United Arab Emirates News
Real-time location systems allow organizations to communicate with visitors, employees, and staff in the event of an emergency Today's threat landscape is bigger and more broad than ever before, with an increasing number of emerging risks falling on the shoulders of security professionals in a variety of markets. Many of these leaders face the growing concerns of finding efficient, integrated solutions that provide protection from threats, but also can be used in everyday comm...
Project registration programs are a benefit manufacturers provide to systems integrators and security dealers who are bidding on an upcoming installation project. In effect, the integrator registers a project he or she is bidding on with a manufacturer, which offers pricing discounts to that integrator for that specific project. Such a program seeks to encourage an integrator to specify a manufacturer's products, while making it more difficult for a competing integrator to bid lower on a pr...
The International Organization for Standardization (ISO) describes standards as guidelines or characteristics for activities or for their results, aimed at achieving the optimum degree of order. They might include product standards, test methods, codes of practice, guideline standards, and management systems standards. In the security marketplace, there are many standards currently used, including those from organizations such as ONVIF, PSIA and ASIS International. Might the value of standardiza...
Access Control as a Service (ACaaS) has grown into a mainstream product offering from many access control manufacturers and the product offering is gaining significant growth in the market. With the adoption of this technology, end users and integrators need to ask several pertinent questions. This White Paper explores several important factors which must be understood in order for end users and integrators to make a sound decision when selecting an Access Control as a Service provider.What's...
A five-acre logistics site in the UK blighted by break-ins and theft of diesel is now being protected by a system that includes a combination of 30 highly reliable detectors from OPTEX, one of the world’s leading detection technology manufacturers. Established in 1995, Intake Transport operates one of the largest fleets on the British road today with one main depot and three satellites around the country. The main depot experienced a number of incidents where diesel was being stolen dire...
Part 4 in our Intercoms in Security Series The ONVIF standard makes it simple to integrate the intercom with other ONVIF-compliant video management systems, access control solutions, and cameras Open standards are enabling new capabilities in the intercom market, some of it driven by the transition to systems based on Internet protocol (IP). Today’s most-used phrase in the intercom business is interoperability, given that the intercom is integrated with solutions s...
The Dahl Auto Plaza in Winona, Minnesota is part of an auto dynasty that first began in 1911, when Andrew H. Dahl began selling Ford Model T’s out of his general store in Westby, Wisconsin. The company is in its fifth generation of Dahl family ownership with over a century of growth behind it. Today Dahl operates three dealership campuses throughout the Midwestern United States that are home to Subaru, Hyundai, Mazda, Toyota, Chevrolet, Buick, GMC, Ford, and Lincoln au...
Part 3 of our Intercoms in Security Series: Zenitel’s Call Access Panel manages intelligible critical communications through a security operations center or control room Greater connectivity, security software enhancements, more customization, and better sound quality are some of the enhancements driving the intercom market.An advantage now offered on Code Blue’s emergency speakerphones include self-diagnosing software that monitors the status of the phones an...
Meeting a customer’s expectations is a key component of success for any business, including the physical security market. However, understanding customers’ expectations is a big challenge, which is made even more difficult because those expectations are a moving target. We asked this week’s Expert Panel Roundtable: How are customer expectations changing in the physical security market? Their wide-ranging answers highlight elements from technology expectations to adaptability to...
AThe IVX, Inc. is a revolutionary technology startup founded by industry veterans from Cisco, Jupiter and Motorola. The company is dedicated to providing innovative, high performance, fully integrated solutions for the public safety sector that effectively manage collaboration among multiple agencies and improve crisis management response time. The IVX enables real-time surveillance data collection, synchronization and collaboration across the private and public safety sectors. Public Safety Ch...
An access control system was required that would cope with increased levels of hotel staff A London landmark, The Ritz London has been one of the world’s greatest and most renowned hotels since 1906. Minimizing Crime At The Hotel With plans underway to expand The Ritz, staff entrances can often be perceived as an easy option for gaining unauthorized entrance to hotels. An access control system was required that would cope with the increased levels of staff and minimiz...
