Cyber security - News
Last week in New Delhi, the Future Crime Summit 2025, India's largest gathering on cyber innovations and synthetic threats, brought together over 1,000 experts, law enforcement officials, and defense pioneers to discuss the growing challenges posed by cybercrime and the latest AI-driven solutions. Key topics included AI-enabled attacks, ransomware, crypto fraud, blockchain vulnerabilities, and the risks of quantum computing. The founder of the Future Crime event, Professor Dr. Triveni Singh, al...
Netwrix, a vendor specializing in cybersecurity solutions focused on data and identity threats, released the new component of Netwrix Privilege Secure, which simplifies secure remote access for distributed workforces and third-party vendors. The new add-on reduces the attack surface by eliminating traditional VPN dependencies through granular, identity-based access control. It enables employees to access critical systems securely from any location, grants just-in-time privileges to reduce risks...
Artificial Intelligence Technology Solutions, Inc., along with its subsidiary Robotic Assistance Devices Residential, Inc. (RAD-R), announced that home security will soon take a major leap forward. RADCam™ Version 15 brings smarter AI-driven monitoring, real-time package protection, and an interactive concierge that makes the home more secure and responsive. Future of proactive security Traditional security cameras simply record events, leaving them to react after the fact. R...
ACI’s 15th Forum on Global Encryption, AI, Cloud & Cyber Export Controls takes place on March 26–27, 2025, in San Francisco and via livestream. The 2025 program will include an enhanced focus on how to comply with evolving “know your customer” and end-user management rules for cloud and AI! No other event in the U.S. offers two days of content-rich, practical takeaways on these critically important aspects of export compliance. Featured speakers John D. Sonderman...
The UK’s AI Safety Institute has been recast as the UK AI Security Institute, bolstering protections against AI risks facing national security and crime, and delivering a key pillar of the government’s Plan for Change. The pivot reflects a focus on serious AI risks with security implications, including malicious cyber-attacks, crimes against fraud and the development of weaponry. Assess the risks by frontier AI AI Security Institute will partner with national units, incl...
HackerOne, a pioneer in finding and fixing critical vulnerabilities and AI safety issues, published When ROI Falls Short: A Guide to Measuring Security Investments with Return on Mitigation, a report that revealed security pioneers’ negative perceptions surrounding ROI for the measurement of cybersecurity value. The whitepaper also introduced Return on Mitigation (RoM) — a new metric that helps security pioneers quantify the financial value of protecting their businesses from c...
Under the motto “Navigating Tomorrow”, MOBOTIX partners participated in this year's MOBOTIX Partner Conference in Langmeil, Rhineland-Palatinate. It was an impressive industry meeting at which MOBOTIX partners were able to discuss trends and developments in video technology and get to know the latest MOBOTIX solutions, in some cases even before they were launched on the market. European and international partners The MPC for the Latin American market had already taken place in Ca...
Corporate Security Advisors (CSA), the premiere management consulting firm specializing in corporate security, announced that it has been selected to join the prestigious American Hospital Association (AHA) Preferred Cybersecurity and Risk Provider Program as the first Preferred Physical Security Advisory Services Provider. CSA will play a critical role in helping hospitals and healthcare systems nationwide enhance their physical security strategies to protect patients, staff, and facilities....
LogiMAT 2025 is hosting a Mobile Robotics User Forum to complement the AGV and AMR solutions on display in Hall 8. Experts from Forum AGV will offer visitors a broad program of information and personal consultation in five categories covering the current trends in how AGV systems and AMRs are deployed. Pre-registration is requested. Mobile robotics is a topic of growing importance for those seeking efficient material flows in intralogistics. But potential users are often daunted by the prospect...
Cyber security and artificial intelligence (AI) are set to fuel a 5 percent rise in IT spending from European businesses during 2025, according to market analysis from Forrester. Total IT spending is projected to reach $4.9 trillion in 2025, Forrester’s Global tech forecast 2024-2029 predicts, with GenAI, cyber security, and cloud services to drive growth by 5.6 percent, compared to just 4.6 percent in 2024. Investment on cyber security and AI Analysts from Forrester believe that concen...
