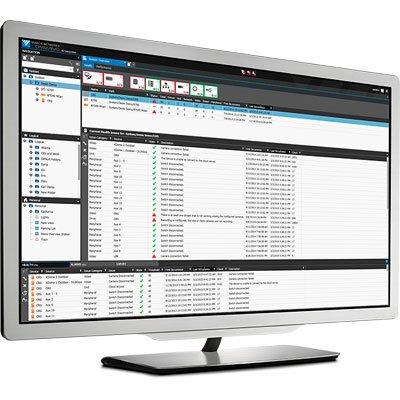
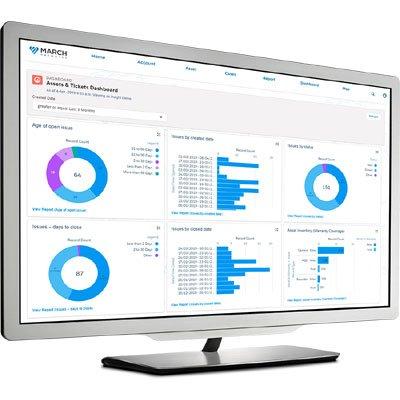
Remote video surveillance
Deep Sentinel, the pioneer in AI-powered proactive video surveillance with real-time human intervention, now announced the launch of its Mobile Monitoring Trailer — a fully mobile, solar-powered security platform that delivers instant access to Deep Sentinel’s remote live guard monitoring anywhere, including places where power and permanent infrastructure are unavailable. Purpose-built for high-value outdoor environments, such as auto and parking lots, construction sites, industrial...
Water ecosystems, ranging from high-altitude glacial lakes to expansive wetlands, are essential to the planet. These ecosystems regulate the climate, filter pollution, and support rich biodiversity. However, many are located in remote, hard-to-access areas, leaving them susceptible to gradual and often unnoticed degradation. The silent crisis in the blind spots The most significant challenge in protecting these vital waters is the growing gap between the rapid pace of environmental change and...
Interface Systems, a pioneering managed service provider delivering remote video monitoring, commercial security systems, business intelligence, and network to multi-location enterprises, outlined the security and technology trends expected to define retail, restaurant, and commercial business safety in 2026. The company anticipates an increased shift toward proactive, exterior-focused measures, AI-driven analytics for operational efficiency, broader adoption of human oversight for AI, and heig...
Artificial Intelligence Technology Solutions, Inc., a pioneer in AI-driven security and productivity solutions, along with its wholly owned subsidiary, Robotic Assistance Devices Group (RAD-G), announced a SARA™ contract covering more than 2000 video channels, marking a large agentic AI monitoring deployment. The agreement begins with SARA Verified replacing a competing solution and is expected to progress into SARA Lite and ultimately SARA Agent as the client expands its use of auto...
Drones are poised to fill long-standing gaps in physical security. Fixed cameras leave blind spots, and human guards cannot quickly cover large or complex properties during high-risk moments. Drones fill the gaps, providing a missing mobile layer, offering unmatched speed, broad aerial visibility, and proactive coverage that elevates security from reactive to truly responsive and deterrent. As an added element in security systems, drones complement fixed cameras, access control, and license pla...
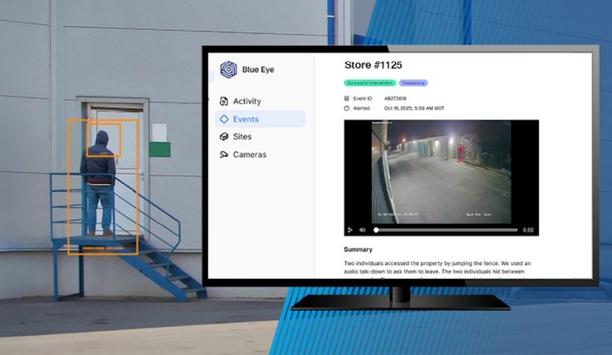
Motorola Solutions announced it has acquired Blue Eye, a pioneering provider of AI-powered enterprise remote video monitoring (RVM) services, based in Salt Lake City, Utah. Blue Eye provides a comprehensive RVM service powered by AI to help detect threats in real time, enabling live voice talk-downs to deter crime and providing verified alerts to help accelerate law enforcement response. Enhanced situational awareness The company’s software platform is interoperable with pioneerin...
News
Artificial Intelligence Technology Solutions, Inc., a pioneer in AI-driven security and productivity solutions, along with its wholly owned subsidiary, Robotic Assistance Devices Group (RAD-G), today announced the release of SARA™ ASSIST, a new extension to its multiple award-winning SARA (Speaking Autonomous Responsive Agent), the Company's agentic AI platform. Designed for Remote Video Monitoring, GSOC, and SOC environments, SARA ASSIST places agentic AI directly on the operator's console, providing real-time verification, notification, and documentation capabilities within active monitoring workflows. Agentic AI platform Artist’s depiction of SARA ASSIST enhancing a busy security monitoring center. The agentic AI platform works in parallel with human personnel, streamlining verification, communication, and reporting across live video feeds. SARA ASSIST creates an efficient hybrid control platform that dramatically increases operator efficiency without turning over all functions to SARA's full agentic AI workflow. An early client call center manager recently remarked, "Our team has really been enjoying the SARA ASSIST feature. It's been a great addition and has helped improve our efficiency. Being able to have SARA make calls for simple tasks with just a click has been a big time-saver." Introduction of SARA ASSIST The introduction of SARA ASSIST marks a key step in bringing agentic AI into mainstream monitoring operations, enabling human operators to manage incidents faster and with greater consistency. SARA ASSIST is included at no extra cost. The Company expects that as central stations gain operational confidence with SARA's performance through the use of SARA ASSIST, they will move quickly to full agentic AI-powered call center operations. Invent new features and functionality "Creating the leading agentic AI platform for the security industry has been a joy and has required us to invent new features and functionality," said Steve Reinharz, CEO/CTO and Founder of AITX and RAD-G. "From fully autonomous systems to operator-assist deployments, our goal is to have a version of SARA on every console, at every site, helping teams make faster, smarter, more confident decisions. This approach positions RAD-G to scale agentic AI across every segment of the monitoring and security industry." SARA platform's capabilities SARA ASSIST extends the SARA platform's capabilities to live operators, serving as the bridge between manual monitoring and full agentic automation. While SARA AGENT and SARA EDGE operate autonomously to verify, communicate, and respond without human input, SARA ASSIST is designed to work alongside monitoring personnel, adding real-time AI support directly into their workflow. It verifies alerts, initiates notifications, and documents activity automatically, giving operators the speed and accuracy of agentic AI without replacing human judgment. Advantages of SARA ASSIST firsthand The SARA ASSIST platform complements existing SARA offerings, including VERIFIED, LITE, AGENT, and EDGE, each designed for specific levels of automation and engagement. Priced to accelerate adoption, SARA ASSIST offers organizations a low barrier entry into agentic AI while establishing a direct path toward full autonomy as operational confidence grows. RAD-G invites all organizations engaged in live video monitoring, GSOC, and SOC operations to experience the advantages of SARA ASSIST firsthand.
Artificial Intelligence Technology Solutions, Inc., a global pioneer in AI-driven security and productivity solutions, along with its wholly owned subsidiary, Robotic Assistance Devices, Group (RAD-G), announced that four Remote Video Monitoring (RVM) companies have entered operational pilot programs with SARA (Speaking Autonomous Responsive Agent), the Company’s multiple award-winning agentic AI platform set to expand the remote video monitoring industry. These pilots represent the next major step in SARA’s rapid expansion, moving from signed commitments to live operations across the monitoring sector. These industry first movers are poised to grow market share and margins with the implementation and use of SARA in lieu of traditional monitoring methods. Ten RVM clients In October, the Company announced that an initial ten RVM clients had signed on to license SARA. The four companies now in operational pilot mode represent the beginning of a series of more than ten active deployments expected to roll out over the next several weeks. Collectively, their networks encompass roughly 100,000 potential monitoring channels that could be transitioned to SARA as performance continues to demonstrate its reliability, scalability, and transformative impact on live monitoring operations. “SARA has moved from concept to demonstrations to non-disclosure agreements and now to live operational testing,” said Steve Reinharz, CEO/CTO of AITX and RAD-G. “These pilots show the industry demand for agentic AI. We’re moving fast and setting a new standard the rest of the industry will have to chase.” Global remote video monitoring market These initial pilots represent only a fraction of the opportunity ahead. The global Remote Video Monitoring market is estimated to encompass more than five million active monitoring channels, and SARA’s growing footprint positions RAD-G at the center of that transformation. As additional monitoring clients prepare to begin their own pilot and deployment phases, the Company expects to announce further rollouts and measurable results that reinforce SARA’s expanding role as the industry’s preferred AI platform for live video monitoring. AITX, through its primary subsidiary, Robotic Assistance Devices, Inc. (RAD), is redefining the nearly $50 billion (US) security and guarding services industry through its broad lineup of innovative, AI-driven Solutions-as-a-Service business model. Cost savings to businesses RAD solutions are specifically designed to provide cost savings to businesses of between 35%-80% when compared to the industry’s existing and costly manned security guarding and monitoring model. RAD delivers these cost savings via a suite of stationary and mobile robotic solutions that complement, and at times, directly replace the need for human personnel in environments better suited for machines. All RAD technologies, AI-based analytics and software platforms are developed in-house. Successful completion of its SOC 2 Type 2 audit The Company’s operations and internal controls have been validated through successful completion of its SOC 2 Type 2 audit, which is a formal, independent audit that evaluates a service organization’s internal controls for handling customer data and determines if the controls are not only designed properly but also operating effectively to protect customer data. This audit reinforces the Company’s credibility with enterprise and government clients who require strict data protection and security compliance. Extensive expertise RAD is led by Steve Reinharz, CEO/CTO and founder of AITX and RAD, who brings decades of experience in the security services industry. Reinharz serves as chair of the Security Industry Association’s (SIA) Autonomous Solutions Working Group and as a member of the SIA Board of Directors. The RAD team also draws on extensive expertise across the sector, including Mark Folmer, CPP, PSP, President of RAD and Chair of the ASIS International North American Regional Board of Directors, Troy McCanna, former FBI Special Agent and RAD’s Chief Security Officer, and Stacy Stephens, co-founder of security robotics company Knightscope. Their combined backgrounds in security industry leadership, law enforcement, and robotics innovation reinforce RAD’s ability to deliver proven, practical, and disruptive solutions to its clients. Prospective sales pipeline RAD has a prospective sales pipeline of over 35 Fortune 500 companies and numerous other client opportunities. RAD expects to continue to attract new business as it converts its existing sales opportunities into deployed clients generating a recurring revenue stream. Each Fortune 500 client has the potential of making numerous reorders over time. AITX is an innovator in the delivery of artificial intelligence-based solutions that empower organizations to gain new insight, solve complex challenges and fuel new business ideas. Through its next-generation robotic product offerings, AITX’s RAD, RAD-R, RAD-M and RAD-G companies help organizations streamline operations, increase ROI, and strengthen business. AITX technology improves the simplicity and economics of patrolling and guard services and allows experienced personnel to focus on more strategic tasks. Customers augment the capabilities of existing staff and gain higher levels of situational awareness, all at drastically reduced cost. AITX solutions are well suited for use in multiple industries such as enterprises, government, transportation, critical infrastructure, education, and healthcare.
