Articles by Larry Anderson
Acre is a company built on mergers and acquisitions (M&A). Since its founding in 2012, Acre acquired several familiar access control companies, from Vanderbilt to RS2 Technologies, Open Options to Feenics, and several others. Acre itself was acquired in 2021 by UK-based private equity firm Triton, thus launching a new chapter in the company's history. Don Joos was named the new CEO in 2022 and set about transforming Acre from a collection of acquired companies into a coherent whole (represe...
Environmental, social, and corporate governance (ESG) standards in the broader marketplace reflect a growing recognition that business needs to lead the way in addressing a range of environmental and social issues. Environmental concerns, especially as they impact climate change, are a familiar facet of business life. In addition, social concerns include human rights and equity; basically, an organization's relationships with people. Governance refers to the structure of rules, practices, and pr...
Every security system is unique, of course. Specific to each installation are the problems the customer and the integrator may experience along their journey. However, given the installation of hundreds of physical security systems, there are commonalities that occur. We asked this week’s Expert Panel Roundtable: What are the major pain points when installing a physical security system?
The return of trade shows has been an invigorating development for the security market. The morning-after reviews of this year's shows could not have been more positive. Everyone in the industry seemed to revel in the excitement and momentum as the shows decisively proclaimed: 'We're back.' Continuing that momentum into the future will depend on how well the shows adapt to changing industry trends and repeatedly reinvent themselves to be better every year. Adding feedback from GSX to our earlier...
Big Data is a persistent buzzword in the broader technology realm and in the physical security market. More every year, it seems we see a greater impact of the compilation of numerous data sources (Big Data) on our market. Smart leaders in the industry are looking at the vast opportunities that exist to leverage Big Data into greater intelligence and situational awareness. We asked this week’s Expert Panel Roundtable: What is the intersection of the security market and "big data?"
Faces captured by video cameras could be perceived as an invasion of privacy, as could images captured through residential windows or that involve private or proprietary information. Fortunately, modern video systems incorporate technological features that help avoid an inadvertent invasion of privacy, while preserving any data that may be needed by authorized persons. For the latest commentary, we turn to our Expert Panel Roundtable with this week’s question: What new features of video sy...
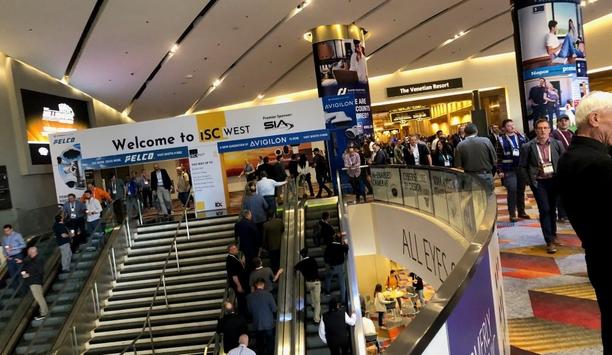
Well attended and generating levels of excitement not seen since before the pandemic, ISC West may provide just the shot of adrenaline we need to drive industry success through the uncertain economic times ahead. Buzzwords like artificial intelligence (AI) and the cloud were still prevalent at the conference and exhibition in Las Vegas, but the hype of yesteryear seemed more subdued. Rather than breakthroughs to be celebrated, AI and cloud were discussed more as ways systems can realize even g...
Challenges of the global supply chain have reverberated into the physical security marketplace in a big way in recent years. Dealers who historically could count on timely delivery of equipment have instead faced extended delays that in some cases have jeopardized their businesses. By most accounts, the situation is improving, so we turned to our Expert Panel Roundtable for an update. Our question this week: What is the current state of the physical security supply chain?
PKOC stands for Public Key Open Credential. It is a new standard that will meet a 30-year industry challenge and strip away much of the complexity and cost involved in protecting and administering credentials for access control. It could also accelerate the transition from cards to mobile access control. PKOC is a standards-based mobile credential that is essentially free, vendor-agnostic, and interoperable across multiple devices and systems. It is a highly secure access credential that can l...
Biometrics is both a mature technology in the physical security world and an innovation perpetually on the cutting edge. Biometric technologies received a boost during the COVID pandemic when “touchless” became a buzzword with particular relevancy to the world of biometrics. Higher security needs, such as “two-factor authentication,” are also driving demand for biometric products. We asked this week’s Expert Panel Roundtable: What are the latest technology trends in...
The upcoming ISC West trade show in Las Vegas will offer innumerable networking and learning opportunities for attendees. Manufacturers will take the opportunity to promote their businesses and showcase products and services to a targeted audience. Best of all, the event will be "in person," an advantage we should never again take for granted. We asked this week's Expert Panel Roundtable: What big announcements do you expect at ISC West 2023?
Some products may become obsolete faster than others, while some may have a longer life span due to ongoing innovation and demand. Technology and security threats are continuously evolving, and older security systems may no longer be effective in protecting against the latest threats. Additionally, older systems may have outdated technology, making them more vulnerable. We asked this week’s Expert Panel Roundtable: Given rapid technology development, are the lifecycles of security sy...
The economic outlook for the year ahead is uncertain at best. Multiple lingering issues are in play, such as inflation, supply chain challenges, global instability, and a changing workforce. But to what extent does a shaky economy equate to a slowdown in the security market? We asked this week’s Expert Panel Roundtable: How does the wider economic climate impact the market for security products and services?
Matter is a new open-source interoperability standard that will simplify the connectivity of smart home systems, including security. The growing popularity of the Matter 1.0 standard was evident at the large Consumer Electronics Show (CES) in January in Las Vegas, where the standard was heavily promoted by companies including Google, Amazon, and Samsung. A flood of Matter-connected products is on the horizon for ship dates in the second half of 2023. Evolve, and manage IoT standards Cr...
