club, and boxes in the east wing. These offer additional space for a total of almost 7,000 people for meetings, press conferences or product presentations. One of the key requirements for the new system was, therefore, the ability to grant and revoke access authorizations individually, especially for external event organizers and operators. Innovative key-based digital access Based on these requirements and their experience with other local venues, D.LIVE chose the eCLIQ programmable-key locking solution, part of a suite of Digital Access Solutions from ASSA ABLOY, which scores highly on security, reliability and convenience. Their new eCLIQ key-operated digital access solution has approximately 2,500 wireless cylinders; around 1,150 programmable eCLIQ Connect keys have been issued. With this solution, every authorized keyholder carries their own eCLIQ key which can be programmed with tailored access authorizations. For added security, access rights can be individually revoked at any time and lost keys can be blocked. Convenient management of contractor access “One of the reasons we chose eCLIQ Connect keys was to enable us to grant or revoke authorizations to external organizers and operators via Bluetooth in a rapid and user-friendly way,” says Lukas Angenendt, VEFK & Project Manager Electrical Engineering, D.LIVE. Powerful, intuitive software makes it easy for stadium managers to issue temporary authorizations for contractors, cleaning staff, and external event service providers, which streamlines site maintenance and management. As an additional layer of security, their eCLIQ Connect keys have to be validated on site by entering a PIN code in the smartphone app. Digital security enhancements In addition to the digital security enhancements, eCLIQ’s high degree of flexibility was another big plus: eCLIQ is convenient to handle and program as, for example, the power supply and communication with each cylinder take place via the battery-powered key. There’s no need to visit every door or device to replace its battery. No wiring is required for the very low-maintenance cylinder, which is fitted flush to the door and thus offers no attack surface for vandalism. Cable-free installation was also simpler and quicker: only two weeks, when no events were taking place in the stadium, were available for the conversion of all doors.
World Trade Center (WTC) Amsterdam is home to more than 300 companies. The commitment of its security team to providing a safe working environment in WTC’s fixed and flexible offices goes without saying. However, building managers wanted more from their access solution. More than just an office space, WTC Amsterdam has complementary onsite facilities, including childcare, a gym, physiotherapy clinic, bar/café, dry cleaning service, and more. Modern digital solution Modern digital solutions would provide better oversight of movement around the building All its facilities must be cleaned and serviced regularly: they sought a more time-efficient way to manage the many contractors and suppliers who come and go every day. They also hoped a modern digital solution would provide better oversight of movement around the building, including usage data to improve maintenance scheduling. For convenience during installation and day-to-day management, they targeted a wire-free solution – for simpler, less disruptive switching of 1,000 doors from mechanical locks to digital access – and intuitive management, allowing for easy changing of individual access authorizations, even at the last minute. ASSA ABLOY’s smart key digital access system With all these criteria in mind, WTC Amsterdam managers decided on ASSA ABLOY’s smart key digital access system, eCLIQ. They upgraded doors from mechanical to digital access simply by swapping the existing cylinder for an eCLIQ device. Doors are unlocked by battery-powered user smart keys, with a typical battery lifespan of 10 years. “Providing these doors with wired access control would be a huge job and become costly. Instead, we opted for the eCLIQ solution,” explains Sander Borggreve, Facility Manager at WTC Amsterdam. Concrete improvements in operations Scheduling is further simplified by storing keys with a Traka key management system The ROI in terms of workflow benefits has been significant. “Granting temporary controlled access to third parties is very easy with the eCLIQ system. We can set access for a certain period of time, but we can also revoke it at any time,” says Sander. Scheduling is further simplified by storing keys with a Traka key management system. After removing a key from the cabinet, authorized team members enter it into the adjacent eCLIQ Wall Programming Device. In seconds, the key is issued with its fine-grained access rights – covering both door-by-door and time validity. eCLIQ system maintenance and operations With the eCLIQ system, WTC Amsterdam gained not only control but also insights into usage and user flows. This data now informs maintenance and operations, reducing the overall Total Cost of Ownership for the solution. “eCLIQ works very pleasantly in practice. My employees are very satisfied with how the keys work,” says Rutger Barendse of D&B The Facility Group, who provides security staff for WTC Amsterdam. “It is easy as pie!” adds Sander.