Artificial Intelligence Technology Solutions, Inc., announces that its subsidiary, Robotic Assistance Devices Group (RAD-G), has launched a new website dedicated to its multiple award-winning agentic AI security monitoring platform, SARA™. The new site, www.saramonitoring.ai highlights recent industry recognition, and its growing adoption across the remote video monitoring sector. Real time monitoring automation The launch of the website follows a series of major milestones for SARA, including two industry awards at ISC West 2025 recognizing its leadership in agentic AI and real time monitoring automation. Last week, SARA drew significant attention at The Monitoring Association’s annual meeting, where live demonstrations showcased how the platform autonomously detects, verifies, and responds to security events without operator fatigue or bias. Two recent case studies, featuring deployments with OneWatch and HUB Enterprises, further illustrate SARA’s proven ability to reduce false alarms, accelerate response times, and deliver consistent results across diverse client environments. Diverse client environments “We’re seeing extraordinary momentum around SARA and the performance it delivers for monitoring centers,” said Mark Folmer, CPP, PSP, Interim President of RAD-G. “This new site showcases how far the platform has come, from concept to award-winning deployment. SARA is changing expectations across the industry, proving that agentic AI can deliver reliable, real-time monitoring that improves outcomes for clients, partners, and communities.” “We’re putting our full marketing power behind SARA because it represents the future of our company and the industry,” said Steve Reinharz, CEO/CTO of AITX and all RAD subsidiaries. “The awareness, interest, and adoption we’re seeing are incredible, and we’re only getting started. This is the era of agentic AI, and SARA is leading the way for our clients, channel partners, and shareholders.” Remote video monitoring The new website, www.saramonitoring.ai is now live and provides a detailed overview of SARA’s capabilities, features, and industry deployments. Visitors can explore case studies, request demonstrations, and learn how SARA is transforming the economics and efficiency of remote video monitoring. AITX, through its primary subsidiary, Robotic Assistance Devices, Inc. (RAD), is redefining the nearly $50 billion (US) security and guarding services industry[i] through its broad lineup of innovative, AI-driven Solutions-as-a-Service business model. RAD solutions are specifically designed to provide cost savings to businesses of between 35%-80% when compared to the industry’s existing and costly manned security guarding and monitoring model. RAD delivers these cost savings via a suite of stationary and mobile robotic solutions that complement, and at times, directly replace the need for human personnel in environments better suited for machines. All RAD technologies, AI-based analytics and software platforms are developed in-house. Security industry leadership The Company’s operations and internal controls have been validated through successful completion of its SOC 2 Type 2 audit, which is a formal, independent audit that evaluates a service organization’s internal controls for handling customer data and determines if the controls are not only designed properly but also operating effectively to protect customer data. This audit reinforces the Company’s credibility with enterprise and government clients who require strict data protection and security compliance. RAD is led by Steve Reinharz, CEO/CTO and founder of AITX and RAD, who brings decades of experience in the security services industry. Reinharz serves as chair of the Security Industry Association’s (SIA) Autonomous Solutions Working Group and as a member of the SIA Board of Directors. The RAD team also draws on extensive expertise across the sector, including Mark Folmer, CPP, PSP, President of RAD and Chair of the ASIS International North American Regional Board of Directors, Troy McCanna, former FBI Special Agent and RAD’s Chief Security Officer, and Stacy Stephens, co-founder of security robotics company Knightscope. Their combined backgrounds in security industry leadership, law enforcement, and robotics innovation reinforce RAD’s ability to deliver proven, practical, and disruptive solutions to its clients. Recurring revenue stream RAD has a prospective sales pipeline of over 35 Fortune 500 companies and numerous other client opportunities. RAD expects to continue to attract new business as it converts its existing sales opportunities into deployed clients generating a recurring revenue stream. Each Fortune 500 client has the potential of making numerous reorders over time. AITX is an innovator in the delivery of artificial intelligence-based solutions that empower organizations to gain new insight, solve complex challenges and fuel new business ideas. Through its next-generation robotic product offerings, AITX’s RAD, RAD-R, RAD-M and RAD-G companies help organizations streamline operations, increase ROI, and strengthen business. AITX technology improves the simplicity and economics of patrolling and guard services and allows experienced personnel to focus on more strategic tasks. Customers augment the capabilities of existing staff and gain higher levels of situational awareness, all at drastically reduced cost. AITX solutions are well suited for use in multiple industries such as enterprises, government, transportation, critical infrastructure, education, and healthcare.
ZE Government Solutions (ZEGS), a wholly owned subsidiary of AI-based gun detection pioneer ZeroEyes, launched ZeroEyes Aerial Detection Kit (ZAD), a portable, drone-based AI threat detection and intelligent situational awareness solution designed for public safety agencies. The kit provides operators with a stand-alone drone solution that can be deployed in minutes from agencies' existing drone platforms to detect firearms, people, vehicles, drones, and maritime vessels. Rapid integration with drones Outdoor spaces are among the most challenging environments to protect due to their size and open nature, leaving them vulnerable to unauthorized access and potential gun-related violence. ZeroEyes Aerial Detection addresses this critical need with layered advanced AI analytics that detect threats in real time through a drone's live camera feed. To provide confidence and situational awareness, detections can be viewed instantly by law enforcement or security personnel and dispatched immediately to on-site staff when detections are made. Rapid integration with drones ensures that first responders or federal agencies are quickly informed of on-scene security threats, allowing for appropriate response posture to the current situation. ZeroEyes Aerial Detection Kit The kit enhances drone operations for a variety of scenarios, including drone response, event and perimeter security, armed assailants, suspect and article searches, barricaded gunmen, hostage situations, and domestic disputes. Providing immediate detections and alerting improves law enforcement situational awareness and personnel safety. ZeroEyes Aerial Detection Kit integrates seamlessly with existing drones and drone programs, and comes equipped with a carry-on case and a ZeroEyes laptop to stream video and deliver automated alerts to dispatch or operations centers via LTE, Wi-Fi, or mesh radio. It connects to drone feeds or controllers through HDMI, IP address, RTSP or Headsets, and is compliant with the National Defense Authorization Act and protected by DHS SAFETY Act designation. New drone solution “Protecting outdoor spaces is one of the greatest challenges in security today,” said Dustin Kisling, Executive Vice President of ZE Government Solutions. “With our new drone solution, we can detect potential threats in real time and provide verified alerts, giving organizations and the public the confidence that help is on the way when it matters most.”
Videx Security has introduced a new 7” handsfree video monitor that brings advanced functionality typically reserved for full IP systems to its popular 2 wire range. The 6789 monitor, part of the 6700 series, is designed for use with the VX2300 system and 2 wire video kits, including the new ERA23V range. It combines a high-resolution capacitive touchscreen with tactile programmable buttons, offering intuitive control, remote connectivity, and smart integration features for residential, commercial and mixed-use applications. Videx CloudNected app As well as operating over the 2 wire bus, the 6789 includes built-in WiFi to enable remote access via the Videx CloudNected app. Users can receive calls, view entry panel cameras and unlock doors and gates from anywhere. The system also supports third-party CCTV integration via RTSP, and includes a web browser for remote management, event log access, and smart home control. Rob Sands, Technical Director at Videx, said: “The 6789 represents a major step forward in 2 wire video systems. It brings together the usability of a modern touchscreen monitor with features such as remote access, third-party integration and smart heating control – all in one unit. It’s an ideal solution for both new installations and retrofit upgrades.” Additional features Additional features include a thermostat and humidity sensor with programmable weekly schedules, smart intercommunication between monitors and the ability to adjust key settings via an internal web browser or IPure Wizard software. A desktop mount kit is also available for added installation flexibility. The 6789 is compatible with other monitors on the VX2300 system and can be used to upgrade existing installations where more advanced features are required.
