PCSC Access Control Accessories (1)
Browse Access Control Accessories
Access control accessory products updated recently
Access control accessories - Expert commentary

RFID and emerging mobile access technologies are easy to implement and allow elevator access to be integrated with other access control solutions throughout the building, from buil...

While the foundation of autonomous retail has been built up over the past few years, it is only now that retailers are beginning to fully experiment with the technology. There were...

From analog to digital, from stand-alone to interlinked, building systems are in a state of transition. Moreover, the rate of change shows no sign of slowing, which can make it dif...
Latest PCSC news

PCSC, a designer and manufacturer of access control solutions and Coolfire Solutions, a St. Louis based software company known for creating Military-Grade situational awareness pla...

The BioConnect Identity Platform provides an integration of Suprema's biometric solutions with the majority of leading access control systems BioConnect and Sup...

Systems may be reliable and performing as originally intended, but can also beoutdated in comparison to current technology offerings Let’s start by defini...
Related white papers
Three Essential Reasons To Upgrade Your Access Control Technology In 2022
10 Top Insights In Access, Cloud And More
Protecting Dormitory Residents and Assets
Mobile access articles
Zenitel, a provider of intelligent communication solutions, announced the launch of two new door entry intercoms: the Turbine Extended Intercoms TEIV1+ and the TEIV4+. The new products display Zenite...
Physical security is essential for a modern production facility, users don’t want just anyone entering the building or accessing secure areas. But what about production machinery? Machine authe...
Sonatype, the end-to-end software supply chain security platform, announced that Sonatype SBOM Manager, its Enterprise-Class Software Bill of Materials (SBOM) solution, and its pre-eminent artifa...
Appdome, the mobile app economy’s one-stop shop for mobile defense, announced it has enhanced its award-winning Geo-Fraud Detection service to include two new defenses: Geo-Location Fencing and...
RecFaces, a provider of advanced facial biometric software, announces the release of its new white paper titled - 'Facial Recognition Systems in Securing Critical Infrastructure'. The whi...
Zenitel, the supplier of intelligent critical communication solutions, announces that it is a full member of ONVIF, an organization that provides and promotes standardized interfaces for effectiv...
Brothers Fire & Security has been selected as a preferred vendor for the State of Minnesota to furnish and install and service card access control systems for all its buildings. This accomplishme...
Following the publication of the EC’s White Paper "How to master Europe's digital infrastructure" Euralarm is emphasizing the potential risks and challenges associated with an uncoordinated and...
While the transformative capabilities of AI have captured the global consciousness, the sustainability of its usage is one such topic that has been slow to attract attention. Due to the intense comp...
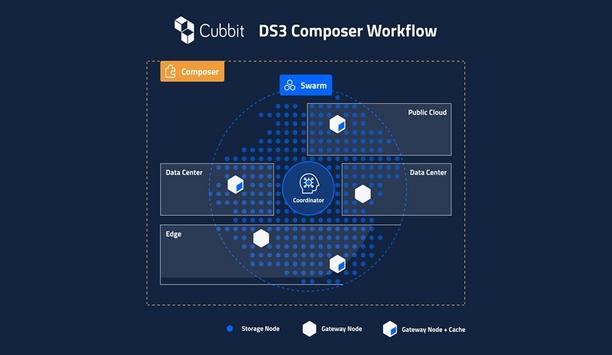
Cubbit, the first geo-distributed cloud storage enabler announced the closing of its $12.5M funding round. With this new funding, the company will enable European Service Providers and Companies to t...
HID®, a pioneer in trusted identity solutions announced an extended partnership with its trusted partner Inner Range, a global provider of integrated access control systems and solutions, to offer...
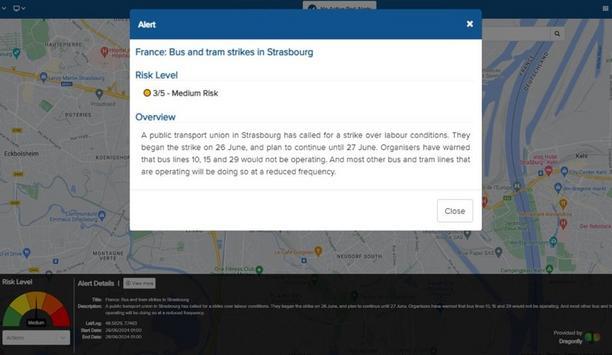
Dragonfly and Vismo announce an integration partnership by which intelligence from Dragonfly’s Security Intelligence & Analysis Service will be available through the Vismo platform. Vismo...
Arcserve, a major data protection and recovery software company, has been recognized for its excellence in SaaS backup, being named Cloud Backup Company of the Year at the Storage Awards 2024. The aw...
