Security cameras - Security beat
Drones are poised to fill long-standing gaps in physical security. Fixed cameras leave blind spots, and human guards cannot quickly cover large or complex properties during high-risk moments. Drones fill the gaps, providing a missing mobile layer, offering unmatched speed, broad aerial visibility, and proactive coverage that elevates security from reactive to truly responsive and deterrent. As an added element in security systems, drones complement fixed cameras, access control, and license pla...
There was high-level energy at GSX 2025, befitting an industry undergoing massive change. Artificial intelligence (AI) was everywhere, but not so much in the booth signage. Rather, AI has made its way beyond marketing claims and solidly into the core of the products themselves. There were hundreds of examples of how AI is changing how security systems operate, all for the better. Clearly on display at GSX 2025 was an industry in the midst of metamorphosis. Deep integration of AI My con...
Ibrahim Kassem, Everon’s new Chief Technology Officer (CTO), has been in the security industry since 1998 in various IT leadership roles. Most recently, he was Chief Information Officer for a video monitoring company. With most of his professional experience rooted in commercial security, Kassem has come to understand how customer needs and demands change with the evolving technology landscape. That understanding is a foundation for his new role at Everon, the national provider of commer...
For all the emphasis on cloud systems and centralized servers at ISC West, a lot of innovation in security video systems is happening at the edge. New advancements inside video cameras are boosting capabilities at the edge, from advancements in processing power to artificial intelligence (AI) and machine learning (ML) algorithms that can now be deployed directly on the cameras or edge devices. Advancements in AI algorithms The progress of video systems becoming smarter at the edge is driven...
Anyone who has been in a proverbial cave for the last couple of years faced a language barrier at this year’s ISC West 2025 trade show. The industry’s latest wave of innovation has brought with it a new bounty of jargon and buzzwords, some of which I heard at ISC West for the first time. As a public service, we are happy to provide the following partial glossary to promote better understanding of the newer terms. (Some are new to the security industry but have been around in the IT...
ISC West 2025 in Las Vegas showcased the latest advancements in security technology, offering security professionals a glimpse into the future of the industry. This year's expo highlighted the growing influence of artificial intelligence (AI), cloud computing, and enhanced integration. The pioneering comprehensive and converged security event attracted nearly 29,000 industry professionals to the Venetian Convention Center. Integration into unified platforms Several companies emphasized...
The practice of executive protection changed forever on Dec. 4, 2024, when UnitedHealthcare CEO Brian Thompson was shot outside a Manhattan, New York, hotel. The shocking event raised awareness in board rooms around the world about the need for, and challenges of, executive protection. Questions followed immediately, including why was the high-level executive not protected? Combination of risk and reward UnitedHealthcare’s stock price has gone down more than 20% since the shootin...
As the pioneering security event in the United States, ISC West is truly the global focal point for bringing together professionals across the physical and cybersecurity landscape. The event seeks to showcase innovation in security technology, nurture professional development, and explore the security implications of today’s connected world. Future of security With the growth of cybersecurity programming and the established Cybersecurity & Connected Internet of Things (IoT) p...
Big news on the mergers and acquisitions (M&A) front is closing out 2024, a year in which several shifts changed the face of the physical security manufacturer community. Announced in December, German giant Bosch Group is selling its Building Technologies division’s product business for security and communications technology to the European investment firm Triton. Bosch division selling to Triton The transaction encompasses three business units – Video, Access and...
With the year 2025 stretched out before us, there are many techniques one could use to predict what will happen in the new year. You might analyze historical data and analyze future trends. Or you could try statistical or economic modeling. Or you could develop multiple scenarios based on various assumptions to explore potential outcomes. Or you could just check your email. At this time of year, my email is full of industry folks looking to predict what the future holds in 2025. Ranging from a...
