Security Assessments
Pioneer wireless fire safety solutions provider Ramtech has established its first international base, opening a new U.S. office in Charlotte, North Carolina. The move reinforces the company’s commitment to delivering modern fire and safety across the construction industry and establishing a full U.S. supply chain. By establishing a permanent presence on the Atlantic coast, Ramtech, which is headquartered in Nottingham, will enhance efficiency, mobilization and reliable delivery of safety...
Abnormal AI, the pioneer in AI-native human behavior security, announced it has been recognized as a Leader in the 2025 Gartner® Magic Quadrant™ for Email Security, marking the company’s second consecutive year in the Leaders Quadrant. Gartner evaluated vendors based on their Completeness of Vision and Ability to Execute. Among 14 vendors evaluated, Abnormal was placed furthest right on the Vision axis. API-based approach In the report, Gartner highlights that “the high...
BlackFog, the pioneer in AI-based anti data exfiltration (ADX) technology, announces the availability of its newest solution, ADX Vision. Designed to secure every endpoint and every LLM interaction, ADX Vision delivers the visibility and control organizations need to manage AI securely. Operating directly on the device, it detects shadow AI activity, prevents unauthorized data movement in real-time, and enforces governance policies automatically, all without disrupting productivity. Increase...
Magenta Security Services marked its 30th anniversary in style last night at the Security & Fire Excellence Awards, where the company was named Security & Fire Sustainability Champion for the third year running. The Security & Fire Awards for Excellence are recognized across the sector as a benchmark for outstanding performance, innovation and best practice in both security and fire. The Sustainability Champion category honors organizations that demonstrate leadership in environment...
Cyware, a pioneer in AI-powered threat intelligence management, automation, and security orchestration, announced a strategic partnership with Microsoft built on deep product integrations to help global enterprises and public sector organizations operationalize threat intelligence with greater speed, ease and confidence. The partnership delivers a uniquely integrated threat intelligence workflow across Cyware and Microsoft Sentinel, giving customers a faster path from threat insights to action....
ZBeta, a pioneer in delivering comprehensive physical security consulting services, has announced the appointment of Chris Martini as Principal Consultant. In this role, Chris will guide strategic initiatives, strengthen client partnerships, and help advance ZBeta's mission of delivering transformative solutions. Prior roles of Chris Martini Chris is a board-certified security pioneer with more than 30 years of experience designing and pioneering enterprise risk, physical security, and resil...
News
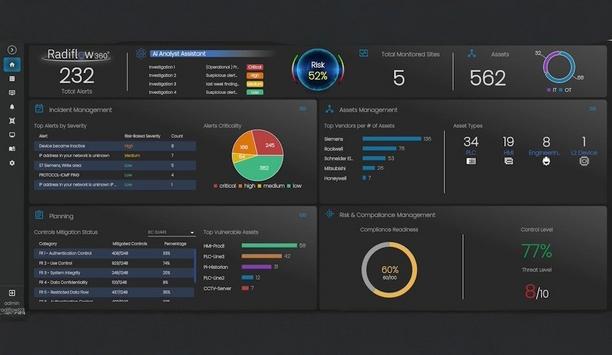
Radiflow, a pioneering provider of cybersecurity solutions for industrial automation networks, announced that the company has launched the new Radiflow360, a unified, AI-enhanced OT cybersecurity platform that delivers full visibility, risk management and streamlined incident response for mid-sized industrial enterprises. Radiflow360 now enables mid-sized industrial operators to gain full visibility and control over their OT networks and risks, and is supported by an AI analyst assistant that speeds up assessments and prioritizes threats. Unified approach to OT cybersecurity The built-in AI analyst assistant seamlessly interfaces with retail GenAI engines to bridge skill gaps This new platform streamlines compliance, accelerates incident response and integrates seamlessly with other Radiflow and third-party tools, delivering a scalable, unified approach to OT cybersecurity. The built-in AI analyst assistant seamlessly interfaces with commercial GenAI engines to bridge skill gaps and accelerate incident investigation. Initial phases of asset discovery Radiflow360 targets OT security teams at mid-sized industrial enterprises that need comprehensive, real-time control of their operational environments, but often struggle with manual processes and siloed tools. The platform frees these organizations from the need to juggle multiple systems by unifying intrusion and anomaly detection with the initial phases of asset discovery and risk assessment in a single pane of glass. New Radiflow360 platform For Radiflow’s partners, the new Radiflow360 platform offers a centralized solution to deliver scalable services This integrated platform enables precise asset mapping, automated risk and compliance scoring, streamlined security control planning and continuous anomaly monitoring, dramatically reducing complexity and accelerating response times. For Radiflow’s partners, the new Radiflow360 platform offers a centralized solution to deliver scalable, differentiated OT security services to their mid-range industrial enterprise and OT operator customers. OT Managed SOC service “Barrier has been working with Radiflow for many years and the company’s solutions add significant agility to our OT Managed SOC service we provide to industrial enterprises across the UK,” said Iain Slater, Sales Director at Barrier Networks. “The new Radiflow360 platform, in particular its unified approach to OT security, is exactly the kind of innovation our mid-market OT operator customers need at a time when UK industrial organizations are facing an increasing wave of targeted OT cyber-threats.” OT cybersecurity risks and threats “2025 marks a pivotal year for Radiflow — we have doubled our sales in the first half of the year and are stepping forward with a renewed focus on our mission to deliver solutions for our industrial enterprise and critical infrastructure customers and partners to efficiently manage the lifecycle of OT cybersecurity risks and threats,” said Ilan Barda, CEO at Radiflow. “The launch of our new Radiflow360 platform is an exciting milestone in our ongoing mission with a focus on providing mid-market industrial operators with a unified framework to manage their OT security lifecycle - from asset discovery to risk assessment and anomalies monitoring to AI-powered risk assessments and prioritizations." Radiflow will be presenting its new Radiflow360 platform at the IT-SA Expo Congress on October 7 to 9 in Nuremberg, Germany.
Sophos, a pioneer of innovative security solutions for defeating cyberattacks, announces the launch of Sophos Advisory Services, a suite of security testing services designed to identify gaps in organizations’ security programs. These offerings – External Penetration Testing, Internal Penetration Testing, Wireless Network Penetration Testing, and Web Application Security Assessment – help fortify an organization’s defenses against cyberattacks and optimize their current security investments. Demonstrating regulatory compliance Regardless of an organization’s size or security maturity, assessing cybersecurity posture is critical to staying ahead of threat actors, demonstrating regulatory compliance, and building trust with customers, partners, and stakeholders. The Sophos State of Ransomware 2025 report highlights that the number one root cause for ransomware attacks is exploited vulnerabilities, and 65% of organizations reported a known or unknown security gap as a reason for being exposed to a ransomware attack. “Adversaries are increasingly skilled at exploiting the smallest cracks in an organization’s security program. With Sophos Advisory Services, we give customers a proactive advantage - helping them find and fix weaknesses before attackers can exploit them. Backed by real-time insights from Sophos X-Ops threat intelligence, our experts enable organizations to strengthen resilience, meet compliance requirements, and build lasting trust with stakeholders,” Jake Dorval, Senior Director, Sophos Advisory Services. Incident response engagements The following services — informed with leading threat intelligence research and insights from Sophos X-Ops, along with findings from threat hunting and incident response engagements — are now available: External Penetration Testing: Simulates an attacker trying to breach the perimeter from the outside. Internal Penetration Testing: Simulates an insider threat or an attacker who has already breached the perimeter, focusing on systems, applications, and data within the internal network. Wireless Network Penetration Testing: Assesses the security of an organization's Wi-Fi networks and infrastructure and evaluates their compliance with appropriate mandates. Web Application Security Assessment: Tests an organization’s web applications for security vulnerabilities and design weaknesses. Neutralisation of active threats Sophos Emergency Incident Response provides rapid identification and neutralisation of active threats Sophos Advisory Services are delivered by dedicated testers with vast cross-discipline security expertise spanning security research, threat intelligence, law enforcement, military and other backgrounds who joined Sophos through the recent acquisition of Secureworks. The team holds hundreds of security certifications, has earned top finishes in capture the flag competitions, and is supported by Sophos X-Ops security analysts, threat intelligence and research specialists. Sophos will release additional Advisory Services in the coming months. Sophos Advisory Services are the latest addition to Sophos’ fast-growing security services portfolio that also includes Sophos Emergency Incident Response. Converging incident response expertise from Sophos and Secureworks in a single, hourly-billing offering, Sophos Emergency Incident Response provides rapid identification and neutralisation of active threats and is available to any organization experiencing a live incident.
