Electronic access control - Security beat
A larger proportion of cyberattacks in the first half of 2019 can be attributed to electronic criminals (eCrime adversaries) compared to state-sponsored or unidentified attacks. CrowdStrike, a cybersecurity company that provides the CrowdStrike Falcon endpoint protection platform, observes that 61% of targeted cybersecurity campaigns in the first half of 2019 were sourced from eCrime adversaries, compared to 39% from other sources. Technology was the top vertical market targeted by cyber-attack...
When violence or a life-threatening incident occurs, hospitals and other healthcare institutions are often in the crosshairs. Hospitals increasingly face a reality of workplace violence, attacks on patients, and threats to doctors and other support staff. And even if violence happens outside a hospital – such as an active shooter at a public place – the local hospital must be prepared to respond to an influx of injured victims. When conflicts arise inside a hospital, there is an urg...
One of the common characteristics of trade shows is booths with walls and walls of new products. Sometimes exhibitors seem intent on displaying everything in their portfolio, even though the displays appear cluttered and may not be welcoming. In an age of system sales, in particular, the emphasis on products can seem off kilter. Discussions with exhibitors at this year’s GSX show reveal a new awareness of the need for less cluttered booths, but the equipment walls persist. Here’s a...
GSX 2019 got off to a jaunty start Tuesday. The show was humming with activity much of the day, and most exhibitors said they were pleased with the numbers and types of potential customers visiting their booths. There seemed to be less emphasis on product introductions than at the ISC West show in the spring (although there is much that is on the new side), while the trend toward system sales is continuing. Here's a review of Day 1 from the show floor. Dahua continues to educate market ...
A week of mass shootings this summer has again spotlighted the horror of gun violence in public spaces. A 19-year-old gunman opened fire at the Gilroy Garlic Festival in California on July 28, injuring 13 and killing four (including the gunman). In El Paso, Texas, less than a week later, a lone gunman killed 22 people and injured 24 others. In Dayton, Ohio, a day later, a gunman shot 26 people during a 30-second attack, killing 9 and injuring 17. Rising active shooting incidents Beyond the gri...
The devil is in the details. The broader implications of the U.S. Government ban on Chinese video surveillance manufacturers are being clarified in the federal rule-making process, and a public hearing in July gave the industry a chance to speak up about the impact of the law. Ban on equipment The hearing centered on Section 889 of Title VII of the National Defense Authorisation Act (NDAA) for FY 2019, specifically paragraph (a)(1)(B). The paragraph "prohibits agencies from entering into a con...
Physical security has been stuck in a forensic and siloed mindset for decades, while the rest of the enterprise has evolved and transformed into proactive, connected operations. A new security management platform based on artificial intelligence (AI) seeks to change that status quo by using modern tools for unification, analytics and controls. AI-based security management “Security teams are managing more moving parts than ever,” says Clayton Brown, Co-Founder of ReconaSense....
All schools and colleges need to address three different levels of security when considering access control. The first level is the least vulnerable of the three and concerns the perimeter entry and exit points. Here, incorporating some level of electronic access control should be a consideration, whether that is a combination of electronic and mechanical door hardware, or a complete electronic solution. An electromechanical solution, such as electric strikes, can be beneficial in the effective...
The Physical Security Interoperability Alliance (PSIA) was founded in 2008 with a goal of creating ‘plug-and-play interoperability’ among physical security devices, systems and services. Since then, the organization’s mission has both expanded to include logical security and focused more narrowly on identity, a critical aspect of security today. In recent years, PSIA has concentrated on its PLAI (Physical Logical Access Interoperability) specification, which provides a means t...
Krowd is an app that connects people together based on geography; that is, if they are at the same place at the same time. Users sign into the app using the local WiFi, identify themselves by username, and are placed immediately in a group chat comprising anyone else at the location who has signed into the app. An enhancement of the Krowd app, known as Krowdsafe, leverages the technology to achieve and promote security and safety. Specifically, Krowdsafe enables users to interact directly with...
