Nedap - Experts & Thought Leaders
White papers from Nedap
Achieving Frictionless Physical Access Control With AEOS
DownloadAccess Control: Bringing Efficiency To Your Lifts' Automatic Destination System
Download6 Ways Access Control Can Contribute To Your Business Continuity
Download3 Reasons To Migrate To A New Access Control System
Download5 Steps To Finding The Right Access Control System For You
DownloadDo You Know The Weakest Link Of Your Access Control System?
DownloadHow To Select An Access Control System In 5 Steps
DownloadNedap’s Long-Range Radio Frequency Identification (RFID) Systems For Automatic Vehicle Identification (AVI)
DownloadLatest Nedap Security Management news & announcements
Manufacturer ROCKWOOL International A.S. has chosen Nedap’s Global Client Programme to secure its offices and factories worldwide. AEOS, the physical security platform by Nedap, installed during the program, enables ROCKWOOL to establish a truly global security policy and unified work processes. An advanced project rollout, the Global Client Programme is developed for large multinationals and offers several benefits, including standardization across sites, shorter implementation times and cost efficiencies. Standardizing Company’s Security Measures The Global Client Programme connects all of ROCKWOOL’s factories and office premises, and standardises the company’s security measuresROCKWOOL has 28 factories across the world. The Global Client Programme connects all of these factories and ROCKWOOL’s office premises, and standardizes the company’s security measures throughout the world. Fokko van der Zee, managing director at Nedap Security Management, says: “The implementation of a standardized security solution across the world is a complex process. It involves a large project spanning many years and involving many stakeholders, and demands a high level of project management. In the absence of a structured program with defined guidelines, a global security rollout is likely to be a stressful execution. That’s why we set up our carefully designed Global Client Programme.” ROCKWOOL Digital Service Lead, Matthew Thorne, agrees: “We’ve worked with Nedap over the past few years and recently became a member of their Global Client Programme. Now we’re equipped with the people and tools we needed to standardize our physical security solution. The Global Client Programme also minimizes risk and guarantees compliance. It really meets our needs in every possible way.” Central Security Platform Saves Money The program helps achieve cost savings by avoiding initial setup costs per site and having one central security platform instead of severalThe Global Client Programme is designed to ensure monitoring and control during every step of the rollout process. Timon Padberg, responsible for business development at Nedap Security Management, explains: “The repetitive nature of local site deployments allows us to work with models and templates, such as standard proposal and calculation documents. We can therefore produce a scalable process that ensures uniformity and a consistently high quality of implementation across each site.” By using the Global Client Programme, ROCKWOOL is aiming for uniformity and alignment across all sites. The program also helps achieve cost savings by avoiding initial setup costs per site and having one central security platform instead of several. Moreover, there are significant savings on operational and maintenance costs due to shared services and economies of scale.
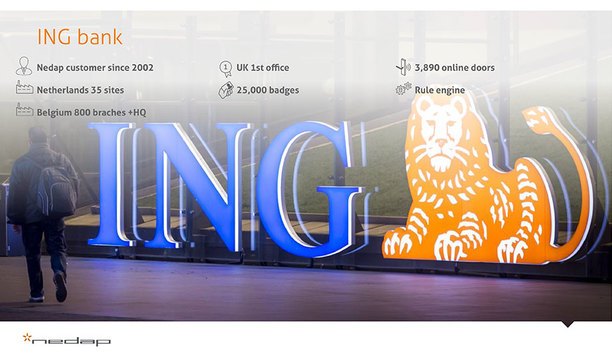
Security management in banking is a discipline unlike any other. Rather than integrating all security into one centralized system, some banks choose decentralized security for their branch offices. AEOS, a leading platform in integrated security, turns out to be just as effective when deployed decentrally. ”We were already using Nedap AEOS in our headquarters, as well as various regional offices. Then, in 2011, the security system used by our 800 branch offices in Belgium needed to be extended with access control. Because we were already aware of AEOS’s capabilities and very satisfied with its performance, it was a logical step to ask Nedap to solve our problem.” - Joris de Greve, Security Manager at ING Belgium. Key Management Challenge ING’s 800 branch offices in Belgium were already equipped with autonomous intrusion detection and camera surveillance. All doors and their accessories, such as locks, push buttons and door contacts, were monitored and controlled by the intrusion detection system. Doors were opened and closed using keys in security cylinders. A central alarm management system handled alarms coming in from local intrusion control systems.It was virtually impossible to keep track of the physical keys and who was authorised to use them" Key management had become a problem, according to De Greve. ”It was virtually impossible to keep track of the physical keys and who was authorized to use them. We had no central database in which authorisations could be assigned or retracted.” In addition, changing locks, replacing keys and keeping key plans up to date had become difficult. “It was time for an electronic access control system,” explains Peter Rommens, Country Manager at Nedap Belgium. “Since all peripherals were connected to the intrusion detection system, the scope of the project was clearly defined. We were looking purely at access control at one or more doors per office.” Expanding The Centralized AEOS System After considering a wide range of solutions, ING eventually selected two for further evaluation. One was to add access