ISC West, the world's largest security industry trade show, is just around the corner. This in-person show gathered more than 1,000 manufacturers and over 30,000 visitors from all over the world in 2019. On top of that, more than 200 brands exhibited at ISC West for the first time. This year's event promises to be just as exciting, if not more so. Let’s overview some leading security trends in video management systems development, and what's worth your time and attention at ISC West 2020.
AI analytics
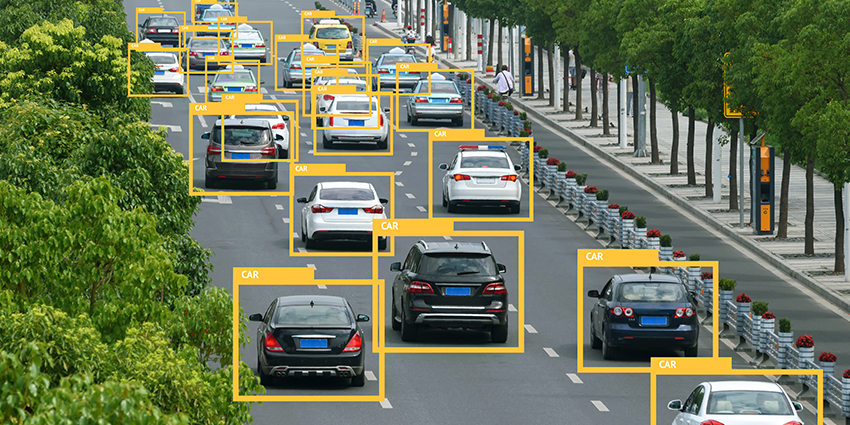
Emerging two or three years ago, the AI-based video analytics market is experiencing a boom in growth. The prototypes and ideas displayed at ISC West 2019 could This year's event promises to be just as exciting, if not more soalready be part of a functioning system today. There's a lot of hype around this new trend. So, if you're looking for solutions for your needs, it is important to be able to tell the difference between technologies that work and marketing bluster. To do that, you have to understand what today's AI-based analytics (also often referred to as a neural network, deep learning, or machine learning) can and can't do.
Let's start with what AI can't do in video surveillance. It can't analyze the sequence in which events occur or understand the 'logic' of what's happening in the scene. In other words, there's no such thing as a 'suspicious behavior detection tool'. Nevertheless, neural networks are really good at recognizing and classifying objects. For instance, they can distinguish humans from vehicles, vehicles from other moving objects, and cyclists from pedestrians.
Neural network trackers
This technology is primarily used as a neural network tracker or object tracker that can identify and track objects of a specific type. Usually, it's applied to complex scenes with a large amount of non-relevant details where a classic tracker would drown in false alarms. The neural tracker can be used to detect people in dangerous areas at production facilities, cyclists riding on pedestrian lanes, or poachers trying to sneak into a nature preserve.
Neural networks are really good at recognizing and classifying objectsObject identification function can be used for other site-specific tasks, such as detecting people without a helmet or a high-visibility vest at facilities where those are required by safety regulations. It can also be used to detect fire and smoke in open spaces, or at big premises with high ceilings or active air circulation, where common fire alarm systems can't be used or may go off too late.
Behavior analytics
Behavior analytics is another field of analytics based on artificial neural networks. Even if recognizing suspicious or inappropriate behavior is nearly impossible, it can detect risky situations based on human postures, such as an active shooter pose, raised arms, crouching, or man down. In addition to that, AI has been successfully used to perform facial and license plate recognition for quite some time now. Although these systems aren't new, their recognition quality improves each year.
Looking for solutions? You'll definitely find some interesting and new options from developers specializing in VMS and modular AI analytics at ISC West 2020.
 |
| Even if recognizing suspicious or inappropriate behavior is nearly impossible, AI can detect risky situations based on human postures |
Smart search
The ability to perform a quick, flexible search in a video archive is one of the most important features of a video surveillance system. In many ways, it's even more AI has been successfully used to perform facial and licence plate recognition for quite some time nowimportant than real-time monitoring itself. Constantly keeping an eye out for what's happening onsite is the security service's job. Medium- to large-sized companies usually have that kind of department. Meanwhile, lots of small businesses and households use video footage to investigate accidents, resolve conflicts, or analyze employee's work. They generally don't need real-time monitoring, but video search is a crucial element.
