Office security - Security beat
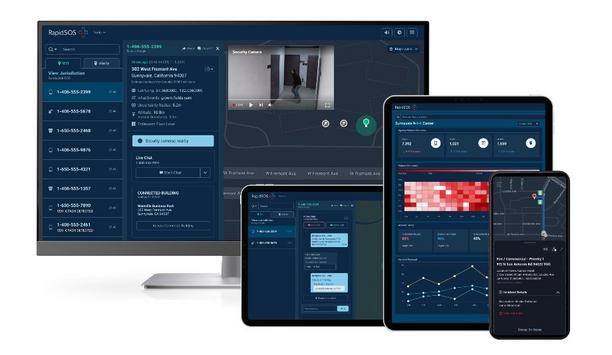
In an emergency, information is pivotal. More information provides better understanding of an emergency and empowers potentially life-saving decision-making. Emergency response teams depend on information to guide their efforts and to deliver targeted assistance. On the front lines of emergency response are 911 and field responder agencies, which must direct reaction to life-or-death situations rapidly and efficiently. Historically, 911 operators had to respond based on very little information,...
When it comes to security cameras, the end user always wants more—more resolution, more artificial intelligence (AI), and more sensors. However, the cameras themselves do not change much from generation to generation; that is, they have the same power budgets, form factors and price. To achieve “more,” the systems-on-chips (SoCs) inside the video cameras must pack more features and integrate systems that would have been separate components in the past. For an update on t...
New buzzwords were abundant in the articles that generated the most clicks on our website in 2022. From the metaverse to the Internet of Things, from frictionless access control to artificial intelligence (AI), the topics most popular among our site’s visitors were at the cutting edge of change and innovation in the physical security marketplace. Here is a review of the Top 10 Articles of 2022, based on reader clicks, including links to the original content: Metaverse will promote collab...
Collaboration among manufacturers in the physical security industry can result in systems that are easier to install for integrators and that provide a better customer experience for end users. Illustrating the point is the recent collaboration among a turnstile technology company, a supplier of short-range wireless readers/writers, and a biometric business focused on ‘frictionless’ access control. “The more manufacturers collaborate with each other, the more benefits fo...
Operational technology (OT) uses hardware and software to monitor and control physical processes, devices, and infrastructure. Historically, OT systems were not connected to the Internet and were therefore not vulnerable to cyber-threats. Internet of Things (IoT) However, today’s OT systems are increasingly part of a company’s networks as technologies converge and the Internet of Things (IoT) gains prominence. No longer can OT systems be counted on to be “air-gapped,” t...
New robots and indoor drones for security applications are on the horizon, based on the work of ADT Commercials’ Innovation Lab, which is evaluating the new technologies’ value to customers and some typical use cases. The Innovation Lab has been in place for just under a year and just moved into a 2,000-square-foot facility that is staffed with four dedicated ADT Commercial employees and teams from various commercial innovation partners. The idea of the lab is to close the gap bet...
IFSEC International took place over three days at the ExCel in London, presented alongside shows covering fire safety, intelligent buildings, facilities management, and safety and health. While perhaps not on the same scale as pre-pandemic events, the atmosphere was convivial and spirits high, everyone glad to be back amongst their peers in the industry. Predictably, the trending topics were steered by issues in the wider world: sustainability, moving services to a subscription-based model...
Access control systems are plagued by problems, such as false alarms and tailgating. Hakimo is a new company that applies concepts of deep learning to reduce false alarms and tailgating, and to make access control more accurate. False or nuisance alarms from access control systems take a lot of time and attention for operators in global security operations centers (GSOCs). It’s wasted time they could use to perform more high-level duties. Hiring enough GSOC operators to monitor and resolv...
Technology is driving new opportunities in the security industry. Innovation trends include artificial intelligence (AI), edge-based systems, mobile systems, a greater focus on software, and efforts to simplify operation of security systems, even as capabilities become more complex. ISC West 2022 reflected these changing trends. “In addition to emphasizing technology innovation, ISC West also reflected an industry that is resilient, dedicated and passionate,” said Mary Beth Shaughne...
Metaverse is a familiar buzzword today, but few people grasp what it really means. In the simplest terms, the metaverse is an online ‘place’ where physical, virtual and augmented realities are shared. The term, Metaverse, suggests a more immersive online environment that combines elements of augmented reality (AR) and virtual reality (VR). metaverse Expectations of the metaverse today are largely built on hype. You hear more about future and eventual potential than about the curren...
It’s been almost exactly a decade since HID Global launched the world's first university pilot of smartphones carrying secure mobile IDs. A lot has changed in the following 10 years. Today’s technology has matured, advanced, and proliferated across a variety of high-value use cases. To catch up on the latest developments in mobile access, we contacted Luc Merredew, Product Marketing Director, Physical Access Control, at HID Global. Q: What has changed since the first pilot implem...
