Articles by Larry Anderson
More crowded aisles and productive conversations continued to set the tone on the second day of ISC West in Las Vegas. No big technology breakthroughs have surfaced, but there is plenty of interest, and some degree of curiosity, about whether (and when) the recent hype about artificial intelligence (AI) and deep learning will translate into usable products. Vertical Market Solutions “Yesterday we saw a tremendous amount of traffic in the booth, and today is more of the same,” said...
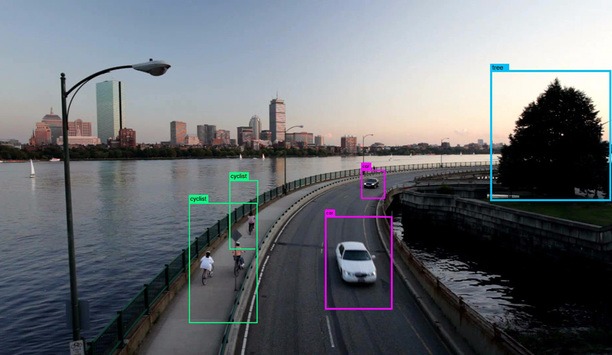
ISC West in Las Vegas kicked off with a bang on Wednesday, reflecting a healthy physical security industry with an overall upbeat outlook on the future. Driving the optimism is a pending new wave of product innovation, propelled largely by developments in artificial intelligence (AI) and deep learning. Some of that new wave is evident at ISC West, but much of the talk still centers on what’s to come. Attendees flocked to the first day of the show to check out the newest technologies, and t...
As ISC West opens today in Las Vegas, many companies will be introducing new products. But the announcements today from Arecont Vision will have a larger impact, and they involve much more than new products. In fact, the megapixel camera company is staking a claim to a broader slice of the market, and expanding its go-to-market strategy in the process. “The industry has changed, and the amount of competition out there today is significantly different and more pervasive,” says Raul C...
A few friends from the security industry will gather this April to see, hear and touch the latest technologies to make the world a safer place. Actually, more than a few: there will be more than 30,000 security professionals gathering at the Sands Expo in Las Vegas April 11-13 for the International Security Conference and Exposition, usually known as ISC West. Many of the attendees will be returning to what has become a yearly ritual. The site, the players, the pace and even atmosphere of ISC...
Mike Taylor has been involved in security industry sales for more than 20 years, on the front line of industry changes and watching how they impact customers. Among the changes is a shift in the nature of the sales function itself. As Director of Sales, Americas, for Milestone Systems, Mike Taylor currently oversees a team that brings to market the full suite of Milestone open platform solutions. We sat down at Milestone Community Days (MIPS) earlier this year to discuss the technologies and tr...
President Trump has recently proposed a series of tariffs that could disrupt global trade and impact the global physical security market, among many others. He first proposed tariffs targeting aluminum and steel imports; in effect, the proposal would place a 25 percent tax on steel and a 10 percent tax on aluminum entering the United States. Rising Prices, Rising Tariffs The resulting higher prices of imported aluminum and steel could raise the costs of a range of goods manufactured in the Uni...
Open architecture in physical access control is built around Mercury Security’s access control panels, the de facto standard embraced by more than two dozen access control original equipment manufacturers (OEMs). Mercury and several of its OEMs teamed up March 3-4 to present MercTech4, a conference in Miami aimed at updating security consultants about the latest developments related to the Mercury platform. MercTech4 highlighted a new generation of access control products, which are incre...
A new crime wave is hitting automated teller machines (ATMs); the common banking appliances are being rigged to spit out their entire cash supplies into a criminal’s waiting hands. The crime is called “ATM jackpotting” and has targeted banking machines located in grocery shops, pharmacies and other locations in Taiwan, Europe, Latin America and the United States. Rough estimates place the total amount of global losses at up to $60 million. What Is Jackpotting? ATM j...
