Network / IP security
Suprema, a pioneer of AI-powered security solutions, announced that BioStation 3 is expected to set a new annual global sales record by the end of this year. This represents the highest annual sales record for Suprema’s biometric devices and highlights the accelerating global demand for facial authentication solutions. Global security market Importantly, this growth reflects balanced momentum across major regions rather than a temporary spike in a single market. BioStation 3 has achieve...
IDIS has launched two new advanced PTZ cameras, providing powerful AI and NIR performance. The extended range offers a broader choice of PTZ cameras to more efficiently cover open areas, in applications including public and communal spaces, commercial offices, schools, logistics centers and warehouses, retail settings, and perimeters. The new NDAA-compliant cameras from South Korea’s largest in-country surveillance manufacturer now include the 4MP AI PTZ (LightMaster) DC-S6481HRA an...
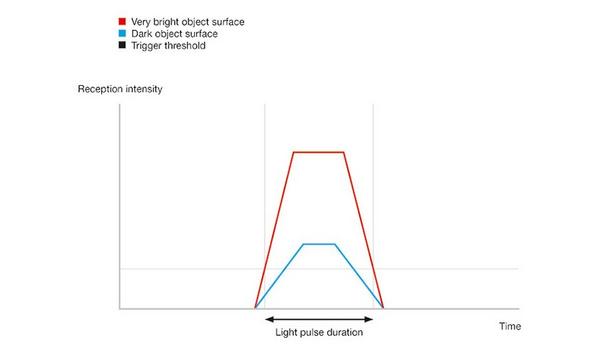
Leuze uses artificial intelligence (AI) to significantly improve the measurement accuracy of optical distance sensors for challenging industrial applications. This innovation improves measurement accuracy without the need for additional computing resources during operation. The solution is based on a neural network. Object surfaces as challenges Optical distance sensors with time-of-flight technology (TOF) offer practical benefits. The sensors enable fast, contactless measurement of large dis...
Alarm.com and Everon, LLC, a pioneering security integrator and premier provider of commercial security, video, fire, and life safety solutions, today announced a strategic partnership to deliver a unified console for Everon customers to manage integrated intrusion protection, access control, remote video monitoring, and business management solutions. The partnership reflects the growing demand for integrated commercial security platforms that can easily connect with existing infrastructure whi...
Integrated access control and security manufacturer TDSi now announces that from 1st January 2026, it will operate under the new name: TDSi by Hirsch. The change follows the global transformation of its parent company, Vitaprotech, into the Hirsch Group, unifying its security brands worldwide under one trusted name. TDSi’s integrated access control For more than 40 years, TDSi’s integrated access control solutions have been at the heart of thousands of installations&nbs...
Aetina Corporation, a pioneering provider of Edge AI solutions, has announced the launch of its next-generation MXM AI Accelerator Module series accelerated by NVIDIA RTX PRO Blackwell Embedded GPUs, which is part of its CoreEdge MXM AI Module family. This new series is accelerated by the NVIDIA Blackwell GPU platform to deliver up to 3X the AI performance uplift of its predecessor, establishing a new benchmark for advanced AI computing at the edge These modules are designed to be compact,...
News
Abnormal AI, the pioneer in AI-native human behavior security, announced it has been recognized as a Leader in the 2025 Gartner® Magic Quadrant™ for Email Security, marking the company’s second consecutive year in the Leaders Quadrant. Gartner evaluated vendors based on their Completeness of Vision and Ability to Execute. Among 14 vendors evaluated, Abnormal was placed furthest right on the Vision axis. API-based approach In the report, Gartner highlights that “the high volume of sophisticated, email-enabled social engineering attacks, combined with the difficulty in consistently quantifying true detection efficacy across the market, justifies organizations utilizing multiple vendors for comprehensive protection.” To better combat these sophisticated threats, there is growing potential in solutions that utilize behavioral AI and natural language processing to analyze user behavior and help detect anomalies. The Abnormal Behavior Platform analyzes identity, behavior, and contextual signals in order to baseline normal activity and help identify deviations indicative of malicious activity. This API-based approach is designed to enable autonomous protection against a wide range of attacks — including business email compromise, credential phishing, and account takeover — without requiring cumbersome mail routing changes or complex configurations. AI-native approach “Being named a Leader in the Gartner Magic Quadrant for the second year in a row—while maintaining the furthest placement on Vision—is an incredible milestone for us,” said Evan Reiser, chief executive officer of Abnormal AI. “We’re proud to see our AI-native approach continuing to drive innovation and impact as we build toward a future where understanding human behavior is the cornerstone of keeping people and organizations safe.” AI Phishing Coach and AI Data Analyst This recognition follows a year of exceptional growth and innovation for Abnormal AI. In 2025, Abnormal launched its first autonomous AI agents—AI Phishing Coach and AI Data Analyst—to help organizations detect, remediate, and train themselves against threats in real time. The company also achieved FedRAMP Moderate Authorization and earned the ISO/IEC 42001 AI governance certification, underscoring its commitment to both security and responsible AI. Abnormal now protects more than 25% of the Fortune 500 and continues its global expansion, recently entering new markets in Germany, Japan, and France. The year also brought strong industry and customer validation—from featuring on the CNBC Disruptor 50, to the Forbes Cloud 100, and the Fortune Cyber 60. Abnormal was also named a Gartner Peer Insights™ Customers’ Choice for Email Security Platforms in July 2025, earning a 99% “Would Recommend” rating and, in our opinion, reaffirming the trust placed in Abnormal’s AI-native approach.
DigiCert, a pioneer in intelligent trust, unveiled its 2026 Security Predictions, forecasting how AI, quantum computing, and automation will reshape global trust frameworks. The predictions highlight a pivotal shift toward AI integrity, resilience, and quantum readiness as core tenets of intelligent trust. DigiCert’s full predictions and outlook for the new year can be found at DigiCert’s blog. 1. AI Integrity Becomes the New Trust Standard: AI authenticity will overtake data confidentiality as the top enterprise trust concern. Organizations will require verifiable identity, provenance, and tracking for every model, dataset, and autonomous agent. 2. Resilience Becomes the New Compliance: Resilience will shift from an IT goal to a board-level mandate as regulations like Digital Operational Resilience Act (DORA) and new global standards tighten expectations. Organizations will be required to prove that their DNS, identity, and certificate systems can withstand disruption, with uptime and recoverability directly tied to financial and operational stability. 3. Automation Accelerates as Certificate Lifespans Shrink: With TLS certificate lifetimes reducing to 200 days as part of the phased reduction to 47 days, the effort associated with manual renewal doubles. Organizations will adopt full-stack automation to eliminate outages and create self-healing trust ecosystems. 4. Quantum Computing Puts Encryption on Notice: The first practical quantum computer capable of solving meaningful problems will emerge. Organizations beginning their initial pilots will discover interoperability hurdles as certificate and software ecosystems adapt to quantum-safe requirements. 5. Content Authenticity Moves from Principle to Policy: Governments and major platforms will begin enforcing C2PA for AI-generated and edited content. Watermarking and cryptographic provenance will become required for distribution across news, social, and commerce. 6. Federated PKI Reinvented for the Post-Chrome Era: Organizations will modernize private PKI as Chrome phases out legacy client authentication and Microsoft sunsets old CA architectures. Identity will shift toward cloud-native, automated, and passwordless trust models. 7. Email Trust Redefined: Verified Identities Take the Lead: AI-driven phishing will push enterprises to standardize on Verified Mark Certificates and strict DMARC enforcement. Verified sender identity will become the baseline expectation for secure, enterprise-grade communication. 8. Machine Identities Outnumber Humans 100:1, and PQC Becomes Mandatory: Connected devices and AI agents will surpass human identities by two orders of magnitude. PQC-ready identity frameworks will become mandatory as standards bodies embed quantum-safe algorithms into device ecosystems. Integrity across every digital interaction “Security in 2026 won’t just be about protecting systems, it will be about proving integrity across every digital interaction,” said Jason Sabin, Chief Technology Officer at DigiCert. “As AI accelerates, machine identities multiply, and quantum computing advances, intelligent trust will become the foundation that keeps businesses resilient, verifiable, and secure. The organizations that embrace automation, provenance, and quantum-safe readiness now will define the trust landscape for the next decade.”
Building on earlier research published in October 2025, Zimperium announced that its zLabs team has uncovered a significantly enhanced variant of ClayRat, an Android spyware family first detailed in the technical brief “ClayRat: A New Android Spyware Targeting Russia”. While the original ClayRat strain was able to exfiltrate SMS messages, call logs, notifications, device data, take photos, and send mass SMS or place calls, effectively allowing infected devices to become distribution hubs. The newly observed variant demonstrates a substantial escalation in functionality and stealth. The updated strain abuses both Default SMS privileges and Accessibility Services, enabling it to: Capture lock-screen credentials (PIN, password, or pattern) and automatically unlock the device. Record the screen via the MediaProjection API. Present deceptive overlays (for example, fake system-update prompts) to prevent user detection. Programmatically initiate taps — blocking the user from powering down or uninstalling the malicious app. Generate fake or interactive notifications, then intercept and exfiltrate responses. This expanded functionality enables full device takeover, making ClayRat far more dangerous than the version first reported, especially since victims may no longer detect or easily remove the malware. The updated behavior also increases the risk to corporate endpoints: compromised devices could leak corporate credentials, MFA codes, or sensitive enterprise data through hijacked SMS, notification flows, or screen captures. Reliant on phishing webpages The malware continues to leverage social engineering at scale. As before, ClayRat masquerades as legitimate, widely used applications and services, including major video and messaging platforms, as well as localised or regional services (for example, certain Russian taxi or parking apps). Distribution remains heavily reliant on phishing webpages and sideloaded APKs, including via cloud-storage platforms such as Dropbox. According to zLabs telemetry, more than 700 unique APKs tied to ClayRat have already been identified in a short time window. BYOD environments “ClayRat’s evolution shows exactly why enterprises need protection that works at the device level, not just network-based,” said Vishnu Pratapagiri, lead researcher at zLabs. “By abusing Accessibility Services and overlay tricks, this variant turns Android devices into fully compromised endpoints and conventional defenses may not be enough.” As ClayRat continues to evolve, expanding its spyware, remote-control, and lock-screen manipulation capabilities, enterprises should treat this campaign as a critical reminder: mobile devices, especially in BYOD environments, remain among the most vulnerable entry points for attackers. Zimperium continues to monitor ClayRat and share relevant indicators of compromise with industry partners.