The pattern of veins in the hand contains unique information that can be used for identity. Blood flowing through veins in the human body can absorb light waves of specific wavelengths. Irradiating the human palm with near-infrared light waves yields an image of the vascular pattern. A venous distribution map can be processed and compared to pre-registered data to match and confirm identity. Palm vein biometrics The idea of palm vein biometrics goes back to the 1980s when pa...
The information age is changing. Today, we are at the center of addressing one of the most critical issues in the digital age: the misinformation age. While most awareness of this problem has emerged in the consumer and political worlds, the issue cannot be ignored when it comes to the authenticity and protection of video and security data. Video surveillance data SWEAR is a company with the mission to ensure the integrity of video surveillance data by mapping video data and writing it into...
Casinos face multiple security issues caused by potential bad actors, everything from cheating to vandalism, from theft to vagrancy. A new intelligent technology can monitor for specific keywords and behaviors. The technology scans the entire casino premises constantly for potential threats and notifies key personnel when they happen. Casinos are among the environments deploying the OpticSense system by Huvr Inc., which uses special fiber optic technology called an interferometer to secure larg...
In today's complex security landscape, ensuring the safety of building occupants and assets requires more than just cutting-edge technology. Holistic approach The SHIELD certification, introduced by the Secure Buildings Council, is designed to help building owners, tenants, and security professionals navigate this challenge effectively. SHIELD offers a holistic approach to physical security that emphasizes not just the systems in place, but the collaboration among all stakeholders. With prac...
Security applications for drones have evolved to provide benefits such as bird's-eye views of large areas, easy access to remote locations, and rapid deployment. However, to date, most drone applications have been outdoors. Not for long. Today, indoor drones are also finding unique opportunities for enhanced surveillance, security, and operational efficiency in indoor environments such as offices, warehouses, self-storage facilities, and malls. Indoor drones can navigate complex indoor spaces,...
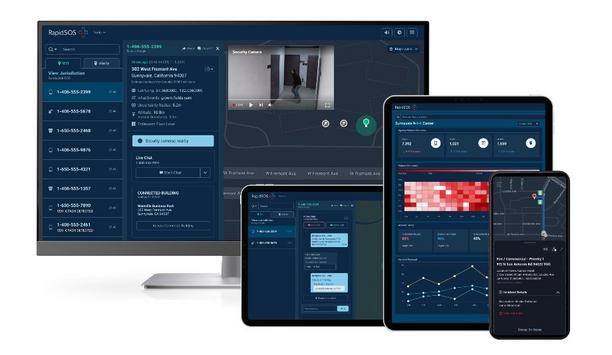
In an emergency, information is pivotal. More information provides better understanding of an emergency and empowers potentially life-saving decision-making. Emergency response teams depend on information to guide their efforts and to deliver targeted assistance. On the front lines of emergency response are 911 and field responder agencies, which must direct reaction to life-or-death situations rapidly and efficiently. Historically, 911 operators had to respond based on very little information,...
Security professionals are recognizing the intelligence value of leveraging publicly and commercially available information. This information can now be accessed more effectively from typically hard-to-reach regions. Also, the technological capabilities have matured in our age of artificial intelligence, machine learning, and data science. Intelligence has historically been based on classified data. However, today’s unclassified data, including open-source intelligence (OSINT), is increa...
Already a strong player, particularly in New Zealand and Australia, Gallagher is still climbing in the U.S. market, which it sees as a big opportunity to invest in the company. Active in the United States for 10 years, Gallagher undertook a more aggressive growth strategy about five years ago. There are 52 employees in Gallagher’s U.S. security business, and about half the workforce has been hired in the last couple of years. They have grown from three sales territories to 16, operated b...
As the physical security and cybersecurity worlds converge, many industry professionals are finding themselves moving from one realm to the other. Or, more likely, they are embracing both disciplines as integral to the future of security as a whole. One security professional bringing her cybersecurity expertise to the physical security market is Wendy Hoey, Director of Sales, US Sales Leadership, North America, for Milestone Systems. With more than 23 years of experience in cybersecurity, Wend...
