Technology & Trends - Video Surveillance
For high value individuals such as the Pope,agencies have access to unlimited publicresources in terms of money and people The Pope’s visit to the United States reminds us that protecting big-name executives, celebrities and dignitaries is a highly specialized security function. Public and private executive protection groups begin preparing for the visit of major world figures months ahead of time. “It is a task of massive proportions,” says Tom M. Con...
NVRs make it easy to benefit from HD solutions and integrations to access control, alarm systems, intercoms and other technologies Developments in the IP video camera market have a direct impact on the other components in a system. With the emergence of higher definition cameras – whether 4K cameras or 8K or even higher – the market now needs back-end devices that can perform the decoding work. Also, more intelligence is needed, including smart functions such as pe...
7K cameras are best suited for large openspaces such as stadiums and city centers,capturing the finest details in their footage With several manufacturers now offering 4K CCTV cameras, Avigilon, based in Vancouver, B.C., raised the bar in April 2015 with the launch of their 7K HD Pro surveillance solution. The 30-megapixel camera is the latest addition to the company’s Professional Series, an innovative model Avigilon believes will drive competition in the security indus...
How do you get all of your various vendors, services, resources, manpower, and technology to integrate and work together? Creating an efficient operating environment in physical security is no small feat - especially when the organization undertaking such an endeavor has a nationwide presence. How do you get all of your various vendors, services, resources, manpower, and technology to integrate and work together? How do you aggregate all of the data being recorded into inf...
Enterprise security strategies identifyliabilities & ways to mitigate risks, showinghow the cost of mitigation prevents largerliabillity costs The security profession continues to take on new risk management responsibilities. The big thing now is called Enterprise Security and Risk Management (ESRM). ASIS International has issued a standard on the subject: ANSI/ASIS/RIMS RA. 1-2015, and a couple of booths at the recent ASIS International 2015...
As technology advances and more surveillance features become available, it can be difficult for security integrators to know which system will fit their customer’s needs It’s no secret that Internet Protocol (IP) cameras are on a steady march to replace analog video. Network-centric surveillance cameras bring a host of value to the protected premises, above and beyond traditional physical security. Now, cameras are increasingly used for safety, such as in liability...
NVRs come preinstalled with latest software releases to minimize setup time Looking for a perfect marriage of hardware and software for a video management system application? A preconfigured network video recorder (NVR) appliance may fit the bill. Consider these advantages of going the NVR appliance route, as suggested by vendor companies contacted by SourceSecurity.com. 1. Greater Freedom Of Deployment NVRs provide more application flexibility – because the recorders...
The open and exposed nature of rail yards exposes railway assets to tremendous risk The importance of rail transportation in driving the U.S. economy cannot be overstated. In recognition of this, America’s railroads are investing in the infrastructure and technology necessary to improve security for the tracks, bridges, tunnels and other vital components that make up this critical transportation network. The unique security requirements of these assets present a nu...
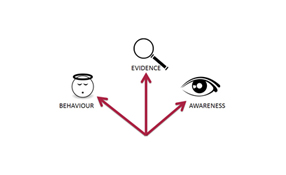
Ballantyne has created the "Three Vectors of Value" for video surveillance - Awareness, Evidence and Behaviiour The annual global expenditure in new video surveillance systems is currently estimated at about 20 billion USD and grows at a rate of better than 15% per year. To those of us in the business, these figures both encourage and validate. The expenditure is impressive, but only because commensurate value is delivered. That is, we expect expenditure and value to bal...
The potential costs and consequences of hackers getting through firewalls and onto the user’s computer networks can be devastating Theft of NATO data. Leakage of emails. Hackers setting up a live streaming website for over 100 New York City private webcams and even hacking the infrastructure servers of the U.S. government. As news of malicious takeover of private and corporate networks as well as incidents of malicious software programs, referred to as malware, conti...
NVR appliances ease analog to IP transition by providing end users with a hybrid-ready product There should be a palatable migration path from a large installed base of analog to the latest IP technology. The biggest missed opportunity related to network video recorder (NVR) NVR appliances in the video surveillance marketplace is effectively using existing analog camera investments while transitioning to the network. For example, IP encoders can be utilized as a bridg...
Aventura continues to expands expand its feature set of products beyond PSIM As the 61st annual ASIS 2015 kicked off in Anaheim, Calif., it became increasingly clear that physical security continues to move from the realm of traditional intrusion detection, video surveillance and alarms into value-added applications that extend into new markets, uses and purposes – many of them centred on business and operational processes. While video surveillance, intrusion detection,...
The potential is huge for vendors in the security and technology industries that have gun detection-related services & products Gunshot detection systems are a fast growing trend that helps police and security guards to protect the public, capture criminals and collect forensic evidence for investigations. Gunshot detectors use digital microphones installed on (or in) buildings or along streets that listen for evidence of gunshots, provide near instantaneous notification,...
NVRs of the past may have been expensive & complicated to use, but today NVRs have user-friendly functionality How much do you know – or think you know – about network video recorder (NVR) appliances? Manufacturers in the sector say there is a lot of misinformation in the market about these workhorse system components. We asked several manufacturers to help us set the record straight. A common misconception among end users is that NVRs lack features and reliab...
Organizations can develop security master plan internally or use the assistance of an independent security consultant Whether it’s a college campus, a healthcare facility or a large corporation, organizations often tackle issues related to security management, operations, programs and technology in a reactionary manner. They often fail to consider the need to plan and develop a written roadmap to define and provide direction for the big picture of their security program....