Iris officially launches today, introducing a platform that transforms how cameras are controlled, and productions are managed. By turning virtually any PTZ camera into a software-connected, remotely controlled device, Iris eliminates the traditional constraints of camera operation, such as hardware dependencies, inconsistent control, and the lack of on-site crews. The platform removes long-standing pain points for production teams: fragmented control tools and protocols across brands, the need for constant manual adjustments, and the inherent limits of on-site equipment and staffing. Iris changes this by providing universal, browser-based control that works across camera brands and enables full production management from anywhere in the world. Traditionally manual tasks The platform's AI-powered automation handles traditionally manual tasks, like real-time subject tracking and framing, allowing operators to focus on creative decisions rather than technical adjustments. Its intuitive interface ensures that non-technical users can achieve professional results, democratising access to advanced capabilities that deliver the production quality of larger-budget operations. The impact extends far beyond individual productions. Organizations using Iris can scale their operations without proportionally increasing their costs or crew size. A single operator can manage multiple cameras across multiple locations, while remote teams collaborate in real time as if they were in the same room. This scalability opens doors to productions that were previously impractical or impossible, from small community theater livestreams to global corporate events spanning multiple time zones. PTZ camera manufacturers Through the Iris desktop application, production teams can quickly discover, link to, and control over 300 models of cameras on their local network. For those using Iris-enabled cameras, the platform is built directly into the device’s firmware, connecting instantly to the cloud without any additional hardware or complex setup. This direct-to-cloud capability debuts alongside broad support from PTZ camera manufacturers, including AIDA, BirdDog, Bolin, BZBGear, Everet, HDKATOV, Lumens, Marshall, NEOiD, Telycam, and Z CAM. Together, these integrations position Iris as the leading software standard for camera control. Iris-enabled firmware “Setup now takes minutes, not hours,” said Noah Johnson, Founder of Iris. “Our custom drivers unlock every camera feature—not just the common ones—and our intelligent framing tools make operating cameras feel natural, fast, and cinematic. And because Iris lives in the cloud, your cameras are now truly remote—you can manage, access, and control them from anywhere, anytime.” Iris is designed to ensure that no production is left behind, even if its cameras aren’t equipped with Iris-enabled firmware. With the innovative Iris desktop utility and browser-based interface, virtually any PTZ camera can be connected and controlled without hardware. This bridging software allows production teams to unlock advanced automation and PTZ control features in cameras from brands not yet natively supported, ensuring that even legacy or third-party hardware can access the platform’s capabilities, extending equipment life and maximising investment. Professional-looking livestreams The Iris platform is a reimagining of what’s possible in nearly any type of production. Houses of worship can empower volunteer teams to deliver professional-looking livestreams using automation and visual effects. Educational institutions can manage cameras across lecture halls with a centralised, remote-control room. Corporate teams can produce executive communications and all-hands meetings across multiple offices. Media producers can collaborate in real time across locations for seamless productions. With Iris, even remote interviews become effortless: ship a camera, plug it in, and instantly access the video and controls in their Iris account. Delivering exceptional experiences By removing traditional barriers to camera control and production management, Iris empowers creators to focus on what matters most: telling compelling stories and delivering exceptional experiences. Users can update any Iris-enabled camera firmware to instantly enhance their PTZ camera. The Iris platform is available at tryiris.ai for content producers to begin connecting cameras immediately. Additionally, its software is included in select camera manufacturers through simple firmware updates. The platform's flexible pricing model—which includes a free tier for individuals whose productions use one camera source—means users only pay for the size of productions they produce, making professional-grade capabilities accessible to organizations of all sizes. With plug-and-play setup and an intuitive interface, teams can begin transforming their workflows within minutes. What camera manufacturers say about Iris AIDA “From local studios to global stages, Iris gives our cameras the power to go wherever our customers do – secure, remote, and crystal-clear, without compromise.” - John Wu, Marketing at AIDA Imaging. BirdDog “At BirdDog, we’re committed to giving creators the freedom to work their way. Partnering with Iris extends that flexibility, adding powerful and intuitive way to control our cameras from anywhere, helping creators focus on what matters most - telling great stories.”- Dan Miall, CEO at BirdDog. Intuitive remote management Bolin “Bolin has always focused on technology that reduces complexity and helps users do more with less. It's about removing what they don't need. Iris builds on that by enhancing the capabilities of our cameras. With intelligent control, advanced tracking, and powerful tools in one place, it brings a new level of simplicity and capability to remote production.” - Sapan Doshi, Product Manager, Bolin. BZBGear “People want to produce broadcast-quality content with simple, flexible control. BZBGEAR PTZ cameras combined with Iris universal camera control deliver exactly that, enabling more efficient and seamless productions through intuitive remote management from anywhere in the world.” – Eugene Bocharov, CEO and President of BZBGEAR. Advanced PTZ cameras Everet Imaging "The combination of Everet cameras and the Iris platform gives users the tools to manage complex productions effortlessly. From cloud-based control to AI features, it’s a natural fit for the fast-moving, professional workflows we support.” - Michaël Hegeman, General Manager, Everet Imaging HDKATOV “At HDKATOV, we’re redefining the future of production with our latest integration of cutting-edge camera technology and the Iris platform. By combining our advanced PTZ cameras with Iris’s cloud-based control and AI features, we’re providing users with the tools to manage complex productions effortlessly. Whether in the studio or on location, this seamless integration ensures that our customers can streamline their workflows, achieving professional results with remarkable ease.” – Helen Huang, Senior Manager at HDKATOV Next-generation AI automation Lumens “Organizations worldwide, from corporate and education to government sectors, are embracing cloud-based AV workflows and supporting distributed environments. By integrating Iris directly into our PTZ cameras, we’re enabling customers as well as integrators to standardize and simplify remote-control capabilities, remove hardware and system complexity, and reduce on-site labor and setup time.” – Chester Lee, VP of Sales at Lumens USA, and Joris Nevens, General Manager at Lumens Europe Marshall "Iris solves real problems that production teams face every day. By moving camera control to the cloud and adding next-generation AI automation, we're giving Marshall customers the freedom to focus on creativity while the technology handles the technical details. Our partnership with Iris is focused on making remote production practical, affordable, and scalable for all users.” - Bernie Keach, Broadcast AV Consultant, Marshall Professional PTZ cameras NEOiD “Cloud-based workflows are transforming every aspect of video production. NEOiD is excited to work with Iris to bring this innovation to our customers, enabling them to scale their operations without the traditional constraints of hardware and location.” - Laurindo Almeida, CEO at NEOiD Telycam “By integrating Iris into our camera portfolio, we’re taking another step toward providing intelligent, future-ready solutions that elevate the user experience. This partnership represents a major leap forward in bringing cloud-based control and automation to our customers, and we believe it will redefine what’s possible in professional video production.” - Jenny Liu, Head of Sales and Marketing at Telycam Z CAM “The collaboration with Iris enhances our professional PTZ cameras' capabilities and provides users with a powerful and flexible solution for modern productions. The Z CAM P2-R1 is already known for its exceptional image quality, and with Iris integration it is now even more versatile.” – Kinson Loo, CEO of Z CAM.
Secutech, Asia’s premier security exhibition, will be held from 22 – 24 April 2026 at the Taipei Nangang Exhibition Center, Hall 1. This edition promises a robust showcase of more than 400 international exhibitors and an expected influx of over 15,000 visitors. Against the backdrop of Taiwan’s government investing USD 3 billion to accelerate its transformation into an “AI island”, this year’s focus will center on four key industry pillars across seven thematic zones prioritizing intelligent security solutions that integrate AIoT and data-driven technologies to enable proactive safety, precise management, and sustainable operations. Demand for next-generation solutions With AI playing a key role in Taiwan’s new development plan, Ms Regina Tsai, General Manager, Messe Frankfurt (HK) Ltd – Taiwan Branch stated: "Taiwan’s significant investment in AI and smart security technologies is fueling demand for next-generation solutions." "Consequently, Secutech provides a preview of Taiwan’s security future by bringing together global pioneers from the security, fire safety, disaster prevention, occupational safety, building technology, and cybersecurity sectors.” Four key industry pillars This year’s show highlights four key industry pillars, each centered around the implementation of smart security technologies across key verticals: Critical Infrastructure Protection: featuring AIoT, image recognition, sensing, and cybersecurity to enable comprehensive “predict–detect–respond–recover” capabilities, strengthening resilience across vital sectors such as energy, transportation, healthcare, and manufacturing. Smart Fire Safety & Emergency Response: Showcasing AI visual detection, thermal sensing, wireless monitoring, and smart fire control systems to build intelligent city-wide safety networks for improved disaster and rescue management. Smart Industrial Safety & ESG Protection: Centered on smart tech, digitalization, and sustainability, with demonstrations of AI wearables, gas detectors, and cloud safety management platforms that assist industries in achieving zero accident, zero downtime, and zero carbon targets. Sustainable Smart Building & ESG Applications: Focusing on energy efficiency, low carbon footprint, health, and safety through innovations like BIM/FM/GIS systems, AIoT energy control, and indoor air quality monitoring, supporting the construction industry’s transition to net-zero and smart living environments. Convergence of IT and OT systems The solutions and products pertaining to these pillars will be organized thematically into seven zones and pavilions – Critical Infrastructure Security, Smart Surveillance, AI Innovation, Smart Living & Building, Smart Industrial Safety, Fire & Disaster Rescue, and the AIoT Cybersecurity Pavilion – each designed to provide visitors with a hands-on look at cutting-edge, cross-sector security innovations from around the world. Secutech 2026 will also spotlight Cybersecurity & AI integration, addressing the convergence of IT and OT systems and emphasizing AI threat detection, Zero Trust Architecture, and supply chain security. These will align with international standards such as ISA/IEC 62443 to meet evolving local and global security demands. Key industry players and system integrators Ms Tsai commented: “For key industry players and system integrators in Taiwan, this event serves as a vital one-stop platform to discover cutting-edge products, gain fresh industry insights, and foster international partnerships. By creating unparalleled opportunities to enhance visibility and maximize return on investment across the entire value chain, Secutech continues to propel the industry towards a safer, smarter future for Taiwan and beyond.” To complement the exhibition, the Asia Disaster Prevention Summit will be held concurrently. This summit assembles experts to share insights on earthquake case studies, cross-border collaboration, and innovative approaches to strengthening disaster resilience in Taiwan and the wider Asia-Pacific region. The fair also takes place alongside the concurrent Fire & Safety and SMAbuilding events. Secutech is organized by Messe Frankfurt (HK) Ltd – Taiwan Branch and is part of a global network of Safety, Security & Fire trade fairs. The next edition will be held from 22 to 24 April 2026.