control to the existing intrusion detection systems. This was technically the least complicated option, because the basic infrastructure and necessary hardware were already in place. The other option was to expand the centralized AEOS system that was already up at headquarters and regional offices to include access control at the branch offices. The latter offered the major advantage of being able to connect all branch offices to one central database, while retaining the ability to delegate responsibility for authorisations to lower-level security management layers. Other benefits of this option included its system architecture, the proven stability of the system for large numbers of offices and cardholders, the system’s scalability and flexibility, the native IP controllers’ ability to communicate peer-to-peer and bypass the server, and the system’s redundant facilities and security (failsafe, switching servers, etc.). Flexible And Extra Secure The factor that clinched the deal was that AEOS allowed for decentralized management of separate units and the use of entrance filters. This meant local offices could be authorized to manage their own security without access to other offices’ data, Joris de Greve explains. “The bank’s security structure is based on central access to buildings and central facilitation of technical solutions, but decentralized security and access responsibility per zone. Therefore, the system must allow us to cluster cardholders into groups with different authorisations. AEOS supports this.”Cardholders who lose or forget their badge are issued a replacement while the original badge is invalidated" “Another factor was ING’s requirement that authorisations not be assigned to a badge, but to a cardholder,” adds Rommens. ”This builds in extra security: cardholders who lose or forget their badge are issued a replacement while the original badge is invalidated. This guarantees there are no unaccounted-for, authorized badges ‘floating around’. Decentralized Approach ING combines centralized and decentralized policies. Overall security policy is set at top headquarters; security management there decides who is authorized to manage accounts and which authorisations may be assigned. This is part of the bank’s security structure. We ask ING Belgium Security Manager De Greve to illustrate. “For example, the Milan office uses a server in Belgium and the technical facilities provided by central security management. However, the management in Milan are in full control of who is allowed access to their building and when,” he says. User training is also decentralized. There are some 500 administrators, all of whom were trained internally and decentrally. AEOS enables this flexibility. Because AEOS is web-based, interventions are simply and swiftly carried out. Keeping An Eye On Things A consequence of decentralisation is the need for reports. “Central management wants to keep an eye on what is happening at the various branch offices,” De Greve says. ”Is security functioning properly? And are offices complying with security policy?” He believes reports “are also a valuable management tool.” For example: how many people are at work at any given time, or whether people only come in a few times a week. “This helps us to make sound decisions concerning flexible office space, for instance, and that’s an important way to reduce costs.” Proxy Offices Roll-Out ING BE has two different types of offices: Proxy offices where all money is distributed by ATMs and Full Service where staff behind counters provide service. In both types of branches local staff is present and mobile specialists are available to respond to specific needs or questions customers may have. Nedap is currently installing AEOS at the 800 Belgian branch offices at an approximate rate of nine offices per week. Peter Rommens explains how the roll-out is being organized logistically: “In preparation for installation, ING centrally creates the appropriate authorisations in AEOS. Then, Nedap’s business partner defines the configuration and uploads this to the controller. This means on-site installation is quick; once the controller is connected and deployed, the system is up and running.”Each office is prepared for expansion of its access control or the addition of other security functionalities" AEOS At Proxy Offices “The bank preferred our proposed solution, with one AP4803x per branch office, over a solution with one or more AP6003 network controllers per office but only one AEpu per ten offices,” Rommens says. “Although having one AEpu per office is costlier, availability is more sure with the AP4803x and it offers more long-term advantages. It means each office is prepared for expansion of its access control or the addition of other security functionalities.” Proxy offices are defined as individual access control zones. Each office has its own profiles defining who is allowed access and on what basis. Proxy offices are secured with readers and a key replacement badge. The alarm system runs separately from the access control system. The badge only provides access, while arming and disarming the alarm system requires identification. In line with existing policy, if an unauthorized person finds a badge and tries to use it when the office is empty, this sets off an alarm. If a person tries to use a stray badge when the office is manned, he or she is immediately exposed by staff (social control). “Badges are also blocked based on expiry date or end of contract because in general the fewer badges in circulation and the fewer people with access, the smaller the security risk,” says De Greve.
