Incident Management - Security beat
In the physical security industry, the advent of artificial intelligence (AI) and deep learning is most commonly associated with potential improvements in video analytics performance. However, AI is also applicable to a variety of content analytics beyond video. It will be interesting to watch how companies that take the next step beyond proving viability for security purposes to deliver true business applications to the market. Right now, we’re seeing organizations working hard to develo...
The Global Security Exchange (GSX) seems smaller this year, which is not surprising given the absence on the show floor of several big companies such as Hikvision and Assa Abloy (although their subsidiary HID Global has a big booth). A trend affecting the number of companies exhibiting at GSX 2018, and other trade shows, is industry consolidation, which is impacting the show even beyond the fewer exhibitors this year in Las Vegas. GSX is the new branding for the trade show formerly known as ASIS...
When an active assailant strikes, it’s over fast, and most of the damage happens before help arrives. Responding appropriately can save lives, and it takes training and practice to know what to do as a tragedy unfolds: Where can I hide? Can I get out? Where do I run? If you hear shots or see someone with a knife, your training empowers the best response, and thorough and repetitive training avoids being paralyzed by panic. Standards On Workplace Violence ASIS International is a member of...
One factor aggravating concerns about workplace violence in corporate America is the easy availability of firearms. In many states, citizens, including employees, have the right to carry firearms onto a company’s property even though firearms are prohibited in the workplace. In effect, an employee prone to violence may have a firearm as near as their vehicle in the company parking lot. Currently, 23 states in the U.S. have so-called “parking lot storage” laws, which enable em...
Twitter has around 350 million active users a month, all eagerly posting 280-character “tweets” about the world around them. It’s a vast amount of data from all over the globe. Security professionals have begun to appreciate the value of mining all that data for insights to help them protect people, assets and operations. One company leveraging the Twitterverse to provide real-time situational awareness to corporate security end users is Dataminr.Dataminr assembles this inform...
Several recent terrorist and mass violence attacks have been directed at soft targets, or relatively unprotected locations where people gather such as outside a music venue or in the unscreened passenger areas at airports. Attacks in public areas have led to the development of new security technologies aimed at protecting soft targets. One company addressing the challenges is Evolv Technology and its Edge automated high-speed personnel screening solution. The system integrates walkthrough fire...
Open architecture in physical access control is built around Mercury Security’s access control panels, the de facto standard embraced by more than two dozen access control original equipment manufacturers (OEMs). Mercury and several of its OEMs teamed up March 3-4 to present MercTech4, a conference in Miami aimed at updating security consultants about the latest developments related to the Mercury platform. MercTech4 highlighted a new generation of access control products, which are incre...
Heightened security is the watchword throughout Europe and around the world after the recent dual terror attacks in Brussels. Two explosions at Brussels’ Zaventem airport were followed an hour later with a third bomb at the Maelbeek Metro station, just 100 meters (about 300 feet) from the headquarters of the European Union. In all, 35 people died (including three suicide bombers), and more than 300 others were injured, 62 critically. Raised Security Levels Worldwide In Belgium, flights w...
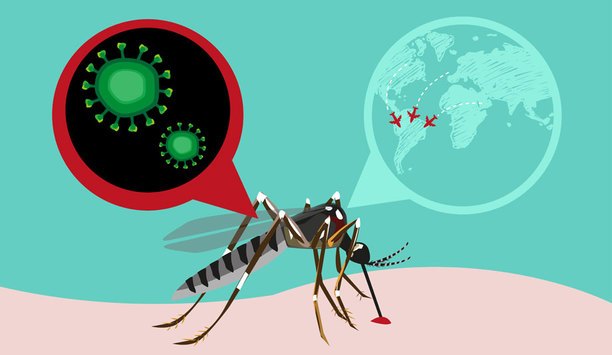
Many companies are considering carefully the possible risks of business travel to the areas most impacted by the Zika virus, and others may have facilities located in affected areas. What Is The Zika Scare? Transmitted by mosquito bite, the Zika virus can cause a fever that typically involves minor symptoms. There is an additional risk to pregnant women as Zika fever has been linked to incidences of microcephaly (a neurodevelopmental disorder) in newborn babies through mother-to-child transmi...
Politics will be dominating current events in 2016 in the United States, building up to the Presidential election in November. Given the Presidential primaries coming up soon, almost everything – including security – is being seen through a political prism. With the recent San Bernardino attacks, the focus has once again shifted to protection of citizens against terrorist attacks. Government surveillance, such as monitoring of suspected terrorists or individuals has always been a con...
Second guessing is to be expected in the wake of terrorist attacks like the recent tragedy in Paris. After such attacks, security and intelligence professionals are prone to soul-searching – and to speaking out on the public airwaves –to address important questions: Could we have prevented it? What should we have done? There tend to be two categories of second-guessing. The first centers on the idea that the intelligence community should have known about the planned attack and...
In a school security lockdown, teachers typically display red or green cards on the doors or in the windows of their classrooms. The manual procedure uses red cards to alert to a crisis condition; green cards designate that everything is safe inside the classroom or office. Color-Coded Crisis Management System Physical security company Sielox has adapted the idea of using a color scheme to characterize an emergency situation into its electronic security system. CLASS [Crisis Lockdown Alert Sta...