Physical Security Information Management (PSIM)
Alcatraz, the pioneer in facial biometric authentication for physical access, now announced the successful completion of its SOC 2 examination as of November 7, 2025. The independent audit was conducted by A-LIGN, the pioneering provider in cybersecurity compliance trusted by more than 4,000 global organizations. Biometric access with confidence “Trust in biometric systems depends on strong data stewardship,” said Tina D’Agostin, CEO of Alcatraz. “At Alcatraz, we work...
Datalogic, a pioneer in automatic data capture and process automation, will demonstrate how its integrated portfolio is empowering the intelligent store at NRF 2026, thanks to AI-driven integration. Visitors to Booth 6128 will discover how advanced scanning, mobile computing, RFID, and IoT solutions are driving measurable outcomes for retailers: better customer loyalty, more revenue, fewer errors, higher labor efficiency, accelerated in-store productivity, and the creation of seamless customer...
Deep Sentinel, the pioneer in AI-powered proactive video surveillance with real-time human intervention, now announced the launch of its Mobile Monitoring Trailer — a fully mobile, solar-powered security platform that delivers instant access to Deep Sentinel’s remote live guard monitoring anywhere, including places where power and permanent infrastructure are unavailable. Purpose-built for high-value outdoor environments, such as auto and parking lots, construction sites, industrial...
The contract was signed, live at the SPS in Nuremberg, Germany: CADENAS is now the newest member of the Eplan Partner Network. CADENAS Managing Director Terry Jonen and Eplan Managing Director Haluk Menderes signed the new technology partnership agreement on 26 November 2025. The stated goal of the cooperation is the expanded provision of technical device data via the Eplan Data Portal, which will be implemented using a direct interface between the Data Portal and the CADENAS platform 3Dfi...
AI is one of the fastest-growing technologies in the history of modern business, with the ability to revolutionize industries, optimize operations, and drive innovation, but it is also introducing security gaps, risks, and vulnerabilities. According to McKinsey, 78% of organizations are using AI in at least one business function, up from 55% two years ago. As a result, 73% of them are investing in AI-specific security tools, either with new or existing budgets, according to the 2025 Thales Data...
WatchGuard® Technologies now announced that its endpoint security solution delivered outstanding performance in the latest MITRE ATT&CK® Enterprise Round 7 (ER7) Evaluation. The results highlight WatchGuard’s ability to combine strong threat prevention with low-noise detection, giving Managed Service Providers (MSPs) a reliable and efficient way to deliver high-quality security services at scale. WatchGuard’s commitment In the Windows “Hermes” scenario, Wat...
News
Security-Net, Inc., a network of pioneering security system integrators, is pleased to welcome its newest member, Mala Grover, president and chief executive officer of Digitronics, based in Herndon, Va. With the addition of Grover, Security-Net strengthens its presence in the Mid-Atlantic region, including Washington, D.C., Maryland, Virginia, and West Virginia, while gaining a member with deep expertise in federal government security projects. Advanced electronic security systems Grover brings three decades of experience in the security industry, including more than 20 years pioneering Digitronics, a woman-owned small business specializing in design, installation, and support of advanced electronic security systems. The company is uniquely positioned in the federal sector, maintaining CSEIP certification and UL 2050 certification, which enable Digitronics to serve highly regulated government environments and protect critical national infrastructure. In recent years, the company has expanded its footprint into the commercial market, offering the same level of rigorous design and implementation expertise to private sector clients. Project management, bidding, and integration practices “Security-Net is truly an elite group of seasoned companies spread across the United States,” said Grover. “One of the biggest benefits is the network itself and having trusted partners across the country who I can reach out to for support on projects or team with to get them completed on time and within budget. It’s like having an extended arm that helps me deliver the best possible service to my customers.” Through her participation in Security-Net, Grover is eager to both contribute her federal sector expertise and learn from her peers’ extensive experience in project management, bidding, and integration practices. She believes the relationships she builds through Security-Net will help her business to continue to grow, innovate, and evolve. Security-Net’s collective capabilities With Digitronics joining Security-Net, the organization gains additional depth in federal government integration and expands its footprint in the important Washington, D.C. corridor, which is a region known for its complex and high-security installations. "Mala brings an exceptional level of professionalism and technical expertise to the group,” said Roy Stephenson, director of business development for Utah Yamas Controls, and a long-time Security-Net member. “Her company’s experience in the federal sector, along with its UL 2050 certification, adds a tremendous amount of value to Security-Net’s collective capabilities.” Prior roles of Grover Grover entered the security industry in 1995 after beginning her career in international business. What started as a single $450 project grew into a thriving company managing large-scale federal installations, including projects with the U.S. Department of Education. Today, Digitronics employs 23 people, including Grover’s son, who is helping expand the company’s commercial business. Security-Net currently has 19 members with an extensive geographical footprint to serve customers throughout the United States, Canada, and internationally. Together, members share best practices, including technical knowledge and training initiatives, and partner on customer projects that extend beyond a company’s geographic reach to ensure national account-level service.
The 19th Real Estate Development Summit Saudi Arabia – Luxury Edition successfully concluded after two days of high-level exchange, strategic collaboration, and global networking, bringing together more than 800 leaders, investors, and decision makers shaping the future of the Kingdom’s rapidly evolving built environment. Held under the theme “Together Towards Tomorrow,” the summit showcased the unprecedented transformation underway across Saudi Arabia, where the real estate and construction pipeline has surpassed $2 trillion, redefining global standards of development, hospitality, and innovation. A milestone moment for leadership In the welcome address, Ravi Kumar Chandran, Founder & Managing Director – GBB Venture, as the organiser, highlighted the launch of the summit’s first dedicated investment track, featuring over 200 global investment leaders, and announced a strategic partnership with VCM to ensure the event achieved net-zero emissions through carbon measurement, reduction, and offsetting, reinforcing Saudi Arabia’s leadership in sustainability. Developer leadership & regional growth In the opening session of the summit, on a fireside conversation lead by Lama Alhamawi, Head of Diplomacy & Foreign Affairs - Arab News, with the speaker Eng. Essam Ahmad Kalthoum, Chief Executive Officer – Asmou Development Company, reflected on 40 years of development experience, highlighting rapid growth and evolving demand for smart, compact, amenity-rich housing. He discussed major mixed-use and high-rise projects across the Kingdom and regional expansion into Cairo, Muscat, and Amman, emphasizing governance, ESG, and public listing as critical for credibility and long-term success. Localization & industrial expansion In a major industry announcement, Jalal Al Kurdi, Commercial Director - HH Shaker, unveiled the launch of Midea Shaker Company (MSA), a joint venture marking a transformational step in manufacturing localization. The project begins with a 20,000 sqm facility with capacity for 650,000 AC units annually, expanding to 85,000 sqm with components manufacturing including compressors and robotics. Supporting giga-projects like NEOM, Red Sea, and Qiddiya, the facility will generate employment, raise installation standards, and establish Saudi Arabia as a regional export hub for the GCC and Levant. Art as experience Osan Ghaddaf, Founder and Creative Director - Artevo Consulting, demonstrated how art transforms destinations into living cultural experiences, rather than decoration. With landmark projects across the region including The Red Sea, Diriyah Gate, Rosewood, and the Qatar National Museum, Artevo highlighted the power of storytelling and experiential installations in shaping distinctive luxury developments. Biotech innovation powering the cities of tomorrow Nicolás Otero, Business Development Manager - BIOO introduced breakthrough biotechnology capable of transforming green spaces into producers of electricity, water savings, cooling, and interactive experiences, through systems such as biopanels, bioswitch installations, and bioluminescent landscapes. With implementation readiness and ROI within 5 - 7 years, these innovations position Saudi Arabia at the forefront of biotech-powered cities. Redefining luxury through legacy and exclusivity Tetyana Kovalenko, Founder & Chairwoman - Elite Stone Srl. also contributed to this theme by exploring the pillars of luxury: Legacy, Worldwide recognition & branding, Uncompromising quality, Limited availability & exclusivity and High economic value with reference to her 2000 year-old quarry in Italy that incorporates all the true elements of luxury in their products. Carbon markets driving Saudi Arabia’s net-zero momentum Miklós Veszprémi, Senior Strategic Partnerships Manager – VCM further elaborated on growing role of carbon credits and the Voluntary Carbon Market (VCM) in Saudi Arabia. Established in 2021 with Public Investment Fund support, the Kingdom’s carbon exchange has rapidly become one of the world’s largest, enabling corporations to accelerate net-zero commitments. The session framed sustainable real estate not only as an environmental obligation, but a regulatory requirement, financial opportunity, and national expectation, supporting Vision 2030 ambitions. From smart to human-centric Ron Bakker, Co-Founder - PLP Architecture presented a shift from purely sustainable and smart buildings toward human-centred architecture, using research-based design and biophilia to create spaces that inspire connection. Their global mixed-use projects in Rotterdam, Tokyo, London, and Riyadh illustrated how public realm quality, mobility, and integrated lifestyles drive city vitality. Redefining luxury through storytelling and sensory design The panel: ‘Art of Enhancing Experiences’ focused on the evolving meaning of experience in luxury hospitality, noting that today’s travellers seek emotion, memory, and authenticity beyond physical luxury. Lead by Siddharth Peters, Co-Founder - Love That Design panellists: Kristina Zanic, Founder & CEO - Kristina Zanic Consultants Mira Alassaad, Deputy Head of Technical & Head of Interior Design - Dar Global Dharmali Kusumadi, SVP - Design & Business Development - Banyan Tree Hotels & Resorts Pte Ltd Rachel Johnson, Managing Principal - Wimberly Interiors Dalia Muhndis, Executive Director - Interior Designer at Diriyah Company Discussed the importance of storytelling, cultural heritage, and sensory connection, emphasizing wellness, community, and indoor-outdoor living as fundamental design priorities. Innovation shaping the real estate projects of tomorrow The Panel, “Innovation Defining the Real Estate Projects of Tomorrow,” explored technology’s role in reshaping development. Moderated by John Fekete, General Manager - CBRE Saudi Arabia, speakers, Eng. Faisal bin Abdulrahman Alnasser, CEO - Al-Andalus Properties Mohammed Habis, CEO - Al Gharbia Development & Investment Company Arch. Mohammed K. Alduraibi, Managing Director - Oud Real