South Africa News
A new crime wave is hitting automated teller machines (ATMs); the common banking appliances are being rigged to spit out their entire cash supplies into a criminal’s waiting hands. The crime is called “ATM jackpotting” and has targeted banking machines located in grocery shops, pharmacies and other locations in Taiwan, Europe, Latin America and the United States. Rough estimates place the total amount of global losses at up to $60 million. What Is Jackpotting? ATM j...
In today's world of heightened security threats, the Internet of Things (IoT) and the availability of overwhelming amounts of data, comprehensively securing a single small facility is no easy task. Enterprise organizations tend to face even greater challenges when it comes to safety, as multiple people scattered throughout separate locations aiming to collaboratively respond to situations can easily become complicated. Individual buildings, divisions and branches of a large and/or global ente...
The manufacturers behind today’s security technologies are a varied bunch. There are large manufacturers with deep pockets and plenty of resources. And there are smaller manufacturers who are nimble, can react faster to changing market conditions and to whom each customer represents a hard-fought win. There are also plenty of manufacturers in the middle ground. But what impact does the size of a company have on the quality of its products? We took the question to this week’s Expert P...
While there is much hype around drone technology today, initial successful drone usage for security can be dated back to the 1960s, when the US utilized the Lightning Bug 147, a camera-equipped unmanned aerial vehicle that could travel 600 miles for surveillance in Vietnam, China and Korea. Drones For Effective Surveillance Since this initial deployment, drones have been used for a variety of security and surveillance applications. However, as professional-grade commercial drones incorporate...
PenTesting, also known as “ethical hacking” or “white-hat hacking,” has always been viewed as the “sexy” side of cybersecurity, a task that is far more exciting than monitoring systems for intrusions, shoring up defenses, or performing compliance audits. Numerous security conferences are devoted to the fine art of attempting to hack into systems – with an owner’s full knowledge and permission – and reporting on the results. At an organizati...
Milestone Systems is embracing artificial intelligence and deep learning in a big way at this week's yearly Milestone Community Days (MIPS 2018) in Las Vegas. The Danish company's theme is "Creating an Intelligent World," and Milestone's stated goal is to make "the Milestone community part of every surveillance installation in the world." Science Fiction Becomes Reality In a presentation on opening day, Milestone CSMO Kenneth Hune Petersen pointed to the 2002 movie The Mino...
The way we purchase services and products is changing. The traditional concept of buying and owning a product is giving way to the idea that it is possible to purchase the services it offers instead. This approach has come from the consumer realisation that it is the outcome that is important rather than the tools to achieve it. For example, this approach is evident with the rise of music streaming services as opposed to downloads or physical products. With the physical...
Organizations across the world face a new risk paradigm: one that encompasses cyber and physical threats. We’ve heard the stories associated with ATM skimming, identity theft, data breaches, scams, and phishing. Large financial services organizations are often the victim of hackers looking to steal corporate information and transactional data or funds, and criminals continue to become more sophisticated in their approach. Growth In Cyber-Attacks Additionally, cyber-threats have taken a...
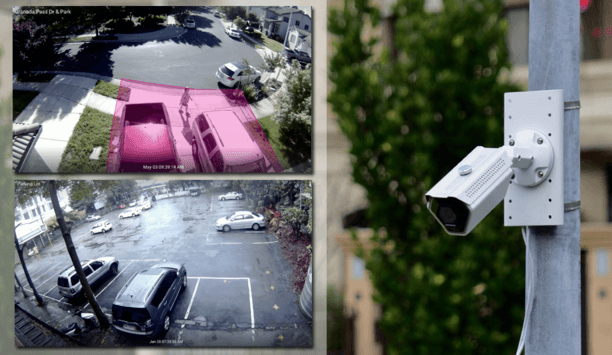
Among its many uses and benefits, technology is a handy tool in the fantasy world of movie and television thrillers. We all know the scene: a vital plot point depends on having just the right super-duper gadget to locate a suspect or to get past a locked door. In movies and TV, face recognition is more a super power than a technical function. Video footage can be magically enhanced to provide a perfect image of a license plate number. We have all shaken our heads in disbelief, and yet, our indus...