As the cybersecurity landscape rapidly evolves, Entrust announced a landmark achievement: The Entrust nShield Hardware Security Module’s (HSMs) implementation of three NIST standardized post-quantum algorithms have been validated by NIST’s Cryptographic Algorithm Validation Program (CAVP). This milestone empowers enterprises to secure their sensitive data against the looming threats of quantum computing with confidence, backed by the credibility of NIST-validated, production-ready cryptographic solutions. With native nShield HSM firmware (v13.8.0) support for ML-DSA, ML-KEM, and SLH-DSA, organizations have a path to quantum-safe security. Quantum computing advancements Organizations must urgently secure cryptographic keys and maintain compliance, as quantum computing advancements threaten established security protocols. Choosing the right hardware security module is critical; Entrust nShield HSMs are purpose-built to not only meet current standards but also scale with the organization’s future needs, providing reassurance for the transition to post-quantum cryptography. Robust cryptographic implementations Entrust nShield HSMs have met these stringent needs for ML-DSA, ML-KEM, and SLH-DSA algorithms NIST’s Cryptographic Algorithm Validation Program (CAVP) enforces rigorous standards, ensuring only the most robust cryptographic implementations are validated. Entrust nShield HSMs have met these stringent requirements for ML-DSA, ML-KEM, and SLH-DSA algorithms. Entrust has submitted the nShield HSM firmware – featuring these three quantum-safe algorithms –for updated FIPS 140-3 Level 3 certification through the Cryptographic Module Validation Program (CMVP), reinforcing Entrust’s commitment to advanced, standards-based security. NIST validation for the post-quantum algorithms “Our achievement in obtaining NIST validation for the post-quantum algorithms in production-ready Entrust HSMs is a key differentiator for our customers. This certification gives organizations the confidence that their nShield HSMs are post-quantum ready and recognized by the world’s pioneering standards body, NIST,” said Mike Baxter, Chief Technology and Product Officer at Entrust. Entrust nShield HSMs deliver state-of-the-art, tamper-resistant protection for the organization’s most sensitive keys, allowing organizations to generate and safeguard cryptographic keys with confidence, flexibility, and scalability.
International SOS, the world’s pioneering health and security risk management services firm, announced a strategic partnership with Exlog Global (Exlog), a boutique, veteran-owned risk solutions provider. Together, they will deliver a seamless, intelligence-led executive services solution that integrates security and protective intelligence in one unified program. Intelligence and threat monitoring The joint solution will feature executive exposure assessments, protective intelligence and threat monitoring The joint solution will feature executive exposure assessments, protective intelligence and threat monitoring, a dedicated executive response hotline, high-quality security and medical support and proactive escalation protocols. Optional services include executive protection, residential and office Physical Security Assessments, security awareness training, risk assessments, online profile reduction, resilience training and technical surveillance countermeasures. Exlog Global’s protective intelligence capabilities Giles Hill, Global Head of Security Services, International SOS, said, “By combining our global intelligence, security, and medical expertise with Exlog Global’s protective intelligence capabilities, we are able to deliver a powerful executive services program that meets the ever-evolving needs of our clients." George Taylor, CEO, Exlog Global, said, “This partnership ensures that pioneers are supported by best-in-class protective intelligence, security, and health integration—delivered discreetly, globally, and with measurable value.” Evolving threat landscape Exlog is a veteran-founded U.S. risk solutions firm that has protective intelligence, contingency planning Exlog is a veteran-founded U.S. risk solutions firm that delivers protective intelligence, contingency planning and critical incident response backed by 24/7 global monitoring customized to end user requirements. This collaboration unites two industry pioneers dedicated to safeguarding people and organizations against the complex and evolving threat landscape. Integrated medical and security assistance International SOS brings over 40 years of experience supporting multinational corporations, governments, and NGOs with integrated medical and security assistance in more than 190 countries. Leveraging elite military, intelligence, and risk management backgrounds, Exlog complements this global footprint with specialized expertise in protective intelligence, critical incident response and the development and staffing of client-dedicated GSOCs and VSOCs. Shared commitment to global assistance The partnership is grounded in a shared commitment to global assistance, integrated expertise and proven value. By aligning capabilities, International SOS and Exlog deliver: Global Reach – Operational capability in 190+ countries. Integrated Expertise – A unified health, intelligence, and security program. Proven Value – Cost and operational efficiency by consolidating fragmented vendor solutions. Privacy Prioritization – Highest levels of data privacy and discretion with information. Standards-Based Delivery – Best practice aligned with ISO 31000, 31030, and 22361. This partnership underscores both organizations’ mission to protect people and enable organizations to operate with confidence—anywhere in the world.
Gallagher Security is proud to announce that its recently-released High Security Controller 7000 (High Sec C7000) has received two prestigious accolades: a GOVIES Government Security Award for Access Control-Software/Controllers and a Fortress Cybersecurity Award in the Operational Technology (OT) category. These awards further affirm the High Sec C7000’s position as a best-in-class access control solution engineered to meet the evolving cybersecurity demands of critical infrastructure, government, and high-consequence commercial environments. Power of Gallagher’s approach “This recognition underscores the power of Gallagher’s approach to secure, unified architecture,” says Jim Rayner, Senior Product Manager for Gallagher Security. “The High Sec C7000 builds on a long legacy of innovation, with cybersecurity deeply embedded from silicon to software. It’s an honor to see this platform recognized for helping customers meet tomorrow’s challenges today.” FIPS-approved microprocessor High Sec C7000 is GSA-approved and PIV-compliant with UL/ULC compliance and Class 5 certification Launched in 2025 to serve high-security sites in the Americas and beyond, the High Sec C7000 is GSA-approved and PIV-compliant (FIPS 201-3) with UL/ULC compliance and Class 5 certification for Australian and New Zealand markets. It integrates a FIPS-approved microprocessor, EdgeLock Secure Element, and Trusted Execution Environment (TEE) to protect against firmware attacks and supply chain vulnerabilities. Resilient solutions with proactive cybersecurity “Our team has engineered the High Sec C7000 for the most demanding operational environments,” says Jeff Fields, Director of Government Programs - Americas. “Whether it’s federal agencies, utilities, or data centers, our customers need resilient solutions with proactive cybersecurity capabilities. To be recognized by both the GOVIES and the Fortress Cybersecurity Awards shows that our solutions aren’t just secure, they’re leading the way.” Cyber risk and secure operational integrity The GOVIES Government Security Awards, hosted by Security Today, recognize outstanding products that address the unique security challenges of government applications. The Fortress Cybersecurity Awards, presented by Business Intelligence Group, highlight the world’s pioneering companies and products that help mitigate cyber risk and secure operational integrity. These wins mark another milestone for Gallagher’s award-winning controller portfolio, which includes the C7000 Single Door, Standard, Enhanced, and now, High Security variants, delivering security, scalability, and cyber assurance from the edge to the enterprise.
The Z-Wave Alliance, the standards development organization dedicated to advancing the smart home and Z-Wave® technology, announces that pioneering silicon providers Silicon Labs and Trident IoT have both achieved the Alliance’s newly established Z-Wave Protocol Certification. As the silicon solutions providers currently supporting the Z-Wave ecosystem, this certification ensures that all products developed on their platforms maintain the required levels of interoperability, heightened security, and continued innovation across a global Z-Wave marketplace. Z-Wave Protocol Certification The new Z-Wave Protocol Certification contributes to and further validates the rigorous standards The new Z-Wave Protocol Certification contributes to and further validates the rigorous standards set by the Z-Wave Alliance, ensuring that core tenets of Z-Wave technology, such as interoperability, backwards compatibility, enhanced security, and robust developer resources, remain across all Z-Wave-enabled products. Trident IoT brings a focused, developer-first approach to Z-Wave innovation. Founded by long-time pioneers within the IoT space, the company was established to meet growing demand for streamlined silicon, certification, and design support tailored to the Z-Wave ecosystem. Innovative Z-Wave products “Achieving Z-Wave Alliance certification for our semiconductor solutions and SDK is a testament to our dedication to quality, interoperability, and developer empowerment,” said Mariusz Malkowski, CTO at Trident IoT. “This milestone enables our partners to confidently accelerate their time-to-market with fully certifiable and innovative Z-Wave products.” Latest Z-Wave software release Z-Wave Protocol Certification enables Silicon Labs customers to develop and certify Z-Wave products Silicon Labs, a pioneering innovator in low-power wireless solutions, builds upon its extended pedigree of Z-Wave innovation through this certification achievement. The Z-Wave Protocol Certification enables Silicon Labs customers to develop and certify Z-Wave products using its EFR32ZG23, EFR32ZG28, and ZGM230S hardware platforms along with their latest Z-Wave software release (v7.23.1). Open Z-Wave technology “When Silicon Labs made the strategic decision to open Z-Wave technology up to the community in the name of open-source advancement, the goal was always to drive member contribution, broader adoption, and strengthen the ecosystem,” said Abitzen Xavier, Staff Product Manager for Proprietary & Z-Wave at Silicon Labs. “Z-Wave continues to be a pioneering platform in the smart home and beyond. Silicon Labs is pleased to provide this new certification and its accompanying enhancements to help our customers continue to build secure, reliable, and interoperable Z-Wave devices.” Smart home and IoT innovation Avi Rosenthal, Chairman of the Board for the Z-Wave Alliance, praised the contributions of both companies, stating, “The achievements by Trident IoT and Silicon Labs mark significant milestones, reinforcing the strength and versatility of the Z-Wave ecosystem." "By taking the necessary steps to certify their solutions, these companies now provide manufacturers and developers with essential tools for accelerating smart home and IoT innovation.”


