Railway security
Transportation systems need robust physical security to protect human life, to ensure economic stability, and to maintain national security. Because transportation involves moving large numbers of people and critical goods across vast, often interconnected infrastructure, it presents a highly attractive target for various threats. More threats equate to a greater need for security. We asked our Expert Panel Roundtable: What are the emerging applications of physical security in the transportation...
As cable theft continues to plague rail networks, energy systems, construction and utilities sites and vacant commercial properties, First Response Group (FRG) has unveiled FRG Tremors - a breakthrough seismic detection system that senses tampering to both laid cable and cable drums in storage, and tracks stolen cable in real time, giving operators instant visibility over critical infrastructure and the means to respond immediately. FRG Tremors, exclusive to First Response Group in the UK, uses...
Those who’ve worked on railway security projects know that procuring a video surveillance system is not just about buying equipment — it’s about ensuring accountability, compliance, and system longevity. Take a common case: cameras installed before monsoon begin failing within months due to ingress and temperature stress. A security lapse follows, and multiple departments are drawn into scrutiny — S&T for specifications, procurement for documentation, and finance for...
Rail modernization has delivered unprecedented benefits, yet these advances have simultaneously introduced safety and security challenges. Designers and manufacturers now face the critical task of addressing these emerging risks while maintaining the performance gains modern rail systems provide”, writes David Kelly, Applications Engineer at Southco. The difference between ordinary and exceptional rail equipment often lies in the smallest details – the components passengers rarely s...
3DX-Ray announces a contract for the sale of further ThreatScan®-AS1 systems to a Middle Eastern Law Enforcement Agency. This sale is a follow-on order to multiple similar systems already in service with the agencies EOD and search teams. The 3DX-RAY ThreatScan®-AS1(ISC) is a robust amorphous silicon portable X-ray inspection system. It comprises as standard a detector panel with an imaging area of 43cm x 35cm, a new high penetration 150kV generator, and a laptop along with batteries, c...
RecFaces, a provider of ready-made biometric software solutions, announces the online expert panel “All Aboard Securely: Facial Biometrics for Asian Railway & Metro”, which takes place on September 19 at 2 PM (GMT+7). The event brings together pioneering voices from the transport, security, and advanced tech industries to explore how facial biometric technologies support the rapid development of railway and metro systems across Southeast and South Asia. Demands for securi...
News
Teleste has signed an agreement with Hitachi Rail to supply advanced passenger information systems for new battery-powered trams in Florence, Italy. The contract covers 16 five-car vehicles, with an option for up to 14 additional units. Teleste’s delivery includes a complete onboard passenger information system featuring information displays, CCTV, Ethernet connectivity, and an automatic passenger counting system. Onboard security These technologies will enhance the passenger experience, strengthen onboard security These technologies will enhance the passenger experience, strengthen onboard security, and support more efficient operations through precise monitoring of passenger flow. The project marks a significant step in modernizing urban mobility in Florence, introducing Hitachi Rail’s innovative battery-powered trams to the historic city. These vehicles enable high-capacity public transport in the city center without the need for overhead electric lines, preserving the visual harmony of the cityscape and driving forward sustainable public mobility. Tram technology “Florence is the first city to benefit from Hitachi Rail’s battery-powered tram technology, and we are proud to contribute to the success of this innovative tram platform,” said Valerian Sand, Senior Vice President, Public Safety and Mobility, Teleste. “We believe that urban public transport plays a key role in the green transition of mobility, and we are excited to ensure passengers enjoy high-quality, real-time information throughout their journey.”
Exein, the embedded IoT cybersecurity company at the forefront of defending Europe’s critical infrastructure, has raised €70m in a Series C round. The round was led by Balderton and joined by Supernova and Lakestar, with 33N, United Ventures, and Partech following on from the previous round. The fresh capital will drive Exein’s ambitious global expansion plans across the US, Japan, Taiwan, and South Korea, as well as to strengthen its established European presence. Identified smart devices Hackers have identified smart devices as a back door into critical systems at businesses Hackers, including many state-sponsored actors, have identified smart devices as a back door into critical systems at businesses and organizations, with one in three data breaches involving an IoT device. Exein, which secures more than a billion smart devices globally, including critical infrastructure for railway networks and healthcare providers, is creating a digital immune system for connected devices, which is fast becoming the global standard for embedded IoT security. Exein's strategic partnerships Exein offers AI-enabled, real-time threat detection across key industries, including critical infrastructure, semiconductor, energy, automotive, healthcare, and robotics. Achieving over 450% year-over-year growth, Exein has formed strategic partnerships with the world’s pioneering chipset and OEM/ODM manufacturers, including MediaTek, Supermicro, Kontron, SECO, and AAEON. Exein’s cybersecurity regulations Exein’s end-point approach creates a digital immune system, securing individual devices rather than relying solely Exein’s end-point approach creates a digital immune system, securing individual devices rather than relying solely on network defenses. This decentralized approach ensures that manufacturers can seamlessly integrate the latest security tools into their products, safeguarding devices from cyber threats and ensuring compliance with stringent global cybersecurity regulations such as Europe’s NIS2 and the Cyber Resilience Act – which comes into force in 2026 – and the US Cyber Trust Mark. Exein’s strategic global expansion As part of Exein’s strategic global expansion, the company is also developing runtime security solutions to secure AI infrastructure and large language models (LLMs), addressing the growing demand to secure AI and LLMs operating within devices, rather than in a centralized cloud environment. Additionally, the funding will support Exein’s pursuit of strategic M&A opportunities in the cybersecurity industry, further enhancing its growth plans. Building the digital immune system Exein’s pursuit of strategic M&A options in the cybersecurity drive further enhances its growth plans Gianni Cuozzo, Founder & CEO, of Exein, says: "Exein’s extraordinary growth is a testament to the urgent demand to secure devices which are ubiquitous in our everyday lives. Embedded security at the device level is fundamental, and we are proud to support manufacturers in providing the highest levels of security, offering them confidence in knowing they are compliant with the latest security legislation." "I’m extremely proud to be fortifying the foundations of European tech innovation, and to have the trust of our partners and investors as we expand globally and continue our mission of building the digital immune system for the connected world.” AI enabling attackers Elena Moneta, Principal at Balderton, says: “We’re living in an era where everything — from rail networks to industrial machinery — is connected, and therefore exposed. As critical infrastructure becomes increasingly software-defined and networked, the risks multiply, especially with AI enabling attackers to hit more targets faster than ever before." "And they are no longer breaching through the front door; the microwave on a military ship, or the smart fish tank in a hospital waiting room - any one of these could be exploited to compromise the entire network." "Exein tackles this threat where it begins: on the device itself, embedding real-time security on the edge — continuously monitoring, learning, and responding in real time. There is no better team to take on this challenge, and we are immensely proud to be partnering with Gianni and team as they build the cybersecurity foundation for the AI-powered, hyper-connected world ahead.”
Secure Logiq is proud to return to Intersec 2025, where the team will be available to discuss the latest advancements in surveillance storage technology and share their insights on optimizing video systems for the most demanding applications. Visitors can meet the Secure Logiq team at Stand S1-G40, where they’ll have the opportunity to connect with industry experts, including Ben Yoxall, Robin Hughes, Anand Subbiah and the dedicated Middle East sales team. Demand for robust surveillance systems Secure Logiq is eager to expand its presence in the region, bringing even more tailored "Our presence at Intersec has always been about building connections and helping customers overcome the challenges of large-scale surveillance deployments," says Anand Subbiah, Regional Director for the Middle East. He adds, "This year, we’re excited to share how our solutions continue to drive efficiency and performance in enterprise video projects." Building on the momentum of last year’s success, Secure Logiq is eager to expand its presence in the region, bringing even more tailored, next-gen solutions to meet the growing demand for robust surveillance systems. Future of video surveillance Ben Yoxall, Secure Logiq’s Commercial Director, says: "Intersec 2024 was an incredible milestone for us, and this year, we aim to build on that success by pushing the boundaries even further." He adds, "Our goal is to continue empowering businesses across the Middle East with that not only meet today’s needs, but also anticipate future challenges. We’re excited to demonstrate how our solutions are shaping the future of video surveillance storage at Intersec 2025." Visit Stand S1-G40 to learn more about how the expertise can help take the security projects to the next level.