Honeywell has announced the release of its smart building technology, Command and Control Suite Release 200 (CCS R200), which connects building personnel with data analytics to help drive operational improvements and efficiencies. CCS R200 builds on the original Command and Control Suite by offering more user interfaces to bring building performance data to key personnel, when and where they need it—from building operators and managers to security incident response teams—helping to...
BCDVideo, producer of purpose-built IP video storage solutions, announced the signing of an Original Equipment Manufacturing (OEM) agreement with Dell EMC OEM Solutions. The collaboration enhances BCDVideo’s product portfolio with the inclusion of end-to-end solutions featuring Dell EMC Server, Storage and Networking platforms, along with Dell commercial client products. Dell EMC has demonstrated a strong commitment to providing security integrators unparalleled access to a wide range of...
In a significant move for the video security market, BCDVideo has announced that it is set to become Dell EMC’s OEM partner in the video surveillance space. For nearly a decade, the Chicago-based company has been known as a key OEM partner of Hewlett Packard Enterprise (HPE), providing storage and networking technology to security integrators on a global scale. This latest partnership will allow BCDVideo to take their offerings to the next level. BCDVideo Vice President Tom Larson spoke to...
Founded in 1871, Fulton County School System is the fourth largest school district in Georgia, United States. It consists of 101 schools and administrative support buildings, including 67 elementary schools, 19 middle schools, 17 high schools and eight charter organizations. Fulton’s mission is to provide a safe and secure environment for its more than 96,000 students and more than 12,000 full-time employees. To help enhance safety at more than 100 schools, Fulton has installed a full Avi...
The Food Standards Agency (FSA) in the UK has begun investigations into meat wholesalers after a raise in concern for food hygiene. This investigation has impacted businesses such as Wetherspoons, as well as schools and care homes up and down the country. Consumers are beginning to lose trust in businesses that are supplied by untrustworthy production companies and it seems to be becoming more common, if we are to look back to the horse meat scandal in 2013. But what are the benefits of havin...
The Monterey Bay Aquarium has a rich history of innovation. Since its founding in 1984, the facility has become one of the world’s leading public aquariums and ocean conservation organizations. Monterey Bay Aquarium has produced significant insights into the life history of sharks, sea otters, and bluefin tuna. The aquarium also was the first to exhibit a living kelp forest, and in 2004 it was the first to successfully exhibit and return to the wild a young great white...
Fly-tipping – the illegal act of dumping large amounts of waste on unlicensed land without authorization – occurs on both private and business land and can be a real annoyance to those in the UK. Items that fall under the banner of fly-tipping include tyres, mattresses, beds, garden waste, and construction rubbish. Unfortunately, the property owner will be responsible if somebody dumps their rubbish. Although this seems unfair, following some basic steps will help handle the proble...
Until recently, data laws have differed from one country to the next. This meant that for those organizations conducting business or protecting assets abroad, they needed to localize both their infrastructure and policies dependant on the country they were operating in. However, with the impending arrival of the EU GDPR (General Data Protection Regulation), which comes in to force on the 25th May this year, all of that will need to change. Data Management In CCTV Surveillance Surprisingly, des...
How much does a security system cost? We all know that total costs associated with systems are substantially higher than the “price tag.” There are many elements, tangible and intangible, that contribute to the costs of owning and operating a system. Taking a broad view and finding ways to measure these additional costs enables integrators and users to get the most value from a system at the lowest total cost of ownership (TCO). However, measuring TCO can be easier said than done. We...
VMS software and IP products from Hikvision, a supplier of innovative video surveillance products and solutions, are now being used by the Government of Gujarat Directorate of Technical Education (DTE), to protect and administer education facilities and services across Western India. A government organization that provides qualitative and higher level technical training for students from a diverse mix of financial and social backgrounds, the Directorate of Technical Education’s (DTE) goal...
Leadership roles are changing inside enterprise companies, where higher profiles of roles like CIO and CISO are blurring the lines separating legacy security departments from the larger enterprise. The role of security – protecting the company – now overlaps with broader concerns such as business optimization. The changes are impacting how technology is used; what was once considered a “security system” can now impact the company in larger ways. It’s not just prot...
Over the past year, we’ve heard a lot of big buzzwords in conversations at different conferences, meetings and events. Deep learning, artificial intelligence and cybersecurity are hot topics, and these trends will undoubtedly define the landscape over the coming year. Other issues, mostly IT related, are also making their way into more and more surveillance-focused conversations and to me, none is more complicated — or beneficial — than hyperconvergence. W...