Expert commentary
Digital access control has well-known benefits over traditional security, of course, but also costs attached to each stage of its lifetime. However, these costs are not fixed. Many factors – including building size, shape, type, location, national regulations and more – impact affordability and efficiency calculations. Crucially, the type of access solution a business selects – wired or wireless – impacts total operating costs, including during installation, running, and any potential expansion or reconfiguration stages. Wireless installation Wiring premises can be expensive. So, the potential cost savings from choosing wireless digital access begin at the very start. Installation stage is the largest contributor to potential cost savings when businesses go wireless. In calculations for one report, access experts at ASSA ABLOY examined projected costs for a fictional 100-door installation. Labor savings for those who chose wireless over wired locks were 82.5%. Why? Firstly, because wireless installation is much faster. It is also less intrusive. Most wireless locking devices require little or no drilling of the door, whereas wired security needs cabling through and partly around a door – which means not just door damage, but the contracting of specialist electrical installers who may require multiple site visits. These costs add up. Digital access technology Torus aims for the highest level of LEED certification for all its new properties In Poland, for example, developer Torus aims for the highest level of LEED certification for all their new properties around Gdansk. Where possible, they choose products with Environmental Product Declarations (EPDs) and Green Circle documentation, favoring access solutions which reduce their carbon footprint. Wireless digital access technology is a natural choice. “The lack of wiring significantly reduces materials use, reduces costs, and ensures quick installation,” confirms Torus’ Roman Sokolowski. There’s no cabling, which cuts power consumption. There’s less damage to the building fabric and fitters make fewer journeys to and from the site. Adaptable locking solution By choosing a wireless solution, organizations also upgrade building security with little disruption. A wireless system makes it easier to improve security at an existing building via a retrofit process which does not inconvenience staff or disturb work routines. This was one goal at Plexal, a £15 million flexible work environment for London enterprise and academia. Plexal chose battery-powered wireless locks integrated with DoorFlow, NetNodes’ online platform for managing and auditing building access. “Plexal required an adaptable locking solution for a range of different doors and, with no wiring required, it was quick and easy to install ASSA ABLOY Aperio® devices with minimal disruption,” confirms Stewart Johnson, Director at NetNodes. Cost savings with improved energy efficiency Choosing wireless over wired locking can play a vital role in reducing ongoing energy use Choosing wireless over wired locking can play an important role in reducing ongoing energy use – and, therefore, expenditure. Wholesale electricity prices in Europe are approximately double what they were in 2019, according to the IEA’s “Electricity 2024” report. For a variable cost such as energy, where businesses have little control over unit prices, it is critical to control usage, especially if high and/or changeable energy prices become what analysts at ING called “the new normal for business”. Thus, the fact that battery-powered locks consume much less energy than traditional wired solutions is increasingly relevant and important. Additional savings on energy costs Traditional wired door access devices often work via magnets connected permanently to mains electricity. These doors draw power around the clock to remain locked. Wireless locks work differently. They only “wake up” when presented with a credential, to make the access decision. This translates to an additional saving on energy costs during operation: more than 70%, or thousands of euros over a typical access system’s lifetime. Wireless digital access Wireless locks only need a change of their standard battery, which may be rechargeable Related energy and materials costs during in-use stage are also lower. Wireless locks only need a change of their standard battery – which may be rechargeable – typically once every two years. No specialist maintenance is required, saving on specialists and their travel to and from the site(s). By choosing wireless digital access, businesses help protect themselves against these ongoing costs, notably energy price increases and volatility. Cost-efficient flexible working, for staff and facilities managers Perhaps harder to quantify, but equally easy to imagine, the financial benefits of choosing a wireless digital solution are felt in the increased convenience and efficiency of daily operations. In the co-working sector, for example, flexible access to offices is a priority. As “fixed” office space rented by corporations continues to fall, co-working spaces are expected to keep growing, with one estimate suggesting almost 18% CAGR to 2030. To stand out from the competition, the founders of ULab in Alicante sought the latest innovations in access and design to create their 21st-century business center. Part of the suite of digital access solutions from ASSA ABLOY, a SMARTair® system gave ULab real-time access management via battery-powered locks and Openowä, the Mobile Key solution for SMARTair, without any need to wire doors and other openings. SMARTair TS1000 Web interface With SMARTair and Openow, workspace residents can carry virtual keys on their smartphone With SMARTair and Openow, workspace residents can carry virtual keys on their smartphone; ULab’s security team update their rights over the air. An office manager can perform any operation remotely from the SMARTair TS1000 Web interface. In case of an emergency, they could lock-down the site or open doors remotely, for example. It’s convenient, efficient and boosts ULab’s security, benefiting users and managers. And because of SMARTair’s flexibility, they can comfortably welcome many more than their usual 100 daily users. “In addition to regular daily traffic, weekly traffic can almost multiply by 10 if an event is held,” says Enrique Burgos Pérez, Director at ULab. “We needed an access control system as flexible and convenient as SMARTair.” ASSA ABLOY benchmarking report Choosing wireless locks also adds flexibility – and can reduce costs – when an organization reconfigures or expands their commercial space. High-quality wireless devices like SMARTair can typically be reinstalled at another opening without impacting reliability. They move to wherever is convenient. If a business is rethinking workspace to encourage flexible or hybrid work patterns, for example, cost efficiencies could be significant. Typical savings on office relocation or expansion are estimated at around 30% with wireless over wired locking, according to the same ASSA ABLOY benchmarking report. Cost efficiency and more control with ASSA ABLOY digital access To refit and improve their student accommodation, managers at the University of St Andrews sought energy- and cost-efficient access control. They chose Aperio, another innovative digital access solution from ASSA ABLOY. Approximately 1,600 doors so far are equipped with battery-powered Aperio escutcheons – without cabling. Aperio devices integrate fully with both the university’s existing central security system and their student ID card. University security managers continue to enjoy the efficiency benefits of monitoring and controlling access from a single point and in real-time, including for doors across multiple buildings. Aperio, another innovative digital access solution from ASSA ABLOY. Benefits of cost-efficiency In comparison to a wired solution, Aperio offers significant cost-efficiency benefits. Devices are wireless, so can be installed with little energy use and no need for wiring to the mains. They consume near-zero energy when idle and run on standard batteries, consuming little power during operation. Through the entire product life-cycle, Aperio combines reliability with cost effectiveness. “Aperio gives us central management and control,” says Pauline Brown, Associate Chief Information Officer at the University of St Andrews, “and contributes to our award-winning track record in energy efficiency.”