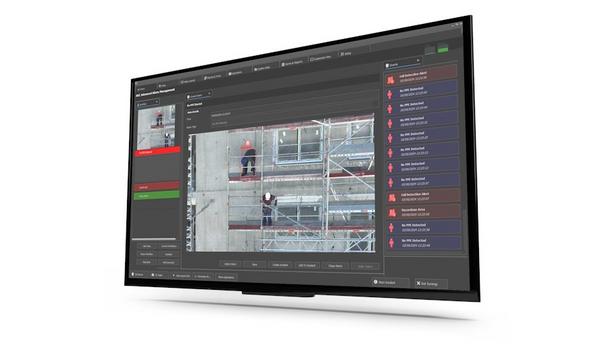
Synectics, a pioneer in advanced security and surveillance systems, has launched ‘Synergy DETECT’, part of Synergy’s AI suite, that allows users to select and activate up to 12 AI-driven tools depending on their safety, security, or service-related needs. Safety protocol enforcement PPE Detection is just one of many safety-oriented tools included. It automatically generates alerts when workers appear in the frame without protective helmets or high-visibility vests. Users can also activate the Hazardous Area tool to receive alerts whenever people or vehicles enter zones designated as dangerous, for example, rail tracks or areas immediately surrounding potentially hazardous equipment or substances. A Fall Detection tool supports improved accident detection, generating alarms if a worker slips or falls to the ground. Stopped Object detection is ideal for flagging when a decelerating or stopped vehicle or person poses a safety risk – for example, if a car is blocking an entrance/exit or is a danger to other traffic. Rapid detection of potential security risks Synergy DETECT features tools for identifying security risks to better protect the public and personnel Synergy DETECT also features tools for identifying security risks to better protect the public, personnel, and physical assets. Automated Crowd Detection, for example, can alert operators when the number of people in a set zone exceeds a predefined threshold. This could indicate that an incident is taking place, causing a crowd to gather, or that additional services, such as in a retail or transport environment, are required to ease heavy footfall or satisfy the high demand. High-security zones Another useful tool is Intrusion Detection, which uses detectors with long-range accuracy to identify and classify people or ground vehicles accessing a restricted area – from staff car parks and high-security zones to restricted access and backstage areas at stadiums. Loitering Detection is another valuable tool. It is especially useful for monitoring areas where regular comings and goings by people and vehicles are common. This can flag suspicious behavior based on lingering for time periods outside the norm. Vehicle and traffic flow monitoring Synergy DETECT makes it simple to detect, count, classify, and track the movements of vehicles Synergy DETECT makes it simple to detect, count, classify, and track the movements of vehicles – including cars, buses, trucks and bicycles. Multi-Object Detection and Multi-Object Counting ensure operators are alerted to vehicles in the wrong place or at the wrong time. A Wrong Direction tool is available for monitoring vehicles moving against an area's typical direction of travel, perhaps indicating a fleeing suspect or drunk driver. The Traffic Counting tool can also monitor incoming and outgoing traffic for a specific zone. This is useful for alerting operators about parking capacity levels or checking that all vehicles have left the premises as part of security checks and emergency drills. Alternatively, Zone Crossing can be used when only incoming vehicles need to be monitored. Easy set-up, filters, and flexible camera compatibility Activating Synergy DETECT is simple. Once the hardware is installed, users can connect any of the cameras in their network, including fixed, PTZ and thermal models. The tools can be tailored to suit specific operational needs and re-configured depending on evolving requirements. Settings include zone size, time period, sensitivity, and alarm frequency thresholds. Dan Noble, Head of Product Strategy – Synergy, said, “AI truly does have the power to supercharge surveillance-based risk detection, but only if the AI tools themselves are easy and intuitive to use. Synergy DETECT meets this important requirement, putting powerful capabilities at the fingertips of busy surveillance teams in a way that is completely tailored to an organization’s exact needs.”
Matrix concluded a remarkable showcase at Inno Rail 2024, held from November 28 to 30 at the RDSO Stadium Ground in Lucknow. At Booth No. 81, Matrix captivated attendees with its trailblazing security and communication solutions, specifically designed for railway and transportation sectors. Meeting stringent cybersecurity standards Visitors experienced Matrix’s RDSO 6.0-compliant network cameras, a first for India, which meet the stringent cybersecurity standards of Indian Railways. These STQC-certified cameras uphold OWASP ASVS 4.0 L2 standards, ensuring unmatched data protection for sensitive passenger information, a key attraction for railway decision-makers. How to ensure reliability? Matrix’s 4-Channel NVRs, with compact, fanless designs, proved how to ensure reliability Matrix's EN50155-certified and now EN45545-2-certified Ruggedized IP Cameras, engineered for harsh railway and roadway environments, drew significant attention. With features like anti-vibration, shock resistance, and low-light image clarity, these cameras impressed stakeholders seeking dynamic surveillance solutions. Additionally, Matrix’s 4-Channel NVRs, with compact, fanless designs and up to 10TB storage, demonstrated how to ensure reliability and longevity in critical railway applications. Cyber-secure video management for railways Matrix showcased its STQC-certified cyber-secure Video Management Software (VMS), which addresses railway-specific operational challenges. Attendees were particularly interested in its ability to protect data from OWASP Top 10 security risks, providing centralized control for seamless video surveillance across stations, depots, and control rooms. Solutions for railway infrastructure Keys are tailored to meet the needs of railway infrastructure, ensuring streamlined access Railway professionals appreciated Matrix’s COSEC ARGO FACE, a face recognition-based access control system, and COSEC VEGA, an AADHAAR-enabled biometric attendance solution. Designed to enhance both security and operational efficiency, these solutions are tailored to meet the unique needs of railway infrastructure, ensuring streamlined access and personnel management. Telecom solutions for railway communication Matrix’s telecom offerings, including IP-PBX systems and Unified Communication servers, showcased resilient communication networks essential for efficient railway operations. Visitors were impressed by the ability of these solutions to support seamless coordination across vast territories. Strengthening partnerships for a safer rail network “Inno Rail 2024 was an incredible opportunity to engage with key decision-makers and stakeholders in the railway sector,” said Tarun Sharma, Marketing Head at Matrix. “Our solutions resonated with the audience, reflecting our commitment to strengthening railway security and operational efficiency with cutting-edge technology.” Matrix’s successful participation at Inno Rail 2024 reinforced its position as a trusted technology provider for the Indian Railways, paving the way for future collaborations aimed at safer, more efficient rail transport systems.