Building on their highly popular series of integrated high-security solutions events, the CNI Security Group has announced their next event, ‘Protecting CNI Scotland – The importance of cyber-secure solutions in critical national infrastructure’. Designed for all end users, consultants and system designers in the CNI sector, the free-to-attend event will be held at Dakota Eurocentral, Motherwell, on Wednesday 19th November, between 9:30 am and 4 pm. The event will show insights from multiple perspectives into the importance of cyber-secure solutions in critical national infrastructure environments. Cybersecurity and end-users The format of the day will include presentations and panel discussions from specialists in cybersecurity and end-users in the CNI space - all looking to share their own 'real world' experiences. In addition, pioneering security industry manufacturers barox Kommunikation, Hirsch UK, Nedap Security, ISM Ltd, Commend, Overview and Lochrin Bain, will be showcasing the very latest in cutting-edge CNI/NPSA security technologies - suitable for deployment across high security sites, including, utilities, power, prisons, nuclear, and airports. Cyber and physical security The highlight of the morning program will be a keynote presentation from the award-winning Mike Gillespie FCIIS MSyl CIRM of Advent IM. A specialist in Cyber Security and Governance, Mike is a Chartered Institute of Information Security Fellow and Senior Vice President Europe at CSCIS, and a seasoned expert in cyber risks. A former Security Institute Director, he advises globally and contributes to major media, and will be speaking about cyber and physical security and promoting awareness of organizational threats. National security policy and implementation In the afternoon, what is set to be a mind-blowing panel discussion session, entitled ‘What lessons have we learnt from experience? What does the future hold? How can we be more CNI resilient?’ comprising of senior pioneers in the CNI space, will be led by Chair of CNI Scotland, Malcolm Warr OBE. Malcolm has over 20 years’ experience in National security policy and implementation, and has chaired defense, cyber and physical security conferences internationally. Details of additional speakers and panellists will be released in the coming weeks. Cyber security on a global scale “We are so excited about our first event in Scotland, particularly as it is building up to be the best one so far. Once again, we have a fantastic line-up of presenters and panellists, from specialists in cyber security on a global scale, to end users in the CNI space,” says Sara Fisher, Chairperson CNI Security Group. “More than that though, and on a personal note, I feel extremely privileged to be working with such an amazing team of people, from fellow CNI Security Group members and partners, to those experts who are giving up their time to share their knowledge and experience with our audience. Our delegates are in for a really spectacular day.” Full agenda and register for the free-of-charge event Lunch will be provided for all attendees, and the day will finish with post-event drinks. To see the ‘Protecting CNI Scotland’ full agenda and register for the free-of-charge event, interested parties should visit the website. As places are strictly limited, allocated tickets will be offered on a ‘first come, first served’ basis, so please book early to reserve your place. Due to limited space, strictly no other manufacturers or suppliers can be accepted to this event.
