Hungary News
Value Isn't Always Just About Monetary Worth In any sales conversation, price will inevitably be one of the points of discussion. When it comes to large investments such as security systems, customers want to ensure that their money is well spent. Where price is concerned, systems and solutions providers would want to impart the worth of their products. At the end of the day, in the consumer world, customers want the best value for the least amount of money po...
Access control can sometimes get overshadowed by video surveillance Technology is shifting rapidly in the access control market, but another obstacle is the need to communicate the value of the technology to users. Specifically, access control can sometimes get overshadowed by video surveillance as it competes for a share of the customer’s security dollars. From a pure security standpoint, electronic access control is better suited than video surveillance to keeping...
A planned migration provides the ability to plan, budget and control the path to an improved access control environment The installed base of legacy systems presents opportunities and obstacles for providers of newer access control systems. Most end users would prefer not to do a full rip-and-replace upgrade. Therefore, integrators (and manufacturers) have to find a smooth transition path. Access control customers eager to embrace the newest capabilities on the market are ofte...
Access control systems that leverage proprietary technologies severely limit system flexibility Access control’s ongoing transition from closed systems to more open integration provides benefits for integrators, and especially for end users looking to maximize their system return on investment. End users want greater flexibility, specifically in terms of hardware choice. As a result, more non-proprietary solutions are coming to market. For the integrator, offering more o...
How do you stand out in a world of commoditization? We live in a world of commoditized consumer goods. You probably own at least one item which would be considered "commoditized" by the majority of the population today, but you can probably also remember the days when it would have been described as "new" and "unique". Think about smart phones: most people you know are likely to own a smart phone. But remember when not everyone even a regular cell phone? Now they'r...
Communicating access control information across multiple platforms is simplified with the PSIA's PLAI specification Managing access control across large companies or institutions, including those that span giant campuses or even multiple locations all over the world, is essential to optimum security. Too often, however, the effectiveness of a company’s access control system – or, more likely, of its multiple access systems that were installed in various locations o...
The archives allow organizations to easily scale the available storage capacity of their surveillance system Genetec™, a leading provider of unified IP security solutions recently announced its new Cloud Archives service for Security Center that will allow organizations to easily scale the available storage capacity of their surveillance system, and eliminate the need to invest in additional servers. With the ability to continue leveraging their existing on-premise s...
Identiv reaffirms revenue guidance for fiscal year 2014 of revenue between $80 million and $90 million Identiv, a global security technology company that provides trusted identity solutions for premises, information, and everyday items, reports its financial results for the third quarter (Q3) of 2014. "In Q3 2014, we saw continued growth in revenue and achieved positive adjusted EBITDA," said Jason Hart, Identiv CEO. "The steps taken to streamline our business have allowed us...
The ability to view surveillance footage on mobile devices adds greater flexibility to an organization's security monitoring system. But of course, there are drawbacks. In the age of mobile devices, we are able to do more and more while "on the go" and are less limited by the need to be at a desktop computer with internet / network connectivity. We are seeing the proliferation of mobile apps designed to enable us to access our most important files and perform important tasks...
Safe Cities will be a central hub within IFSEC to shape future of urban security, civil welfare & disaster management IFSEC International, organized by UBM Live, is excited to announce development plans for the leading global security event in June 2015. Following the phenomenal success of the 2014 show, IFSEC International 2015 is in high demand with 92 per cent of the floor plan already sold out. Big name sign-ups and stand out new exhibitors include DELL, Mitsubishi El...
"Going green" is not a new initiative, but rather, one that businesses and individuals are constantly aware of and continuously making a conscious effort to contribute to. The global population has become increasingly environmentally conscious over the years. Businesses and homeowners alike are investing more in green alternatives for their various needs. Many businesses adopt a green business ethic by ensuring that their products and ways of working are compliant with certa...
