Technology & Trends - Access control software
How AI and humans can work together is a longstanding debate. As society progresses technologically, there’s always the worry of robots taking over jobs. Self-checkout tills, automated factory machines, and video analytics are all improving efficiency and productivity, but they can still work in tandem with humans, and in most cases, they need to. Video analytics in particular is one impressively intelligent piece of technology that security guards can utilize. How can video analytics he...
Recent cyber-attacks have disabled and even shut down physical assets. Robust foundational security and training staff, able to recognize an attack can help mitigate the threat, as ABB’s Rob Putman explains. Edge devices and data analytics As cyber security specialists, we must navigate an ever-changing threat landscape, one that is made even more complex by the increased interconnectivity between Operational Technology (OT) and Information Technology (IT), as companies look to leverage...
The COVID-19 pandemic is only accelerating the expansion of Automation, Robotics, Machine Learning (ML) and Artificial Intelligence (AI), and changing how people live their daily lives. This expansion leads the way with technologies that are developed to solve problems, improve operations, streamline processes and assist people, to focus on learning new skills, creativity, and imagination. Transformation of the physical security industry One of the latest industries to be permanently transform...
Recently, the European Parliament called for a ban on police use of facial recognition. In the US, too, some cities have restricted police use of facial recognition. The first question that comes to mind is - why ban police from using technology that is allowed to private companies? Point of difference The key difference between the way police use facial recognition and the way commercial facial recognition products work is that: The police get a picture of a suspect from a crime scene and wan...
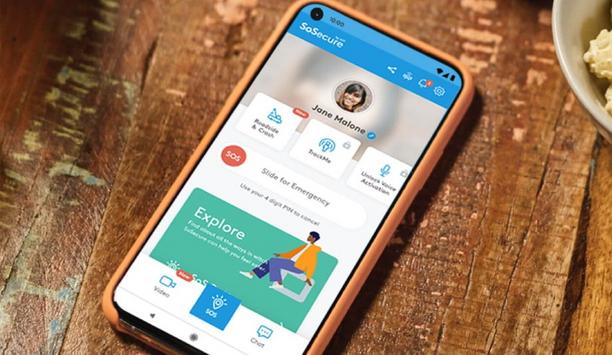
The past year has elevated consumer awareness about personal safety, from COVID-19 issues to social unrest, making safety top-of-mind and the need for personal safety solutions, even more prevalent. In addition, consumers spent more time at home, as schools closed, events were canceled and remote work increased. This prompted two major shifts that, in my opinion, most significantly opened the need for and raised the popularity of mobile safety solutions. Demand for grocery and food delivery...
Today’s organizations face numerous diverse threats to their people, places and property, sometimes simultaneously. Security leaders now know all too well how a pandemic can cripple a company’s ability to produce goods and services, or force production facilities to shut down, disrupting business continuity. For example, a category three hurricane barreling towards the Gulf of Mexico could disable the supplier’s facilities, disrupt the supply chain and put unexpected pressure o...
From analog to digital, from stand-alone to interlinked, building systems are in a state of transition. Moreover, the rate of change shows no sign of slowing, which can make it difficult to keep up to date with all the latest developments. If asked to pinpoint the single biggest driver of this revolution, one could point out the growing clamor for platform convergence. A security guard in a building doesn’t want to use different systems to check video cameras, fire alarms or if someone ha...
Today, we live in a technology-obsessed age. Whichever way you look, it’s hard to avoid the increasing number applications, products and solutions that continue to redefine the boundaries of what we previously thought possible. From autonomous vehicles and edge computing to 5G and the Internet of Things, all facets of our lives are continuing to evolve, thanks to an endless stream of differentiated innovations. In this article, we’ll be focusing on the latter of these - the Internet...
Heras was a premium partner exhibitor at this year’s International Security Expo (ISE) – and it’s fair to say that visitors couldn’t miss the stand, which was at the entrance of the Grand Hall at London’s Olympia. Heras’s Country Marketing Manager (UK) Rebecca Hughes pinpoints five things that the Heras team learned from the show and talking to visitors. 1) Physical still just as important as cyber Cyber(security) was the buzzword of the show – and the...
