Hacking, data theft and security system compromise: it’s in the news daily. And as the internet of Things (loT) continues to introduce more network-connected sensors and devices, security dealers need to offer customers cyber-hardened products. The Connect ONE web-hosted service from Connected Technologies, LLC is purpose-built with safeguards that make it extremely difficult for unauthorized persons to use bots and other malicious tools to access systems.
Network Access Control With Built-In Safeguards
The Connect ONE interface allows for a limited number of login attempts, with bolstered safeguards. Three log-in fields, not two, are required: user name, password and customer number, making hacking more difficult. After the first three unsuccessful attempts, the CAPTCHA prompt appears – a human verification response test. After additional failed attempts, the Connect ONE interface log-in shuts down, and as an additional safeguard, the incoming IP address is locked out for a period of time.
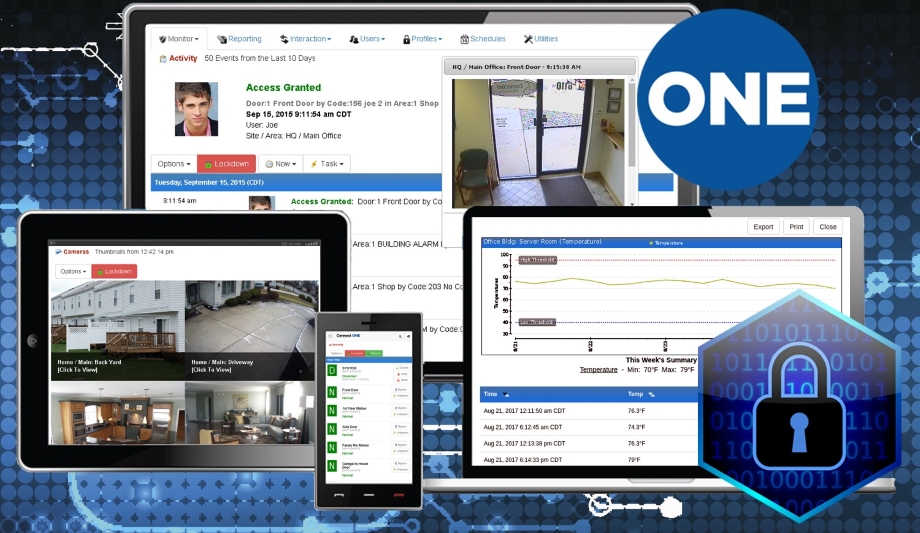
Connect ONE is the only interface you need for all your customer’s integrations – security, access control, video monitoring, energy management and critical environmental monitoring. View, control and interact with all systems on ONE screen from any web-enabled device.
Find out about secure physical access control systems through layered cybersecurity practices.