Estate Company Akram Omar, Chief Development Officer - AWJ Holding Company Highlighted AI integration, digital transformation across construction and operations, and new financing frameworks enabling powerful public-private partnerships. They emphasized merging technology with cultural identity to create unforgettable destinations. Investment & returns outlook Matthew Green, Head of Research - CBRE MENA, provided a detailed overview of the real estate landscape for 2025, noting Saudi Arabia’s continued economic momentum driven by regulatory reform, infrastructure expansion, and global events including Riyadh Expo 2030 and the 2034 FIFA World Cup. Real estate now accounts for around 12% of national GDP, supported by institutional foreign investment and high occupancies, office markets in Riyadh are operating at 98% capacity with 15% annual rent growth. Residential development is accelerating, with 200,000 units planned by 2030, while major retail destinations highlight rising demographic demand. The sector’s growth is reinforced by tools such as white land tax, private credit, and increased sovereign fund participation. Partnership announcements & signing ceremonies The summit hosted multiple signing ceremonies celebrating major new developments such as: 26H Jeddah – A landmark mixed-use project with a collaboration between Alworoud Real Estate Investment and LDP Partners featuring a 270-key Hilton Tempo Hotel (first Hilton Tempo Hotel outside USA), 180 residential rental units, and 7,000 m² of retail space. The partnership was signed by: Abdullah Mohammad Kamel, CEO - Alworoud Real Estate Investment Company Dr. Mostafa Mwafy, Co-Founder - Ldp+Partners Company Nader Fouda, Co-Founder - Ldp+Partners Company An iconic luxurious hotel and residential tower spanning more than 20,000 square meters, prominently positioned on Al Kurnaysh Road in the Ash Shati district, overlooking the serene waters of Jeddah’s coastline. This partnership was signed by and between: Yazeed Bin Rawaf - Associate Director - AlJazira Capital Ahmed Said Al-Angari – Land Owner Arch. Mohammad Alderaibi, Managing Director Oud Real Estate Company Both announcements received enthusiastic applause, underscoring ongoing investor confidence. Connecting manufacturers & distributors for market growth The Distributor-Manufacturer Meet, brought together leading manufacturers and distributors shaping Saudi Arabia’s rapidly expanding real estate supply ecosystem. This exclusive networking session was designed to facilitate meaningful introductions, product discovery, and partnership opportunities between companies offering unique, high-value solutions for the Kingdom’s development landscape. Focused, purposeful, and business-driven, the meet enabled stakeholders to explore distribution channels, align on market needs, and build collaborations that support Saudi Arabia’s fast-growing real estate and construction sectors. Saudi Arabia’s investment potential beyond 2030 The Panel ‘Unveiling Saudi's Investment Potential: Vision beyond 2030’ highlighted Saudi Arabia’s real estate boom, fueled by foreign capital, infrastructure growth, and rising demand across sectors. Moderated by Charles Habak, Senior Partner Dubai - McKinsey & Company, panellists: Walid Almurshed, CEO - Quara Holding Khalid Hassan Al Gahtani, Chairman - Haka Group Waleed Al Rashdan, CEO - Arbah Capital Mohamed El Samman, Group CEO - Rajhi Investment Co Noted a shift from speculative to value-driven development, with opportunities beyond major cities, positioning the Kingdom as a top destination for long-term investment. Hospitality & tourism insights Harmen De Jong, Regional Partner - Head of Consulting, Knight Frank, presented data-driven insights into hospitality and travel demand, revealing tourism spending has exceeded pre-COVID levels and now accounts for 6.1% of GDP, targeted to reach 10% by 2030. Visitor numbers have already surpassed original Vision 2030 targets, hitting over 100 million in 2023 and now aiming for 150 million. Meanwhile, hotel capacity is set to nearly triple from 170,000 to 358,000 keys. Key opportunities include mid-scale hospitality, secondary-city development, and branded residences in the holy cities, with 45% of high-net-worth investors willing to pay USD 10,000/m² for premium units in Mecca and Medina. The growing appeal of branded residences in Egypt The session “Investment in Branded Residences in Egypt” featured insights from: Mohamed Salah Mohamed Abdelhakim, CEO - A Capital Holding Dalia El Kordy, CCO – A Capital Holding The discussion explored the rising demand for branded residential developments in Egypt, driven by investor confidence, premium living standards, and strong market fundamentals. The speakers highlighted how branded residences are reshaping buyer expectations, elevating lifestyle value, and creating long-term investment resilience across key Egyptian cities. Building for long-term value The ‘Built for Returns’ panel explored Saudi Arabia’s real estate transformation under Vision 2030, highlighting a shift from short-term returns to mixed-use, sustainable developments backed by institutional capital and diversified financing. Panellists: Ibrahim Alalwan, Managing Director - Watheeq Capital Anas AlDowayan, CEO - Aldowayan Holding Company Abdullah Kamel, CEO - Al Woroud Real Estate Investment Company Mohammad Arab, Group Chief Executive Officer - Arab Group Lead by Susan Amawi, General Manager - KSA - Knight Frank, emphasized strong demand across sectors, the impact of giga-projects in boosting national confidence and tourism, and the growing importance of ESG, placemaking, and community value in delivering long-term, multi-dimensional returns. GBB future minds program This edition introduced the GBB Future Minds Program, a dedicated initiative that brought 30 students from Effat University into dialogue with global architects and designers. Delivered in collaboration with LWK + Partners, PLP Architecture, and Alien Architecture, the program created a meaningful platform for learning, mentorship, and next-generation talent development. Through sessions led by Kerem Cengiz Managing Director, LWK + Partners (MENA) on resilient cities, Ron Bakker Founding Partner, PLP Architecture (UK), on human-centric design, and Alaa Qathani, Founder and Design Director, Alien Architecture (KSA) on Saudi identity and cultural storytelling, students explored the future of the built environment through sustainability, ethics, and innovation. The program concluded with a hands-on workshop and town hall, where students presented ideas and engaged in an open dialogue on how young architects can shape Saudi Arabia’s evolving urban future. RICA - Saudi Arabia’s premier real estate choice awards The REDS Industry Choice Awards (RICA 2025) celebrated the organizations and professionals driving transformation across Saudi Arabia’s real estate, architecture, and design sectors. With 59 nominees across 15 categories, the awards recognized leadership, innovation, and excellence aligned with the Kingdom’s Vision 2030 development goals. Winners Included: Celebrated Residential Developer of the Year – Roshn Group Celebrated Mixed-Use Developer of the Year – Rua Al Madinah Holding Company Celebrated Hospitality Developer of the Year – Red Sea Global Celebrated Architecture Firm of the Year – Foster + Partners Celebrated Interior Design Firm of the Year – International Design Associates, Bahrain Celebrated PMC of the Year – JLL Celebrated Investor of the Year – Alramz Real Estate Company Celebrated Urban Project of the Year – Sports Boulevard Foundation Celebrated Innovative Project of the Year – Jeddah Front Celebrated Non-Urban Project of the Year – Desert Rock Celebrated CEO of the Year – Men – Eng. Ahmed A. Alsulaim, CEO, Jeddah Central Development Celebrated CEO of the Year – Women – Dina Alawadh, CEO, OWN Real Estate Company Emerging Interior Designer of the Year – Jannat Abdulla Husain, Interior Designer, International Design Associates Emerging Architect of the Year – Lama Al-Kharboush, Senior Associate and KSA Country Manager, Aedas Honorary RICA – Lifetime Achievement Award – Dr. Zuhair Hamed Fayez, Chairman, Zuhair Fayez Partnership Closing perspective Across discussions, a clear theme emerged: Saudi Arabia is one of the world’s most dynamic real estate markets, driven by Vision 2030 ambition, institutional capital, innovation, and global confidence. Leaders emphasized that future success requires balancing financial returns with sustainability, community value, and cultural authenticity, creating developments built to last, not just built to sell. In this spirit, GBB took a defining step forward by introducing a Net-Zero pathway for the summit in partnership with VCM, measuring emissions, facilitating verified offsets, and championing a responsible model for industry-led climate action. By aligning innovation with accountability, GBB continues to elevate the ecosystem and set a new benchmark for how platforms can shape the future of development in the Kingdom.
DigiCert, a pioneer in intelligent trust, unveiled its 2026 Security Predictions, forecasting how AI, quantum computing, and automation will reshape global trust frameworks. The predictions highlight a pivotal shift toward AI integrity, resilience, and quantum readiness as core tenets of intelligent trust. DigiCert’s full predictions and outlook for the new year can be found at DigiCert’s blog. 1. AI Integrity Becomes the New Trust Standard: AI authenticity will overtake data confidentiality as the top enterprise trust concern. Organizations will require verifiable identity, provenance, and tracking for every model, dataset, and autonomous agent. 2. Resilience Becomes the New Compliance: Resilience will shift from an IT goal to a board-level mandate as regulations like Digital Operational Resilience Act (DORA) and new global standards tighten expectations. Organizations will be required to prove that their DNS, identity, and certificate systems can withstand disruption, with uptime and recoverability directly tied to financial and operational stability. 3. Automation Accelerates as Certificate Lifespans Shrink: With TLS certificate lifetimes reducing to 200 days as part of the phased reduction to 47 days, the effort associated with manual renewal doubles. Organizations will adopt full-stack automation to eliminate outages and create self-healing trust ecosystems. 4. Quantum Computing Puts Encryption on Notice: The first practical quantum computer capable of solving meaningful problems will emerge. Organizations beginning their initial pilots will discover interoperability hurdles as certificate and software ecosystems adapt to quantum-safe requirements. 5. Content Authenticity Moves from Principle to Policy: Governments and major platforms will begin enforcing C2PA for AI-generated and edited content. Watermarking and cryptographic provenance will become required for distribution across news, social, and commerce. 6. Federated PKI Reinvented for the Post-Chrome Era: Organizations will modernize private PKI as Chrome phases out legacy client authentication and Microsoft sunsets old CA architectures. Identity will shift toward cloud-native, automated, and passwordless trust models. 7. Email Trust Redefined: Verified Identities Take the Lead: AI-driven phishing will push enterprises to standardize on Verified Mark Certificates and strict DMARC enforcement. Verified sender identity will become the baseline expectation for secure, enterprise-grade communication. 8. Machine Identities Outnumber Humans 100:1, and PQC Becomes Mandatory: Connected devices and AI agents will surpass human identities by two orders of magnitude. PQC-ready identity frameworks will become mandatory as standards bodies embed quantum-safe algorithms into device ecosystems. Integrity across every digital interaction “Security in 2026 won’t just be about protecting systems, it will be about proving integrity across every digital interaction,” said Jason Sabin, Chief Technology Officer at DigiCert. “As AI accelerates, machine identities multiply, and quantum computing advances, intelligent trust will become the foundation that keeps businesses resilient, verifiable, and secure. The organizations that embrace automation, provenance, and quantum-safe readiness now will define the trust landscape for the next decade.”
