South Africa News
As we approach National Safe Schools Week (October 21-27), it is appropriate for a conversation to begin regarding establishing standards for K12 school security. Currently no standards exist for assisting schools navigate the complexity of understanding what they need, how much it will cost and how they will secure their learning environments. Security Industry Experts The Partner Alliance for Safer Schools (PASS) is one of the organizations at the forefront of establishing security standards...
Hikvision, the world’s supplier of innovative security products and solutions, announced its IP camera product series, DS-2CD3 and DS-2CD5, have achieved the Certificate of Common Criteria for Information Technology Security Evaluation (abbreviated as Common Criteria or CC) with assurance type EAL2 augmented with ALC_FLR.2 (EAL2+). It demonstrates Hikvision’s commitment to global customers on reliability and cybersecurity. As one of the most widely recognized international standards...
The last day of Global Security Exchange (GSX) in Las Vegas proved to be the calm after the storm. But a slower third day could not undermine a largely successful 2018 show for exhibitors and attendees. Sometimes the success of a trade show isn’t measured by numbers of attendees (which were reportedly down again this year). Sometimes it’s the individual successes that make an impression. “Just learning about this made the whole trip worthwhile,” said one GSX attendee at...
Johnson & Quin, a nationally-trusted provider of edge direct mail production, integrated marketing solutions, data services and high-speed color inkjet printing, has successfully completed a rigorous examination of its data security processes and procedures, under the SOC 2 Type 1 standards. The SOC 2 examination was administered by the professional IT assurance and compliance staff, at 360 Advanced, a respected national Qualified Security Assessor, HITRUST CSF Assessor and CPA firm, based...
NAPCO Security Technologies has released a new upgrade for any alarm system and any dealer: the professional-grade, full-featured iBridge Video Doorbell. Today, it seems everyone wants a video doorbell and this new product from Napco can be an easy add-on and RMR-generating convenience for any alarm account, using either the standalone video App, or integrated with iBridge Connected Suite Smart App & optional new, iBridge Touch™ 7” Touchscreen. The iBridge Video Doorbell l...
More good news for exhibitors on the second day of the Global Security Exchange (GSX) in Las Vegas. Brisk attendance continued early in the day, and then slowed somewhat in the afternoon, but most comments from exhibitors were positive. Exhibitors such as Lenel were “thrilled” with the show, and noticed the steady, good traffic and lots of sales leads. Lenel’s position at the front of the hall probably helped. New developments in mobile credentialing are a big trend at GSX, an...
The Global Security Exchange (GSX) seems smaller this year, which is not surprising given the absence on the show floor of several big companies such as Hikvision and Assa Abloy (although their subsidiary HID Global has a big booth). A trend affecting the number of companies exhibiting at GSX 2018, and other trade shows, is industry consolidation, which is impacting the show even beyond the fewer exhibitors this year in Las Vegas. GSX is the new branding for the trade show formerly known as ASIS...
ISC West, like any large trade show, can be daunting for attendees. At big shows, there can be hundreds of physical security manufacturers and dealers vying for your attention. As the scope of physical security expands from video surveillance and access control to include smart building integrations, cyber security and the Internet of Things (IoT), there is an increasing amount of information to take in from education sessions and panels. With ISC West approaching April 19-12 in Las Vegas, we p...
Dallmeier offers comprehensive security solutions for all areas of application around airports. Specifically, in the area of cameras a wide range of systems allow customers to tackle all of their safety and security challenges and be able to comply fully with operational and regulatory requirements. On top of that, Dallmeier supplies video management solutions that not only give operators an exhaustive overview of security-relevant events, but also allow the video data to be analyzed with a vi...
Recife’s urban trains system carries around 400 thousand passengers a day – it is the third largest railway operator in number of users in Brazil. To ensure a safe journey for passengers, it is imperative to increase the subway security with modern technologies and monitoring equipment. The main challenge was to adapt the technology to the specific conditions such as lighting, people flow and speed of a subway station while not interrupting the transportation service. Therefore, eas...
I have been thinking a lot about the U.S. government’s ban on video surveillance technologies by Hikvision and Dahua. In general, I question the wisdom and logic of the ban and am frankly puzzled as to how it came to be. Allow me to elaborate. Chinese Camera Manufacturers Reality check: The government ban is based on concerns about the potential misuse of cameras, not actual misuse. Before the government ban, you occasionally heard about some government entities deciding not to use camer...
