Phillip Merrick

Phillip Merrick
Chief Executive Officer (CEO), FuguePhillip Merrick is currently working in the capacity of Chief Executive Officer (CEO) at Fugue. He has previously worked as Advisor at Secure Credit Systems, CEO at SparkPost and a Board Member on Revitas.
News mentions
Sonatype, the globally renowned provider of innovation-friendly open source security tools, has announced entering into a strategic partnership with Fugue, the company putting engineers in command of...
Fugue, the company putting engineers in command of cloud security, announced next-generation cloud security posture management (CSPM) capabilities to help customers bring their cloud infrastructure in...
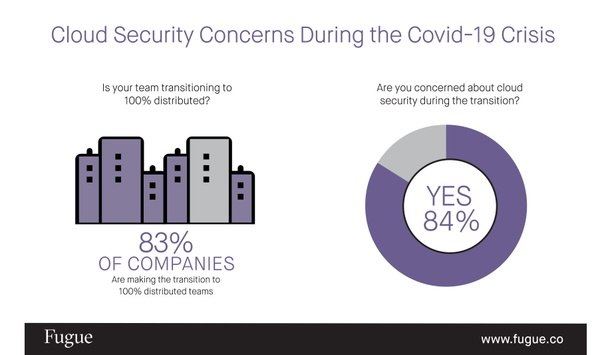
As a vast majority of companies make the rapid shift to work-from-home to stem the spread of COVID-19, a significant percentage of IT and cloud professionals are concerned about maintaining the securi...
Fugue, the company delivering autonomous cloud infrastructure security and compliance, has announced the release of the Fugue Best Practices Framework to help cloud engineering and security teams iden...
Fugue, the company delivering autonomous cloud infrastructure security and compliance, has announced its support for Open Policy Agent (OPA), an open source general-purpose policy engine and language...