International Security Expo is thrilled to announce that it has appointed a new chair. Figen Murray OBE, initiator and lead campaigner for Martyn's Law, will be taking on the role effective immediately. As chair, Figen will help steer the future direction and growth of International Security Expo, whilst also ensuring it best serves the needs of the industry. She will also lead the Advisory Council that is comprised of an outstanding selection of the industry’s foremost experts, representing a broad range of sectors and Government. Figen will take over from Angela Essel, senior account director – national security at Thales UK, and former head of JSaRC, Home Office, who has held the position for the past two years. Counter terrorism legislation Having transformed her grief into a powerful movement for change, Figen is the initiator behind the campaign to introduce counter terrorism legislation – the Terrorism (Protection of Premises) Act 2025 – informally known as Martyn’s Law, after her son, Martyn Hett, was tragically killed alongside 21 others at the Manchester Arena terrorist attack on 22 May 2017. Her tireless campaigning has secured national support from cross-party politicians, the security industry, businesses and the public, to introduce legislation that will better protect venues and the public from the potential impact of a terrorist attack. Homeland and international security Beyond Figen’s legislative work, she has achieved a distinction in a counter terrorism master’s degree from the University of Lancashire. Figen’s expertise and dedication to making Britain safer saw her awarded an OBE in the 2022 New Year’s Honours List. There are very few people who have been able to bring together all elements of the security industry in such a unifying manner, whilst at the same time effecting change at a legislative level. This sees Figen ideally placed to take on the role of chair, as International Security Expo brings together Government, Industry, Academia and the entire end-user community from all corners of the world, with a key focus on both homeland and international security, and countering terrorism. Global security industry Speaking about her appointment to the role Figen says, “It is a real privilege and honor to become chair of International Security Expo. For many years it has been clear how important this event is to the global security industry – from the wealth of innovation on display to the incredible speakers who impart their knowledge and experience, along with the unique opportunity to engage with the UK Government.” “I know first-hand just how valuable this has been in the long journey to get Martyn's Law signed into legislation. The event is one of my highlights of the year and I am extremely excited to take on this prestigious role, lead the Advisory Council and help steer the direction of International Security Expo so it continues as one of the world's leading events for countering terrorism and keeping us all safe.” Ensuring public safety Angela Essel says: “It has been a great pleasure to serve as chairwoman for this fantastic event and to see how many people view it as a must-attend date in their calendar. These past two editions of International Security Expo have been the best ever and I am delighted to have helped contribute towards their success. Figen’s drive and resolve is awe-inspiring and I have no doubt she will make a superb chair and I wish her the best of luck in the role.” Rachael Shattock, Group Event Director, added: “We are extremely honored to welcome Figen as chair of International Security Expo. Watching her tireless campaigning over the years has been truly inspirational and I cannot think of anyone better to bring the energy and passion for ensuring public safety to the event. As the event continues to go from strength to strength, this is the ideal time to welcome Figen aboard and the whole team and I are very excited to work with her. I would also like to thank Angela for the fantastic work she has done as chairwoman over the past two years in helping make the event unmissable.”
Zimperium, the world's pioneer in mobile security, now announced that Alistaire Davidson has joined the company as Chief Financial Officer, reporting directly to CEO Shridhar Mittal. Alistaire brings more than 20 years of finance leadership experience across private equity–backed and public software companies. Alistaire most recently served as Regional CFO, Americas at The Access Group, where he led the post-acquisition integration of two strategic business units. Prior to The Access Group, he held progressive finance leadership roles at AVEVA, supporting the company’s SaaS transition across the Americas and driving a global services transformation that delivered significant margin improvements. Zimperium’s continued expansion “Alistaire’s deep financial expertise and proven ability to scale global software organizations make him a strong addition to our leadership team,” said Shridhar Mittal, CEO of Zimperium. “As demand for mobile security continues to accelerate worldwide, his leadership will be instrumental in guiding Zimperium through our next phase of growth.” As CFO, Alistaire will oversee financial strategy, planning, operations, and performance management to support Zimperium’s continued expansion across global markets.
Kindoo, a pioneer in modern smartphone wireless access control system solutions, announces the expansion of its Reseller Partner Program to serve the growing North American market. Kindoo’s unique access solution eliminates the longstanding barriers to entry for modern access control systems with a high-performance, highly cost-effective mobile access control solution that is easy to sell and to use providing a win-win for both resellers and end-users. Installing security dealers “We are looking to partner with forward-looking installing security dealers who are looking to increase sales and profits with long-term RMR,” said Michael Chaftari, Partner at Kindoo. “Kindoo has documented success with both enterprise and small business users across the United States, serving over 100,000 end-users, and we are now looking to further expand our sales network with a select group of new reseller partners.” Key advantages of the Kindoo platform Kindoo brings a revolutionary and cost-effective approach to modern access control with a unique mobile access platform that overcomes the longstanding barriers for security dealers to offer access control and users to install it. Key advantages of the Kindoo platform include: Smartphone credentialing eliminates costly physical credentials Compatibility with ANY electronic lock, gate, turnstile, or security entrance Range of battery-operated devices eliminate the need for local power Cloud-based access management – no need for network/IT expertise Remote management of all on-boarding and off-boarding credentials Unlimited scalability to accommodate system expansion 256-bit encryption ensures secure communications Personal privacy protection Kindoo offers new reseller partners Kindoo offers new reseller partners the support they need to be successful. Resources include demo kits, training videos and material, sales playbooks and marketing support resources, project registration/reseller protection, special partner pricing, and real sales leads. A limited number of resellers will be approved by regional area/coverage to further support growth.


Expert commentary
It is the time of year when city centers transform, as outdoor Christmas markets fill town squares and high streets. An estimated 6,000 markets will open across Europe during the festive season, with some of the largest — including Nuremberg’s Christkindlesmarkt, London’s Hyde Park Winter Wonderland and Craiova in Romania — welcoming millions of visitors. Sadly, these popular events have in recent years been the subject of attacks, most notably Berlin in 2016 and the tragedy in Magdeburg last December, where a vehicle was driven into the crowd. Incidents such as these have encouraged governments, including the UK with the introduction of Martyn’s Law, to strengthen planning and preparation for large-scale public events. Digital twins: A new standard for event preparation Drone-based photogrammetry captures streets, squares and surrounding buildings with exceptional detail One of the most effective tools for preparing and safeguarding public spaces today is the creation of a photorealistic digital twin — a highly accurate 3D virtual model of the intended market area. Drone-based photogrammetry captures streets, squares and surrounding buildings with exceptional detail, enabling planners to work within a realistic and immersive environment long before any physical structures are installed. Digital twin design tools can ingest these datasets and visualize them using advanced technologies, creating a lifelike representation of even the most complex outdoor scenes. Designing the market in 3D before construction begins Once the digital twin is created, event organizers, city authorities and security specialists can begin shaping the market virtually. Temporary stalls, lighting installations, stages, decorative structures, back-office units, Christmas trees, ice rinks and other festive features can be positioned directly within the digital model. It‘s also possible to place static representations of people or larger groups to approximate crowd density and understand how occupied space will influence visibility, accessibility and the overall perception of the environment. This ability to design and refine the market layout before construction allows planners to test multiple variations, understand how structures interact and ensure that the environment remains safe and manageable throughout the event. Virtual camera planning, coverage assessment and analysis Digital twins also provide a robust foundation for planning the deployment of visual-monitoring systems Digital twins also provide a robust foundation for planning the deployment of visual-monitoring systems. Cameras can be placed directly into the 3D environment, allowing planners to immediately see how temporary structures, decorations or pedestrian flows will influence the field of view. Blind spots become apparent, alternative camera heights or angles can be explored and strategic decisions about additional mounting points or temporary towers can be made with confidence. For each planned camera, the expected resolution per meter or per foot is visualized directly inside the digital twin. Instead of relying on theoretical charts or static design tables, planners can instantly see whether a particular camera position will deliver the clarity required for the intended purpose, whether it is early detection of movement, recognition of behavior patterns or full identification of individuals. Real-time visual feedback This real-time visual feedback makes the entire planning process more precise, transparent and efficient. These evaluations can be carried out within the realistic daytime environment captured by the digital twin. Planners can also prepare alternative scene variants — for example, dedicated night-time versions or layouts reflecting festive lighting — to understand how visibility and coverage may change throughout the event. Even without full weather simulation, this approach allows teams to anticipate typical operational challenges and refine the monitoring concept well before the first stall is erected. Testing safety and security scenarios Perhaps the greatest advantage of working with a digital twin is the ability to explore the environment from multiple perspectives before the event begins. Although the scene itself is static, planners can move through it using a virtual intruder to understand how the market will appear from ground level and to identify potential vulnerabilities that may not be obvious from a top-down view. This makes it possible to assess where hostile-vehicle barriers should be positioned, how narrow passages might feel when occupied, or where visibility may be reduced due to temporary structures or decorations. The static digital twin also provides a clear way to evaluate emergency access lanes, determine suitable locations for help points or medical posts and plan the general layout of security patrol routes. By navigating the scene freely and observing it from different perspectives, teams can refine the design and address potential blind spots long before construction begins. A unified environment with LiDAR The created digital twin also becomes the primary visualization environment for LiDAR during live operations Beyond planning, the created digital twin also becomes the primary visualization environment for LiDAR during live operations. Operators can interact with this 3D map directly and with a single click on any location, all PTZ cameras capable of viewing that point automatically reposition to it. This provides an unmatched navigation interface for real-time camera control, making situational awareness significantly faster and more intuitive. LiDAR then works seamlessly with a video management system, which controls all camera streams, recordings and video evidence, creating a tightly integrated monitoring workflow. Supporting real-world operations Once the market opens, the digital twin continues to serve as a valuable operational resource. If layouts change during the event — for example, because of additional attractions, adjusted walkways or altered security checkpoints — these modifications can be quickly modelled and evaluated before implementation. When the festive season concludes, the same model can be repurposed for future events, long-term city planning or other public-space deployments. A safer and smarter festive season Christmas markets are vibrant, high-profile and densely populated environments, making them attractive targets for those seeking to cause disruption. By combining detailed photogrammetry, advanced 3D visualization, and rigorous spatial evaluation, cities can create safer, better-prepared, and more resilient festive settings. With tools such as digital twins and LiDAR, authorities can plan more effectively, anticipate risks earlier and ensure that every stall, pathway and vantage point contributes to a joyful — and secure — holiday season.
