Expert commentary
The IP surveillance market is taking anunusually long time to reach maturity, partiallydue to lack of industry standards Video surveillance has been a growth industry ever since the release of the first IP security camera in the mid-1990s. Generally, high-growth industries are immature, meaning they have not yet reached a state of equilibrium. This is particularly true in the IP video surveillance market where many new companies enter the market takin...
Derren Lu, CEO of Synology Inc and Scott Lee,Senior Manager of Software DevelopmentGroup for Surveillance Synology – a company founded by two former Microsoft employees – began as a storage solution provider and grew to include surveillance in its product offerings. While many security companies in Taiwan are voicing their concerns over falling sales, Synology is seeing its products grabbing shares in the security market and the sales figures are continuing to grow...
Home security devices are evolving and expanding their offered features, providing new opportunities for the security industry Home security isn’t just home security anymore. These days cameras, door and window alarms are just pieces of the web–enabled “smart home.” And, the home is getting smarter, as service providers begin to merge home security systems with home automation. The added value of these additional features is now drawing more potential c...
The vision of a utopian urban future restsheavily on the success of Open Dataand a Cloud Computing paradigm Confronting urban challenges using technology requires the private sector to work in tandem with governments to enable "smart cities." In fact, one report predicts the number of safe cities worldwide will quadruple in the next decade. It’s a topic that is increasingly top-of-mind. For example, the Safe Cities Asia 2015 conference in Singapore in May brought to...
Problems caused by physical systems in terms of cyber-attack are quite extensive, damaging systems and assets Security experts of various disciplines agree that physical systems are increasingly being leveraged in attacks on organizational networks and supply chains. Many manufacturers maintain that security (including that of security systems) is the responsibility of the end user, which would be fine if they were only expected to maintain security and not create th...
The security industry’s continued migration to networked IP-based systems ensures that PoE will be integral in their design and installation Power over Ethernet (PoE) has without question become the de facto choice of security installers for delivering power to security and access control devices. This should come as no surprise given PoE’s ability to reduce labor and installation costs by delivering power and data over a single cable, thereby increasing overall to...
For high value individuals such as the Pope,agencies have access to unlimited publicresources in terms of money and people The Pope’s visit to the United States reminds us that protecting big-name executives, celebrities and dignitaries is a highly specialized security function. Public and private executive protection groups begin preparing for the visit of major world figures months ahead of time. “It is a task of massive proportions,” says Tom M. Con...
NVRs make it easy to benefit from HD solutions and integrations to access control, alarm systems, intercoms and other technologies Developments in the IP video camera market have a direct impact on the other components in a system. With the emergence of higher definition cameras – whether 4K cameras or 8K or even higher – the market now needs back-end devices that can perform the decoding work. Also, more intelligence is needed, including smart functions such as pe...
7K cameras are best suited for large openspaces such as stadiums and city centers,capturing the finest details in their footage With several manufacturers now offering 4K CCTV cameras, Avigilon, based in Vancouver, B.C., raised the bar in April 2015 with the launch of their 7K HD Pro surveillance solution. The 30-megapixel camera is the latest addition to the company’s Professional Series, an innovative model Avigilon believes will drive competition in the security indus...
How do you get all of your various vendors, services, resources, manpower, and technology to integrate and work together? Creating an efficient operating environment in physical security is no small feat - especially when the organization undertaking such an endeavor has a nationwide presence. How do you get all of your various vendors, services, resources, manpower, and technology to integrate and work together? How do you aggregate all of the data being recorded into inf...
Enterprise security strategies identifyliabilities & ways to mitigate risks, showinghow the cost of mitigation prevents largerliabillity costs The security profession continues to take on new risk management responsibilities. The big thing now is called Enterprise Security and Risk Management (ESRM). ASIS International has issued a standard on the subject: ANSI/ASIS/RIMS RA. 1-2015, and a couple of booths at the recent ASIS International 2015...
As technology advances and more surveillance features become available, it can be difficult for security integrators to know which system will fit their customer’s needs It’s no secret that Internet Protocol (IP) cameras are on a steady march to replace analog video. Network-centric surveillance cameras bring a host of value to the protected premises, above and beyond traditional physical security. Now, cameras are increasingly used for safety, such as in liability...
Automation is another hallmark of PIAM solutions, which can perform a wide variety of processes that are prone to error if performed manually Security departments in organizations face a number of threats from both internal and external sources, thus forcing security personnel to remain vigilant and aware of the growing number and scope of new and emerging risks. The most powerful weapon in this seemingly endless battle is data. Every organization has it – probably more...
NVRs come preinstalled with latest software releases to minimize setup time Looking for a perfect marriage of hardware and software for a video management system application? A preconfigured network video recorder (NVR) appliance may fit the bill. Consider these advantages of going the NVR appliance route, as suggested by vendor companies contacted by SourceSecurity.com. 1. Greater Freedom Of Deployment NVRs provide more application flexibility – because the recorders...
The open and exposed nature of rail yards exposes railway assets to tremendous risk The importance of rail transportation in driving the U.S. economy cannot be overstated. In recognition of this, America’s railroads are investing in the infrastructure and technology necessary to improve security for the tracks, bridges, tunnels and other vital components that make up this critical transportation network. The unique security requirements of these assets present a nu...