Hikvision announced recently that it has achieved the ISO 37301:2021 Compliance Management System certification from SGS, the world's renowned testing, inspection, and certification company. This milestone, highlighted in the certification ceremony at the Shaping Intelligence Hikvision Commercial Summit 2025 in Bangkok, Thailand, affirms that Hikvision’s robust compliance framework aligns with global standards, supporting the company's resilient growth worldwide. A Testament to Compliance Achievement ISO 37301 serves as the authoritative international benchmark for compliance management systems. It provides guidelines for creating and sustaining an effective and responsible compliance management system within organizations. For Hikvision, being awarded the ISO 37301 certification by SGS is a testament to its proactive measures in establishing and enhancing its compliance management system. It underscores the company’s strong alignment with international standards and industry best practices, highlighting its steadfast commitment to ethical business operations and enduring trust. Continuous Efforts for Robust Compliance This certification is more than a recognition. It is the outcome of Hikvision’s continuous governance building progress. Driven by the principle of “upholding integrity and compliance to achieve sustainable development,” Hikvision has established a governance management framework that connects the Board of Directors, management levels, every department and employee, along with its valued partners. This framework ensures accountability and standardized operations, while remaining dynamic and resilient to the evolving global landscape. With the guidance of strategic philosophy and framework, Hikvision turns compliance spirits into real actions, strictly adhering to business ethics and enforcing compliance practices. By adopting global best practices, the company effectively embeds compliance requirements — ranging from cybersecurity, trade compliance, data protection, human rights protection, and so on — into the full lifecycle of R&D, manufacturing, sales, and daily operations. End-to-end approach This end-to-end approach transforms Hikvision’s compliance management into a proactive value driver, fueling high-quality, and sustainable growth. During the certification ceremony, Mr. Terachai Yaoprukchai, SGS Thailand Sustainability Business Manager, validated this effort by stating, “Hikvision has demonstrated industry-leading maturity and robustness in its compliance management system by deeply embedding compliance in its operations and strengthening globally adaptable risk controls.” Advance the Future of Responsible Operations The awarding of ISO 37301 certification coincides with Hikvision's 2025 Compliance Culture Month. Themed “Integrity in Action, Value in Union,” the event underscores the company's focus on transforming compliance principles into shared value and collective strength. As Ms. Gao Aiping, General Manager of Hikvision’s Compliance Department, remarked: “With a long-term commitment, we will continue to invest in our global compliance framework and enhance connection with all our stakeholders. By leveraging it as a strategic value engine, we are bolstering the company's resilience and paving the way for sustainable growth.” Echoing this sentiment, Hikvision will continue to collaborate closely with its partners and stakeholders to advance compliance practices jointly, fostering a stable and responsible business environment that promotes sustainable growth for our shared world.


Expert commentary
Artificial intelligence (AI) creates efficiencies throughout various industries, from managing teams to operating businesses. Key outcomes include faster investigations, fewer false alerts, automated operational checks, and quicker support experiences. These advancements free up valuable time for users, allowing them to focus on high-impact priorities that drive greater ROI. When it comes to surveillance, AI is most visibly powering a new generation of vision language-powered video analytics, a technology that has adapted systems meant solely for security into solutions capable of identifying actionable insights and streamlining workflows. Fast-moving AI landscape When choosing a surveillance system powered by AI, it’s vital to select an open platform. To stay ahead in the fast-moving AI landscape, it’s more important than ever for businesses to choose an open platform that empowers them to adapt and innovate. In contrast to closed systems, an open platform enables flexible integration with existing security and business systems. This offers businesses a greater return on their initial security investment while still providing an adaptable model built for the innovations of tomorrow. Below, we’ll look at the benefits provided by an open system in the age of AI, and how it can give you the strongest foundation to meet your goals. Supercharge Your Existing System An open platform also gives businesses the flexibility to scale security systems and add devices as needs evolve Having to invest in entirely new security infrastructure while simultaneously deploying AI technology presents a variety of problems and risks for businesses. Your team will have to manage both rollouts for your teams at the same time, driving up higher costs and more issues with training. By selecting an open platform, businesses can apply their newfound AI capabilities to existing cameras that weren’t built with analytics originally. Instead of having to completely replace your entire system, which can involve multiple weeks, months, or years of ripping out cabling and video security infrastructure, businesses can leverage analytics on the server itself to save valuable time while reducing deployment costs. This gives cameras a new lifespan by unlocking all the advantages video analytics brings, including basics like person and vehicle detection and line crossing analytics, to provide additional power to system alerts and visual search capabilities. An open platform also gives businesses the flexibility to scale security systems and add devices as needs evolve. This approach enables organizations to upgrade at a more optimal pace, bringing in new devices when it best fits the budget and operational priorities. Choose the Solution That Works Best for You With an open platform, businesses have the ability to find and select the AI solutions that work best for them. This gives organizations greater flexibility when implementing a video analytics solution. AI-enabled devices can be added in the timeframe that works best for your business or according to your needs. For example, if a business needs a camera with edge-based slip-and-fall analytics for just one area of their facilities, an open platform enables integration with the best solution for that specific need without having to replace the entire system. This approach ensures you get maximum value from your investment while gaining the targeted benefits of video analytics. They can also bring onboard several analytic-enabled cameras while keeping the majority of their existing system, test different analytics offerings, or slowly phase out their old system. This is all possible thanks to the open platform which gives businesses the freedom of choice to find the best solutions for their business needs. Stay Ready for What’s Next AI is a refined, intelligent technological triumph, and today is the lower level of skill it will ever produce Finally, an open platform is inherently ready for future innovations, allowing businesses to stay ready for what’s next. AI is an advanced, intelligent technological achievement, and today is the lowest level of performance it will ever produce. The system investment you make today will need to be capable of taking advantage of the unknown but, undoubtedly, compelling features in five years' time. As new technologies continue to emerge, businesses can expand their ecosystem through an open platform, allowing them to integrate the applications that matter most to their business without being constrained by a single proprietary solution. This reduces the risk businesses may feel by committing to a single platform. Instead, they can leverage existing technology, including hardware, lowering the overall cost up front and providing an opportunity to adopt and integrate future solutions down the road. This also helps keep your surveillance current and up to date while mitigating timeline issues with the rollout of new AI features and helping you get the most out of your investment. It also provides a way to test new solutions and continue optimizing your system for your business. Combining AI and an Open Platform The open video platform is one of the best ways to ensure your business is getting the most out of the exciting advancements in AI. With as many data points as there are provided by a modern security system, having a way to bring that information together in an integrated place is key. Thanks to AI, that information can be parsed more efficiently for proactive insights into potential optimizations and visibility during critical events. When finding the right video surveillance system for your business, be sure to select one that is not only AI-capable but also open. This will provide your organization with all of the benefits discussed above, including: Integrated Solutions: Thanks to the open platform, your business can still leverage existing hardware while using advanced video analytics on the recorder itself. Freedom of Choice: There’s no need to choose one system when it isn’t the best fit for your company. The open platform offers freedom of choice to leverage the best AI-powered technologies for your work. Futureproofed: As new innovations arise, you’ll be able to quickly integrate these cutting-edge technologies into your existing system without having to continually reinvent your system architecture.