The Internet of Things is growing quickly. It has moved far beyond a few smart gadgets at home. Today, connected technology is in homes, factories, hospitals, farms, and cities. Experts expect the global market for IoT devices to rise from about $70 billion in 2024 to more than $181 billion by 2030. This means more devices, more data, and more opportunities for industries everywhere. This growth comes from several advances working together. 5G connections make it possible to send and receive data faster. Edge computing processes information close to where it is created, which helps with quick decisions. Analytics allow organizations to understand and act on the data they collect. Together, these improvements are opening the door to new ways of working, producing, and communicating. IoT: The next generation As devices become more advanced, they use more energy and send more data. Think about high-quality security cameras, detailed environmental sensors, or systems in vehicles that send constant updates. All of these devices require a strong supply of power and a steady connection. In 2024, sensors made up more than 32 percent of all IoT device sales. Sensors are essential, yet the next wave of devices will do even more. They will process information themselves, use artificial intelligence, and include many features in one unit. This progress depends on networks that deliver both the energy and the bandwidth to support them. Into the future Devices and applications keep improving, so networks need the flexibility to handle what comes next Setting up IoT systems is about more than meeting today’s needs. Devices and applications keep improving, so networks need the flexibility to handle what comes next. A future-ready design provides extra capacity in both power and data flow. This way, when it’s time to add new devices or upgrade existing ones, the system is prepared without requiring major changes. One smart approach is to use modular equipment. For example, a network switch might deliver more power than devices currently use, while allowing room to connect more advanced devices later. This helps keep the system ready for growth. Built for all IoT devices often operate in challenging places. Factories, power plants, rail lines, and shipping ports face extreme temperatures, dust, vibration, and other difficult conditions. Network equipment in these locations needs the strength to keep working through heat, cold, and constant use. Industrial-grade gear is designed for these environments. It can run in a wide range of temperatures, handle physical impacts, and resist interference. Features such as port security, which keep a connection safe if a cable is removed, help protect both the equipment and the data it carries. Systems with backup power inputs continue to run even when one power source goes offline. Plug into PoE Power over Ethernet (PoE) sends both energy and data through the same cable Power over Ethernet (PoE) sends both energy and data through the same cable. This makes installation simpler and allows flexibility in where devices are placed. And as devices become more capable, they often need more power to operate. The latest innovation for PoE can deliver up to 90 watts on each port. This is enough to support advanced devices like AI-enabled cameras or multi-sensor units. When every port on a switch can supply that much power at the same time, adding more devices is straightforward and performance stays strong. Protecting the network Every connected device is part of a larger network. Protecting this network means securing data from the moment it leaves the device until it reaches its planned destination. Built-in security features in network equipment — such as secure architecture, encryption support, and physical safeguards — help keep information safe. They also help meet industry and government requirements for equipment sourcing and design. A clear path Organizations leading in IoT think ahead. They prepare for the next stage of technology by building networks with flexibility, durability, and protection in mind. These networks supply extra power, allow more bandwidth, and keep data secure while adapting as the system grows. The focus is on creating a foundation that supports innovation year after year. This means planning for devices that are faster, more capable, and more connected, while making sure the infrastructure grows right along with them. Looking ahead Strong, adaptable, and secure networks will allow connected devices to reach their full potential The IoT of the future will touch nearly every part of daily life. It will help farmers grow food more efficiently, guide self-driving vehicles, improve medical care, and keep cities running smoothly. As devices multiply and gain new abilities, the networks powering them need to grow in step. Strong, adaptable, and secure networks will allow connected devices to reach their full potential. By planning for both today’s needs and tomorrow’s possibilities, organizations can make the most of the opportunities IoT brings—and keep those opportunities expanding for years to come. Key takeaways: Preparing for the future of IoT The IoT market is growing fast The global market for connected devices is expected to grow from $70 billion in 2024 to more than $181 billion by 2030. This means more devices in more industries, from farming to healthcare to transportation. Devices are using more power and data Newer devices have more features — such as high-quality video, built-in AI, and multiple sensors — and these require stronger power supplies and faster connections. Future-ready networks are essential Infrastructure should allow extra capacity for both power and data. This ensures new devices can be added without major changes or delays. Environments vary, so equipment should match the setting Industrial areas, outdoor spaces, and transportation hubs need rugged, reliable equipment that works in extreme conditions and stays secure. Security starts at the network level Built-in protections — like secure architecture, encryption, and physical safeguards — help keep information safe and meet important industry requirements.
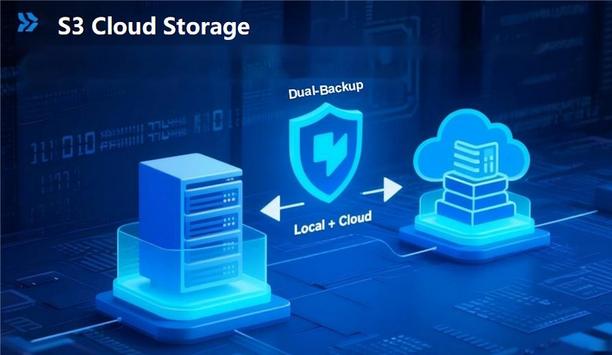
Where and how to store security camera footage usually depends on the scale of the video surveillance project, the way you are using to record the video and how long you want to keep the recordings. If there are only few IP cameras, say 2~3 IP cameras for example, and you don’t need to keep the recordings for the month, usually using SD card which is installed in the camera is enough. Video management software A VMS provides a unified platform to manage all cameras and record footage onto centralized local storage servers If there are more than four cameras, even up to 128 cameras, NVR or CVR become the practical choice for managing and storing recordings reliably. However, if there are hundreds or thousands cameras, which need to managed and recorded, in this way video management software with centralized recording storage becomes essential. A VMS provides a unified platform to manage all cameras and record footage onto centralized local storage servers. S3-compatible cloud platforms Critically, if the VMS supports the S3 object storage protocol, users gain the flexibility to store recordings on S3-compatible cloud platforms (public or private), offering significant hardware cost savings and enhanced scalability. For such demanding environments, selecting a VMS built on an open platform architecture is strongly advised, ensuring the system can expand infinitely to meet future project growth. Video surveillance management system Users can seamlessly add subordinate servers (or disk groups like IPSAN/NAS), disk arrays, and network bandwidth Take the video surveillance management system SVMS Pro as an example. Its foundation is an open 1+N stackable architecture, enabling unlimited expansion of recording storage servers. Users can seamlessly add subordinate servers (or disk groups like IPSAN/NAS), disk arrays, and network bandwidth. This achieves extended recording durations and boosted storage performance while maintaining system stability during sustained operation (assuming environmental requirements are met). Key architectural advantages Each centralized storage module based on a Linux OS, supports up to 200 front-end video channels per server. Its N+1 stackable expansion capability utilizes a distributed architecture, forming clusters of storage servers. Scaling the project involves simply adding subordinate storage modules – no modifications to existing deployments are required. Seamless S3 object storage integration Furthermore, SVMS Pro features deep integration of the S3 object storage protocol Furthermore, SVMS Pro features deep integration of the S3 object storage protocol. This allows seamless connection to major public cloud services like Alibaba Cloud OSS, Tencent Cloud COS, and Amazon S3 cloud, as well as private S3-compatible object storage solutions. This integration delivers truly limitless capacity expansion, leveraging the inherent elasticity of the cloud to effortlessly accommodate petabyte-scale video growth. Dual insurance: Multi-layered data protection The critical value of security data comes with inherent risks; losing video footage can lead to immeasurable losses. To mitigate these risks comprehensively, SVMS Pro innovates with its "Local + Cloud" Dual-Backup mechanism, leveraging S3 features to build multiple security layers: Real-Time Dual-Writing: Recordings are first written to the local disk (acting as a cache buffer). Upon local persistence, data is simultaneously replicated to cloud-based S3 storage, guaranteeing instant failover if either node fails. Smart Hot/Cold Tiering: Frequently accessed ("hot") data remains on high-performance local storage, while historical footage is automatically archived to low-cost cloud tiers, optimizing storage expenses. Cross-Regional Disaster Recovery: Utilizing the multi-replica and cross-region replication features of carrier-grade S3 storage inherently protects against physical disasters like earthquakes or fires. Additionally, the platform ensures comprehensive data protection through integrity verification and encrypted transmission, safeguarding data integrity and confidentiality across its entire lifecycle – from storage and transmission to access. Conclusion In essence, selecting the optimal storage solution for security footage hinges on a fundamental understanding of scalability requirements, retention needs, and data protection imperatives. As surveillance deployments grow from a few cameras to enterprise-scale systems, the underlying architecture must evolve: Localized storage (SD cards/NVRs) suffices for limited scope and short retention. Centralized VMS platforms become essential for unified management at scale, with open, modular architectures providing critical future-proofing for expansion. S3 object storage integration represents a paradigm shift, decoupling storage capacity from physical hardware and enabling truly elastic, cost-efficient scaling – both on-premises and in the cloud. Ultimately, successful large-scale video surveillance storage relies on architecting for flexibility, embedding data protection intrinsically, and strategically leveraging object storage protocols to balance performance, cost, and resilience – principles essential for safeguarding critical security data now and in the future.
