Surveillance cameras News
With every technological advance that canbenefit museum management comes anotherthat may assist thieves When protecting art treasures, the first instinct for many security professionals may well be to look at recent advances in technology. Hasn’t the advent of IP-addressable devices provided sufficient tools to protect art exhibits from theft in a discreet manner? Apparently not, and entrenched attitudes abound among curators. Consultants who so much as m...
Williams Meredith recently stepped out of his Kentucky home to see a drone hovering over his porch, videotaping his young daughters by the family pool. It wasn’t the first time one of these small flying devices had wandered over to take a look, but it had never gotten so close. So he did what any red-blooded American would do when confronted with a home invader – he blew it from the sky with a single shotgun blast. The confrontation is another example o...
Ethernet switches are often overlooked andsometimes deemed a cheap connectivity pointwith little to no importance The Ethernet switch is a critical link between cameras, network video recorders (NVRs) and computers that need access to video feeds. The Ethernet switch not only provides the data connectivity but often the power to the IP cameras via Power over Ethernet (PoE). Ethernet switches are the fundamental backbone of a Local Area Network (LAN) and the critical connectivi...
The IoT threat is magnified asuncontrolled devices are introduced into thenetwork through people ‘bringing their owndevices to work’ Intelligent building management, combined with the dramatic increase in IP connected devices brought about by the advent of the Internet of Things (IoT), provides a vast opportunity for large organizations to work smarter, faster and more efficiently than ever before. Intelligent building management systems have the potentia...
Healthcare organizations are an important vertical market for many security manufacturers and integrators. Like other vertical markets, healthcare has its own unique set of requirements and challenges for physical security systems. We asked this week’s Expert Panel: What are the distinctive security problems faced by healthcare organizations? What technologies are being embraced to increase security?
The city of the future needs smart, secure and resilient infrastructure solutions According to the United Nations, the world population will reach almost 8.5 billion by 2030. As populations grow, so do cities. Even now more than half of the world’s inhabitants live in urban areas, and more than one million move from the country to the city every week. This trend places enormous demands on people and infrastructures. Because only when communication, energy, safety, s...
Security cameras provide live, real-time video to assist security personnel in spotting potential or real problems Efficient security systems for parking structures deter criminal activities and anti-social elements from destroying property. Over the years, security companies have responded to this need and developed a range of security systems for parking facilities, such as audio intercoms, access cards and video analytic solutions. Systems integrators who want to add new s...
There's nothing like a visit to the China Public Security Expo (CPSE) in Shenzhen to open your eyes to a new world of security market manufacturers and customers in the Asia-Pacific market. The show is huge by Western standards – someone told me it's five times the size of ISC West in Las Vegas. But even more than the size of the show, it was the crowd that made an impression on this first-time visitor. Huge numbers of attendees and exhibitors Think of the mass of humanity you might exp...
Social media channels have active and consistent users and may constitute a promising audience for security integrator’s marketing efforts If you have any lingering doubts about the impact of social media, consider this: Worldwide, there are over 1.44 billion monthly active Facebook users, which is a 13 percent increase year over year, according to the social media giant. In addition, 936 million people log onto Facebook daily (as of March 2015), whi...
(Click to see larger image) The ASIS Foundation & the University of Phoenix College of Security and Justice's Enterprise Security Competency model Are you competent in your security job or profession? How do you know? According to research carried out by the ASIS Foundation, security has begun to evolve beyond guarding doors, checking IDs and screening briefcases and purses. Today, something called Enterprise Security Risk Management (ESRM) is subsuming the tra...
Major art heists often feature audacity that defeats even the most thorough security protocols Museum security, like art, is ever-changing. Traditional security practices like manned guarding alone are not sufficient to keep thieves at bay. Modern security technologies such as video surveillance, motions detectors, intruder alarms and other physical security devices also play an equally important role in securing museums and its art work. Regrettably, having a...
Home security devices are evolving and expanding their offered features, providing new opportunities for the security industry Home security isn’t just home security anymore. These days cameras, door and window alarms are just pieces of the web–enabled “smart home.” And, the home is getting smarter, as service providers begin to merge home security systems with home automation. The added value of these additional features is now drawing more potential c...
Discussions in our industry about cyber-threats to physical security systems, including IP video, often center around hypotheticals. How might a hacker gain access to a video camera feed? How might he or she enter the larger enterprise system through a software vulnerability related to physical security? We all know assessing threats often involves considering the hypothetical, of course, but we should also seek to learn from actual events in the past. In relation to vulnerabilities of video su...
Problems caused by physical systems in terms of cyber-attack are quite extensive, damaging systems and assets Security experts of various disciplines agree that physical systems are increasingly being leveraged in attacks on organizational networks and supply chains. Many manufacturers maintain that security (including that of security systems) is the responsibility of the end user, which would be fine if they were only expected to maintain security and not create th...
People using computers to surf the Internet is "so 20th century". Today, the big trend involves machines using the Internet to communicate, exchange and analyze data in what has widely become known of as the Internet of Things. Various security devices are among the IoT components, and how devices connect effectively using the Internet – even devices not related to security – will constitute a large part of the future business of security integrators and installers, whether in the re...
For high value individuals such as the Pope,agencies have access to unlimited publicresources in terms of money and people The Pope’s visit to the United States reminds us that protecting big-name executives, celebrities and dignitaries is a highly specialized security function. Public and private executive protection groups begin preparing for the visit of major world figures months ahead of time. “It is a task of massive proportions,” says Tom M. Con...