Smiths Detection, a pioneer in threat detection and security screening technologies, and a business of Smiths Group, announces that its state-of-the-art IONSCAN 600 detectors will be tested by the Polish railway, PKP Group. The six-month pilot, the first in Poland, will help develop standards for future anti-terrorism and anti-sabotage systems, strengthening the protection of critical infrastructure. The equipment was loaned by the Directorate General for Home Affairs and Migration (DG HOME) of the European Commission, which initiated the project. Develop security practices The IONSCAN 600 detectors will be used to assess and develop security practices for the railway system, with a particular focus on strengthening anti-terrorism and anti-sabotage measures. These detectors, which use scanning strips to identify explosives and hazardous substances, will be used in random screenings of baggage and cargo at selected train stations, on trains, and at cargo terminals. The goal is to implement security protocols similar to those already in place at airports, ensuring comprehensive protection of critical infrastructure. Workshop held at Warszawa Central station Live demonstrations of the IONSCAN 600’s capabilities took place at key locations To kick off the initiative, a workshop was held at Warszawa Central Station, attended by representatives from the European Commission, Smiths Detection, the Polish Police, Border Guard, Railway Security Services, and PKP Group. Live demonstrations of the IONSCAN 600’s capabilities took place at key locations, including PKP Intercity trains and the PKP CARGO Connect terminal, showcasing the effectiveness of the detectors in real-world scenarios. Shaping future security standards The European Commission and Smiths Detection will use the test to provide valuable insights to refine operational requirements for the use of these devices in the railway environment. The results will contribute to the Commission's efforts to establish standardized security protocols for railway systems across Europe. These findings will also help define the future development of anti-terrorism and anti-sabotage technologies tailored for the rail sector. Poland becomes the sixth country to test this technology as part of the EU’s wider railway security initiative, following similar trials in the Netherlands, Belgium, Germany, Slovakia, and Romania. The operational feedback from these tests will be instrumental in shaping future security practices and devices for the rail industry. Enhancing border security In addition to its railway testing, the IONSCAN 600 detectors will also be deployed by the Polish Border Guard at key border crossings with Ukraine and Belarus. These devices are capable of detecting both explosives and dangerous chemical substances and can identify whether an individual has come into contact with these materials or with weapons. This capability is particularly important in securing the EU’s external borders. Identifying security threats This initiative aims to expand the use of advanced threat detection technologies beyond aviation The IONSCAN 600 testing in Poland is part of the European Commission’s broader Counter-Terrorism Plan (CT Agenda), launched in 2020 to strengthen the security of public infrastructure across the EU. This project is part of a series of ongoing detection trials aimed at developing balanced security solutions in collaboration with manufacturers, operators, and law enforcement, addressing both facilitation and security concerns. This initiative aims to expand the use of advanced threat detection technologies beyond aviation, with a focus on harmonizing standards for the protection of public spaces. The program also supports the voluntary adoption of EU-wide standards for detection equipment, ensuring that technologies like the IONSCAN 600 are effective at identifying security threats while enabling the free movement of people and goods. Rail safety standards Matthew Clark, VP Commercial, Smiths Detection, said of this initiative: "This pilot program is a vital step toward enhancing rail safety standards, which are essential in today’s evolving threat landscape. By testing the IONSCAN 600 in real-world rail environments, we’re not only expanding the applications of our technology beyond aviation, but also helping shape the future of security for critical infrastructure across Europe." He adds, "Our commitment is to provide reliable, cutting-edge solutions that safeguard public spaces, and this project is a testament to that vision." European Commission’s Counter-Terrorism Plan The European Commission’s Counter-Terrorism Plan is part of an ongoing effort to bolster the EU's overall security posture. In 2019, the EU Railway Safety Platform adopted a set of best practices for rail safety, including the use of mobile detection devices for random and targeted checks. These initiatives are designed to address emerging threats and create a more secure and resilient Europe.


Expert commentary
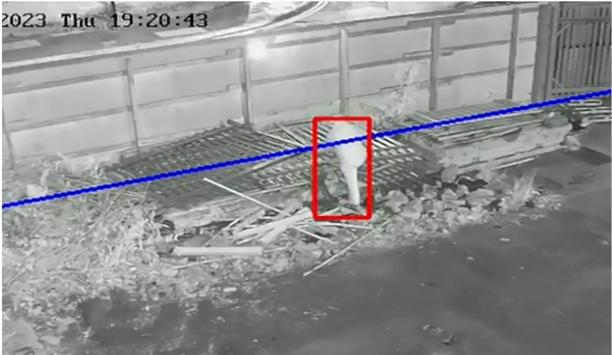
In the old days, hopping onto the platform from a not-yet-stopped train was a commonplace stunt for daily commuters in a hurry. It was a thrilling, but dangerous part of railway travel. Today, rail travel is generally much safer, but thrill and fame seekers are finding new, creative ways to use the railway to court notoriety online. Earlier this month, a young man filmed himself laying on the tracks and allowing a train to pass over him. In another instance, two people were seen misusing a level crossing to get an 'Instagram worthy' picture. Meanwhile, the media has recently reported stories from Austria to Australia of people (and in some cases children) being seriously hurt or killed while attempting to train surf. Safety and security of the railway Safety and security have always been a top priority for railways and supporting agencies For rail companies, such incidents cause great distress and bring often unjust headlines that question the level of safety and security of the railway. Then, of course, there is the impact on the timetable when incidents cause significant delays. The ramifications of just one incident can be significant, as illustrated by a case in February when a track trespasser caused 16 trains to be canceled and a further 54 to be partially canceled at the cost of approximately 600,000 euros. Despite the negative stories, safety and security have always been a top priority for railways and supporting agencies. The British Transport Police, for example, traces its origin back to 1830 when the force was established following the death of a member of Parliament, who was struck by a passing train after alighting onto the track of the newly opened Liverpool and Manchester Railway. Modern surveillance Today, trains, platforms, yards, level crossings and sections of track are monitored by some of the very latest technology hardware and software, from high-definition cameras with built-in advanced video analytics capabilities to PSIM (physical security information management) systems that can be used to orchestrate a response to anything from a trespasser on the line to a major derailment. Even with all these systems, the sheer scale of rail networks means it is simply not possible to always have eyes everywhere. True of video analytics If a driver spots someone or something on the line and immediately applies the emergency brake What’s more, while the technology continues to make huge leaps forward, affordability and usability can limit their effectiveness. This has been especially true of video analytics and object detection, where distinguishing between a human trespasser or an animal can be challenging, especially in low light (a particular issue with passenger and freight trains running round the clock). With trains moving at a high speed, early detection is everything. If a driver spots someone or something on the line and immediately applies the emergency brake, it could take the train as much as one mile to come to a stop. LiDAR to the rescue So, what can be done to improve response times for drivers and other stakeholders? One recommendation is to focus on key sections of the rail network that provide easier access for trespassers, such as stations, platforms, tunnels, bridges and level crossings, where more than a quarter of all significant accidents occur on EU railways. This is already standard operating procedure for most rail companies. However, a growing number are going beyond the 'standard' safety and security measures, with the introduction of high-tech solutions such as 3D LiDAR (Light Detection and Ranging) sensors. This technology is already familiar to the rail industry. It has been used for some time in applications ranging from surveying environments in preparation for building high-speed rail networks to mapping railway tracks and surrounding infrastructure for ongoing maintenance works. Management of virtual perimeters LiDAR enables the creation and management of virtual perimeters and/or safe zones In the context of safety and security on the railway, LiDAR enables the creation and management of virtual perimeters and/or safe zones with pinpoint accuracy. A good example would be at level crossings where a high volume of vehicle and pedestrian traffic crosses the track when the barrier is raised, but it must be clear for rolling stock to pass safely. LiDAR sensors can be programmed to automatically switch on minutes before a train is scheduled to pass through the crossing and turned off after it has cleared the area. During this time, any movement detected with this ‘live zone’ would create an alert in the control room. Further layer of protection The addition of cameras would provide a real-time feed of the situation, enabling the control room operator to act. That could involve sending a message via a public address system to clear the area, alerting the approaching train driver to take appropriate action, and alerting emergency services and maintenance teams if there is a vehicle, animal or other blockage on the track. The investment many rail operators have made in PSIM and CAD (computer-aided dispatch) can add a further layer of protection. These systems provide the operator not only with guidance regarding the next best action but also automatically triggered responses to orchestrate the entire incident management process. Protecting critical infrastructure All of these pieces of rail infrastructure and the joint network stand to benefit from the use of LiDAR Level crossings are a good example of environments where it is not viable to have round-the-clock live surveillance, but monitoring is essential at key times. It is a similar case for stations late at night, bridges and depots, all of which are susceptible to acts of trespass, vandalism (particularly graffiti) and theft. All of these pieces of rail infrastructure and the collective network stand to benefit from the use of LiDAR, as incidents are prevented or their impact mitigated in terms of the effect on the timetable, negative publicity, fines and the costs of investigations. Latest Report on Railway Safety and Interoperability The latest Report on Railway Safety and Interoperability in the EU stated that “European railways remain among the safest in the world, with major accidents becoming rare and significant accidents decreasing in the last two decades.” This good news is heightened by the fact that more people than ever in Europe are choosing to let the ‘train take the strain’, with passenger numbers reaching record levels. However, while passengers may no longer be swinging open train doors and jumping from moving carriages just to get to work a few seconds earlier, the risks on the railways have evolved. With more rolling stock traveling at higher speeds on lines old and new, there is a need to revisit the traditional methods of safeguarding areas on the network, to deter, detect and protect against those seeking fame, infamy or gain.