Remote monitoring offers a multiplying effect on security efforts The growth of IP-based networks has made it possible for security professionals to easily monitor surveillance activity from any internet-enabled PC, smartphone, or tablet anytime, anyplace. More and more, businesses are realizing that remote monitoring can have a significant impact on their bottom line. Whether you’re a retail outlet, bank or hotel, remote monitoring offers a multiplying effect on securit...
Sometimes companies want to buy their physical security software separate from the servers it runs on. Other times, companies prefer to buy an “appliance” – a purpose-built machine that is perfectly matched with the software it is running. The latter category is especially popular among small- and medium-sized business customers. For example, preconfigured video management appliances contribute an element of simplicity. That’s why you see video software companies –...
Iris recognition has been used as a biometric for access control applications for many years, but we have heard a lot more lately about fingerprint scans. However, iris recognition has many advantages over fingerprints and other biometrics, and the technology has come a long way. Mark Clifton, vice president of the Products and Services Division of SRI International, calls the iris a “protected” biometric, typically not injured and unlikely to be contaminated as fingers or hands mig...
Newer concepts and modern security solutions help achieve operational efficiencies in the retail sector Asset protection across retail organizations is a necessary evil. When shrinkage is on the rise, margins are low, competition is fierce and the economic climate is still somewhat uncertain, retailers need to maximize any investment in technology and consider how it can positively impact their bottom line. Steve Bocking, Sales Engineering Manager at Genetec, explains that...
Security standardization reduces operational requirements Controlling identified risks at all of your sites, anywhere in the world, can be difficult. Especially when taking budget constraints into account. How can you ensure all of your people have a secure working environment? And that all employees, everywhere, adhere to your security policy? Nancy Wanders, Business Development Manager Asia/Pacific at Nedap, states that standardising security gives this assurance and more. I...
Cybersecurity is a critically important aspect in today’s increasingly IP-driven world of physical security The physical security market tends to dismiss issues of cybersecurity as outside its area of expertise, but cyber-threats are a problem that has been ignored for too long. The fact is, cybersecurity is a critically important aspect of the systems our industry provides in the increasingly IP-driven world of physical security. And the risk isn’t just reserved...
Just like many things, security systems have their own life cycles. Most end users would say that a "good" system should last a certain amount of time. Each system or device has a generally established and expected life span, and anything that falls short of its life expectancy is generally deemed as "poor quality." We asked some of our panellists to reflect on the life cycles of security systems. We wanted to get their insights on trends they have observed i...
The program helps engineers and consultants develop expertise with DVTEL’s video surveillance technologies DVTEL, INC., the video surveillance solutions provider, recently announced that it has named Jack Meltzer as Senior Director, Global A&E Program. The program helps network architects, engineers and consultants to develop expertise with DVTEL’s intelligent, open video surveillance technologies and to specify projects that incorporate DVTEL solutions. Mr. M...
Especially for younger individuals, sharing on social media is almost an automatic reflex. Bystanders at any event are likely to constantly be tweeting and/or posting real-time words, pictures and video using their smart phones. Accessing a culmination of that data can provide real-time intelligence of what’s happening on the ground at any event or location before emergency responders or police even get on the scene. There are multiple ways security can benefit from an affordable so...
IndigoVision's video technology allows Rio Tinto to control over 200 driverless trucks to move 130 million tons of material When it comes to safety, mining is still seen as one the riskiest industries in the world. Mining giant Rio Tinto recently made the news with its innovative technology approach, making mining safer and more efficient. Using IndigoVision’s video technology, Rio Tinto can now control over 200 driverless trucks to move 130 million tons of material, th...
900 MHz wireless and WiFi (2.4GHz) are different technologies but sometimes used interchangeably 900 MHz wireless and Wi-Fi (2.4 GHz) are sometimes used interchangeably in the access control world to describe solutions that do not require running wires all the way to the opening. It’s true that, as wireless options, both technologies offer some general advantages over traditional hardwired solutions.In this article, Minu Youngkin, Allegion, Integrator Marketing Mana...