As the backbone of community welfare, healthcare facilities cater to crucial public needs from emergency care to specialized medical treatments, and due to its position as a significant facet of the world's critical infrastructure, the healthcare sector faces a multitude of challenges in ensuring patient and visitor security, managing high traffic, and safeguarding sensitive data. Medical sites, such as large hospitals and urgent care clinics, see a wide variety of patients, medical staff, administrative teams, and visitors throughout the day. In addition to protecting patients, visitors, and staff, healthcare environments must protect medical and patient data, ensure immediate response to urgent medical events, and maintain 24/7 operations. Security challenges Cloud-based solutions have made their mark on healthcare security, offering unparalleled scalability Addressing the security challenges presented by 24/7 availability and high patient and visitor traffic calls for a merging of technology, processes, and security strategies that go beyond what a typical security infrastructure would look like. Cloud-based solutions have made their mark on healthcare security, offering unparalleled scalability, accessibility, and integration capabilities. These advancements address the multifaceted demands of healthcare organizations, ensuring seamless around-the-clock operations while prioritizing patient care and safety. Enhancing Operational Efficiency to Save Lives Cloud-based access control solutions have revolutionized how healthcare security professionals approach collaboration within medical facilities. These solutions offer unparalleled accessibility and insight into patient and visitor security information and access logs, improving coordination among security teams and leading to more accurate monitoring and response to developing medical events. By managing and operating access control solutions via the cloud, healthcare facilities can implement effective physical security measures while ensuring seamless collaboration among staff to deliver the highest medical care possible to patients across facilities. Physical access controls Cloud-based access control systems allow users to securely access and manage physical access controls Cloud-based access control systems allow multiple users to securely access and manage physical access controls and visitor management data simultaneously, enabling them to keep track of patient movements as they are transferred throughout the facility or between different facilities. For larger hospitals or medical campuses with multiple facilities hosting access controls via the cloud empowers users with the ability to find patients and patient data in an instant, as well as opening the door to collaborate with teams separated by long distances, ensuring all team members have access to the information they need to continue saving lives. Scaling the way to top-notch care Healthcare institutions are constantly growing and changing in response to evolving industry regulations and standards, and the access control solutions these organizations rely on should be able to scale to meet their changing needs. To ensure their access control systems can keep up with these growing demands, healthcare security professionals can invest in access control solutions hosted in the cloud to avoid the tedious hardware constraints that come with traditional on-premises solutions. Cloud solutions offer significant levels of scalability, enabling healthcare organizations to adjust their storage requirements and computing resources based on changing requirements on the fly. This capability for flexibility ensures users can manage large amounts of data without significant upfront investments in hardware. Cloud-based access control solutions Cloud-based access control solutions provide healthcare organizations with the flexibility they need to expand their access In addition to compliance with changing regulations, cloud-based access control solutions provide healthcare organizations with the flexibility they need to expand their access control platform across a growing campus or multiple buildings. Larger healthcare facilities typically consist of multiple sites of varying sizes across diverse landscapes, each with distinctive security needs. Systems hosted in the cloud provide scalability and flexibility for user organizations, allowing security teams to modify or expand upon their security infrastructure as needed without spending on costly new hardware. This adaptability is crucial for helping address varying risks over multiple sites, providing security personnel the flexibility they need to ensure patient safety over long distances. Ease of use for security teams To truly understand the value of a cloud-based access control system, healthcare security professionals must consider the long-term savings and ROI these solutions provide by bolstering operational efficiencies and enabling unprecedented scalability. These systems ensure compliance with changing standards and deliver a simplified user experience across platforms, prioritizing security and ease of use for security teams across the healthcare sector.
For K12 education pioneers, embarking on a journey to upgrade security controls can present a myriad of questions about finding the best-fit solutions and overcoming funding hurdles. A majority of public-school districts today are faced with outdated infrastructure and security controls, requiring necessary upgrades. By addressing these concerns head on, schools will ensure a safer environment for both students and staff, mitigating risks posed by unforeseen physical and digital threats. Common K12 security pain points There’s no one-size-fits-all solution in school district security. School districts may have big plans to implement upgraded security systems but to set out on the right foot, pioneers must have a clear vision of their long-term strategy. When embarking on their security journey, education pioneers often wonder where to start and what exact steps are they need to be taking to identify and address weaknesses. Local K12 and government pioneers are promoting and mandating security assessments to uncover safety gaps on campuses and mitigate these risks with advanced technology solutions. Not only do assessments provide detailed, customizable roadmaps for district pioneers, but they also recommend technologies and funding opportunities to help close threat gaps. K12 school districts are mainly vulnerable to cyber-attacks due to the sensitive nature of student records In today’s climate, schools face a growing number of physical and digital security threats. From a cybersecurity standpoint, K12 school districts are particularly vulnerable to cyber-attacks due to the sensitive nature of student records. However, only one-third of these districts have adequate staffing to address threats effectively. In addition, according to a recent survey from Johnson Controls and Forrester Consulting, security decision-makers are having trouble receiving actionable insights. Nearly two-thirds of respondents said that they struggle to receive information from all necessary systems regarding their security threats. To gain more clarity into what school districts need in terms of security tools and threat mitigation, implementing system-wide monitoring and optimization can be invaluable. This approach enhances equipment and operational efficiency, while providing necessary resources and expertise for critical patch updates across all systems, strengthening their overall security posture. Achieving a well-rounded security program In the past few years, AI technology has emerged as a trending solution and is generating considerable attention. While the allure of implementing cutting-edge technologies is undeniable, it’s important to recognize that a robust security program hinges on solid access control. Access control technology provides administrators with the means to oversee and regulate entry into facilities, serving as the foundation for basic physical security. The technology helps administrators and staff control access to multiple areas from web-enabled devices, even during lockdowns which is crucial in emergency situations. School district pioneers should utilize available digital risk assessment tools to uncover threat areas Once basic security controls are in place, school districts must address their next set of security pain points and identify which solutions meet their specific needs. This involves identifying and prioritizing the highest need and most cost-effective investments that will have the greatest impact on enhancing security measures. To accurately determine which security solutions are needed for a specific environment, school district pioneers should utilize available digital risk assessment tools to uncover threat areas and determine levels of priority. By focusing on these priority areas, districts can allocate their resources and efforts where they are needed most, ensuring maximum effectiveness in mitigating risks and vulnerabilities. Securing funding before approaching deadlines A major challenge for school districts surrounding campus security is identifying and securing the necessary funding to implement solutions aligned with their goals. Leveraging available funding sources is critical, especially considering certain programs are approaching their deadline, like the Elementary and Secondary School Emergency Relief (ESSER) fund. Announced during the pandemic, ESSER is a funding program that has allocated nearly $190 billion in aid to U.S. public school districts to fund projects benefitting the well-being of occupants. Notable ESSER funding deadlines to keep in mind as the clock winds down include September 30, 2024 Notable ESSER funding deadlines to keep in mind as the clock winds down include September 30, 2024, when schools must attribute all of their funds to assigned contracts. Following this date, pioneers will need to complete all ESSER spending by January 2025 unless approved for an extension into March 2025. As ESSER wanes, school districts are acutely aware of the fiscal cliff in budgets through 2025. However, many states are ramping up grant funding to close the deficit gap. Administrators should become familiar with these grant opportunities at a local and state level. Get started on security plans The time for school district pioneers to act is now. While the safety and well-being of students and staff are always top priorities, it’s crucial to acknowledge that a lack of insight into necessary security upgrades and available funding options will leave districts behind the curve. Seizing the final months of ESSER funding presents an ideal window to address security pain points and build a safer future for K12 facilities. Looking beyond ESSER, pioneers must proactively seek out and leverage other funding avenues to help ensure the continuity of their security efforts and maintain a proactive stance in safeguarding healthy and safe educational environments.