The Middle East security market provides a healthy opportunity for manufacturers who can capitalize on the region’s key verticals. Intersec’s 20th edition show focused more on solutions than on products, including solutions for the growing retail sector and an infrastructure market requiring ruggedized equipment to stand up to harsh environments. Intersec hosted security, safety and fire protection exhibitors from over fifty countries at Dubai’s spacious International Conventi...
An initial investment of $100 million launched the first American public university campus in Mexico: Arkansas State University Campus Queretaro (ASUCQ). Within five years of its 2017 opening, around 7,500 staff and students are expected to use the site, including campus accommodation for up to 1,500 students. To accompany such a high-profile development, the university needed security and access control systems with a trusted and proven track record protecting staff, students and other univers...
Security solutions today do more than merely observe and prevent criminal activity. Systems are increasingly tasked with making sense of the world around us. At Intersec 2018, which took place January 21 – 23 in Dubai, manufacturers set out to show how predictive analytics and artificial intelligence are already being used in real world applications: predicting criminal behaviour, managing traffic, and streamlining smart city operations. Dubai Smart City Initiatives...
There’s a new big player – and familiar household name – coming into the security marketplace with the announcement of Motorola’s intent to acquire Canadian video manufacturer Avigilon Corporation, provider of video surveillance and analytics. Motorola Solutions points to an “avalanche of video in public and private sectors” as a motivation for the acquisition. Motorola Solutions’ dominance in the public safety market – where t...
Motorola Solutions has announced that it has entered into a definitive agreement to acquire video surveillance provider Avigilon in an all-cash transaction that will enhance Motorola Solutions’ portfolio of mission-critical communications technologies. Under the terms of the agreement, Motorola Solutions will acquire all of Avigilon’s outstanding shares for CAD$27.00 per share. The enterprise value of the transaction is approximately US$1.0 billion ...
The cloud and deep learning are two technologies on the verge of transforming the video surveillance market. You often hear the two technologies mentioned as separate trends, but lately, I have been hearing about how interdependent they are. Economies of scale provided by the Cloud (Software as a Service, or SaaS) are making the sophisticated capabilities of deep learning affordable to a wider audience. Meanwhile, deep learning augments cloud systems with capabilities that...
In November of 2017, the Vietnamese police seized a number of smuggler dens that had illegally sold Dahua security equipment while they were conducting "smuggling and counterfeiting" remediation operations. The smugglers allegedly conducted illegal smuggling and counterfeiting of popular brand products. After being informed of the incident, Dahua cooperated actively with the investigation of Vietnamese police, providing supports to technically identify the goods. Dahua equipment tampered Furt...
In tidying up after a year of Expert Panel Roundtable questions and answers, we came across some previously unpublished responses from our panel. These interesting responses address some of the hottest topics in the industry, from robots and deep learning to the “race to the bottom.” Taken together, the varied comments offer their own range of insights into the evolving physical security market. This week, we highlight some of these assorted Expert Panellist comments submitted over t...
Pelco by Schneider Electric, a provider of surveillance and security, will exhibit their latest innovative solutions at Intersec 2018 in the Dubai International Convention and Exhibition Center. Visitors to Pelco’s stand will experience solutions for markets that are specifically engineered for the Middle East and Africa regions and that provide truly innovative and comprehensive solutions to customer challenges. Integration And Partnerships Pelco is showcasing recent partnerships with t...
Browse security news
Featured products
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
The Key To Unlocking K12 School Safety Grants
DownloadHoneywell GARD USB Threat Report 2024
DownloadPhysical Access Control
DownloadThe 2024 State Of Physical Access Trend Report
DownloadThe Security Challenges Of Data Centers
Download- South Africa Security companies
- South Africa Manufacturers
- South Africa Distributors
- South Africa Resellers / Dealers / Reps
- South Africa Installers
- South Africa Consultants
- South Africa Systems integrators
- South Africa Events / Training / Services
- South Africa Manned guarding
- South Africa Training organisations
- South Africa Associations / regulatory bodies
- South Africa Event organisers
- South Africa Media
- South Africa Services
- South Africa Recruitment / personnel