The average business owner or investor has some kind of security precaution in place, especially in the after-hours when there are fewer deterrents to inhibit criminal activity. Security guards, video surveillance systems, motion sensor lights, or even just fake cameras placed around the property are some of the common options people choose. Future of overnight security Smart business owners are starting to realize, however, that some of these traditional security measures are becoming antiquated and no longer cutting. The now and future of overnight security is in remote guarding. Pioneered by companies like Los Angeles-based Elite Interactive Solutions, which was founded back in 2007, remote guarding is revolutionizing the overnight security business. Minimizing criminal activity Remote guarding is fast becoming the most popular choice among commercial end-user property owners Remote guarding utilizes a combination of cutting-edge technology, “digital guards,” highly trained security agents, and local law enforcement if and when necessary to minimize the potential of criminal activity. For those adequately enlightened to its overwhelmingly impressive crime prevention capabilities, remote guarding is fast becoming the most popular choice among commercial end-user property owners to secure and protect their investments. What Is Remote Guarding? Remote guarding is a revolutionary concept and increasing trend in security systems that utilize a combination of methods to effectively analyze potential threats to property. Cameras and/or other monitoring devices running highly advanced algorithmic software are installed in strategic areas or vulnerable places onsite and remotely located security agents are immediately notified of any activity within a designated perimeter of the property. A blend of AI, cybersecurity, and video analytics When properly deployed by an expert provider, the technology stack includes a proprietary blend of video analytics, artificial intelligence, cybersecurity, and more. Done right, “noise” is effectively filtered out, allowing agents to act on legitimate alerts and achieve zero false alarms communicated to first responders. Today, there are a lot of terms and descriptions tossed around about remote guarding, remote video, virtual guarding, etc., but those attributes must be present to represent the true definition of the offering and its many virtues. Realtime situational awareness Many systems have a two-way speaker that allows the security agent to give a verbal warning When specially trained security agents are alerted to trespassers, possible intruders, or other suspicious activity, they analyze the situation in real time and determine the necessary level of action. Many systems have a two-way speaker that allows the security agent to give a verbal warning, known as a voice-down, to the individual(s) that they are being watched. Most perpetrators, often believing the response is emanating directly from security personnel on the property itself rather than from a remote command center, flee immediately. However, if the threat persists, the security agent enlists local law enforcement to get on the scene. Customized remote guarding When properly deployed, remote guarding systems are also customized to specific properties. A team of consultants visits the client’s property to evaluate its vulnerabilities and where to best place cameras and/or other monitoring devices for system efficacy. Traditional Security Shortfalls According to Keith Bushey, a retired commander for the Los Angeles Police Department, there is much frustration between law enforcement officers and potential victims of crime due to the historically unreliable performance of traditional burglar alarm systems and central monitoring stations. He states about 90% of security-related calls are false alarms, a problem that has been well-documented through the years. Onsite challenges When a legitimate emergency does occur, the perpetrators have often already done their damage When a legitimate emergency does occur, the perpetrators have often already done their damage and/or escaped by the time law enforcement arrives. Onsite security guards are not the remedy either as they bring their own set of issues and challenges. Unexpected costs Traditional security systems can also have unexpected costs. The cost is not only in the security guards’ paycheck or the cost of the equipment itself. The cost comes when an actual incident occurs. In worst-case scenarios, the security guard(s) are injured, the business suffers inventory loss, and/or damage is sustained to the property. The medical and other costs for the security guard(s), the loss of inventory, property damage, deployment of law enforcement resources, and possible fallout of legal expenses all add up. Even in the best-case scenario, false alarm expenses incur if law enforcement is dispatched. These, among many others, are some of the primary issues that remote guarding resoundingly answers as a superior alternative. A Bounty of Benefits Remote guarding systems have been proven to cut costs and be more effective than traditional security systems. Even though the monthly monitoring costs of remote guarding are significantly higher than traditional intrusion detection system monitoring, the much higher effectiveness in crime reduction, elimination of false alarms, and augmenting or replacement of manned guards result in a substantially higher return on investment (ROI) to the end user. Easy tracking of threats The security cameras already have their image captured on record, making them easier to track down For example, case studies have demonstrated reduced security costs for clients by 60%, on average. These reductions have come from the costs of security staff, inventory, or property loss, plus saving money on insurance premiums and deductibles. The nature of remote guarding reduces the risk and costs of false alarms, with professional security agents able to determine an actual threat before law enforcement is called. In a rare instance when a perpetrator escapes before law enforcement arrives or can detain the individual(s), the security cameras already have their image captured on record, making them easier to track down and identify. Reduction of false alarms The significant reduction in false alarms is greatly appreciated by law enforcement, as it allows them to focus on real emergencies or crises. Better relationships are also developed between clients and law enforcement, as remote guarding systems are highly reliable in providing accurate and real-time information to officers as they approach the scene. In short, it assists law enforcement in doing their job more effectively, as well as more safely thanks to having eyewitness information before engaging in an active crime scene. Partnership When you combine the decreased cost with the increased efficiency and success rate, it is easy to see why many commercial end-user property owners across the country are making the shift to remote guarding. It’s also an outstanding opportunity for professional security dealers and integrators to partner with a remote guarding services provider to bring a superior solution to their end customers and pick up a recurring monthly revenue stream in the process.