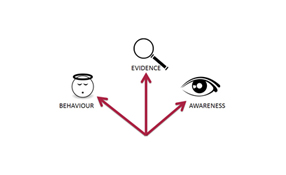
Ballantyne has created the "Three Vectors of Value" for video surveillance - Awareness, Evidence and Behaviiour The annual global expenditure in new video surveillance systems is currently estimated at about 20 billion USD and grows at a rate of better than 15% per year. To those of us in the business, these figures both encourage and validate. The expenditure is impressive, but only because commensurate value is delivered. That is, we expect expenditure and value to bal...
Internet of things is worth the resilience trade-offs it demands – effort, thought and inconvenience ‘No society is more than three meals from revolution’ says the old adage. Updating the idea for the Information Age is a revealing, if somewhat worrying, exercise. How resilient are we as a society? Could your company function efficiently after a complete failure in IT? How effective would your employees be if forced to work from home following a collapse in t...
The potential costs and consequences of hackers getting through firewalls and onto the user’s computer networks can be devastating Theft of NATO data. Leakage of emails. Hackers setting up a live streaming website for over 100 New York City private webcams and even hacking the infrastructure servers of the U.S. government. As news of malicious takeover of private and corporate networks as well as incidents of malicious software programs, referred to as malware, conti...
NVR appliances ease analog to IP transition by providing end users with a hybrid-ready product There should be a palatable migration path from a large installed base of analog to the latest IP technology. The biggest missed opportunity related to network video recorder (NVR) NVR appliances in the video surveillance marketplace is effectively using existing analog camera investments while transitioning to the network. For example, IP encoders can be utilized as a bridg...
Aventura continues to expands expand its feature set of products beyond PSIM As the 61st annual ASIS 2015 kicked off in Anaheim, Calif., it became increasingly clear that physical security continues to move from the realm of traditional intrusion detection, video surveillance and alarms into value-added applications that extend into new markets, uses and purposes – many of them centred on business and operational processes. While video surveillance, intrusion detection,...
The potential is huge for vendors in the security and technology industries that have gun detection-related services & products Gunshot detection systems are a fast growing trend that helps police and security guards to protect the public, capture criminals and collect forensic evidence for investigations. Gunshot detectors use digital microphones installed on (or in) buildings or along streets that listen for evidence of gunshots, provide near instantaneous notification,...
NVRs of the past may have been expensive & complicated to use, but today NVRs have user-friendly functionality How much do you know – or think you know – about network video recorder (NVR) appliances? Manufacturers in the sector say there is a lot of misinformation in the market about these workhorse system components. We asked several manufacturers to help us set the record straight. A common misconception among end users is that NVRs lack features and reliab...
Organizations can develop security master plan internally or use the assistance of an independent security consultant Whether it’s a college campus, a healthcare facility or a large corporation, organizations often tackle issues related to security management, operations, programs and technology in a reactionary manner. They often fail to consider the need to plan and develop a written roadmap to define and provide direction for the big picture of their security program....
Have interactive services lost their edge? Are users discouraged and disenthralled? That’s a myth that needs busting, because security companies continue to have success offering these solutions to customers. Alarm companies who began their business with traditional intrusion detection continue to deliver interactive services as part of a total, connected home solution. Companies like Complete Security Systems, Marlboro, N.J.; Marshall Alarm Systems, Yorktown Heights, N.Y.; and The Securi...
The pre-seminar will also offer educational sessions on cutting-edge subjects It is that time of the year again, when security industry stalwarts gather together at ASIS to showcase the latest in physical security systems and other technological innovations. The event will focus on domestic threats as well as intelligence gathering tools to protect organizations against social media threats. The organizers of the ASIS International 61st Annual Seminar and Exhibits — ASI...
ASIS is a great opportunity to not only learn about new technologies first hand, but also to benchmark offerings against competitors Now in its 61st year, the American Society of Industrial Security (ASIS) Seminar & Exhibits is more than an end-user show. Many systems integrators also attend, walk the show and even exhibit to meet with potential customers and perhaps see technology they may need to apply to their clients’ security challenges and issues. This ye...
Police intelligence can help security directorsto understand the criminal trends across theirarea or city Corporate security has changed dramatically over the last few years. Traditionally, security has always been associated with physical protection and installation of security systems. In this article, Tom M. Conley, president and CEO of The Conley Group, discusses the importance of information received from law enforcement. A good rapport with law enforcement can help...
NVR appliances are increasingly importantfor businesses incorporating a well-roundedphysical security plan A major, oft-mentioned advantage of network video recorder (NVR) appliances is their ease of installation and use. These machines come pre-installed with software and are as close to plug-and-play as you can get in the IP video surveillance world. NVRs are also being designed to support 4K technology as well withstand a variety of applications and uses. W...
Network video recorders (NVRs) are at the center of today’s IP video systems. The video surveillance market includes a wide range of NVR choices for integrators and end users alike. NVR appliances include purpose-built machines that have embedded software systems as well as servers that are sold by video management system (VMS) software vendors and that have been pre-installed and preconfigured with their latest software capabilities. This article will take a loo...
System integration is about adding value, and value-engineering is the solution to address the challenges facing the customer and their facility Leading systems integrators continue to embrace new technology and add a range of services focusing on IT, connectivity and integration. The trend will continue for forward-thinking companies seeking to differentiate themselves from the competition and gain a loyal following of end-user customers. Pref-Tech - History And Backg...
Browse expert commentaries
Expert Section
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
Security beat
- Summer Of Mass Shootings: US Secret Service Report Looks For Answers
- Security Device Manufacturers Develop Interfaces To Be Compatible With Gunshot Detection Technologies
- Could Hackable Automobiles Result In A Large-Scale Disaster?
- viisights’ Next Generation Of Video Analytics Offer ‘Behavioral Understanding’