DVTEL develops open-standard, end-to-end video surveillance solutions DVTEL, INC., the video surveillance solutions provider, will host an educational webinar on Tuesday, Oct. 28, 2014, to familiarise both integrators and end users with DVTEL Cloud Services, the company’s remote monitoring solution that enables a proactive approach to system monitoring in real-time, from anywhere. DVTEL Cloud Services is a surveillance system health monitoring tool that allows users to...
The general public often has misconceptions about security systems. How should security industry experts educate the general public to better understand security systems and their capabilities? As security industry professionals, our panellists are more than used to explaining security systems to customers and other members of the general public. As experts in the field, it is their prerogative to help set the records straight when it comes to what people understan...
There’s a new international company in the security market this week with the acquisition of Siemens’ Security Products business in Europe by Vanderbilt Industries, a new U.S. company that rebranded the Schlage Security Management Systems (SMS) product line after acquiring it from Ingersoll Rand in August 2012. The European arm of the new global player will be called Vanderbilt International, based out of Germany and led by Managing Director Joseph Grillo, who many remember from his...
The joint solution of SeeTec's Cayuga and BCDVideo recording servers offer customers a powerful and reliable system SeeTec AG and BCDVideo, a global manufacturer of high-performance IP recording systems for the video surveillance market, announced their technology partnership for SeeTec's Cayuga and the BCDVideo product family. As both companies are leading in their segment the cooperation provides high standard for video surveillance projects of any size. Since the year 2000...
Vanderbilt Industries, a global leader providing state-of-the-art security systems, announced today it has entered into an agreement to acquire Siemens’ Security Products business, part of the Siemens’ Building Technologies Division. The business will be renamed Vanderbilt International. Security industry veteran Joseph J. Grillo will be Managing Director, working from the new operational headquarters in Germany.The acquisition will significantly boost Vanderbilt&...
Access control growth is driven by several factors A major shift from PC-based clients systems to solid state, embedded operating systems, browser-based user interfaces, remote services, and changes in compliance legislation are helping drive the rapidly growing adoption of access control systems in both the residential and commercial security markets. John LaFond, VP of Integrated Systems at Linear LLC, explains these contributing factors as Linear LLC looks towards the futur...
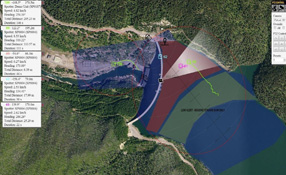
In a layered approach to security, the outermost layer increasingly might refer to an area outside a fence line. The sooner a facility is alerted to a possible threat, the better, and when a threat reaches inside a facility’s fence, it may be too late to mitigate it. Security directors need situational awareness that extends outside the facility and provides the ability to intercept intruders before they become a threat. Zones of interest, or buffer zones, outside a facility’s fence...
Spread of the Ebola virus beyond Western Africa has heightened concerns among healthcare professionals and the general public. In practical terms, healthcare facilities – including their security departments – are preparing to deal with whatever happens next as concerns about the disease continue. Even areas that are not a “hot zone” for Ebola virus exposure may face additional challenges, given uncertainty about the spread of the disease and a possible influx into hospit...
Browse security news
Featured products
Related videos
CLIQ Connect
DNAKE Access Control Terminals: Minimalist Design, Maximum Security!
Unlock the Future with Abloy Pulse: Keyless, Energy-Efficient Security Systems
The Key To Unlocking K12 School Safety Grants
DownloadHoneywell GARD USB Threat Report 2024
DownloadPhysical Access Control
DownloadThe 2024 State Of Physical Access Trend Report
DownloadThe Security Challenges Of Data Centers
Download- Hungary Security companies
- Hungary Manufacturers
- Hungary Distributors
- Hungary Resellers / Dealers / Reps
- Hungary Installers
- Hungary Consultants
- Hungary Systems integrators
- Hungary Events / Training / Services
- Hungary Manned guarding
- Hungary Training organisations
- Hungary Associations / regulatory bodies
- Hungary Event organisers
- Hungary Media
- Hungary Services
- Hungary Recruitment / personnel