Artificial Intelligence Technology Solutions, Inc., a global pioneer in AI-driven security and productivity solutions, along with its wholly owned subsidiary, Robotic Assistance Devices, Group (RAD-G), has signed six additional remote video monitoring clients for SARA (Speaking Autonomous Responsive Agent), the Company’s multiple award-winning agentic AI platform for remote video monitoring. This follows the Company’s announcement on October 8 of four initial monitoring clients and brings the total number of monitoring centers now engaged with SARA to ten, solidifying RAD-G’s dominant position as adoption of AI-powered automation accelerates across the industry. Additional client commitments These additional client commitments follow the strong reception SARA received during the recent The Monitoring Association (TMA) Annual Meeting. The rapid growth in adoption highlights the industry’s recognition of SARA as the most advanced and effective AI platform designed specifically for remote video monitoring. “The remote video monitoring industry has forever changed,” said Steve Reinharz, CEO/CTO and founder of AITX and all RAD subsidiaries. “SARA is delivering the intelligence, consistency, efficiency, and cost reductions that operators have been seeking for years.” “This new platform allows monitoring companies to have a cost-effective solution to start tackling the billions of unmonitored cameras around the world today. Our vision is to have every camera monitored with responses as needed. It’s truly astounding the direction this is headed. For us, it’s SARA leading the way.” Continued expansion The Company expects continued expansion of its monitoring client base in the weeks ahead as additional centers move forward with SARA commitments and integrations. The Company anticipates announcing further client additions along with projected SARA license volumes as deployments progress and adoption scales across the remote video monitoring industry. As adoption accelerates, RAD-G continues to position SARA as the #1 agentic AI platform for security and remote monitoring. The Company remains focused on supporting its growing roster of monitoring clients while driving innovation and market pioneership across the broader AI-powered security sector. Redefining security and guarding services industry AITX, through its primary subsidiary, Robotic Assistance Devices, Inc. (RAD), is redefining the nearly $50 billion (US) security and guarding services industry through its broad lineup of innovative, AI-driven Solutions-as-a-Service business model. RAD solutions are specifically designed to provide cost savings to businesses of between 35%-80% when compared to the industry’s existing and costly manned security guarding and monitoring model. RAD delivers these cost savings via a suite of stationary and mobile robotic solutions that complement, and at times, directly replace the need for human personnel in environments better suited for machines. All RAD technologies, AI-based analytics and software platforms are developed in-house. Operations and internal controls The company’s operations and internal controls have been validated through successful completion of its SOC 2 Type 2 audit, which is a formal, independent audit that evaluates a service organization’s internal controls for handling customer data and determines if the controls are not only designed properly but also operating effectively to protect customer data. This audit reinforces the Company’s credibility with enterprise and government clients who require strict data protection and security compliance. Extensive expertise RAD is led by Steve Reinharz, CEO/CTO and founder of AITX and RAD, who brings decades of experience in the security services industry. Reinharz serves as chair of the Security Industry Association’s (SIA) Autonomous Solutions Working Group and as a member of the SIA Board of Directors. The RAD team also draws on extensive expertise across the sector, including Mark Folmer, CPP, PSP, President of RAD and Chair of the ASIS International North American Regional Board of Directors, Troy McCanna, former FBI Special Agent and RAD’s Chief Security Officer, and Stacy Stephens, co-founder of security robotics company Knightscope. Their combined backgrounds in security industry pioneership, law enforcement, and robotics innovation reinforce RAD’s ability to deliver proven, practical, and disruptive solutions to its clients. Prospective sales pipeline RAD has a prospective sales pipeline of over 35 Fortune 500 companies and numerous other client opportunities. RAD expects to continue to attract new business as it converts its existing sales opportunities into deployed clients generating a recurring revenue stream. Each Fortune 500 client has the potential of making numerous reorders over time. AITX is an innovator in the delivery of artificial intelligence-based solutions that empower organizations to gain new insight, solve complex challenges and fuel new business ideas. Through its next-generation robotic product offerings, AITX’s RAD, RAD-R, RAD-M and RAD-G companies help organizations streamline operations, increase ROI, and strengthen business. Simplicity and economics of patrolling AITX technology improves the simplicity and economics of patrolling and guard services and allows experienced personnel to focus on more strategic tasks. Customers augment the capabilities of existing staff and gain higher levels of situational awareness, all at drastically reduced cost. AITX solutions are well suited for use in multiple industries such as enterprises, government, transportation, critical infrastructure, education, and healthcare.


Expert commentary
The average business owner or investor has some kind of security precaution in place, especially in the after-hours when there are fewer deterrents to inhibit criminal activity. Security guards, video surveillance systems, motion sensor lights, or even just fake cameras placed around the property are some of the common options people choose. Future of overnight security Smart business owners are starting to realize, however, that some of these traditional security measures are becoming antiquated and no longer cutting. The now and future of overnight security is in remote guarding. Pioneered by companies like Los Angeles-based Elite Interactive Solutions, which was founded back in 2007, remote guarding is revolutionizing the overnight security business. Minimizing criminal activity Remote guarding is fast becoming the most popular choice among commercial end-user property owners Remote guarding utilizes a combination of cutting-edge technology, “digital guards,” highly trained security agents, and local law enforcement if and when necessary to minimize the potential of criminal activity. For those adequately enlightened to its overwhelmingly impressive crime prevention capabilities, remote guarding is fast becoming the most popular choice among commercial end-user property owners to secure and protect their investments. What Is Remote Guarding? Remote guarding is a revolutionary concept and increasing trend in security systems that utilize a combination of methods to effectively analyze potential threats to property. Cameras and/or other monitoring devices running highly advanced algorithmic software are installed in strategic areas or vulnerable places onsite and remotely located security agents are immediately notified of any activity within a designated perimeter of the property. A blend of AI, cybersecurity, and video analytics When properly deployed by an expert provider, the technology stack includes a proprietary blend of video analytics, artificial intelligence, cybersecurity, and more. Done right, “noise” is effectively filtered out, allowing agents to act on legitimate alerts and achieve zero false alarms communicated to first responders. Today, there are a lot of terms and descriptions tossed around about remote guarding, remote video, virtual guarding, etc., but those attributes must be present to represent the true definition of the offering and its many virtues. Realtime situational awareness Many systems have a two-way speaker that allows the security agent to give a verbal warning When specially trained security agents are alerted to trespassers, possible intruders, or other suspicious activity, they analyze the situation in real time and determine the necessary level of action. Many systems have a two-way speaker that allows the security agent to give a verbal warning, known as a voice-down, to the individual(s) that they are being watched. Most perpetrators, often believing the response is emanating directly from security personnel on the property itself rather than from a remote command center, flee immediately. However, if the threat persists, the security agent enlists local law enforcement to get on the scene. Customized remote guarding When properly deployed, remote guarding systems are also customized to specific properties. A team of consultants visits the client’s property to evaluate its vulnerabilities and where to best place cameras and/or other monitoring devices for system efficacy. Traditional Security Shortfalls According to Keith Bushey, a retired commander for the Los Angeles Police Department, there is much frustration between law enforcement officers and potential victims of crime due to the historically unreliable performance of traditional burglar alarm systems and central monitoring stations. He states about 90% of security-related calls are false alarms, a problem that has been well-documented through the years. Onsite challenges When a legitimate emergency does occur, the perpetrators have often already done their damage When a legitimate emergency does occur, the perpetrators have often already done their damage and/or escaped by the time law enforcement arrives. Onsite security guards are not the remedy either as they bring their own set of issues and challenges. Unexpected costs Traditional security systems can also have unexpected costs. The cost is not only in the security guards’ paycheck or the cost of the equipment itself. The cost comes when an actual incident occurs. In worst-case scenarios, the security guard(s) are injured, the business suffers inventory loss, and/or damage is sustained to the property. The medical and other costs for the security guard(s), the loss of inventory, property damage, deployment of law enforcement resources, and possible fallout of legal expenses all add up. Even in the best-case scenario, false alarm expenses incur if law enforcement is dispatched. These, among many others, are some of the primary issues that remote guarding resoundingly answers as a superior alternative. A Bounty of Benefits Remote guarding systems have been proven to cut costs and be more effective than traditional security systems. Even though the monthly monitoring costs of remote guarding are significantly higher than traditional intrusion detection system monitoring, the much higher effectiveness in crime reduction, elimination of false alarms, and augmenting or replacement of manned guards result in a substantially higher return on investment (ROI) to the end user. Easy tracking of threats The security cameras already have their image captured on record, making them easier to track down For example, case studies have demonstrated reduced security costs for clients by 60%, on average. These reductions have come from the costs of security staff, inventory, or property loss, plus saving money on insurance premiums and deductibles. The nature of remote guarding reduces the risk and costs of false alarms, with professional security agents able to determine an actual threat before law enforcement is called. In a rare instance when a perpetrator escapes before law enforcement arrives or can detain the individual(s), the security cameras already have their image captured on record, making them easier to track down and identify. Reduction of false alarms The significant reduction in false alarms is greatly appreciated by law enforcement, as it allows them to focus on real emergencies or crises. Better relationships are also developed between clients and law enforcement, as remote guarding systems are highly reliable in providing accurate and real-time information to officers as they approach the scene. In short, it assists law enforcement in doing their job more effectively, as well as more safely thanks to having eyewitness information before engaging in an active crime scene. Partnership When you combine the decreased cost with the increased efficiency and success rate, it is easy to see why many commercial end-user property owners across the country are making the shift to remote guarding. It’s also an outstanding opportunity for professional security dealers and integrators to partner with a remote guarding services provider to bring a superior solution to their end customers and pick up a recurring monthly revenue stream in the process.