It is the time of year when city centers transform, as outdoor Christmas markets fill town squares and high streets. An estimated 6,000 markets will open across Europe during the festive season, with some of the largest — including Nuremberg’s Christkindlesmarkt, London’s Hyde Park Winter Wonderland and Craiova in Romania — welcoming millions of visitors. Sadly, these popular events have in recent years been the subject of attacks, most notably Berlin in 2016 and the tragedy in Magdeburg last December, where a vehicle was driven into the crowd. Incidents such as these have encouraged governments, including the UK with the introduction of Martyn’s Law, to strengthen planning and preparation for large-scale public events. Digital twins: A new standard for event preparation Drone-based photogrammetry captures streets, squares and surrounding buildings with exceptional detail One of the most effective tools for preparing and safeguarding public spaces today is the creation of a photorealistic digital twin — a highly accurate 3D virtual model of the intended market area. Drone-based photogrammetry captures streets, squares and surrounding buildings with exceptional detail, enabling planners to work within a realistic and immersive environment long before any physical structures are installed. Digital twin design tools can ingest these datasets and visualize them using advanced technologies, creating a lifelike representation of even the most complex outdoor scenes. Designing the market in 3D before construction begins Once the digital twin is created, event organizers, city authorities and security specialists can begin shaping the market virtually. Temporary stalls, lighting installations, stages, decorative structures, back-office units, Christmas trees, ice rinks and other festive features can be positioned directly within the digital model. It‘s also possible to place static representations of people or larger groups to approximate crowd density and understand how occupied space will influence visibility, accessibility and the overall perception of the environment. This ability to design and refine the market layout before construction allows planners to test multiple variations, understand how structures interact and ensure that the environment remains safe and manageable throughout the event. Virtual camera planning, coverage assessment and analysis Digital twins also provide a robust foundation for planning the deployment of visual-monitoring systems Digital twins also provide a robust foundation for planning the deployment of visual-monitoring systems. Cameras can be placed directly into the 3D environment, allowing planners to immediately see how temporary structures, decorations or pedestrian flows will influence the field of view. Blind spots become apparent, alternative camera heights or angles can be explored and strategic decisions about additional mounting points or temporary towers can be made with confidence. For each planned camera, the expected resolution per meter or per foot is visualized directly inside the digital twin. Instead of relying on theoretical charts or static design tables, planners can instantly see whether a particular camera position will deliver the clarity required for the intended purpose, whether it is early detection of movement, recognition of behavior patterns or full identification of individuals. Real-time visual feedback This real-time visual feedback makes the entire planning process more precise, transparent and efficient. These evaluations can be carried out within the realistic daytime environment captured by the digital twin. Planners can also prepare alternative scene variants — for example, dedicated night-time versions or layouts reflecting festive lighting — to understand how visibility and coverage may change throughout the event. Even without full weather simulation, this approach allows teams to anticipate typical operational challenges and refine the monitoring concept well before the first stall is erected. Testing safety and security scenarios Perhaps the greatest advantage of working with a digital twin is the ability to explore the environment from multiple perspectives before the event begins. Although the scene itself is static, planners can move through it using a virtual intruder to understand how the market will appear from ground level and to identify potential vulnerabilities that may not be obvious from a top-down view. This makes it possible to assess where hostile-vehicle barriers should be positioned, how narrow passages might feel when occupied, or where visibility may be reduced due to temporary structures or decorations. The static digital twin also provides a clear way to evaluate emergency access lanes, determine suitable locations for help points or medical posts and plan the general layout of security patrol routes. By navigating the scene freely and observing it from different perspectives, teams can refine the design and address potential blind spots long before construction begins. A unified environment with LiDAR The created digital twin also becomes the primary visualization environment for LiDAR during live operations Beyond planning, the created digital twin also becomes the primary visualization environment for LiDAR during live operations. Operators can interact with this 3D map directly and with a single click on any location, all PTZ cameras capable of viewing that point automatically reposition to it. This provides an unmatched navigation interface for real-time camera control, making situational awareness significantly faster and more intuitive. LiDAR then works seamlessly with a video management system, which controls all camera streams, recordings and video evidence, creating a tightly integrated monitoring workflow. Supporting real-world operations Once the market opens, the digital twin continues to serve as a valuable operational resource. If layouts change during the event — for example, because of additional attractions, adjusted walkways or altered security checkpoints — these modifications can be quickly modelled and evaluated before implementation. When the festive season concludes, the same model can be repurposed for future events, long-term city planning or other public-space deployments. A safer and smarter festive season Christmas markets are vibrant, high-profile and densely populated environments, making them attractive targets for those seeking to cause disruption. By combining detailed photogrammetry, advanced 3D visualization, and rigorous spatial evaluation, cities can create safer, better-prepared, and more resilient festive settings. With tools such as digital twins and LiDAR, authorities can plan more effectively, anticipate risks earlier and ensure that every stall, pathway and vantage point contributes to a joyful — and secure — holiday season.
The terrorism threat in the UK is very real. In fact, since July 2019, the threat level has never dropped lower than “substantial” or “severe.” To ensure preparedness across public places and events, the UK government has introduced the new Terrorism (Protection of Premises) Act 2025, more commonly known as Martyn’s Law in memory of Martyn Hett, a victim of the 2017 Manchester Arena bombing. Overarching aim The new legislation requires operators of public spaces and events to immediately assess and improve their readiness to respond to a terrorist attack. The overarching aim: being better prepared, protected and ready to respond should an attack occur. Everything from busy shopping centers to large stadiums must comply with Martyn’s Law by April 2027, and the Security Industry Authority (SIA) is charged with enforcing the rules. Upgraded security systems The smaller venues and events are only required to enforce low-cost solutions with no physical measures There are different rules depending on the capacity of public premises or the event, ranging from a standard-duty premises (200 – 799 people, including staff) to an enhanced-duty premise (over 800). The smaller venues and events are only required to implement low-cost solutions with no physical measures. Enhanced environments, however, must provide monitoring in and around the facility and document public protection measures. Many organizations will likely invest in upgraded security systems. However, effective responses depend not only on hardware but also on situational awareness and training, helping staff identify potential threats and respond effectively under pressure. Physical security information management systems Terror-related attacks are rare and unpredictable, and the most experienced personnel are not always on shift when something does occur. Even if they are, the most seasoned security professionals can’t ensure every decision they make is the right one. One solution gaining attention is physical security information management (PSIM) systems, which integrate siloed security tools — such as CCTV, access control, and fire sensors — into a unified platform. PSIMs enable rapid information processing, automated workflows and coordinated responses to incidents, whether routine or critical. Use PSIMs to handle emergencies PSIM systems have been around for many years and have been embraced by large airports and mass transit organizations PSIM systems have been around for many years and have been embraced by large airports, mass transit organizations and critical infrastructure companies. However, these systems are ideally suited to any larger-scale environment, such as those classified as an enhanced-duty premise by Martyn’s Law. For example, airports use PSIMs to handle emergencies, locate missing persons or assess potential threats like unattended luggage. Similarly, PSIMs can improve situational awareness for stadiums, shopping centers and event venues, aiding crowd management, emergency evacuations and collaboration with police or emergency services. External stakeholder intervention Should an incident require external stakeholder intervention, the PSIM becomes a mission-critical collaboration tool, enabling real-time information (including video footage) to be shared with decision-makers, emergency control rooms and first responders en route to the scene. This ensures they arrive with the appropriate resources and can deploy faster to the right places. PSIM systems also facilitate post-incident analysis, helping organizations improve protocols, demonstrate compliance and fulfill their duty of care. Impacted by terror-related tragedies Martyn’s Law aims to eliminate the complacent mindset of “it won’t happen here” when assessing the risks associated with public gatherings. Communities impacted by terror-related tragedies serve as a stark reminder that such incidents can and do occur. Within the security sector, it is crucial to promote discussions on how new approaches, technologies, and training can enhance preparedness. Equally important is the responsibility to raise awareness about Martyn’s Law and its role in fostering safer public spaces.
