Featured white papers
Guide For HAAS: New Choice Of SMB Security System
DownloadPrecision And Intelligence: LiDAR's Role In Modern Security Ecosystems
DownloadAre You Ready For An On-Site Emergency?
DownloadIntegrating IT & Physical Security Teams
DownloadUnderstanding All-In-One Solutions
DownloadTop 7 Trends To Watch In The Physical Security Industry
DownloadVerkada Workplace Safety Survey
DownloadHow Video Technology Is Transforming Loss Prevention, Operations, And Customer Experience In The Retail Sector
DownloadTroubleshooting IP Video Systems
Download2024 Trends In Video Surveillance
DownloadHow Intelligent Video Is Transforming Banking And Financial Institutions
DownloadSecuring Data Centers: Varied Technologies And Exacting Demands
DownloadHow To Create A Successful Physical Security Roadmap
DownloadThe Real Cost Of An Outdated Video Security System
DownloadBoost Efficiency And Streamline Security With Integrated Access Control
DownloadMobile access articles

Zenitel, a provider of intelligent communication solutions, announced the launch of two new door entry intercoms: the Turbine Extended Intercoms TEIV1+ and the TEIV4+. The new pro...

Physical security is essential for a modern production facility, users don’t want just anyone entering the building or accessing secure areas. But what about production mach...

Gallagher Security announced the latest release of their award-winning security site management software, Command Center v9.10, marking a significant evolution for the security pla...

Gunnebo Entrance Control has announced its acquisition of DG Concept and Diadem, a French entrance control, design, installation, and service specialist, marking a significant step...
Healthcare security articles

Just like fighting against the spread of disease in a clinical environment, healthcare providers must mobilize, coordinate with interconnected partners, and apply sufficient budget...

According to the U.S. Occupational Safety and Health Administration (“OSHA”), hospitals are considered one of the most dangerous places to work in America. In...

Johnson Controls, the global pioneer for smart, healthy, and sustainable buildings, demonstrated complete building security solutions at ISC West 2024 in Las Vegas. The company sho...

Choosing the appropriate fingerprint technology for a given application is dependent on factors including the required level of security and matching accuracy, the desired capabili...
Search for products
Search from our vast range of products (39,854)Featured products
Editor’s picks

In the realm of physical security, the distinction between being perceived as a security vendor and a security partner holds great importance. While both may seem interchangeable at first glance, how...

In the competitive world of physical access control, Big Tech companies are seeking to play a larger role. Physical access competition Apple Wallet continues to stake its claim on mobile credentialing. Amazon One Enterprise is pushing a palm-based identity service. Google/Nest offers smart locks for home access control, with identity and access management provided in the Google Cloud. The entry of these big companies in the historically fragmented physical access control market is causing di...

Fueled by mounting concerns about the cybersecurity vulnerability of U.S. ports, President Joe Biden has signed an Executive Order aimed at shoring up defenses against cyberattacks. Cybersecurity initiative The cybersecurity initiative marks a significant shift in policy, empowering key agencies and outlining concrete actions to bolster defenses. By empowering agencies, establishing clear standards, and fostering collaboration, the initiative aims to strengthen U.S. ports against the ev...

The importance of data is ever-growing. For every profession, we’re witnessing the increasing reliance on data and its ability to promote efficiency for corporate decision-makers. The security industry is no different. The growing reliance on data and technological tools has allowed for a new breed of professionals with specialized skill sets. This evolution reflects the changing nature of security challenges in the digital age. The new security environment We know one thing from near...

Editor
Round table discussions

The security industry offers a vast array of technologies and vendors. This can be overwhelming for end users, who depend on security integrators for guidance and service. But how well do security integrators provide end users with what they need? We asked thi...

Technology offers a range of tools to bolster security at public events, including before, during, and after. This year, the 2024 Summer Olympics in Paris will draw the attention of the world, requiring the best protection available for the venues, the athlete...

Technology can be a powerful tool, but it can also be misused. Ethical principles help ensure that technology is used in a way that minimizes risks and avoids causing harm to people or society. Issues could include factors such as data privacy and algorithmic...
Latest videos
-
 HID Powers Secure Mobile Banking For Santander International With HID Approve
HID Powers Secure Mobile Banking For Santander International With HID Approve -
 Top-Of-The-Line Intercom Systems By DNAKE
Top-Of-The-Line Intercom Systems By DNAKE -
 ABLOY UK : ABLOY Critical Infrastructure
ABLOY UK : ABLOY Critical Infrastructure -
Siemens Sony Partnership Accelerates Digital Transformation Through Immersive Engineering
-
 IDIS Launches Efficient AI-Powered Security Camera Range
IDIS Launches Efficient AI-Powered Security Camera Range -
 Honeywell: The Future is What We Make It
Honeywell: The Future is What We Make It -
 Hikvision Introduces DS-K1T342-E1 Series PoE Power Supply
Hikvision Introduces DS-K1T342-E1 Series PoE Power Supply -
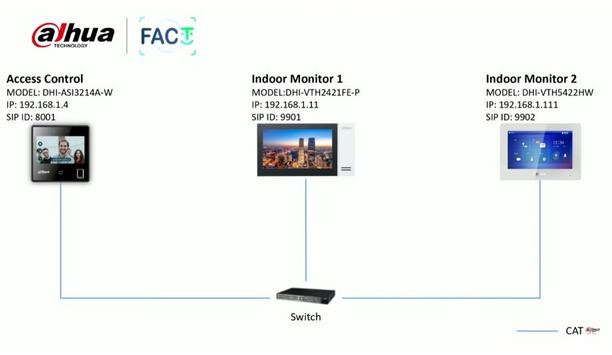 ASI3A Series Video Intercom Function Call Room
ASI3A Series Video Intercom Function Call Room -
 Creating A Digital Ecosystem To Enhance Hybrid Working - Webinar
Creating A Digital Ecosystem To Enhance Hybrid Working - Webinar
Case studies