Active shooter situations grab the most attention, but there is a long list of other threats facing schools, including bullying, vandalism and emergency medical situations. Broadly speaking, a comprehensive approach to school security should prioritize prevention, preparedness and response to all threats. Holistic security approach “Fostering a culture of safety within a school, which involves strong relationships, trust, and communication, is highly effective and does not require...
Companies at GSX 2023 emphasized new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the...
GSX 2023 has its share of new product announcements, although many of the new products are enhancements to technologies shown at last spring’s ISC West show in Las Vegas. Booth traffic on the first day seemed busy at the Kay Bailey Hutchison Convention Center in Dallas, although one exhibitor complained that it takes some time for the traffic to make its way to the farthest areas of the show floor. Apparent throughout the GSX show is an expanding idea of what constitutes security. Incre...
When it comes to security cameras, the end user always wants more—more resolution, more artificial intelligence (AI), and more sensors. However, the cameras themselves do not change much from generation to generation; that is, they have the same power budgets, form factors and price. To achieve “more,” the systems-on-chips (SoCs) inside the video cameras must pack more features and integrate systems that would have been separate components in the past. For an update on t...
Well attended and generating levels of excitement not seen since before the pandemic, ISC West may provide just the shot of adrenaline we need to drive industry success through the uncertain economic times ahead. Buzzwords like artificial intelligence (AI) and the cloud were still prevalent at the conference and exhibition in Las Vegas, but the hype of yesteryear seemed more subdued. Rather than breakthroughs to be celebrated, AI and cloud were discussed more as ways systems can realize even g...
Matter is a new open-source interoperability standard that will simplify the connectivity of smart home systems, including security. The growing popularity of the Matter 1.0 standard was evident at the large Consumer Electronics Show (CES) in January in Las Vegas, where the standard was heavily promoted by companies including Google, Amazon, and Samsung. A flood of Matter-connected products is on the horizon for ship dates in the second half of 2023. Evolve, and manage IoT standards Cr...
New buzzwords were abundant in the articles that generated the most clicks on our website in 2022. From the metaverse to the Internet of Things, from frictionless access control to artificial intelligence (AI), the topics most popular among our site’s visitors were at the cutting edge of change and innovation in the physical security marketplace. Here is a review of the Top 10 Articles of 2022, based on reader clicks, including links to the original content: Metaverse will promote collab...
Collaboration among manufacturers in the physical security industry can result in systems that are easier to install for integrators and that provide a better customer experience for end users. Illustrating the point is the recent collaboration among a turnstile technology company, a supplier of short-range wireless readers/writers, and a biometric business focused on ‘frictionless’ access control. “The more manufacturers collaborate with each other, the more benefits fo...
Clean, safe mass transit systems benefit everyone. Today’s transit operators face tremendous challenges, including declining revenue due to work-from-home policies, concerns about disease prevention, and high crime environments. Among these concerns, difficulty recruiting and retaining police resources has been exacerbated by the ongoing mental health crisis that disproportionately impacts public transportation networks. Mass transit systems Safe cities require an operational environme...
Milestone Systems wants to double its revenue in the next five years while also setting a new standard of how technology companies behave, spotlighting more responsible use of technology. In short, the open platform video management system (VMS) company seeks to revolutionize the industry, deploying data-driven video software in security and beyond. Milestone is also shifting the approach from tech-centric to emphasizing business outcomes; that is, focusing on solving problems that keep their...
Operational technology (OT) uses hardware and software to monitor and control physical processes, devices, and infrastructure. Historically, OT systems were not connected to the Internet and were therefore not vulnerable to cyber-threats. Internet of Things (IoT) However, today’s OT systems are increasingly part of a company’s networks as technologies converge and the Internet of Things (IoT) gains prominence. No longer can OT systems be counted on to be “air-gapped,” t...