Matrix reinforced its position as a key player in the IT sector with a strong presence at the CMDA B2B IT Expo 2025, held in Pune. The event, a pivotal platform for IT industry pioneers, showcased cutting-edge innovations, fostering collaboration and growth in the ever-evolving technology landscape. Showcasing IT-centric Innovations At the expo, Matrix exhibited its Enterprise-Grade Security and Telecom Solutions, designed to meet the evolving demands of businesses and government entities. Fr...
Matrix, a pioneering OEM in Security and Telecom solutions, is excited to announce its participation in the 12th edition of IBEX India 2025, scheduled for February 13 - 14 at Jio World Convention Center, BKC, Mumbai. IBEX INDIA is a premier trade fair and conference connecting the BFSI Tech and Fintech sectors with cutting-edge banking technologies, where Matrix will showcase its advanced security solutions tailored for the banking sector, ensuring robust surveillance and access control for a s...
Security and threat intelligence technology company, Silobreaker announced its partnership with the Health Information Sharing and Analysis Center (Health-ISAC) as a Community Services Partner. Health-ISAC is a global non-profit organization dedicated to improving the security and resilience of the healthcare sector. It connects thousands of health security professionals worldwide to share real-time insights, alerts, and best practices. This enables healthcare organizations to better detect, mi...
Threat Evolution, an advanced cybersecurity training and consulting platform, has officially achieved Cyber Essentials certification, reinforcing its commitment to helping businesses strengthen their digital security. Part of the Magenta Security Services family of businesses, which is a pioneer in sustainable security solutions, Threat Evolution provides cutting-edge cybersecurity training and consulting services designed to mitigate cyber risks. Common entry point for cyber threats Threat E...
The International Maritime Cyber Security Organization (IMCSO), an independent maritime standards organization, has released its cybersecurity testing methodology for those maritime vessels looking to assess their risk and join the Cyber Risk Registry, a risk register database maintained by the IMCSO. The methodology aims to provide IMCSO-accredited cyber consultants and the senior maritime personnel they will be assessing with standardized testing by outlining test scope and the language...
Virtual Security Showcase has opened registration for their next VSS Tech Talk: Transforming Security into Safety for Food Processing and Manufacturing, scheduled for February 27th from 2-3 PM EST. Attend this informative online event where a panel of cyber-physical security experts will discuss how to transform leading security technologies into safety solutions to better protect people, property, and products at food processing and manufacturing facilities. Panelists S...
Video security systems have become a critical asset across industries, with pioneers confident in their systems’ resilience against cyber threats. Research from Hanwha Vision Europe shows that more than nine in 10 security and IT managers in the UK, France, Germany, Spain, and Italy believe their video systems are well-protected. Security practices Overall, confidence is high across different organization sizes, countries, and sectors. In Italy, confidence reaches 97%, while Spain...
Indonesia is set to host the most anticipated 10th NXT CX-DX Summit & Awards which will explore the intersection of Customer Experience (CX) and Digital Transformation, bringing together industry pioneers, innovators, and decision-makers to discuss strategies for driving business growth in the digital age. Scheduled on the 11th of February 2025 at JW Marriott in Jakarta, Indonesia the summit will feature insights from global thought pioneers, successful case studies, and practical strategie...
In Indonesia, cybersecurity stands as a critical concern, despite its relative insulation from global advanced persistent threats. Nevertheless, cyber-attacks persist, impacting citizens and government institutions alike. As businesses transition to digital platforms, the increased implementation of transformative technologies introduces a slew of security risks, endangering critical infrastructure and sensitive data. The Indonesia Cybersecurity market is projected to grow from US$ 2.05 billion...
The Z-Wave Alliance, the standards development organization dedicated to advancing the smart home and Z-Wave® technology, is excited to announce the launch of the 2024B Z-Wave Specification package as well as the introduction of a new Accelerator Membership Level aimed at empowering startups and young companies in the IoT ecosystem. These initiatives demonstrate the Alliance’s ongoing commitment to innovation, collaboration, and ensuring interoperability in the IoT market. Z-Wa...
Nutanix, a pioneer in hybrid multi-cloud computing announced the findings of its seventh annual Enterprise Cloud Index (ECI) survey and research report, which measures global enterprise progress with cloud adoption. The report sheds light on Generative Artificial Intelligence (GenAI) adoption, investment priorities, and benefits along with key challenges organizations face to meet the demands of these emerging workloads. GenAI application adoption As GenAI application adoption...
artius.iD, the global pioneer in secure, self-managed, decentralized individual identity solutions, has appointed former Oracle and Google enterprise sales pioneer Jeffrey Keplar to its Board of Strategic Advisors. Jeffrey Keplar Keplar has more than three decades of experience building sales teams and pioneering enterprise tech sales strategies at the world's largest businesses. He held various sales leadership roles at Oracle over nearly 20 years, ultimately serving as Group Vice P...
