Articles by Larry Anderson
An expanding outreach and programming targeted especially to international visitors are among the ways ASIS International is seeking to attract more global attendance than ever to its 63rd Annual Seminar and Exhibits, which will take place between 25-28 September in Dallas, Texas. In addition to returning, long-time international visitors, ASIS International is looking to expand global attendance. One initiative is the International Buyer Program (IBP), a joint government/industry effort, whic...
Exhibitors at this year’s IFSEC are thinking outside the box in terms of how they communicate their value proposition and how they interface with customers. In the process, some are rethinking how big trade shows like IFSEC fit with their goals. Panasonic's approach to the 'race to the bottom' Thomas Lausten, MOBOTIX new CEO How Gallagher benefits from IFSEC without exhibiting Panasonic Systems Communications Europe Panasonic Systems Communications Europe is one of several compani...
Has there ever been a better time for a security trade show in Europe? Shifting threats such as terrorism and a volatile political climate serve as reminders every day of the importance of security in our lives, and even the role of technology. IFSEC opened in London on Tuesday at the ExCeL center, covering every aspect of security, from access control and video surveillance to home automation and perimeter security. Amid sweltering heat, attendees came to find the latest-and-greatest inno...
Security control rooms should be functional and durable, and their aesthetics should incorporate matching colors that are conducive to a 24/7 operating environment—not too much contrast and easy on the eyes. Another factor driving aesthetics is an enterprise’s desire to create a ‘showpiece’ to demonstrate a commitment to security for shareholders and other stakeholders. “Everyone wants to have a good-looking control room and a cost-effective design,” says Mat...
Technology is changing the look and function of today’s security control rooms. Old-school CRT (cathode-ray tube) monitors are giving way to the thinner, flat screen monitors in the control room environment, but the transition is gradual. Randy Smith of Winsted still sees many control rooms that need to make the conversion, which is a boon to his company’s business. Furniture today is designed differently to accommodate the thinner monitors, often with larger screens. Need For Inte...
Manufacturers depend on consultants to get their technologies specified in customer projects. Consultants often depend on manufacturers to provide them current information about the technologies that are the building blocks of their projects. It’s a symbiotic relationship, but not always a perfect one. We recently gathered three consultants to discuss what they want from manufacturers, and a representative of HID Global to add a manufacturer’s perspective. Manufacturers also look to...
Mobile access is probably the largest emerging trend in the security marketplace, but it is only one of several that are changing the face of the access control market. Another factor showing potential to change the market is the emergence of location systems and positioning systems, as reflected by HID Global’s recent acquisition of Bluvision, a provider of real-time location tracking system for assets and employees, and building information modeling (BIM) is impacting how consultants do...
How do you make a 63-year-old organization even better? That’s the challenge for ASIS International as it continues an effort to be more transparent and inclusive, and to adapt to 21st century work environments. Transforming The Focus Of ASIS International “ASIS International is undergoing a tremendous amount of transition and reexamination, creating a lot of opportunities,” says Amy Fischer, Vice President of Marketing and Communications. There’s a new CEO and there h...
Some end users and integrators are daunted by the idea of designing control rooms, but they shouldn’t be. “It’s not difficult to design because we will help,” says Randy Smith, President of Winsted. “We will walk you through the entire process.” Some control rooms still need storage areas for consoles underneath the workspace; however, when hardware is relocated to a server room, Winsted has modern, streamlined and simplified designs with no doors or storage...
Security consultants are on the front lines of trends such as “smart buildings” and the increasing demand for green technologies. We recently gathered together several consultants to reflect on what’s new in these areas, joined by a representative of HID Global. Participants were Chris Grniet of Guidepost Solutions, Brandon Frazier of Elert & Associates, Terry Harless of Burns & McDonnell, and Harm Radstaak, HID Global’s Vice President and Managing Director, Phy...
The transition from analog to IP technologies has had a large impact on the ways intercoms are used in the security industry. The analog-to-IP transition has generated a lot of attention in the camera market, and the transition is also taking place for intercoms. Twenty years ago, Axis Communications (2N’s parent company) led the industry in converting from analog cameras and video to IP. Integrated IP System The conversion took 15 years to achieve, but the same conversion in intercoms i...