The most basic search tools offer an interface that enables easy access to recorded video and event-based search (from video analytics, detectors, etc.). Smart systems with forensic search features that allow the user to set criteria enhance the system's search capabilities even more.
How it works
VMS analyzes the video as it is recorded and saves the resulting metadata to a database. In the most basic case, the metadata contains information about motion in the scene as well as the moving object's coordinates. When searching, you can select an area of interest within the frame and take a quick look at all video segments containing motion in this area. More advanced systems save the parameters of moving objects, such as their size, color, motion speed and direction. TThe ability to perform a quick, flexible search in a video archive is one of the most important features of a video surveillance systemYou'll quickly find what you're looking for by setting more precise criteria.
The first VMS with forensic search features appeared in the early 2010s. Since then, a growing number of users and VMS developers have recognized the importance of these tools. More and more manufacturers enrich their products with forensic search features, starting from basic search by motion detection.
Integrating search functions with AI
Recently, search technologies have gone even further by integrating search functions with AI analytics. Some systems are capable to recognize all faces and number plates captured by cameras and save them to the database. You can quickly find all videos containing an image of a person or a car just by searching a photo or a number plate across multiple camera archives at a time. One usage scenario for these systems can be seen in law enforcement deploying them to find suspects using CCTV cameras around the city.
Another option for integrating smart search and AI is searching by criteria based on a neural network tracker. When you use it, you can set object's size, color, motion speed and direction in the scene, as well as object's type (such as a human or a vehicle). So, if you need to find out when a red car appeared in the surveillance area, the system will show you only red cars while ignoring other objects like people in red clothes. This technology lets you find what you're looking for even faster.
If you or your clients use VMS primarily to record video, be sure to ask the manufacturers you'll talk to at the show what search capabilities they offer.
 |
| More advanced systems save the parameters of moving objects, such as their size, color, motion speed and direction |
Hardware AI acceleration
High CPU resource consumption is one of the hardest challenges that stem from implementing a neural network–based video analytics system. This significantly decreases the number of cameras that can be connected to a server that hosts AI analytics. It also makes the system much more expensive.
AI technology lets you find what you're looking for even fasterThe solution is to use AI accelerators. GPUs and dedicated accelerator cards are used on servers to provide hardware acceleration for the neural networks' workload. These devices are mostly manufactured by Intel and NVIDIA. Intel also offers the OpenVINO™ toolkit, a software package for developers that helps distribute workload between CPU, GPU, and accelerators as effectively as possible using all available resources.
New solutions
Due to AI's growing popularity, lots of minor microchip manufacturers became interested in developing neural accelerator chips. The healthy competition will work in the market's favor, serving to stimulate tech development and cut prices. New solutions in the field were on display at ISC West 2019; they'll definitely be present at ISC West again in 2020. Developers specializing in VMS and modular AI video analytics should absolutely check these out.
But users should understand that it's impossible to build a cost-effective video surveillance system with significant number (10–20 and more) of AI analytics channels without using neural accelerators. That said, various accelerator models may significantly differ in price and power consumption. So, when you talk to developers specializing in VMS and AI analytics modules, ask what accelerator makes and models they support.
In conclusion
Whether you're an integrator looking for interesting VMS offers for clients or an end-user searching for solutions to your own tasks, check out what AI analytics can do. This sector is developing very fast and is continuously introducing new features that may be just what you're looking for. Incorporating forensic search in recorded video footage is key to building an effective video surveillance system for users, and important to creating a unique product offering for integrators. Needless to say, you can't build a cost-effective video surveillance system without using CPU resources wisely. If a system's functionality completely aligns with what you're looking for, ask what neural accelerator hardware it supports to correctly estimate the cost of your video servers.
Learn why leading casinos are upgrading to smarter, faster, and more compliant systems