Security beat
Companies at GSX 2023 emphasized new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the security market. Today, more than half of the company’s lineup supports AI at the edge so the customer has a wide choice of form factors when seeking to leverage the feature set. AI processing relay, extended warranty i-PRO is increasing their warranty period from 5 to 7 years, which could be a lifetime warranty in some cases I-PRO also has an “AI processing relay” device that accepts non-AI video streams and applies edge analytics. AI has progressed from a high-end technology to a feature available in a variety of cameras at different price points. i-PRO is also increasing its warranty period from 5 to 7 years, which could be a lifetime warranty in some cases depending on a customer’s refresh schedule and lifecycle management. Active Guard, MonitorCast The company’s video management system (Video Insight) is continuing to build new features including “Active Guard,” an integrated metadata sorter. Their access control platform, MonitorCast, is a Mercury-based solution that is tightly integrated with Video Insight. Their embedded recorders now have PoE built in. “We can move at a faster pace to fill out our product line since leaving Panasonic,” says Adam Lowenstein, Director of Product Management. “We can focus our business on adapting to the market.” Emphasis on retail and other verticals Shoplifting is a timely issue, and retail is a vertical market that got a lot of attention at GSX 2023. “We see a lot of retailers who are primarily interested in protecting employee safety, but also assets,” says Brandon Davito, Verkada’s SVP of Product and Operations. “Shrinkage is a CEO-level priority.” “Retailers are getting more engaged with security posture, instead of letting perpetrators walk,” Davito adds. Intrusion detection Verkada has an intrusion product that will notify a central station if there is an alarm On the alarm side, Verkada has an intrusion product that will notify a central station if there is an alarm, and operators can review videos to confirm the alarm. Other capabilities seeking to discourage trespassers include sirens, strobes, and “talkdown” capabilities. International expansion Verkada continues to expand internationally with 16 offices in all, including Sydney, Tokyo, and London. The core value proposition is to enable customers to manage their onsite infrastructure more simply, including new elements such as PTZ cameras, intercoms, and visitor management. Verkada emphasizes ease of use, including a mobile application to allow access to be managed across the user base. Forging partnerships “We are committed to the channel and industry, and we continue to build relationships and expand our reach,” says Davito. Among the industry relationships is a new partnership with Convergint, which was hinted at during the show and announced later the same day. They are also expanding their partnerships with Schlage, Allegion, and ASSA ABLOY. Working with other verticals They offer new features for K -12 schools, and a new alarm platform is easier to deploy and manage Verkada has also found success across multiple other verticals, notably healthcare, where they integrate with an electronic medical records system. They offer new features for K-12 schools, and a new alarm platform is easier to deploy and manage. They are integrating wireless locks to secure interior doors in schools, looking to secure the perimeter, and installing guest management systems. Transitioning the Mid-Market to the Cloud Salient is squarely focused on the “mid-market,” a large swath of systems somewhere between small businesses and enterprise-level systems. Pure cloud systems are not as attractive to this market, which has a built-out infrastructure of on-premise systems. Adding a camera to an existing system is easier and less expensive than tying it to the cloud. Benefits of cloud It’s a market that may not be ready for pure cloud, but there are benefits to be realized from adding a cloud element to existing systems. “We are continuing to augment our premise-based solutions with added cloud capabilities and flexibility,” says Sanjay Challa, Salient’s Chief Product Officer. The feedback Salient hears from their customers is “I want to own my data.” The hybrid cloud approach offers the right mix of control, flexibility, and unit economics. Cloud add-on capabilities We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive" Cloud add-on capabilities include bringing more intelligence about system operation to the user via the cloud. Over time, Salient expects to sell more cloud-centric offerings based on feedback from integrators and customers. “We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive over time,” says Challa. Vaidio AI technology Salient seeks to be a transition pioneer to help customers realize the path to the cloud. Their approach is “crawl, walk, run,” and helping customers make the transition at each stage. Salient has added AI to its product offering, incorporating Vaidio AI technology from IronYun into a powerful suite and broad array of on-premise analytics, which are gaining traction. The seamless approach makes it easy for customers to embrace AI analytics, although Salient remains broadly committed to open systems. Addressing ‘Soft’ Features for Integrators AMAG is in the process of enhancing its product line with the next generation of access control panels. However, “product” is just part of the new developments at AMAG. In addition to “hard” features (such as products), the company is looking to improve its “soft” features, too; that is, how they work with the integrator channel. Integrator channel Rebuilding a process to make your organization more efficient, is relatively easy; it just takes a lot of persistence" “We have the depth of our legacy customer base we can learn from, we just need to close the feedback loop quicker,” says Kyle Gordon, AMAG’s Executive Vice President of Global Sales, Marketing, and commercial Excellence, who acknowledges the value of reinstating face-to-face meetings after COVID. “We are laser-focused on nurturing our integrator channel,” he says. “Developing new features takes time, but rebuilding a process to make your organization more efficient, that’s relatively easy; it just takes a lot of persistence,” says Gordon. More cohesive internal communication is another useful tool, he says. Disrupting the cloud based on price Wasabi is working to make cloud applications less expensive by offering a “disruptive” price on cloud storage, $6.99 per terabyte per month (80% less than hyperscalers). Contending “hyperscalers” like AWS are charging too much for cloud storage, Wasabi is using its own intellectual property and server equipment co-located in data centers around the world. Wasabi sells “hot cloud storage,” which refers to the fact that they only have one tier of storage and data is always accessible. In contrast, a company such as AWS might charge an “egress fee” for access to data stored in a “colder” tier. Cloud storage “We saw that several video surveillance companies had not yet adopted cloud storage, and we saw an opportunity to make it easy to use,” said Drew Schlussel, Wasabi’s Senior Director of Product Marketing. “We just install a little bit of software that allows them to store data in the cloud and bring it back from the cloud.” Performance, protection (cybersecurity), and price Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies such as Genetec and Milestone. Emphasizing performance, protection (cybersecurity), and price, their data centers are certified to SOC 2 and ISO 27001 standards. Faster throughput for weapons detection Xtract One is a young company focusing on weapons detection in a time of accelerated concern about gun issues post-COVID. Founded in Canada and based on technology developed at McMaster University, Xtract One has found a niche in providing weapons detection at stadiums and arenas. These customers already have budgets, and it is easy to shift the money to a newer, faster technology. Madison Square Garden in New York City is among its customers. Cost savings solution Xtract One can increase throughput to 30 to 50 people per entrance per minute (compared to 5 to 6 people per minute when using metal detectors). The solution doesn’t require anyone to empty their pockets and the system alarms on items beyond guns and knives. Using Xtract One allows customers to reduce the number of screening lanes and security staff, providing additional cost savings, all while getting fans through the screening process in half the time. Purpose-built sensors The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties In addition to stadiums and arenas, Xtract One, formerly Patriot One, is also getting “inbound” interest from schools, hospitals, manufacturers, and other verticals that makeup 50% of their business. “We’re on a rocket ride, mainly because the weapons issues are not going away,” says Peter Evans, CEO and Director at Xtract One. The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties, all correlated by an AI engine. Providing early warning of violence ZeroEyes is another company focused on weapons detection. Their AI gun detection system works with video images to identify if someone is “brandishing” (carrying) a weapon. In other words, the system does not detect concealed weapons. Identifying someone carrying a weapon provides early warning of a possible violent act. Increased response with AI-enables images Images are identified by AI and sent to a monitoring center where a human confirms the image before contacting first responders. Knowing the location of a shooter enables staff to lock entry points, move people to safety, and direct first responders. The company was founded to leverage existing camera views to stop mass shootings and gun violence by reducing response times.
When it comes to security cameras, the end user always wants more—more resolution, more artificial intelligence (AI), and more sensors. However, the cameras themselves do not change much from generation to generation; that is, they have the same power budgets, form factors and price. To achieve “more,” the systems-on-chips (SoCs) inside the video cameras must pack more features and integrate systems that would have been separate components in the past. For an update on the latest capabilities of SoCs inside video cameras, we turned to Jérôme Gigot, Senior Director of Marketing for AIoT at Ambarella, a manufacturer of SOCs. AIoT refers to the artificial intelligence of things, the combination of AI and IoT. Author's quote “The AI performance on today’s cameras matches what was typically done on a server just a generation ago,” says Gigot. “And, doing AI on-camera provides the threefold benefits of being able to run algorithms on a higher-resolution input before the video is encoded and transferred to a server, with a faster response time, and with complete privacy.” Added features of the new SOC Ambarella expects the first cameras with the SoC to emerge on the market during early part of 2024 Ambarella’s latest System on Chip (SOC) is the CV72S, which provides 6× the AI performance of the previous generation and supports the newer transformer neural networks. Even with its extra features, the CV72S maintains the same power envelope as the previous-generation SoCs. The CV72S is now available, sampling is underway by camera manufacturers, and Ambarella expects the first cameras with the SoC to emerge on the market during the early part of 2024. Examples of the added features of the new SOC include image processing, video encoders, AI engines, de-warpers for fisheye lenses, general compute cores, along with functions such as processing multiple imagers on a single SoC, fusion among different types of sensors, and the list goes on. This article will summarize new AI capabilities based on information provided by Ambarella. AI inside the cameras Gigot says AI is by far the most in-demand feature of new security camera SoCs. Customers want to run the latest neural network architectures; run more of them in parallel to achieve more functions (e.g., identifying pedestrians while simultaneously flagging suspicious behavior); run them at higher resolutions in order to pick out objects that are farther away from the camera. And they want to do it all faster. Most AI tasks can be split between object detection, object recognition, segmentation and higher-level “scene understanding” types of functions, he says. The latest AI engines support transformer network architectures (versus currently used convolutional neural networks). With enough AI horsepower, all objects in a scene can be uniquely identified and classified with a set of attributes, tracked across time and space, and fed into higher-level AI algorithms that can detect and flag anomalies. However, everything depends on which scene is within the camera’s field of view. “It might be an easy task for a camera in an office corridor to track a person passing by every couple of minutes; while a ceiling camera in an airport might be looking at thousands of people, all constantly moving in different directions and carrying a wide variety of bags,” Gigot says. Changing the configuration of video systems Low-level AI number crunching would typically be done on camera (at the source of the data) Even with more computing capability inside the camera, central video servers still have their place in the overall AI deployment, as they can more easily aggregate and understand information across multiple cameras. Additionally, low-level AI number crunching would typically be done on camera (at the source of the data). However, the increasing performance capabilities of transformer neural network AI inside the camera will reduce the need for a central video server over time. Even so, a server could still be used for higher-level decisions and to provide a representation of the world; along with a user interface for the user to make sense of all the data. Overall, AI-enabled security cameras with transformer network-based functionality will greatly reduce the use of central servers in security systems. This trend will contribute to a reduction in the greenhouse gases produced by data centers. These server farms consume a lot of energy, due to their power-hungry GPU and CPU chips, and those server processors also need to be cooled using air conditioning that emits additional greenhouse gases. New capabilities of transformer neural networks New kinds of AI architectures are being deployed inside cameras. Newer SoCs can accommodate the latest transformer neural networks (NNs), which now outperform currently used convolutional NNs for many vision tasks. Transformer neural networks require more AI processing power to run, compared to most convolutional NNs. Transformers are great for natural language processing (NLP) as they have mechanisms to “make sense” of a seemingly random arrangement of words. Those same properties, when applied to video, make transformers very efficient at understanding the world in 3D. Transformer NNs require more AI processing power to run, compared to most convolutional NNs For example, imagine a multi-imager camera where an object needs to be tracked from one camera to the next. Transformer networks are also great at focusing their attention on specific parts of the scene—just as some words are more important than others in a sentence, some parts of a scene might be more significant from a security perspective. “I