It’s no secret that the data security sector is constantly changing. It has an annual CGR of about 12.3%. Future trends in data security Much of this has to do with the rise of cybercrime in recent years, with reports showing that cyberattacks happen as often as every 39 seconds. To combat the growing rate of cybercrime, data security has been on the rise. As we journey further into this era, it becomes evident that a spectrum of significant trends is molding the future of data security. This exploration delves into a selection of these trends, unraveling their importance and the potential implications they carry 1. AI security tools will increase Artificial Intelligence is also being used in the development of smart attacks and malware The introduction of Artificial Intelligence in the data security industry brought significant changes, especially in cybersecurity. AI has been the golden standard for face detection, natural language processing, automated threat detection, and automated security systems. Additionally, Artificial Intelligence is also being used in the development of smart attacks and malware, bypassing even the latest security protocols in data control. And as time progresses, AI security tools will flourish and dominate the scene. Let’s take a more in-depth look at three of the top AI security tools. Targeted attack analysis tool Manufacturers utilize targeted attack analysis tools to uncover targeted and stealthy attacks. Artificial Intelligence can be applied to the program’s capabilities, processes, and knowledge. For instance, Symantec launched this tool to combat the Dragon 2.0 attack in 2022. The phishing attack reprimanded multiple energy companies while trying to gain access to their operational networks. Targeted Attack Analysis Tools can analyze incidents and look for similarities from previous situations. They also help detect suspicious activities and collect all the necessary data to determine whether a specific action is malicious. Intercept X tool Results from the Intercept X Tool feature high accuracy and a low false positive rate Sophos, a British security hardware and software company, launched the Intercept X Tool. It engages a neural network that records and analyses data like a human brain. Sophos’ Intercept X Tool can extract features from a single file and perform a deep analysis. It detects malicious activities within 20 milliseconds. Plus, it’s also trained to work on bi-directional sharing and real-world feedback of threat intelligence. Results from the Intercept X Tool feature high accuracy and a low false positive rate. IBM Watson Technology IBM’s QRadar Advisor uses IBM Watson Technology, a unique AI tool for fighting cyber attacks. Artificial Intelligence can auto-investigate activities and indicators for potential exploitation or compromise. With cognitive reasoning, IBM Watson Technology can present critical insights to accelerate the response cycle. Security analysts can utilize this technology to search for threat incidents, reducing the risk of letting them fly under the radar. 2. Blockchain as a security solution It guarantees no points of failure or hackable entrances that can expose datasets inside the system Blockchain is a type of distributed ledger technology (DLT) that aims to establish trust within an untrusting ecosystem. Today it’s one of the most robust cybersecurity technologies in the industry. Blockchain utilizes a decentralized ledger system, but your team members can still gain access to transparent information in the cloud. Members can also record, pass along, and view necessary transactional data in the blockchain. The entire blockchain process maintains data integrity within the system while establishing trust among team members. It guarantees no points of failure or hackable entrances that can expose datasets inside the system. Cybersecurity, biometrics Cybersecurity primarily benefits from these features because blockchain can create a secure and robust wall between data and hackers. On top of that, blockchain ledgers can include biometrics like fingerprints and retina scans. These prevent hackers from accessing any private data. Because blockchain is decentralized, it also limits hackable data. Together with the technology’s record-keeping system, each node is provided insight into data manipulation exposing real-time cybercrime attempts. 3. Increased and widened access control Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data Access control is critical in data security. More than a valuable security tool, business leaders can use access control to regulate people accessing any given resource. A company with an IT security setting can control who has the liberty to edit certain files. One of the primary goals of access control is to minimize threats or attacks to organizations and businesses to keep people and data secure. Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data protection laws. Benefits The benefits of increased and widened access control include: Identifying who can access and control your data at specific time intervals. Protecting data from overwriting, accidental deletion, and malicious intent. User permissions that can be readily changed. Compliance and regulation with data privacy laws. Central management of access to data through a reporting portal or a dashboard. Multi-factor authentication Access control comes in various types and systems, so it’s critical to know the features of what you’re looking for. The most common type is multi-factor authentication or MFA. It involves multiple steps before logging in, requiring the user to enter other relevant information besides the password. Some other examples of information include biometrics, answering a security question, or entering a code sent to the user’s email address. Two-factor authentication, role-based access control Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession. Another type of access control is role-based access control. In this setup, only one individual can set up access guidelines and grant permissions to specific team members within an organization. 4. Greater use of the zero-trust security model The zero-trust security model is a framework that requires every user within and outside the organization to undergo authentication, authorization, and validation. These are all essential to ensure proper security configuration before access is granted to the company’s applications and data. A zero-trust model assumes that anyone can cause data breaches and that a traditional network edge is not taken into effect. Moreover, it addresses the following modern-day challenges: Hybrid cloud environments. Security of remote workers. Ransomware threats. This framework utilizes the combination of multiple advanced technologies, including: A risk-based multi-factor authentication. Endpoint security. Identity protection. Cloud workload technology. The zero-trust model uses all these innovative tools for system identification, user verification, access consideration, and system security maintenance. Constant validation and monitoring Enforcing strict policies and compliance with data privacy laws are also essential Additionally, it also considers data encryption, email security, and asset verification before establishing connections with applications. The architecture of a zero-trust framework requires constant validation and monitoring of the users and the devices they are using. Enforcing strict policies and compliance with data privacy laws are also essential. More importantly, the zero trust architecture requires all organizations to be aware of all their available services and accounts to gain complete control of data handling and manipulation. 5. Increased privacy regulations Privacy regulations and policies guide organizations in proper data control, handling, and security. These policies guide organizations in proper data control, handling, and security. As a responsible business owner, you must comply with these regulations to avoid legal issues. With cybersecurity attacks becoming common, expect increased and stricter privacy regulations to be released in the next few years. While current policies are still taken into effect, various modifications and adjustments will occur to compete with the rising numbers of data breaches, thefts, data loss, and more. California Privacy Rights Act (CPRA) Currently, the California Privacy Rights Act (CPRA) is the most comprehensive legislation on state data privacy. It only started to take effect on January 1, 2023. The CPRA introduces the following principles: Broad individual consumer rights. Significant duties of people who need to collect sensitive and personal information. Additional definitions of data privacy and security. An individual’s duties include releasing information about data collection to concerned data subjects and proper access, correction, and deletion of information. Final thoughts 2023 is a big year for data security. Trends such as increased adoption of zero-trust policies, a greater reliance on AI security tools, and the implementation of blockchain as a security solution are all things we expect to see shortly. Staying up-to-date with these trends is important for keeping your business current and ensuring that you’re adhering to new and changing regulations. Doing so can give you an edge over the competition and keep you out of legal hot water.
GSX 2023 marks a poignant moment for the security industry as an increasingly complex risk landscape converges with the acceleration of technology innovation. Emerging from this environment are three key trends that will dominate the conference and the future of the security industry: (i) the adoption of AI, (ii) the use of predictive analytics, and (iii) a hybrid global and local risk management approach. As Chief Security Officer of Crisis24, a GardaWorld company, I regularly advise clients on how these trends are evolving and impacting their security and risk management approach. Here’s how we can expect to see them discussed at the show next month: Trend 1: Artificial intelligence is the new industry standard. AI is this year's buzzword. While AI is not new to the industry, this year it has become a standard to operate with AI being adopted or expanded more ubiquitously. Legacy AI-enhanced security offerings that have been years in the making are becoming more advanced and are being integrated into expert analyst teams to leverage the best of both man and machine. Limitations AI augments the data processing ability; however, human-led intelligence is still necessary AI can generate unparalleled levels of data and insights, but it also has its limitations. AI does not have the emotional intelligence that can influence decision-making. For instance, our Crisis24 analyst teams know that every one of the intelligence alerts they provide to leadership may save a life or protect a business. AI augments the data processing ability; however, human-led intelligence is still necessary to effectively elevate knowledge of those threats through an organization to incite action. Trend 2: Predictive analytics powered by AI will transform security operations. Predictive analytics enabled by AI will allow for more precise planning and execution of true emergency management. Those living or operating in conflict zones must be ready to spring into action and predictive analytics can help better evaluate risks, threat levels, and the probability of certain events. When I served in Iraq in 2003, our greatest challenge was operating in an unpredictable environment and navigating the many unknown threats. With these large-scale threats, it was difficult to account for the vast array of variables involved and ensure that all parties were protected. Broad and instant visibility Predictive analytics provides broad and instant visibility into numerous potential outcomes, impacts, and mitigation strategies for a wide variety of threats. When dealing with risks that are constantly evolving and quickly accelerating, the insights from predictive analytics can have a direct impact on risk management, mitigation strategies, and preparedness levels. Predictive analytics can anticipate the ripple effect that threats can have on organizations, their people, and their assets and enable security teams to plan. Trend 3: Risk mitigation is increasingly both global and hyper-local. A company’s workforce is often scattered across the country or the world, working from home or on the go Remote work and a flood of 24/7 data sources have driven demand for timely, accurate, and hyper-local intelligence. Where before an organization may have had a handful of facilities around the world where its employees gathered, now a company’s workforce is often scattered across the country or the world, working from home or on the go. Preventive mitigation steps To keep their people and assets safe, business pioneers need to know what’s happening in all corners of the globe, while also easily accessing details on what is happening at the street corner level. How a business takes care of its people, including anticipating risks and taking preventive mitigation steps as well as responding quickly in the face of threats, can directly affect its reputation. Every company is in the business of safety and security when it comes to looking after its people on a global, national, and increasingly hyper-local scale.
