Cyber security - News
Abnormal Security, the pioneer in AI-native human behavior security, announced it has been recognized as a pioneer in the first-ever Gartner® Magic Quadrant™ for Email Security Platforms. A complimentary version of the full report can be found. Gartner evaluated 14 vendors across the email security market and placed Abnormal in the Leaders Quadrant. They feel this placement recognizes Abnormal for excelling in both Completeness of Vision by addressing current and future email threats,...
OPSWAT, a global pioneer in critical infrastructure protection established in the U.S., announced its acquisition of Fend Incorporated. Fend is a pioneering data pipeline and cybersecurity company dedicated to securing operational technology (OT) against cyber threats, ransomware, and other evolving risks. Based in Arlington, Virginia, Fend is known for its expertise in protecting U.S. government agencies, utilities, oil and gas, manufacturing, and other critical industries where air-gappe...
Global cybersecurity firm Performanta celebrates the recognition of its Head of Security Automation, Torvald Johnson, as one of Microsoft’s first Security Copilot Most Valuable Professionals (MVPs). The first of only 10 Security Copilot MVPs worldwide, Johnson has been recognized for his practical expertise, leadership, and guidance across the cybersecurity sector and wider industries, and commitment to pursuing a future of cyber safety. Performanta’s cyber innovation “It is...
Gallagher Security is celebrating a landmark year distinguished by the growth and innovation of its industry-pioneering solutions. As 2024 approaches, the global executive team reflects on the milestones that defined the year and offers a glimpse into the bold plans for 2025. Award-winning excellence Gallagher’s dedication to innovation and quality was recognized across the globe in 2024. Controller 7000 The cyber-forward Controller 7000 (C7000) earned top honors in New Ze...
ISC West 2025 opens registration with its premier sponsor the Security Industry Association (SIA). Taking place March 31 – April 4 (SIA Education@ISC: March 31 – April 3 | Exhibit Hall: April 2-4) at The Venetian Expo in Las Vegas, ISC West will feature an additional day of education for the first time in the event’s history. SIA Education@ISC Spanning four days, SIA Education@ISC returns bigger and more impactful than ever. The expanded program features over 110 sessio...
The collaboration of Bosch and Genetec™ is bringing even greater benefits to customers with direct-to-cloud integration of Bosch cameras with Genetec Security Center SaaS, as well as new intelligent detection and enhanced search capabilities available through Genetec Cloudlink™ cloud-managed appliance connections. Available with camera firmware release 9.40, customers choosing Genetec Security Center SaaS gain support for Bosch application-specific artificial int...
As organizations around the world struggle with extended downtime and revenue loss due to widespread cyberattacks, cybersecurity company Rubrik, Inc. announces Rubrik Turbo Threat Hunting. This unprecedented new feature is designed to dramatically accelerate cyber recovery and enables organizations to locate clean recovery points across their entire data estate in seconds. Turbo Threat Hunting aims to allow customers to immediately identify clean recovery points and swiftly recover from c...
Colt Technology Services, the digital infrastructure company, announced that it is the first to successfully trial Cisco’s 800G ZR+ coherent pluggable optics in its production network using the Cisco 8000 series routers, powered by Cisco Silicon One. The Routed Optical Networking testing– carried out across the 667 km between Frankfurt and Munich, Germany– is the latest in a series of Colt trials with high-profile global partners designed to rethink technology’s previous...
Cequence, a pioneer in API security and bot management, unveiled new insights from its CQ Prime threat research team that underscore the growing cyber threats targeting the global retail sector during the holiday season. The research reveals that businesses could face average potential losses of £2.02 million ($2.58 million) per hour throughout December due to malicious bot traffic and fraud attempts. Cequence’s UAP platform Drawing on billions of real transactions and attack data...
HackerOne, the cybersecurity company dedicated to eliminating vulnerabilities through continuous testing, announced updates to its intelligent copilot Hai. Hai’s new program insights synthesize data across a customer’s programs, giving them instant understanding and actionable summaries of performance, results, and trends. Now more seamlessly integrated into workflows, Hai continues to help customers save time by making it easy to understand comprehensive program data, improve team...