Milestone Systems is embracing artificial intelligence and deep learning in a big way at this week's yearly Milestone Community Days (MIPS 2018) in Las Vegas. The Danish company's theme is "Creating an Intelligent World," and Milestone's stated goal is to make "the Milestone community part of every surveillance installation in the world." Science Fiction Becomes Reality In a presentation on opening day, Milestone CSMO Kenneth Hune Petersen pointed to the 2002 movie The Mino...
Leadership roles are changing inside enterprise companies, where higher profiles of roles like CIO and CISO are blurring the lines separating legacy security departments from the larger enterprise. The role of security – protecting the company – now overlaps with broader concerns such as business optimization. The changes are impacting how technology is used; what was once considered a “security system” can now impact the company in larger ways. It’s not just prot...
There’s a new big player – and familiar household name – coming into the security marketplace with the announcement of Motorola’s intent to acquire Canadian video manufacturer Avigilon Corporation, provider of video surveillance and analytics. Motorola Solutions points to an “avalanche of video in public and private sectors” as a motivation for the acquisition. Motorola Solutions’ dominance in the public safety market – where t...
The cloud and deep learning are two technologies on the verge of transforming the video surveillance market. You often hear the two technologies mentioned as separate trends, but lately, I have been hearing about how interdependent they are. Economies of scale provided by the Cloud (Software as a Service, or SaaS) are making the sophisticated capabilities of deep learning affordable to a wider audience. Meanwhile, deep learning augments cloud systems with capabilities that...
Security is more-than-ever linked to consumer electronics, especially in the residential/smart home market. CES 2018 in Las Vegas is therefore brimming with news that will have a direct impact on the security market, today and especially looking into the future. Products for the future of security CES is a giant trade show for consumer electronics with 2.75 million net square feet of exhibitor space and featuring more than 3,900 exhibitors, including 900 startups - in contr...
Rapid changes in the physical security market this year have largely overshadowed one arena where change has slowed down in 2017 – mergers and acquisitions (M&A). Although there were no “mega-mergers” as in years past (such as Axis-Canon and Johnson Controls-Tyco, M&A activity still made headlines last year on SourceSecurity.com. In 2017, we wrote about M&A news involving companies such as HID Global, Eagle Eye Networks, ADT, and Honeywell. ...
A downside of our thriving economic times is a shortage of skilled personnel to work in the physical security marketplace. Strong economic growth translates into a low unemployment rate, and greater competition among employers to attract the best talent. The field of cybersecurity, in particular, is seeing a serious talent shortage, but any physical security company can also attest to our own challenges finding and keeping the best talent; not to mention the obvious - that cybersecurity is now...
Information can be a scarce commodity in the midst of terrorism or a mass shooting incident. Information can also save lives during the first critical moments of such events. The general public can now download a free smartphone app that provides instantaneous real-time information as a terrorism or mass shooting event is unfolding. TerrorMate Crawler Software Called TerrorMate, the app began development in 2013, in the wake of several terrorist attacks in France. People in the affected areas...
Qognify’s security management systems compile information from a variety of sensors to provide situational awareness, and now they can leverage the benefit of a different kind of sensor, what the company calls the “human sensor.” Employees see and hear a lot of information during their work day, and some of it has an impact on security. Now that information can become part of an integrated security system, reported by trusted employees through a smart phone app. Qognify&rsquo...
A USB drive from Heathrow Airport, found on a London street in late October, contained confidential information about accessing restricted areas at the airport and security measures used to protect the Queen. The drive also contained a timetable for anti-terrorism patrols at the airport and documentation of the ultrasound system used by Heathrow security to check perimeter fences and runways for breaches. The data was not encrypted, and the London resident who found it turned it over to a newspa...
Cybersecurity is a growing concern for manufacturers of life safety and security products, and Underwriters Laboratories (UL) wants to help solve the problem. Specifically, UL seeks to work with manufacturers to up their game on cybersecurity and to certify compliance to a minimum level of cybersecurity “hygiene.” UL Cybersecurity Certification UL is a familiar brand in consumer goods and in the security and life safety markets. UL certification is sought by manufacturers in a ran...