Security beat
Companies at GSX 2023 emphasized new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the security market. Today, more than half of the company’s lineup supports AI at the edge so the customer has a wide choice of form factors when seeking to leverage the feature set. AI processing relay, extended warranty i-PRO is increasing their warranty period from 5 to 7 years, which could be a lifetime warranty in some cases I-PRO also has an “AI processing relay” device that accepts non-AI video streams and applies edge analytics. AI has progressed from a high-end technology to a feature available in a variety of cameras at different price points. i-PRO is also increasing its warranty period from 5 to 7 years, which could be a lifetime warranty in some cases depending on a customer’s refresh schedule and lifecycle management. Active Guard, MonitorCast The company’s video management system (Video Insight) is continuing to build new features including “Active Guard,” an integrated metadata sorter. Their access control platform, MonitorCast, is a Mercury-based solution that is tightly integrated with Video Insight. Their embedded recorders now have PoE built in. “We can move at a faster pace to fill out our product line since leaving Panasonic,” says Adam Lowenstein, Director of Product Management. “We can focus our business on adapting to the market.” Emphasis on retail and other verticals Shoplifting is a timely issue, and retail is a vertical market that got a lot of attention at GSX 2023. “We see a lot of retailers who are primarily interested in protecting employee safety, but also assets,” says Brandon Davito, Verkada’s SVP of Product and Operations. “Shrinkage is a CEO-level priority.” “Retailers are getting more engaged with security posture, instead of letting perpetrators walk,” Davito adds. Intrusion detection Verkada has an intrusion product that will notify a central station if there is an alarm On the alarm side, Verkada has an intrusion product that will notify a central station if there is an alarm, and operators can review videos to confirm the alarm. Other capabilities seeking to discourage trespassers include sirens, strobes, and “talkdown” capabilities. International expansion Verkada continues to expand internationally with 16 offices in all, including Sydney, Tokyo, and London. The core value proposition is to enable customers to manage their onsite infrastructure more simply, including new elements such as PTZ cameras, intercoms, and visitor management. Verkada emphasizes ease of use, including a mobile application to allow access to be managed across the user base. Forging partnerships “We are committed to the channel and industry, and we continue to build relationships and expand our reach,” says Davito. Among the industry relationships is a new partnership with Convergint, which was hinted at during the show and announced later the same day. They are also expanding their partnerships with Schlage, Allegion, and ASSA ABLOY. Working with other verticals They offer new features for K -12 schools, and a new alarm platform is easier to deploy and manage Verkada has also found success across multiple other verticals, notably healthcare, where they integrate with an electronic medical records system. They offer new features for K-12 schools, and a new alarm platform is easier to deploy and manage. They are integrating wireless locks to secure interior doors in schools, looking to secure the perimeter, and installing guest management systems. Transitioning the Mid-Market to the Cloud Salient is squarely focused on the “mid-market,” a large swath of systems somewhere between small businesses and enterprise-level systems. Pure cloud systems are not as attractive to this market, which has a built-out infrastructure of on-premise systems. Adding a camera to an existing system is easier and less expensive than tying it to the cloud. Benefits of cloud It’s a market that may not be ready for pure cloud, but there are benefits to be realized from adding a cloud element to existing systems. “We are continuing to augment our premise-based solutions with added cloud capabilities and flexibility,” says Sanjay Challa, Salient’s Chief Product Officer. The feedback Salient hears from their customers is “I want to own my data.” The hybrid cloud approach offers the right mix of control, flexibility, and unit economics. Cloud add-on capabilities We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive" Cloud add-on capabilities include bringing more intelligence about system operation to the user via the cloud. Over time, Salient expects to sell more cloud-centric offerings based on feedback from integrators and customers. “We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive over time,” says Challa. Vaidio AI technology Salient seeks to be a transition pioneer to help customers realize the path to the cloud. Their approach is “crawl, walk, run,” and helping customers make the transition at each stage. Salient has added AI to its product offering, incorporating Vaidio AI technology from IronYun into a powerful suite and broad array of on-premise analytics, which are gaining traction. The seamless approach makes it easy for customers to embrace AI analytics, although Salient remains broadly committed to open systems. Addressing ‘Soft’ Features for Integrators AMAG is in the process of enhancing its product line with the next generation of access control panels. However, “product” is just part of the new developments at AMAG. In addition to “hard” features (such as products), the company is looking to improve its “soft” features, too; that is, how they work with the integrator channel. Integrator channel Rebuilding a process to make your organization more efficient, is relatively easy; it just takes a lot of persistence" “We have the depth of our legacy customer base we can learn from, we just need to close the feedback loop quicker,” says Kyle Gordon, AMAG’s Executive Vice President of Global Sales, Marketing, and commercial Excellence, who acknowledges the value of reinstating face-to-face meetings after COVID. “We are laser-focused on nurturing our integrator channel,” he says. “Developing new features takes time, but rebuilding a process to make your organization more efficient, that’s relatively easy; it just takes a lot of persistence,” says Gordon. More cohesive internal communication is another useful tool, he says. Disrupting the cloud based on price Wasabi is working to make cloud applications less expensive by offering a “disruptive” price on cloud storage, $6.99 per terabyte per month (80% less than hyperscalers). Contending “hyperscalers” like AWS are charging too much for cloud storage, Wasabi is using its own intellectual property and server equipment co-located in data centers around the world. Wasabi sells “hot cloud storage,” which refers to the fact that they only have one tier of storage and data is always accessible. In contrast, a company such as AWS might charge an “egress fee” for access to data stored in a “colder” tier. Cloud storage “We saw that several video surveillance companies had not yet adopted cloud storage, and we saw an opportunity to make it easy to use,” said Drew Schlussel, Wasabi’s Senior Director of Product Marketing. “We just install a little bit of software that allows them to store data in the cloud and bring it back from the cloud.” Performance, protection (cybersecurity), and price Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies such as Genetec and Milestone. Emphasizing performance, protection (cybersecurity), and price, their data centers are certified to SOC 2 and ISO 27001 standards. Faster throughput for weapons detection Xtract One is a young company focusing on weapons detection in a time of accelerated concern about gun issues post-COVID. Founded in Canada and based on technology developed at McMaster University, Xtract One has found a niche in providing weapons detection at stadiums and arenas. These customers already have budgets, and it is easy to shift the money to a newer, faster technology. Madison Square Garden in New York City is among its customers. Cost savings solution Xtract One can increase throughput to 30 to 50 people per entrance per minute (compared to 5 to 6 people per minute when using metal detectors). The solution doesn’t require anyone to empty their pockets and the system alarms on items beyond guns and knives. Using Xtract One allows customers to reduce the number of screening lanes and security staff, providing additional cost savings, all while getting fans through the screening process in half the time. Purpose-built sensors The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties In addition to stadiums and arenas, Xtract One, formerly Patriot One, is also getting “inbound” interest from schools, hospitals, manufacturers, and other verticals that makeup 50% of their business. “We’re on a rocket ride, mainly because the weapons issues are not going away,” says Peter Evans, CEO and Director at Xtract One. The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties, all correlated by an AI engine. Providing early warning of violence ZeroEyes is another company focused on weapons detection. Their AI gun detection system works with video images to identify if someone is “brandishing” (carrying) a weapon. In other words, the system does not detect concealed weapons. Identifying someone carrying a weapon provides early warning of a possible violent act. Increased response with AI-enables images Images are identified by AI and sent to a monitoring center where a human confirms the image before contacting first responders. Knowing the location of a shooter enables staff to lock entry points, move people to safety, and direct first responders. The company was founded to leverage existing camera views to stop mass shootings and gun violence by reducing response times.
New buzzwords were abundant in the articles that generated the most clicks on our website in 2022. From the metaverse to the Internet of Things, from frictionless access control to artificial intelligence (AI), the topics most popular among our site’s visitors were at the cutting edge of change and innovation in the physical security marketplace. Here is a review of the Top 10 Articles of 2022, based on reader clicks, including links to the original content: Metaverse will promote collaboration and enable more efficiencies for security Metaverse is a familiar buzzword currently, but few people grasp what it means. In the simplest terms, the metaverse is an online “place” where physical, virtual, and augmented realities are shared. The term, Metaverse, suggests a more immersive online environment that combines elements of augmented reality (AR) and virtual reality (VR). For the physical security industry, the looming creation of a complex online environment offers possibilities and challenges. Establishing identity will be a central principle of the metaverse, and various biometrics are at the core of ensuring the identity of someone interacting in the virtual world. Cybersecurity elements are also key. On the benefits side, the security market is already taking advantage of technologies related to the eventual evolution of the metaverse. For example, the industry has deployed AR to provide information about a door lock’s status on a screen, headset, or smart glasses as a patrolling guard walks by. What are the security challenges of the transportation industry? Because transit agencies rely on several IoT devices, they get exposed to higher cybersecurity risks Rapid technological advancement, increasing urbanization, and the growing expectations of commuters and governments are pressuring transit industry players to modernize. Commuters, urban planners, first responders, and other stakeholders want to use transit data to support their decision-making. Transit agencies’ security and operations teams need closer collaboration to stay ahead. However, for many years, most transit agencies have relied on siloed, proprietary systems. Because transit agencies rely on an ever-growing number of Internet of Things (IoT) devices, they also get exposed to higher cybersecurity risks as there are more network access points to manage. The future is here: ADT’s innovation lab evaluating robots and indoor drones New robots and indoor drones for security applications are on the horizon, based on the work of ADT Commercials’ Innovation Lab, which is evaluating the latest technologies’ value to customers and some typical use cases. The ideal use of humanoid robots is to perform jobs that are considered repetitive, dirty, dangerous, and/or mundane. In security, that describes most security guard positions. As the name implies, autonomous indoor drones are focused on flying indoors versus the outdoor environment, which is heavily regulated by the U.S. Federal Aviation Administration (FAA). Flying autonomously indoors not only eliminates FAA oversight but also will enable ADT Commercial to offer another choice to customers to further reduce their dependencies on and costs of human guards. Innovative security: the key to business efficiency, cost savings, and more Organizations have shifted business focus countless times since the onset of the pandemic. While many leaders have been primarily concerned with the immediate health and safety of their customers and employees, 2022 has given rise to a new trend. More than ever, business leaders are seeking security solutions that increase operational efficiency and cost savings as well as improve logistics and business insight. As working environments become more complex, organizations looking to drive higher productivity and profitability margins should consider security upgrades that prioritize integrated analytics and automation. Shoplifting today is more sophisticated, and so are the tools to fight it One tool to fight shoplifting is analytics, which can be used to determine where shrink is occurring Shoplifting is often viewed as petty theft by individuals, but that is not always the case. Overall, shoplifting is becoming more sophisticated and coordinated. Traditional “shoplifting” has two major differences when compared to organized retail crime (ORC). The differences are numbers and motivation. ORC consists of groups working together to monetize theft, very different than an individual taking an item they need. One tool to fight to shoplift is analytics, which can be used to determine where shrink is occurring. Understanding where crimes take place helps retailers make strategic decisions about where to place their loss prevention efforts. Oosto offers 10 reasons to switch to frictionless access control in commercial buildings Access control for buildings is nothing new. It’s only in recent years that the urgency to implement smarter, more efficient, and more convenient forms of access control has increased, in the context of public and private sector digital transformation. Upheavals from the COVID-19 pandemic have forced organizations to re-think, pivot, and invest in new technology solutions that will incorporate Artificial Intelligence (AI) and Machine Learning, to gain speed in their operations, glean actionable insights from their video analytics, and enhance productivity with their teams. Which security trend is here to stay? Technologies and trends in the security marketplace come and go with some regularity. But how can you tell which trends are gaining traction and which amount to “the flavor of the month.” For example, while many physical security departments were hesitant to consider cloud-connected solutions in the past, they now better understand the benefits these solutions bring and how they can help them utilize their resources to achieve business goals while minimizing overall operational complexity. Other technologies mentioned in the article include mobile credentials, AI-based analytics, video management systems, cybersecurity, and a new emphasis on data. What do these technology trends have in common? They are opening new possibilities for greater system efficiency and functionality. In short, they are playing a role in transforming our industry. GSX 2022 reflects changing technologies and evolving role of security The role of the security director increasingly will encompass facets of cybersecurity and physical security GSX 2022 in Atlanta highlighted the changing role of security in the enterprise. The role of the security director increasingly will encompass facets of cybersecurity as well as physical security. Transitioning to an operation that incorporates both disciplines requires a workforce that embraces education and building new skills. Education and the opportunity to build new skills are evident everywhere at GSX, including in the hundreds of education sessions and also in the knowledge shared on the show floor in the exhibit hall. Consolidation changing the face of the security market Consolidation is a dominant trend in the security marketplace. Large companies typically swallow up smaller companies as a means of expanding both their technology portfolios and their geographic reach. Sometimes a big fish is swallowed up by an even bigger fish. Despite the pandemic and resulting economic challenges, the security market has continued to be a desirable environment for both big players and startups, which then provide abundant acquisition targets for larger companies. This article highlighted recent mergers and acquisition news. Six trends at the intersection of video and AI Video has evolved beyond the capabilities of advanced imaging and performance to include another level: Artificial Intelligence. Video imaging technology combines with AI, delivers a wealth of new data, not just for traditional physical security applications, but for a much deeper analysis of past, present, and even future events across the enterprise. This is more than a big development for the physical security industry; it is a monumental paradigm shift that is changing how security system models are envisioned, designed, and deployed. Much of the heightened demand for advanced video analytics is being driven by six prevalent industry trends.