Security beat
Already a strong player, particularly in New Zealand and Australia, Gallagher is still climbing in the U.S. market, which it sees as a big opportunity to invest in the company. Active in the United States for 10 years, Gallagher undertook a more aggressive growth strategy about five years ago. There are 52 employees in Gallagher’s U.S. security business, and about half the workforce has been hired in the last couple of years. They have grown from three sales territories to 16, operated by a full sales and engineering staff. Culture of innovation sets As it happens, Gallagher’s U.S. headquarters is located a short drive from my home office in the wider vicinity of Atlanta. I missed seeing them at GSX in Dallas, so we scheduled an in-person visit to catch up on their company. Gallagher’s strong culture of innovation sets them apart, as does their “people-first” commitment, says Scott Elliott, Gallagher’s Executive Vice-President, The Americas. “We have intentionally recruited for a diversity of thought that drives the business,” says Elliott. “We are a people business.” Melissa Vidakovic, Director of Marketing, Americas; and Scott Elliott, Executive VP, Americas, at Gallagher Security's office in Canton, GA. Unified approach An advantage Gallagher has in the market is total ownership of their supply chain; it manufactures each of the hundreds of products used across their solutions, from plastic components to readers to controllers to their own software systems. Among other advantages, the unified approach enables tighter control from a hardening and cybersecurity perspective, enabling them to minimize any threat vectors or vulnerabilities. The strategy also avoids dependence on third-party suppliers, which was a huge advantage during recent supply chain disruptions. While competitors struggled with availability issues related to third-party manufacturers, Gallagher’s supply was uninterrupted. Gallagher’s commitment Gallagher uses the same norms as the nation and subjects its effects to inner and outer penetration As a manufacturer serving a broad spectrum of markets, it’s Gallagher’s commitment to the high end of the market (e.g., high-security applications), where the company incorporates core tenets such as authentication and encryption. Gallagher uses some of the same standards as the government and subjects its products to internal and external penetration testing. These core strengths are also integral to Gallagher’s complete product line. “If it’s good enough for a high-level customer, it’s good enough for Mr. Business Owner,” says Elliott. The New Zealand company was founded in 1938 and was the first company to commercialize the electric fence, which it still uses for its agriculture business sector, separate from the security business. Gallagher entered the access control business 35 years ago in 1988 when a product used to restrict access to fuel pumps evolved into broader access control. Gallagher platform In the intervening years, the product has grown into a unified platform that incorporates access control, intrusion detection, and perimeter detection in a single ecosystem. “The platform is all-encompassing,” says Elliott. “No other platform does all three.” Augmenting access control, intrusion, and perimeter protection, there are other applications available in the Gallagher platform, such as workforce management, health and safety functions, and a spectrum of features useful to a wider stakeholder community. Fatigue management applications For example, Gallagher can implement routine randomized checks to proactively mitigate potential risks such as drug or alcohol abuse, thus ensuring workers are fit to work, to operate various machinery and that they do not pose a threat to fellow employees or the company. “Fatigue management” applications can monitor the use of equipment to avoid repetitive injuries or manage how long an employee works at a job site, requiring a worker to swipe or tap a card to a reader mounted on a machine to monitor and limit the time they operate that machine. Mobile mustering provides location and identification of evacuees in case of an emergency. Impact of digital transformation Gallagher’s “Better Ways of Working” concept zeroes in on the impact of digital transformation Gallagher is also embracing the “digital transformation” of the industry. Security companies must adapt to a more agile workforce and shifting processes, says Elliott. Gallagher’s “Better Ways of Working” concept zeroes in on the impact of digital transformation on their workforce. They also seek to address the changing workforce, where Gen-Z’ers work side-by-side with tenured, experienced workers, and where creating trust is the best approach to closing the generational gap. Gallagher also seeks to educate the market on trends such as artificial intelligence (AI), machine learning, cloud adoption, various service delivery models, and other issues. Industry consolidation Gallagher has more than 1,200 employees; operates in 140 countries, from South America to Canada, Europe to the Asia-Pacific and Australia; and serves almost 16,000 customers. Gallagher is part of New Zealand’s growing technology export sector, which is growing 30% faster than the overall economy and is now the second-largest export sector in New Zealand. In an age of industry consolidation and a market dominated by corporate conglomerates, Gallagher is a privately held organization seeking to be agile and innovative, and to deliver customer value more quickly. Gallagher re-invests about 15% of its profits into research and development. “Our customer service is the primary reason people buy from us,” says Elliott. Security integrators Security integrators quickly appreciate the breadth and strength of the product line Gallagher positions itself as an alternative in a market in the midst of disruption. Brand awareness continues to be a challenge in the United States, and the sales team often hears the question: “Who is Gallagher?” Once the introduction is made, security integrators quickly appreciate the breadth and strength of the product line, says Elliott. “We allow our customers to select among best-of-breed platforms, and [using open systems,] we are not limited by the technology we offer,” says Elliott. “Our value proposition to the integrator channel is our focus on the relationship,” says Elliott. Supporting end users through an authorized, certified channel, Gallagher also emphasizes value, cost-competitiveness, and cybersecurity. “Our partner relationships are built around cultural alignment,” says Elliott. Product innovation perspective What’s ahead for Gallagher and for the industry as a whole? Hard to say, notes Elliott, given the unfolding of unpredictable geopolitical and financial trends. However, from a product innovation perspective, Gallagher will continue to evolve, balancing a dependence on “cash cow” legacy product lines with investment in leapfrog innovations such as frictionless access control, cloud platforms, and mobile systems. In general, Elliott predicts AI will yield an opportunity to analyze a person’s pattern of behavior and intent, thus enabling a security system to adapt down the road. “With the ability to predict with some degree of certainty what might happen, these capabilities will evolve,” says Elliott.
When it comes to security cameras, the end user always wants more—more resolution, more artificial intelligence (AI), and more sensors. However, the cameras themselves do not change much from generation to generation; that is, they have the same power budgets, form factors and price. To achieve “more,” the systems-on-chips (SoCs) inside the video cameras must pack more features and integrate systems that would have been separate components in the past. For an update on the latest capabilities of SoCs inside video cameras, we turned to Jérôme Gigot, Senior Director of Marketing for AIoT at Ambarella, a manufacturer of SOCs. AIoT refers to the artificial intelligence of things, the combination of AI and IoT. Author's quote “The AI performance on today’s cameras matches what was typically done on a server just a generation ago,” says Gigot. “And, doing AI on-camera provides the threefold benefits of being able to run algorithms on a higher-resolution input before the video is encoded and transferred to a server, with a faster response time, and with complete privacy.” Added features of the new SOC Ambarella expects the first cameras with the SoC to emerge on the market during early part of 2024 Ambarella’s latest System on Chip (SOC) is the CV72S, which provides 6× the AI performance of the previous generation and supports the newer transformer neural networks. Even with its extra features, the CV72S maintains the same power envelope as the previous-generation SoCs. The CV72S is now available, sampling is underway by camera manufacturers, and Ambarella expects the first cameras with the SoC to emerge on the market during the early part of 2024. Examples of the added features of the new SOC include image processing, video encoders, AI engines, de-warpers for fisheye lenses, general compute cores, along with functions such as processing multiple imagers on a single SoC, fusion among different types of sensors, and the list goes on. This article will summarize new AI capabilities based on information provided by Ambarella. AI inside the cameras Gigot says AI is by far the most in-demand feature of new security camera SoCs. Customers want to run the latest neural network architectures; run more of them in parallel to achieve more functions (e.g., identifying pedestrians while simultaneously flagging suspicious behavior); run them at higher resolutions in order to pick out objects that are farther away from the camera. And they want to do it all faster. Most AI tasks can be split between object detection, object recognition, segmentation and higher-level “scene understanding” types of functions, he says. The latest AI engines support transformer network architectures (versus currently used convolutional neural networks). With enough AI horsepower, all objects in a scene can be uniquely identified and classified with a set of attributes, tracked across time and space, and fed into higher-level AI algorithms that can detect and flag anomalies. However, everything depends on which scene is within the camera’s field of view. “It might be an easy task for a camera in an office corridor to track a person passing by every couple of minutes; while a ceiling camera in an airport might be looking at thousands of people, all constantly moving in different directions and carrying a wide variety of bags,” Gigot says. Changing the configuration of video systems Low-level AI number crunching would typically be done on camera (at the source of the data) Even with more computing capability inside the camera, central video servers still have their place in the overall AI deployment, as they can more easily aggregate and understand information across multiple cameras. Additionally, low-level AI number crunching would typically be done on camera (at the source of the data). However, the increasing performance capabilities of transformer neural network AI inside the camera will reduce the need for a central video server over time. Even so, a server could still be used for higher-level decisions and to provide a representation of the world; along with a user interface for the user to make sense of all the data. Overall, AI-enabled security cameras with transformer network-based functionality will greatly reduce the use of central servers in security systems. This trend will contribute to a reduction in the greenhouse gases produced by data centers. These server farms consume a lot of energy, due to their power-hungry GPU and CPU chips, and those server processors also need to be cooled using air conditioning that emits additional greenhouse gases. New capabilities of transformer neural networks New kinds of AI architectures are being deployed inside cameras. Newer SoCs can accommodate the latest transformer neural networks (NNs), which now outperform currently used convolutional NNs for many vision tasks. Transformer neural networks require more AI processing power to run, compared to most convolutional NNs. Transformers are great for natural language processing (NLP) as they have mechanisms to “make sense” of a seemingly random arrangement of words. Those same properties, when applied to video, make transformers very efficient at understanding the world in 3D. Transformer NNs require more AI processing power to run, compared to most convolutional NNs For example, imagine a multi-imager camera where an object needs to be tracked from one camera to the next. Transformer networks are also great at focusing their attention on specific parts of the scene—just as some words are more important than others in a sentence, some parts of a scene might be more significant from a security perspective. “I believe that we are currently just scratching the surface of what can be done with transformer networks in video security applications,” says Gigot. The first use cases are mainly for object detection and recognition. However, research in neural networks is focusing on these new transformer architectures and their applications. Expanded use cases for multi-image and fisheye cameras For multi-image cameras, again, the strategy is “less is more.” For example, if you need to build a multi-imager with four 4K sensors, then, in essence, you need to have four cameras in one. That means you need four imaging pipelines, four encoders, four AI engines, and four sets of CPUs to run the higher-level software and streaming. Of course, for cost, size, and power reasons, it would be extremely inefficient to have four SoCs to do all this processing. Therefore, the latest SoCs for security need to integrate four times the performance of the last generation’s single-imager 4K cameras, in order to process four sensors on a single SoC with all the associated AI algorithms. And they need to do this within a reasonable size and power budget. The challenge is very similar for fisheye cameras, where the SoC needs to be able to accept very high-resolution sensors (i.e., 12MP, 16MP, and higher), in