Johnson Controls Limited Access Controllers (3)
Browse Access Controllers
- Controller Type
- Networkable
- Standalone
- Standalone/Networkable
- Other Johnson Controls Limited products
- Johnson Controls Limited Access control readers
- Johnson Controls Limited Access control systems & kits
Access control controller products updated recently
Access control controllers - Expert commentary

In this article, Peter Jackson, Managing Director at Jacksons Fencing, emphasizes the significance of implementing and upholding robust security measures, highlighting their role i...

A study found that over 80% of smartphones have biometric protection enabled, up from 68% a few years ago - these statistics alone show the trajectory of biometric security solutio...

RFID and emerging mobile access technologies are easy to implement and allow elevator access to be integrated with other access control solutions throughout the building, from buil...
Latest Johnson Controls, Inc. news

At GSX 2024, the Physical Security Interoperability Alliance (PSIA) will show an expanded roster of devices supporting its Public Key Open Credential (PKOC) specification. PSIA wil...

There is no shortage of threats facing security professionals, including some that are new and emerging. Understanding various new threats allows individuals and organizations to t...

The Orange County Emergency Services, Public Safety Communications Division became the 146th Emergency Communications Center (ECC) in the United States and the 14th ECC in the Stat...
Related white papers
Cybersecurity in Keyless Access Management
Three Essential Reasons To Upgrade Your Access Control Technology In 2022
Securing Unmanned Infrastructure at the Network Edge
Mobile access articles
Zenitel, a provider of intelligent communication solutions, announced the launch of two new door entry intercoms: the Turbine Extended Intercoms TEIV1+ and the TEIV4+. The new products display Zenite...
Physical security is essential for a modern production facility, users don’t want just anyone entering the building or accessing secure areas. But what about production machinery? Machine authe...
ASSA ABLOY Opening Solutions returns to Global Security Exchange (GSX) for 2024's powerhouse get-together of security professionals from around the world. Digital access control Attendees can visit...
Salient announced CompleteView v7.5, the latest update to its industry-leading video management platform. This version introduces improvements to operator experiences as well as major new enterprise c...
Munich’s Hofbräuhaus enjoys an iconic status, as both a heritage property and a spiritual home for lovers of German beer. “In this historic building is the world’s most famous t...
Radiofrequency (RF) technology specialists, SPX Communication Technologies launched Evenlode Lite, an entry-level video downlink system designed for regions new to airborne surveillance or those looki...
Wavelynx Technologies, a trailblazer in advanced, secure, and versatile reader and credential solutions, announced the launch of its industry-first app, Configure by Wavelynx, to revolutionize th...
HID, a worldwide pioneer in trusted identity solutions, announces the expansion of its signature line of Signo™ Readers to include models that meet varying customer needs – from harsh cond...
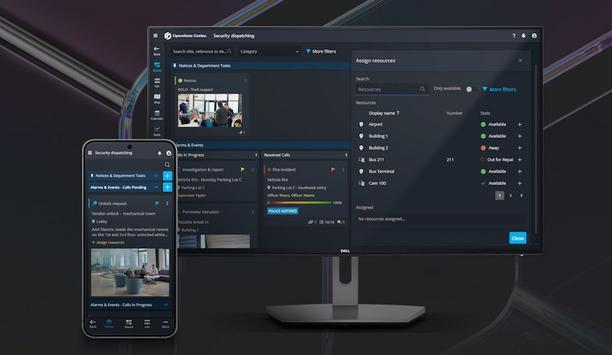
Genetec Inc., a pioneering technology provider of unified security, public safety, operations, and business intelligence solutions, announced the launch of Operations Center, a cloud-based work m...
Hanwha Vision, the global vision solution provider, has released the XRN-426S-1T recorder - a compact NVR with a built-in 1TB solid-state drive (SSD). The 4-channel recorder supports AI search, when...
Fences, gates, storage cages, racks, containers, tool cabinets, and other non-standard openings often require restricted access and greater control. In many cases, they are secured with mechanical loc...
IDEMIA Public Security North America, the global provider of convenient and trusted biometric-based solutions, including physical and digital secure credentialing in the U.S, is partnering with My Fam...