Bridewell, the trusted cyber security partner for organizations operating within Critical National Infrastructure (CNI), is proud to announce that it has been awarded the prestigious ‘Thriving Together’ award at the Heathrow Business Summit. The award recognizes Bridewell’s integral role in supporting Heathrow Airport’s sustainable growth and operations. Heathrow Business Summit The Heathrow Business Summit brought together strategic suppliers, senior representatives,...
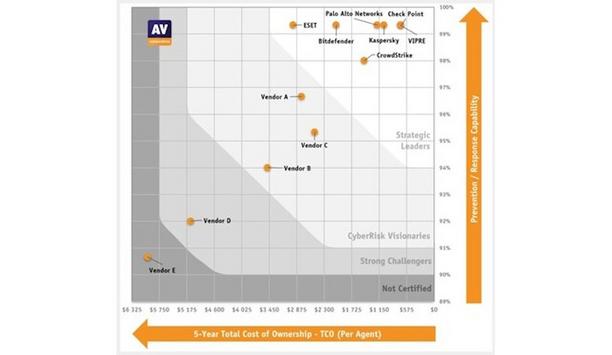
AV-Comparatives, the globally recognized authority in independent cybersecurity testing, has released its 2024 Endpoint Prevention and Response (EPR) Comparative Report, showcasing the exceptional performance of pioneering cybersecurity solutions. The report evaluates the ability of these products to detect, prevent, and respond to advanced threats in real-world scenarios. MITRE ATT&CK® framework AV-Comparatives' rigorous assessment covered products from Bitdefender, Check P...
Genetec Inc., the global pioneer in enterprise physical security software, shared the results of its 2025 State of the Physical Security Report. Based on insights from more than 600 physical security pioneers, including end users, channel partners, systems integrators, and consultants based in the Middle East, Turkey, and Africa (MEA) markets, the report offers a comprehensive analysis of evolving trends in physical security operations. Hybrid cloud adoption According to the report, 48%...
Arctic Wolf, a pioneering provider of security operations, and Immersive Labs, the pioneer in people-centric cyber resilience, announced that Arctic Wolf has joined the Immersive Labs Cyber Million program, which aims to solve the cybersecurity talent deficit by increasing access to one million entry-level cybersecurity operations jobs over the next decade. As a new partner, Arctic Wolf has made entry-level cyber jobs available on the platform. Cyber Million program Launched by Imme...
Auguria, Inc., a pioneer in AI-powered security operations solutions announced the latest version of its Security Knowledge Layer™ Platform. The newly enhanced platform can integrate with some of today's biggest data sources, including SentinelOne, CrowdStrike, Palo Alto Networks, and Microsoft Windows Event Logs. Auguria also unveiled its Explainability Graph Feature, a trailblazing tool that provides visual, context-rich threat data for security teams. Expanded integrations Secur...
Kong Inc., a pioneering developer of cloud API technologies, recently released findings from their API Security Perspectives 2025: AI-Enhanced Threats and API Security Report, which highlights the API security landscape and how new developments in AI will impact it. Most notably, 25% of respondents have encountered AI-enhanced security threats related to APIs or LLMs, with 75% of respondents expressing serious concern about AI-enhanced attacks in the future. And while 85% say they’re conf...
iDenfy, a global RegTech company specializing in Know Your Customer (KYC), Anti-Money Laundering (AML), and Know Your Business (KYB) verification solutions, has announced its achievement of SOC II certification with the submission of an independent auditor’s report. New office This milestone confirms iDenfy’s position as a trusted partner in the US market, ensuring that its data handling practices meet rigorous standards of security and confidentiality. The certification coi...
Sensitive data exposure is a top concern given the volume and types of data consumed by generative AI (Gen AI). Inadequate sensitive data controls and resulting data leakage can halt the use of innovative AI tools. DSPM helps accelerate AI adoption by quickly and easily identifying data risks, which is why Rubrik, Inc. is announcing Rubrik DSPM in RSC. Available in early 2025, organizations can rapidly enable DSPM for increased data visibility and sensitive data control across cloud, SaaS, and...
Global cybersecurity pioneer, Hornetsecurity, has unveiled an upgraded version of its 365 Total Backup solution, introducing self-service recovery for end users while also offering full backup and recovery support for Microsoft OneNote. This new functionality is also available with 365 Total Protection Plans 3 and 4. Enabling end users to recover data Hornetsecurity has added a new self-service functionality to its backup solution. This allows end users to independently recover their mailbox,...