RiverSafe, a global cybersecurity, DevOps, and AppSec professional services provider, has partnered with education-based charity - World Vision to improve access to education for children in Africa....
Landsec, one of the UK’s commercial real estate companies, is launching an optimized Landsec Experience app across its entire London portfolio of prime workplaces using Smart Spaces’ smart...
Healthcare security articles
Milestone Systems, a global pioneer in video technology, is at the forefront of the video security industry, emphasizing responsible technology innovation across its operations. The company will host...
Just like fighting against the spread of disease in a clinical environment, healthcare providers must mobilize, coordinate with interconnected partners, and apply sufficient budgetary resources to com...
iDenfy, a Lithuania-based AI-powered identity verification, fraud prevention and compliance tool provider, has partnered with Transparent Care, an American-based innovative healthcare staffing platfor...
Carlisle Support Services appoints public and private security expert, John Lambert as Managing Director of Security and Events in the North. With a background that stems across 15 years within the pu...
Security applications for drones have evolved to provide benefits such as bird's-eye views of large areas, easy access to remote locations, and rapid deployment. However, to date, most drone applicati...
Check Point Research (CPR) releases new data on Q2 2024 cyber attack trends. The data is segmented by global volume, industry, and geography. These cyber attack numbers were driven by a variety of re...
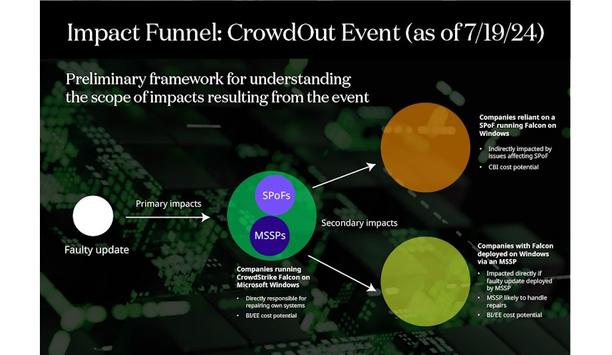
The faulty CrowdStrike Falcon Sensor update and subsequent outage – the CrowdOut Event – underscore the potential for Single Point of Failure (SPoF) technology outages...
Synectics has increased its rapidly growing healthcare portfolio, with two more NHS trusts opting to enhance its surveillance and security management with Synergy software. Multi-phase, multi-site up...
Siemens Smart Infrastructure has expanded its Siemens Xcelerator partner ecosystem with the addition of the AI-driven field service and asset management suite from IFS, the world’s pioneering pr...
Aqua Security, the pioneer in cloud-native security revealed new research that shows how credentials, API tokens, and passkeys – collectively referred to as secrets – from organizations...
MOBOTIX ONE is an extremely robust and maintenance-free video system 'Made in Germany' that impresses with both its application-oriented design and its high-quality components: fiberglass-reinforced,...
ZeroEyes, the creators of the only AI-based gun detection video analytics platform that holds the U.S. Department of Homeland Security SAFETY Act Designation, announced a new partnership with Access T...
MOBOTIX celebrates its 25th anniversary this year. Founded on June 21st by Dr. Ralf Hinkel, Sabine Hinkel, and Klaus Borchers in 1999, MOBOTIX revolutionized the video technology market with the world...
Matrix SARVAM UCS is an enterprise-grade (SME and ENT) unified communication solution that offers collaboration, communication, messaging, and mobility. It brings diverse users from multiple location...
Being the catalysts of growth, smart cities are founded on a technology-powered infrastructure. Digitization in global economies has led the way to a transformative shift to smart security, universal...
Honeywell GARD USB Threat Report 2024
DownloadThe Role Of Artificial Intelligence To Transform Video Imaging
DownloadAccess Control System Planning Phase 1
DownloadKey Findings From The 2024 Thales Cloud Security Study
DownloadVideo Surveillance
Download- Protecting A Manufacturing Site With Incedo™ Access Control Solution
- MLA Installs Mul-T-Lock's New MTL800 Platform For Premium Protection
- Pimloc And Rhombus Partner To Protect People And The Right To Privacy In The US
- VuWall Enables Transformation Of Sports Stadium Into A Police Command Center For International G7 Summit