A building development can fairly be described as ‘iconic’ when it changes the very skyline of a city. That was the case in Islamabad, Pakistan, for Centaurus, a three-skyscraper complex –the tallest buildings in the city – all linked by a prestigious shopping mall. When the four-story mall housing over 250 shops needed a powerful and effective surveillance system, they turned to Hikvision for high quality IP security video. Centaurus is a mixed use real estate developme...
Gaps in video from dropped video frames are a common problem. A web search on the phrase “dropped video frames” turns up links oriented towards gamers, YouTube videographers and even the world of video surveillance, discussing why frame drops happen and providing advice for coping with them. On Windows computers, video frame drops are a fact of life. Much of the advice can help reduce the number of frame drops, though never completely eliminate them. If you are an amateur filmmaker,...
One leading company has developed an identity management system using patents that verify the identity of an applicant Most enterprises rely on background screening providers to report accurate and complete information without understanding the litigious landscape. Security executives often have little input in how background checks are performed or by what provider, as this has become the domain of human resources (HR). A growing trend finds employers and their background scr...
By drawing data from a number of different sources and subsystems, including building automation, it is possible to move towards a truly smart environment Security solutions should be about integration not isolation. Many organizations are considering their existing processes and systems and looking at how to leverage further value. Security is part of that focus and is a central component in the move towards a more integrated approach, which results in significant benefits. G...
Technology is a valuable tool for increasing security, but occasionally technology can create a threat. An example is the threat 3D printing technology poses to one of the most mature security technologies, mechanical locks and keys. The ability of 3D printing to duplicate keys presents new challenges for lock manufacturers, and new vulnerabilities to end users. Keys that could previously only be duplicated by skilled thieves can now easily be copied using off-the-shelf technologies and informat...
As security industry buzzwords go, “convergence” is perhaps the best known and most pervasive. We have been hearing about convergence in our market for almost 20 years. We have heard it’s happening soon. We have heard it’s inevitable. And yet, for all the talk of convergence, it has sometimes seemed there has been more talk than action. We wanted to check in with our Expert Panel Roundtable and get their latest takes on this most enduring of industry buzzwords. We asked t...
Part 1 in our Intercoms in Security Series Lambert-St. Louis International Airport uses Code Blue intercoms Organizations are demanding a new level of interoperability among mission-critical security systems. Intelligible audio, the ability to hear, be heard and be understood, is critical to communication, which is essential to the core security processes within an organization, as well as to emergency situations. Intelligible audio provides a platform to optimize v...
Part 2 of our Intercoms in Security Series The 2N Helios IP family intercoms present a comprehensive portfolio of security offerings for businesses and individuals Some integrators and end users may think of intercoms as older technology that isn’t required as part of a robust security system. Not true. Intercoms include innovative technologies that have developed rapidly, keeping pace with other categories. Just as cameras and access control systems have made techn...
Customers want and expect quality service, whether it is searching for an answer online or speaking to a live person via telephone or face-to-face How do you provide unparalleled, personalized customer service and support in a high-tech, self-service world? This blue ribbon is achievable by fusing the human component of superb customer care with user-friendly, cutting-edge solutions that are available around the clock. Technology has made it possible for customers to get assi...
Once again, ISC West has come and gone. The show continues to please exhibitors and attendees. Reviews are generally glowing and enthusiastic. For all its successes, however, there is a certain repetition from year to year – a lot of the same players, the same technology trends (not to mention the same venue every year, but who doesn’t like Vegas?) But even among the repetition, there is usually at least one element that is surprising. Perhaps it’s the unexpected elements that...
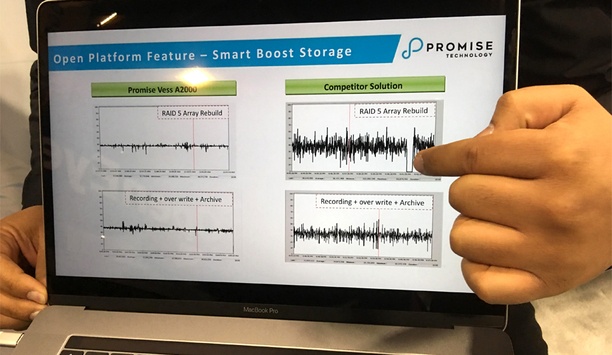
Demand is increasing rapidly for more video, higher quality video, and increasing use of video for innovations like video analytics that provide enhanced security and operational intelligence. The growing demand is driving higher resolutions, larger camera counts, and longer retention times, which have all contributed to the growing importance and higher profile of data management and storage systems in the video surveillance industry. Customers need...