When people think of control rooms, images from James Bond movies or intense action stories come to mind. What they fail to realise is the incredible level of ergonomics, technology, precision and craftsmanship required to create a top-notch command and control room. “These are rooms of complex functionalities, where hundreds of elements must be integrated and function in sync,” says Jim Coleman, National Sales Manager, AFC Industries. Professional teams from several different indus...
A technology poised to transform the physical security market is deep learning, which is a neural network approach to machine learning, differentiated by an ability to train using large data sets for greater accuracy. In effect, the system “learns” by looking at lots of data to achieve artificial intelligence (AI). Phases Of Deep Learning I heard a lot about AI, including how it can transform the physical security marketplace, when I attended NVIDIA’s GPU Technology Conferenc...
Ergonomics are a critical, but often misunderstood aspect of designing control rooms for security. Ergonomics have a deep impact on the integrity of an operation, and the issue goes beyond the control room furniture. Matko Papic, Chief Technology Officer of Evans Consoles, divides ergonomics into three areas: physical (reach zones, touch points, monitors); cognitive (the individual’s ability to process information without overlooking a critical element) and organization...
Project registration programs are a benefit manufacturers provide to systems integrators and security dealers who are bidding on an upcoming installation project. In effect, the integrator registers a project he or she is bidding on with a manufacturer, which offers pricing discounts to that integrator for that specific project. Such a program seeks to encourage an integrator to specify a manufacturer's products, while making it more difficult for a competing integrator to bid lower on a pr...
Part 4 in our Intercoms in Security Series The ONVIF standard makes it simple to integrate the intercom with other ONVIF-compliant video management systems, access control solutions, and cameras Open standards are enabling new capabilities in the intercom market, some of it driven by the transition to systems based on Internet protocol (IP). Today’s most-used phrase in the intercom business is interoperability, given that the intercom is integrated with solutions s...
The ASIS International 63rd Annual Seminar and Exhibits, held between September 25th-28th in Dallas, will see several changes in 2017. The ASIS Board of Directors has directed ASIS staff members to look for new ways that the yearly show can provide more value, while continuing a 63-year tradition and demonstrated ability to serve the market. Under the general leadership of the Board, ASIS staff members have evaluated feedback from members, exhibitors and attendees to guide them as they seek to r...
Part 3 of our Intercoms in Security Series: Zenitel’s Call Access Panel manages intelligible critical communications through a security operations center or control room Greater connectivity, security software enhancements, more customization, and better sound quality are some of the enhancements driving the intercom market.An advantage now offered on Code Blue’s emergency speakerphones include self-diagnosing software that monitors the status of the phones an...
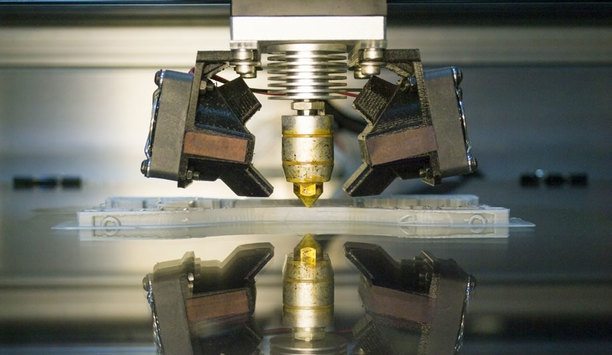
Technology is a valuable tool for increasing security, but occasionally technology can create a threat. An example is the threat 3D printing technology poses to one of the most mature security technologies, mechanical locks and keys. The ability of 3D printing to duplicate keys presents new challenges for lock manufacturers, and new vulnerabilities to end users. Keys that could previously only be duplicated by skilled thieves can now easily be copied using off-the-shelf technologies and informat...
Part 1 in our Intercoms in Security Series Lambert-St. Louis International Airport uses Code Blue intercoms Organizations are demanding a new level of interoperability among mission-critical security systems. Intelligible audio, the ability to hear, be heard and be understood, is critical to communication, which is essential to the core security processes within an organization, as well as to emergency situations. Intelligible audio provides a platform to optimize v...
Part 2 of our Intercoms in Security Series The 2N Helios IP family intercoms present a comprehensive portfolio of security offerings for businesses and individuals Some integrators and end users may think of intercoms as older technology that isn’t required as part of a robust security system. Not true. Intercoms include innovative technologies that have developed rapidly, keeping pace with other categories. Just as cameras and access control systems have made techn...
