ESP Witness Observation Kits
Sorry no products match your search. Your search criteria may have been too narrow. If you remove some of your search criteria, this may yield more productive results.
Observation system products updated recently
Observation systems & accessories - Expert commentary

Educational institutions worldwide increasingly rely on robust wireless networks to enhance academic pursuits, safety measures, and operational efficiency. The campus environment...

The promise of electric vehicles is closer to reality than ever before. New plans and investments at the federal level designate billions of dollars to move our country toward clea...

Intrusion alarm systems are currently facing a growing number of potential error sources in the environment. At the same time, alarm systems must comply with increasingly demanding...
Related white papers
Connected Video Technology for Safe Cities
The Borderless Control Room
Monitoring Traffic Flow: Everywhere, All The Time
Trending topic articles
Suprema, a pioneer of AI-powered security solutions, announced that BioStation 3 is expected to set a new annual global sales record by the end of this year. This represents the highest annual sales...
The 19th Real Estate Development Summit Saudi Arabia – Luxury Edition successfully concluded after two days of high-level exchange, strategic collaboration, and global networking, bringing toget...
IDIS has launched two new advanced PTZ cameras, providing powerful AI and NIR performance. The extended range offers a broader choice of PTZ cameras to more efficiently cover open areas, in applicatio...
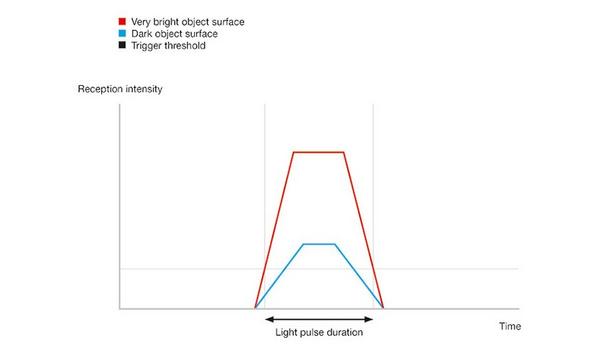
Leuze uses artificial intelligence (AI) to significantly improve the measurement accuracy of optical distance sensors for challenging industrial applications. This innovation improves measurement acc...
Alarm.com and Everon, LLC, a pioneering security integrator and premier provider of commercial security, video, fire, and life safety solutions, today announced a strategic partnership to deliver a un...
Integrated access control and security manufacturer TDSi now announces that from 1st January 2026, it will operate under the new name: TDSi by Hirsch. The change follows the global transformation of...
Aetina Corporation, a pioneering provider of Edge AI solutions, has announced the launch of its next-generation MXM AI Accelerator Module series accelerated by NVIDIA RTX PRO Blackwell Embedded GPUs,...
Abnormal AI, the pioneer in AI-native human behavior security, announced it has been recognized as a Leader in the 2025 Gartner® Magic Quadrant™ for Email Security, marking the company&rsquo...
DigiCert, a pioneer in intelligent trust, unveiled its 2026 Security Predictions, forecasting how AI, quantum computing, and automation will reshape global trust frameworks. The predictions highlight...
Building on earlier research published in October 2025, Zimperium announced that its zLabs team has uncovered a significantly enhanced variant of ClayRat, an Android spyware family first detailed in t...
Iris officially launches today, introducing a platform that transforms how cameras are controlled, and productions are managed. By turning virtually any PTZ camera into a software-connected, remotely...
Secutech, Asia’s premier security exhibition, will be held from 22 – 24 April 2026 at the Taipei Nangang Exhibition Center, Hall 1. This edition promises a robust showcase of more than 400...
Hikvision announced recently that it has achieved the ISO 37301:2021 Compliance Management System certification from SGS, the world's renowned testing, inspection, and certification company. This mil...
Balancing operational efficiencies and customer satisfaction with costs, resources, and legislative obligations is a challenge faced by every security services provider offering keyholding and alarm r...
Axis Communications, a industry pioneer in video surveillance, announces it has signed the U.S. Cybersecurity & Infrastructure Security Agency’s (CISA) Secure by Design pledge to transp...
The Key To Unlocking K12 School Safety Grants
DownloadHoneywell GARD USB Threat Report 2024
DownloadPhysical Access Control
DownloadThe 2024 State Of Physical Access Trend Report
DownloadThe Security Challenges Of Data Centers
Download