South Africa News
Amazon Go is a new idea in retailing, now being tested at a store in Seattle, that eliminates the need for customers to go through a checkout line. The so-called “just walk out” experience depends on “the world’s most advanced shopping technology.” Customers simply enter a retail store, choose the goods they want, and leave. The checkout process is automated: The selected goods are charged to the customer’s account automatically. Solving Shoplifting Most of...
The forecast for 2017 is also based on a breakthrough in adoption of mobile identity technology in 2016 HID Global, a provider of trusted identity solutions, forecasts a shift in the use of identity technology that will lead to increased adoption of mobile devices and the latest smart card technology, a greater emphasis and reliance on the cloud, and a radical new way of thinking of trust in smart environments and Internet of Things (IoT). Ultimately, HID Global predicts the...
Physical access control has been a key component of many organizations’ security strategies for several decades. Like any technology, access control has evolved over the years, and solutions now offer more security and convenience than ever before. From swipe technologies, such as the now antiquated magnetic stripe, to a variety of contactless technologies and mobile access credentials, businesses now have several choices when it comes to access control. Upgrading Outd...
High definition has become the camera technology of choice for new installations Video storage is the foundation for new video surveillance infrastructures. Depending on your platform, storage can enhance your surveillance system’s capabilities, or it can limit them. But one thing is certain: your storage decision can no longer be an afterthought. Tremendous Growth In Data Storage Digital technology is transforming the surveillance industry. In fact, it’s estimat...
With the current state of economic uncertainty, there is a huge opportunity in 2017 for perimeter intrusion detection (PID) manufacturers to reach the commercial market. Petty crime rates, such as theft and vandalism, are on the rise and, as a result, small business owners are looking for new security options to enhance their current camera and alarm systems. Often thought of as complicated, expensive, and only for high-value applications, PID has a chance to change its perception in the years...
The security industry will continue to see consolidation through acquisition in 2017. At the advent of IP camera adoption, we saw a great decline in large vertically integrated companies, which spurred a new era of innovation within smaller IP camera manufacturers, VMS providers and other hardware companies for storage and managed switches. We are now living in a new era of consolidation that is taking us full-circle back to vertical integration. Ultimately, the industr...
Some Expert Panel Roundtable topics are more challenging than others. Occasionally a question will “stump” the panel – i.e., no one will choose to answer it. Other times, only one or two panelists will step forward to answer a question. One comment does not a “panel” make. Taken together, however, these varied comments offer their own range of insights into the evolving physical security market. Let’s look at some of these assorted Expert Panel comments over t...
The year of 2016 ended with Vanderbilt finalizing the acquisition of Access Control Technology Ltd., which strengthened the company’s product portfolio and introduced an entirely new market segment to partners and customers in Ireland and the United Kingdom. ACT brings an existing cloud-based access control solution to Vanderbilt, thereby complementing the existing product mix. This new technology adds significant value to our customers in Europe, and we plan to deliver it to our customer...
Ongoing attacks on private networks drew attention in 2016. Most public were the Wikileaks and other privacy violations during the 2016 election cycle. Whether or not the information had a bearing on the election outcome will never truly be known, but one’s overall sense of privacy is shaken. In many ways, these attacks and other less publicized cybercrimes were the result of a perfect storm. Organizations struggled with the sheer volume and constantly changing threats from advanced malwa...
At the end of last year, we anticipated that data gathering and analysis would continue to be a strong trend, and that certainly proved to be the case in 2016. More and more organizations are seeing the value of the intelligence provided by diverse systems’ data. The number and variety of networked systems and devices – both security and non-security – continued to grow steadily in the last year, and the data these disparate sources create has proven highly...
As the whirlwind of 2016 quickly winds down, it is a good opportunity to look back at the significant trends from this year. As predicted, the industry experienced accelerated data growth, the continued convergence of security and IT, and the ever-expanding impact of the Internet of Things (IoT).Overall, 2016 was a good year. IT investments were strong and organizations rapidly adopted new data center advancements such as hyper converged infrastructure (HCI) to help manage the huge influx of cri...