The Global Security Exchange (GSX 2022) in Atlanta in September 2022 is the latest example of the energetic post-COVID resurgence of security trade shows. On the vibrant show flow, discussions centered on topics such as the security industry’s need for more employees and the lingering impact of a months-long supply chain crisis. Against a backdrop of continuing industry challenges, exhibitors and attendees were diverted by a wealth of new opportunities as the industry rebounded. Several major players had big product announcements at GSX 2022 in Atlanta. Manufacturers unveil the latest technology The big news at Genetec was “5.11.” That’s the newest version of Security Center, which is “all in,” i.e., providing everything Genetec offers in a single “unified” platform. The unified approach streamlines the process for systems integrators, makes quotes easier, and adds value for customers. Standard, Pro, and Enterprise versions provide video, access, and LPR “right out of the box.” Genetec is also launching a new web and mobile client for the “next generation operator.” Paid intern program Kyle Hurt says the security industry’s biggest challenge is attracting personnel Kyle Hurt, Genetec’s Senior Sales Director, North America, says the security industry’s biggest challenge is attracting personnel (even more challenging that the supply chain.) Genetec’s response is a robust paid intern program, welcoming 120 interns into various departments for a full semester. The program helps to feed Genetec’s need for new talent. “You can’t coach passion,” said Hurt. WiseNet Edge Hanwha Techwin introduced a “serverless camera” at GSX 2022, named the WiseNet Edge. It is a video camera with a built-in solid-state hard drive for storage. The camera can store its own video and take in other camera feeds. In effect, it operates like an NVR but is less expensive and with an internal solid-state drive. Video can be viewed through a cloud browser, and Hanwha’s WAVE software, loaded on the camera, enables the management of several cameras at a site. High-res video is stored inside the camera, and any information can be shared with the cloud according to the needs of the application. i-PRO Mini i-PRO launches its own Video Insight video management system and MonitorCast access control i-PRO has fully transitioned away from Panasonic and is charting its own ambitious future path. Seeking to be “bold, trusted, and flexible,” the company is releasing a raft of new products, filling in previous gaps in the line, and bringing forward new innovations, including a full complement of AI. In addition to hardware, they have their own Video Insight video management system and MonitorCast access control, which was part of the Video Insight acquisition in 2015. An i-PRO Mini is a tiny camera, smaller than a smartphone. All cameras are NDAA compliant. People are coming together “The show has been phenomenal,” said Josh Letourneau, Chief Commercial Officer, Prosegur USA. “It’s very nice to see that people are coming back. After the pandemic, we are finally in a position of coming together. Lots of organizations are coming to see us.” Intelligence-led risk management Prosegur is a global company looking to expand aggressively in the United States, creating multiple “metropolitan service areas,” where the company’s fully integrated offerings are available. What makes the company unique is its “intelligence-led risk management,” says Josh Letourneau, adding “It’s more than AI, it’s about human intelligence, too." Prosegur sees evolution and growth opportunities in the U.S. market. “We are one of the largest companies no one has heard of,” adds Letourneau. “The show seems as back to normal as possible,” said Keith Bobrosky, President of Delta Scientific, who attended the show although his company did not exhibit, adding “There seems to be a generally positive spirit about the show this year.” Physical security protocols Bobrosky sees data centers as the next big market for his company’s vehicle barriers Bobrosky’s company has worked aggressively to avoid the impact of supply chain issues, ordering plenty of extra inventory to avoid the possibility of a part running out of stock. “We got ahead of it and are past the worst of it,” he said. Bobrosky sees data centers as the next big market for his company’s vehicle barriers. “The government will mandate physical security protocols for cybersecurity locations because they house data that affects national security,” he says. Robots and indoor drones ADT Commercial highlighted robots and indoor drones for security apps at their booth. The newest versions of the humanlike robots offer extra padding, more fluid movement, and 360-degree viewing for a better virtual reality (VR) experience, including better peripheral vision. Robots can operate for four hours without a charge and “know” when to return to the charger (to “top off” every hour). Fully autonomous indoor drones can also replace guards, flying near the ceiling and generally after business hours. The use of either robots or drones can lower costs when compared to hiring human guards. Varied uses for canines in security Glen Kucera, Chief Executive Officer, MSA Security, highlighted the capabilities of canines for explosives and firearms detection. “People don’t realize the flexibility of what they can do,” he said. Kucera says canines provide a sophisticated solution to address the escalating active shooter and criminal threat. MSA Security was acquired last year by Allied Universal, adding to the company’s varied offerings for threat detection and management. Rather than individual products, Allied Universal’s emphasis at the show was on bringing solutions together. Their message: Risk is multi-dimensional and different from one client to the next. Access control Access control needs to develop more modern interfaces to compete with new technology companies AMAG’s news at the show included a new president, David Sullivan, who highlighted AMAG’s role as one of the “last independent access control companies.” He said, “The beauty of AMAG is its installed base and loyal integrator channel.” Sullivan sees changing trends in how office space is managed in the wake of the pandemic. More workplace management applications will emerge, with one of the elements being access control. Access control also needs to develop more modern interfaces to compete with new technology companies entering the market. An encouraging sign is that AMAG had its best year ever in 2021. Orion Entrance Control Orion Entrance Control showed off one of its modern new turnstiles at the RealNetworks/SAFR booth at GSX 2022. The turnstile incorporates an access control module from Elatec to update and expand card reader functionality. Using the module streamlines Orion’s processes and avoids having to update a customer’s readers individually. The turnstile at GSX also incorporated a facial recognition system from SAFR, which could be used instead of, or in addition to, the access control reader. Balancing the cloud and on-premise systems Salient Systems is looking to balance the use of on-premise and cloud systems and emphasize data instead of video. Rather than a single market, Salient sees security as a variety of smaller markets, each focused on different needs. Salient’s customers are typically larger and have multi-site deployments with thousands of cameras. On-premise systems appeal here because they offer an element of control. Open-platform APIs Internal teams at customer sites are seeking out and finding new ways to leverage the data from video systems “People have a keen interest in control and ownership of their data,” says Sanjay Challa, Chief Product Officer, Salient Systems. Internal teams at customer sites are seeking out and finding new ways to leverage the data from video systems, and some of the uses fall outside the traditional “security” market. Open-platform application programming interfaces (APIs) enable more integration with various systems, and broader applications enable customers to leverage budgets from other stakeholders in an organization. Add-on services “They’re unwilling to shift the entire solution to the cloud, but they want to leverage cloud technologies,” says Challa. For Salient, a cloud system provides remote access to monitor and service video installation remotely. “We enable the integrator to reach into your system to provide a higher level of service,” says Sanjay Challa. He concludes, “Our add-on services bring the best of the cloud to on-premise systems, and integrators don’t have to roll a truck to solve a problem with the system. We are focused on helping integrators succeed.”
Case studies
Kitakobushi Resort operates multiple distinctive properties in Shiretoko, Hokkaido – a UNESCO World Natural Heritage site since 2005. Their portfolio includes a large resort hotel overlooking the Sea of Okhotsk, a forest retreat, private cottages, and a historic hotel with over 60 years of operation – all showcasing the region’s stunning landscapes and local charm. As Shiretoko grew in popularity, maintaining a consistently safe and comfortable environment across multiple dispersed properties became increasingly important. This demand prompted a comprehensive review of the resort’s aging surveillance infrastructure. Challenge Towards smarter, unified, and more efficient video management As visitor numbers continued to rise, expectations for safety and operational efficiency increased across Kitakobushi Resort’s dispersed properties. The limitations of the resort’s aging, siloed surveillance system became particularly evident at its two flagship properties: Kitakobushi Shiretoko Hotel & Resort and KIKI Shiretoko Natural Resort – where modernization became a strategic priority. The resort faced three critical challenges: Upgrading aging infrastructure: The resort’s existing cameras and NVR had served reliably for many years, but an upgrade became essential to maintain smooth operations. Unifying scattered monitoring operations: With several properties to oversee, each facility’s video was previously monitored separately, limiting operational efficiency and making management more complex. The resort wanted to enable remote monitoring, allowing staff to view live footage from anywhere without needing to be on-site. Maximizing coverage while controlling costs: Comprehensive coverage across facilities required numerous cameras spanning public spaces, parking areas, and back-of-house operations, yet keeping the system cost-effective remained an important consideration. The resort sought a solution that could modernize infrastructure, unify operations, and maximize value while achieving smart upgrading within budget constraints. Solutions Smart video integration for a safer, more connected resort As a global pioneering security solution provider, VIVOTEK was selected for its proven reliability, performance, and strong local support in Japan. The solution deployed 58 VIVOTEK network cameras across key areas at Kitakobushi Shiretoko Hotel & Resort and KIKI Shiretoko Natural Resort, with centralized management through two NVR-Pro units powered by System K’s SK VMS. Strategic camera deployment included: SD9161-H (17 units): This PTZ camera, installed throughout hotel interiors and parking areas, offers 10x optical zoom and flexible pan-tilt-zoom capabilities. Staff can effortlessly monitor wide areas and zoom in on points of interest in real time — all without leaving the office. FD9369 (41 units): Compact and discreet, this dome camera was installed mainly indoors, preserving the resort’s natural ambiance while delivering reliable, cost-effective performance. By unifying all 58 cameras into a single management platform, the resort gained complete visibility across both properties. The centralized system streamlines daily monitoring, reduces patrol labor, and enables faster response to on-site needs. Staff can now monitor multiple facilities from a single interface, significantly improving overall operational efficiency. Result and customer feedback Making resort operations smarter and guest experiences safer The VIVOTEK solution has transformed resort operations, enabling centralized monitoring, real-time flexibility, and enhanced safety. Key improvements Streamlined multi-facility management: Staff can now monitor multiple properties from a single interface. This unified system eliminates the need to check each facility separately, simplifying operations and boosting overall efficiency. Flexible monitoring with PTZ cameras: The SD9161-H PTZ cameras allow staff to pan, tilt, and zoom in real time from any location, reducing the effort required for routine monitoring. Seamless aesthetic integration: The compact FD9369 dome cameras blend discreetly into the resort’s interior, preserving the natural ambiance while delivering reliable performance at a cost-effective price. Enhanced safety and guest experience: By combining advanced video technology with centralized management, the resort ensures a safe, seamless, and welcoming experience for both staff and guests. Customer insights "Based on System K’s recommendation, we explored and selected VIVOTEK due to its stability, intuitive interface, and excellent value. VIVOTEK offers strong warranty support, reliable performance, and an easy-to-manage system. Integrating all cameras with the NVR-Pro platform allows us to manage multiple properties in one place, greatly improving daily operations," Chief Digital Officer (CDO), Kitakobushi Resort. "VIVOTEK offers an impressive balance of high functionality and affordability. With strong local support and ongoing firmware updates, the system continues to deliver reliability and satisfaction," Sales Representative, System K (VIVOTEK Distributor).