The ‘new normal’ was all we heard about when it came to the working model shift after the pandemic hit. Businesses worldwide adopted working from home, and then the hybrid model: a balance of remote work and office work. And according to a recent survey by 451 Research, nearly 80% of organizations surveyed said they have implemented or expanded universal work-from-home policies as a result of COVID-19, whilst 67% expect these policies to remain in place either permanently or for th...
Most consumers are enjoying the convenience brought by electronic locks. With the existence of electronic locks, people no longer need to be restricted by keys. There are a variety of unlocking methods and more convenient remote control unlocking options. Suppose, you are going on vacation, and with the presence of an electronic lock, you can easily enter your house with your babysitter, without a spare key. Of course, not only smart homes, but also some infrastructure and commercial buildings...
As the number of connected devices increases worldwide, the ways that they are being used, designed, and tested have also expanded. The rise of connected devices is demanding engineers to harness the power of the internet of things, which is expected to hit 28 billion by 2025. A comprehensive approach to device design is needed more than ever to address the challenges that this rapid growth will bring. Why engineers should be using IoT technology in product design The demand for devices desig...
Ensuring employee health and safety remains a key priority for organizations this year, especially as we see COVID-19 cases continue to rise in different areas of the world. As an ongoing challenge, COVID-19 has shifted the priorities of many organizations. In fact, “improving health and safety for employees” is the top strategic goal this year of manufacturing and logistics organizations in the U.S. and U.K., according to research conducted by Forrester on behalf of STANLEY Securit...
In the past decade, we’ve seen an unfortunate increase in gun-related incidents on school campuses, making security and policy efforts a top priority for educational facilities nationwide. While the causes for this increase are hotly debated in and around the education community, the facts remain that specific steps can be taken to mitigate risks. To tackle this issue, officials from campus stakeholders, law enforcement officials, architects, and security personnel, have met to find solut...
Video surveillance systems are producing more unstructured data than ever before. A dramatic decrease in camera costs in recent years has led many businesses to invest in comprehensive surveillance coverage, with more cameras generating more data. Plus, advances in technology mean that the newest (8K) cameras are generating approximately 800% more data than their predecessors (standard definition). Traditional entry-level solutions like network video recorders (NVRs) simply aren’t built...
Access control and management of trusted identities are the building blocks of security, safety, and site management policies for many businesses and organizations. The current pandemic has compounded this with the introduction of new policies and regulations, particularly around social distancing and contact tracing. Most organizations will have some form of legacy access control in place, ranging from the most simplistic options, such as locks and keys, to technology-based systems. The issue...
For many businesses and organizations, the term 'authentication' is synonymous with 'password' or 'multi-factor authentication (MFA)’. However, because today's business ecosystem is complex and stretches across distributed workforces with work from home, BYOD policies, and multiple cloud environments, it is very challenging to efficiently recognize and authenticate identities of people, processes, and devices throughout the enterprise using traditional methods. The problem with passwords...
Martyn’s Law (also known as ‘Protect Duty’) could forever change the landscape of event security if changes to legislation are passed. Some would argue it already has. In 2017, just as concertgoers were leaving the Manchester Arena, a terrorist detonated an improvised explosive device in a suicide attack killing 22 and injuring more than 250. The mother of one of the victims, Martyn Hett, has tirelessly campaigned for tighter security and a duty of care to be placed upon venu...
The last year revolutionized the way people work. When offices transitioned to work-from-home and worksites implemented social distancing, the security industry saw an overnight shift in what technologies our customers wanted. Now that businesses are bringing employees back to work in-person, management has broadened their focus to include healthy access in their security plans. Healthy access is a modern security concept that uses the latest technologies to blend employee and visitor health wi...
Travel and tourism are a colossus of a global industry. From backpackers to private jets, people from all backgrounds can explore the world in a variety of different ways for several different purposes. Many may associate the mention of travel with leisure – holidays, cruises, or other pastimes. However, a significant proportion of the industry is driven by travel for business-related means. According to the World Travel & Tourism Council (WTTC), business travel expenditure exceeded...