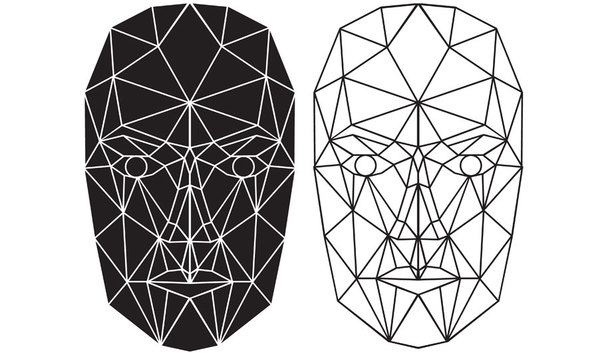
The latest challenge to facial recognition technology is “anti-surveillance clothing,” aimed at confusing facial recognition algorithms as a way of preserving “privacy.” The clothing, covered with ghostly face-like designs to specifically trigger face-detection algorithms, are a backlash against the looming possibility of facial recognition being used in retail environments and for other commercial purposes. Increasingly Common Facial Recognition Technology It’s a...
Predicting where or how security access trends would develop in 2016 was an educated guess at best. We did, however, forecast continued growth in the areas of wireless readers; smartphone usage as a credential; and more migration to web-based software/hardware solutions.In hindsight, we were not so far off the mark. Wireless security systems proved to be a growing option for extending an access control system and a practical solution for retrofits. Smart phone credentials gained popularity by fr...
Overall, 2016 has been a great year for AxxonSoft. We have seen great progress in the industry on an economic level as well as in development. Europe’s economy has been on the rise and particularly the United Kingdom. As a result, we have seen new technologies emerging in the market and a lot more opportunities. Benefits Of Cloud Services And Future Trends From a software stance, we have noticed the benefits of cloud service, and requests are becoming more regular. In the UK, Brexit ha...
Nedap provided Unilever with a new security solution for physical access to its sites across the world Unilever wanted to enhance user experience, increase security and reduce costs, and chose AEOS as the solution to this challenge. AEOS will secure 20,000 doors across more than 800 Unilever sites, as well as providing video surveillance and a range of other access management services. Ian Dunning, Unilever’s Global Facilities Director, and Jeroen Gieling, Nedap&r...
Vanderbilt SMS helps make sure that all personal information at the Sheriff's office is protected Home to 30,000 residents, Bradford County is a rural community located 45 miles Southwest of Jacksonville, Florida. The Bradford County Sheriff’s Office is mandated to protect its citizens and at the same time, safeguard sensitive criminal justice information, such as fingerprints and backgrounds from unauthorized exposure. Bradford County started out using security technol...
The emergence of smart technology into the security sector is changing risk management economics and strategy in unique ways. Such technology leverages information management at its core for a more effective security program. Case in point is the burgeoning role of autonomous data machines (ADMs or robots) that are purposely built for security. Will the advent of robots eliminate physical security officers at a site? Not any time soon, but robots are a real force multiplier by adding effec...
In the past year, we have continued to see that the global security market is both dynamic and evolving. The term “security” no longer means simply protecting the perimeter of a building; it also involves securing corporate networks and sensitive data. In 2016, this trend was driven by a change in organizational threats. Businesses as a whole are much more focused on cyber-threats, a growing paradigm that challenges business and security leaders to stay one step ahead of crime and fr...
After two decades of advances from simple visual ID badges to smart cards, standards-based access control systems and mobile ID solutions, the industry began entering its next new chapter in 2016. We began “mobilizing” security to make it more pervasive and personalized, with a better user experience. We entered a new era of secure connected identities will not only make us safer but fuel innovation in how we work, shop and play. The industry began paying much closer attention to p...
SourceSecurity.com’s Expert Panel covered a lot of ground in 2016 about a variety of topics in our Roundtable discussions. The very most-clicked-on Roundtable discussion in 2016 was about how to choose between a cloud-based system and a server-based system. Other hot topics that made the Top-10 list of Roundtable discussions included edge-based video storage, the challenges of commoditization, and mistakes customers make when buying and installing security systems. He...
Again in 2016, the most well-trafficked articles posted at SourceSecurity.com tended to be those that addressed timely and important issues in the security marketplace. In the world of digital publishing, it’s easy to know what content resonates with the market: Our readers tell us with their actions; i.e., where they click. Let’s look back at the Top 10 articles we posted in 2016 that generated the most page views. They are listed in order here with the author&r...
