Technology & Trends - Access control systems & kits
Small-timers with big ideas can always make their way into the industry In recent years, home automation technology has given birth to the “Smart Home” in which internet-enabled and controlled devices are bringing a new level of comfort to the standard house. From locking doors to setting the temperature to opening the blinds for a view of the sunset, technology is transforming the home into something reminiscent of the now-quaint 1960s sci-fi cartoon, The Jetsons....
Voice biometrics is fast becoming a security imperative due to increasing instances of fraud and identity theft. From identifying customers at banks and call centers to securing mobile devices in a “bring your own device” world, the use of a person’s unique “voiceprint” is fast gaining ground as an identifier. The global voice biometrics market is expected to reach $4.7 billion (U.S.) by 2020. Much of it is being driven by the increasing need to...
The key driver to growth in the IP market is the effectiveness and efficiency of the technology Technological advances in video surveillance are allowing end users the flexibility to do more with their systems than previously imagined. 2014 saw several new technological trends that shaped the future of the security market, with 4K and cyber security being the main drivers. The drift continues this year too with end users demanding HD video surveillance and wide-spread impl...
Large busy casinos must maintain continuous surveillance of multiple tables and machines High-definition (HD) cameras are a perfect fit for the casino market. HD security cameras provide six times the resolution of analog cameras, supplying images with sharper edges that easily identify faces, cards, dice, chips, currency, and fill slips. In addition, high-definition IP cameras can reduce camera count. A single, 1080p camera can effectively cover poker, roulette or craps table...
Complete Security Systems Inc., Marlboro, New Jersey, is a UL-listed central station and security installation company serving New Jersey and other East Coast areas. According to Chris Mosley, President of Complete Security Systems, attracting young people to the security industry is a challenge. Chris highlights Complete Security Systems' new products, services and training programs that have been developed to keep up with the fast-changing security industry. He admits that...
Once home automation – controlling everything from HVAC to door locks to lights to security cameras – was solely the providence of the high-end home. Custom systems were pricey – some ranging upwards of $100,000 or more. That was before widespread access to broadband internet and before everyone started carrying a powerful internet-connected mini-computer – called a smart phone – in their pocket. Home Automation Goes Mainstream These days the Smart Home has gone...
National Union Fire Insurance Company claims that Tyco failed to protect confidential details of the warehouse security systems A civil trial against Tyco Integrated Security was adjourned by a federal judge on July 14 and is now rescheduled for October 19. The lawsuit arose out of the burglary of a pharmaceutical warehouse in Enfield, Conn., owned by Eli Lilly. Eli Lilly’s insurance company, National Union Fire Insurance Company claims that Tyco failed to protect confid...
Intimate body search at airports also takes a psychological toll on the person conducting the search SourceSecurity.com's European Correspondent, Jeremy Malies gives an account of the Body Search 2015 security conference that was held at Hounslow, London. Along with emphasis on aviation security, the conference also covered an array of safety and commercial applications. Some of the topics outlined in this article include: New techniques in body scanning, the exasperation publ...
School security has increasingly become an area of focus among school boards and municipalities. Officials are constantly seeking to implement or improve security and safety policies, procedures and technologies to offer the highest level of protection for students, staff and visitors. Every second counts in an emergency or crisis, making it imperative that schools have policies and procedures in place that make it possible to lock down buildings instantly while simultaneousl...
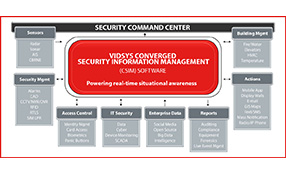
(see bigger image) The very nature of true enterprise PSIM software is that it has the capability to connect to other systems and subsystems In this article, James I. Chong, CEO & Founder of Vidsys, sheds light on true PSIM (Physical Security Information Management). He mentions how Vidsys is continually innovating and accelerating its roadmap for PSIM toward Converged Security and Information Management or CSIM. Citing various analysts’ projection, James s...
Honeywell, Twitter integration brings security communication to its life safety products Honeywell, Northford, Conn., is leveraging the Twitter social media platform to bring higher levels of situational awareness and emergency communications to its life safety products. This move focuses to improve emergency response by monitoring various security, safety or building systems and providing information to identify potential threats. Gamewell-FCI’s Focal4 Now, Gamewe...
As the home automation industry has expanded with an ever growing number of devices and services, companies are placing bets on which wireless protocols will dominate. The past few years the leaders have been Z-Wave and ZigBee. Companies are also using a variety of other standards including Crestron’s Infinet, Insteon, and proprietary technologies such as Lutron’s ClearConnect. Next-Generation Protocols: Bluetooth And Wi-Fi “Right now companies are releasing really i...
EMERgency 24 developed the Incident Command and Control platform to deliver faster and more succinct data to first responders and others At ISC West 2015 in Las Vegas, EMERgency24 introduced a groundbreaking web-based software platform called Incident Command and Control Service, which allows system owners to generate alerts for situations such as lockdown, severe weather or HAZMAT (hazardous materials) situations and enables instant communication to pre-defined contact groups...
A US Department of Homeland Security investigation showed that undercover agents defeated airport screening in 95 percent of cases by smuggling mock explosives and weapons past checkpoints. With admirable transparency, U.S. Office of Inspector General (OIG) has described how so-called “Red Teams” posed as regular passengers and exposed inadequate measures at some of the busiest airports across the United States. The revelations came a few days before Body Search 2...