Interface Systems, a pioneering managed service provider delivering business security, actionable insights, and purpose-built networks for multi-location businesses, announced the successful completion of a major security upgrade for Bethesda Community Church and Bethesda Christian School in Fort Worth, Texas. Serving more than 530 students from preschool through 12th grade, Bethesda Christian School is recognized among the top private schools in Texas. Modern safety and security systems High level of activity required modern safety and security systems to protect students Between church services, school operations, and community events, the multi-building, 26-acre campus welcomes hundreds of people daily. This high level of activity required modern safety and security systems to protect students, staff, and parishioners while simplifying daily operations. Bethesda’s aging fire alarms, intercoms, and CCTV system were increasingly unreliable, creating false alarms and communication challenges. To address these concerns, the church turned to Interface to modernize its infrastructure. Deployed an integrated solution Interface designed and deployed an integrated solution that included: Fire Alarm System: Replacing the outdated system with a modern fire alarm system that communicates urgency effectively without causing unnecessary panic, particularly important for schoolchildren. Managed Access Control: Introducing a modern system that makes it easier for administrators to manage entry to the campus. The cloud-based setup means they can grant or restrict access remotely, without having to manage complex on-site servers. Video Surveillance Upgrade: Installing a 64-channel IP camera system on the new school building, with expansion capability to replace legacy analog cameras over time. The system provides remote monitoring and allows staff to verify alarms with live video before responding, helping to reduce unnecessary dispatches. Intercom and Paging: Replacing the outdated intercom with a flexible IP-based system that supports school bell scheduling, room-to-room communication, and all-campus announcements. It also integrates with access control, giving administrators a simple way to manage visitor entry. Remote access to cameras and alarms The installation was carefully phased to minimize disruption to classes and worship services “The new system is effective. It gets the point across that it’s time to evacuate, but it doesn’t create panic, especially among the kids,” said Rick Campbell, Facilities Manager at Bethesda Community Church. “Having remote access to cameras and alarms has been a huge help.” The installation was carefully phased to minimize disruption to classes and worship services. “Interface worked around the kids and kept us up and running during installation,” Campbell added. “The integration was seamless, and now everything is running smoothly.” Interface’s upgrades With Interface’s upgrades, Bethesda has significantly reduced false dispatches, streamlined communication across the campus, and gained the ability to scale its systems for future growth. “Initially, we were unsure about the cost, but the investment has been well worth it,” Campbell concluded. “I’d recommend Interface to other churches without hesitation.”
Artificial Intelligence Technology Solutions, Inc. (the Company), along with its wholly owned subsidiary Robotic Assistance Devices, Inc. (RAD), announced the publication of a new case study detailing the successful deployment and performance of RAD’s SARA platform at OneWatch, an Indiana-based monitoring center and a RAD authorized dealer. The release of this case study follows a recent presentation during The Monitoring Association’s Virtual Product Review (VPR) series, titled “Agentic AI Is Transforming Remote Monitoring Operations, Are You Ready?” SARA RVM solution SARA enabled OneWatch to reduce false alarms by 85%, accelerate response times The newly published case study, titled “SARA, RAD’s Agentic AI Monitoring Platform, Drives Efficiency at OneWatch,” explores how OneWatch addressed staffing challenges, operator fatigue, and alarm overload by deploying RAD’s SARA RVM solution. Designed to automate remote video monitoring, SARA enabled OneWatch to reduce false alarms by 85%, accelerate response times, and maintain service quality without increasing headcount. The results illustrate how AI-driven automation can directly support GSOC operations, helping organizations scale without compromising performance. Seamless integration OneWatch CEO Austin Smith cited SARA’s seamless integration with existing infrastructure OneWatch CEO Austin Smith cited SARA’s seamless integration with existing infrastructure and its ability to autonomously detect, verify, and respond to incidents as decisive factors in OneWatch’s adoption of SARA. “SARA has completely transformed how we approach security monitoring,” Smith said. “Our operators are no longer overwhelmed by false alarms and can focus on genuine security threats.” The platform’s autonomous voice-down capabilities and detailed reporting tools now serve as a foundation for OneWatch’s daily operations and long-term growth strategy. GSOC operations RAD’s SARA platform shifted OneWatch’s GSOC operations from continuous human surveillance to AI-supported exception management. Rather than manually monitoring hundreds of feeds, operators now rely on SARA to surface verified incidents and provide real-time context. This transition has improved operator morale, reduced burnout, and created a more efficient work environment. In addition to filtering nuisance alerts, SARA has demonstrated its value in deterring intrusions, preventing asset loss, and delivering faster incident resolution. Autonomous responses At a healthcare facility, the system detected suspicious activity near a restricted area The case study details specific incidents where SARA initiated autonomous responses that led to positive outcomes. At a healthcare facility, the system detected suspicious activity near a restricted area, which triggered immediate notifications, enabling on-site personnel to intervene before property was removed. In another event at a construction site, SARA’s voice-down feature deterred a theft in progress while simultaneously alerting OneWatch and local law enforcement, resulting in a successful intervention without delay. Monitoring industry Steve Reinharz, CEO/CTO and founder of AITX and RAD, emphasized the significance of the SARA deployment’s impact on the broader monitoring industry. “In over two decades of innovation in this sector, I have never witnessed such immediate recognition and adoption of a new technology as we’ve seen with SARA,” Reinharz said. “Monitoring centers are not just interested, they’re acting. The results at OneWatch reflect what is possible when organizations are ready to let AI take a leadership role in their operations.” Success of SARA The success of SARA at OneWatch signals a shift in how remote monitoring centers can evolve to meet growing demand without relying solely on human resources. By integrating agentic AI into daily operations, OneWatch not only improved internal efficiency but also strengthened its competitive position in the market. With SARA handling routine detection and engagement, the company has redefined operator roles, transforming them into AI Surveillance Analysts focused on incident resolution, client communication, and strategic oversight. RAD is actively working to bring similar outcomes to its network of nearly 100 authorized dealers and GSOC operators across the country. By equipping partners with SARA, the Company aims to transform remote monitoring at scale, empowering more organizations to lower costs, reduce false alarms, improve response times, and enhance service delivery through agentic AI.
Artificial Intelligence Technology Solutions, Inc., along with its wholly owned subsidiary Robotic Assistance Devices, Inc. (RAD) announces the publication of a new case study detailing the successful deployment and performance of RAD’s SARA platform at OneWatch, an Indiana-based monitoring center and a RAD authorized dealer. The release of this case study follows a recent presentation during The Monitoring Association’s Virtual Product Review (VPR) series, titled “Agentic AI Is Transforming Remote Monitoring Operations, Are You Ready?” RAD’s SARA RVM Designed to automate remote video monitoring, SARA enabled OneWatch to reduce false alarms The newly published case study, titled “SARA, RAD’s Agentic AI Monitoring Platform, Drives Efficiency at OneWatch,” explores how OneWatch addressed staffing challenges, operator fatigue, and alarm overload by deploying RAD’s SARA RVM solution. Designed to automate remote video monitoring, SARA enabled OneWatch to reduce false alarms by 85%, accelerate response times, and maintain service quality without increasing headcount. The results illustrate how AI-driven automation can directly support GSOC operations, helping organizations scale without compromising performance. Seamless integration OneWatch CEO Austin Smith cited SARA’s seamless integration with existing infrastructure and its ability to autonomously detect, verify, and respond to incidents as decisive factors in OneWatch’s adoption of SARA. “SARA has completely transformed how we approach security monitoring,” Smith said. “Our operators are no longer overwhelmed by false alarms and can focus on genuine security threats.” The platform’s autonomous voice-down capabilities and detailed reporting tools now serve as a foundation for OneWatch’s daily operations and long-term growth strategy. AI-supported exception management Operators now rely on SARA to surface verified incidents and provide real-time context RAD’s SARA platform shifted OneWatch’s GSOC operations from continuous human surveillance to AI-supported exception management. Rather than manually monitoring hundreds of feeds, operators now rely on SARA to surface verified incidents and provide real-time context. This transition has improved operator morale, reduced burnout, and created a more efficient work environment. In addition to filtering nuisance alerts, SARA has demonstrated its value in deterring intrusions, preventing asset loss, and delivering faster incident resolution. The case study details specific incidents where SARA initiated autonomous responses that led to positive outcomes. Successful intervention At a healthcare facility, the system detected suspicious activity near a restricted area, which triggered immediate notifications, enabling on-site personnel to intervene before property was removed. In another event at a construction site, SARA’s voice-down feature deterred a theft in progress while simultaneously alerting OneWatch and local law enforcement, resulting in a successful intervention without delay. Monitoring industry Remote monitoring centers can evolve to meet growing demand without relying solely on human resources Steve Reinharz, CEO/CTO and founder of AITX and RAD, emphasized the significance of the SARA deployment’s impact on the broader monitoring industry. “In over two decades of innovation in this sector, I have never witnessed such immediate recognition and adoption of a new technology as we’ve seen with SARA,” Reinharz said. “Monitoring centers are not just interested, they’re acting. The results at OneWatch reflect what is possible when organizations are ready to let AI take a leadership role in their operations.” The success of SARA at OneWatch signals a shift in how remote monitoring centers can evolve to meet growing demand without relying solely on human resources. By integrating agentic AI into daily operations, OneWatch not only improved internal efficiency but also strengthened its competitive position in the market. Routine detection and engagement With SARA handling routine detection and engagement, the company has redefined operator roles, transforming them into AI Surveillance Analysts focused on incident resolution, client communication, and strategic oversight. RAD is actively working to bring similar outcomes to its network of nearly 100 authorized dealers and GSOC operators across the country. By equipping partners with SARA, the Company aims to transform remote monitoring at scale, empowering more organizations to lower costs, reduce false alarms, improve response times, and enhance service delivery through agentic AI.