Pioneering global cyber security and investigations consultancy S-RM has identified five critical steps for financial institutions and their ICT providers to achieve compliance with the Digital Operational Resilience Act (DORA), which will enter force from 17 January 2025. DORA establishes an EU-wide oversight framework designed to ensure the financial sector can withstand severe operational disruptions. Covering over 20,000 entities, including financial institutions, crypto-asset service provi...
Colt Technology Services, the digital infrastructure company released key enterprise technology forecasts and market trends for 2025. Based on its proprietary research among over 1000 global CIOs, and gathered from market intelligence sources, Colt anticipates sustainability-driven innovation, AI regulation, and a ‘coming of age’ for Network as a Service (NaaS) to dominate the enterprise tech pioneer’s agenda over the next 12 months. Need for AI frameworks Mirko Voltol...
Dotlines UK has announced the upcoming launch of Audra Security, a new suite of hardware and software security products that promise to level up how homes and small businesses in the UK manage their security and internet usage. Audra is designed to make internet security more accessible to a wider audience, by making it simpler, more affordable and user-friendly, while also championing planet-friendly initiatives. Key features Audra Security portfolio The announcemen...
Arctic Wolf® Labs, a global pioneer in security operations, has published the findings of its 2025 predictions report revealing the cybersecurity trends set to dominate the threat landscape over the next year. The report predicts social engineering and ransomware attacks to be some of the most common attack types in 2025, allowing threat actors to effectively bypass defenses and gain entry to victim organizations. Weaknesses in identity and access management (IAM) systems, alongside a conti...
Elite Interactive Solutions, a remote video guarding pioneer using proprietary intelligence and integration to achieve proven crime prevention, announces the company has produced a new series of educational videos. Consisting of five segments ranging from just over four minutes to a little more than seven, the series is designed to provide a synopsis of remote guarding along with more detail on some of the key aspects in a straightforward and easily digestible way. Panel of subject matter exp...
In a vidcast interview for journalists, industry pioneers Kirsten Bay, CEO of Cysurance, and Enterprise Security Architect Randle Henry from Check Point, shed light on the emerging role of insurability assessments in bridging the gap between cybersecurity and insurance. The conversation put into context the Cysurance Insurability Assessment Program, Powered by Check Point – a joint initiative that is bending the risk curve in favor of businesses by assessing and managing their cyber...
As part of its Pan-European expansion plan, Integrity360 has acquired pioneering European PCI QSA (Payment Card Industry Qualified Security Assessor) and cyber security services company Adsigo. The terms of the transaction were not disclosed. The acquisition will enable Integrity360 to expand further into continental Europe and provides additional skilled resources to its existing substantial PCI and cyber security compliance teams. QSA organization by Visa Adsigo has a pioneering position in...
IT services and solutions provider, Roc Technologies, has announced the launch of its Security Operations Center (SOC), advancing its mission to provide accessible cyber security solutions to businesses and public sector organizations of all sizes across the UK. The SOC offers 24/7/365 monitoring and tailored security services that enhance resilience against the growing landscape of increasingly sophisticated cyber threats. A modular and scalable approach enables small and mid-sized organizatio...
Ivanti, the tech company that breaks down barriers between IT and security so that Everywhere Work can thrive, released its latest report, Generative AI and Cybersecurity: Risk and Reward, which explores how organizations are navigating the complexities of generative AI (GenAI) in the realm of cybersecurity, highlighting both the opportunities and challenges it presents. GenAI is a powerful tool that can be used by security teams to protect organizations, however, it can also be use...
The National Cyber Security Center (NCSC) new cyber chief, Richard Horne, has issued a stark warning about the growing complexity of “widely underestimated” cyber threats. Speaking at the launch of the NCSC’s eighth annual review, Richard Horne, Cyber Security Chief, commented: “What has struck me more forcefully than anything else since taking the helm at the NCSC is the clearly widening gap between the exposure and threat we face, and the defenses that are in place to...
Wipro Limited, a pioneering technology services and consulting company, announced a partnership with Netskope, a Secure Access Service Edge (SASE) pioneer, to provide global enterprises with an integrated service that optimizes and improves cybersecurity outcomes for people, processes, and technology investments. Wipro’s CyberTransformSM Optimization Service, powered by Netskope, analyzes organizations’ current cybersecurity and infrastructure investments, provides consolidation gui...