believe that we are currently just scratching the surface of what can be done with transformer networks in video security applications,” says Gigot. The first use cases are mainly for object detection and recognition. However, research in neural networks is focusing on these new transformer architectures and their applications. Expanded use cases for multi-image and fisheye cameras For multi-image cameras, again, the strategy is “less is more.” For example, if you need to build a multi-imager with four 4K sensors, then, in essence, you need to have four cameras in one. That means you need four imaging pipelines, four encoders, four AI engines, and four sets of CPUs to run the higher-level software and streaming. Of course, for cost, size, and power reasons, it would be extremely inefficient to have four SoCs to do all this processing. Therefore, the latest SoCs for security need to integrate four times the performance of the last generation’s single-imager 4K cameras, in order to process four sensors on a single SoC with all the associated AI algorithms. And they need to do this within a reasonable size and power budget. The challenge is very similar for fisheye cameras, where the SoC needs to be able to accept very high-resolution sensors (i.e., 12MP, 16MP, and higher), in order to be able to maintain high resolution after de-warping. Additionally, that same SoC must create all the virtual views needed to make one fisheye camera look like multiple physical cameras, and it has to do all of this while running the AI algorithms on every one of those virtual streams at high resolution. The power of ‘sensor fusion’ Sensor fusion is the ability to process multiple sensor types at the same time and correlate all that information Sensor fusion is the ability to process multiple sensor types at the same time (e.g., visual, radar, thermal, and time of flight) and correlate all that information. Performing sensor fusion provides an understanding of the world that is greater than the information that could be obtained from any one sensor type in isolation. In terms of chip design, this means that SoCs must be able to interface with, and natively process, inputs from multiple sensor types. Additionally, they must have the AI and CPU performance required to do either object-level fusion (i.e., matching the different objects identified through the different sensors), or even deep-level fusion. This deep fusion takes the raw data from each sensor and runs AI on that unprocessed data. The result is machine-level insights that are richer than those provided by systems that must first go through an intermediate object representation. In other words, deep fusion eliminates the information loss that comes from preprocessing each individual sensor’s data before fusing it with the data from other sensors, which is what happens in object-level fusion. Better image quality AI can be trained to dramatically improve the quality of images captured by camera sensors in low-light conditions, as well as high dynamic range (HDR) scenes with widely contrasting dark and light areas. Typical image sensors are very noisy at night, and AI algorithms can be trained to perform excellently at removing this noise to provide a clear color picture—even down to 0.1 lux or below. This is called neural network-based image signal processing, or AISP for short. AI can be trained to perform all these functions with much better results than traditional video methods Achieving high image quality under difficult lighting conditions is always a balance among removing noise, not introducing excessive motion blur, and recovering colors. AI can be trained to perform all these functions with much better results than traditional video processing methods can achieve. A key point for video security is that these types of AI algorithms do not “create” data, they just remove noise and clean up the signal. This process allows AI to provide clearer video, even in challenging lighting conditions. The results are better footage for the humans monitoring video security systems, as well as better input for the AI algorithms analyzing those systems, particularly at night and under high dynamic range conditions. A typical example would be a camera that needs to switch to night mode (black and white) when the environmental light falls below a certain lux level. By applying these specially trained AI algorithms, that same camera would be able to stay in color mode and at full frame rate--even at night. This has many advantages, including the ability to see much farther than a typical external illuminator would normally allow, and reduced power consumption. ‘Straight to cloud’ architecture For the cameras themselves, going to the cloud or to a video management system (VMS) might seem like it doesn’t matter, as this is all just streaming video. However, the reality is more complex; especially for cameras going directly to the cloud. When cameras stream to the cloud, there is usually a mix of local, on-camera storage and streaming, in order to save on bandwidth and cloud storage costs. To accomplish this hybrid approach, multiple video-encoding qualities/resolutions are being produced and sent to different places at the same time; and the camera’s AI algorithms are constantly running to optimize bitrates and orchestrate those different video streams. The ability to support all these different streams, in parallel, and to encode them at the lowest bitrate possible, is usually guided by AI algorithms that are constantly analyzing the video feeds. These are just some of the key components needed to accommodate this “straight to cloud” architecture. Keeping cybersecurity top-of-mind Ambarella’s SoCs always implement the latest security mechanisms, both hardware and software Ambarella’s SoCs always implement the latest security mechanisms, both in hardware and software. They accomplish this through a mix of well-known security features, such as ARM trust zones and encryption algorithms, and also by adding another layer of proprietary mechanisms with things like dynamic random access memory (DRAM) scrambling and key management policies. “We take these measures because cybersecurity is of utmost importance when you design an SoC targeted to go into millions of security cameras across the globe,” says Gigot. ‘Eyes of the world’ – and more brains Cameras are “the eyes of the world,” and visual sensors provide the largest portion of that information, by far, compared to other types of sensors. With AI, most security cameras now have a brain behind those eyes. As such, security cameras have the ability to morph from just a reactive and security-focused apparatus to a global sensing infrastructure that can do everything from regulating the AC in offices based on occupancy, to detecting forest fires before anyone sees them, to following weather and world events. AI is the essential ingredient for the innovation that is bringing all those new applications to life, and hopefully leading to a safer and better world.
Collaboration among manufacturers in the physical security industry can result in systems that are easier to install for integrators and that provide a better customer experience for end users. Illustrating the point is the recent collaboration among a turnstile technology company, a supplier of short-range wireless readers/writers, and a biometric business focused on ‘frictionless’ access control. “The more manufacturers collaborate with each other, the more benefits for end users,” says Steve Caroselli, the Chief Executive Officer (CEO) of Orion Entrance Control. Better collaboration means a better user experience We look for opportunities to collaborate and make sure the experience is above and beyond" Steve Caroselli adds, “Better collaboration means a better user experience. We look for opportunities to collaborate and make sure the experience is above and beyond.” Orion’s collaboration with ELATEC RFID Systems and SAFR touchless biometrics by RealNetworks Inc. highlights the advantages of manufacturers working together to ensure technologies operate smoothly in the real world. Taking ownership of the customer experience When Orion Entrance Control provides a SpeedGate swing-glass optical turnstile, they take full ownership of the customer’s experience. That means ensuring the turnstile application operates as it should, regardless of which component of the broader system might be at fault. To the customer experience, a card reader that doesn’t work is the equivalent of a turnstile that doesn’t work. Which component is at fault is irrelevant, and in fact, invisible, to the overall customer experience. Importance of dependable operation of turnstiles As the most visible element in many access control systems, dependable operation of turnstiles reflects positively on the manufacturer and on the entire system. Orion tests various third-party components with their turnstiles To ensure an optimum customer experience, Orion tests various third-party components with their turnstiles, in order to ensure flawless operation before a turnstile is delivered to a customer. Customers buying an Orion turnstile send the card readers they want to use to Orion’s corporate headquarters in Laconia, New Hampshire, USA, where Orion engineers ensure seamless operation. Ensuring optimum customer experience All readers are designed to be bolted to the wall rather than installed inside a turnstile In addition to scenario-based testing, readers are placed inside the turnstile for a streamline appearance, which can be a challenge given the variety of sizes and types of readers a customer might choose. All readers are designed to be bolted to the wall rather than installed inside a turnstile, which complicates adaptation efforts. In short, historically for Orion, ensuring the optimum customer experience involved extra time and effort, although obviously it was worth it. Providing flexibility for any environment Seeking to simplify the process, Orion has found an alternative to using many different types and models of card readers for its turnstiles. Deploying an RFID reader/writer from ELATEC provides flexibility to operate in a variety of card and reader environments, including almost all 125 kHz and 13.56 MHz contactless technologies. The product is compatible with low-frequency (LF), high-frequency (HF), near field communication (NFC) or Bluetooth Low Energy (BLE) signals. An integrated BLE module supports mobile ID and authentication solutions. There is an integrated antenna for LF and HF to ensure excellent contactless performance. ‘Universal’ configuration of the ELATEC reader hardware Using applicable firmware, the ‘universal’ configuration of the ELATEC reader hardware is compatible with any card system. It works with all the access control protocols, including SEOS, OSDP and other open protocols. “We can stock an open SKU and flash the firmware as per the customer requirement,” says Steve Caroselli. The small form factor (around 1 1/2 inches square) of the ELATEC module lends itself to easy installation inside the turnstile housing. Easy availability of the ELATEC readers helps Orion continue to serve customers, despite recent disruptions in the supply chain. And, ELATEC’s reader hardware has earned global certifications that enable Orion to use their products for customers around the world. Testing to ensure smooth operation ELATEC was responsive at every stage as the relationship evolved, providing sample equipment for testing Before embracing the ELATEC reader module, Orion tested it for several months to ensure compatibility with its turnstiles. ELATEC was responsive at every stage as the relationship evolved, providing sample equipment for testing and working closely with the Orion team. Everyone in the ELATEC sales and engineering team, right up the company’s C-suite, worked to support Orion during the testing phase. In the end, in addition to other advantages, ELATEC’s detection speed and read range compares favorably to competing technologies. “We move really fast as an organization, so we are looking for other organizations that move very fast,” says Steve Caroselli, adding “We met with ELATEC one week and had the equipment for testing the next week. We like to work with companies that move fast, and they are culturally aligned with how we do business.” Orion turnstiles with ELATEC TWN4 Palon Compact panel The Orion turnstiles incorporate an ELATEC TWN4 Palon Compact panel, a versatile panel-mount reader designed for integration into third-party products and devices. It supports enhanced interfaces, especially RS-485, and reflects the advantages and integrated tool support of the ELATEC TWN4 family. Orion is implementing SAFR SCAN biometric technology using hardware and software from RealNetworks Inc. “The selection of ELATEC products allows Orion to provide their customers and partners with a flexible RFID reader solution that supports numerous credential options and virtually all transponder technologies,” said Paul Massey, the Chief Executive Officer (CEO) of ELATEC, Inc., adding “This is especially valuable in multi-tenet, multi-credential environments.” Orion works with all the various stakeholders – architects, consultants, integrators, and end users – to ensure total satisfaction with an installation. Biometric technology for ‘frictionless’ access control Orion is also implementing SAFR SCAN biometric technology into their turnstiles using hardware and software from RealNetworks Inc. The facial recognition reader technology, designed for mainstream commercial access control, provides a ‘frictionless’ experience, and allows users to pass through turnstiles at a walk. The system can authenticate up to 30 individuals per minute with 99.9% accuracy, despite varied lighting conditions. SAFR’s system provides a good user experience Orion designed a mounting system to incorporate the biometric reader into their turnstile design Orion designed a mounting system to incorporate the biometric reader into their turnstile design. SAFR’s system provides a good user experience, when it comes to enrollment. On each turnstile, the SAFR technology can operate separate from the ELATEC reader or in conjunction with it for multi-factor authentication in higher-security applications. Innovation for new applications A broad approach to the customer experience reflects Orion’s positioning as a technology company, in addition to being a manufacturer of turnstiles. Their Infinity software is the ecosystem ‘nerve center’ platform to ensure operation and connected through a single ‘pane of glass.’ The need to protect more entrances beyond the lobby led Orion to develop its recently patented DoorGuard, a LIDAR-based solution that detects each person who passes through a doorway and prevents tailgating (like a turnstile) for applications, such as stairway doors, perimeter doors, data centers, IDF closets, etc. The software mimics the advantages of a turnstile to monitor access control and occupancy. Removing friction during installation and beyond Orion’s Constellation is a presence detection system that uses UWB (ultra-wideband) radar to sense where people are in a building for emergency response and building utilization applications. “One of our core values is to remove friction and make customers’ lives easier,” says Steve Caroselli, adding “Our people-first philosophy is: What can we do to make your life better? We want to be systematic, and everything must be repeatable in terms of how we react and interact with customers.”