Governments and corporations face crisis events every day. An active shooter terrorizes a campus. A cyber extortionist holds a city for ransom. A hurricane washes away a key manufacturing facility. Not all critical events rise to the level of these catastrophic emergencies, but a late or inadequate response to even a minor incident can put people, operations and reputations at risk. Effective Response Plan In 2015, for example, the City of Boston experienced several record-breaking snowstorms...
Using a smart phone as an access control credential is an idea whose time has come – or has it? The flexible uses of smart phones are transforming our lives in multiple ways, and the devices are replacing everything from our alarm clocks to our wallets to our televisions. However, the transformation from using a card to using a mobile credential for access control is far from a no-brainer for many organizations, which obstacles to a fast or easy transition. We asked this week’s Exper...
In 1973, a brilliant economist named E.F. Schumacher wrote a seminal book titled ‘Small Is Beautiful:’ taking an opposing stance to the emergence of globalization and “bigger is better” industrialism. He described the advantages of smaller companies and smaller scales of production, highlighting the benefits of building our economies around the needs of communities, not corporations. In almost every industry or market that exists in the world today, you're like...
Repercussions are rippling through the physical security industry since President Trump signed into law the ban on government uses of surveillance equipment by Chinese manufacturers Hikvision and Dahua. In addition to the direct and indirect consequences of the new law, there have also been other developments likely to impact the future of Chinese companies in the video surveillance market. The ban has raised awareness of Chinese companies’ role in video surveillance, and other developme...
There’s a lot of excitement around artificial intelligence (AI) today – and rightly so. AI is shifting the modern landscape of security and surveillance and dramatically changing the way users interact with their security systems. But with all the talk of AI’s potential, you might be wondering: what problems does AI help solve today? The Need For AI The fact is, today there are too many cameras and too much recorded video for security operators to keep pace with. On top of...
Newly modernized halls with lots of daylight will house hundreds of exhibitions and conference events at the upcoming Security Essen 2018 at Messe Essen, Germany. A new layout and hall numbering system will be unfamiliar to past attendees but promises to simplify the experience as it brings together attendees and exhibitors. European Physical Security Market Security Essen is an international trade fair, but the emphasis is more on German, Austrian and Swiss companies. In all, Security Essen w...
There are many aspects to consider when developing a retail security strategy, including loss prevention, physical security, asset protection, risk management, and IT. All these areas could be the responsibility of just a few people working to secure a handful of stores or each of these areas could be entirely separate departments, as is often the case for major retailers with locations throughout the country. Regardless of the size of the retailer, there are many different technologies that ca...
GSX 2018 is both a new event for the security industry and the continuation of a 63-year tradition. Global Security Exchange (GSX) is the new branding for ASIS International’s annual seminar and exhibits, which have been held since 1955. In recent years, the ASIS event has joined forces with other organizations to expand its scope and to appeal to a broader audience. Partners include ISSA (Information Systems Security Association) and Infragard, a public-private partnership between U.S. b...
Fidano, a software and business solutions provider for the payment processing industry, has successfully completed a rigorous fifth annual examination of its policies and procedures, under the System and Organization Controls (SOC) 1 Type 2 standards, demonstrating its ongoing commitment to data security at all levels of its operations. SOC 1 Type 2 standards examination The demanding third-party examinations that led to the achievement were administered by the professional IT assurance and co...
KnowBe4, a provider of security awareness training and simulated phishing, has completed a rigorous third-party audit of its data security procedures and processes under the System and Organization Controls 2 (SOC 2) Type 2 standards. KnowBe4 completed the SOC 2 Type 1 examination in April, and immediately initiated action to achieve a SOC 2 Type 2 status. The examination that led to compliance with the demanding SOC 2 Type 2 data security standards was administered by the professional IT compl...
By now your organization should know the drill. To keep your enterprise safe from unauthorized access you take the basic precautions: create strong passwords that are not re-used and are updated frequently, use updated anti-virus software, employ host and network-based intrusion detection and prevention, data encryption, etc. etc. However, complacency has no place in cybersecurity. Hackers are working round-the-clock to outwit your most ardent security professionals. Here are a few specific vu...