In 1899, the Texas Legislature authorized the formation of the Southwest Texas State Normal School, which opened in San Marcos four years later. At the time, the school’s mission was to prepare Texas public school teachers. Still, over the years, it has undergone several expansions and name changes to reflect its evolution into the major multi-purpose university Texas State has become. San Marcos campus From its humble beginnings located in a single building, Texas State’s original San Marcos campus has grown to cover a 485-acre campus home to 267 buildings and an additional 5,038 acres of recreational, instructional, farm, and ranch land. The university added a second campus in Round Rock, which has grown from 15 temporary buildings to a 101-acre campus with state-of-the-art facilities. Need for electronic key control Texas reviewed its policies and determined the necessity of implementing electronic key control Texas State’s student population has kept pace with its physical expansion, growing from 303 in 1903 to more than 35,546 in 2013. This marks the university's 16th consecutive year of enrollment growth. Anticipating continued physical and population growth, Texas reviewed its policies and determined the necessity of implementing electronic key control systems in sensitive areas. Given its size, as many as 85 of these systems could potentially be needed as part of this initiative. Challenges faced Texas State was faced with a particularly challenging growth-related issue in September 2013, as its freshman enrollment surged to more than 5,000. Like many universities, Texas State requires its freshmen to live on campus, which it sees as a tool for retention. That policy seems to be working, with approximately 80 percent of freshmen living on campus technically returning for the following semester. Student accommodation The university has pursued an aggressive construction campaign to accommodate the growing number of on-campus residents. Every two years, a new residence hall complex is built to house approximately 600 additional students, and a third new housing complex will be built this fall. In all, Texas State spent more than $190 million on new or renovated buildings, and more construction is planned for the foreseeable future. Key management policies The decision was made to update key management policies and practices to make them more efficient and effective With a large number of individuals requiring access to so many facilities, the university recognized that key management had the potential to become a high-risk issue and determined to become proactive in reducing that risk. Maintenance staff members would often reach for the key to a particular building they needed to access, only to find it was already checked out. They would then be forced to go through the time-consuming – and frustrating – process of determining who had the key last and tracking that person down to retrieve it. The decision was made to update key management policies and practices to make them more efficient and effective. Solution: KeyWatcher Touch To combat these problems and increase the security and effectiveness of its key management, Texas State charged its University Police Department and other stakeholders with undertaking an extensive review of the available options for key management systems on the market. This exhaustive process involved gathering research from printed materials and online research, having discussions with current customers of the various vendors, and listening to on-site presentations from the companies under consideration. After it reviewed key control cabinets and systems, Texas State chose KeyWatcher Touch from Morse Watchmans. Key features The main factors that led Texas State to choose KeyWatcher Touch systems were its robust feature set and competitive pricing. The school was also impressed by Morse Watchmans’ receptiveness to its specific needs – a six-digit user ID, for example – and ability to implement changes quickly. Access to support was also a main consideration, so Texas State appreciated that the system was produced domestically by a company with a 130-year history. Implemented at housing and services The department also operates a facilities service group consisting of 110 full-time employees and a staff Of the KeyWatcher systems to be implemented, the largest number were to be deployed for Texas State’s Department of Housing and Residential Life, which provides housing and services to approximately 7,000 residents in 25 facilities. The department also operates a facilities service group consisting of 110 full-time employees and a staff of 170 building paraprofessionals. Enterprise management "Because of the personnel changes the department experiences on an annual basis, the system’s enterprise management capability has been a valuable feature, as have its robust reporting capabilities," says Kyle Estes, Texas State’s Associate Director of Housing Facilities Services. "Having keys available in each residence hall for use by maintenance staff has made the department more efficient and reduced their liability; staff no longer need to carry multiple master keys across campus for different buildings." Employee accountability “Because the system automatically generates a log of who has each key, we’ve been able to establish much better employee accountability for key usage,” Estes says. “The ability to set a maximum duration that each key can be checked out and to receive alarms when that limit is exceeded has eliminated the problem of having keys unnecessarily checked out and as a result inaccessible when someone needs them.” Ease of use and centralized management The ease of use and centralized management features provided by the system’s network All KeyWatcher Touch systems deployed at Texas State are connected to the university’s network and interface with its card access and email systems. The ease of use and centralized management features provided by the system’s network capabilities have streamlined the once cumbersome process of generating reports and reviewing incidents. "One particular feature, the ability to access the system from anywhere, has made the system even more effective," Estes says. A test case As one of the earliest adopters of KeyWatcher Touch, the Housing and Facilities Department served as a test case of sorts for the system. Based on the success the department has had, combined with its continued rapid growth and expansion, Texas State University’s 85-system implementation is ongoing. As more systems are added, expansion will be a consideration moving forward, but Estes doesn’t anticipate that being a problem. Reliable system “We’ve found that expanding these systems is fairly easy and doesn’t involve time-consuming processes that could delay implementation of key management for particularly sensitive areas,” Estes says. “Overall, the system has been very reliable, and the support staff has been very responsive and regularly available to help resolve the very few minor issues we’ve encountered promptly.” The University of Texas expanded its KeyWatcher Touch systems in 2015, 2017, 2018, 2020, and 2021. Key watcher touch features Vibrant 7” touchscreen. Modular, customizable design. Easy-to-use interface. KeyFind – locate the key you need. Key reservations. KeyAnywhere – return keys to any system. Patented SmartKey system. Full scalability. True touch software New access control-style interface. Extensive and detailed reporting options. Flexible, email/SMS-capable notifications. Easy-to-read color reports (including PDFs). Schedule reports to email automatically. Automatically sync changes. Profiles – easily assign user access. “We’ve been especially happy with the KeyWatcher’s access and reporting capabilities, and the system’s reporting tools make reviewing events and issues incredibly simple,” said Kyle EstesAssociate Director of Housing for Facilities Services Texas State.