Case studies
Colt Technology Services (Colt), the global digital infrastructure company, released the key enterprise technology and market trends it expects to dominate the CIO agenda in 2026. Based on customer insights, market intelligence and its own proprietary research, Colt anticipates AI Inference, the evolution of NaaS to ‘NaaS 2.0’ and quantum-safe security to shape the technology landscape over the next 12 months. Ever-changing regulatory environment “CIOs will continue to face headwinds in 2026 as they balance complex business transformation programs at scale – often centered around AI – with ongoing cost-reduction programs in an ever-changing regulatory environment,” said Buddy Bayer, chief operating officer, Colt Technology Services. “But there’s huge opportunity too: AI programs are beginning to mature, digital infrastructure has greater capacity than ever before, and we’re seeing an evolution of solutions like NaaS which are reshaping our digital experiences. It’s an exciting time and, at Colt, we’re leading the way for our customers.” New ways to generate ROI from AI Businesses continue to drive major investments in AI, but ROI, value creation and monetization are proving elusive. Colt’s research finds one in five global firms spend US$750,000 annually on AI while 95% of the respondents in a recent MIT report study see no return on their investments. This misalignment between spending and measurable returns will shrink in 2026, as AI projects mature and begin to generate ROI, and as businesses find new ways to create value from AI. More vendors will build in AI maturity assessments and structured ROI models to help businesses define, track and quantify value across their AI tools. AI inference and Agentic AI 2026 will see AI inferencing reaching the next level of maturity, shifting from experimentation to integration into the enterprise IT environment, extracting insight, making predictions, and enabling smarter, context-aware decisions in real-time. McKinsey expects AI inference to account for a majority of AI workloads by 2030. This won’t just be limited to enterprises: Agentic AI, driven by inference, will be the force behind the automation and digitalization of day-to-day consumer tasks from privacy management and healthcare to scheduling assistance and management of household chores, according to research from the IEEE. AI Wide Area Networking (WAN) Many of Colt’s conversations with customers center around digital infrastructure’s ability to manage and optimize the performance, latency and security needed for AI workloads. AI WAN moves the conversation towards software-driven wide area networks, built for AI workloads, which dynamically manage AI traffic for peak performance and ensure application-level security of critical data. Innovation in sustainable networking technologies Similarly, AI workloads transmitted over transatlantic cables will grow in 2026 and are projected to surge from just 8% of total capacity in 2025 to 30% by 20351, placing additional strain on global network routes. Innovative tech trials and global partnerships are pioneering technologies which boost performance without increasing energy consumption or carbon emissions. Sovereign AI As nations grow their AI investments and regulations around AI governance come into force across many of the world’s major economies, sovereign AI is gaining momentum. It will rise up the CIO’s agenda as countries and organizations build and run their own AI systems using their own data, infrastructure, people, and rules. Sovereign AI is becoming more prevalent and increasingly important as nations look to stay in control of their technology, protect their data, and stay resilient in a world increasingly shaped by AI. NaaS 2.0 The NaaS market continues to grow, driven by a number of factors from AI, edge computing and cloud adoption to enterprises’ need to build in flexibility as they navigate dynamic global markets. Colt research found 58% of the 1500 CIOs it questioned said they were increasing their use of NaaS features due to growing AI demands. In 2026 and beyond, people will see NaaS evolve to meet the demands of the AI era, moving beyond its traditional role in supporting digital experiences. The next generation of NaaS will be intelligent, automated, and outcome-focused, designed to deliver real-time performance, adaptability, and autonomy for AI-driven enterprises. Quantum security Rise in quantum security investment as Q Day gets nearer CIOs are under constant pressure to protect their data and infrastructure from emerging risk, and as governments and businesses develop a deeper understanding of quantum’s power and potential, attention and investment turn to quantum security. In its 2026 Technology and Security Predictions report2, Forrester forecasts that quantum security spending will exceed 5% of enterprises’ overall IT budget next year, while a report from The Quantum Insider estimates the quantum security market to grow at over 50% CAGR to 2030, reaching $10 billion. Traditional data cryptography methods are at risk of being deciphered by quantum computers. The point at when this happens is known as Q Day, and latest estimates suggest it could come as soon as 2030. Technologies such as post-quantum cryptography (PQC) and quantum key distribution (QKD) protect traffic from this risk as it travels across a network. 2026 will bring developments, trials and innovation in protecting data from quantum risk. Low Earth Orbit technologies – and quantum 2026 is set to be a breakthrough year for Low Earth Orbit satellites, with organizations launching new satellites and new services. These services are a vital part of global telecoms infrastructure, providing connectivity in underserved or rural areas, and providing resiliency to businesses looking for back-up options for their enterprise infrastructure. Colt is looking to trial low earth orbit satellite connectivity for quantum key distribution: this will enable secure and protected exchange of symmetric encryption keys using quantum technology, while overcoming the distance limitations of terrestrial connectivity. 2026 will see Colt and partners trialing space-based and subsea techniques which extend quantum security to global networks. Hybrid cloud computing models 2026 will see multi cloud models becoming the default, as enterprises look for more ways to build in flexibility and resilience to their infrastructure and move beyond single-provider strategies. Increasingly, APIs and secure interconnects between providers and hyperscalers are streamlined, complementary and competitive in pricing terms and accessible through aggregators. Edge computing will continue to grow through 2026 and beyond, driven by factors such as AI inference expansion, the rise in real-time analytics, and increasing data sovereignty requirements. Next-generation cloud providers Next-generation cloud providers are prioritizing deployment of infrastructure at the edge, processing data closer to where it’s generated, while hyperscalers focus on scale and compute power in centralized locations. Both strategies are needed and complementary: Edge requires highly distributed, localized infrastructure which complements centralized cloud, used for heavy compute and storage. As demand for Edge grows in 2026 and beyond – one forecast estimates a CAGR of 33.0% from 2025 to 2033 - expect rising demand for distributed architectures across new geographies. Tighter regulatory frameworks In 2026, expect to see a slew of reporting obligations, regulations, strategies and guidelines impacting CIOs, particularly in AI and cybersecurity. Most of the obligations under the EU AI Act will apply from 2 August 2026, while implementation of certain requirements for high-risk AI systems may be postponed. Reporting obligations for the EU Cyber Resilience Act are expected from September 2026, with phased obligations continuing from September 2026 onward under the EU Data Act. Cyber Security and Resilience Bill Peolpe also see the ISO/IEC 42001:2023 global standard for AI governance, which will lead CIOs and CAIOs to integrate AI governance into enterprise architecture and procurement decisions, as well as operational impacts for the Digital Services Act and the Digital Markets Act. In the UK, all eyes will be on the Cyber Security and Resilience Bill, while across Asia, Japan will see the impact of its AI Promotion Act and major initiatives following Singapore’s National AI Strategy 2.0 (NAIS 2.0) are also expected to come into effect in 2026.
In recent years, campus safety and student mental health have drawn growing attention. Government data in Taiwan show a rise in emotional and stress-related issues among students aged 15–24. Unauthorized attempts to enter campuses still occur, unsettling students and staff. Strengthening security management and proactive alerting has therefore become a priority for schools. To address risks such as expansive campuses, multiple entry points, blind spots, and potential intrusions, VIVOTEK (3454-TW), the leading global security solution provider, has been promoting its AI-driven education security solutions, designed to proactively detect risks and safeguard school environments. Era of real-time detection and proactive response According to a report by research firm GII, the global education security market is projected to reach USD 910 million in 2025 and grow to USD 1.6 billion by 2030, representing a compound annual growth rate (CAGR) of 11.96%. As AI video analytics, edge computing, and cloud management platforms mature, security systems are evolving beyond passive video playback into an era of real-time detection and proactive response. In education settings, AI can automatically detect intrusions into restricted zones and trigger instant alerts, enabling security personnel to make swift and informed decisions. VSS Pro platform Recently, VIVOTEK deployed a comprehensive education security solutions at a renowned national university in Taiwan, installing hundreds of AI Bullet and Fixed Dome cameras across entrances, rooftops, classrooms, corridors, walls, elevators, and parking areas. Integrated with the VAST Security Station (VSS) Pro platform, the system delivers: Proactive prevention: AI virtual fence defines restricted zones, detects loitering, notifies the security center, triggers on-site audio alerts, and coordinates real-time response. Efficient investigations: Broad coverage flags abandoned objects, while AI deep search traces intruders or vehicles in the shortest time using attributes (e.g., clothing color, backpack, vehicle type) to quickly assemble event timelines. VIVOTEK’s education security solutions With comprehensive, AI-enabled coverage, schools can monitor in real time and avert risks, fostering safe, welcoming, and sustainable learning environment. Beyond Taiwan, VIVOTEK’s education security solutions are also used in the United States, Belgium, and Indonesia, tailored to local needs to build a global network of smart, sustainable campuses.