It’s no secret that the data security sector is constantly changing. It has an annual CGR of about 12.3%. Future trends in data security Much of this has to do with the rise of cybercrime in recent years, with reports showing that cyberattacks happen as often as every 39 seconds. To combat the growing rate of cybercrime, data security has been on the rise. As we journey further into this era, it becomes evident that a spectrum of significant trends is molding the future of data security. This exploration delves into a selection of these trends, unraveling their importance and the potential implications they carry 1. AI security tools will increase Artificial Intelligence is also being used in the development of smart attacks and malware The introduction of Artificial Intelligence in the data security industry brought significant changes, especially in cybersecurity. AI has been the golden standard for face detection, natural language processing, automated threat detection, and automated security systems. Additionally, Artificial Intelligence is also being used in the development of smart attacks and malware, bypassing even the latest security protocols in data control. And as time progresses, AI security tools will flourish and dominate the scene. Let’s take a more in-depth look at three of the top AI security tools. Targeted attack analysis tool Manufacturers utilize targeted attack analysis tools to uncover targeted and stealthy attacks. Artificial Intelligence can be applied to the program’s capabilities, processes, and knowledge. For instance, Symantec launched this tool to combat the Dragon 2.0 attack in 2022. The phishing attack reprimanded multiple energy companies while trying to gain access to their operational networks. Targeted Attack Analysis Tools can analyze incidents and look for similarities from previous situations. They also help detect suspicious activities and collect all the necessary data to determine whether a specific action is malicious. Intercept X tool Results from the Intercept X Tool feature high accuracy and a low false positive rate Sophos, a British security hardware and software company, launched the Intercept X Tool. It engages a neural network that records and analyses data like a human brain. Sophos’ Intercept X Tool can extract features from a single file and perform a deep analysis. It detects malicious activities within 20 milliseconds. Plus, it’s also trained to work on bi-directional sharing and real-world feedback of threat intelligence. Results from the Intercept X Tool feature high accuracy and a low false positive rate. IBM Watson Technology IBM’s QRadar Advisor uses IBM Watson Technology, a unique AI tool for fighting cyber attacks. Artificial Intelligence can auto-investigate activities and indicators for potential exploitation or compromise. With cognitive reasoning, IBM Watson Technology can present critical insights to accelerate the response cycle. Security analysts can utilize this technology to search for threat incidents, reducing the risk of letting them fly under the radar. 2. Blockchain as a security solution It guarantees no points of failure or hackable entrances that can expose datasets inside the system Blockchain is a type of distributed ledger technology (DLT) that aims to establish trust within an untrusting ecosystem. Today it’s one of the most robust cybersecurity technologies in the industry. Blockchain utilizes a decentralized ledger system, but your team members can still gain access to transparent information in the cloud. Members can also record, pass along, and view necessary transactional data in the blockchain. The entire blockchain process maintains data integrity within the system while establishing trust among team members. It guarantees no points of failure or hackable entrances that can expose datasets inside the system. Cybersecurity, biometrics Cybersecurity primarily benefits from these features because blockchain can create a secure and robust wall between data and hackers. On top of that, blockchain ledgers can include biometrics like fingerprints and retina scans. These prevent hackers from accessing any private data. Because blockchain is decentralized, it also limits hackable data. Together with the technology’s record-keeping system, each node is provided insight into data manipulation exposing real-time cybercrime attempts. 3. Increased and widened access control Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data Access control is critical in data security. More than a valuable security tool, business leaders can use access control to regulate people accessing any given resource. A company with an IT security setting can control who has the liberty to edit certain files. One of the primary goals of access control is to minimize threats or attacks to organizations and businesses to keep people and data secure. Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data protection laws. Benefits The benefits of increased and widened access control include: Identifying who can access and control your data at specific time intervals. Protecting data from overwriting, accidental deletion, and malicious intent. User permissions that can be readily changed. Compliance and regulation with data privacy laws. Central management of access to data through a reporting portal or a dashboard. Multi-factor authentication Access control comes in various types and systems, so it’s critical to know the features of what you’re looking for. The most common type is multi-factor authentication or MFA. It involves multiple steps before logging in, requiring the user to enter other relevant information besides the password. Some other examples of information include biometrics, answering a security question, or entering a code sent to the user’s email address. Two-factor authentication, role-based access control Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession. Another type of access control is role-based access control. In this setup, only one individual can set up access guidelines and grant permissions to specific team members within an organization. 4. Greater use of the zero-trust security model The zero-trust security model is a framework that requires every user within and outside the organization to undergo authentication, authorization, and validation. These are all essential to ensure proper security configuration before access is granted to the company’s applications and data. A zero-trust model assumes that anyone can cause data breaches and that a traditional network edge is not taken into effect. Moreover, it addresses the following modern-day challenges: Hybrid cloud environments. Security of remote workers. Ransomware threats. This framework utilizes the combination of multiple advanced technologies, including: A risk-based multi-factor authentication. Endpoint security. Identity protection. Cloud workload technology. The zero-trust model uses all these innovative tools for system identification, user verification, access consideration, and system security maintenance. Constant validation and monitoring Enforcing strict policies and compliance with data privacy laws are also essential Additionally, it also considers data encryption, email security, and asset verification before establishing connections with applications. The architecture of a zero-trust framework requires constant validation and monitoring of the users and the devices they are using. Enforcing strict policies and compliance with data privacy laws are also essential. More importantly, the zero trust architecture requires all organizations to be aware of all their available services and accounts to gain complete control of data handling and manipulation. 5. Increased privacy regulations Privacy regulations and policies guide organizations in proper data control, handling, and security. These policies guide organizations in proper data control, handling, and security. As a responsible business owner, you must comply with these regulations to avoid legal issues. With cybersecurity attacks becoming common, expect increased and stricter privacy regulations to be released in the next few years. While current policies are still taken into effect, various modifications and adjustments will occur to compete with the rising numbers of data breaches, thefts, data loss, and more. California Privacy Rights Act (CPRA) Currently, the California Privacy Rights Act (CPRA) is the most comprehensive legislation on state data privacy. It only started to take effect on January 1, 2023. The CPRA introduces the following principles: Broad individual consumer rights. Significant duties of people who need to collect sensitive and personal information. Additional definitions of data privacy and security. An individual’s duties include releasing information about data collection to concerned data subjects and proper access, correction, and deletion of information. Final thoughts 2023 is a big year for data security. Trends such as increased adoption of zero-trust policies, a greater reliance on AI security tools, and the implementation of blockchain as a security solution are all things we expect to see shortly. Staying up-to-date with these trends is important for keeping your business current and ensuring that you’re adhering to new and changing regulations. Doing so can give you an edge over the competition and keep you out of legal hot water.
Security beat
Several recent terrorist and mass violence attacks have been directed at soft targets, or relatively unprotected locations where people gather such as outside a music venue or in the unscreened passenger areas at airports. Attacks in public areas have led to the development of new security technologies aimed at protecting soft targets. One company addressing the challenges is Evolv Technology and its Edge automated high-speed personnel screening solution. The system integrates walkthrough firearm and explosive detection for high-throughput protection of events and soft targets.The Edge system has multiple detection sensitivity settings to respond to various threat scenarios Enhanced Visitor Experience The system seeks to increase security without compromising the ‘customer experience’. People simply walk through single-file – between two 5-foot-tall stanchions. One lane can screen up to 800 people per hour, and the system detects explosives or metallic objects without the need for pat-downs or wands or other invasive procedures. Any personal belongings can remain in visitors’ pockets. A single security guard is needed for each lane to verify any detected threats. “The system combines an improved security posture with a better visitor experience,” says Mike Ellenbogen, CEO of Evolv Technology. “We need to fly and have been trained to be screened at the airport, but we don’t expect to be screened going to see a ball game or a Mozart concert. Evolv recognized a need for a new way to inspect people before they enter these types of facilities. It’s a seamless system that pulls various technologies together. We want to feel safe but without having to sacrifice the quality of the experience.”Screening analytics provide data on the numbers of people screened by time of day and by result The system combines millimeter wave and magnetic field sensors, along with artificial intelligence (AI)/ machine learning and can incorporate additional data such as biometrics. Known bad actors can be identified using facial recognition. The system has multiple detection sensitivity settings to respond to various threat scenarios. Expanding Perimeter Protection A security guard provides the human touch by verifying any threats detected by the system. The locations of concealed items are displayed on a photo of the individual using a color-coded box overlay. Screening analytics provide data on the numbers of people screened by time of day and by result. Ellenbogen says the company is working to have the system adopted at entertainment venues, performing arts centers, sports centers, for air and rail transportation, and to protect high-profile government buildings. The Edge system can expand the protected perimeter to a wider area that was previously unprotected. The Edge system can expand the protected perimeter to a wider area that was previously unprotected For example, concert-goers exited the arena of an Ariana Grande concert May 22, 2017, in Manchester, U.K., and entered the surrounding area that was unscreened and unsecured. Placing a user-friendly screening system around a wider perimeter outside the concert venue might have prevented the use of an improvised explosive device in the terrorist attack.Placing a user-friendly screening system around a wider perimeter outside the concert venue might have prevented the use of an improvised explosive device in the terrorist attack Threat Mitigation With Soft Target Approach Likewise, a 2016 bombing at the Brussels Airport occurred in the departure hall outside the passenger screening areas. Securing a wider perimeter – for example, screening customers discreetly as they enter the airport building from a parking area – could have provided additional security against such an attack. Ellenbogen confirms Evolv has sold a number of systems to major European airports to screen visitors and passengers as they enter the front door. “Addressing the threat to an airport or train system is different than screening passengers; we are looking for different types of objects and different types of materials. The idea is to be able to detect threats to a venue before they get into the venue.” The soft target approach can also be applied to public buildings, such as courthouses, and used in lieu of more invasive metal detectors and x-ray machines. The portability of the Edge system enables a ‘pop-up’ approach to security – i.e., to relocate the system to address specific or changing security threats easily. The self-contained system only requires a wall plug. Labor reduction (because of faster throughput) can help offset the system costs but it’s difficult to quantify the improvement in the visitor experienceImproving Security Posture At Event Venues “It’s surprising the level of importance [venue owners] put on the visitor experience,” says Ellenbogen. “They see that their brand starts at the front door. They are eager to find alternative security solutions that come across as more inviting, less imposing, less closed down, less invasive than the solutions they have been using,” he says. “They are driven by a desire to improve the visitor experience as they improve the security posture.” He says current events, including terrorist attacks and mass shootings, drive awareness among venue owners to improve the security of soft targets. “The level of interest is high, and it spikes somewhat when there is a big headline,” Ellenbogen says. He notes that the system is more expensive than a metal detector, but about a third the cost of familiar airport body scanners. Labor reduction (because of faster throughput) can help offset the system costs, but “it’s difficult to quantify the improvement in the visitor experience,” Ellenbogen says.
