John L. Moss

John L. Moss
CEO, S2 Security Corporation USMr. Moss has been an innovative force in security systems technology for more than 30 years. Before founding S2 Security in 2002, in 1981 he created Software House (now owned by Tyco International). He has led the creation of two successful companies and over a dozen major commercial products in the industry.
News mentions
Hakimo, a technology company dedicated to modernising physical security through its artificial intelligence (AI) software, announced $6 million in new funding led by Rocketship.vc, with participation...
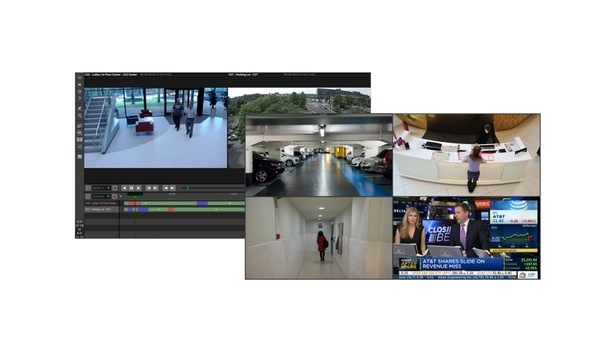
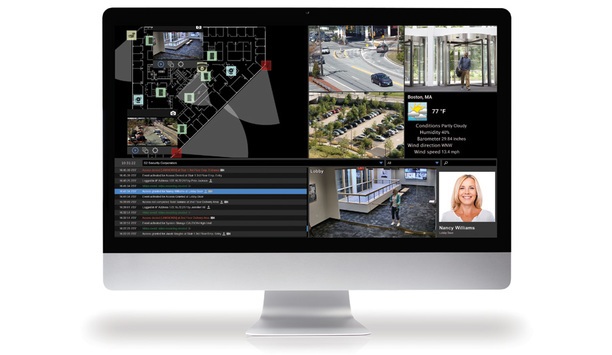
LenelS2 announces major enhancements to VRx, a next-generation video management platform that features advanced analytics based on deep learning technology. VRx provides a unified access control and v...
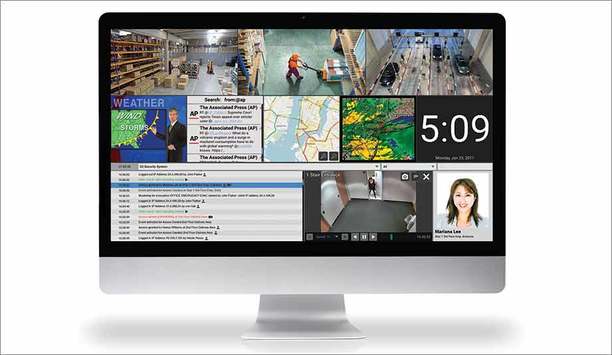
S2 Security, the developer of complete enterprise security solutions, announces S2 Magic Monitor Version 6.1. With a range of media options that now includes Internet-streamed TV as well as enhancemen...
S2 Security, a developer of complete enterprise security solutions, has announced the availability of S2 Magic Monitor Version 6. S2 Magic Monitor unifies access control, video surveillance, forensics...
S2 Security, a provider of IP-based access control, video management and mobile security management systems, introduced S2 Magic Monitor Version 5. S2 Magic Monitor unifies access control, video surve...
S2 Security Monitor Version 4 includes audio support for cameras, video clips and online digital content S2 Security, a provider of IP-based access control, video management, and mo...
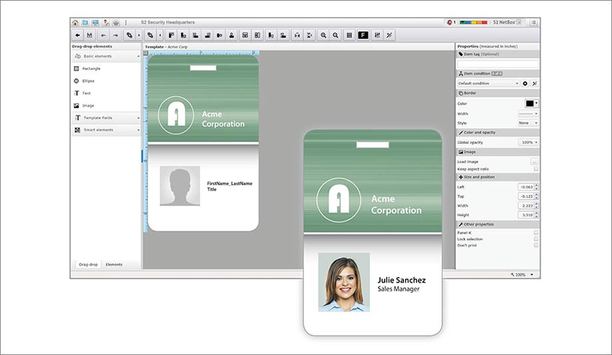
Latest version of access control and event monitoring software also introduces S2 NetBox Virtual Machine and S2 NetBox Offsite Recovery S2 Security, the leader in IP-based access co...
S2 Security, the leader in IP-based access control, video management and mobile security management systems, recently released NetBox software Version 4.8. With new integrations and many enhancements...
S2 Security, the leader in IP-based access control, video management and mobile security management systems, recently released Version 2 of S2 Magic Monitor, an award-winning dynamic digital canvas th...
S2 Security, the leader in IP-based access control, video management and mobile security management systems, recently introduced S2 MicroNode Plus, the company’s latest two-reader panel for S2 N...
Customer support, application engineering and training will be integrated and reinforced under new executive leadership S2 Security, the leader in IP-based access control, video man...
S2 Security, the leader in IP-based access control, video management and mobile security management systems, recently announced Version 4.7 NetBox software featuring a new, icon-based user interface a...
S2 Security, the leader in IP-based access control, video management and mobile security management systems, today introduced S2 NetVR® 600 video management system, the newest addition to S2 Secur...
S2 Security, the leader in IP-based, integrated access control, video management and mobile security management systems, recently announced the introduction of S2 Network Node VR, an intelligent field...
More attention needs to be placed on the development of readers that can accommodate Wireless and Wi-Fi technology Many of the changes in the access control market are happening at...
Access control can sometimes get overshadowed by video surveillance Technology is shifting rapidly in the access control market, but another obstacle is the need to communicate...
S2 Mobile Security Officer is designed for speed of information sharing, and real time response to situations in the field S2 Security, the leader in IP-based integrated physical se...
In support of its channel partner programs, S2 Security has appointed Sarah as Senior Director of Marketing S2 Security, the leader in IP-based integrated physical security systems,...