order to be able to maintain high resolution after de-warping. Additionally, that same SoC must create all the virtual views needed to make one fisheye camera look like multiple physical cameras, and it has to do all of this while running the AI algorithms on every one of those virtual streams at high resolution. The power of ‘sensor fusion’ Sensor fusion is the ability to process multiple sensor types at the same time and correlate all that information Sensor fusion is the ability to process multiple sensor types at the same time (e.g., visual, radar, thermal, and time of flight) and correlate all that information. Performing sensor fusion provides an understanding of the world that is greater than the information that could be obtained from any one sensor type in isolation. In terms of chip design, this means that SoCs must be able to interface with, and natively process, inputs from multiple sensor types. Additionally, they must have the AI and CPU performance required to do either object-level fusion (i.e., matching the different objects identified through the different sensors), or even deep-level fusion. This deep fusion takes the raw data from each sensor and runs AI on that unprocessed data. The result is machine-level insights that are richer than those provided by systems that must first go through an intermediate object representation. In other words, deep fusion eliminates the information loss that comes from preprocessing each individual sensor’s data before fusing it with the data from other sensors, which is what happens in object-level fusion. Better image quality AI can be trained to dramatically improve the quality of images captured by camera sensors in low-light conditions, as well as high dynamic range (HDR) scenes with widely contrasting dark and light areas. Typical image sensors are very noisy at night, and AI algorithms can be trained to perform excellently at removing this noise to provide a clear color picture—even down to 0.1 lux or below. This is called neural network-based image signal processing, or AISP for short. AI can be trained to perform all these functions with much better results than traditional video methods Achieving high image quality under difficult lighting conditions is always a balance among removing noise, not introducing excessive motion blur, and recovering colors. AI can be trained to perform all these functions with much better results than traditional video processing methods can achieve. A key point for video security is that these types of AI algorithms do not “create” data, they just remove noise and clean up the signal. This process allows AI to provide clearer video, even in challenging lighting conditions. The results are better footage for the humans monitoring video security systems, as well as better input for the AI algorithms analyzing those systems, particularly at night and under high dynamic range conditions. A typical example would be a camera that needs to switch to night mode (black and white) when the environmental light falls below a certain lux level. By applying these specially trained AI algorithms, that same camera would be able to stay in color mode and at full frame rate--even at night. This has many advantages, including the ability to see much farther than a typical external illuminator would normally allow, and reduced power consumption. ‘Straight to cloud’ architecture For the cameras themselves, going to the cloud or to a video management system (VMS) might seem like it doesn’t matter, as this is all just streaming video. However, the reality is more complex; especially for cameras going directly to the cloud. When cameras stream to the cloud, there is usually a mix of local, on-camera storage and streaming, in order to save on bandwidth and cloud storage costs. To accomplish this hybrid approach, multiple video-encoding qualities/resolutions are being produced and sent to different places at the same time; and the camera’s AI algorithms are constantly running to optimize bitrates and orchestrate those different video streams. The ability to support all these different streams, in parallel, and to encode them at the lowest bitrate possible, is usually guided by AI algorithms that are constantly analyzing the video feeds. These are just some of the key components needed to accommodate this “straight to cloud” architecture. Keeping cybersecurity top-of-mind Ambarella’s SoCs always implement the latest security mechanisms, both hardware and software Ambarella’s SoCs always implement the latest security mechanisms, both in hardware and software. They accomplish this through a mix of well-known security features, such as ARM trust zones and encryption algorithms, and also by adding another layer of proprietary mechanisms with things like dynamic random access memory (DRAM) scrambling and key management policies. “We take these measures because cybersecurity is of utmost importance when you design an SoC targeted to go into millions of security cameras across the globe,” says Gigot. ‘Eyes of the world’ – and more brains Cameras are “the eyes of the world,” and visual sensors provide the largest portion of that information, by far, compared to other types of sensors. With AI, most security cameras now have a brain behind those eyes. As such, security cameras have the ability to morph from just a reactive and security-focused apparatus to a global sensing infrastructure that can do everything from regulating the AC in offices based on occupancy, to detecting forest fires before anyone sees them, to following weather and world events. AI is the essential ingredient for the innovation that is bringing all those new applications to life, and hopefully leading to a safer and better world.
Collaboration among manufacturers in the physical security industry can result in systems that are easier to install for integrators and that provide a better customer experience for end users. Illustrating the point is the recent collaboration among a turnstile technology company, a supplier of short-range wireless readers/writers, and a biometric business focused on ‘frictionless’ access control. “The more manufacturers collaborate with each other, the more benefits for end users,” says Steve Caroselli, the Chief Executive Officer (CEO) of Orion Entrance Control. Better collaboration means a better user experience We look for opportunities to collaborate and make sure the experience is above and beyond" Steve Caroselli adds, “Better collaboration means a better user experience. We look for opportunities to collaborate and make sure the experience is above and beyond.” Orion’s collaboration with ELATEC RFID Systems and SAFR touchless biometrics by RealNetworks Inc. highlights the advantages of manufacturers working together to ensure technologies operate smoothly in the real world. Taking ownership of the customer experience When Orion Entrance Control provides a SpeedGate swing-glass optical turnstile, they take full ownership of the customer’s experience. That means ensuring the turnstile application operates as it should, regardless of which component of the broader system might be at fault. To the customer experience, a card reader that doesn’t work is the equivalent of a turnstile that doesn’t work. Which component is at fault is irrelevant, and in fact, invisible, to the overall customer experience. Importance of dependable operation of turnstiles As the most visible element in many access control systems, dependable operation of turnstiles reflects positively on the manufacturer and on the entire system. Orion tests various third-party components with their turnstiles To ensure an optimum customer experience, Orion tests various third-party components with their turnstiles, in order to ensure flawless operation before a turnstile is delivered to a customer. Customers buying an Orion turnstile send the card readers they want to use to Orion’s corporate headquarters in Laconia, New Hampshire, USA, where Orion engineers ensure seamless operation. Ensuring optimum customer experience All readers are designed to be bolted to the wall rather than installed inside a turnstile In addition to scenario-based testing, readers are placed inside the turnstile for a streamline appearance, which can be a challenge given the variety of sizes and types of readers a customer might choose. All readers are designed to be bolted to the wall rather than installed inside a turnstile, which complicates adaptation efforts. In short, historically for Orion, ensuring the optimum customer experience involved extra time and effort, although obviously it was worth it. Providing flexibility for any environment Seeking to simplify the process, Orion has found an alternative to using many different types and models of card readers for its turnstiles. Deploying an RFID reader/writer from ELATEC provides flexibility to operate in a variety of card and reader environments, including almost all 125 kHz and 13.56 MHz contactless technologies. The product is compatible with low-frequency (LF), high-frequency (HF), near field communication (NFC) or Bluetooth Low Energy (BLE) signals. An integrated BLE module supports mobile ID and authentication solutions. There is an integrated antenna for LF and HF to ensure excellent contactless performance. ‘Universal’ configuration of the ELATEC reader hardware Using applicable firmware, the ‘universal’ configuration of the ELATEC reader hardware is compatible with any card system. It works with all the access control protocols, including SEOS, OSDP and other open protocols. “We can stock an open SKU and flash the firmware as per the customer requirement,” says Steve Caroselli. The small form factor (around 1 1/2 inches square) of the ELATEC module lends itself to easy installation inside the turnstile housing. Easy availability of the ELATEC readers helps Orion continue to serve customers, despite recent disruptions in the supply chain. And, ELATEC’s reader hardware has earned global certifications that enable Orion to use their products for customers around the world. Testing to ensure smooth operation ELATEC was responsive at every stage as the relationship evolved, providing sample equipment for testing Before embracing the ELATEC reader module, Orion tested it for several months to ensure compatibility with its turnstiles. ELATEC was responsive at every stage as the relationship evolved, providing sample equipment for testing and working closely with the Orion team. Everyone in the ELATEC sales and engineering team, right up the company’s C-suite, worked to support Orion during the testing phase. In the end, in addition to other advantages, ELATEC’s detection speed and read range compares favorably to competing technologies. “We move really fast as an organization, so we are looking for other organizations that move very fast,” says Steve Caroselli, adding “We met with ELATEC one week and had the equipment for testing the next week. We like to work with companies that move fast, and they are culturally aligned with how we do business.” Orion turnstiles with ELATEC TWN4 Palon Compact panel The Orion turnstiles incorporate an ELATEC TWN4 Palon Compact panel, a versatile panel-mount reader designed for integration into third-party products and devices. It supports enhanced interfaces, especially RS-485, and reflects the advantages and integrated tool support of the ELATEC TWN4 family. Orion is implementing SAFR SCAN biometric technology using hardware and software from RealNetworks Inc. “The selection of ELATEC products allows Orion to provide their customers and partners with a flexible RFID reader solution that supports numerous credential options and virtually all transponder technologies,” said Paul Massey, the Chief Executive Officer (CEO) of ELATEC, Inc., adding “This is especially valuable in multi-tenet, multi-credential environments.” Orion works with all the various stakeholders – architects, consultants, integrators, and end users – to ensure total satisfaction with an installation. Biometric technology for ‘frictionless’ access control Orion is also implementing SAFR SCAN biometric technology into their turnstiles using hardware and software from RealNetworks Inc. The facial recognition reader technology, designed for mainstream commercial access control, provides a ‘frictionless’ experience, and allows users to pass through turnstiles at a walk. The system can authenticate up to 30 individuals per minute with 99.9% accuracy, despite varied lighting conditions. SAFR’s system provides a good user experience Orion designed a mounting system to incorporate the biometric reader into their turnstile design Orion designed a mounting system to incorporate the biometric reader into their turnstile design. SAFR’s system provides a good user experience, when it comes to enrollment. On each turnstile, the SAFR technology can operate separate from the ELATEC reader or in conjunction with it for multi-factor authentication in higher-security applications. Innovation for new applications A broad approach to the customer experience reflects Orion’s positioning as a technology company, in addition to being a manufacturer of turnstiles. Their Infinity software is the ecosystem ‘nerve center’ platform to ensure operation and connected through a single ‘pane of glass.’ The need to protect more entrances beyond the lobby led Orion to develop its recently patented DoorGuard, a LIDAR-based solution that detects each person who passes through a doorway and prevents tailgating (like a turnstile) for applications, such as stairway doors, perimeter doors, data centers, IDF closets, etc. The software mimics the advantages of a turnstile to monitor access control and occupancy. Removing friction during installation and beyond Orion’s Constellation is a presence detection system that uses UWB (ultra-wideband) radar to sense where people are in a building for emergency response and building utilization applications. “One of our core values is to remove friction and make customers’ lives easier,” says Steve Caroselli, adding “Our people-first philosophy is: What can we do to make your life better? We want to be systematic, and everything must be repeatable in terms of how we react and interact with customers.”