There’s a new big player – and familiar household name – coming into the security marketplace with the announcement of Motorola’s intent to acquire Canadian video manufacturer Avigilon Corporation, provider of video surveillance and analytics. Motorola Solutions points to an “avalanche of video in public and private sectors” as a motivation for the acquisition. Motorola Solutions’ dominance in the public safety market – where the Chicago company supplies police technologies, radios and other products – will provide new opportunities for Avigilon in a realm where it previously has not been dominant. Avigilon has millions of cameras deployed across airports, rail, streets, and public and private buildings. Meanwhile, Avigilon will “bring [its] advanced video surveillance and analytics platform to [Motorola’s] rapidly evolving public safety workflow,” according to Motorola, and enhance the larger company’s portfolio of “mission-critical communications technologies.” Avigilon’s end-to-end security and video surveillance platform includes cameras, analytics, video management and video storage. Avigilon has millions of cameras deployed across airports, rail, streets, and public and private buildings The Broader Solution Early clues point to Motorola positioning Avigilon as part of a broader solution, especially in the municipal/safe cities market. The company says the acquisition will enable more safe cities projects and more public-private partnerships between local communities and law enforcement. Motorola sees Avigilon as “a natural extension to global public safety and U.S. federal and military” applications, according to the company. The all-cash deal pays CAD$27.00 per share of Avigilon, and totals approximately $1 billion including Avigilon’s net debt. Not a bad price considering Avigilon’s stock price has traded as low as $13 a share in the last year. Avigilon has 1,200 employees with locations in Vancouver and Richmond, British Columbia, and Dallas and Plano, Texas. Revenue was $354 million in 2016. The transaction is expected to be completed in Q2 of 2018. Deploying Pre-engineered Solutions As an innovator in the security market, Avigilon has spearheaded an end-to-end solutions approach. Their success has even prompted some component manufacturers to expand their proposition into a broader “solutions” sale. Led largely by Avigilon, the industry pendulum has swung toward the simplicity of deploying pre-engineered end-to-end solutions. Open systems integrated using best-in-breed components from several manufacturers still have their devotees, and are needed in some situations, but Avigilon has made a strong case for the end-to-end alternative. Others have followed. The all-cash deal pays CAD$27.00 per share of Avigilon, and totals approximately $1 billion including Avigilon’s net debt Avigilon has also lately been a leader in implementing artificial intelligence and deep learning, including Appearance Search technology that can locate a vehicle or person from video across a site. Avigilon’s video surveillance platform seeks to transform video from reactive – looking back at what has taken place – to proactive, issuing alerts in real time. Avigilon also recently introduced Avigilon Blue cloud service platform to enable video system users to manage more sites with fewer resources. Investing And Building Motorola would presumably continue Avigilon’s licensing program, but rules-based video analytics patents’ importance may fade Motorola is not a completely new name to the security market. Old-timers will remember Motorola Indala, a previous presence in the RFID access control market that was sold to HID Corp. in 2001. More recently, Motorola Solutions has invested in Vidsys, a provider of converged security and information management (CSIM) software and has implemented Vidsys CSIM through its Protect Series unified platform that aggregates and analyses information from multiple inputs for military and federal government properties. Motorola is also known as the inventor of the Six Sigma quality improvement process - and commitment to quality plays well among security integrators and end users. Avigilon owns 750 U.S. and international patents, including some covering basic underlying principles of video analytics, for which several video companies currently pay license fees. Motorola would presumably continue the licensing program, although the importance of rules-based video analytics patents may fade as new deep learning and artificial intelligence (AI) approaches to video analytics emerge. Channel Conflict A possible concern surrounding the acquisition is the issue of channel conflict. When it comes to larger end user customers, Motorola has embraced a direct-to-user approach that could be problematic in the eyes of Avigilon’s 2,000 resellers. Among the benefits Motorola says they bring to the table is the ability to “leverage [their] direct enterprise safes force for large deals.” They also say they “complement Avigilon’s channel with [Motorola’s] channel network.” The security industry has a spotty history of larger companies entering the market to buy existing businesses. Some have been a good fit, while others have not. The entrepreneurial spirit of more than one successful security company has suffered under larger corporate ownership, sometimes withering as new corporate overlords cut costs and stifle R&D. The more successful recent large acquisitions in our market – notably Canon’s acquisition of Milestone Systems and Axis Communications – have worked well because the acquired companies have retained some degree of independence and preserved the existing corporate culture. In the case of Motorola and Avigilon, obviously, time will tell.