Insights & Opinions from thought leaders at Nedap
With the rise of organized retail crime (ORC) making headlines, retailers are grappling with the dual challenge of safeguarding both their staff and store assets, while addressing the economic pressures that impact profitability and consumer demand. RFID technology The key lies in identifying effective solutions to counter the current surge in ORC, enabling retailers to secure their vulnerable staff and protect inventory for paying customers. Technology plays a crucial role in supporting brands on this mission, with RFID technology continuing to be a valuable solution. It aids retailers in gaining better control over retail crime, leveraging inventory data. The ongoing surge in retail crime Inflation has elevated the challenges around affording items, prompting criminals to target the retail sector Seen as a global issue, the British Retail Consortium recently reported that incidents of theft have increased by 27% across 10 of the largest cities in the UK, with some cities reporting up to a 68% increase. In the US, retailer Target reported an inventory loss of $500 million for 2023, amounting to a 100-basis point hit to gross margins in 2023. The current surge in theft is not attributed to a singular cause. Inflation has elevated the challenges around affording items, prompting criminals to target the retail sector. Lack of preventive measures A significant contributing factor is the lack of sufficient preventive measures by law enforcement, which in some cases has led to a rise in more severe incidents. However, the implementation of technologies like RFID allows retailers to efficiently build cases against criminals, putting them in a stronger position when it comes to reporting thefts. Not all retail crimes are orchestrated by large entities or executed through sophisticated methods. Some stores have seen a reduction in staff numbers and, as a result, there are fewer people on the shop floor, making it easier for shoplifters to carry out their activities unnoticed. The true impact of retail crime Over 70% of retailers believed the threat of ORC had increased over the past five years, according to a recent survey The impact of retail crime on businesses extends beyond financial and economic consequences; it has also led to a surge in violence against retail staff, an ongoing trend elevated by the pandemic. Over 70% of retailers believed the threat of ORC had increased over the past five years, according to a recent survey conducted by the National Retail Federation. This escalation in violence not only results in immediate repercussions but also contributes to long-term mental health issues for staff, fostering an atmosphere of insecurity that has compelled some retailers to close their physical stores. Policy implementation Given the challenge of staff retention across various businesses, addressing retail crime becomes an even more urgent matter. Additionally, retailers are wary of their employees facing potential danger and the prospect of legal action. Consequently, many have implemented policies prohibiting employees from actively intervening when confronted with shoplifters. Privacy concerns with facial recognition Retail crime also affects customers, as businesses seek to offset losses by raising prices Retail crime also affects customers, as businesses seek to offset losses by raising prices, further burdening financially strained consumers. The presence of visible security systems not only makes stores more hostile but also diminishes the overall customer experience. While facial recognition technology is considered a potential solution, privacy concerns have emerged in its various applications. Today’s problems, yesterday’s solutions Retailers are resorting to historic measures such as steel cables, physical monitoring, or plastic screens to resolve customer issues. However, the reality is that these solutions are unfit for solving the problem, causing friction for both customers and staff. Digital solutions The newer approach involves equipping retail staff with body cams and providing new training The newer approach involves equipping retail staff with body cams and providing new training to deter shoplifters. Some stores are even offering the police discounted food and beverages to encourage their presence. The responsibility lies with management teams to seek effective solutions. In an era dominated by data and technology, retailers must shift their focus from traditional security methods to digital solutions that align with the challenges of today’s society and modern retail environments. Shrinkage When discussing theft or organized retail crime, retailers commonly use the term "shrinkage," referring to not only theft but the broader issue of lost inventory. Additional drivers of shrinkage include damage, fraud, and internal theft. A significant problem arises as losses are often based on guesswork and estimates rather than concrete numbers. Retailers may lack a comprehensive understanding of their inventories, further increasing the issue of shrinkage. Combating shrinkage Utilizing RFID technology notably helps in boosting inventory accuracy Some retailers still struggle with limited knowledge of the whereabouts of items, a challenge heightened by the issue of shrinkage. Utilizing RFID technology notably helps in boosting inventory accuracy. This enhancement enables retailers to obtain a clearer understanding of their inventory and the precise locations of items. Comprehensive strategy Changes in the in-store experience have highlighted the relevance of RFID, especially as self-service checkouts encounter double the shrinkage levels compared to traditional checkout stores. To combat retail theft effectively, a comprehensive strategy should involve the integration of labels, deactivation, electronic article surveillance, and data analytics. This combination works synergistically to reduce shrinkage and enhance product availability. Retail data analytics platforms RFID data can swiftly alert nearby stores, providing an opportunity for staff to monitor shop floors Linking hardware to an underlying data analytics platform empowers retailers to make more informed decisions. Retail data analytics platforms delve into alarms, deactivations, and visitor metrics, providing a deeper understanding of theft patterns. RFID technology drives efficiency by pinpointing frequently stolen items, allowing for the identification of theft patterns. In instances of flash mobs in major metropolitan areas, RFID data can swiftly alert nearby stores, providing an opportunity for staff to monitor shop floors and incoming customers. Real-time optimization The crucial question remains whether both shoppers and retailers are prepared to shoulder the responsibility for these additional precautions. Nevertheless, these changes leverage data more effectively, optimizing loss prevention strategies almost in real-time rather than relying on biannual inventory counts, therefore transitioning from static to dynamic loss prevention. Holistic approach Striking a balance between security measures and providing a seamless shopping experience is key In a retail environment, not all items require protection, and prioritizing the safeguarding of the most frequently stolen and valuable items can significantly impact shrinkage. A holistic approach to retail theft is imperative, considering the entire journey of an item through the retail environment. Striking a balance between security measures and providing a seamless shopping experience is key. Protection without hindrance As stores move towards being checkout-free, retail criminals (or ORC gangs) will be presented with lucrative opportunities to steal, so retailers need to be one step ahead by introducing unobtrusive and effective technology solutions. For example, case building can be improved with item-level data. RFID data offers a more precise means of assessing the value of stolen items compared to relying solely on CCTV. It provides detailed insights into the specific items removed from the store and the timing of these incidents. This proves beneficial in tracking repeat offenders. Increased visibility with a proactive approach The modern retail environment continues to evolve and criminals are never far behind. RFID technology plays a crucial role in minimizing shrinkage by enhancing inventory visibility. Moreover, it leverages the power of data to stay ahead, enabling better predictions of retail crime and the formulation of prevention strategies. This proactive approach allows for the implementation of more tailored solutions to alter outcomes positively.