The physical security industry is embracing the cloud in a big way. Cloud-based systems – which involve accessing a shared pool of information technology resources via the Internet – are much higher-profile in the video and access control markets, and large and small companies are getting on the cloud bandwagon. We asked this week's Expert Panel Roundtable: What factors are contributing to growth in cloud systems in the security market?
We are living in the age of Big Data, and businesses are inundated with large volumes of data every day. Success depends on capturing, analyzing and ultimately transforming that data into information and intelligence that can be used to improve the business. So, it is with today's physical access control and video systems, too, which also generate unprecedented levels of data. But how can we make the data useful to end users and how can they realize its full value? We asked this week's Expert Pa...
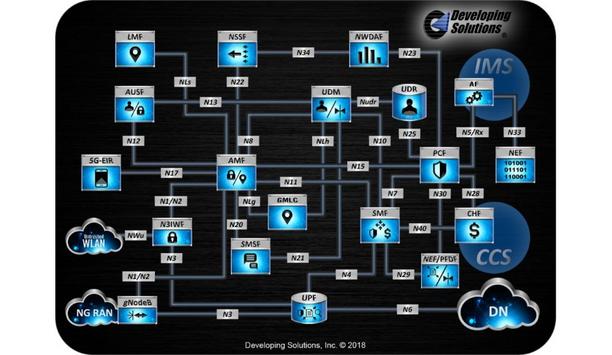
Developing Solutions, Inc. dsTest v5.1 is available to all current customers with active support agreements. It is available for downloading from the Developing Solutions secure support website. All features available in v5.0 are carried forward into v5.1. In addition to the continued support and development for 3G and 4G core network testing, dsTest v5.1 will include the initial releases of 5G core services for the N2, N8, N10, N13, N12, N11, and N4 reference points. Implementing automated te...
It has been an eventful few months for Arecont Vision, which has gone through Chapter 11 bankruptcy and, ultimately, was acquired by Costar Technologies Inc. What emerged is a new company, Arecont Vision Costar, poised for future growth unfettered by previous debt. For insights into what’s next for the newly minted company, we posed several questions to Jim Pritchett, CEO, Costar Technologies Inc., and Raul Calderon, President, Arecont Vision Costar. Q. Please relate how Costar came to...
When an active assailant strikes, it’s over fast, and most of the damage happens before help arrives. Responding appropriately can save lives, and it takes training and practice to know what to do as a tragedy unfolds: Where can I hide? Can I get out? Where do I run? If you hear shots or see someone with a knife, your training empowers the best response, and thorough and repetitive training avoids being paralyzed by panic. Standards On Workplace Violence ASIS International is a member of...
Facial recognition has a long history dating back to the 1800s. To track down criminals, such as infamous bandits Jesse Woodson James and Billy the Kid, law enforcement would place “Wanted Alive or Dead” posters advertising bounties and soliciting public cooperation to help locate and even apprehend the alleged criminals. In addition to the bounty, these posters would include a photo and brief description of the crime, which would then be circulated to law enforcement agencies arou...
Wireless locks offer specific advantages for access control end users and integrators, and some of their value has yet to be realized in the market. Wireless locks expand the range of applications for electronic locks to complement traditional wired systems. They offer flexibility and scalability. They save on integrators’ labor costs. They even provide opportunities for integrators to earn recurring monthly revenue (RMR). A recent Allegion panel discussion highlighted the value, opportun...
The beginning of the school year and upcoming seasonal changes remind us that demand for security systems, like almost everything else, is seasonal to some extent. Making improvements to educational facilities during the summer months – including installation of security systems – is the most obvious example of seasonal demand, but there are others. We asked this week’s Expert Panel Roundtable: Which vertical markets for security are impacted by seasonal changes in demand?
Browse security news
Featured products
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
The Key To Unlocking K12 School Safety Grants
DownloadHoneywell GARD USB Threat Report 2024
DownloadPhysical Access Control
DownloadThe 2024 State Of Physical Access Trend Report
DownloadThe Security Challenges Of Data Centers
Download- South Africa Security companies
- South Africa Manufacturers
- South Africa Distributors
- South Africa Resellers / Dealers / Reps
- South Africa Installers
- South Africa Consultants
- South Africa Systems integrators
- South Africa Events / Training / Services
- South Africa Manned guarding
- South Africa Training organisations
- South Africa Associations / regulatory bodies
- South Africa Event organisers
- South Africa Media
- South Africa Recruitment / personnel
- South Africa Services