The enthusiasm of ISC West 2017 continued through to the final hours of Friday, reflective of a show jam-packed with new technologies to address industry trends. Exhibitors seemed happy enough with booth traffic, which held up even on the final day. Security Industry Trends Industry trends drove much of the technology. For example, cameras are getting less expensive, which means it’s more cost-effective to specify systems with higher camera counts. Also, cameras are providing more...
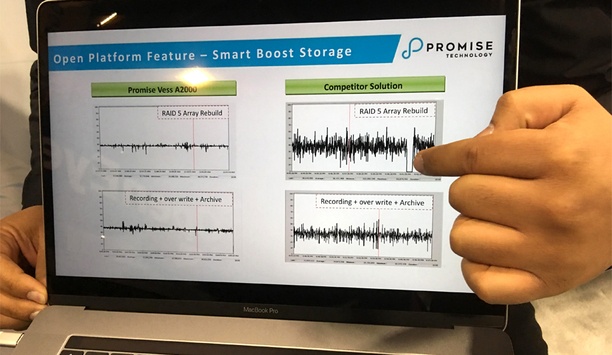
For all its value in the security market, one has to wonder: How much captured video is actually used for security? Among hours and hours of video, only brief segments here or there are ever actually viewed or used for security applications, such as to review an incident or to provide evidence in court. But what about all that other video, much of it stored for 30 or 90 or 120 days or longer? Does it have to be merely a costly consequence of providing the security benefits of video? Not necess...
ISC West in Las Vegas kicked off Wednesday with an expanding focus on new technologies and new applications, including some that go beyond any narrow definition of “the security industry.” Qognify QBlock And Cloudscann “Technology is disrupting the market and executives are taking our solutions beyond security,” says Moti Shabtai, CEO and President of Qognify. “They are starting with security and quickly moving to other risk and business continuity issues in the...
Using an asymmetric approach to perimeter security is more efficient and cost-effective. The approach, advocated by Applied Research Associates (ARA), involves strategic deployment of the company’s Pathfinder seismic-acoustic sensors. Asymmetric placement of the sensors is in contrast to typical perimeter security systems, which are linear: Sensors are distributed at specific intervals along a perimeter and require infrastructure to communicate back to a control center. Instead, asymmetr...
“Mixed reality” may seem like a strange term to apply to the physical security industry, but it describes a new approach to enable the features of access control and video surveillance systems to be used by operators in the field. Mixed or augmented reality technology combines a real-time view of the world through Microsoft’s HoloLens headset, with placement of virtual devices and controls as holograms in a three-dimensional space. Virtual Devices And Controls In effect, a s...
Smartphones offer a new alternative to traditional physical access control form factors such as smart cards or fobs. Convenience is the most obvious benefit, but there are others. Here are some advantages of using smart devices for access control: 1. Less vulnerability to cloning when compared to magstripe or low-frequency proximity cards. Digital credentials and mobile IDs are securely stored and protected. 2. Longer-distance communication, which allows readers to be mount...
Artificial intelligence and deep learning are poised to transform how video images are used and managed. In today’s surveillance systems, video from more and more cameras leave operators at risk of drowning in data, requiring hours of manual effort to track assets or persons of interest. They need more intelligent systems. Among the new tools is use of neural networks to create video analytics systems that are trained, not programmed. In effect, the systems have the ability to “lear...
Several of the hot trends in the physical security industry – robots, drones, video analytics – have one thing in common: The need for greater intelligence. More complex physical security systems that incorporate artificial intelligence, deep learning, speech recognition and other sophisticated functions depend on a higher-than-ever level of computing power inside embedded devices at the edge. Graphics Processing Unit Graphics processing unit (GPU) manufacturer NVIDIA is empowering...
A gunshot localization solution can turn a video camera system into a real-time safety system in the event of an active shooter. Called ShotPoint, the system is completely automated. Working with a video management system (VMS), it can enable a video image of an active shooter to be provided in seconds based on the location of a gunshot. “For responders, the police department doesn’t have to manage cameras, but has the instant availability of a camera feed,” says Kathleen Grigg...