How can security system integrators not just survive but thrive in today’s IT-led market? The key seems to be in training. As increasingly more clients look to integrate access control with IT environments, they want integrators with the specialist skills to achieve this. For integrators that don’t invest in training, the risk is being left behind. Because many security system integrators aren’t providing specialist IT support, manufacturers are now offering services to make implementations and integrations easier. This isn’t a scalable or desirable option for many manufacturers though, they don’t want to become integrators. The result? Manufacturers will be pushed into developing products that can be integrated with IT networks off the shelf. And this isn’t necessarily the best option for end user, manufacturer or integrator. With a growing number of cloud-based security solutions, integrators also face the threat of clients opting for installation-only services. How security system integrators can survive and thrive today It’s not all doom and gloom for security system integrators though. To avoid becoming redundant, or being downgraded to simple access control installers, there’s lots you can do to strengthen your position. Listen carefully Many integrators are reluctant to do this, but it’s a great way to demonstrate the depth of your experience One of the first ways you can distinguish yourself from your competitors is by really listening to what your clients want and need. You can then translate this into a security or access control application tailored carefully to them. Many integrators are reluctant to do this, but it’s a great way to demonstrate the depth of your experience and product knowledge. It’s far superior to carrying out a standard implementation, which can leave clients feeling they’ve not been listened to or given good value. Up your IT knowledge TCP/IP has become the standard for communication between devices and central server applications in access control and security in general. So every technician now needs to know how to connect IP devices to networks and configure them in the central application. This is only the tip of the iceberg though, there’s so much more that integrators now need to be proficient in when it comes to IT. From understanding a client’s WAN, LAN and VPN networks to back-up systems, encryption technologies, key management and transparent communication. It’s also important to know how to integrate applications at server level, whether you’re integrating two or more security systems or a HR database. Most integrators have begun to invest in one or two IT experts, but this usually isn’t enough to meet clients’ needs. To really stay ahead, it’s crucial to invest more heavily in IT training and expertise. Choose your portfolio carefully When considering your portfolio, ensure you check the background of each product’s manufacturer Ideally, your portfolio should be small but rich, which is more difficult than it sounds. Choosing products that will scale easily is complex, and you need to consider the potential for increased functionality or connectivity as well as scalability. When considering your portfolio, make sure you check the background and outlook of each product’s manufacturer. You don’t want to select items that are likely to be discontinued in the near future, which can often happen after a manufacturer is acquired, for example. Get in the cloud In the security market, the mid and low segments are already shifting to cloud-based solutions that need neither integration nor IT skills. This leaves you with opportunities for just installation and maintenance services, where profit opportunities are reduced. An alternative is to begin selling cloud-based security services yourself to help you attract and retain clients for the long-term. Give clients added commercial value As competition increases and budgets shrink, offering added value, to new and existing clients, is a vital way to differentiate your business. This will help you to not just defend against competitors but to grow your business and increase your profitability. Configuring access control reports for clients is just one example. It’s relatively straightforward to do but provides really valuable insight into visitor flow. This can then enable them to, for example, staff reception adequately and provide sufficient catering, which all improves the experience for visitors and employees. Providing this kind of consultative service, instantly pushes you up the value chain. Stay agile and well informed To survive and grow as a security system integrator today, the upshot is that it’s crucial to keep pace with the market’s ever-changing trends, technology and client needs. And, to make sure you’re ready to adapt and give clients the services they want, it’s vital to give your people the in-depth training they need.