Among the cloud’s many impacts on the physical security market is a democratization of access control. Less expensive cloud systems are making electronic access control affordable even to smaller companies. cloud-based access control With the growing cloud-based access control market, integrators can find more opportunities in small businesses and vertical markets that typically wouldn’t be on the radar of their sales team. Large upfront costs for a server, software and annua...
Deploying security robots at a company is about more than providing and programming the hardware. There is also an element of “change management” involved in smoothing the way for robots to play a security role working side-by-side with human counterparts. Rising Popularity Of Security Robots As security robots increase in popularity, more companies are adapting to such cultural challenges "As security robots increase in popularity, more companies are adapting to such cultural cha...
Nexkey says its mission is to disrupt the access control market and ‘change the way people experience access to physical places’. The startup is embracing the latest buzzword for access control – frictionless – while also enabling electronic access control for doors currently protected by mechanical locks. The system is simple with only three components – a controller, an electronic replacement lock core, and a smart phone app. The ‘controller’, a combi...
As physical security systems increasingly resemble the architecture of an IT (information technology) network, the cybersecurity risks are increasing. Sometimes hacks in physical security go unrecognized because of poor detection. Here's part two of our Cybersecurity series. Going forward, the physical security industry should adopt the same principles as the information security market, embracing new elements such as risk assessment and certifications. A change in culture is needed to align an...
Cloud platforms and applications are becoming prevalent across security solutions. In the simplest terms, cloud systems store and access data and programs over the Internet instead of using an on-premises computer server. The cloud is a metaphor for the Internet. This technology helps security integrators provide managed services and the advantages of off-site systems and services to customers, which is why cloud computing is often mentioned among the 'megatrends' in the physical security indus...
A futuristic alternative to plastic cards for access control and other applications is being considered by some corporate users in Sweden and the United Kingdom. The idea involves using a microchip device implanted into a user’s hand. About the size of a grain of rice and provided by Swedish company Biohax, the tiny device employs passive near field communication (NFC) to interface with a user’s digital environment. Access control is just one application for the device, which can be...
There is a new event on the calendar for the security industry in 2019: The Security Event 2019, 9-11 April, at NEC, Birmingham. For additional details and a preview of the new trade show and conference, we spoke with Tristan Norman, Founding Partner and Event Director, The Security Event. Q: It seems recently that some trade shows have been on the decline in terms of exhibit size and attendance. Why does the physical security industry need another trade show? Norman: I think there are numer...
ADT Inc.’s acquisition of Red Hawk Fire & Security, Boca Raton, Fla., is the latest move in ADT Commercial’s strategy to buy up security integrator firms around the country and grow their footprint. In addition to the Red Hawk acquisition, announced in mid-October, ADT has acquired more than a half-dozen security system integration firms in the last year or so. Here’s a quick rundown of integrator companies acquired by ADT: Protec, a Pacific Northwest commerc...
Avigilon Corp. is a relatively young company in the security market and has come a long way since it was founded in 2004. From an early focus on high-megapixel imaging, the company’s end-to-end solutions have evolved to include access control, video analytics and now artificial intelligence (AI). A reflection of how far Avigilon has come in a short time is the recent $1 billion acquisition of the Canadian company by Motorola Solutions. Avigilon’s President and COO, James Henderson,...
IFSEC International 2018 kicked off last week at London’s ExCel Centre. Visitors were lucky enough to experience a rare three days of British sunshine as they came together to discuss the latest trends and technologies in the physical security industry. Many exhibitors commented on how the show seemed smaller than previous years, with stands more spread out, and fewer ‘double-decker’ offerings than earlier shows. Although exhibitors represented all aspects of physical security...
After the 2012 Sandy Hook school shooting, Jody Allen Crowe set out to develop a threat suppression tool to address school violence. Five years later, the result of that effort is the Crotega Threat Suppression System, displayed this year at ISC West. The remotely-deployed threat suppression system drenches a perpetrator with a repulsive water-based solution, thus impairing their ability to enact violence. The solution irritates eyes, throat, lungs and skin, but does not cause permanent injury....