Convergint Technologies’ rapid growth has come through a combination of organic growth and acquisitions — they have acquired 35 companies since 2014. Growth has been a focus since day one when the founders started the systems integration company with 10 colleagues in a basement. Today, the diverse company includes more than 5,000 employees globally. As technology has advanced and business practices have evolved, Convergint’s core values and beliefs have guided their path forwa...
Can a smart card be used securely for multiple applications (and among multiple manufacturers )? End users are demanding such interoperability, and they also want openness to switching out components of their access control systems in the future without being “locked in” to one vendor. Those are the goals of the LEAF Identity consortium, a collection of companies that share and support end user-owned encryption keys stored securely in smart cards with MIFARE DESFire EV2 chips and ar...
The task of protecting shared spaces, such as offices and schools, has become increasingly complex, particularly with ever-rising political tensions and the difficulties of assessing threats for schools, workplaces and law enforcement. Given the randomness of when and where a violent person may strike, those who manage facilities need an emergency plan, as well as robust training, detection and awareness. To gain more insights into dealing with such threats, we interviewed John Torres, Presiden...
Many venues are using access control, video surveillance systems, sensors, and additional hardware solutions as part of a broader security strategy. By utilizing so many disparate systems, corporate security teams are left with information “silos” that create inefficiencies and hamper communication. This abundance of hardware has left teams with too much data or too many tools, to manage effectively. Armored Things offers a software solution. The company’s “spatial intel...
During the Parkland, Florida, school shooting in 2018, the shooter was caught on a security camera pulling his rifle out of a duffle bag in the staircase 15 seconds before discharging the first round. However, the School Resource Officer didn’t enter the building because he wasn’t confident about the situation, and the Coral Springs Police Department had no idea what the shooter even looked like until 7 minutes and 30 seconds after the first round was fired. If the video system had...
As police use of live facial recognition (LFR) is called into question in the United Kingdom, the concerns can overshadow another use of facial recognition by police officers. Facial recognition is incorporated into day-to-day police operations to identify an individual standing in front of them. This more common usage should not be called into question, says Simon Hall, CEO of Coeus Software, which developed PoliceBox, a software that enables police officers to complete the majority of their...
Gunshot detectors use digital microphones installed on (or in) buildings or along streets that listen for evidence of gunshots, provide near instantaneous notification, triangulate the location of shooters and direction of a shot, detect the type of gun and ultimately aid in catching fleeing suspects and solving crimes. Gunshot detection is just one technology playing a role in the larger trend by city agencies to improve core city services. Cities are turning to what are referred to as ‘...
All schools and colleges need to address three different levels of security when considering access control. The first level is the least vulnerable of the three and concerns the perimeter entry and exit points. Here, incorporating some level of electronic access control should be a consideration, whether that is a combination of electronic and mechanical door hardware, or a complete electronic solution. An electromechanical solution, such as electric strikes, can be beneficial in the effective...
A complex set of biological, psychological, sociological, contextual and environmental factors are involved when a perpetrator decides to commit an act of workplace violence. In many cases, the perpetrator doesn’t really want to become violent; rather, they are seeking to achieve an outcome and mistakenly believe violence is their only option. An underused approach to preventing workplace violence is to consider the issue from the perspective of the instigator, to seek to understand their...
Security is more-than-ever linked to consumer electronics, especially in the residential/smart home market. CES 2018 in Las Vegas is therefore brimming with news that will have a direct impact on the security market, today and especially looking into the future. Products for the future of security CES is a giant trade show for consumer electronics with 2.75 million net square feet of exhibitor space and featuring more than 3,900 exhibitors, including 900 startups - in contr...
The European Union has spelled out specific requirements and safeguards for handling and protecting personal data. In the General Data Protection Regulation (GDPR), the EU makes clear exactly what is expected of those who control and process data. (The United Kingdom has committed to follow the regulation despite the Brexit vote.) Everyone is facing a deadline on May 25 2018 to comply with the GDPR. What are the exact implications for the physical security market? What do customers need to do to...
How much is the security risk each time an employee leaves a company? Unfortunately, many enterprises don’t manage the risk very well. Often, processes for canceling passwords or retrieving physical assets may be slipshod, or even non-existent. Research by IS Decisions highlights the problem: Over a third (36 percent) of desk-based workers in the United States and the United Kingdom are aware of having access to a former employer’s systems or data after leaving an organization. The...
While riding the Tube in London during IFSEC, I came across an attention-grabbing headline in a newspaper someone left in the next seat: “Coming To a Workplace Near You: RoboOfficeCop.” The article was about a robot that can patrol an office, checking that doors are shut and desks are uncluttered, using cameras and scanners to see whether anything is out of the ordinary. If something is amiss, the 6-ft-tall machine can store information to a hard drive to be reported later to a huma...