The Deutsches Theater is a Berlin landmark of 19th-century Classical architecture. Built in 1849, it is among the most prestigious theatres in the German-speaking world. It has an elegant, classical façade, 3 stages inside and with the help of CLIQ® technology from ASSA ABLOY, its building security and access management is now flexible, reliable and future-proofed for its 21st-century audience. CLIQ Mechatronic Locking System Security managers at the Deutsches Theater chose CLIQ®...
Over the years, video analytics has gained an unfavourable reputation for over-promising and under-delivering in terms of performance. One of the biggest complaints regarding video analytics has been its inability to correctly identify objects in situations which appear trivial to the human observer. In many cases, this has resulted in a tendency to generate substantial numbers of false alarms, while not detecting actual events accurately. This, together with a propensity for complex set-up proc...
Fredrik Nilsson is Vice President of the Americas for Axis Communications, overseeing the company’s operations in North and South America and serving on the global management team. In his 20-year career at Axis, he has undertaken various roles in both Sweden and the United States. Since assuming responsibility for the Americas in 2003, revenues have increased from $20M to over $450M. Nilsson has also been instrumental in leading the surveillance industry shift from analog closed circuit te...
Lower equipment prices (with less margin) are one industry trend leading more integrators to seek out new sources of revenue. With margins shrinking on lucrative, but unpredictable, “project-based” business, integrators are looking for more revenue stability. One solution is recurring monthly revenue (RMR), which is already common in the related field of alarm monitoring. But where does RMR come from? Creating more RMR also requires that integrators change how they do business, from...
The enthusiasm of ISC West 2017 continued through to the final hours of Friday, reflective of a show jam-packed with new technologies to address industry trends. Exhibitors seemed happy enough with booth traffic, which held up even on the final day. Security Industry Trends Industry trends drove much of the technology. For example, cameras are getting less expensive, which means it’s more cost-effective to specify systems with higher camera counts. Also, cameras are providing more...
Having a quality video surveillance solution to provide a safe and secure environment in shopping centers is more important than ever given the turbulent world we live in. That’s why Norway’s Olav Thon Group turned to March Networks certified partner, Focus Security, to recommend an enterprise-class video surveillance solution to replace an aging system at the Gronland Basar, a shopping center in downtown Oslo. The Olav Thon Group is one of Scandinavia’s largest real estate en...
PVcomBank, one of Vietnam’s fastest growing and most progressive banks, has acquired a cutting-edge March Networks video surveillance system. Established in 2013 through a merger of PetroVietnam Finance Corporation and WesternBank, the Hanoi-based financial institution is a joint stock commercial bank with 115 branches throughout the country. Shareholders include Petro Vietnam with a 52 percent stake and Morgan Stanley with a 6.7 percent strategic interest. Prior to s...
For all its value in the security market, one has to wonder: How much captured video is actually used for security? Among hours and hours of video, only brief segments here or there are ever actually viewed or used for security applications, such as to review an incident or to provide evidence in court. But what about all that other video, much of it stored for 30 or 90 or 120 days or longer? Does it have to be merely a costly consequence of providing the security benefits of video? Not necess...
Browse security news
Featured products
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
The Key To Unlocking K12 School Safety Grants
DownloadHoneywell GARD USB Threat Report 2024
DownloadPhysical Access Control
DownloadThe 2024 State Of Physical Access Trend Report
DownloadThe Security Challenges Of Data Centers
Download- UAE Security companies
- UAE Manufacturers
- UAE Distributors
- UAE Resellers / Dealers / Reps
- UAE Installers
- UAE Consultants
- UAE Systems integrators
- UAE Events / Training / Services
- UAE Manned guarding
- UAE Training organisations
- UAE Associations / regulatory bodies
- UAE Event organisers
- UAE Media
- UAE Services
- UAE Recruitment / personnel




















![[Download] Choosing The Right Solution For Video Data Needs](https://www.securityinformed.com/img/news/612/hitachi-vms-editorial920.jpg)