Security beat
Drones are poised to fill long-standing gaps in physical security. Fixed cameras leave blind spots, and human guards cannot quickly cover large or complex properties during high-risk moments. Drones fill the gaps, providing a missing mobile layer, offering unmatched speed, broad aerial visibility, and proactive coverage that elevates security from reactive to truly responsive and deterrent. As an added element in security systems, drones complement fixed cameras, access control, and license plate recognition (LPR) systems by serving as dynamic, rapid-response assets that reach areas other technologies cannot. Integrated with existing alarms and sensors, drones can auto-launch on triggers to deliver near-instant, real-time aerial video for accurate threat verification, giving security teams critical information before taking action. Drones as first responders Drones as first responders (DFR) are a new tool in Flock’s suite of security technologies “Drones are a natural fit for physical security because they provide teams with fast, flexible visibility that fixed cameras and human patrols cannot always deliver, especially on large properties,” says Keith Kauffman, Senior Director of DFR Strategy at Flock Safety. Drones as first responders (DFR) are a new tool in Flock’s suite of security technologies, which includes LPR, video surveillance, and gunshot detection systems. “Drones act as a force multiplier, improving coverage without increasing head count,” says Kauffman. “Scaling is easy with the ability for one pilot to control multiple drones stationed at multiple locations.” Drones as a force multiplier Drones reduce manpower needs by offering wide-area coverage that would normally require several guards or patrol vehicles. Drones boost security team productivity and safety by automating the most dangerous and tedious tasks, such as alarm verification. Acting as a first responder, a drone can clear a significant portion of false alarms, allowing human guards to concentrate on high-priority roles, complex issues, or confirmed intrusions with real-time aerial intelligence. This improves personnel deployment and cuts down workload, risk, and costly overtime. Drones also significantly improve efficiency and safety for security personnel, says Kauffman. A drone system delivers real-time aerial intelligence in seconds, enabling guards to respond wisely and safely. Initial threat verification Some drone systems' yearly costs are similar to a single mid-level guard's salary Some drone systems' yearly costs are similar to a single mid-level guard's salary, but they can cover up to 38 square miles. This investment provides ROI by reducing large-scale losses and allowing human guards to focus on high-touch roles, while the drone handles initial threat verification. Flock Safety entered the drone space after acquiring Aerodome DFR in October 2024, with their private-sector drone as automated security (DAS) system rolling out in Q3 2025. And because the drones plug directly into FlockOS and work alongside other tools like license plate recognition (LPR) and gunshot detection, they can launch automatically on alerts, creating a smarter, faster response workflow. Immediate intelligence to combat false alarms Drones fundamentally change false alarm management by providing security teams with immediate, real-time aerial intelligence. When an alarm triggers, the drone can be dispatched to the exact location in seconds, allowing operators to verify instantly the threat's legitimacy via a live HD or thermal video feed. This capability enables staff to safely clear or ignore false alarms remotely, preventing guards from wasting time and resources on unnecessary, lengthy, or potentially dangerous physical checks. This process can significantly reduce alarm fatigue and allow personnel to reallocate their time to genuine security threats. Emerging drone use cases enhance security operations Emerging drone use cases enhance security operations by integrating with existing systems and enabling novel applications. One key area is Post-Storm Damage Assessment, where drones provide rapid, safe aerial visuals of expansive sites, documenting damage for insurance claims far faster than ground inspections. Another area is Ecosystem Integration via platforms such as FlockOS, where the drone automatically launches in response to alerts from other security sensors (LPR, gunshot detection). This creates a powerful, automated workflow that unifies responses, enabling quicker incident interruption, better evidence capture, and a proactive security posture without increasing the number of human patrol staff. Evolving regulations expanding drone usage Evolving FAA regulations and corporate airspace policies impact the usage of drones Evolving Federal Aviation Administration (FAA) regulations and corporate airspace policies impact the usage of drones. Today, operating drones beyond the visual line of sight (BVLOS), at night, and over-people/roadway operations requires special FAA waivers. However, the trend — Remote ID, expanded FAA Part 107 allowances, and growing BVLOS exemptions proven in drones as first responders (DFR) — reduces overhead and allows more automation. Combined with enterprise standard operating procedures (SOPs), geofencing, and data governance, drone adopters can standardize flights, minimize risk, and integrate with other technologies. “In practice, that means automated dock-based dispatch on verified alerts, scheduled perimeter sweeps, and incident-to-incident coverage without on-site pilots,” says Kauffman. “The results are faster detection-to-dispatch, stronger evidentiary chains, and lower costs per incident — unlocking 24/7 remote operations across campuses, logistics, and sites.” Winning Over Public Acceptance Public perception plays an important role in how communities embrace drone technology, which is why transparency and clear policy are essential. When employees and community members understand the drone’s purpose — responding to alarms, patrolling after hours, and deterring crime — they tend to view it much as they do security cameras or access control: a safety tool, not surveillance. Flock’s system is event-driven, privacy-minded, and used only by authorized personnel, and every flight is logged, documented, and fully audit-traceable for accountability. “With clear communication and responsible use, drones become a reassuring layer of protection rather than a cause for concern,” says Kauffman. Drones are extremely safe, actually reducing human risk by acting as a first responder to scout ahead of personnel. They come with layers of protection, such as geofencing, obstacle avoidance, precision landing, autonomous deconfliction with aircraft, and automated safety modes. Smartest approach For security teams considering adding drones, the smartest approach is to choose a system built specifically for 24/7 security operations. That usually means the drone provider handles FAA paperwork, writes clear procedures, develops sound policy, and trains customers’ staff so everything runs smoothly. “With the right partner, drones become a safe, compliant, and incredibly helpful part of your security toolkit,” says Kauffman. Flock ramps up drone production Flock Safety’s immediate focus is ramping production of its U.S.-designed and assembled Flock Alpha hardware, which is already NDAA-compliant and built to meet the growing demand for American-made drone solutions. At the same time, the next six to 12 months will center on releasing key software updates, such as automated scheduled patrols. Together, increased hardware production and these software advancements will move the DAS product line toward full capability and broader commercial availability. Flock DAS Flock DAS essentially provides a guard’s vantage point from above, with the ability to instantly fly to any corner of a property. “And it doesn’t sleep on duty or call in sick,” says Kauffman. “Picture your traditional security measures: cameras are your static sentries; guards are your roaming patrollers. Now add Flock DAS: it’s your mobile, flying camera that can respond anywhere, anytime.” Just as a dispatcher coordinates police calls, Flock DAS serves as an aerial dispatcher for the security team, triaging alerts and providing eyes on the scene before anyone sets foot into potential danger. It gives the security team immediate, property-wide awareness so they can make safer, more informed decisions during any incident.
There was high-level energy at GSX 2025, befitting an industry undergoing massive change. Artificial intelligence (AI) was everywhere, but not so much in the booth signage. Rather, AI has made its way beyond marketing claims and solidly into the core of the products themselves. There were hundreds of examples of how AI is changing how security systems operate, all for the better. Clearly on display at GSX 2025 was an industry in the midst of metamorphosis. Deep integration of AI My conversations with companies across the security ecosystem revealed an industry heavily focused on leveraging advanced technologies like AI and the cloud to address increasingly complex global and localized threats. Several key themes emerged at the Global Security Exchange (GSX), sponsored by ASIS International, held Sept. 29–Oct. 1 at the Ernest N. Morial Convention Center in New Orleans, La. Themes I heard repeated throughout the show floor included deep integration of AI, the ongoing shift toward cloud-based and hybrid architectures, and a sharp focus on modernizing security systems to meet current challenges. AI and intelligent automation transform security The use of GenAI is moving beyond simple search functions into real-time decision support Companies are integrating AI and intelligent technologies to enhance analytics, streamline incident response, and improve internal efficiency. The use of Generative AI (GenAI) is moving beyond simple search functions into real-time decision support. For example, Bosch Video Systems introduced a "second tier" to its video analytics capabilities by combining highly sensitive edge detection with GenAI models in the cloud. For example, in visual gun detection, edge analytics might flag a potential gun (yellow), but the cloud-based GenAI then quickly reviews and confirms the threat (red), helping to filter out false alarms. Bosch is also using GenAI for more open-ended searches, such as a "Where's Waldo" application demonstrated at their booth. GenAI-powered system Eagle Eye Networks says they are focused on helping integrators "organize the AI chaos” through their cloud-based video platform. Their precision person and vehicle detection capabilities work across multiple cameras. Motorola Solutions introduced Inform, an AI-assisted incident response solution designed to bring clarity to the "noise" and help security teams respond to complex threats. They also offer Avigilon Visual Alerts, an on-prem GenAI-powered system that expands the natural language interface. AI internally to improve processes The Body Workforce Mini protects frontline workers and businesses "amid rising violence and theft." The Axon Body Workforce Mini, a small “computer with a lens” for non-police applications, is AI-capable and can perform real-time translations, automated report writing, and summarization, and can even act as a personal assistant by incorporating company policies. All those functions are built into a lightweight body-worn camera designed to safeguard frontline workers in retail and healthcare verticals. The Body Workforce Mini protects frontline workers and businesses "amid rising violence and theft." Beyond products, integration company Everon is using AI internally to improve processes, such as handling commoditized tasks, which they expect will result in better customer satisfaction. Everon wants to be known as a premier service provider and will be introducing new services in the video realm. AI-powered search and continuous system upgrades Genetec prefers the term Intelligent Automation (IA), instead of AI, to describe its empathetic interface, which can "know" what additional information a security professional needs when they click on an image, for example. Genetec says the advantages of the cloud include AI-powered search and continuous system upgrades. Their Security Center SaaS has had a fast and successful launch. It enables cloud-based systems with local storage. Genetec also highlighted the Cloudlink 210, a cloud-managed appliance designed to unify physical security operations that can be simply plugged in without involving IT staff. They call it a “headless appliance.” Cloud migration and the push for hybrid systems Hanwha debuted OnCAFE (Cloud Access for Everyone), a new cloud-based access control product The industry continues its strategic march toward the cloud, often through hybrid applications that blend on-prem strength with cloud flexibility. Acre's access control is described as "cloud-first technology," and they continue to focus on cloud solutions, incorporating AI. To help customers transition, they offer the "Bridge," a migration tool that allows systems to communicate throughout the move. At the same time, they are continuing to develop and enhance their core on-prem products – DNA Fusion and AccessIt!. Adding access control to supplement their video product line, Hanwha debuted OnCAFE (Cloud Access for Everyone), a new cloud-based access control product. The goal is to provide “access control that is easy;” It works alongside their OnCloud direct-to-cloud VMS as a Service platform. Future of video management The future of video management is increasingly hybrid. Milestone recently completed a three-year process of updating XProtect and building for the future of hybrid applications. At GSX, they showcased how their XProtect Evidence Manager seeks to "democratize evidence management" by collecting video, cell phone data, notes, and other metadata related to a case for easy sharing and prosecution. Also, Milestone’s “app center” enables additional features to enhance XProtect without involving integration. Milestone is also focusing on "Metadata Ingest," which collects and aggregates data from various manufacturers (including Genetec, Motorola, and Exacq) for use by AI. Strategic modernization and open integration Convergint and Genetec collaborated on a "2026 Technology Modernization Outlook" white paper A key theme for the future is the shift toward open systems and strategic modernization, enabling security professionals to better utilize new technology. Convergint and Genetec collaborated on a "2026 Technology Modernization Outlook" white paper, arguing that dealers and end-users need to think more strategically when buying technology. They predict that "2026 will be the year of modernization," with tangible results including unified intelligence, flexible deployment, and lower total cost of ownership. The call for open standards and architecture was also strong. What AI needs from open systems Johnson Controls noted that cloud, AI, and open standards are its three big focus areas. Their C-CURE IQ 3.10 is gaining adoption as it unifies access and video. OpenEye is seeking to address the "AI disruption anxiety" in the industry, focusing on what AI needs from open systems. The emphasis is on the value of a Model Context Protocol (MCP), an open standard and framework to enable AI systems to integrate and share data with external tools and sources. Addressing shifting global and local threats Allied Universal's "World Security Report 2025" highlights a risen focus on executive protection Companies unveiled solutions targeted at new security concerns, particularly the rising threat of violence, theft, and misinformation. Allied Universal's "World Security Report 2025" highlights an increased focus on executive protection and cites the rise of misinformation and disinformation as the number two threat. They noted that macro trends around instability and the political and social environment are driving security threats globally. To combat physical threats, Shooter Detection Systems introduced a new outdoor sensor, which is now generally available after a favorable feedback period that included an apprehension in one municipality. The company notes the unique challenge of developing technology for a "non-cooperative" threat like a person with a gun, in contrast to most security technologies that are "cooperative" and depend on user compliance. Implementation of integrated security Flock Safety is expanding its focus beyond license plate readers into solutions for retail, with a new initiative to automate and streamline investigative processes, which are often manual. The company also showcased "drones as automated security guards," which can be deployed within 90 seconds to provide "eyes" on a site and enhance safety. The system works on its own network and is firewalled away from the city system A tour of the City of New Orleans' Real Time Crime Center (RTCC), hosted by Axis Communications, demonstrated a mature implementation of integrated security. The RTCC uses Axis cameras, Genetec VMS, and is tied to a Motorola Solutions Command Center to enhance efficiency and effectiveness, operating independently of the police department. They measure success in terms of valuable hours saved in an investigation or even when an event is happening. The system works on its own network and is firewalled away from the city system. Rapidly changing industry on display The GSX 2025 highlights an industry that is moving toward more intelligent and integrated solutions. The investment in AI is shifting security from reactive monitoring to proactive, automated assistance. Throughout the show floor, the continued embrace of hybrid cloud architectures, coupled with an emphasis on open standards and modernization roadmaps, suggests a security ecosystem built for agility and future growth. These trends, and the GSX show itself, collectively underscore the industry's commitment to delivering scalable, next-generation solutions for a changing threat landscape.