The shift from wired to wireless access control was expected to gather pace in 2016—and that has happened. This year we at Assa Abloy surveyed a large cross-section of security professionals, seeking their insight into the changing market. Comparing our data with research we did in 2014 showed a clear trend towards wireless access control. Wireless Access Data Our 2014 survey found 23% of commercial properties using a wireless or hybrid wired/wireless access control s...
The winds of change have swept into the access control market in 2016. The hardware is transitioning away from being solely panel-based, software is rapidly moving to the cloud, and credentials are going mobile. It seems that the security access control world is finally waking up from its technological slumber, and 2017 will be an exciting time. These three major trends are feeding off one another and are driving the growth all around. IP And Edge Based SystemsIn 2016, hardware companies like...
Merger and acquisition activity has become a familiar topic in the physical security market. In 2016, SourceSecurity.com covered M&A news involving some of the industry’s largest companies, including high-profile names such as Tyco, Honeywell, Hikvision, ADT, and Ingram Micro. Here’s a look at the top 10 M&A stories in 2016, as covered by SourceSecurity.com: 1. Johnson Control And Tyco merge Johnson Controls and Tyco announced their merger into one comp...
Over the last year, we have continued to see the rise of manufacturers from China in the mid- to low-end market for video surveillance - a trend that currently shows no signs of tapering. Additionally, the shift from analog to IP systems has remained consistent, with end users increasingly looking to network-enabled devices to mitigate risk from both a physical and cyber perspective. Complex network attacks in 2016 demonstrated the need for increased network security for network-connected devic...
The economy positively impacted the security marketplace in 2016 as end users have been more willing to invest in new security systems or upgrade existing systems. Organizations are breaking down department silos as it has become clear that security impacts everyone. Companies are realizing they need to do more with the data they have. Utilizing Security System Data Access control, video management, identity management and visitor management systems provide data that can help companies streaml...
Drastic increase in cybersecurity discussions is one thing that many of us in the security industry didn’t predict for 2016. Cybersecurity has obviously always been an important issue in general, but the discussion has gained a lot of momentum in the past year. As I said, this wasn’t predicted by most of us in the industry. The intensity of the focus on and discussion around cybersecurity in 2016 was a response to some of the high-profile denial of service (DoS)...
The end of the year is a great time to reflect on what the security industry has accomplished and to look ahead. We invited our Expert Panel Roundtable to weigh in on what they expect looking forward to the new year. Most industry-watchers are familiar with the major trends, but how will those trends play out in 2017? Specifically, we asked this week’s Expert Panel Roundtable: What will be the biggest headlines for the security marketplace in 2017?
With security, as with any business cost-center, business leadership wants to find savings where they make sense. As a result, one of the trends we are seeing is that security departments are teaming up with other departments - IT, operations, marketing - to maximize their investment in security systems and leverage the data collected by their physical security sensors to inform their business strategies. Rise In Cyber-Attacks We have also seen a worrying increase in cyber-attacks, like the hi...
The past year has seen growth in the deployment and use of edge analytics, plus a significant emphasis placed on robust cybersecurity. The expectation for 2017 is that these two trends will continue to be a driving factor for value-based decision making of large, influential customers. IP camera product lines from reliable and well-regarded brands that include edge analytics and offer a trusted, secure platform will be at an advantage over those that don’t. Looking back at the expectation...
Browse security news
Featured products
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
The Key To Unlocking K12 School Safety Grants
DownloadHoneywell GARD USB Threat Report 2024
DownloadPhysical Access Control
DownloadThe 2024 State Of Physical Access Trend Report
DownloadThe Security Challenges Of Data Centers
Download- South Africa Security companies
- South Africa Manufacturers
- South Africa Distributors
- South Africa Resellers / Dealers / Reps
- South Africa Installers
- South Africa Consultants
- South Africa Systems integrators
- South Africa Events / Training / Services
- South Africa Manned guarding
- South Africa Training organisations
- South Africa Associations / regulatory bodies
- South Africa Event organisers
- South Africa Media
- South Africa Services
- South Africa Recruitment / personnel


![[Download] The Evolution Of Cards And Credentials In Physical Access](https://www.securityinformed.com/img/news/612/HID-whitepaper-Evolution of Cards and Credentials-920.jpg)