Case studies
Comelit-PAC has successfully upgraded the access control infrastructure at Blackpool Victoria Hospital, ensuring a seamless and secure environment for staff, patients, and visitors. Blackpool Victoria Hospital is one of the largest and busiest hospitals in the Northwest, providing essential healthcare services to thousands of patients each year. As a pioneering medical facility, ensuring a secure and efficient environment is a top priority. Integrated PAC Access Central Security technology works program integrated PAC Access Central with multiple PC workstations Designed to provide a robust and scalable security solution, the security technology works program integrated PAC Access Central with multiple PC workstations for comprehensive global administration across the hospital’s network To safeguard critical areas within the hospital, Comelit-PAC’s advanced 500 series controllers were utilized. This includes the 511, 512 model door controllers linked into the existing 500 Access & Alarm servers on site, offering a mix of ethernet and RS485 connectivity to enhance system flexibility and efficiency. Security and administrative control Martyn McKechnie, Head of Digital Identity at Blackpool Victoria Hospital, commented: "As a busy hospital with multiple departments and critical areas, we required an access control system that could integrate seamlessly while offering high levels of security and administrative control." Martyn McKechnie adds, "PAC Access Central provides the scalability and reliability we need to manage hospital-wide access efficiently. The ability to oversee all access points from multiple PC workstations ensures our Digital Identity and Security teams can respond quickly to any situation." Future-proof access control system Blackpool Victoria Hospital benefits from a resilient and future-proof access control system A key element of the installation is its server-based architecture, providing enhanced security measures and fail-safe redundancy. This ensures Blackpool Victoria Hospital benefits from a resilient and future-proof access control system, capable of meeting the bespoke demands of the healthcare environment. Advanced security infrastructure Jason Sullivan, PAC / GDX Strategic Development Manager at Comelit-PAC, said: "We worked closely with Blackpool Victoria Hospital right from the initial specification stage to deliver a solution to balance security with ease of management." Jason Sullivan adds, "PAC Access Central presents a future-proof system that allows the hospital to maintain strict access control, while adapting to evolving needs. By adopting this advanced security infrastructure, Blackpool Victoria Hospital continues its commitment to maintaining a safe and secure environment, leveraging Comelit-PAC’s expertise in access control technology."
In 1979, nine districts and five cities in Bavaria, Germany, founded a joint association for the disposal of residual waste. They targeted future-oriented, environmentally friendly and economical fulfillment of local statutory obligations. Now with 17 association members, ZMS (Zweckerverband Müllverwertung Schwandorf) disposes waste for around a fifth of Bavaria, almost two million citizens. They also use the energy generated by the waste power plant as efficiently as possible. Different levels of security Devices and other access hardware also need high weather resistance, for deployment outdoors In the past, a mechanical locking system was used on all ZMS properties. The association planned a digital upgrade to boost flexibility over their existing mechanical locking. Their principal site at Schwandorf has areas requiring different levels of security. Devices and other access hardware also need high weather resistance, for deployment outdoors. Managers also considered workflow efficiency. They wanted a way to manage access authorisations more flexibly and align security infrastructure with upcoming IT security laws such as NIS2. Digital Access Solutions from ASSA ABLOY The company chose eCLIQ, part of the suite of Digital Access Solutions from ASSA ABLOY. This innovative, programmable key-based solution now equips not only the power plant and headquarters in Schwandorf, but also buildings across eastern Bavaria, including transfer stations, a waste disposal site, a sorting plant in Bodenwöhr, and a sludge drying plant, as well as all technical and commercial offices, gate control systems and local control points. Because eCLIQ offers a broad range of digital cylinders within its single ecosystem, it suits diverse and complex organizations like ZMS. The benefits of programmable key-based digital access These Wall PDs also make it easy to set limited access time windows for fitters or maintenance contractors The digitally networked eCLIQ system allows access rights and security levels to be defined and assigned flexibly and precisely. A total of 20 Wall Programming Devices (Wall PDs) installed in the head office and branch offices ensure that only authorized employees gain access. These Wall PDs also make it easy to set limited access time windows for fitters or maintenance contractors. If a key is lost, it can be programmed out immediately to prevent misuse. Standard eCLIQ keys “Now we are going with the times and can conveniently enjoy a wide range of advantages,” says Manuel Emerich, Project Manager at ZMS. “As a critical infrastructure company, we can also react very rapidly and flexibly to future requirements.” The solution offers the advantage that a depleted battery does not render a cylinder useless With eCLIQ, each of ZMS’s approximately 1,000 wireless digital cylinders is powered by a battery inside the keyholder’s personalized key. Standard eCLIQ keys have a battery life of 10 years with typical usage. The solution offers the advantage that a depleted battery does not render a cylinder useless. The key is simply fitted with a spare battery, saving time and effort. Future of evolving physical and cyber-security threats Security is a critical concern at municipal and infrastructure sites: every eCLIQ device offers reliable protection against manipulation and intelligent break-in attempts. Keys are robust, with a waterproof casing, and operate reliably in the most challenging environmental conditions. With eCLIQ, ZMS feel ready to face a future of evolving physical and cyber-security threats. “For us, the introduction of digital locking technology and the ability to respond quickly and specifically to security incidents is a decisive step towards a holistic and future-proof system to defend against cyber–physical threats,” adds Manuel Emerich.
Crime analysts at DeterTech, a trusted security partner to renewables and the police, have identified the unwanted import of a crime type more commonly seen in mainland Europe and North America. The theft of copper cabling from inside wind turbines has historically been rare in the UK. However, this has dramatically changed over the past month. There have been 9 reported offenses since 14 April suggesting an organized group is targeting the industry. Wind farm complex The targeted locations span several counties, including Cambridgeshire, Bedfordshire, Derbyshire, Essex, Humberside, Northamptonshire, North Yorkshire and Lincolnshire. In one instance, three turbines within a single wind farm complex were broken into, further underscoring the scale and potential coordination of these operations. Risk of electrocution The offenders appear undeterred by the fact that the turbines are active at the time of entry Once offenders have gained entry, the turbine door is forcibly opened, and the electricity supply is isolated to eliminate the risk of electrocution. The copper cabling is then cut and removed. Notably, the offenders appear undeterred by the fact that the turbines are active at the time of entry, indicating a high level of confidence and familiarity with the infrastructure. Recent CCTV footage Richard Crisp, Intelligence Analyst, DeterTech, says: “With such a surge of cable theft incidents in the UK, we are urging wind farm management companies to inspect their turbines for any signs of tampering or theft. Any incidents need to be reported immediately to the local police. Additionally, we encourage operators to review recent CCTV footage for any suspicious activity, particularly around entrance gates, and to remain vigilant to unfamiliar vehicles or individuals near their sites”. In the first instance, all thefts, suspicious vehicle and hostile reconnaissance need to be reported to local police force – this allows the National Infrastructure Crime Reduction Partnership (NICRP) and UK policing agencies to build a comprehensive picture of the threat and coordinate an effective response.