The massacre in Las Vegas is both sadly familiar and terrifyingly novel. Because of the recent series of violent attacks on innocent people gathered in public places, high body counts are no longer unheard-of, although the 59 dead after the Las Vegas tragedy sets a depressing new record. These news stories have become so grimly commonplace as to dull our collective sensitivity to their shock. However, the modus operandi of the latest attack, apparently by a “lone wolf” – caref...
As the dust settles after ASIS 2017 in Dallas, most agree it was a good show. It was different in some respects from previous shows, but several of the changes seemed to work well. Launching the exhibition on Tuesday instead of Monday was a big hit, and who could fault the idea of happy hour drinks on the show floor? Attendance may not have broken records, but end user VIPs were among the crowd, and foot traffic held up fairly well, even on the final, shortened day. STANLEY Security Virtual Re...
End users at ASIS 2017 in Dallas may feel overwhelmed by all the new technology on display, but often their integrator partners can offer a helping hand. Traffic continued through much of Day 2 of the ASIS exhibition, but the foot traffic appeared to slow considerably as the day wore on. Convergint Seeks Closer Manufacturer Relationship Integrators are prominent at ASIS and play an important role connecting end user customers with manufacturers' products that meet their need. "We are taking t...
ASIS 2017 was off to a strong start on Tuesday, presenting a new wave of innovation to the U.S. security end user community. Many attendees to the Dallas show are well-placed in their companies to influence or direct the purchase of security products and equipment, and exhibitors sought to impress them with a range of new and enhanced options. Moving From Integration To Unification In general, the ASIS show has a quieter, less frantic feel than the spring ISC West show in Las Vegas. Conversat...
We can add another technology category to those aspects of the physical security market on the verge of being changed by cloud technology. The new category is the printing and encoding of ID cards. HID Global is adapting the benefits of cloud computing to the ID card printing market with the introduction of HID Fargo Connect, a cloud-based personalization and issuance system for ID cards. The new cloud approach, which will be introduced at the ASIS 2017 show in Dallas, converts standalone card...
The Internet is awash in information, and some little bit of it somewhere might represent a threat to your company. How much would you pay someone on your staff to read more than a billion Internet posts a day in 200 languages, sort through it all, provide what’s relevant to your company in your inbox, and then alert you, in real time, to the most threatening information? It’s an interesting question that points to the value proposition of Babel Street, one of the exhibitors at th...
Millennials are an important market, and in one sense, they represent future possibility. The changing tastes and trends of this tech-savvy “Generation Y,” who came of age around the turn of the millennium (circa 2000), are an important consideration in the marketing of security technologies, among many other things. Fortunately, according to a recent survey from ADT, millennials will likely be dependable consumers of security technology products and services for years to come. Smar...
Despite the increasing popularity of body-worn cameras, the technology has its detractors. For example, this month, Big Brother Watch, a British civil liberties and privacy organization, is raising new questions about the effectiveness of body-worn cameras. Specifically, Big Brother Watch found that 32 of the 45 police forces that have adopted body-cams in the United Kingdom were “unable to say” how often the footage was used in courts. To be clear, being “unable to say”...
Protecting power grids is essential to deliver electricity that serves millions of consumers. Transmission substations are a component of the power infrastructure that presents unique security challenges. These important facilities often sit out in the open, in remote locations, and were historically protected by little more than cameras or chain-link fences. Much of the current concern about securing electrical substations in the United States originated in response to a 2013 sniper attack, us...
Working together to develop an intelligent body-worn camera for public safety users, Motorola Solutions and artificial intelligence (AI) company Neurala are demonstrating how AI can be added to everyday devices such as smart phones using existing hardware platforms. AI software, working at the “edge,” provides the capability to add AI functionality to existing cameras, such as Motorola’s Si500 body-worn camera. An agreement to develop the products follows Motorola&rsquo...
The European Union has spelled out specific requirements and safeguards for handling and protecting personal data. In the General Data Protection Regulation (GDPR), the EU makes clear exactly what is expected of those who control and process data. (The United Kingdom has committed to follow the regulation despite the Brexit vote.) Everyone is facing a deadline on May 25 2018 to comply with the GDPR. What are the exact implications for the physical security market? What do customers need to do to...