TOA Corporation (UK) Ltd discuss what changes COVID-19 has bought to the installation of VA/PA Systems and how the integration of IP has impacted on that. With a year and a half of global uncertainty, we have seen huge changes in what VA/PA systems will need to deliver in order to provide safe and robust solutions with advanced zone and directional messaging. The impact of COVID has pushed installers to re-think what end-users need long-term to manage any future changes in guidelines especiall...
Small and medium businesses of all kinds encountered unprecedented challenges during the COVID-19 pandemic. And now that businesses have reopened, they are facing new obstacles through each stage of recovery. Business owners need to look for solutions that can help them manage these issues now and beyond. Challenges ranging from lack of cash flow to staffing challenges to IT security issues for businesses with remote workers can be lessened by security and automation solutions. One of the main...
It has long been recognized that no one is safe from cyber-attacks, but some sectors face a much higher level of threat than others. Critical infrastructure sectors such as utilities, energy and industrial manufacturing are some of those that face an intense level of interest from cyber criminals and nation-state groups across the globe. The impacts of a successful attack can have detrimental consequences, for both the cyber and physical side of the business, in terms of business disruption, ec...
Amongst the many negative consequences of the pandemic is a rise in violent and abusive behavior across society. Health workers have experienced it on a regular basis. So too have police officers and public transport workers. Unfortunately, violence and abuse towards shop workers is also endemic in British society. To address this problem which, in truth, has been on the rise since long before the emergence of COVID-19, we need better deterrents. The ability to prosecute these offenses is one...
Have you ever stopped to consider the volume of new data created daily on social media? It’s staggering. Take Twitter, for instance. Approximately 500 million tweets are published every day, adding up to more than 200 billion posts per year. On Facebook, users upload an additional 350 million photos per day, and on YouTube, nearly 720,000 hours of new video content is added every 24 hours. While this overwhelming volume of information may be of no concern to your average social media user...
In daily work and life, various locks have always played the role of protecting asset safety. In different usage scenarios, the most appropriate lock must be selected to maximize benefits. In the past applications, the difficulties encountered by managers are as follows. Unlocking authority is difficult to control, unclear access records, emergency unlocking, and troublesome upgrade and installation. Through the following points, how the key-centric access management system solves such problems...
The UK Government has set out an ambitious ten-point plan, known as the green industrial revolution, with an aim “to forge ahead with eradicating its contribution to climate change by 2050.” This makes our government the first major economy to embrace such a legal obligation. Green recovery Acknowledging climate change and meeting net-zero is a demanding challenge especially for those affected by the pandemic. But the UK Government, with the launch of its aspiring strategy, is inve...
Prices and delivery times for essential components in video surveillance systems are being driven up as demand soars from other industries. Secure Logiq’s Robin Hughes explains the current state of the market. Challenges Component shortages and supply chain challenges are a hot topic in just about every industry based on semi-conductors and silicon chips right now, and security is no exception. It’s common knowledge that the global Covid lockdown caused a shutdown in the mining of...
It is a truism that in the physical security industry your workforce and your reputation are the business’s largest and most important assets. Managing your workforce with empathy to ensure happy, engaged employees can be a balancing act. However, providing flexible working practices that are still profitable for your business is achievable, and something that every security business should be aiming for. SmartTask CEO, Paul Ridden discusses the hidden benefits of an engaged workforce an...
Steven Kenny, Axis Communications, looks at the benefits of physical access control systems within smart environments, and how knowledge gaps and dated methods can inhibit adoption. Physical security is becoming more dynamic and more interconnected, as it evolves. Today’s modern access control solutions are about so much more than simply opening doors, with digitalization bringing multiple business benefits, which would simply not be possible using traditional models. Digital transformat...
Browse expert commentaries
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
Climax Mobile Lite: Advanced Personal Emergency Response System (PERS)
Hanwha Vision OnCAFE: Cloud-Based Access Control for Modern Enterprises
Delta Scientific MP100 Portable Barricade Solution