Technology & Trends - IP cameras
When video analytics first emerged in the security industry about a decade ago, there were high hopes it would instantly transform the landscape of video surveillance. Problem was, the technology was not mature and, in essence, was oversold as far as its capabilities. Analytics such as heat mapping, directional and license plate recognition technology have improved, lending themselves to applications beyond security and into the realm of actionable business intelligence Integra...
The technological resources from the physical security sector available to prisons dealing with contraband threats are effective For those outside the security industry, the idea of prison contraband rarely extends beyond the old gag of a file inside a cake. In fact, contraband at prisons and other custodial premises is a major challenge: deterring and detecting it occupies many man-hours, and manufacturers devote much R&D activity to the problem. Contrabands In Prison T...
The ultimate goal is to predict violent incidents through analytical intelligence Potential deployments of video analytics, or my own preferred term “intelligent scene analysis,” are being worked on by some of the best minds at university campuses across the United Kingdom. Later this year I will visit Kingston University whose Digital Imaging Research Centre is one of the largest computer vision groups in Europe. Violence Prevention Through Analytical Intelligenc...
In the vast center of the hall almost none of the randomly shaped stands display their index number I enjoy IFSEC each year, spending three days walking the halls. I do feel frustrated by the acres of "me too" products prompting a "meh" response. So often I’m left feeling the "big news" is that hype and lies are growing and continue to drown out the truth. If companies' marketing budgets were simply given over to their product development departments, we would find thing...
When asking exhibitors at IFSEC International 2015 about what drives their markets, many cite system integration as a key factor. And they want more of it. Integration As Business “Driving Force” For example, John Davies of TDSI says customers are now seeking out system integration. “They want a solution rather than components, such as linking access control with building management systems or with an organization’s IT network to control access to its computers,”...
Security beyond its traditional boundaries is a big theme at IFSEC 2015 The security landscape is changing. Touring exhibitors on the first day of IFSEC International in London, it seems an increasing number of vendors are offering products that go beyond what may be termed "security," offering solutions for applications such as health and safety and data collection. They are also offering more smart technology with mobile phones and tablets, and are selling smarter by tailori...
Although in many cases CCTV has been an effective investigation tool, its full potential is not being realised It’s all very well installing CCTV cameras, but to be effective users have to know what to do to make images available to the police and courts, according to detective chief inspector Mick Neville of the Metropolitan Police. Although in many cases CCTV has been an effective investigation tool, its full potential is not being realised, says Neville, who is due t...
Security is a big concern for local government buildings, but there are measures that can make a difference Back in August of 2013, Rockne Warren Newell, armed with a rifle and a handgun, stormed a township meeting in the Ross Township Municipal Building in Saylorsburg, Pa. Witnesses say he fired through a wall into the meeting room and then burst into the room itself, guns blazing. Three people died, and two sustained wounds before citizens attending the meeting restrained hi...
Organizations are looking for ways to maximize resources and extract value from video security investment "There’s valuable information hiding within surveillance video. Extracting it can make a security department more efficient and provide a clear return on investment to their organization." - Dror Irani, CEO and President, BriefCam - The Video Synopsis company. Challenges Of Video Surveillance Video surveillance systems are a blessing to security. They are also a cu...
Managed and hosted services allow users access from a variety of connected devices It’s not about hardware anymore, although quality components are a must. Now, it’s about how technology performs. For the systems integrator, there’s also an opportunity to provide essential services to keep customers connected. As with many other businesses, the security industry is being “disrupted” and influenced by the cloud. Delivering outsourced security and...
The future will produce cost-effective solutions that can provide meaningful coverage of wide expansive areas The greatest trend in history will continue to change the world, and the physical security market. It’s called Moore’s Law. In accordance with Moore’s Law, our electronics have consistently doubled in speed, halved in size, or halved in price every two years for decades already. This trend means that our electronics, communications networks, data ne...
Strategic management of costs is important when considering video storage systems Costs are at issue when considering any component of a video system. Strategic management of costs is especially important when considering video storage systems because storage accounts for such a large cost component of networked systems. Gartner’s Total Cost of Ownership (TCO) As enterprise products begin to dominate the video storage market, more attention needs to be addressed to Gar...
Integrators and end users should be aware that their definition of open might differ from those of security manufacturers Much of the buzz in the industry today about open architecture is driven by the IT world, with many security-related decisions now falling on an organization’s IT department, where true open architecture has been around for a long time. Closed systems like we’ve experienced in the security world are not just viewed as foreign to the IT world; th...
The fundamental value of data is widely apparent in modern society, and its loss may have significant consequences Video data is critical to today’s enterprise. The latest video storage systems must offer dependable operation that doesn’t risk loss of that critical data. DDN - When Performance Matters “Not only is bandwidth very important, but functionality cannot be lost when a storage system is having a bad day,” says Jeff Adams, director of sales,...
According IHS Technology, more than 11 million consumer and DIY network cameras will be shipped worldwide this year Perhaps we should start looking at do-it-yourself (DIY) systems such Google’s Nest and other devices as an opportunity for existing security contractors – those that are open-minded anyway – to bring in additional customers and new streams of recurring monthly revenue (RMR). DIY systems continue to proliferate in the marketplace and are availab...
The trend towards greater unification is facilitated by an all-encompassing shift to IP technologies As more organizations are looking for ways to maximize resources and increase operational efficiencies, unification of multiple security and business systems is gaining popularity. From the central command center, there is significant time lost when operators have to jump from video surveillance to access control systems to analyze an incident and take appropriate measures. Eve...