Forklift collisions cost UK businesses over £100 million annually in workplace injury claims and equipment damage, according to HSE statistics. SharpEagle Technology, a globally renowned provider of industrial safety solutions, has announced a significant breakthrough in warehouse safety across the UK. Facilities that adopted SharpEagle’s Radar Blind Spot Detection System have reported up to 70% reduction in forklift-related accidents, marking a major milestone in workplace safety. The UK's blind spot crisis With over 1,300 forklift-related incidents reported to HSE each year, many involving serious injuries, UK regulators are pushing for smarter safety solutions. Traditional mirrors and cameras frequently fail in: Rainy loading docks Dusty manufacturing plants Crowded retail distribution centers Visual and audible signals The system, which uses radar sensors to monitor blind spots and detect real-time sign around forklifts The system, which uses radar sensors to monitor blind spots and detect real-time movement around forklifts, has proven to be a game changer in accident prevention. It immediately alerts operators through visual and audible signals when people or objects enter dangerous proximity zones, reducing the likelihood of collisions, especially in busy loading docks and narrow warehouse aisles. Real-time awareness "In a typical warehouse, poor visibility and human error can lead to severe accidents. Our technology gives operators real-time awareness they didn’t have before," said the UK Business Head of SharpEagle Technology, adding "The impact has been measurable. Clients report fewer incidents, improved productivity, and safer working conditions." Adoption growing across logistics The system offers cost-effective safety enhancement without the need for vehicle relief The Radar Blind Spot Detection System has quickly gained popularity among UK logistics providers, manufacturing units, and retail distribution centers — sectors where high forklift traffic and pedestrian movement often intersect. By integrating with existing forklift infrastructure, the system offers cost-effective safety enhancement without the need for vehicle replacement. It is also compatible with SharpEagle’s wider range of forklift safety solutions, including AI-based camera systems and anti-collision lights. Regulatory & insurance benefits In addition to preventing injuries, the deployment of radar-based detection systems has helped warehouses comply with UK Health and Safety Executive (HSE) guidelines. Several facilities have seen a reduction in insurance claims and premiums, along with fewer incidents of lost workdays due to injury. "Workplace safety is not just a legal requirement — it’s a business imperative. This technology ensures companies are equipped to meet the demands of a modern, high-speed supply chain without compromising on the well-being of their workforce."
Omnilert, a pioneer in AI-driven safety solutions and AT&I Systems, announced that Amerant Bank has chosen Omnilert’s AI technology to help bolster the security at all of its locations in Florida. AT&I Systems, a longtime security partner of Amerant Bank, was chosen as the security integrator. Omnilert’s software, which recently received the full SAFETY Act Designation by the U.S. Department of Homeland Security (DHS), will be integrated into more than 160 existing Amerant Bank cameras to provide advanced 24/7 surveillance with automated response capabilities. Key layer of security “Omnilert technology has become a key layer of security that can transform traditional surveillance capabilities and ensure a fast, robust and automatic response in an emergency,” said Dave Fraser, CEO of Omnilert. “With our software running non-stop in the background, Amerant can focus on carrying out their daily business knowing their workers and patrons are being kept safe from harm.” New and innovative ways to enhance the safety “At Amerant Bank, we are always looking for new and innovative ways to enhance the safety of our bank locations, and Omnilert’s AI technology will be an important part of our overall security infrastructure,” said Orlando Gonzalez, Head of Corporate Security at Amerant Bank. “Integrating the software into our existing cameras made the installation quick and seamless, and once installed, it transformed these cameras into powerful, intelligent surveillance devices that are constantly detecting potential threats.”
VIVOTEK, the global pioneering security solution provider, has played a pivotal role in enhancing campus safety at CDO Newton, a renowned educational institution in Sint-Niklaas, Belgium, that helps guide students in taking their first steps toward the job market. As CDO Newton expanded its facilities, ensuring the security of students, staff, and visitors across a larger, more dynamic campus became increasingly challenging. To address this, CDO Newton turned to VIVOTEK's state-of-the-art AI security solutions to provide a scalable, comprehensive security system that offers maximum coverage, advanced AI capabilities, and improved operational efficiency. Challenges CDO Newton's previous security infrastructure was unable to effectively monitor all areas CDO Newton's previous security infrastructure was unable to effectively monitor all areas of its expanding campus. It lacked full coverage and had blind spots, while system administrators spent long hours manually searching footage. Additionally, the time-consuming manual video review process hindered the quick identification and response to potential incidents. The institution needed a solution that would: old and outdated. Provide comprehensive coverage with minimal blind spots. Enable efficient monitoring and management using AI-driven technology. Be scalable to accommodate future growth and evolving security needs. Reduce the total cost of ownership by minimizing the number of cameras required and simplifying maintenance. VIVOTEK, in collaboration with trusted partners Educorner bvba and Optima Networks, provided a powerful solution that addressed these challenges head-on. By combining VIVOTEK’s AI-powered cameras with a user-friendly video management platform, the solution ensured enhanced campus security, and a more efficient overall system. Solutions VIVOTEK’s security technology played a central role in transforming CDO Newton’s security infrastructure. A carefully planned deployment saw the installation of a range of VIVOTEK cameras, complemented by Network Optix Video Management System(VMS) and VIVOTEK's Deep Search Plugin, to provide an integrated and effective solution. Key components of the system included: 12MP 360-Degree Fisheye Cameras: These cameras deliver panoramic coverage, eliminating blind spots and reducing the number of cameras needed. With their wide coverage area, they also minimize installation and maintenance costs, offering a highly cost-effective long-term solution. 5MP 180-Degree Panoramic Cameras: Ideal for areas requiring broad, high-definition coverage, these cameras ensure clear, distortion-free footage across key zones. 89-v2 Fixed Dome Cameras: These cameras were strategically placed to secure high-risk areas, delivering clear, AI-powered analytics that support enhanced object detection and incident management. Network Optix VMS and VIVOTEK Deep Search Plugin: Integrated into the system, these tools significantly enhance usability, enabling security personnel to quickly search and identify objects and individuals within large video datasets using advanced AI-based filters. Key benefits to CDO Newton Comprehensive Coverage with Cost Savings: VIVOTEK’s combination of 360-degree and 180-degree panoramic cameras ensures wide coverage of CDO Newton’s campus, reducing the need for additional cameras. This translates to lower installation and maintenance costs while still providing robust security coverage. AI-Powered Object Detection and Real-Time Alerts: Equipped with VIVOTEK’s Edge AI technology, the system’s advanced object recognition capabilities detect unusual trespassing in restricted areas or unauthorized vehicles parked in no-parking zones. This ensures security staff can investigate and intervene promptly, minimizing risks and enhancing overall campus safety. Intuitive Video Management: The integration of VIVOTEK’s Deep Search Plugin with Network Optix VMS provides a user-friendly interface that allows security staff to easily manage and monitor live footage, conduct investigations, and access historical data. This streamlined process reduces the need for extensive training and enhances operational efficiency. Scalability for Future Growth: The modular nature of the system ensures that it can be expanded to meet the future needs of CDO Newton as the campus continues to grow. Additional cameras can be easily added without significant disruption to existing operations, ensuring that the institution’s evolving security requirements are met. Results and customer feedback VIVOTEK, in collaboration with local partners Educorner bvba and Optima Networks, successfully implemented an efficient security solution at CDO Newton. This exciting example demonstrates the integration of innovative technology and expertise to create a secure, scalable, and cost-effective system, providing a safer learning environment for both campus management and students. VIVOTEK continuously offers the most trusted cutting-edge security solutions to its customers and deeply develops various vertical markets in the future, including the educational sector that fosters knowledge.


Round table discussion
By all accounts, technology development is moving at a rapid pace in today's markets, including the physical security industry. However, market uptake of the newest technologies may lag, whether because of a lack of clear communication or not enough education of potential customers. We asked this week's Expert Panel Roundtable: How can the industry do a better job of promoting emerging technologies in physical security environments?
The hospitality industry drives economic growth and development by creating jobs, generating revenue, and initiating a ripple effect to improve profitability throughout the supply chain. The hospitality industry includes a vast number of small businesses, including hotels and restaurants. But what are the security challenges of these businesses, and how is the security marketplace serving those needs? We asked this week's Expert Panel Roundtable: How can technology address the security challenges of the hospitality market?
Retaining top talent is a route to bring innovative ideas and creative solutions to a company. Talent drives product development, improves processes, and helps businesses stay ahead of the competition. In essence, retaining top talent is essential for businesses to remain competitive, innovative, and successful. Unfortunately, staffing shortages are a reality for many corporate players in the security industry, as well as throughout the business community. We asked this week's Expert Panelists: How can physical security organizations attract and retain top talent?
White papers

Safeguard Students With New Techniques And Technology
DownloadCybersecurity in Keyless Access Management
Download
Assessing Safety Readiness For Education Campuses
Download
Preparing Your Organization With Quality Situational Awareness
Download
Expanding Video Surveillance In The Enterprise Market
Download