7K cameras are best suited for large openspaces such as stadiums and city centers,capturing the finest details in their footage With several manufacturers now offering 4K CCTV cameras, Avigilon, based in Vancouver, B.C., raised the bar in April 2015 with the launch of their 7K HD Pro surveillance solution. The 30-megapixel camera is the latest addition to the company’s Professional Series, an innovative model Avigilon believes will drive competition in the security indus...
How do you get all of your various vendors, services, resources, manpower, and technology to integrate and work together? Creating an efficient operating environment in physical security is no small feat - especially when the organization undertaking such an endeavor has a nationwide presence. How do you get all of your various vendors, services, resources, manpower, and technology to integrate and work together? How do you aggregate all of the data being recorded into inf...
With more physical security systems using Internet protocol and being connected to the enterprise IT network, it’s not surprising that the corporate IT department is more involved than ever in the buying decision – for better or worse. Does the IT department bring valuable resources to the table, or are they an impediment to the sales and integration process? It’s not a new issue, but an increasingly important one as the industry changes. We asked this week’s Expert Panel...
Enterprise security strategies identifyliabilities & ways to mitigate risks, showinghow the cost of mitigation prevents largerliabillity costs The security profession continues to take on new risk management responsibilities. The big thing now is called Enterprise Security and Risk Management (ESRM). ASIS International has issued a standard on the subject: ANSI/ASIS/RIMS RA. 1-2015, and a couple of booths at the recent ASIS International 2015...
Hikvision USA’s ascension from virtual obscurity to the upper tier of manufacturers in the U.S. market is being built on the Chinese company’s huge manufacturing capacity – they turn out 50,000 to 60,000 surveillance cameras every day from factories in China. The large capacity enables Hikvision to achieve economies of scale. In effect, they can make high quality video surveillance products at a lower price, a capability that will continue to serve them well as they begin compe...
The open and exposed nature of rail yards exposes railway assets to tremendous risk The importance of rail transportation in driving the U.S. economy cannot be overstated. In recognition of this, America’s railroads are investing in the infrastructure and technology necessary to improve security for the tracks, bridges, tunnels and other vital components that make up this critical transportation network. The unique security requirements of these assets present a nu...
Software changes constantly. There’s always a new patch or fix, and our computers persistently remind us that an update is available. As a core component of today’s IP networked video systems, video management software (VMS) is also subject to the need to be constantly updated and refined. We asked our Expert Panel Roundtable to elaborate: Why is it important that networked video customers keep up to date with the latest version of video management software (VMS)?
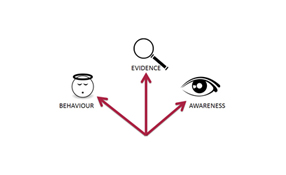
Ballantyne has created the "Three Vectors of Value" for video surveillance - Awareness, Evidence and Behaviiour The annual global expenditure in new video surveillance systems is currently estimated at about 20 billion USD and grows at a rate of better than 15% per year. To those of us in the business, these figures both encourage and validate. The expenditure is impressive, but only because commensurate value is delivered. That is, we expect expenditure and value to bal...
The potential costs and consequences of hackers getting through firewalls and onto the user’s computer networks can be devastating Theft of NATO data. Leakage of emails. Hackers setting up a live streaming website for over 100 New York City private webcams and even hacking the infrastructure servers of the U.S. government. As news of malicious takeover of private and corporate networks as well as incidents of malicious software programs, referred to as malware, conti...
NVR appliances ease analog to IP transition by providing end users with a hybrid-ready product There should be a palatable migration path from a large installed base of analog to the latest IP technology. The biggest missed opportunity related to network video recorder (NVR) NVR appliances in the video surveillance marketplace is effectively using existing analog camera investments while transitioning to the network. For example, IP encoders can be utilized as a bridg...
Aventura continues to expands expand its feature set of products beyond PSIM As the 61st annual ASIS 2015 kicked off in Anaheim, Calif., it became increasingly clear that physical security continues to move from the realm of traditional intrusion detection, video surveillance and alarms into value-added applications that extend into new markets, uses and purposes – many of them centred on business and operational processes. While video surveillance, intrusion detection,...
The potential is huge for vendors in the security and technology industries that have gun detection-related services & products Gunshot detection systems are a fast growing trend that helps police and security guards to protect the public, capture criminals and collect forensic evidence for investigations. Gunshot detectors use digital microphones installed on (or in) buildings or along streets that listen for evidence of gunshots, provide near instantaneous notification,...
Organizations can develop security master plan internally or use the assistance of an independent security consultant Whether it’s a college campus, a healthcare facility or a large corporation, organizations often tackle issues related to security management, operations, programs and technology in a reactionary manner. They often fail to consider the need to plan and develop a written roadmap to define and provide direction for the big picture of their security program....
Have interactive services lost their edge? Are users discouraged and disenthralled? That’s a myth that needs busting, because security companies continue to have success offering these solutions to customers. Alarm companies who began their business with traditional intrusion detection continue to deliver interactive services as part of a total, connected home solution. Companies like Complete Security Systems, Marlboro, N.J.; Marshall Alarm Systems, Yorktown Heights, N.Y.; and The Securi...
Related videos
Find Lost Wallet with Dahua WizSeek
Dahua Traffic Signal Controller Highlight
CLIQ Connect
- View more IP cameras
- IP cameras
- IP Dome cameras
- Intercom Systems
- Network Video Recorders (NVRs)
- Surveillance cameras
KentixONE – IoT Access And Monitoring For Data Centers
Climax Technology HSGW-Gen3 Modular Smart Security Gateway
Delta Scientific DSC50 ‘S’ Barrier: Portable, Crash-Rated Vehicle Mitigation Solution