Multiple technology trends are transforming the physical access control market. There is a fundamental shift away from physical cards and keys toward digital identities — mobile credentials, digital wallets, biometrics, and cloud-native access platforms. These next generation access solutions are radically reshaping how buildings operate, protect staff, and perform functionally. At the same time, AI and analytics solutions are being layered onto these physical access control systems to support predictive threat detection and behavioral insights. Access data itself is becoming an asset for sustainability, space optimization, and smart building initiatives. Risk, impact operations and experience The annual HID Global Security and Identity Trends Report highlights these and other issues The annual HID Global Security and Identity Trends Report highlights these and other issues. The survey cites improving user convenience as a priority for nearly half of organizations, while 41% are focused on simplifying administration, and 28% struggle with system integration. These are not theoretical challenges, they are day‑to‑day friction points that add cost, increase risk, impact operations and experience, and, of course, must be addressed. HID Global’s commercial focus HID Global’s commercial focus is to help organizations digitize their access control — with mobile identities, biometrics, and cloud platforms — and then to use the data to deliver more value. “We are turning access control from an operational cost into a software-driven asset that improves efficiency, supports Environmental, Social, and Governance (ESG) goals and even creates new revenue opportunities,” says Steven Commander, HID Global’s Head of Consultant Relations. The impact of digital transformation Digital transformation is the method of moving access control from hardware and physical credentials Digital transformation is in the process of moving access control from hardware and physical credentials to a software-driven, integrated experience. The transformation strengthens security while also improving user convenience — transforming the “pavement to the desk” journey. HID enables this shift through mobile credentials, biometrics, cloud-native platforms, and solutions that allow third-party applications to run on door hardware. “This helps customers turn access data into operational and commercial outcomes, while also improving the overall user experience,” says Commander. Digital transformation in access control is not focused on chasing the latest trends. Rather, transformation is about turning software, data and integration into outcomes that matter to customers, says HID. “Security becomes stronger and more adaptive,” says Commander. “Operations become simpler and more cost‑effective. Experiences become seamless and consistent. Sustainability moves from ambition to action. And the financial case becomes clearer as efficiencies are banked and new value streams emerge.” The challenge of futureproofing with long lifecycles Given that physical security technologies will be in place for 15 to 20 years, it is important to plan for how systems can evolve over time. Considering how rapidly security threats, compliance standards, and user expectations change, 15 to 20 years is a long time. The decisions made at the beginning of a system’s lifecycle can either limit flexibility later (which will be costly) or enable long-term adaptability. Support for open standards such as Open Supervised Device Protocol (OSDP) is therefore important Choosing products and platforms that are open, interoperable, and designed for updates can enable future-proof projects. Support for open standards such as Open Supervised Device Protocol (OSDP) is therefore important. In addition, systems built on open controller platforms — such as Mercury — enable organizations to switch software providers or expand functionality without replacing core door hardware. Architectural openness is key to system lifecycles and maximizing the return on investment (ROI) from a chosen solution. Digital credentials and mobile access Flexibility and upgradeability should also be top of mind when it comes to endpoints like access control readers. While RFID cards are still commonplace, there is a clear trend toward digital credentials and mobile access. Readers that support both allow organizations to transition at their own pace, without committing to a full system overhaul. A long system lifecycle does not mean technology should remain static. Security, particularly cybersecurity, demands more frequent updates. Technologies that support firmware upgrades in the field extend the value of a deployment while helping organizations keep pace with emerging threats. In that sense, lifecycle thinking is not just about longevity — it’s about maintaining resilience and readiness over time. Applying biometrics and mobile identities Biometrics is becoming mainstream as a credential alternative, strengthening security without adding friction Biometrics is becoming mainstream as a credential alternative, strengthening security without adding friction. Many organizations are now deploying biometrics to support fast, seamless access journeys, with adoption already around 39% in access control according to HID’s recent research. In addition, 80% of organizations surveyed expect to deploy mobile identities within the next five years. Full technology integration enables tap‑to‑access without opening an app; the user journey becomes faster, safer, and more convenient. “It is where the industry is headed and we are at the vanguard of this,” says Commander. Ongoing challenge of cybersecurity At HID Global, cybersecurity is embedded into everything, from corporate processes and development practices to the solutions they bring to market. “Our approach ensures that customers can strengthen their overall security posture, not only by deploying secure products but by benefitting from HID’s commitment to the highest industry standards,” says Commander. HID holds multiple globally recognized certifications, including ISO 27001, ISO 14298, SOC Type 2, and CSA STAR, which demonstrate their robust information security and cloud security practices. In addition, HID’s SEOS® secure chipset is independently SEAL-certified, providing one of the most advanced levels of protection available on the market today. “Ultimately, this means organizations are not just purchasing isolated secure products; they are implementing solutions developed and delivered within a comprehensive, cybersecure framework,” says Commander. “When deployed according to best practices, HID solutions enable customers to achieve the highest levels of resilience against evolving physical and cyber threats.” Developing green and sustainable solutions A huge amount of waste is generated from the manufacture of plastic RFID access cards Digital credentials align with the sustainable solutions that everyone wants. A huge amount of waste is generated from the manufacture of plastic RFID access cards. Over 550 million access cards are sold annually. This creates 2,700 tons of plastic waste and 11,400 tons of carbon, based on a PVC card weighing 5 grams. Therefore, digital credentials self-evidently reduce the reliance on plastic cards (helping reduce carbon emissions by up to 75% according to HID’s research), while leveraging access control system data supports energy optimization by shutting down or reducing systems in unused spaces. Energy use and CO₂ emissions can be cut dramatically, showing how access systems can contribute to sustainability goals and green building certification. What is the latest in smart buildings? Smart buildings increasingly rely on mobile access control as the backbone for digital services. Real-time access data enables new services such as automated room bookings, HVAC control, lift/elevator calling, e-bike hiring, and so on. Smart buildings increasingly rely on mobile access control as the backbone for digital services The financial upside is clear; smart, digitally transformed buildings can deliver around 8% higher yields per square foot versus traditional office space. Operational savings accrue from reduced administration, the removal of card production and shipping, and lighter IT support. This creates a value cycle — better experiences drive adoption, adoption fuels monetization, and monetization funds further improvements. Achieving technology impact in the real world One standout project is One Bangkok – a $3.9 billion mixed-use development in Thailand – which demonstrates the scale of what can be achieved when access control data is used for optimization, particularly when it comes to monitoring facilities usage and occupier behaviors. By switching lights off or lowering the temperature in unused rooms, for example, the One Bangkok building demonstrates this potential with a 22% reduction in energy consumption, saving 17,000 MWh and 9,000 tons of CO₂ annually. Sustainability is a key factor in contributing to how properties are valued. And sustainability extends far beyond digital credentials having a lower environmental impact than plastic cards. Buildings with recognized sustainability certifications often command rental premiums of around 6%, and three‑quarters of security decision‑makers now consider environmental impact in their procurement assessments.
Case studies
Xtract One Technologies announced its SmartGateway has been selected by Nova Scotia Health to strengthen security measures and provide AI-powered weapons detection across facilities province-wide, with an initial order of 25 systems. Nova Scotia Health, in tandem with its nurses’ union, is working to modernize and strengthen security across its facilities to ensure a safe environment for all patients, visitors, and staff. Adopting and deploying advanced technologies like SmartGateway is an important step toward achieving that goal. Safe and secure health care By helping to limit the number of potentially dangerous items entering their hospitals, this technology supports its commitment to providing safe and secure health care. Xtract One was selected for its proven efficacy to accurately detect knives, a top priority for the organization. Previously tested in Truro, Nova Scotia, over a 12-day trial period, SmartGateway successfully scanned 7,400 individuals entering the facility and detected 49 prohibited items during that period, mostly pocket knives and box cutters. Deploying SmartGateway “Violence against healthcare workers is a challenge that persists and demands addressing. By deploying SmartGateway, Nova Scotia Health is setting an important example for what it means to take meaningful action to protect frontline healthcare workers, patients, and visitors,” said Peter Evans, CEO of Xtract One. “This installation marks another key step in our expanding work with Canadian healthcare organizations, having deployed in Manitoba earlier this year. We look forward to continuing to deliver effective threat detection as more providers take proactive measures to prioritize security and peace of mind for their teams.” Overall approach to security “Our goal is to deliver first class healthcare, and ensuring the safety of all who enter our facilities is a critical step in providing that service,” said Dean Stienburg, Director of Security for Nova Scotia Health. “With SmartGateway, we’re making tangible strides in bolstering our overall approach to security. We were impressed by the system’s effectiveness during the trial period and are looking forward to the deployment helping us mitigate and respond to the threats of today’s environment.” Maximising security screening outcomes SmartGateway delivers fast, discreet, and accurate individual screening, utilizing AI-powered sensors to unobtrusively scan for weapons and other prohibited items upon entry. This technology replaces intimidating, traditional metal detectors and mitigates the need for individuals to remove personal items. This prioritizes individual privacy and comfort, all while maximizing security screening outcomes. SmartGateway is designed to enable seamless passage through checkpoints and promote the uninterrupted flow of movement.