Case studies
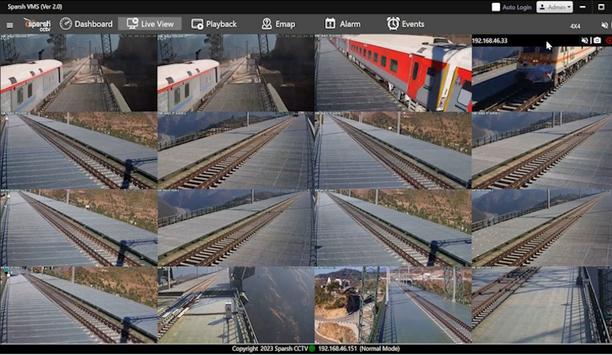
Sparsh CCTV, a pioneer in electronic surveillance, has partnered with Indian Railways to enhance security and operational efficiency for the newly inaugurated Jammu Railway Division. This collaboration coincides with the inauguration of three new trains and marks a historic milestone in enhancing connectivity between Kashmir and the rest of India. Additionally, Sparsh CCTV played a key role in ensuring comprehensive security during the Maha Kumbh at Prayagraj, safeguarding millions of pilgrims. Sparsh’s comprehensive solutions Sparsh’s comprehensive solutions have been integral to ensuring the success of the Udhampur-Srinagar-Baramulla Rail Link (USBRL), a project of immense strategic and economic significance for India. By enabling seamless rail connectivity in this sensitive region, USBRL underscores the Government of India’s commitment to infrastructure growth and national security. Sparsh’s integrated CCTV solutions Sparsh’s integrated CCTV and video management keys set up a control room to oversee operations Also, during the Maha Kumbh, Sparsh CCTV ensured comprehensive security for millions of pilgrims arriving at Prayagraj’s railway stations. Key highlights include cyber-secured STQC-certified cameras installed across all major stations, end-to-end video management systems for real-time monitoring and efficient crowd control, 360-degree security coverage at Prayagraj (PRYJ), Prayagraj Junction (PYGS), Phaphamau Junction (PFM), and Rambag (PRRB), and crowd management analytics deployed at major locations, ensuring seamless handling of large gatherings. Sparsh’s integrated CCTV and video management solutions established a control room to oversee operations, providing a secure and seamless experience for pilgrims. Challenging railway undertakings Mr. Sanjeev Sehgal, Founder & CEO of Sparsh CCTV, stated, “We are immensely proud to contribute to both the USBRL project and the Maha Kumbh, two monumental initiatives that reflect India’s spirit of progress and unity. By delivering innovative, 100% Made in India solutions, we have reinforced our commitment to safety, quality, and the vision of Atmanirbhar Bharat.” The USBRL project, hailed as one of the most challenging railway undertakings in post-independence India, features engineering marvels such as 38 state-of-the-art tunnels spanning 119 kilometers, 927 bridges covering 13 kilometers, and the iconic Chenab Bridge—the world’s highest arch railway bridge, standing at 359 meters above the riverbed. Advanced AI and SCADA systems Sparsh CCTV has ensured the safety and active efficiency of this task by surveillance technologies Sparsh CCTV has ensured the safety and operational efficiency of this project by deploying advanced surveillance technologies, including fire and smoke detection, abandoned object monitoring, face recognition, and train speed analytics. An integrated Command and Control Center, equipped with advanced AI, SCADA systems, and an Emergency Calling System, facilitates real-time monitoring of train movements and signaling, ensuring improved safety, efficiency, and operational management. Integrating cutting-edge surveillance Security has been a paramount concern in the Kashmir region, and the USBRL project sets a benchmark for integrating cutting-edge surveillance and operational systems in such a sensitive area. For the first time in India, an entire railway surveillance system has been executed by a single OEM/ manufacturer. Sparsh has deployed a range of solutions, including explosion-proof cameras, stainless steel cameras, advanced video management software, Video Analytics and Integrated Control Command Center (ICCC), all designed and manufactured in India. This achievement highlights the country’s capability to address complex challenges with indigenous technology. Advanced LiDAR 3D technology The implementation of this surveillance infrastructure has been driven in alliance with key stakeholders The implementation of this surveillance infrastructure has been managed in collaboration with key stakeholders such as RailTel, Konkan Railways, Ircon, and renowned integrators like L&T, TATA, Honeywell and Siemens, PSJV ensuring a world-class safety framework for the project. Sparsh’s solutions have been pivotal in addressing critical challenges, including monitoring overhead cable operations, detecting track obstructions, and integrating advanced LiDAR 3D technology to enhance operational efficiency, enabling seamless functioning even in the region’s rugged and unpredictable terrain. Sparsh CCTV’s advanced surveillance systems With the inauguration of the Jammu Railway Division, the operational readiness of the Vande Bharat Express between Katra and Srinagar signifies the completion of the Kashmir-to-Kanyakumari rail link. This rail journey offers passengers a unique and extraordinary experience, crossing engineering marvels like the Chenab Bridge and the Anji Khad cable-stayed bridge. The successful execution of this monumental project not only strengthens national unity but also ensures a robust security framework in one of India’s most sensitive regions, thanks to Sparsh CCTV’s advanced surveillance systems.
The Swiss Federal Railways (SBB) is the largest rail and transport company in Switzerland with 1.2 million passengers and 180,000 tonnes of freight transported every day. SBB is a pioneering rail system in Europe due to its quality of service, safety, and reliability. It operates passenger, cargo, and freight services, with large real estate holdings across Switzerland that it needs to keep secure and protect from crime, anti-social behavior, and trespassing. High-performance cameras SBB video team needed to replace an existing video surveillance system across its rail network The SBB video team needed to replace an existing video surveillance system across its rail network. Hanwha Vision cameras were chosen due to their high performance, intelligent analytics, and attractive pricing. Hanwha Vision cameras from its X and P series, including a vandal-resistant network dome camera, plus PTZ cameras and network boxes, have been installed and used continuously since 2021. Video analytics for greater awareness The cameras have a wide range of beneficial functions and analytics such as audio detection, automatic lens distortion correction, and WDR (Wide Dynamic Range). If an event occurs, the dome cameras can switch to PTZ cameras. The cameras also feature tamper detection, fog detection, and day and night functions. Cost optimization in the project and in operation SBB is using dome and multi-directional cameras from the X and P series SBB is increasingly using dome and multi-directional cameras from the X and P series with the option of remote lens alignment. These help to optimize costs in the project and during operation, as the alignment and the lens can be adjusted and corrected remotely at any time, eliminating the need for on-site adjustment. Securing perimeters With intelligent video analytics, such as loitering detection and virtual line-crossing and area detection, carried out on the device, the cameras deliver accurate motion detection, allowing operators to quickly understand if there is unauthorized entry to any restricted areas. The integrated AI supports the differentiation between people and different vehicles, increasing the accuracy of the analysis and minimizing false alarms. "We are very satisfied with the performance of the Hanwha Vision cameras. They help us to secure our stations and buildings, optimize processes in rail operations, improve public safety and ensure that our trains run on time,” said Chei Seung-Kyoo, responsible for Technology Video at SBB.
In a groundbreaking initiative to bolster security measures, Indian Railways has successfully implemented Herta's state-of-the-art facial recognition solutions across its extensive network of train stations in the Eastern region. This transformative project marks a significant step towards ensuring the safety and well-being of passengers and staff throughout the railway system. The project becomes the largest one in the world in the transport sector. Herta has also been awarded two more regions that will be implemented after the Eastern one. Facial recognition technology The deployment of Herta's cutting-edge facial recognition technology is part of IndianRailways' commitment to embracing advanced solutions for enhancing security. By leveraging Herta's expertise, the railway network aims to create a safer environment for passengers, mitigate potential security threats, and streamline operational efficiency. Key features Key features of Herta's facial recognition solutions implemented at 230 train stations using thousands of video surveillance cameras include: Real-time Identification: Herta's technology provides real-time facial identification capabilities, allowing for swift and accurate recognition of individuals within the train station premises. Enhanced Security: The implementation of facial recognition enhances security by automatically identifying and alerting authorities about the presence of individuals with potential security concerns, contributing to the overall safety of passengers and staff. Efficient Monitoring: Herta's system enables efficient monitoring of the train stations, offering a proactive approach to security management. The technology assists in the quick response to incidents and ensures a rapid resolution of security issues. User-Friendly Interface: The intuitive user interface of Herta's solutions facilitates easy integration with existing security systems, providing a seamless experience for railway personnel responsible for monitoring and managing security. Stringent security requirements Mr. Rahat Jain, IDIS INDIA - MD, expressed his enthusiasm about the successful implementation, stating, "We are delighted to announce the successful integration of Herta's facial recognition solutions at Indian Railways." Startologic, the official partner overseeing the deployment of Herta's facial recognition solutions at Indian Railways, is proud to be part of this transformative project. The successful implementation showcases the capability of Herta's technology to meet the stringent security requirements of one of the world's largest railway networks.