Just as with network switches, there are no real standards for midspans In general terms, a midspan is a power over Ethernet (PoE) power source that is placed between a network switch and the device being powered, hence the term midspan. The real question is, with almost all network switches providing PoE power, why do we need a midspan? The answer is, in some cases we don’t, but in others we do. As with any other product we have discussed, we need to first consider that...
Honeywell recently helped the Penns Valley Area School district in Pennsylvania design and implement a custom security system Security systems are just part of the solution to protecting K-12 schools. Technology can contribute to a broader, holistic approach to security that is customized to meet the needs of each educational institution. Honeywell has helped many schools customize security systems to meet each school’s unique needs, says Bruce Montgomery, Business Deve...
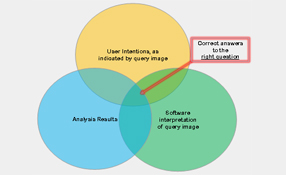
see bigger image Figure 5: Providing correct and useful results requires intersection of user intentions, VCA interpretation, and results provided by VCA tool The term Video Content Analysis (VCA) is often used to describe sophisticated video analytics technologies designed to assist analysts in classifying or detecting events of interest in videos. These events may include the appearance of a particular object, class of objects, or action. VCA technology employs a comple...
Beyond the need to install new systems, often overlooked is how schools are going to pay for security upgrades Limited financial resources are a common pain point for K-12 schools looking to implement cutting-edge security technology. But security needs persist despite scarce resources. All school administrators want to do everything in their power to secure their facilities against threats. More schools are recognizing the benefits and, in some cases, requirement of upgradin...
Wong was the first Asian woman to obtain the Alarm Contractor License Mun C. Wong, PSP and president of VinTech Systems Inc. in Chicago, is a successful entrepreneur who has brought new technologies and a knack for superior service to her integration business. In fact, at the age of 29, she was the first Asian woman to obtain the Alarm Contractor License from the State of Illinois and its Department of Financial and Professional Regulation. But she doesn't focus on gend...
Employees are the front line of defense — as well as the most economical defense — against shrinkage losses The financial cost of retail shrinkage is huge. The latest Annual Shrink Report issued by Dr. Richard Hollinger and Dr. Read Hayes at the University of Florida puts the total at $36 billion annually. Shrinkage has several causes: customers shoplifting , employee theft, supplier fraud and administrative errors. Frequent inventories and accounting audits coun...
Integrators must understand that the K-12 market has a unique and urgent need for access control, but with limited budgets Systems integrators play a key role delivering effective security solutions to the kindergarten through 12th grade (K-12) education market. Schools certainly depend on an integrator’s expertise regarding which electronic products to choose. However, schools also rely the benefit of an integrator’s experience and the insight gained by putting se...
Readily available security technology can help officials take control of their campuses Two top priorities for school security are the ability to communicate within a facility, and the ability to control access of who comes and goes. Paul Timm, president of RETA Security, an independent school security consulting firm, acknowledges the value (and popularity) of video cameras for school security, but that value is almost completely realised in terms of forensics – reactin...
Layering as applied to computers is a made up term having no relationship to any particular standards When it comes to setting the criteria for network switching, we often hear “I only want a layer 3 switch.” We naturally assume that since the number 3 is bigger than the number 2, a layer 3 switch must be better than a layer 2 switch. It may surprise you, but when it comes to video security applications, this may not be the case. In fact, just the opposite may...
Kevin Brownell, principal physical security consultant at PTS Consulting Group, considers convergence of IT networks and physical security. He argues that current best practice shows that they no longer need to be separate disciplines and reassures installers that their diversity has been exaggerated. Brownell describes experiences of working with IT managers who no longer see networked CCTV and access control as ‘black arts’ and are buying into the idea of IP security as an integr...
Companies need to increase the knowledge within their business on the range of cyber-vulnerabilities At one time, embedded devices, such as access control components communicating with application software, used proprietary protocols like RS485. Use of proprietary protocols kept these devices safe from attack. However, in this article TDSi Technical Director Mike Sussman explains that the growth of the Internet of Things (IoT) involves a move toward IP-based systems and open s...
Organizations must find more effective ways to optimize the use of the resources they have available As market demand intensifies for higher resolution from megapixel, and 4K cameras, customers will begin to feel the ensuing cost pressures caused by the increased need for greater processing power. As customers update their system and add new cameras, operators must monitor additional cameras concurrently, oftentimes leveraging high resolution video streams. HPC For Quick...
School administrators are now choosing products that make the biggest, long-term impact on campus security Well-publicised events such as the U.S. school shootings at Columbine and Sandy Hook lead to an increased demand of security equipment to protect kindergarten through 12th grade (K-12) education campuses. But do they also result in buying decisions made on impulse that don’t necessarily meet a school’s most pressing security needs? Increase In Demand For Secu...
4K places extra demands on video security but the results can be rewarding Since last year there has been a lot of talk with regard IP security cameras with 4K resolution. As with any advancement in video security, this too has come about due to advances in consumer electronics. While being the “latest and greatest,” it still raises questions as to actual, practical everyday usage. What Is 4K Resolution? Let’s start by defining 4K. Back in the day we had HD...
Browse expert commentaries
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
Climax Mobile Lite: Advanced Personal Emergency Response System (PERS)
Hanwha Vision OnCAFE: Cloud-Based Access Control for Modern Enterprises
Delta Scientific MP100 Portable Barricade Solution
























_286x175.jpg)



