Have interactive services lost their edge? Are users discouraged and disenthralled? That’s a myth that needs busting, because security companies continue to have success offering these solutions to customers. Alarm companies who began their business with traditional intrusion detection continue to deliver interactive services as part of a total, connected home solution. Companies like Complete Security Systems, Marlboro, N.J.; Marshall Alarm Systems, Yorktown Heights, N.Y.; and The Securi...
The pre-seminar will also offer educational sessions on cutting-edge subjects It is that time of the year again, when security industry stalwarts gather together at ASIS to showcase the latest in physical security systems and other technological innovations. The event will focus on domestic threats as well as intelligence gathering tools to protect organizations against social media threats. The organizers of the ASIS International 61st Annual Seminar and Exhibits — ASI...
ASIS is a great opportunity to not only learn about new technologies first hand, but also to benchmark offerings against competitors Now in its 61st year, the American Society of Industrial Security (ASIS) Seminar & Exhibits is more than an end-user show. Many systems integrators also attend, walk the show and even exhibit to meet with potential customers and perhaps see technology they may need to apply to their clients’ security challenges and issues. This ye...
NVR appliances are increasingly importantfor businesses incorporating a well-roundedphysical security plan A major, oft-mentioned advantage of network video recorder (NVR) appliances is their ease of installation and use. These machines come pre-installed with software and are as close to plug-and-play as you can get in the IP video surveillance world. NVRs are also being designed to support 4K technology as well withstand a variety of applications and uses. W...
Network video recorders (NVRs) are at the center of today’s IP video systems. The video surveillance market includes a wide range of NVR choices for integrators and end users alike. NVR appliances include purpose-built machines that have embedded software systems as well as servers that are sold by video management system (VMS) software vendors and that have been pre-installed and preconfigured with their latest software capabilities. This article will take a loo...
System integration is about adding value, and value-engineering is the solution to address the challenges facing the customer and their facility Leading systems integrators continue to embrace new technology and add a range of services focusing on IT, connectivity and integration. The trend will continue for forward-thinking companies seeking to differentiate themselves from the competition and gain a loyal following of end-user customers. Pref-Tech - History And Backg...
IP video recording systems offer high-resimaging, speed & analytics to its end users Familiarity With Analog Systems Familiarity is one factor in the slow conversion of casino customers to IP technologies. Many end users and integrators are comfortable with and have long-term experience with the more simplistic analog systems. However, as IP systems continue to become easier to install and maintain with more plug-and-play technology, this dynamic should ch...
IP is here and is continuing to proliferate in the security industry and its next major advancement is in pure IP access control IP technologies in the security industry are nearly ubiquitous today. End users and integrators have adopted and embraced IP cameras, building automation systems, wireless mesh networks, alarms, monitoring, and regularly view all of these technologies from the palm of their hand, on their smart phone. The technologies are easier to in...
Increases in the number of cameras and storage capacity have created an overabundance of video information that is difficult to manage Investment in video surveillance technology continues to increase as technology improves and security equipment becomes more affordable. Companies invest in video surveillance primarily to protect people and property, for both deterrence and more crucially for incident response. While there’s no doubt that the systems can...
The worst insider threats are existential, dangerous enough to literally destroy an organization The key to maintaining an effective security system is timely detection of security breaches. Widespread use of technology has resulted in massive amounts of data transfer which in turn makes organizations vulnerable to both internal and external threats. Mass shootings, data thefts and other internal breaches of security have cast a spotlight on the issue of insider threats. Accor...
RFI Enterprises has a Central Station Alarm Association (CSAA) Five-Diamond Monitoring Center RFI Enterprises started in a small town and has over the years grown to a large regional business. The company has developed innovative security solutions to fulfill customer’s requirements for a secure environment. It has managed to stay ahead of growing competition within the systems integrator sector and design solutions for customers ranging from aerospace, banking and healt...
9-11 caused a sharp refocus of attention on security assessment and risk management Fifteen to 20 years ago, security was a relatively sleepy, small-time business. Companies typically hired a guard or two to walk around the property, usually at night, sometimes during the day. If a guard spotted someone who wasn’t supposed to be there, he (it was usually a he) ran the person off. Larger companies had more sophisticated video and access control systems, but those systems...
Successful video infrastructure management requires visibility into the network’s behaviour The importance of video in an organization has been growing over the past several years, almost exponentially. In retail, video images can help detect or deter theft by employees and patrons. Casinos use video partly due to state regulations, to ensure gaming activity is free of deceit or fraud. Branch offices use video to communicate with the head office. Schools use video for di...
Any wireless device can be a soft target for hackers Security network hacking is one of the hottest topics today. The ability to access security systems or devices anywhere, leaves them vulnerable and prone to hacking. Any wireless device can be a soft target for hackers. Let’s start with the concept that nothing on a network is really secure. Let’s admit this to ourselves and take the next steps to make our security networks more secure. Internet of Things Securi...
With the power of new technology and analytics, security systems could be used in other ways as well Security and surveillance systems are valuable beyond strictly providing compliance in the casino market. Even beyond ensuring physical security on premises outside the casino floor, systems are providing additional benefits including customer service, marketing and profitability, says Maureen Bruen, vertical market specialist – gaming, Honeywell Security Products Ame...
Browse expert commentaries
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
KentixONE – IoT Access And Monitoring For Data Centers
Climax Technology HSGW-Gen3 Modular Smart Security Gateway
Delta Scientific DSC50 ‘S’ Barrier: Portable, Crash-Rated Vehicle Mitigation Solution