When major fire and security specialists Cornerstone were appointed to deliver the life safety systems for the refurbishment of 77 Grosvenor Street, they faced a unique challenge. Located in the heart of London’s Mayfair district, the prestigious building features classical architecture and over 50,000 square feet of premium open-plan office space spread across six floors. The goal was to upgrade the fire protection without compromising the building’s refined aesthetics. The client, a major property management company, required a solution that was robust, reliable and unobtrusive. Working closely with the design and construction teams, Cornerstone turned to Hochiki Europe, a long-standing partner known for dependable systems that blend seamlessly into high-end environments. Latitude fire detection and alarm control system At the core of the installation is the Latitude fire detection and alarm control system. Chosen for its powerful cause and effect programming, flexible networking and modular scalability, Latitude was well suited to the demands of a multi-level heritage building. Its ability to support complex configurations made it ideal for a site where multiple zones, floors and room functions needed to be managed with precision. To deliver complete protection across the site, Cornerstone selected a combination of Hochiki's Enhanced System Protocol (ESP) addressable devices and the FIRElink aspirating detection system. The FIRElink system is adaptable to a broad range of environments and applications. ESP detectors From small, to very large areas, the system is particularly useful in protecting computer rooms or data centers but can be designed to fit almost any environment. ESP detectors offer high performance with a minimal visual footprint, ideal for preserving the character of the restored interiors. In areas requiring an even more discreet solution, such as decorative ceilings or high airflow zones, FIRElink was installed using capillary sampling pipes hidden within the building’s structure. One of the key advantages of the Latitude platform is its ability to interface with wider building management systems (BMS). At Grosvenor Street, this opens the door to centralized monitoring and control of fire safety in conjunction with other building systems. Open integration Latitude’s open integration options mean it can share status updates and alarm events in real time with the BMS, enabling facilities teams to coordinate responses quickly and efficiently. For a high-spec office environment, this not only improves safety outcomes but also supports smoother day-to-day operation and building performance. Patrick Anthony, Project Manager at Cornerstone, explained the decision: “We have a trusted relationship with the Hochiki team. Their systems and devices are reliable, help reduce false alarms and are designed to aesthetically fade into the background, exactly what this project needed and delivers complete peace of mind for the management team.” The site at Grosvenor Street is now protected by a fully integrated, future proof life safety system that meets modern building safety standards while maintaining the building’s elegance.
3xLOGIC, Inc., a major provider of integrated, intelligent security solutions, and a three-time Deloitte Technology Fast 500 winner, announced that Panda Restaurant Group, Inc. (parent of Panda Express, Panda Inn, and Hibachi-San) has completed deployment of 3xLOGIC’s VIGIL Trends Business Intelligence software to all of its North American locations. Interface Security Systems, headquartered in St. Louis, Missouri, is the integrator and overall project manager for this ambitious endeavor. Largest family-owned restaurant Panda Express is the largest family-owned restaurant in America, with more than 2,000 stores globally, 35,000 associates and $3 billion in sales. Since it was established in 1983, Panda has steadily grown with roughly 125 stores opening each year. Privately owned and operated, the restaurant is guided by the core values of its co-founders and co-CEO, Andrew and Peggy Cherng and is dedicated to developing its team members and giving back to the community. Business intelligence solutions “As an industry leader, Panda Express’s culture sets an expectation of best-in-class results,” explained Lyle Forcum, executive director of asset protection at Panda Express. “Accordingly, we needed a state-of-the-art business intelligence solution to provide us with truly actionable information. Intelligence we can act on is central to Panda’s business strategy, which focuses on meeting high standards through continuous operational improvement.” Starting in August 2017, 3xLOGIC and Interface Systems worked with Panda Express to customize Trends to meet the company’s unique, comprehensive needs. Interface began system deployment in QI 2018 with the first location going live in March 2018. Presently, Trends is deployed at 1,960 locations and has been integrated with existing Interface video surveillance and alarm systems. Tracking and improving operations “It was impressive that we were able to integrate Trends so seamlessly with existing intrusion and video systems,” said Sean Foley, senior vice president of national accounts at Interface Systems, “and the entire solution was rolled out without a single technician visiting any store.” Unlike many retail BI implementations, the focus at Panda Restaurant Group is not solely on retail loss prevention, but also on tracking and improving all operations at every store. Here are some of the key elements of store operations that Trends enables Panda to monitor, track, and improve: People Development: To set its people up for success, store managers are able to review all transactional behavior and address opportunity areas with employees within two days. Comparing Store Performance: The store managers’ Trends dashboard shows very clearly how the restaurant is performing compared to other stores in the region and to their prior month’s performance. Optimizing Store Efficiency: Trends visually displays how many people are working per hour, what job they are facilitating, and the revenue generated per hour. Monitoring Intrusion Data: Trends provides intrusion data, which shows in a very simple display when stores are opened and closed, deliveries are made, cleaning is done, and whether the store is being remotely armed and disarmed. Tracking Cash: Panda Express can track currency, how much is in the safe and when it was last counted, as well as petty cash spend along with scanned receipts for purchases. Custom Dashboards: The system provides an array of dashboards for all levels in the organization that give an at-a-glance or drilled-down overview of an employee’s priorities and responsibilities. “At Panda, safety and loss prevention are key priorities in executing great operations,” said Lyle Forcum, executive director of asset protection at Panda Express. “We worked with 3xLOGIC and Interface for over a year to implement a highly-customized solution to meet these priorities. Now, we have a cutting-edge tool deployed across the entire enterprise that we can all be proud of.”
Allied Universal®, the world’s pioneering security and facility services provider, has been selected by Seton Hall University™ to provide campus security programs. This moves strengthens the University’s commitment to providing a safe, secure, and welcoming environment for students, faculty, staff, and visitors. New security program Allied Universal will deliver comprehensive campus security services, including trained personnel, safety patrols, and emergency response support. The new security program is designed to enhance the University’s existing safety infrastructure, while helping to ensure that the campus community benefits from Allied Universal’s expertise in proactive risk management and security operations. New partnership “On behalf of Allied Universal, I want to express our sincere appreciation for this new partnership and for our shared commitment to creating a safer campus community,” said Steve Jones, Allied Universal Global Chairman and CEO. He adds, “As the pioneering security provider for higher education, we are excited to have been chosen to work with Seton Hall University as a higher education campus safety partner.” Seton Hall’s ongoing commitment The selection of Allied Universal builds on Seton Hall’s ongoing commitment to campus safety, combining the University’s strong public safety framework with Allied Universal’s proven expertise in higher education security. Together, the collaboration aims to provide a proactive, community-focused approach that reinforces a secure, welcoming environment for everyone on campus. Seton Hall’s mission “Allied Universal brings deep experience supporting higher education institutions across the country,” said Sergio Oliva, Associate Vice President for Public Safety and Security, adding “Their approach emphasises professionalism, training, and engagement with the communities they serve, values that align closely with Seton Hall’s mission and our own Public Safety philosophy.”
Cognitec Systems Pty Ltd is working with Home Affairs Australia to deliver 250 camera devices for facial image capture, image quality check, and traveler identity verification at all major international airports in Australia. With approximately 41 million international travelers entering and leaving Australia each year, the Department uses facial biometrics to collect and electronically verify the identity of eligible international travelers. Cognitec hardware and software systems Cognitec’s capture device, FaceVACS-Entry, detects the person’s height, automatically adjusts the camera position to capture a frontal pose photo, and uses automated face recognition to verify person identity. Cognitec is also providing integration software, mounting hardware, device installation services, as well as ongoing support and maintenance services for all Cognitec hardware and software systems. Relationship with the Department of Home Affairs “Cognitec is proud to continue a successful relationship with the Department of Home Affairs, and to deliver our technology for quick collection of biometric photos and for accurate traveler verification at the Australian border primary lines,” says Terry Hartmann, Cognitec’s Vice President Asia Pacific, adding “This project contributes to the security and ongoing digitization of the Australian border, ensuring trusted traveler identities.” FaceVACS-Entry is used by governments worldwide for applications that require the acquisition of standards-compliant photos, and the verification of a live image against reference images, such as access control, border control, and entry/exit programs.


Products


Round table discussion
To serve various vertical markets and industries effectively, security professionals must recognize that each sector has unique assets, risks, compliance requirements, and operational needs. Instead of offering a one-size-fits-all solution, security system providers must tailor their products, services, and integration strategies to address the distinct requirements of vertical markets. We asked our Expert Panel Roundtable: Which vertical markets have the greatest growth potential for physical security systems?
Transportation systems need robust physical security to protect human life, to ensure economic stability, and to maintain national security. Because transportation involves moving large numbers of people and critical goods across vast, often interconnected infrastructure, it presents a highly attractive target for various threats. More threats equate to a greater need for security. We asked our Expert Panel Roundtable: What are the emerging applications of physical security in the transportation market?
Installing physical security systems requires integrating diverse technologies (e.g., cameras, access control, alarms) that often use different protocols and must be adapted to a building's unique physical layout and legacy infrastructure. Specialized technical expertise is required for seamless networking and proper configuration. Hopefully, no important factors are overlooked in the installation process. We asked our Expert Panel Roundtable: What is the most overlooked factor when installing physical security systems?
White papers

Aligning Physical And Cyber Defence For Total Protection
Download
The Power Of Integration In Physical Security Systems
Download
The Ultimate Guide To Mastering Key Control
Download
7 Proven Solutions For Law Enforcement Key Control And Asset Management
Download
Physical Access Control
Download
The Key To Unlocking K12 School Safety Grants
Download
Security Practices For Hotels
Download
Precision And Intelligence: LiDAR's Role In Modern Security Ecosystems
Download
Integrating IT & Physical Security Teams
Download
2024 Trends In Video Surveillance
Download
Securing Data Centers: Varied Technologies And Exacting Demands
Download
How To Create A Successful Physical Security Roadmap
Download
Best Practices For Asset Management
Download
5 Easy Steps To An Upgraded Video Surveillance System
Download
The Top 4 Reasons To Upgrade Physical Security With The Cloud
Download