Comelit-PAC has partnered with Kings Group SW to deliver a bespoke video door entry solution at the historic Bridgwater Arts Center, a Grade I listed building renowned for its architectural and cultural significance. Situated in the heart of Bridgwater, now owned and operated by the Town Council, the Arts Center construction was in 1723 and established on its existing site since 1946 to run a theater program of performance, music and film. Enhancing video security and access To complete a renovation program, the Arts Center worked with Kings Group SW to upgrade its door entry system to incorporate a modular video design. “The Grade I listing of Bridgwater Arts Center means that any changes, however minor, must be carefully planned to protect the building’s historic character,” said Scott Mason, Director of Amenities at Bridgwater Town Council. “We involved our teams in the initial design and specification process to ensure the solution could be installed to seamlessly blend with its surroundings while enhancing video security and access.” Latest security standards Kings Group SW specified Comelit-PAC’s Ultra Door Entry system, a high-definition video intercom solution designed to allow staff to monitor all entry points via high-definition video intercoms, providing real-time visibility and secure access control. Adam Pitman, Security and Life Safety Systems Supervisor at Kings Group SW, added: “Every aspect of the door entry upgrade had to be approached sensitively. This included routing cables discreetly, installation and ensuring the system met the latest security standards. By choosing Comelit-PAC’s modular system, this could be achieved with minimal disruption to the building’s historic fabric while providing a flexible solution that can be adapted as the Center’s security needs evolve.” Configuration of the door entry solution The Ultra system was selected because its modular design enabled a simple configuration of the door entry solution to meet the specific requirements of the Arts Center. Its 2-Wire and ViP door stations allow a combination of audio, video, and button modules in a compact layout, giving the team flexibility to adapt the system to access points. Tony Berry, Business Development Manager at Comelit-PAC, concluded: “Working closely with Kings Group SW and Bridgwater Arts Center early on allowed us to tailor the solution specifically for this site. By understanding the needs of the team and how the building operates, we were able to deliver a system that functions seamlessly for staff, visitors and performers while integrating thoughtfully into the historic environment.”
The University of Southampton, a multi-campus estate with a research institution, has recently enhanced its fire safety provision for deaf and hard-of-hearing individuals through a pioneering paging system installation. Advanced’s MxPro 5 fire panels, integrated with the ESPA Pager Interface, form the core of the new solution delivered by Premier Fire Security and Scope Communications, providing targeted alerts and improved accessibility across the university. Traditional audio alarms With over 200 Advanced panels deployed across the site, including two networks of 30–40 nodes and a growing number of extinguishing panels, the university required a solution that could deliver precise, location-specific fire alerts to individuals without relying on traditional audio alarms. The ESPA 4.4.4-compliant Pager Interface from Advanced provided the ideal bridge between the fire detection system and Scope’s PageTek Pro Mk2 transmitter and EPOCBLUM pagers. The system is configured so that each building or group of buildings triggers a distinct pager address. This ensures that only relevant alerts reach the end user, reducing confusion and improving response times. Users can manually program their pagers to activate or deactivate specific locations, with password protection for added security. For nighttime safety, Scope’s pillow pad and nightstand accessories ensure that alerts are received even while users are asleep. Dedicated paging group Chris Chance, University of Southampton Contract Manager at Premier Fire Security, explained: “We’ve worked closely with Scope and Advanced to create a system that’s not only reliable but incredibly flexible. The ability to configure pagers for any location means we can reduce hardware stock and improve coverage across the entire campus. It’s a huge step forward in inclusive safety.” The installation also includes a dedicated paging group for engineers, janitors, security, and fire marshals, who receive diagnostic and fault messages from the Advanced network. This group can also trigger fire messages for specific locations, enhancing operational control and coordination. Enhancing operational control Rob Baker, Head of Technical Support at Scope Communications, added: “This project demonstrates how powerful the ESPA interface can be when paired with our paging technology. The system ensures that alerts are both accurate and accessible, and we’re proud to support Premier Fire Security in expanding this solution across the university.” The long-term vision is to roll out the paging system to all student halls, allowing pagers to be reconfigured for use anywhere on campus. This approach not only improves safety but streamlines inventory and reduces costs. Delivering tailored fire alerts Salvy Vittozzi, Regional Sales Manager for the South East at Advanced, commented: “This installation is a great example of how our ESPA Pager Interface can be used to deliver tailored fire alerts in complex environments. It’s rewarding to see our technology helping to make campuses safer and more inclusive for all users.” By combining Advanced’s robust fire panel technology with Scope’s innovative paging solutions, the University of Southampton now benefits from a highly adaptable, inclusive fire safety system, one that’s already being expanded to meet the evolving needs of its diverse community. Intelligent fire systems As a pioneer in the development and manufacture of intelligent fire systems, Advanced products are specified in locations around the world, from single-panel installations to large, multi-site networks. The Advanced portfolio includes complete fire detection systems, multiprotocol fire panels, extinguishing control, false alarm management and reduction systems as well as emergency lighting. Advanced is owned by FTSE 100 company Halma PLC – a global group of life-saving technology companies with a clear purpose to grow a safer, cleaner, healthier future for everyone, every day.
Acoustic imaging offers a powerful early warning solution, enabling operators to detect issues before they escalate and keep turbines running efficiently. For any government, sourcing energy involves complex decisions that extend beyond logistics, finance, and environmental considerations to include geopolitical factors. While all of these elements have influenced the rapid expansion of wind turbines worldwide, environmental and geopolitical concerns have been particularly instrumental in driving their significant growth. The global rise of wind energy In 2023 the global wind industry installed a record 117 gigawatts of new capacity, a 50% increase compared to the previous year. This surge brought the total global wind capacity to over 1,000 gigawatts. China led the way in new installations, followed by the United States, Germany and India. The vast majority of wind turbines are land based, with offshore making up the remaining 7%. However, offshore is experiencing faster growth and is expected to play a more significant role in the future as more countries develop and invest in the new technology. Looking to the future, the wind energy sector is expected to continue its growth trajectory, with an anticipated compound average growth rate of 8.8% according to the Global Wind Energy Council. Offshore wind capacity, where stronger and more consistent winds are experienced, is expected to grow tenfold from its current level by 2030, exemplifying the sector’s staggering growth. Challenges in turbine maintenance The very nature of wind capture means that wind turbines are usually located in remote, hard the reach areas. Offshore windfarms clearly pose logistical challenges both in terms of construction and maintenance, but even land-based turbines often create real challenges for maintenance crews when positioned in remote mountainous terrain where wind capture is maximized. Maintenance logistics even within the turbine itself can be a challenge. The nacelle, which houses the gearbox must be accessed via the tower with very limited space to move around. Inserting heavy components and lubricating oil into the nacelle is often difficult. For this reason, any measure that enhances the durability and reliability of key nacelle components is highly valuable to wind farm operators. Monitoring of critical components One of the critical components of a wind turbine is the gearbox. It is responsible for increasing the rotational speed from the blade shaft to the electrical generator, decreasing torque and increasing speed. Many designs incorporate planetary gearbox systems, given the efficiency of these systems to increase speed from the shaft. Containing an array of helical gears and multiple bearings these gearboxes are both intricate and expensive. Failure can prove extremely expensive both in terms of replacing components, but also in turbine downtime, as logistical challenges of getting replacement parts often proves difficult. For these reasons, proactive condition monitoring of critical components is essential. Early detection of potential issues allows operators to address problems before they escalate, reducing costly downtime and extending the lifespan of the turbine. Acoustic imaging as an effective early warning system Flir have introduced a series of advanced acoustic imaging cameras capable of detecting abnormal sounds that occur when a bearing is showing early signs of failure. These handheld cameras are non-obtrusive and can pick up sounds from a significant distance, keeping the operator safe and allowing for inspections without halting operations. The Flir Si2-Series features a 12 MP camera that captures sound, and the signal is displayed on a 5-inch, 1280 × 750 high-definition color screen providing clear, concise, real-time results. These lightweight, cutting-edge devices are designed to provide an early warning system for preventative maintenance. Detecting abnormalities in bearings and gearbox systems is just one of their many applications. They can also identify leaks in compressed air or gas systems and detect partial discharge in electrical systems, offering not only significant cost savings but also ensuring health and safety in potentially hazardous environments.