Some systems and assets are so vital that their incapacity or destruction would have a debilitating impact on security, economic security, public health or safety, or any combination of those factors. This so-called critical infrastructure has historically faced many complex threats. In 2023, we can add growing concerns about cybersecurity to the mix. We asked this week’s Expert Panel Roundtable: What is the largest risk to critical infrastructure in 2023? How can we address it?
There’s always more to talk about in our Expert Panel Roundtable discussions, and we appreciate the variety of opinionated responses offered throughout the year. Looking back at 2022, we found several random and uncategorized Expert Panel responses that were not previously published. We have rescued these responses from our cutting-room floor and present them here in the interest of generating even more discussion.
As much as we each seem to live in our own bubble, the reality is that everything is connected and we are all part of a greater whole. So it is with the security market, which can be both inward-focused and also play a role in the bigger societal picture. A couple of recent questions we posed to the Expert Panel Roundtable highlight how the security market can and should interact with society in general.
Intellicene is a new name in security, but not a newcomer to the industry. Intellicene is the new brand for a company with a long history. Previously known as Verint Situational Intelligence Solutions, the company spun off its cyber intelligence business in 2021, which was rebranded as Cognyte. The former Cognyte Situational Intelligence Solutions is now Intellicene. It still delivers the Symphia platform and portfolio of solutions that enable organizations to better understand and respond to m...
A multi-factor authentication is a layered approach that requires users to provide two or more verification factors, such as credentials, to gain access to data and applications. If one of the credentials is compromised, the thinking goes, an unauthorized user will still be unable to meet the second authentication requirement and will be denied access to a targeted physical space, computing device, network, or database. Cybersecurity applications have long embraced the idea of MFA, which is also...
Some trends in the security marketplace continue for several years, while others come and go quickly and are soon forgotten. Scrutinizing a trend’s expected lifespan can help predict its impact on the marketplace. Trends that evaporate seemingly overnight are not useful for the greater good, and they can also distract customers from more enduring subjects. Unfortunately, sometimes hype is just hype. We asked this week’s Expert Panel Roundtable: Which new security trend do you think w...
From lodging to food service to event planning to tourism, the hospitality market faces a large and growing range of security threats and challenges. Given the competitiveness of the market and the heightened flow of information about customer satisfaction via social media, there is more at stake than ever as hospitality professionals seek to ensure the safety and security of guests. We asked this week's Expert Panel Roundtable: What security challenges are impacting the hospitality market of to...
Security and privacy are often seen as being at odds. In effect, you must have less of one in order to get more of the other. However, newer technologies are eliminating the need to make such a difficult choice. Innovation is paving the way for greater security and protection in a climate where privacy concerns are also paramount. We asked this week’s Expert Panel Roundtable: How can security address individual privacy concerns while increasing protection?
New buzzwords were abundant in the articles that generated the most clicks on our website in 2022. From the metaverse to the Internet of Things, from frictionless access control to artificial intelligence (AI), the topics most popular among our site’s visitors were at the cutting edge of change and innovation in the physical security marketplace. Here is a review of the Top 10 Articles of 2022, based on reader clicks, including links to the original content: Metaverse will promote collab...
As cloud-based systems become more common, Video Surveillance as a Service (VSaaS) is becoming mainstream in the physical security marketplace. There are certainly benefits for manufacturers and end users, but we asked our Expert Panel Roundtable to focus on the benefits to the dealer channel. We asked this week’s Expert Panel Roundtable: What is the impact of video surveillance as a service (VSaaS) on security integrators?
Large-scale events, including both corporate and sporting events, are coming back strongly in the aftermath of the pandemic. With the increase in activity comes more demand for oversized credentials preferred by many event planners and end users. Pent-up demand due to the pandemic has caused a tremendous uptick in the entire ID card industry in 2022. The return of large-scale events and in-person trade shows will extend the higher demand for cards well into 2023 and beyond, says Andrew Schonzei...
For decades now, usernames and passwords have been a critical, and highly visible, element in data protection and cybersecurity. However, the use of passwords is a far-from-perfect approach to protecting access to computer systems. Nowadays, newer, more sophisticated forms of user identification and authentication have emerged on the scene. We asked this week’s Expert Panel Roundtable: Is the password on the brink of extinction in physical security? Why or why not?
Since they were invented, video surveillance cameras have been used mostly for security applications. However, the advent of video analytics and artificial intelligence (AI) has paved the way for use of video data in a variety of other applications, from process control to measuring occupancy to analyzing customer traffic trends. The ‘data’ aspects of ‘video data’ are feeding many new applications that no longer involve operators looking at video images on a screen. We as...
The holiday season is marked by festive spirit and family celebrations, but it is also the busiest time of year for retailers. Busy shoppers willing to spend money are an upside to the holiday shopping season, and many businesses depend on the holiday rush as a critical element to having a successful year. A downside of a busy holiday season is an increase in retail security threats including shoplifting. We asked this week’s Expert Panel Roundtable: How can technology address loss prevent...
Collaboration among manufacturers in the physical security industry can result in systems that are easier to install for integrators and that provide a better customer experience for end users. Illustrating the point is the recent collaboration among a turnstile technology company, a supplier of short-range wireless readers/writers, and a biometric business focused on ‘frictionless’ access control. “The more manufacturers collaborate with each other, the more benefits fo...
Connectivity is literally the difference between products operating individually and those combined into a more powerful system. Many of the devices that connect today’s security products reflect mature technologies that have been proven over time. However, innovation is also driving the need for new approaches to connectivity and networking. We asked this week’s Expert Panel Roundtable: What are the new developments in networking and connectivity for security?