Opened to mark the 100th anniversary of Bauhaus’ founding, the Bauhaus Museum Dessau is a comprehensive public presentation of the Bauhaus Dessau Foundation collection. On show for the very first time, this valuable collection includes around 49,000 cataloged exhibits and is the second-largest Bauhaus collection in the world. Transparency and simplicity Located in the center of the city, the museum is a building within a building – a suspended concrete structure inside a glass shell. Its architecture is characterized by transparency and simplicity in both concept and aesthetics. The glass façade reflects the surroundings to different degrees or can be transparent, depending on lighting conditions. An intelligent digital key system It should fit unobtrusively within the building's sophisticated architectural concept Requirements for an intelligent digital key system in the museum were set out in advance. The chosen solution must enable the simplest possible management of access authorizations. It should also fit unobtrusively within the building's sophisticated architectural concept. eCLIQ programmable digital key As in the Bauhaus main building and master houses, the Bauhaus Foundation chose a proven system: ASSA ABLOY’s eCLIQ programmable digital key solution. “The building has an increasingly digital future,” says David Moser, SVP and Head of Digital Access Solutions at ASSA ABLOY Opening Solutions EMEIA. “Choosing a digital solution like eCLIQ, rather than mechanical access, can help organizations to work smarter and collaborate better.” Benefits of digital access: security, convenience, reliability An eCLIQ system can bring digital access to almost any opening, helping filter authorized entry “The electromechanical CLIQ master key system has already proven itself extremely well in the Bauhaus main building and the master houses in Dessau,” explains Uwe Becker, Managing Director of Becker Sicherheitstechnik GmbH, the museum’s security partner on the project. The eCLIQ system is a fully digital version of the CLIQ electromechanical key-operated solution. An eCLIQ system can bring digital access to almost any opening, helping filter authorized entry through doors and much more. Convenient and robust solution Robust, durable cylinders and padlocks with eCLIQ technology can protect lifts, server racks, furniture, gates, mailboxes, cabinets, and more with the same level of control as sensitive doors. Every key has an integrated chip, which makes it unique. As a result, keys may be programmed individually to meet specific needs and access permissions. For keyholders, it’s a convenient solution. Versatility and security benefits The versatility and security benefits of eCLIQ are demonstrated whenever a key is lost. Each key’s access authorizations can be removed individually by reprogramming the cylinders. For greater flexibility, eCLIQ also enables access authorizations to be issued on a time-limited basis, which simplifies the management of external service providers such as maintenance contractors and cleaners. “Digitalization helps all kinds of organizations to boost their site security and makes everyday access more convenient for everyone – employees, visitors, and contractors,” adds David Moser. Aesthetics and the switch to digital All eCLIQ keys and cylinders are compatible with the high demands that Bauhaus places on design All eCLIQ keys and cylinders are compatible with the high demands that Bauhaus places on design. They blend seamlessly with the varied installation situations of different doors and with the overall building concept in Dessau. A standard battery inside each key powers the eCLIQ cylinder and encrypts the data transfer between the lock, key, and system. With eCLIQ, there is no need to wire cylinders or doors, which leaves building designs intact. Digital transition “ASSA ABLOY’s innovative access solutions can help you digitalize and truly future-proof access at almost any kind of site or building,” says David Moser. “Our vast range of reliable, convenient solutions showcase the value of the digital transition and can be tailored to meet any organization’s needs or goals.”