Colt Technology Services (Colt), the global digital infrastructure company, released the key enterprise technology and market trends it expects to dominate the CIO agenda in 2026. Based on customer insights, market intelligence and its own proprietary research, Colt anticipates AI Inference, the evolution of NaaS to ‘NaaS 2.0’ and quantum-safe security to shape the technology landscape over the next 12 months. Ever-changing regulatory environment “CIOs will continue to face headwinds in 2026 as they balance complex business transformation programs at scale – often centered around AI – with ongoing cost-reduction programs in an ever-changing regulatory environment,” said Buddy Bayer, chief operating officer, Colt Technology Services. “But there’s huge opportunity too: AI programs are beginning to mature, digital infrastructure has greater capacity than ever before, and we’re seeing an evolution of solutions like NaaS which are reshaping our digital experiences. It’s an exciting time and, at Colt, we’re leading the way for our customers.” New ways to generate ROI from AI Businesses continue to drive major investments in AI, but ROI, value creation and monetization are proving elusive. Colt’s research finds one in five global firms spend US$750,000 annually on AI while 95% of the respondents in a recent MIT report study see no return on their investments. This misalignment between spending and measurable returns will shrink in 2026, as AI projects mature and begin to generate ROI, and as businesses find new ways to create value from AI. More vendors will build in AI maturity assessments and structured ROI models to help businesses define, track and quantify value across their AI tools. AI inference and Agentic AI 2026 will see AI inferencing reaching the next level of maturity, shifting from experimentation to integration into the enterprise IT environment, extracting insight, making predictions, and enabling smarter, context-aware decisions in real-time. McKinsey expects AI inference to account for a majority of AI workloads by 2030. This won’t just be limited to enterprises: Agentic AI, driven by inference, will be the force behind the automation and digitalization of day-to-day consumer tasks from privacy management and healthcare to scheduling assistance and management of household chores, according to research from the IEEE. AI Wide Area Networking (WAN) Many of Colt’s conversations with customers center around digital infrastructure’s ability to manage and optimize the performance, latency and security needed for AI workloads. AI WAN moves the conversation towards software-driven wide area networks, built for AI workloads, which dynamically manage AI traffic for peak performance and ensure application-level security of critical data. Innovation in sustainable networking technologies Similarly, AI workloads transmitted over transatlantic cables will grow in 2026 and are projected to surge from just 8% of total capacity in 2025 to 30% by 20351, placing additional strain on global network routes. Innovative tech trials and global partnerships are pioneering technologies which boost performance without increasing energy consumption or carbon emissions. Sovereign AI As nations grow their AI investments and regulations around AI governance come into force across many of the world’s major economies, sovereign AI is gaining momentum. It will rise up the CIO’s agenda as countries and organizations build and run their own AI systems using their own data, infrastructure, people, and rules. Sovereign AI is becoming more prevalent and increasingly important as nations look to stay in control of their technology, protect their data, and stay resilient in a world increasingly shaped by AI. NaaS 2.0 The NaaS market continues to grow, driven by a number of factors from AI, edge computing and cloud adoption to enterprises’ need to build in flexibility as they navigate dynamic global markets. Colt research found 58% of the 1500 CIOs it questioned said they were increasing their use of NaaS features due to growing AI demands. In 2026 and beyond, people will see NaaS evolve to meet the demands of the AI era, moving beyond its traditional role in supporting digital experiences. The next generation of NaaS will be intelligent, automated, and outcome-focused, designed to deliver real-time performance, adaptability, and autonomy for AI-driven enterprises. Quantum security Rise in quantum security investment as Q Day gets nearer CIOs are under constant pressure to protect their data and infrastructure from emerging risk, and as governments and businesses develop a deeper understanding of quantum’s power and potential, attention and investment turn to quantum security. In its 2026 Technology and Security Predictions report2, Forrester forecasts that quantum security spending will exceed 5% of enterprises’ overall IT budget next year, while a report from The Quantum Insider estimates the quantum security market to grow at over 50% CAGR to 2030, reaching $10 billion. Traditional data cryptography methods are at risk of being deciphered by quantum computers. The point at when this happens is known as Q Day, and latest estimates suggest it could come as soon as 2030. Technologies such as post-quantum cryptography (PQC) and quantum key distribution (QKD) protect traffic from this risk as it travels across a network. 2026 will bring developments, trials and innovation in protecting data from quantum risk. Low Earth Orbit technologies – and quantum 2026 is set to be a breakthrough year for Low Earth Orbit satellites, with organizations launching new satellites and new services. These services are a vital part of global telecoms infrastructure, providing connectivity in underserved or rural areas, and providing resiliency to businesses looking for back-up options for their enterprise infrastructure. Colt is looking to trial low earth orbit satellite connectivity for quantum key distribution: this will enable secure and protected exchange of symmetric encryption keys using quantum technology, while overcoming the distance limitations of terrestrial connectivity. 2026 will see Colt and partners trialing space-based and subsea techniques which extend quantum security to global networks. Hybrid cloud computing models 2026 will see multi cloud models becoming the default, as enterprises look for more ways to build in flexibility and resilience to their infrastructure and move beyond single-provider strategies. Increasingly, APIs and secure interconnects between providers and hyperscalers are streamlined, complementary and competitive in pricing terms and accessible through aggregators. Edge computing will continue to grow through 2026 and beyond, driven by factors such as AI inference expansion, the rise in real-time analytics, and increasing data sovereignty requirements. Next-generation cloud providers Next-generation cloud providers are prioritizing deployment of infrastructure at the edge, processing data closer to where it’s generated, while hyperscalers focus on scale and compute power in centralized locations. Both strategies are needed and complementary: Edge requires highly distributed, localized infrastructure which complements centralized cloud, used for heavy compute and storage. As demand for Edge grows in 2026 and beyond – one forecast estimates a CAGR of 33.0% from 2025 to 2033 - expect rising demand for distributed architectures across new geographies. Tighter regulatory frameworks In 2026, expect to see a slew of reporting obligations, regulations, strategies and guidelines impacting CIOs, particularly in AI and cybersecurity. Most of the obligations under the EU AI Act will apply from 2 August 2026, while implementation of certain requirements for high-risk AI systems may be postponed. Reporting obligations for the EU Cyber Resilience Act are expected from September 2026, with phased obligations continuing from September 2026 onward under the EU Data Act. Cyber Security and Resilience Bill Peolpe also see the ISO/IEC 42001:2023 global standard for AI governance, which will lead CIOs and CAIOs to integrate AI governance into enterprise architecture and procurement decisions, as well as operational impacts for the Digital Services Act and the Digital Markets Act. In the UK, all eyes will be on the Cyber Security and Resilience Bill, while across Asia, Japan will see the impact of its AI Promotion Act and major initiatives following Singapore’s National AI Strategy 2.0 (NAIS 2.0) are also expected to come into effect in 2026.
Set in 33 hectares of woodland on the edge of Dartmoor National Park, the zoo is home to an impressive variety of exotic and native animals, including Amur tigers, African lions, and Amur leopards. New patented master key system On-site challenges before the introduction of the new patented master key system. Before implementing the new master key system, the zoo faced the challenge of ensuring secure and efficient access control to sensitive areas, particularly enclosures with potentially dangerous animals. The previous master key systems were outdated and did not provide the necessary security and flexibility required for the zoo's daily operations. Installation of EPS NP and its advantages The EVVA EPS NP system was installed in collaboration with local partner Sir Fix-a-Lock. This system offers robust patent protection, long-term key control and high reliability in demanding environments. A total of 192 Asec weatherproof padlocks were installed in a 6-level master key system. The flexibility of EPS NP enabled graduated key control across the entire site, including special levels for animal care. Advantages of the new patented key system for the zoo Thanks to the new master key system, the zoo has been able to implement a secure and practical solution that enables staff to work efficiently while maintaining strict access controls. The color-coded keys make it easy to quickly identify access authorisations, which is particularly advantageous in security-critical areas. The Asec weatherproof padlocks also offer high resistance to environmental influences, ensuring the longevity of the system. "EPS has revolutionized our access control and gives us the security and flexibility we need." The project at Dartmoor Zoo impressively demonstrates how EVVA's flexible master key systems can be adapted to specific requirements to ensure security, control and long-term protection.


Products


Round table discussion
Transportation systems need robust physical security to protect human life, to ensure economic stability, and to maintain national security. Because transportation involves moving large numbers of people and critical goods across vast, often interconnected infrastructure, it presents a highly attractive target for various threats. More threats equate to a greater need for security. We asked our Expert Panel Roundtable: What are the emerging applications of physical security in the transportation market?
Installing physical security systems requires integrating diverse technologies (e.g., cameras, access control, alarms) that often use different protocols and must be adapted to a building's unique physical layout and legacy infrastructure. Specialized technical expertise is required for seamless networking and proper configuration. Hopefully, no important factors are overlooked in the installation process. We asked our Expert Panel Roundtable: What is the most overlooked factor when installing physical security systems?
The healthcare industry faces unique and significant security challenges. Healthcare security professionals must balance an open, welcoming environment for patients and visitors with the need to protect valuable assets and personnel in a high-stress, 24/7 setting. These requirements direct the physical security technologies deployed in medical facilities. We asked our Expert Panel Roundtable: What are the unique aspects of the healthcare market, and how should the physical security industry adapt?
White papers

One System, One Card
Download
Aligning Physical And Cyber Defence For Total Protection
Download
Understanding AI-Powered Video Analytics
Download
Modernizing Access Control
Download
Enhancing Physical Access Control Using A Self-Service Model
Download
Combining Security And Networking Technologies For A Unified Solution
Download
Open Credential Standards And The Impact On Physical Access Control
Download
What is a universal RFID reader?
Download
System Design Considerations To Optimize Physical Access Control
Download
Milestone Cloud Deployment Guide
Download
Maximizing Enterprise Security Systems In The Cloud
Download
The 4 Pillars Of AI In Managing High-Stakes Critical Events
Download
The Power Of Integration In Physical Security Systems
Download
Using Artificial Intelligence (AI) To Automate Physical Security Systems
Download
A Modern Guide To Data Loss Prevention
Download