SourceSecurity.com’s Expert Panel covered a lot of ground in 2017 about a variety of topics resonating in the security market. The most-read Roundtable discussion in 2017 was about a familiar and ongoing debate: What is an open system? Other hot topics that made the Top-10 list of Roundtable discussions included smartphones, buzzwords, standards and product life cycles. Here is a listing of our Top 10 Expert Panel Roundtable discussions posted in 2017, along with a “sound bite” from each discussion, and links back to the full articles. Thanks to everyone who contributed to Expert Panel Roundtable in 2017 (including the quotable panelists named below). 1. What is an open system? Is there a consensus in the marketplace on the definition of “open?” "Being truly ‘open’ means going above and beyond when designing your product line, keeping in mind the ability for end-users to easily interface your product with other open-platform solutions. That's why offering an open-platform design must be coupled with the ability to provide exceptional support through training, follow-up and innovation as they are brought to market.” [Mitchell Kane] 2. How are smartphones impacting the physical security market? "The security protocols on phones (such as fingerprint readers and encryption) have become some of the strongest available to consumers and are regularly used to access essential services such as banking. With this level of trust and user convenience from mobile device security, it makes sense to produce physical security systems that also take advantage of it." [John Davies] TDSi's John Davies says it makes sense to produce physical security systems that take advantage of trust and user convenience on mobile devices 3. What is the biggest missed opportunity of security systems integration? "Integrators need to be more savvy on how they can meet their customers’ IT and surveillance goals, from both a technology and services perspective. Being knowledgeable about new innovations can help integrators sell infrastructure, keeping that piece of business rather than losing server sales to a customer’s internal IT department. Integrators are tasked with ensuring surveillance customers can benefit from best practices, and solutions proven in the world of IT offer significant benefit." [Brandon Reich] 4. What are the security industry’s newest buzzwords? "End-to-End Security is a buzzword reflecting how cyber threats are increasing and the importance of ‘the security of security systems,’ especially for companies operating in the critical national infrastructure. Convergence has been a ‘hot topic’ for years, but has it really happened? In order to create true end-to-end security solutions, IT and physical security best practices need to be combined." [Arjan Bouter] End-to-End Security is a buzzword reflecting how cyber threats are increasing, says Arjan Bouter 5. What technology will have the greatest impact in the second half of 2017? "Cloud-hosted access control is poised to have the biggest impact in the second half of 2017. Organisations are looking to decentralise IT management and eliminate the need for overhead costs in hardware infrastructure and ongoing maintenance costs. This decentralisation is driving them to migrate their day-to-day systems to the cloud, and access control is no exception." [Melissa Stenger] 6. Are mergers and acquisitions good or bad for the security industry? “On the ‘pro’ side, consolidation is good for pulling together a fractured market, as vendors try to gain market share by acquiring solutions they may not otherwise have in their portfolio. On the ‘con’ side, however, consolidation restricts or limits innovation as the merged vendors strive to develop end-to-end solutions that reduce customer choices" [Reinier Tuinzing] 7. What new standards are needed in the security marketplace? "Do we need that many new standards, or do we need the industry to embrace the standards that are already in place? I believe that current standards like ONVIF and OSDP are sufficient in what they offer the industry. Members of the security industry just need to start thinking outside the box and realise that it is with standards in place that real industry growth can occur." [Per Björkdahl] 8. What will be the big news at ISC West 2017? "Security solutions that capture greater data and utilise analytics to transform the data into useful information, or business intelligence, will be the talk of the industry at ISC West this year. It’s not just about surveillance or access control anymore, but about who can best assess the end user’s interests and deliver an end-to-end solution that provides a value beyond the technology and a service beyond security.” [Richard Brent] When buying cameras, customers are often lured by lower upfront costs, but may end up paying more in the medium- to long-term because of lower quality, says Oncam's Jumbi Edulbehram 9. Why should a customer continue to buy “premium” surveillance cameras? "When buying cameras, customers are often lured by lower upfront costs, but may end up paying more in the medium- to long-term because of lower quality (requiring costly site visits and replacements), susceptibility to cyber-attacks, or lower quality of integrations with video management systems. Customers should certainly be prudent buyers and make sure that they’re paying for actual reliability/features/functionality rather than simply paying a premium for a brand-name product. When functionality and reliability are important, it always makes sense to ‘buy nice, not twice.’ [Jumbi Edulbehram] 10. What is an acceptable life cycle for a physical security system? "The answer to this question clearly depends on the seat you sit in. Manufacturers, integrators, distributors, consultants and engineers all have extremely different perspectives on this question. As a manufacturer, we design systems to have a lifecycle between 5 and 7 years." [Robert Lydic]