Cyware, the provider of threat intelligence management, low-code/no-code security automation, and cyber fusion solutions announced an important collaboration with Team Cymru to pre-configure Team Cymru’s industry-pioneering threat feeds into Cyware’s Threat Intelligence Platform (TIP). This packaged solution delivers real-time visibility into botnets, malware, command and control (C2) infrastructure, and external malicious activity, empowering organizations to detect and respond fas...
Cowbell, a provider of cyber insurance for small and medium-sized enterprises (SMEs) and middle-market businesses, has launched a new Cowbell Resiliency Services (CRS) unit in response to a rise in the frequency, severity, and diversity of cyber threats as a complement to its existing risk management program. Cost of data breach Driven by AI advances and an increasingly complex geopolitical landscape, recent reports show the average global cost of a data breach has reached $4.88m, a 10% increa...
C5 Group is proud to announce its upcoming event, the 6th European Forum on Global FDI Reviews taking place on June 3 –4, 2025, in Berlin will delve into the critical changes affecting investment professionals working amid evolving foreign direct investment screening regulations, complex and sometimes obstructive merger controls, and complex foreign subsidy limitations. The most trusted Foreign Direct Investment Review Forum in Europe gathers the foremost FDI practit...
SenseOn has unveiled the integration of new AI-powered case summaries into its adaptive cybersecurity intelligence platform. This latest AI-native feature is designed to help security teams instantly understand critical threats and accelerate response times by transforming complex security incidents into clear, actionable intelligence. Case summaries The new capability uses generative AI, which has been trained by and acts as an extension of the organization’s SOC team, to develop...
Nanodems, a pioneer in Physical Security Information Management (PSIM) announced a strategic partnership between TKH Security, a global pioneer in security and parking guidance technologies. TKH Security TKH Security, based in Zoetermeer, the Netherlands, with over 25 years of experience, provides innovative solutions for security, asset & site, and parking guidance management. Operating in over 80 countries with 12 offices worldwide, TKH Security is committed to delivering high-quality,...
Matrix, an OEM in Security and Telecom solutions, is excited to announce its participation in the 27th CMDA IT Expo 2025, scheduled for February 10-11 at The Westin, Koregaon Park, Pune. As a premier platform for engaging with vendors, channel partners, and industry stakeholders, the event will showcase Matrix's innovative solutions aimed at enhancing safety, streamlining operations, and enabling seamless communication across critical sectors. Cyber-secured IP video surveillance Matrix...
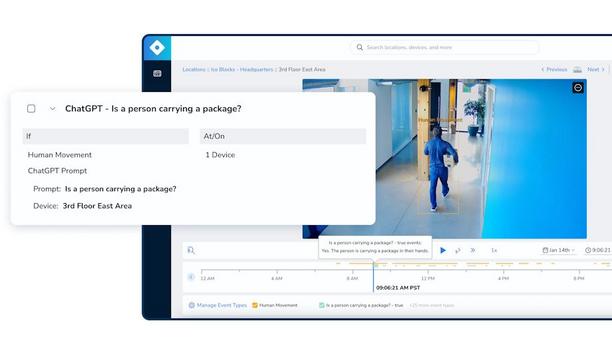
Rhombus, a pioneer in cloud-managed physical security, announced the launch of three new additions to its AI portfolio that transform how organizations search, analyze, and respond to security events. Powered by the release of Rhombus Faces 2.0, combined event search, and a new ChatGPT integration, these AI-powered tools enable security teams to instantly locate specific incidents through natural language queries and automation—dramatically reducing investigation time and improving r...
AxxonSoft, a pioneer in AI-powered video management software, and Eurotech, a pioneer in edge computing solutions, are launching a strategic partnership to deliver advanced AI-enabled video surveillance solutions. AxxonSoft’s intelligent VMS This collaboration combines AxxonSoft’s intelligent video management system with Eurotech’s cybersecurity-certified ReliaCOR hardware platforms featuring the NVIDIA Jetson Orin technology for AI at the edge. In cooperation, AxxonSoft and...