Wetlands, the "kidneys of the Earth", are considered one of the three major ecosystems on Earth, along with forests and oceans. Hosting a diverse range of terrestrial and aquatic plant and animal species, wetlands serve as crucial habitats for numerous bird species. Red-crowned cranes Beautiful Wetlands vs Critically Endangered Cranes The Red-crowned Crane is considered as the "God of Wetlands" and is highly sensitive to environmental changes. It is one of 14 bird species in China classified as critically endangered, with only around 2,000 wild Red-crowned Cranes remaining worldwide. Monitoring these rare bird species not only aids in their effective protection but also reflects changes in the wetland ecosystem to some extent. Red-crowned Cranes migrate between the regions of East China and Northeast China In China, during spring and autumn seasons, Red-crowned Cranes migrate between the regions of East China and Northeast China, requiring wetland management personnel to make all necessary preparations in advance every year. Recording and tracking data (e.g. time of arrival/departure, and total number) play a significant role in monitoring both the Red-crowned Cranes and the wetland ecosystem. Hence, monitoring rare bird species is essential not only for their conservation but also for understanding the changes in wetland ecological environments. Vigilant cranes, eager for improved, smarter observation However, Red-crowned Cranes have extremely strong vigilance. Even while foraging or resting, there are often adult birds designated to be on alert, making warning calls and taking flight if any danger is detected. Therefore, it becomes challenging for monitoring personnel to observe them up close, as they need to maintain a distance of several hundred meters using binoculars to avoid disturbing the cranes. Such limitations in observation pose difficulties in monitoring the population distribution and activities of Red-crowned Cranes. To achieve efficient and intelligent monitoring while minimizing human interference, many wetlands have enlisted the assistance of an intelligent "avian expert". Dahua: the guardian of cranes with smart technologies In recent years, avian intelligent recognition systems have been increasingly applied in wetland monitoring. Dahua Technology actively explores the integration of technology and wetland conservation to support the monitoring and protection of bird species across multiple wetlands. Rare bird species like the Red-crowned Crane can be automatically identified and counted By employing high-point video footage combined with avian intelligent recognition algorithms, rare bird species like the Red-crowned Crane can be automatically identified and counted. This allows monitoring personnel to discover and observe various bird species clearly and promptly without disturbing them. Additionally, techniques such as background removal and contour deformation processing help reduce the interference caused by lighting conditions and backgrounds, ensuring that the footage presents the identifying characteristics, location, and time for each bird. With this approach, comprehensive and accurate data recording and result analysis can be achieved without disturbing the Red-crowned Cranes up close. A brighter future for biodiversity using intelligent analysis In addition to population counting, vocalizations play a crucial role in bird research. By utilizing voiceprint recognition, it becomes possible to track and study the population distribution of rare bird species. Many regions have established and improved databases of avian vocalizations, creating a foundation for biodiversity monitoring and analysis. These databases, combined with visual identification, are being cataloged in order to facilitate more comprehensive research and analysis, optimize timely conservation measures, and enhance dynamic and diverse science communication and education. Dahua Technology continues to empower biodiversity conservation through technology. The Dahua AI platform enables continuous algorithm training that helps reduce the development cycle of recognition algorithms for specific species. At present, Dahua has developed over 800 bird recognition algorithms, with more than 500 focused on waterfowl and migratory birds primarily inhabiting wetland environments. This extensive collection of algorithms greatly supports and contributes to biodiversity conservation efforts around the globe.
Read moreCompany in profile
Increase your online visibility and get found by relevant security professionals.
Upcoming events
Counter terror
- 3xLOGIC’s To Debut Its X-Series Edge Based Deep Learning Analytics Cameras At The Security Event 2024
- Break-Down Of Recent Updates And Threats In C-UAS Innovations & Technologies Impacting The Defense Space At ACI Congress 2024
- Elite Interactive Solutions' Law Enforcement Advisor Appointed To New Role
- CoLCPA & The NSI Announce Building Security Assessment Scheme Partnership
Video analytics
- Drata Acquires Oak9 And Announces New Compliance As Code Capabilities
- Johnson Controls Showcases Complete Building Security Products, Solutions And Service Leadership At ISC West
- FCC Environment And Suffolk's Innovative Recycling Center Project
- Crystal Mountain Resort's Success With Verkada Physical Security Tech
Internet of Things (IoT)
- BSIA Cyber Exposure Mitigation Code Of Practice Released
- Release Of Gallagher Security’s Command Center V9.10 Unlocks New Era Of Security Tech
- Drata Acquires Oak9 And Announces New Compliance As Code Capabilities
- NCSC Warns Of Heightened Security Risk To Critical National Infrastructure At The Hands Of Russia-Linked Cyber Criminals