All seven decision factors contribute to an effective physical security solution Installation of an effective physical security solution can enable end users to avoid serious mistakes. This article presents a comprehensive and consultative decision methodology to help end users make the best decisions about security entrance products for the long term. The decision-making process is based on Boon Edam’s more than 100 years of experience in installing thousands of entry s...
Security and technology are rushing to offer home automation solutions and build out the Smart Home of connected devices and applications. As cameras, alarms, as well as, thermostats and other appliances become controllable and programmable using Internet-enabled smart phones, they are becoming part of a vast web called the internet of things (IoT). Achieving Greater Value Through Smart Data Exchange This network of physical objects or "things" embedded with electronics, software, sensors and...
Affiliated Monitoring’s UL-Listed monitoring center with a second floor dedicated to areas for security company meetings Central monitoring stations have innovative approaches to assist security installing companies in growing their account base, adding value and boosting recurring monthly revenue (RMR). These companies do much more than simply monitor accounts – today they provide a host of services to give security installing companies the added edge in an extrem...
Biometrics is most useful as an additional level of authentication — determining that you are who you say you are Over the years, the growth of biometric security technology has faced challenges of cost and pushback from users. Prices have been higher than more traditional technologies. In addition, users did not advocate storage of their personal biometric data by employers or the government. “I believe this is changing,” says Rueben Orr, CPP, vice preside...
What does it take to be a success in the rapidly expanding home automation sector? For large and small security companies, making the jump from providing traditional security services to enabling the new Smart Home means dealing with competition. Security Firms v/s Cable And Telco Giants The market is filled with providers of all kind who want a piece of the action. In addition to security companies, cable and telco giants have all rolled out a home automation platform – usually on top o...
When it comes to protecting buildings and property, traditional methods of security—such as structural barriers, security guards, and security cameras—have their limitations. Advanced laser scanning technology can overcome many of these limitations and provide a safe, reliable, and easy-to-use solution. Overview Of Laser Scanning Technology Laser scanning technology for building security applications utilizes the time-of-flight method, in which a sensor em...
Suffering a breach is probably something that companies won’t admit to unless they must As the world has grown more and more interconnected through the Internet and company networks, cybercrime has grown at an alarming rate. According to the Federal Trade Commission, 783 businesses reported IT breaches in 2014, up 27.5 percent from 2013. “There were probably many more, but most go unreported,” says Kim Phan, of council with the Washington, D.C., law offices o...
Just how big is the home automation industry? One way to tell is by looking at the sheer number of companies – large and small—that have rushed to enter this fast-growing space. They include some of the world’s largest corporations – Apple and Google – along with the nation’s biggest cable and telecom companies – Comcast and AT&T. It includes big names in security like Honeywell and ADT. Then there are less known, but fast g...
The great increase in the amount of data is driving physical security to the cloud Physical security is migrating to the cloud — because it improves the performance of physical security technology while holding down costs. “Essentially what is happening is that physical security technologies are growing more powerful and generating more and more data,” says Steve Surfaro, business development manager and security industry liaison with Axis Communications, wh...
In the vast center of the hall almost none of the randomly shaped stands display their index number I enjoy IFSEC each year, spending three days walking the halls. I do feel frustrated by the acres of "me too" products prompting a "meh" response. So often I’m left feeling the "big news" is that hype and lies are growing and continue to drown out the truth. If companies' marketing budgets were simply given over to their product development departments, we would find thing...
Security beyond its traditional boundaries is a big theme at IFSEC 2015 The security landscape is changing. Touring exhibitors on the first day of IFSEC International in London, it seems an increasing number of vendors are offering products that go beyond what may be termed "security," offering solutions for applications such as health and safety and data collection. They are also offering more smart technology with mobile phones and tablets, and are selling smarter by tailori...
A retail banking tipping point is fast approaching with the state-side adoption of EMV technology Banking faces a challenge: to reconcile major security concerns with improving technology in order to reflect modern, mobile technology and the self-service solutions that customers have come to expect from their non-banking retail experiences. This is probably the number one issue I discuss with my bank clients. Banks need to make the technology in their branches more automated,...
This year's IFSEC International show in London will provide a reflection of the physical security industry's rapid growth, especially in the video sector, says one industry observer who is also a speaker at the show, coming up 16-18 June. “If we look at the overall trend, it is no surprise to anyone that IP is driving the growth and the future of the security business,” says Jim McHale, managing director of research company Memoori, and a speaker at IFSEC. Secur...
Managed and hosted services allow users access from a variety of connected devices It’s not about hardware anymore, although quality components are a must. Now, it’s about how technology performs. For the systems integrator, there’s also an opportunity to provide essential services to keep customers connected. As with many other businesses, the security industry is being “disrupted” and influenced by the cloud. Delivering outsourced security and...
The future will produce cost-effective solutions that can provide meaningful coverage of wide expansive areas The greatest trend in history will continue to change the world, and the physical security market. It’s called Moore’s Law. In accordance with Moore’s Law, our electronics have consistently doubled in speed, halved in size, or halved in price every two years for decades already. This trend means that our electronics, communications networks, data ne...
Integrators and end users should be aware that their definition of open might differ from those of security manufacturers Much of the buzz in the industry today about open architecture is driven by the IT world, with many security-related decisions now falling on an organization’s IT department, where true open architecture has been around for a long time. Closed systems like we’ve experienced in the security world are not just viewed as foreign to the IT world; th...
Browse expert commentaries
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
Climax Mobile Lite: Advanced Personal Emergency Response System (PERS)
Hanwha Vision OnCAFE: Cloud-Based Access Control for Modern Enterprises
Delta Scientific MP100 Portable Barricade Solution