Eagle Eye Networks, the pioneer in cloud video surveillance, introduced Eagle Eye Precision Person & Vehicle Detection. This AI-powered feature runs entirely in the cloud, and works on any connected camera, setting a new benchmark for highly accurate detection and alerting when intruders are present. Businesses can instantly deploy Eagle Eye Precision Person & Vehicle Detection on any camera connected to the global Eagle Eye platform with the push of a button–no new hardware or setup is required. Intrusion detection system “This advanced, AI-powered feature reduces crime by detecting people and vehicles with precision and immediately alerting the business owner, security team, or monitoring center when intruders are detected,” said Dean Drako, CEO of Eagle Eye Networks. “Eagle Eye Precision Person & Vehicle Detection turns existing security cameras into an intrusion detection system–helping businesses respond faster, prevent incidents, and operate more efficiently, all without costly upgrades.” Feature in the Eagle Eye cloud VMS Eagle Eye Precision Person & Vehicle Detection uses AI and multiple images to detect moving people and vehicles Eagle Eye Precision Person & Vehicle Detection uses AI and multiple images to detect moving people and vehicles with very high accuracy. Used primarily for remote or on-premise monitoring, its deep learning algorithms discern people and vehicles from other objects or activity (such as tree branches moving in the wind, shadows, or lights from vehicle movements) even in poor weather conditions and at long distances, significantly reducing expensive and time-consuming false positive alarms. Long-range accuracy and reliability Ideal for enterprise businesses, apartment complexes, warehouses, car dealerships, schools, and municipalities, Precision Person & Vehicle Detection easily scales across multiple locations. Eagle Eye customers such as Centurion Fire and Security, a security integration company based in Huddersfield, England, praise the long-range accuracy and reliability of the new feature. AI-based false alarm filtering systems Eagle Eye clients such as Centurion Fire and Security, a security integration firm based in Huddersfield "Eagle Eye's new Precision People & Vehicle Detection feature, which sends real-time alerts when people or vehicles are detected, is a game-changer for us and our customers. Unlike many AI-based false alarm filtering systems, Eagle Eye’s analytics have proven exceptionally sensitive and reliable—even detecting a person through a Heras fence 40 meters (130 feet) away." "Crucially, it doesn’t trigger on parked vehicles, which is a major problem with other providers. This level of accuracy is exactly what we need to support our users and our monitoring station effectively," said Nathan Smith, Director, Centurion Fire and Security Ltd. Additional benefits Improved Security – Empowers security professionals to focus on real threats by detecting only people and vehicles, enhancing intrusion detection and crime prevention Camera Compatibility – Works with existing cameras and Eagle Eye Cloud VMS infrastructure, requiring no additional hardware, specialty AI cameras or complicated setup Faster Response Time – Actionable, accurate alerts enable quicker decision-making and response to potential threats Cost Savings – Fewer false positive alarms reduce the workload on security personnel, lowering monitoring costs and improving efficiency Customer Satisfaction –Advanced AI-driven security increases customer satisfaction and engenders customer loyalty for resellers and professional monitoring centers Customizable Alerts – Users can set detection zones, schedules, and preferences for better control Automate additional security processes — Ability to trigger alarm monitoring applications such as Immix and Sentinel via webhook integration Integration with professional monitoring services — Seamlessly and instantly alert third-party monitoring provider. Development of Precision Person & Vehicle Detection "We were pleased to collaborate with Eagle Eye Networks in the development of Precision Person & Vehicle Detection,” said Steven Ballard, Managing Member, iNet Security and Surveillance. “Resellers can offer their business customers 24/7 AI-powered intrusion detection using the cameras they already have. It’s cloud-based, so there’s no need for extra hardware or complicated configurations. Eagle Eye’s Precision Person & Vehicle Detection delivers proactive protection that helps stop crime, not just record it."
RGB Spectrum™, a pioneer in mission-critical video solutions for real-time decision support, announced that the City of Norman, Oklahoma, has selected the company to deliver a video processing and control system for its new Traffic Management Center (TMC). This innovative display approach will replace the traditional front-of-room screen with personal console-based video walls, setting a new standard for operational efficiency. RGB Spectrum’s Zio® 4000 series New system redefines what’s possible in compact, efficient traffic management environments Designed in partnership with global engineering and design firm Stantec, the new system redefines what’s possible in compact, efficient traffic management environments. At the core of the deployment is RGB Spectrum’s Zio® 4000 series video processor, XtendPoint® KVM-over-IP, and RGB Rack PCs, enabling seamless, customized workflows to operators. Norman’s commitment “Norman’s commitment to cutting-edge technology ensures we can effectively monitor traffic patterns and enhance safety for all who live, work, and travel through our city,” said David R. Riesland, City Transportation Engineer, City of Norman. “This project has been over 15 years in the making, and it’s incredibly rewarding to see that long-time vision finally become reality. We’re excited to partner with RGB Spectrum to implement a best-in-class solution that supports our mission.” Five discrete networks The new 2,300 square-foot facility will be transformed from a shell space into a highly functional center, including three offices, an operations room, and an IT room. Within the operations space, four operators oversee five discrete networks—ranging from ATMS/ITS and enterprise to public safety, security, and web administration—through a fully distributed architecture. Each operator will have access to five dedicated Rack PCs located remotely in the IT room, allowing for quiet, clutter-free workstations and centralized maintenance. RGB Spectrum’s XtendPoint KVM The upper displays at the station serve as “videowalls,” dynamically combining a mix of sources Using RGB Spectrum’s XtendPoint KVM-over-IP with multiviewing capability, operators control and interact with any PC across any network from their consoles. The upper displays at each station serve as personalized “videowalls,” dynamically combining a mix of sources. Each operator can mirror a common display layout or configure their own unique, task-specific view. RGB Spectrum performance and adaptability In total, any operator can control and view any or all of the 20 Rack PCs, providing a flexible and resilient operations environment. Whether deploying a centralized videowall or a decentralized, operator-specific layout, RGB Spectrum delivers the mission-critical performance and adaptability that modern traffic management centers demand.


Round table discussion
There is safety in numbers, or so the expression goes. Generally speaking, several employees working together tend to be safer than a single employee working alone. Even so, some environments require that workers complete their jobs alone, thus presenting a unique combination of security vulnerabilities. The U.S. Occupational Safety and Health Administration (OSHA) defines a lone worker as “an employee working alone, such as in a confined space or isolated location.” We asked this week’s Expert Panel Roundtable: How can security technologies help to protect "lone workers?"
As physical security technologies become more complex, it is incumbent on the dealer/integrator to have the skills and expertise needed to ensure that a system operates smoothly. The value of integrators increasingly rests on the skill sets they bring to bear when installing a system. If the skills are missing, there is a problem. We asked this week’s Expert Panel Roundtable: What missing skills among security integrators can cause problems for customers?
Driving the smart homes market is the convenience of simple technology solutions. Almost every home now has a “smart speaker” that makes it easier than ever for homeowners to interface and control their technology. But where does security fit into the new landscape of smart home systems? We asked this week’s Expert Panel Roundtable: What’s new in smart homes and residential security systems?
Products


White papers

Maximizing Security And Performance
Download
Selecting The Right Network Video Recorder (NVR) For Any Vertical Market
Download
How To Lower Labor Costs When Installing Video Surveillance
Download
Guide For HAAS: New Choice Of SMB Security System
Download
Are You Ready For An On-Site Emergency?
Download
Understanding All-In-One Solutions
Download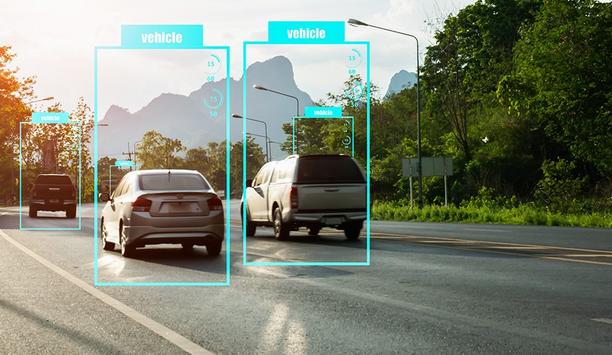
Automatic Vehicle Identification
Download
Cloud Video and Smart Cities
Download
Security Investments Retailers Should Consider For Their 2021 Budget
Download
Optimize Your Business with Analytics and AI
DownloadSinaloa, Mexico: Connected Cities are Safer Cities
Download