Completed in 2023, Thanet Parkway Station, the new high-speed rail hub serving the Thanet area in southeast Kent, has implemented a significant infrastructure enhancement: the installation of high-quality parking barriers to optimize accessibility and safety within its premises. Investment in connectivity Thanet Parkway Station, which opened on 31st July 2023, is a testament to the region's commitment to advancing its transportation infrastructure. With a total investment of £44 million secured through a combination of council financing and various building and growth funds, the station addresses the rising demand for efficient connectivity to London and neighboring towns. Swift and convenient travel Furthermore, its ample car park, boasting space for 293 vehicles, serves as an indispensable "park and ride" facility Featuring two expansive platforms capable of accommodating 12-car trains and strategically situated on the high-speed line through Ashford International, Thanet Parkway Station offers commuters swift journeys to key destinations. Furthermore, its ample car park, boasting space for 293 vehicles, serves as an indispensable "park and ride" facility, alleviating congestion in central Thanet and providing convenient access to the surrounding areas. Enhancing safety and traffic flow To enhance safety and streamline traffic flow within the station's car park and adjoining pedestrian and cycleway, Jacksons Fencing was specified to implement a comprehensive suite of parking barriers and demarcation measures. Warden Swing Barriers were installed along the pedestrian and cycleway to regulate vehicular access. These galvanized steel barriers offer a robust solution while ensuring ease of operation for maintenance and emergency vehicles. Safeguarding pedestrian pathways Along the same path, Jacksons Fencing’s timber knee rail fencing served as an unobtrusive demarcation device. This fencing solution, constructed from kiln-dried, pressure-treated timber and galvanized steel straps, safeguards grass verges and delineates pedestrian pathways. Ensuring peace of mind Strategically positioned to enforce height restrictions within designated parking areas, Jacksons’ MaxHite parking height restriction barriers were installed. Crafted from galvanized steel and finished in a highly visible yellow polyester powder coating, the barriers provide durable protection against unauthorized access, while facilitating smooth traffic management. Each installed product comes with the assurance of Jacksons Fencing’s 25-year guarantee, symbolizing a commitment to quality and sustainability. High-quality, sustainable products Commenting on the project, Peter Jackson, Managing Director of Jacksons Fencing, underscored the transformative impact of the enhanced security measures at Thanet Parkway Station, said "As a local supplier, we’re thrilled to have been involved in this project, and it’s great to see that the developers have invested in high-quality, sustainable products, showcasing this project’s commitment to providing a lasting transport solution for the community." He adds, "Beyond parking, the upgraded access control and increased security measures not only enhance safety, but also foster a profound sense of reassurance and pride in the area for all station users."
A damning new report shows theft from construction sites is surging nationwide, detrimentally affecting projects, firms and employees. Key findings Spike in cases: Two-thirds of respondents say the rate of theft increased in 2023, as the resale value of goods reached record levels. Criminals are getting smarter: one in three believe crime, including theft, physical violence, harassment and vandalism, is becoming more sophisticated. It comes as reports of criminals using drones to target sites become more frequent. A hidden productivity drain: A third of projects have been delayed due to crime, with copper and cable topping the tables as the most frequently targeted goods–delaying the development of critical infrastructure, such as railways. Workers bear the brunt of poor security: one in four workers have been left out of pocket, after having to replace stolen tools, and say being robbed is their “biggest fear.” However, security is seen as a “low priority” on sites they work on (30%). Underestimation of the risks BauWatch, examines the senses of building workers, to understand their incidents of theft at work The “Unseen Threats: 2024 Construction Crime Index,” from pioneering site-security provider, BauWatch, examines insights from construction workers, to understand their experience of theft at work. It suggests a “perfect storm” of factors, including goods inflation, increasingly sophisticated criminal tactics, and a general underestimation of the risks, are making sites vulnerable to crime, in turn causing major delays to projects, as well as denting staff morale. It also identifies the types of perpetrators that might pose a threat, including opportunists, professional gangs, and “insiders” (criminals posing as legitimate personnel), and outlines a list of best practice measures that can be immediately employed to minimize the risk of a robbery. BauWatch’s crime index We’ve observed that, since the Government removed the construction industry’s access to red diesel Rico Wojtulewicz, Head of Policy and Market Insight at the National Federation of Builders said: “We’ve observed that, since the Government removed the construction industry’s access to red diesel, fuel theft has risen, as indicated by responses in BauWatch’s crime index. CCTV has therefore become an even more important tool to help tackle site crime, not only because it acts as a deterrent and helps collect video evidence but as it also offers an insight into how and where a site might be better protected.” With criminals seemingly becoming more brazen, BauWatch, which supplies CCTV security to over 5000 active Construction sites across the UK and Europe, and the National Federation of Builders, are calling for firms to take extra preventative action against thieves, rather than taking a “wait and see” approach. Author's quote “Construction sites have always attracted thieves, but with the resale value of goods going through the roof, they’re now prime targets. So, it’s worrying to see that some workers don’t feel confident about on-site security,” said Alexis Potter, BauWatch’s Managing Director. Potter added: “Repeated incidents, even small ones, have huge repercussions if left unchecked as we can see in this report. The best way to minimize the impact of theft is to deter criminals from entering at all, so we are advocating for the adoption of preventative security measures to protect staff, safeguard investments and maintain project schedules.”
SeeTrue, a global AI software solution pioneer for security screening, disclosed its recent entry into the realm of urban security through a strategic partnership with Israel Railways. This collaborative effort has resulted in the seamless integration of SeeTrue's cutting-edge AI solution into security screening checkpoints at railway stations throughout Israel, including the country's largest stations, where more than 1,000 bags require screening every hour. Faster, smoother security process The integration of SeeTrue into train station security processes has proven to be transformative, maintaining a consistently high level of security and operating continuously around the clock. Passengers benefit from a faster, smoother security process minimizing stress and ensuring that critical security checks do not result in bottlenecks that can negatively impact the journey. Security screening solution This incident offers concrete proof of SeeTrue's invaluable contribution to ensuring public safety In a recent incident at one of the busiest and most central train stations, SeeTrue's AI security screening solution identified a bag containing a concealed 30-centimeter knife, alerting security personnel in real-time. As a result, the potential threat was swiftly and effectively neutralized, resulting in the arrest of the individual carrying the concealed knife. This incident offers concrete proof of SeeTrue's invaluable contribution to ensuring public safety in high-traffic transportation hubs. AI technology Assaf Frenkel, Co-Founder and CEO of SeeTrue, "We take immense pride in deepening our expertise in AI technology to include urban security, an endeavor that complements our pioneering work in aviation, customs, and other urban security checkpoints." Assaf Frenkel adds, "Partnering with a high-quality, innovative mass-transit organization like Israel Railways is a testament to our commitment to revolutionizing safety and security across multiple domains, making our cities and transportation systems safer and more efficient." Innovation and intelligence in railway security Hagay Rozenfeld, Head of Innovation, Israel Railways, said "Innovation at Israel Railways is a key part of our strategy, and AI plays a pivotal role in strengthening our pledge to passenger safety, seamlessly infusing intelligence into our security strategies and enabling us to provide optimal security for our passengers and our employees." Shaked Bar, Head of Security, Israel Railways, said "Acknowledging our responsibility to top-tier security at Israel Railways, we harness the power of AI to provide the highest security standards, ensuring the best passenger experience and safety."


Round table discussion
Headlines of violence in our schools are a reminder of the need to keep educational institutions safe. In fact, if there is a positive aspect to the constant bombardment of headlines, it is that it keeps our attention perpetually focused on how to improve school security. But what is the role of physical security systems? As the new school year begins, we asked this week’s Expert Panel Roundtable: Are schools safer because of physical security systems? Why or why not?
As physical security technologies become more complex, it is incumbent on the dealer/integrator to have the skills and expertise needed to ensure that a system operates smoothly. The value of integrators increasingly rests on the skill sets they bring to bear when installing a system. If the skills are missing, there is a problem. We asked this week’s Expert Panel Roundtable: What missing skills among security integrators can cause problems for customers?
Driving the smart homes market is the convenience of simple technology solutions. Almost every home now has a “smart speaker” that makes it easier than ever for homeowners to interface and control their technology. But where does security fit into the new landscape of smart home systems? We asked this week’s Expert Panel Roundtable: What’s new in smart homes and residential security systems?
Products