Cybersecurity talk currently dominates many events in the physical security industry. And it’s about time, given that we are all playing catch-up in a scary cybersecurity environment where threats are constant and constantly evolving. I heard an interesting discussion about cybersecurity recently among consultants attending MercTech4, a conference in Miami hosted by Mercury Security and its OEM partners. The broad-ranging discussion touched on multiple aspects of cybersecurity, including...
ISC West in Las Vegas kicked off with a bang on Wednesday, reflecting a healthy physical security industry with an overall upbeat outlook on the future. Driving the optimism is a pending new wave of product innovation, propelled largely by developments in artificial intelligence (AI) and deep learning. Some of that new wave is evident at ISC West, but much of the talk still centers on what’s to come. Attendees flocked to the first day of the show to check out the newest technologies, and t...
Open architecture in physical access control is built around Mercury Security’s access control panels, the de facto standard embraced by more than two dozen access control original equipment manufacturers (OEMs). Mercury and several of its OEMs teamed up March 3-4 to present MercTech4, a conference in Miami aimed at updating security consultants about the latest developments related to the Mercury platform. MercTech4 highlighted a new generation of access control products, which are incre...
There’s a new big player – and familiar household name – coming into the security marketplace with the announcement of Motorola’s intent to acquire Canadian video manufacturer Avigilon Corporation, provider of video surveillance and analytics. Motorola Solutions points to an “avalanche of video in public and private sectors” as a motivation for the acquisition. Motorola Solutions’ dominance in the public safety market – where t...
Security is more-than-ever linked to consumer electronics, especially in the residential/smart home market. CES 2018 in Las Vegas is therefore brimming with news that will have a direct impact on the security market, today and especially looking into the future. Products for the future of security CES is a giant trade show for consumer electronics with 2.75 million net square feet of exhibitor space and featuring more than 3,900 exhibitors, including 900 startups - in contr...
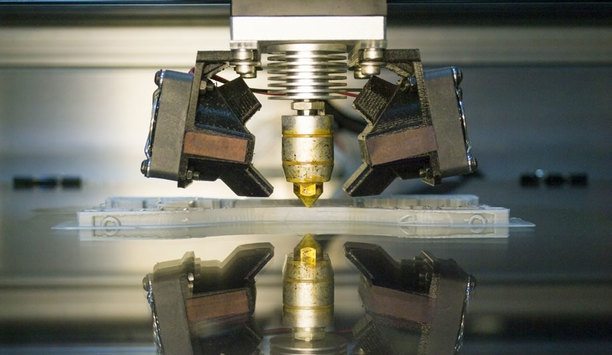
Technology is a valuable tool for increasing security, but occasionally technology can create a threat. An example is the threat 3D printing technology poses to one of the most mature security technologies, mechanical locks and keys. The ability of 3D printing to duplicate keys presents new challenges for lock manufacturers, and new vulnerabilities to end users. Keys that could previously only be duplicated by skilled thieves can now easily be copied using off-the-shelf technologies and informat...
Perimeter security has evolved in recent years from an emphasis on fences and low-cost sensors to a broader systems approach that incorporates a variety of technologies. Protech is among the companies leading the transition and positioning itself as a one-stop systems provider at the perimeter. Mergers And Acquisitions In 2014, U.S.-based Protech merged with Sorhea, a French manufacturer of perimeter security systems. The combination expanded Protech’s business from one product to the a...
I have been unpacking from last week’s ASIS show in Orlando. It was a good show, except if you compare it to last spring’s ISC West in Las Vegas, which was especially well attended and generated a lot of excitement in the market. ASIS was definitely smaller, lower key and less crowded. And there were no big product announcements. But there was still plenty of technology on display. In particular, I saw the show reflecting several ongoing trends in the market. Impact Of M&As Me...
Are smart phones poised to replace all biometrics hardware in the next several years? That’s the bold prediction of Hector Hoyos, CEO of Hoyos Labs, one of the pioneers of biometrics technology who owns 59 patents (pending and issued) related to the field. The advent of the smart phone, which amounts to everyone carrying a computer in the palm of their hand, provides all the ability anyone needs to capture biometric information to use for verification, he says. Breakthrough In Technolo...