Silverstein Properties, a pioneering real estate development, investment, and management firm, and its partners SwiftConnect, Allegion, and Kastle, announced they are live with resident keys in Apple Wallet for all apartment units at a multi-family housing location: Silverstein’s Silver Towers residential property at 606 West 42nd Street in New York City. Silverstein’s residential tenants now have an easy and secure way to add a resident key to Apple Wallet to access the apartment building and unlock their homes with a simple tap of an iPhone or Apple Watch—thus eliminating the need to use a traditional, physical key. Resident key in Apple Wallet The rollout of keys in Apple Wallet marks an important milestone for the U.S. real estate industry “We’re excited to make it easy for our residents to use their resident key in Apple Wallet to get into their buildings, homes, and common areas, which builds upon our previous offering to office tenants who use their employee badge in Apple Wallet to access offices and shared spaces including lounges, cafes, conference facilities, and yoga studios,” said Tal Kerret, President of Silverstein Properties. The rollout of keys in Apple Wallet marks an important milestone for the U.S. real estate industry, as property owners and employers reimagine the home and workplace experience for residents, office tenants, and employees. SwiftConnect’s success: Enhance security for residents “The Silver Towers project builds on SwiftConnect’s success in delivering seamless access via NFC wallets across the most iconic commercial real estate properties in New York and beyond,” said Matt Kopel, co-CEO and President of SwiftConnect. “We are excited to once again partner with Silverstein Properties and to extend our leadership into the multi-family housing market. Now, residents can easily access their personal spaces with their iPhone and Apple Watch, and property teams are able to enhance security for their residents—while also automating the process of managing keys and access.” Modern access-control solution SwiftConnect integrates with the Kastle Access Control platform; Schlage® mobile credentials To provide residential tenants with this experience, SwiftConnect integrates with the Kastle Access Control platform; Schlage® mobile credentials; and access control devices from Allegion™, as well as all other necessary business platforms and systems to create a unified digital network for hassle-free mobile access. “Kastle is thrilled to be a partner on the Silver Tower project, leveraging Kastle’s robust and proven access-control products to create a modern access-control solution that delivers an unparalleled experience both property owners and residents can trust,” said Haniel Lynn, CEO of Kastle. Schlage mobile-enabled wireless locks “We are excited to work with SwiftConnect and play an important role in Silver Tower's resident key in Apple Wallet multifamily housing deployment,” said Mark Casey, Vice President of National Electronic Sales of Allegion. “Resident Keys in Apple Wallet—alongside our Schlage mobile credentials and Schlage mobile-enabled wireless locks—not only enhances security and convenience for residents, but also exemplifies our commitment to driving the future of seamless access and smart apartment technology.” How seamless access works at Silver Towers Tenants can add their resident key to Apple Wallet after an initial set-up through Silverstein’s Inspire app, using SwiftConnect’s AccessCloud platform. Once added, tenants can hold their iPhone or Apple Watch near a door reader or smart lock for seamless access to the apartment building, their home, and shared fitness and amenity spaces. With Express Mode, tenants don’t need to wake or unlock their device to use their resident key—they can simply hold their device near a reader and go. If an iPhone needs to be charged, they can still use their device to access their apartment and amenity spaces with Power Reserve. Resident key in Apple Wallet takes full advantage of the privacy and security features already built into iPhone and Apple Watch. Data is encrypted and protected against tampering and theft, and Apple cannot see when and where a resident uses a home key in Wallet. Silverstein’s holistic customer experience program The new offering falls under Inspire, Silverstein’s holistic customer experience program that reshapes how, when, and where the company’s customers live and work. Inspire brings hospitality services, social and wellness programming, data-driven workplace technology, and a flexible workspace solution under one umbrella. Since its inception 67 years ago, Silverstein Properties has been recognized for driving innovative technology adoption to enhance tenant experience. The company has built a reputation for developing exceptional projects, enhancing local communities, providing outstanding services to customers and partners, and driving innovation within the industry.


Products


Round table discussion
There is safety in numbers, or so the expression goes. Generally speaking, several employees working together tend to be safer than a single employee working alone. Even so, some environments require that workers complete their jobs alone, thus presenting a unique combination of security vulnerabilities. The U.S. Occupational Safety and Health Administration (OSHA) defines a lone worker as “an employee working alone, such as in a confined space or isolated location.” We asked this week’s Expert Panel Roundtable: How can security technologies help to protect "lone workers?"
Headlines of violence in our schools are a reminder of the need to keep educational institutions safe. In fact, if there is a positive aspect to the constant bombardment of headlines, it is that it keeps our attention perpetually focused on how to improve school security. But what is the role of physical security systems? As the new school year begins, we asked this week’s Expert Panel Roundtable: Are schools safer because of physical security systems? Why or why not?
Faces captured by video cameras could be perceived as an invasion of privacy, as could images captured through residential windows or that involve private or proprietary information. Fortunately, modern video systems incorporate technological features that help avoid an inadvertent invasion of privacy, while preserving any data that may be needed by authorized persons. For the latest commentary, we turn to our Expert Panel Roundtable with this week’s question: What new features of video systems are helping to ensure privacy?
White papers

The Ultimate Guide To Mastering Key Control
Download
7 Proven Solutions For Law Enforcement Key Control And Asset Management
Download
Security Practices For Hotels
Download
Best Practices For Asset Management
Download
Understanding Key Control Systems And Best Practices
Download
What Are The Security Technology Needs Of The Hotel Sector?
Download