Wireless access control company, CellGate, has just announced a full family of digital Virtual Key options for Watchman® W480, W482, W461, W462, WXL and WXL2 multi-family models. CellGate’s...
ABLOY rose to the top of the list as Finland’s most valued brand of 2024, according to an annual survey by pollster Taloustutkimus. Market research company - Taloustutkimus surveys Finnish consu...
Signo Express and Seos Essentials provide a comprehensive, affordable access control solution designed for small to mid-sized businesses. This suite maximizes security and flexibility without complex...
Healthcare security articles
Rapid technological advancement, artificial intelligence (AI) and machine learning (ML) are revolutionizing traditional on-premises video security systems. These next-level tools are not just enhancin...
Milestone Systems, a global pioneer in video technology, is at the forefront of the video security industry, emphasizing responsible technology innovation across its operations. The company will host...
As the backbone of community welfare, healthcare facilities cater to crucial public needs from emergency care to specialized medical treatments, and due to its position as a significant facet of the w...
Rhombus, a pioneer in cloud-managed physical security, announced the availability of two additions to its comprehensive lineup of security solutions: the R600 Multisensor Camera and the E50 Envir...
HID®, a worldwide pioneer in trusted identity solutions announces the launch of the next-generation FARGO® HDP5000e designed to deliver vibrant, high-definition cards and IDs. HID's Isaac You...
Suprema, a global pioneer of AI-based security solutions, announces that its products and services are fully compliant with the latest global data protection regulations and security certifications.&n...
Cyber resilience research commissioned by Cohesity, a pioneer in AI-powered data security, reveals the true cost of ransomware to finances and business operations and why overconfidence may be the cau...
Genetec Inc., a pioneering technology provider of unified security, public safety, operations, and business intelligence solutions, announced the launch of Genetec Cloudlink™ 110, the lates...
i-PRO Co., Ltd. (formerly Panasonic Security), a global pioneer in professional security solutions for video protection and public safety announced the establishment of a comprehensive AI governance f...
Gcore, the global edge AI, cloud, network, and security solutions provider announced the launch of Gcore WAAP, its end-to-end web application and API protection solution. Gcore WAAP Leveraging advan...
Barco, a global pioneer in visualization and collaboration solutions, is proud to announce its pivotal role in shaping the visitor experience for the Belgian pavilion at Expo 2025 in Osaka. Bar...
King Faisal Specialist Hospital & Research Center (KFSHRC) is at the forefront of the healthcare AI revolution. Since 2019, the hospital's dedicated AI center has been developing innovative applic...
Convergint, a global pioneer in service-based systems integration, today announced that it has acquired Esscoe, a premier provider of mission-critical security and fire and life safety systems in the...
Huffmaster Management (Huffmaster), the provider of choice for Fortune 500 companies seeking strike services, industrial and healthcare staffing, security services, and more, announced the intern...
Genetec Inc., a pioneering technology provider of unified security, public safety, operations, and business intelligence solutions, announced the introduction of a new I/O module to its portfolio of h...
The Security Challenges Of Data Centers
DownloadSecurity Practices For Hotels
DownloadAccess Control System Planning Phase 2
DownloadSIA Identity and Biometrics Symposium
DownloadGunshot Detection
Download- ASSA ABLOY eCLIQ: Secure Access At Hofbräuhaus Munich
- AMPELMANN GmbH Boosts Security With ASSA ABLOY eCLIQ Solution
- Anviz Transforms Traditional Property Management Into A Smart Reality, Making Digitization More Than Just Talk
- Matrix's COSEC VYOM, A Cloud-Based Attendance System, Enhances Efficiency Across Various Locations For A UK-Based Indian Multinational Public Sector Bank